1. Introduction
Due to the exponential growth of information traffic in fiber-optic communications backbone networks over the last thirty years, the information traffic rate has tripled every two years and is expected to reach its theoretical upper bound of 100 Tbps within a decade [
1]. The more information traffic increases, the more data security should be emphasized. Current information security relies on computational complexity [
2] and is thus vulnerable to both classical [
3] and quantum attacks [
4,
5,
6]. In classical cryptography such as public key cryptography [
7], the key length has gradually increased over decades to protect data from potential eavesdropping, mostly relying on computing power [
8]. As a result, secured data transmission in a classical (unsecured) regime becomes inefficient as the key length increases due to the tradeoff between security and the key generation rate [
8]. Especially for big data-based artificial intelligence applications such as unmanned vehicles and Internet of things applications such as drones, data security must be carried out in an efficient way [
9]. Thus, fundamental innovation in cryptography is required to overcome vulnerabilities in both classical attacks relying on algorithms or computing powers [
3] and quantum attacks relying on quantum parallelism of superposition [
4].
On the contrary, quantum cryptography [
10] has been intensively studied for unconditionally secured quantum key distribution (QKD) over a quantum channel ever since the first QKD protocol of BB84 [
11]. Due to imperfect single-photon detectors and quantum channel losses resulting in quantum loopholes however, QKD is also vulnerable to quantum attacks from a practical point of view [
12]. The detection loopholes affect all QKD protocols, including decoy states [
13] for single photons and Bell states [
14] for entangled photon pairs. For transmission distance, QKD is strongly limited by the no-cloning theorem prohibiting duplication or amplification [
15], unless quantum repeaters are implemented [
16]. Moreover, there are no commercially available deterministic single-photon or entangled-photon pair generators yet, resulting in an extremely low QKD rate [
10]. Besides, the key must be used only once to keep the unconditional security guaranteed by quantum mechanics [
17]. Quantum networking among many parties is much harder to realize due to the limitations of multipartite entangled photon-pair generation [
18]. Based on these practical issues, quantum cryptography seems to have a long way to go for commercial network applications such as e-commerce, including online banking and IoT via both wired and wireless communications [
19], even though some point-to-point QKD protocols have already been launched for a testbed [
20,
21]. Further, QKD is incompatible with conventional information infrastructures in the classical domain such as wired and wireless networks, and thus severely limits its applications in mass data communications such as artificial intelligence based on big data [
22].
To overcome the limitations of classical and quantum cryptographies, an entirely different method of unconditionally secured classical key distribution (USCKD) has been proposed for both wired [
23] and wireless [
24] transmissions using a pair of transmission channels forming a Mach-Zehnder interferometer (MZI) via quantum superposition between the MZI channels and its unitary transformation, resulting in deterministic randomness.This deterministic randomness represents no eavesdropping due to measurement indistinguishability caused by quantum superposition in the MZI channels, as well as the deterministic key distribution between two remote parties via unitary transformation. As demonstrated, the key generation determinacy in USCKD [
23] is well understood in the coherence optics of MZI in terms of the directional determinacy [
25]. The basis of eavesdropping randomness in USCKD has also been understood as measurement indistinguishability caused by channel superposition, as in Young’s double-slit experiments [
26]. Here, a network-compatible USCKD (NC-USCKD) protocol is presented, analyzed, and discussed for arbitrary networking in the classical domain, where a commonly shared pair of transmission lines of MZI plays a key role in both the physics and infrastructure. The classical channel represents a lossy and unsecured transmission line, resulting in open access by anyone. In the proposed NC-USCKD scheme, unconditional security is achieved coherently via addressable quantum superposition between two arbitrary parties in a network through the shared MZI channels. For the robustness of the MZI system, real-time phase stabilization has already been experimentally demonstrated for a few km ranges in both wired [
27] and wireless schemes [
28].
For the network addressability of the present NC-USCKD, addressable quantum superposition between arbitrary two-remote parties is presented as a building block of unconditionally secured classical networking. Compared with the original point-to-point transmission scheme of USCKD [
23], the addressability in the present NC-USCKD is due to the linear expansion of orthogonal bases through the shared MZI channels for N-to-N networking. For the unconditional security of NC-USCKD in a classical network, we also present an authentication protocol via network initialization between any arbitrary parties. The practical advantages of NC-USCKD include high-speed key distribution, addressable networking, and compatibility with conventional optical systems relying on the wave nature of coherence optics. Owing to the coherence optics of MZI [
25,
26], NC-USCKD is naturally compatible with classical systems such as optical switches, optical routers and even optical amplifiers. The phase locking in an optical amplifier such as an erbium-doped fiber amplifier is technically assured due to its coherence optics for regeneration in the fiber-optic communications networks [
29]. The classical compatibility offers a great benefit to the current bottlenecked big-data applications based on CMOS technologies and can lead to a breakthrough in present mass data communications networks.
3. Results
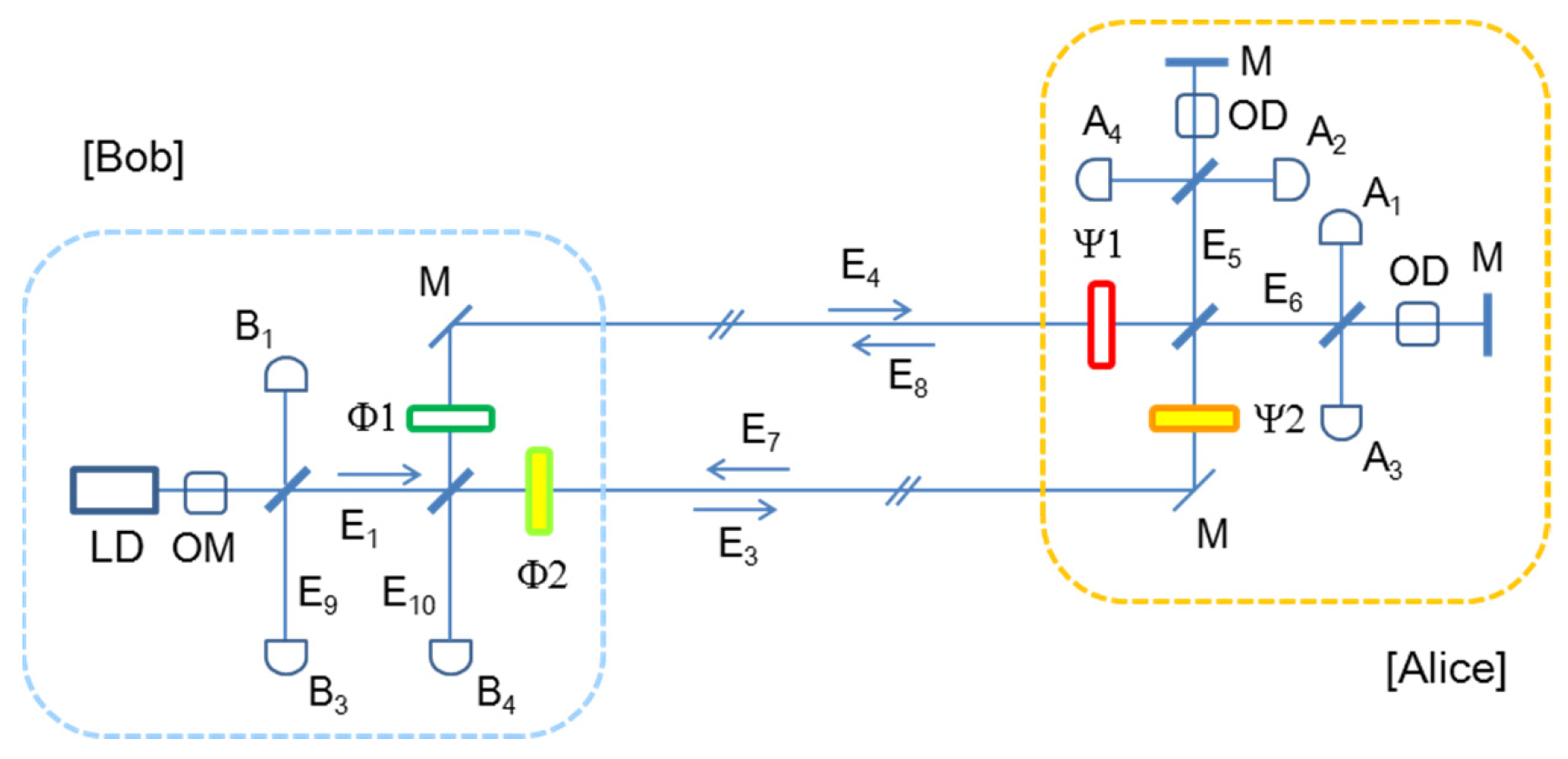
Figure 1 shows a schematic of the proposed NC-USCKD based on a shared pair of round-trip MZI transmission channels in an N-party composed network, where addressable remote parties are called Alice and Bob. Here, the round trip configuration of MZI is the same as symmetrically coupled double MZIs, where Bob (Alice) controls the first (second) MZI. For the N-party networks, the number of arbitrary pairs for networking is
, which is a quadratic expansion. This quadratic scalability in networking may be solved via multi-party superposition, which is beyond the present scope (discussed elsewhere). Each party has dual phase shifters to encode/encode one’s phase bases represented by, for example,
and
for the phase shifters
and
at Bob’s side or
and
for
and
at Alice’s side, respectively. The MZI scheme in
Figure 1 has nothing to do with the phase encoded BB84 protocol [
30], where USCKD uses a pair of transmission channels for deterministic randomness via quantum superposition and its unitary transformation [
23]. For NC-USCKD, the phase controllers
and
are added to the original scheme of USCKD for the purpose of addressable networking, where the original phase controllers (
and
) are used for the unconditional security via deterministic randomness in the doubly coupled MZIs. In USCC without
and
[
23], the round-trip MZI results in the deterministic randomness if
is satisfied, where
and
have the same set of orthogonal phase bases:
. The opposite case of
also works for the key distribution if bit-by-bit network initialization is performed [
23]. Here, we briefly seek an N-party addressable condition in the NC-USCKD scheme of
Figure 1: The phase basis ‘0′ (‘
’) represents the key ‘0′ (‘1′).
According to the unitary transformation in a round-trip MZI configuration of
Figure 1, the returned light (E
9 and E
10) at Bob’s side must satisfy the identity or inversion relation if no network error occurs:
. Here, the added phases
are the assigned address parameters for their sites. As discussed already in USCKD [
23], unconditional security is performed with the phase bases of
and
. For a fixed address set
, Bob randomly prepares a key with his phase basis
, and sends it to Alice: this is the key preparation stage. Relative to Bob’s prepared lights (E
3, E
4), Alice’s phase
is transparent. Likewise, Bob’s phase
is also transparent to the returned light (E
7, E
8). Alice measures her visibility V
A to copy Bob’s choice of
(see
Table 1 in [
23]). Then, Alice randomly chooses her phase basis for
to shuffle Bob’s phase choice and sends it back to Bob: this is the key selection stage. If the returned light E
9 (E
10) hits the detector B
3 (B
4), the identity (inversion) relation is satisfied for the unitary transformation of the MZI matrix in
Figure 1 (
Section A of the Supplementary Information). If Alice chooses the same (opposite) basis as Bob, this results in the identity (inversion) relation. Unlike QKD, the key distribution of USCKD is fully deterministic without the need for sifting due to the MZI directionality, where sifting is used to induce eavesdropping randomness and the unconditional security is provided by the no-cloning theorem of quantum mechanics in QKD [
15]. Thus, the random phase shuffling by Alice corresponds to sifting of the QKD for eavesdropping randomness. Here in NC-USCKD, eavesdropping randomness is achieved by network initialization (see
Table 1). Depending on the key distribution strategy, the inversion case (
Section B of the Supplementary Information) can also be included (see
Table 2) for the key distribution. From Equation (1), the following phase relationship between Alice and Bob is obtained for identity and inversion relations, respectively:
with a deterministic key distribution according to the MZI physics of transmission directionality, the control phase bases
in Equations (2) and (3) must be shifted by the address phase
. For example, the modified phase basis
in
Figure 1 is
, where
is the original binary basis (0,
); similarly for
:
, where
is also the original binary phase basis (discussed in
Figure 2). Due to the phase matching condition of
in USCKD for the identity relation, Equation (2) results in
. In a similar analogy for the inversion case of
, the modified phase basis becomes
(
Section B of the Supplementary Information). Owing to the network addressability with
or
for the identity or inversion case, NC-USCKD works for any arbitrary phase address. Thus,
Figure 1 functions as a basic building block of network compatible USCKD in the classical domain.
In more detail, the control phase depends on for arbitrary networking with a particular address at , where . Obviously, the value varies based on the assigned address with at . As a result, the corresponding phase at Alice’s side also becomes shifted by , satisfying Equation (2), resulting in for the identity relation; otherwise, for the inversion relation. Here, the address phase at plays a key role in addressable networking in NC-USCKD, where can be considered as a continuous phase variable (CPV). This is the generalization of USCKD for networking without changing the original physics of USCKD. Keeping this in mind, we investigate the CPV property in NC-USCKD for the network addressability.
Figure 1 shows a paired party assigned to the address set
through a shared pair of transmission channels of MZI in the N-party network (
Section C of the Supplementary Information). The coherent (bright) input light pulse E
1 in
Figure 1 is launched from a coherent laser (LD) through an optical modulator (OM) by Bob. A random phase basis
controlled by the phase shifter
is added to the split light E
4. The other split light E
3 is encoded by the address phase shifter
with a phase variable
, where
. As explained above, only the
—corresponding receiver (Alice) with the
address satisfies Equations (2) and (3) for deterministic randomness of USCKD through the commonly shared pair of MZI transmission channels. Here, the MZI determinacy represents the phase-dependent transmission directionality: If
assuming no network errors, detector A
1 (A
2) always clicks with E
6 (E
5) for
. The
—controlled returned light E
8 along with E
7 by Alice is also governed by the same MZI transmission directionality, resulting in the identity or inversion relation (discussed in
Figure 2 and
Figure 3). For the return lights of E
7 and E
8, both phases
and
are invisible as mentioned above. Likewise,
and
are invisible to E
3 and E
4, respectively.
Figure 2 shows numerical calculations of the MZI determinacy for the output lights E
5 and E
6 on Alice’s side as well as the measurement randomness (IN
5,6) in the shared pair of transmission channels. The related matrix representation
of the directionality for E
5 and E
6 at the MZI interferometer is as follows:
where
. The added phase
causes a
—phase shift in E
3 in the lower transmission line. To compensate the phase shift,
must be adjusted accordingly for E
4 in the upper transmission line. Thus, the modified phase at
must be
, where
,
, and
is the binary phase basis of
. With this modified phase, Equation (4) can be easily proved for the MZI determinacy (directionality) with an arbitrary value of
for
.
For the numerical demonstrations of the
—dependent MZI determinacy mentioned above, two basis values of
are used to test both the visibility V
5,6 and the interference IN
5,6. Here, the interference IN
5,6 should be the same as IN
3,4 if Eve has the same measurement tool as Alice’s. However, Eve’s measurement with the same interference tool results in either an in-phase or out-of-phase scenario with the same probability due to the measurement indistinguishability caused by the MZI path superposition.
Figure 2a is the reference for
, while
Figure 2b is for any arbitrary value of
.
Figure 2a shows a typical fringe pattern of visibility
, where the maximum occurs at the phase bases,
(see the green dots in the solid curve). On the contrary, the interference
results in the same value for both bases, resulting in measurement indistinguishability (see the green and orange dots in the dotted curve). As discussed in [
21], IN
5,6 should be the same as IN
3,4, showing the physical origin of the measurement immunity in the MZI path corresponding to the no-cloning theorem in QKD. The phase shift of
by the address value of
is numerically demonstrated in
Figure 2b for
. For the maximum visibility
, the phase shift condition is also satisfied. This linear phase shift relation in
with
reveals the infinite number of phase variables in
, resulting in the CPV characteristics of the present protocol as shown in
Figure 2c. In other words, the address phase
is used for networking to the corresponding
at Alice’s side. The corresponding interference IN
5,6 always has the same value if
is satisfied, as shown in
Figure 2d. Thus,
Figure 2 demonstrates the
—dependent MZI directionality in the NA-USCKD scheme of
Figure 1 as well as the indistinguishability in eavesdropping (discussed later). The resulting addressable condition on Alice’s side is
.
Because the relation
must be satisfied for the one-way deterministic key transmission in
Figure 1,
on Alice’s side must be equal to
according to Equation (2).
Figure 3 shows the numerical calculations for the present NA-USCKD with addressable CPV of
and
. To satisfy the identity matrix at Bob’s side for the returned light, the visibility of
for both bases
is numerically shown in
Figure 3a for the right condition of
:
. However, for the wrong condition of
, the maximum visibility of V
B fails. Thus, Equations (2) and (3) are proved, where the modified phase basis of
becomes continuous because
is continuous:
. In practice however, the possible number of CPV is of course determined by the detector’s sensitivity and MZI phase stability.
Figure 3a,b represents for the
—independent identity relation
in the round-trip MZI scheme of
Figure 1. For the address matching condition (
as shown with the dashed curve in
Figure 3a, all
values satisfy the correct V
B if
. The visibility V
A (=V
5,6) is broken if
(see
Figure 2b). Thus, only the dotted curve with
=
in
Figure 3b satisfies directionality condition in both sides with
and
(see the open circle). This is because
must be shifted by the
value, and the shifted
affects
to keep
.
For the key distribution process in
Figure 2 and
Figure 3, how does Alice know the correct
? In other words, how does Bob send his prepared key to Alice without revealing it to Eve? The answer to this question is given by authentication. If
for a wrong choice, the identity relation (
) must fail as shown in
Figure 3c,d (see the open circles). For the correct choice
, both Bob and Alice automatically have
—phase shifted
and
, respectively. Thus, their visibility measurements must fulfill the identity (or inversion) relation. If there is any mismatch in the address
, the return light cannot satisfy the identity (or inversion) relation as shown in
Figure 3d (see the open circle):
. Here,
means that detector B
4 is also clicked on for E
4, indicating an error. Like USCKD [
23], this property of NA-USCKD is also deterministic in the key distribution with random eavesdropping owing to the MZI physics. Details of authentication are discussed in the section on network initialization.
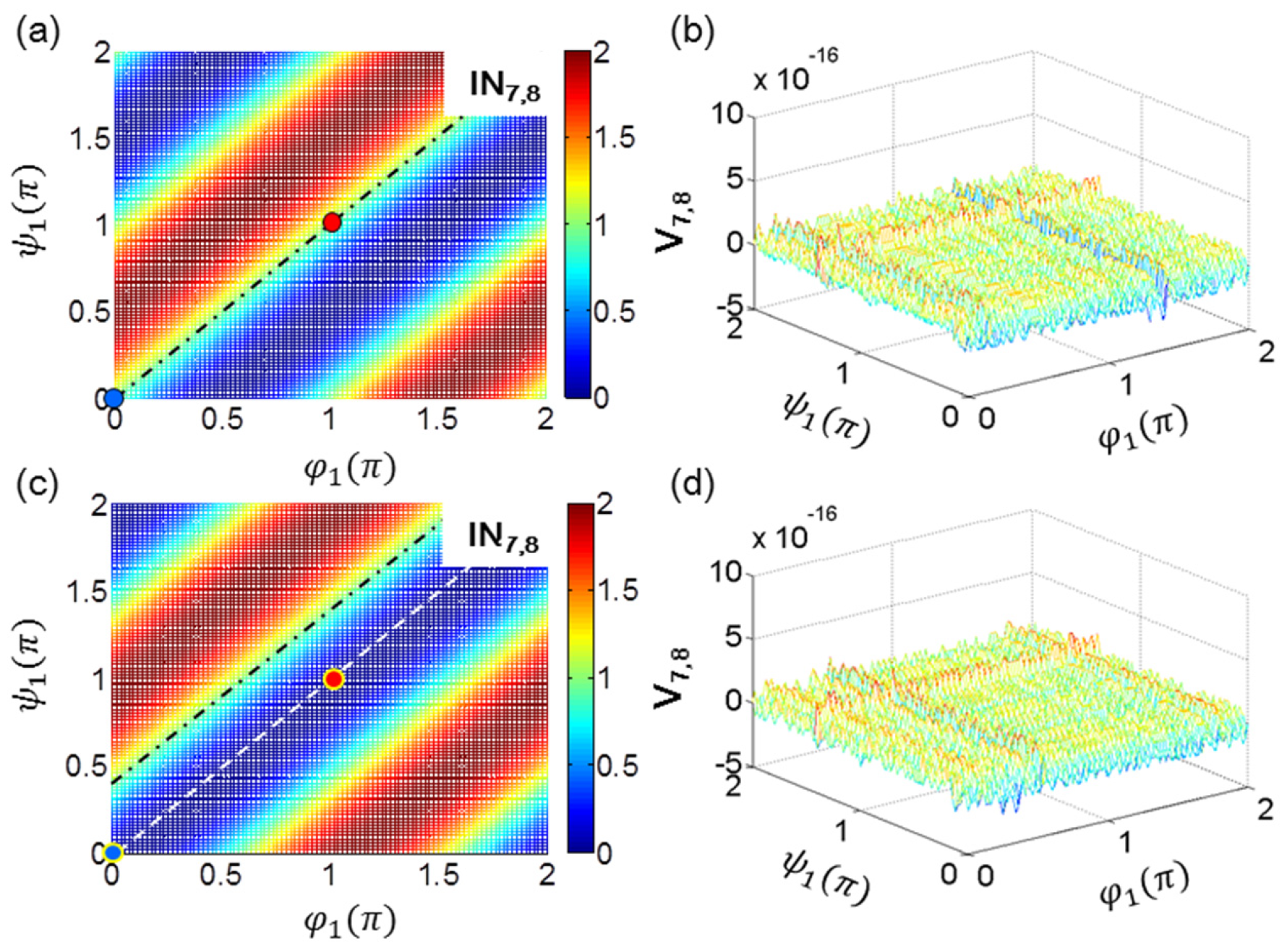
Figure 4 shows numerical calculations for the MZI channel measurements in
Figure 1 for the demonstration of unconditional security in NC-USCKD. The matrix representation
is for both E
7 and E
8 in the MZI paths of
Figure 1:
where
is satisfied (see
Section D of the Supplementary Information).
Figure 4 shows both the interference IN
7,8 and visibility V
7,8 in the shared MZI channels for a smart eavesdropper. Although the channel intrusion by Eve without altering the output fringe is theoretically and technically possible with the same measurement tool, Eve’s chance to decode is just 50% on average because there is no way to keep the same phase difference as Bob or Alice. In other words, the same fringe pattern (visibility) can be achieved by Eve, but the absolute phase information of the light carrier is impossible due to the superposition between the two paths. Thus, Eve’s eavesdropping chance with fringe coincidence is random, resulting in unconditional security. Moreover, a random phase-basis selection technique is added to prevent classical attacks such as memory-based attacks [
23]. According to Equation (2), Alice’s phase adjustment on
with
is automatic as discussed in
Figure 3.
Figure 4a,b is for the address matching
between Alice and Bob, while
Figure 4c,d is for mismatching
. Regardless of knowing or unknowing the address set
,
, Eve’s channel attack must fail due to the MZI physics as well as the channel independence of coherence optics, as shown in
Figure 4. This measurement randomness by Eve is rooted in Equation (5), where the four phase exponents of the matrix elements are all same. Thus, the eavesdropping randomness and measurement indistinguishability in the shared MZI channels by Eve are sustained for
—dependent network channels, resulting in the unconditional security in NC-USCKD.
3.1. Network Initialization: Network Addressing and Authentication
In an N party attached classical network configuration through a commonly shared pair of MZI transmission channels, the network initialization includes network authentications between the two parties assigned by the corresponding address set of
and
. For the deterministic randomness analyzed in
Figure 1,
Figure 2,
Figure 3 and
Figure 4, the network initialization between arbitrary two parties in the network is a prerequisite process to avoid any potential eavesdropping. Suppose that Alice and Bob represent any paired party in the network connected by a specific address set of
and
, respectively (see
Figure 1). For a preparation stage, first, Alice shuffles the MZI network by randomly shifting her phase shifter
with a phase parameter
. Alice is now ready for scanning
for her visibility V
A. Second, Bob repeatedly sends the same test key encoded by his phase shifter
with
randomly. Third, Alice scans her phase shifter
until she obtains an interference fringe of the maxima. Then, Alice sets her phase basis with the
—added one:
. This modified phase set has a 50% chance of correctness due to the MZI randomness as mentioned above for Eve. The network initialization results in authentication.
Eve can also do the same as Alice does, but her chance is worse than for randomness due to . The chance for Eve to have the same as Alice’s is extremely low. In principle, two independent MZI systems set for Bob-Eve and Bob-Alice have a rare chance to be the same as each other, unless the input information by Bob is known to Eve, which is prohibited by definition. This small chance depends on the detector sensitivity, which is lower than one in a million in commercially available avalanche photodetectors. This sensitivity-based resolution defines the maximum number of possible addresses in the network. Of course, the network address number can be increased infinitely by using address layers, e.g., by expanding the address set with the j hierarchy. Although Eve has luckily found the assigned by Alice, Eve still has 50% chance to coincide with Alice’s.
The network initialization is summarized in
Table 1, where the sequence number 1–4 applies for Sequence below. For this, Alice randomly resets the MZI system by modifying her phase shifter
with a new phase variable
as mentioned above, as a preparation stage: Sequence #0. First, Bob randomly selects
for the light pulse E
4 in
Figure 1 and sends it to Alice along with E
3 (see
Figure 2): Sequence #1. Second, Alice measures V
A and randomly sets her phase controller
with either
or
to send the reflected light to Bob: Sequence #2. Alice announces the result of V
A publicly. Note that Alice never announces her phase choice either for
or
. Third, Bob measures his V
B and publicly announces whether Alice’s measurement is correct or not: Sequence #3. Lastly, Alice knows secretly and deterministically whether the
is correct or wrong: Sequence #4. If it is wrong, Alice just adds a
phase to
, otherwise keeps it as her final phase basis set of
.
Table 1 is for the case of a
—phase shifted
.
- 0.
(Network preparation) Initially Alice resets the MZI network by disturbing the MZI with her phase controller and scans until she gets for the test bits provided by Bob. The is a phase variable added to her phase basis . Then, Alice gives a cue to Bob.
- 1.
Bob randomly selects his phase basis , encodes his light with , and sends it to Alice.
- 2.
Alice measures VA, publicly announces the result, and returns the -set light to Bob after encoding it with .
- 3.
Bob measures VB and publicly announces whether Alice’s result is correct (O) or not (X).
- 4.
Alice resets her phase basis to either or depending on the Bob’s announcement: end of network initialization.
Eve may also perform the same network initialization of
Table 1 with an arbitrary value of
for her phase shifter,
. As a result, Eve obtains the same pattern but with unsynchronized maxima with respect to Alice’s because
due to the asymmetry of independent systems. The synchronization chance (
) between Eve and Alice is extremely low, where the chance is decided by the detector’s sensitivity as mentioned above: a commercially available detector sensitivity is very high (>10
4 V/W at GHz). Thus, the addressable networking with unconditional security is achieved by network initialization as shown in
Table 1. The unconditional security is effective with a 50% chance (randomness) via information theory [
31]. As discussed with memory-based attacks [
23], Eve has no chance of eavesdropping the data. One might suggest that Eve’s eavesdropping trials may shift the V
A value causing an error, where the shift must be consistent owing to Eve’s abilities in the coherence setup. However, a consistent V
A shift to Alice does not affect the initialization process at all, otherwise, confirms Eve’s intrusion. Thus, network initialization implies both network addressing and authentication between two addressees because this process completely removes the potential eavesdropping chance by Eve.
3.2. Key Distribution Protocol
Table 2 shows the key distribution procedure without sifting for the present NC-USCC in
Figure 1. This procedure accompanies the network initialization at each order to avoid the memory-based attack, otherwise sifting is performed [
23]. Below is a summary of the key distribution process: Procedure. After network initialization, Bob prepares a random key using the orthogonal bases of
and sends it to Alice via the shared MZI transmission lines. Then, Alice randomly selects the Bob-prepared one using her phase bases
and set it for a raw key. Here,
is modified via the network initialization in addition to the individual address
. Owing to the directional determinacy of MZI, both parties deterministically share the same raw key by simply reading out their visibilities (V
A; V
B). Both the identity and inversion relations in V
B are used for the row keys, resulting in a nearly 100% bit rate. If bit-by-bit network initialization is not performed, then a usual sifting process is performed for a batched order based on the identity relation in V
B (
Section E of the Supplementary Information). In this added sifting case, the network initialization is performed for the batched order. For error corrections, both parties finally publicly announce their error bits only (red numbers), and then remove them from the row key chain. As a result, the same length of final key (m) is shared between Alice and Bob. Here, the mark X represents the discarded bit resulting from the error correction. To evaluate the error rate, Bob compares the final key chain (m) with his prepared one. Privacy amplification may be added by randomly selecting some bits in the final key chain to calculate the error bit rate. The following is the key distribution procedure for NC-USCKD (see
Table 2).
- 0.
The network initialization is performed for both network addressing and authentication: see
Table 1.
- 1.
Bob randomly selects his phase basis to prepare a key and sends it to Alice.
- 2.
Bob converts the chosen basis into a key for his key record x: x , if , x = 0; if , x = 1. The is not influenced by the network initialization process.
- 3.
Alice measures her visibility VA and keeps the record.
- 4.
Alice copies the Bob’s key for her record y via MZI directionality: if VA = 1, y = 0; if , y = 1; if , y = VA (error).
- 5.
Alice randomly selects her phase basis
, encodes the return light, and sends it back to Bob. Here, the
is a corrected value as a result of the network initialization process: see
Table 1.
- 6.
Alice converts the chosen basis into a key record z:; if , z = 0; if , z = 1.
- 7.
Alice compares y and z for the raw key mA: . If , (error).
- 8.
Bob measures his visibility VB and keeps the record.
- 9.
Bob sets the raw key mB via MZI determinacy: if
, ; , . If , .
- 10.
Alice and Bob publicly announce their error bits and remove them from their raw keys to set the shared final key, .