Design of Inter-BAN Authentication Protocols for WBAN in a Cloud-Assisted Environment
Abstract
:1. Introduction
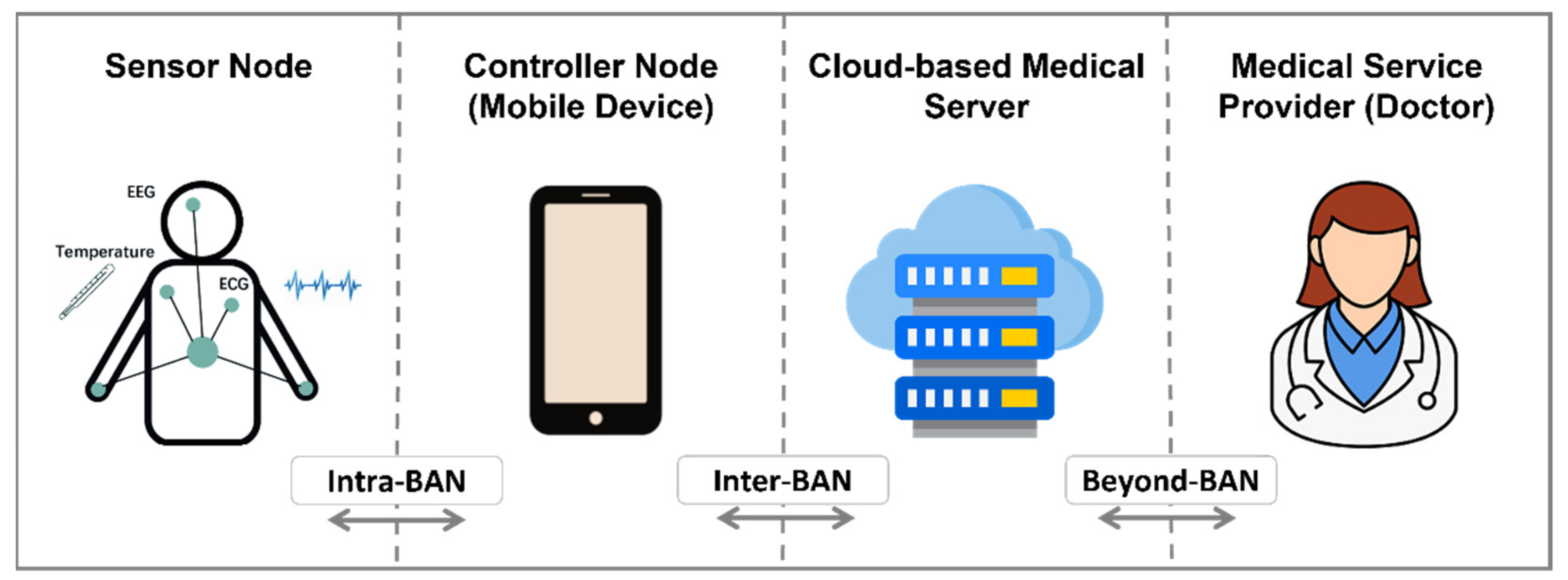
1.1. Overview of WBAN
- In the intra-BAN tier, communication takes place between sensor and controller nodes. The patient’s data is monitored and captured by sensors, and it is subsequently transmitted to the controller node through an unsecured channel.
- In the inter-BAN tier, communication takes place between a controller node and a medical server. Software is developed at the controller node/local server for gathering data from sensor nodes and then sending it to the medical server via unsecured channels. In addition, another software is developed at a remote medical server to obtain the data from the controller and store it in the database system for further analysis.
- In the beyond-BAN tier, communication takes place between a medical server and a doctor. The medical server can be in the cloud, and the doctor can view the data stored on the server.
- The Trusted authority initializes the system and registers the system parties.
- The patient wears sensing devices to gather sensitive medical data, which is then transferred via public channels for medical purposes.
- The doctor can request access to the patient’s data and provide appropriate treatment measures.
1.2. Problem Statement and Main Contributions
- How do we achieve secure and efficient inter-BAN authentication protocols for WBAN in a cloud-assisted environment?
- We design two inter-BAN authentication protocols for WBAN: P-I is for emergency authentication, and P-II is for periodic authentication.
- We conduct an informal security analysis to demonstrate that our protocols meet all of the security requirements in this research.
- We evaluate our proposed authentication protocols using BAN logic and the AVISPA simulation tool.
- We conduct a performance analysis in terms of computation and communication costs.
1.3. Research Scope
2. Literature Review
2.1. Preliminary
2.1.1. Elliptic Curve Cryptography
- Elliptic Curve Discrete Logarithm Problem (ECDLP): Given an elliptic curve Eq(a, b) and two points Q, P on Eq(a, b) such that , it is hard to determine an integer n.
- Elliptic Curve Diffie-Hellman Problem (ECDHP): Given an elliptic curve Eq(a, b) and three points P, x.P, y.P on Eq(a, b), it is hard to determine .
2.1.2. Adversary Model
- All messages exchanged through public channels are completely under the control of the attacker [27].
- A patient’s controller node/mobile device can be stolen, and the attacker can access the data on it [28].
- A patient’s identity (IDi) or password (PWi) could be guessed by an attacker, but not both at the same time [29].
- An attacker has the ability to launch attacks through public channels [30].
- The private key of the trusted authority cannot be compromised by the attacker [31].
2.2. Requirements of WBAN Authentication Schemes
- Emergency and periodic authentication protocols: Whenever a sensor identifies an emergency in the body of the patient, the patient’s controller device begins an emergency authentication with the medical server to send the emergency report in a secure manner. Likewise, when the patient’s data must be obtained from the controller node and stored on the server at a specific time, the cloud-based medical server begins a periodic authentication with the controller node to ensure secure data transmission.
- Perfect forward/backward secrecy: Future and past keys will not be compromised.
- Anonymity and Untraceability: This refers to an attacker’s inability to determine a patient’s identity via message eavesdropping and tracking a patient through messages transmitted during earlier sessions.
- Secure password change: A legitimate mobile device’s password cannot be changed at will by an attacker since the attacker is unaware of IDi and PWi.
- Controller node revocation: It is essential to include a revocation mechanism if a patient’s mobile device/controller node is lost or stolen.
- Replay attack: When messages are sent through insecure channels, an attacker can obtain them. However, if the message has a timestamp, the attacker cannot launch a replay attack.
- Session key disclosure attack: An attacker cannot extract secret values from messages transmitted over an unsecured channel. This prevents the attacker from computing the session key.
- Off-line guessing attack: A patient’s IDi or PWi could be guessed by an attacker, but not both at the same time.
- Impersonation attack: An attacker is unable to generate an authentication message to pretend to be a real entity.
- Controller node stolen attack: An attacker who gets a valid patient’s controller node cannot retrieve any information on it.
- Known session-specific temporary information attack: The session key cannot be computed even if an attacker has the random values produced securely throughout the session.
- Desynchronization attack: This attack, which corrupts the communication between two parties, should be prevented by updating the data kept on both parties during the authentication.
- Computation cost: This refers to the computational load on the involved parties. The computational cost should be minimized since it is critical for devices with constrained resources.
- Communication cost: This is the cost of exchanging messages in terms of bit sizes and communication overhead between the parties participating in the authentication. Regarding communication overhead, the authentication messages should require at most one round trip.
2.3. The Existing Authentication Schemes in WBAN
2.4. Findings
3. Proposed Scheme
3.1. Initialization Phase
- TA chooses an elliptic curve Eq(a, b) over a finite field Fq, and a base point P on Eq(a, b).
- TA chooses a hash function h:{0,1}* → Zq*.
- TA creates a secret number STA ∈ Zq* as its secret key and computes its public key PKTA = STA * P.
- TA makes the parameters (Eq(a, b), PKTA, P, q, h) public while keeping STA secret.
3.2. Registration Phase
- Pi selects IDi and PWi, then produces a number randomly ai ∈ Zq*, and calculates HIDi = h (IDi || ai). Pi transmits (IDi, HIDi) to TA in a secure manner. Then TA calculates Si = h (IDi || STA) as CN secret key, PKi = Si*P, SIDi = (HIDi * STA)*PKTA, and CIDi = h(HIDi || STA). TA stores HIDi and IDi in secure memory and makes (PKi) public.
- MSh chooses IDh and sends (IDh) to the TA securely. Afterward, the TA produces ui ∈ Zq* and retrieves HIDi from secure memory. TA then calculates Sh = h (IDh || STA) as MSh secret key, PKh = Sh*P, Vi = ui ⊕ h (Sh), Wi = HIDi ⊕ h(ui), and REi = CIDi ⊕ h(Sh). The TA makes (PKh, IDh) public.
- TA sends (Sh, HIDi, Vi, Wi, REi) to MSh securely. MSh defines Sh as its secret key and computes PIDh-i = HIDi ⊕ h(Sh). MSh stores PIDh-i, Vi, Wi, and REi in its memory.
- TA sends (Si, SIDi, CIDi, Vi) to CN securely. CN defines Si as its secret key and creates a number bi ∈ Zq*. CN then computes HPWi = h (IDi || PWi || ai), APi = h (IDi || PWi) ⊕ ai, BPi = HPWi ⊕ bi, CPi = SIDi ⊕ bi * P, DPi = h (ai || bi || HPWi || SIDi), and EPi = CIDi ⊕ SIDi. CN keeps (APi, BPi, CPi, DPi, EPi, Vi) in its memory.
3.3. Authentication P-I
- Pi enters IDi and PWi to CN. Then CN calculates ai = APi ⊕ h(IDi || PWi), HIDi = h(IDi || ai), HPWi = h(IDi || PWi || ai), bi = HPWi ⊕ BPi, and SIDi = CPi ⊕ bi*P. Then, CN verifies if DPi ≟ h(ai || bi || HPWi || SIDi), Pi is logged into CN successfully.
- CN produces a number ri ∈ Zq* and a current timestamp T1. CN calculates XRi = ri* P, Xi = ri * PKh, Ji = Vi ⊕ Xi, and Li1 = h (Xi || HIDi || T1 || IDh || Vi). Afterward, CN transmits the message (XRi, Ji, Li1, T1) to MSh through an unsecured channel.
- When (XRi, Ji, Li1, T1) is received, MSh validates the timestamp, i.e., if |T1 − T1*| < ΔT, where T1* denotes the time of message receipt, then MSh calculates Xi = XRi * Sh, Vi = Ji ⊕ Xi, then retrieves Wi of Vi from its memory and calculates ui = Vi ⊕ h(Sh), and HIDi = Wi ⊕ h(ui). MSh checks whether HIDi ⊕ h(Sh) ≟ PIDh-i is in its memory. If this condition is met, CN of Pi is registered. MSh then checks whether Li1 ≟ h (Xi || HIDi || T1 || IDh || Vi). If so, then CN is authenticated.
- Next, MSh creates random numbers rh ∈ Zq*, ui+ ∈ Zq*, and current timestamp T2. Then, MSh calculates Rh = rh * P, Vh = rh * PKi, Vi+ = ui+ ⊕ h(Sh), Wi+ = HIDi ⊕ h(ui+), and SKi-h = h(HIDi || Vh || Xi || Vi). MSh replaces (Vi, Wi) with (Vi, Wi, Vi+, Wi+), then computes C1 = Vi+ ⊕ Vh, and Li2 = h (Vh || SKi-h || IDh || HIDi || Vi+ || T2). Then MSh transmits the message (Rh, Li2, C1, T2) to CN through an insecure channel.
- When (Rh, Li2, C1, T2) is received from MSh, CN checks the validity of the timestamps. If |T2 − T2*| < ΔT, where T2* denotes the time of message receipt, then CN calculates Vh = Si * Rh, SKi-h = h(HIDi || Vh || Xi || Vi), and Vi+ = C1 ⊕ Vh. CN checks if Li2 ≟ h (Vh || SKi-h || IDh || HIDi || Vi+ || T2), CN replaces (Vi) with (Vi+) in its memory, MSh is authenticated, and SKi-h is created between CN and MSh.
3.4. Authentication P-II
- MSh generates secret numbers fh ∈ Zq*, bh ∈ Zq*, and current timestamp T1. MSh retrieves (CIDi) from the secure memory, where CIDi = REi ⊕ h(Sh), (i.e., retrieve the identity of the requested Pi). MSh then computes XBh = bh * P, Bh = bh * PKi, Fh = h (CIDi) ⊕ fh, SKh-i = h (Bh || CIDi || fh), and Lk2 = h (Bh || CIDi || IDh || SKh-i || T1). Afterward, MSh transmits the message (XBh, Fh, Lk2, T1) to CN through an unsecured channel.
- When (XBh, Fh, Lk2, T1) is received from MSh, Pi enters IDi and PWi to CN. Then CN calculates ai = APi ⊕ h(IDi || PWi), HIDi = h(IDi || ai), HPWi = h(IDi || PWi || ai), bi = HPWi ⊕ BPi, and SIDi = CPi ⊕ bi*P. After that, CN verifies if DPi ≟ h(ai || bi || HPWi || SIDi), Pi is logged into CN successfully.
- CN validates the timestamps. If |T1 − T1*| < ΔT, where T1* denotes the time of message receipt, then CN calculates CIDi = EPi ⊕ SIDi, Bh = XBh * Si, fh = Fh ⊕ h(CIDi), and SKh-i = h (Bh || CIDi || fh). Next, CN checks whether Lk2 ≟ h (Bh || CIDi || IDh || SKh-i || T1). If so, MSh is authenticated, and SKh-i is created between MSh and CN.
3.5. Password Change Protocol
- Pi enters IDi and PWi in CN.
- CN calculates ai = APi ⊕ h(IDi || PWi), HIDi = h(IDi || ai), HPWi = h(IDi || PWi || ai), bi = HPWi ⊕ BPi, and SIDi = CPi ⊕ bi * P. Then, CN verifies if DPi ≟ h(ai || bi || HPWi || SIDi), CN prompts Pi to choose a new password.
- Pi chooses a new password PWi+ and transmits it to CN.
- After getting PWi+, CN calculates HPWi+ = h (IDi || PWi+ || ai), APi+ = h (IDi || PWi+) ⊕ ai, BPi+ = HPWi+ ⊕ bi, CPi = SIDi ⊕ bi * P, and DPi+ = h (ai || bi || HPWi+ || SIDi). Finally, CN replaces (APi, BPi, CPi, DPi, EPi,Vi) with (APi+, BPi+, CPi, DPi+, EPi,Vi).
4. Security Analysis
4.1. Informal Security Analysis
4.1.1. Emergency and Periodic Authentication Protocols
4.1.2. Perfect Forward/Backward Secrecy
4.1.3. Patient Anonymity and Untraceability
4.1.4. Secure Password Change
4.1.5. Controller Node Revocation
4.1.6. Replay Attack
4.1.7. Session Key Disclosure Attack
4.1.8. Off-Line Guessing Attack
4.1.9. Impersonation Attack
4.1.10. Controller Node Stolen Attack
4.1.11. Known Session-Specific Temporary Information Attack
4.1.12. Desynchronization Attack
4.2. BAN Logic Proof
4.2.1. Inference Rules
4.2.2. P-I Goals
4.2.3. P-I Assumptions
4.2.4. P-I Idealized Forms
4.2.5. P-I Formal Analysis
- Step 1: D1 is obtained from Msg1.
- Step 2: confirms that the message sent is from . Applying MMR with D1 and A6 yields D2.
- Step 3: checks whether request is fresh. D3 is obtained by applying FR using A1 and D2.
- Step 4: verifies whether request is legitimate. D4 is obtained by applying NVR using D2 and D3.
- Step 5: now trusts and all its sent parameters. D5 is obtained by applying BR using D4.
- Step 6: D6 is obtained by using SKR with D3 and D5 to achieve G4.
- Step 7: has complete control over the sent parameters. D7 is obtained by using JR with A4 and D6 to achieve G3
- Step 8: D8 is obtained from Msg2
- Step 9: confirms that the message sent is from . Applying MMR with D8 and A5 yields D9.
- Step 10: checks whether request is fresh. Applying FR with D9 and A2 yields D10.
- Step 11: verifies whether request is legitimate. D11 is obtained by applying NVR using D9 and D10.
- Step 12: now trusts and all of the parameters it has sent. D12 is obtained by using BR with D11.
- Step 13: D13 is obtained by using SKR with D10 and D12 to achieve G2.
- Step 14: obtains the parameters of the new session key from the sent parameters. D14 is obtained by using JR with A3 and D13 to achieve G1.
4.2.6. P-II Goals
4.2.7. P-II Assumptions
4.2.8. P-II Idealized Forms
4.2.9. P-II Formal Analysis
- Step 1: D1 is obtained from Msg1.
- Step 2: trusts the transmitted parameter and that is genuine. D2 is obtained from D1, A5, fh = h () ⊕ Fh, Bh = bh * PKi, and the session key SKh-i = h ( || CIDi || fh) to accomplish G4.
- Step 3: D3 is obtained by using JR with A3 and D2 to achieve G3.
- Step 4: D4 is obtained from Msg2
- Step 5: confirms that the message sent is from . D5 is obtained by applying MMR using D4 and A4.
- Step 6: checks whether request is fresh. D6 is obtained by using FR with A1 and D5.
- Step 7: verifies whether request is legitimate. D7 is obtained by applying NVR using D5 and D6.
- Step 8: now trusts and all of the parameters it has sent. D8 is obtained by using BR with D7.
- Step 9: D9 is obtained from D8, A6, fh = h () ⊕ Fh, Bh = XBh * Si, and the session key SKh-i = h ( || CIDi || fh) to accomplish G2.
- Step 10: obtains the parameters of the new session key from the sent parameters. D10 is obtained by using JR with A2 and D9 to achieve G1.
4.3. AVISPA Simulation Tool
5. Performance Analysis
5.1. Computation Costs
5.2. Communication Costs
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Poongodi, T.; Rathee, A.; Indrakumari, R.; Suresh, P. IoT Sensing Capabilities: Sensor Deployment and Node Discovery, Wearable Sensors, Wireless Body Area Network (WBAN), Data Acquisition. Intell. Syst. Ref. Libr. 2020, 174, 127–151. [Google Scholar] [CrossRef]
- Hussain, M.; Mehmood, A.; Khan, S.; Khan, M.A.; Iqbal, Z. Authentication Techniques and Methodologies used in Wireless Body Area Networks. J. Syst. Archit. 2019, 101, 101655. [Google Scholar] [CrossRef]
- Alzahrani, B.A.; Irshad, A. A Secure and Efficient TMIS-Based Authentication Scheme Improved Against Zhang et al.’s Scheme. Arab. J. Sci. Eng. 2018, 43, 8239–8253. [Google Scholar] [CrossRef]
- Hsu, C.L.; Le, T.V.; Hsieh, M.C.; Tsai, K.Y.; Lu, C.F.; Lin, T.W. Three-factor UCSSO scheme with fast authentication and privacy protection for telecare medicine information systems. IEEE Access 2020, 8, 196553–196566. [Google Scholar] [CrossRef]
- Liu, X.; Ma, W.; Cao, H. MBPA: A medibchain-based privacy-preserving mutual authentication in TMIS for mobile medical cloud architecture. IEEE Access 2019, 7, 149282–149298. [Google Scholar] [CrossRef]
- Narwal, B.; Mohapatra, A.K. A survey on security and authentication in wireless body area networks. J. Syst. Archit. 2021, 113, 101883. [Google Scholar] [CrossRef]
- Lara, E.; Aguilar, L.; Garcia, J.A. Lightweight Authentication Protocol Using Self-Certified Public Keys for Wireless Body Area Networks in Health-Care Applications. IEEE Access 2021, 9, 79196–79213. [Google Scholar] [CrossRef]
- Taleb, H.; Nasser, A.; Andrieux, G.; Charara, N.; Motta Cruz, E. Wireless technologies, medical applications and future challenges in WBAN: A survey. Wirel. Netw. 2021, 27, 5271–5295. [Google Scholar] [CrossRef]
- Gupta, A.; Tripathi, M.; Sharma, A. A provably secure and efficient anonymous mutual authentication and key agreement protocol for wearable devices in WBAN. Comput. Commun. 2020, 160, 311–325. [Google Scholar] [CrossRef]
- Wu, T.Y.; Yang, L.; Luo, J.N.; Wu, J.M.-T. A Provably Secure Authentication and Key Agreement Protocol in Cloud-Based Smart Healthcare Environments. Secur. Commun. Netw. 2021, 2021, 2299632. [Google Scholar] [CrossRef]
- Deebak, B.D.; Al-Turjman, F. Smart Mutual Authentication Protocol for Cloud Based Medical Healthcare Systems Using Internet of Medical Things. IEEE J. Sel. Areas Commun. 2021, 39, 346–360. [Google Scholar] [CrossRef]
- Ogundoyin, S.O.; Kamil, I.A. PAASH: A privacy-preserving authentication and fine-grained access control of outsourced data for secure smart health in smart cities. J. Parallel Distrib. Comput. 2021, 155, 101–119. [Google Scholar] [CrossRef]
- Ren, Y.; Leng, Y.; Zhu, F.; Wang, J.; Kim, H.J. Data storage mechanism based on blockchain with privacy protection in wireless body area network. Sensors 2019, 19, 2395. [Google Scholar] [CrossRef] [Green Version]
- Wazid, M.; Das, A.K.; Vasilakos, A.V. Authenticated key management protocol for cloud-assisted body area sensor networks. J. Netw. Comput. Appl. 2018, 123, 112–126. [Google Scholar] [CrossRef]
- Almuhaideb, A.M.; Alghamdi, H.A. Secure and Efficient WBAN Authentication Protocols for Intra-BAN Tier. J. Sens. Actuator Netw. 2022, 11, 44. [Google Scholar] [CrossRef]
- Ahmad, W.; Rasool, A.; Javed, A.R.; Baker, T.; Jalil, Z. Cyber security in IoT-based cloud computing: A comprehensive survey. Electronics 2022, 11, 16. [Google Scholar] [CrossRef]
- Chengoden, R.; Victor, N.; Huynh-the, T.; Yenduri, G.; Hjhaveri, R.; Member, S.; Alazab, M.; Bhattacharya, S.; Hegde, P.; Kumar Reddy Maddikunta, P.; et al. Metaverse for Healthcare: A Survey on Potential Applications, Challenges and Future Directions. Available online: https://arxiv.org/ftp/arxiv/papers/2209/2209.04160.pdf (accessed on 7 September 2022).
- Umar, M.; Wu, Z.; Liao, X. Authenticating tier-two body area network devices through user-specific signal propagation characteristics. Comput. Secur. 2022, 120, 102800. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A Secure Three-Factor User Authentication Protocol with Forward Secrecy for Wireless Medical Sensor Network Systems. IEEE Syst. J. 2020, 14, 39–50. [Google Scholar] [CrossRef]
- Ullah, I.; Zeadally, S.; Amin, N.U.; Asghar Khan, M.; Khattak, H. Lightweight and provable secure cross-domain access control scheme for internet of things (IoT) based wireless body area networks (WBAN). Microprocess. Microsyst. 2021, 81, 103477. [Google Scholar] [CrossRef]
- Almuhaideb, A.M.; Alqudaihi, K.S. A Lightweight and Secure Anonymity Preserving Protocol for WBAN. IEEE Access 2020, 8, 178183–178194. [Google Scholar] [CrossRef]
- Xu, Z.; Xu, C.; Chen, H.; Yang, F. A lightweight anonymous mutual authentication and key agreement scheme for WBAN. Concurr. Comput. Pract. Exp. 2019, 31, e5295. [Google Scholar] [CrossRef]
- Kasyoka, P.; Kimwele, M.; Mbandu Angolo, S. Certificateless pairing-free authentication scheme for wireless body area network in healthcare management system. J. Med. Eng. Technol. 2020, 44, 12–19. [Google Scholar] [CrossRef]
- Dhillon, P.K.; Kalra, S. Multi-factor user authentication scheme for IoT-based healthcare services. J. Reliab. Intell. Environ. 2018, 4, 141–160. [Google Scholar] [CrossRef]
- Sowjanya, K.; Dasgupta, M.; Ray, S. An elliptic curve cryptography based enhanced anonymous authentication protocol for wearable health monitoring systems. Int. J. Inf. Secur. 2020, 19, 129–146. [Google Scholar] [CrossRef]
- Song, Y.; Tan, H. Practical pairing-Free sensor cooperation scheme for cloud-Assisted wireless body area networks. Cybersecurity 2020, 3, 21. [Google Scholar] [CrossRef]
- Zhang, J.; Zhang, Q.; Li, Z.; Lu, X.; Gan, Y. A Lightweight and Secure Anonymous User Authentication Protocol for Wireless Body Area Networks. Secur. Commun. Netw. 2021, 2021, 4939589. [Google Scholar] [CrossRef]
- Yu, S.J.; Lee, J.Y.; Park, Y.H.; Park, Y.H.; Lee, S.W.; Chung, B.H. A secure and efficient three-factor authentication protocol in global mobility networks. Appl. Sci. 2020, 10, 3565. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Kim, M.; Yu, S.; Das, A.K.; Park, Y. Design of secure authentication protocol for cloud-assisted telecare medical information system using blockchain. IEEE Access 2020, 8, 192177–192191. [Google Scholar] [CrossRef]
- Yang, X.; Yi, X.; Nepal, S.; Khalil, I.; Huang, X.; Shen, J. Efficient and Anonymous Authentication for Healthcare Service with Cloud based WBANs. IEEE Trans. Serv. Comput. 2021, 15, 2728–2741. [Google Scholar] [CrossRef]
- Ali, Z.; Ghani, A.; Khan, I.; Ashraf, S.; Hafizul, S.K. A robust authentication and access control protocol for securing wireless healthcare sensor networks. J. Inf. Secur. Appl. 2020, 52, 102502. [Google Scholar] [CrossRef]
- Son, S.; Kwon, D.; Lee, J.; Yu, S.; Jho, N.S.; Park, Y. On the Design of a Privacy-Preserving Communication Scheme for Cloud-Based Digital Twin Environments Using Blockchain. IEEE Access 2022, 10, 75365–75375. [Google Scholar] [CrossRef]
- Kumar, M.; Chand, S. A Lightweight Cloud-Assisted Identity-Based Anonymous Authentication and Key Agreement Protocol for Secure Wireless Body Area Network. IEEE Syst. J. 2020, 15, 2779–2786. [Google Scholar] [CrossRef]
- Saeed, M.E.S.; Liu, Q.Y.; Tian, G.Y.; Gao, B.; Li, F. AKAIoTs: Authenticated key agreement for Internet of Things. Wirel. Netw. 2019, 25, 3081–3101. [Google Scholar] [CrossRef]
- Konan, M.; Wang, W. A secure mutual batch authentication scheme for patient data privacy preserving in WBAN. Sensors 2019, 19, 1608. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Almuhaideb, A.M.; Alqudaihi, K. A lightweight three-factor authentication scheme for WHSN architecture. Sensors 2020, 20, 6860. [Google Scholar] [CrossRef] [PubMed]
- Yu, S.J.; Park, Y.H. Slua-wsn: Secure and lightweight three-factor-based user authentication protocol for wireless sensor networks. Sensors 2020, 20, 4143. [Google Scholar] [CrossRef] [PubMed]
- Zhou, L.; Li, X.; Yeh, K.H.; Su, C.; Chiu, W. Lightweight IoT-based authentication scheme in cloud computing circumstance. Futur. Gener. Comput. Syst. 2019, 91, 244–251. [Google Scholar] [CrossRef]
- Amin, R.; Kumar, N.; Biswas, G.P.; Iqbal, R.; Chang, V. A light weight authentication protocol for IoT-enabled devices in distributed Cloud Computing environment. Futur. Gener. Comput. Syst. 2018, 78, 1005–1019. [Google Scholar] [CrossRef]
- Li, X.; Ibrahim, M.H.; Kumari, S.; Kumar, R. Secure and efficient anonymous authentication scheme for three-tier mobile healthcare systems with wearable sensors. Telecommun. Syst. 2018, 67, 323–348. [Google Scholar] [CrossRef]
- Almuhaideb, A.M. Re—AuTh : Lightweight Re—Authentication with Practical Key Management for Wireless Body Area Networks. Arab. J. Sci. Eng. 2021, 46, 8189–8202. [Google Scholar] [CrossRef]
- Wong, A.M.K.; Hsu, C.L.; Le, T.V.; Hsieh, M.C.; Lin, T.W. Three-factor fast authentication scheme with time bound and user anonymity for multi-server e-health systems in 5g-based wireless sensor networks. Sensors 2020, 20, 2511. [Google Scholar] [CrossRef] [PubMed]
- Chen, R.; Peng, D. Analysis and Improvement of a Mutual Authentication Scheme for Wireless Body Area Networks. J. Med. Syst. 2019, 43, 19. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Li, L.; Shen, J. Efficient and Anonymous Authentication Scheme for Wireless Body Area Networks. J. Med. Syst. 2016, 40, 134. [Google Scholar] [CrossRef] [PubMed]
- Rajaram, S.; Maitra, T.; Vollala, S.; Ramasubramanian, N.; Amin, R. eUASBP: Enhanced user authentication scheme based on bilinear pairing. J. Ambient Intell. Humaniz. Comput. 2020, 11, 2827–2840. [Google Scholar] [CrossRef]
- Agrahari, A.K.; Varma, S.; Venkatesan, S. Two factor authentication protocol for IoT based healthcare monitoring system. J. Ambient Intell. Humaniz. Comput. 2022, 1–18. [Google Scholar] [CrossRef] [PubMed]
- Son, S.; Park, Y.; Park, Y. A secure, lightweight, and anonymous user authentication protocol for IoT environments. Sustainability 2021, 13, 9241. [Google Scholar] [CrossRef]
- Khatoon, S.; Rahman, S.M.M.; Alrubaian, M.; Alamri, A. Privacy-Preserved, Provable Secure, Mutually Authenticated Key Agreement Protocol for Healthcare in a Smart City Environment. IEEE Access 2019, 7, 47962–47971. [Google Scholar] [CrossRef]
- Odelu, V.; Saha, S.; Prasath, R.; Sadineni, L.; Conti, M.; Jo, M. Efficient privacy preserving device authentication in WBANs for industrial e-health applications. Comput. Secur. 2019, 83, 300–312. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Karuppiah, M.; Nayyar, A. An efficient anonymous authentication and confidentiality preservation schemes for secure communications in wireless body area networks. Wirel. Netw. 2021, 27, 2119–2130. [Google Scholar] [CrossRef]
- Ryu, J.; Oh, J.; Kwon, D.; Son, S.; Lee, J.; Park, Y.; Park, Y. Secure ECC-Based Three-Factor Mutual Authentication Protocol for Telecare Medical Information System. IEEE Access 2022, 10, 11511–11526. [Google Scholar] [CrossRef]
- Sahoo, S.S.; Mohanty, S.; Majhi, B. A secure three factor based authentication scheme for health care systems using IoT enabled devices. J. Ambient Intell. Humaniz. Comput. 2020, 12, 1419–1434. [Google Scholar] [CrossRef]
- Chen, Y.; Chen, J. An efficient and privacy-preserving mutual authentication with key agreement scheme for telecare medicine information system. Peer-to-Peer Netw. Appl. 2022, 15, 516–528. [Google Scholar] [CrossRef]
- Karthigaiveni, M.; Indrani, B. An efficient two-factor authentication scheme with key agreement for IoT based E-health care application using smart card. J. Ambient Intell. Humaniz. Comput. 2019, 4, 1–12. [Google Scholar] [CrossRef]
- Alzahrani, B.A. Secure and Efficient Cloud-based IoT Authenticated Key Agreement scheme for e-Health Wireless Sensor Networks. Arab. J. Sci. Eng. 2021, 46, 3017–3032. [Google Scholar] [CrossRef]
- Mohammedi, M.; Omar, M.; Bouabdallah, A. Secure and lightweight remote patient authentication scheme with biometric inputs for mobile healthcare environments. J. Ambient Intell. Humaniz. Comput. 2018, 9, 1527–1539. [Google Scholar] [CrossRef]
- Kumari, S.; Renuka, K. Design of a Password Authentication and Key Agreement Scheme to Access e-Healthcare Services. Wirel. Pers. Commun. 2021, 117, 27–45. [Google Scholar] [CrossRef]
- Qiu, S.; Xu, G.; Ahmad, H.; Wang, L. A Robust Mutual Authentication Scheme Based on Elliptic Curve Cryptography for Telecare Medical Information Systems. IEEE Access 2017, 6, 7452–7463. [Google Scholar] [CrossRef]
- Hussain, S.J.; Irfan, M.; Jhanjhi, N.Z.; Hussain, K.; Humayun, M. Performance Enhancement in Wireless Body Area Networks with Secure Communication. Wirel. Pers. Commun. 2021, 116, 1–22. [Google Scholar] [CrossRef]
- Alzahrani, B.A.; Irshad, A.; Albeshri, A.; Alsubhi, K.; Shafiq, M. An improved lightweight authentication protocol for wireless body area networks. IEEE Access 2020, 8, 190855–190872. [Google Scholar] [CrossRef]
- Alzahrani, B.A.; Irshad, A.; Albeshri, A.; Alsubhi, K. A Provably Secure and Lightweight Patient-Healthcare Authentication Protocol in Wireless Body Area Networks. Wirel. Pers. Commun. 2021, 117, 47–69. [Google Scholar] [CrossRef]
- Khadem, B.; Suteh, A.M.; Ahmad, M.; Alkhayyat, A.; Farash, M.S.; Khalifa, H.S. An Improved WBSN Key-Agreement Protocol Based on Static Parameters and Hash Functions. IEEE Access 2021, 9, 78463–78473. [Google Scholar] [CrossRef]
- Chunka, C.; Banerjee, S. An Efficient Mutual Authentication and Symmetric Key Agreement Scheme for Wireless Body Area Network. Arab. J. Sci. Eng. 2021, 46, 8457–8473. [Google Scholar] [CrossRef]
- Narwal, B.; Mohapatra, A.K. SEEMAKA: Secured Energy-Efficient Mutual Authentication and Key Agreement Scheme for Wireless Body Area Networks. Wirel. Pers. Commun. 2020, 113, 1985–2008. [Google Scholar] [CrossRef]
- Narwal, B.; Mohapatra, A.K. SAMAKA: Secure and Anonymous Mutual Authentication and Key Agreement Scheme for Wireless Body Area Networks. Arab. J. Sci. Eng. 2021, 46, 9197–9219. [Google Scholar] [CrossRef]
- Park, K.; Noh, S.; Lee, H.; Das, A.K.; Kim, M.; Park, Y.; Wazid, M. LAKS-NVT: Provably Secure and Lightweight Authentication and Key Agreement Scheme without Verification Table in Medical Internet of Things. IEEE Access 2020, 8, 119387–119404. [Google Scholar] [CrossRef]
- Yu, S.; Park, K. SALS-TMIS: Secure, Anonymous, and Lightweight Privacy-Preserving Scheme for IoMT-Enabled TMIS Environments. IEEE Access 2022, 10, 60534–60549. [Google Scholar] [CrossRef]
- Le, T.V.; Lu, C.F.; Hsu, C.L.; Do, T.K.; Chou, Y.F.; Wei, W.C. A Novel Three-Factor Authentication Protocol for Multiple Service Providers in 6G-Aided Intelligent Healthcare Systems. IEEE Access 2022, 10, 28975–28990. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Nikooghadam, M.; Abbasinezhad-Mood, D. Design of a lightweight and anonymous authenticated key agreement protocol for wireless body area networks. Int. J. Commun. Syst. 2019, 32, e3974. [Google Scholar] [CrossRef]
- Shuai, M.; Xiong, L.; Wang, C.; Yu, N. Lightweight and privacy-preserving authentication scheme with the resilience of desynchronisation attacks for WBANs. IET Inf. Secur. 2020, 14, 380–390. [Google Scholar] [CrossRef]
- Xu, Z.; Xu, C.; Liang, W.; Xu, J.; Chen, H. A lightweight mutual authentication and key agreement scheme for medical Internet of Things. IEEE Access 2019, 7, 53922–53931. [Google Scholar] [CrossRef]
- Almuhaideb, A.M.; Alqudaihi, K.S. Authentication in Wireless Body Area Network: Taxonomy and Open Challenges. J. Internet Things 2021, 3, 159–182. [Google Scholar] [CrossRef]
- Koya, A.M.; Deepthi, P.P. Anonymous hybrid mutual authentication and key agreement scheme for wireless body area network. Comput. Netw. 2018, 140, 138–151. [Google Scholar] [CrossRef]
- Kilinc, H.H.; Yanik, T. A survey of SIP authentication and key agreement schemes. IEEE Commun. Surv. Tutor. 2014, 16, 1005–1023. [Google Scholar] [CrossRef]











| Symbol | Description |
|---|---|
| Pi | Patient-i |
| CN | Controller node of Pi |
| MSh | Cloud-based medical server-h |
| TA | Trusted authority |
| IDi, PWi | Pi’s identity and password |
| HIDi | Pi’s masked identity |
| SIDi | Pi’s secret identity |
| IDh | MSh’s identity |
| Si, PKi | CN’s secret and public keys |
| Sh, PKh | MSh’s secret and public keys |
| STA, PKTA | TA’s secret and public keys of |
| ai, bi, ri | CN-created random numbers |
| rh, ui+, fh, bh | MSh-created random numbers |
| ui | TA-created a random number |
| HPWi, APi, BPi, CPi, DPi | Data used by CN to authenticate Pi |
| Vi, Wi, Vi+, Wi+ | Data to verify message synchronization |
| Tn | Timestamp n |
| ΔT | The maximum transmission delay |
| Tn* | The time of message receipt |
| XRi | Public data generated by CN and used by MSh to compute Xi |
| Xi | Elliptic Curve Diffie-Hellman Problem |
| Ji | Data utilized to retrieve Vi in P-I |
| PIDh-i | Data stored on MSh to check CN’s registration |
| Rh | Public data generated by MSh and used by CN to compute Vh |
| Vh | Elliptic Curve Diffie-Hellman Problem |
| C1 | Data utilized to retrieve Vi+ in P-I |
| Li1 | Data that MSh uses in P-I to authenticate CN |
| Li2 | Data that CN uses in P-I to authenticate MSh |
| REi | Data that MSh uses in P-II to retrieve CIDi |
| CIDi | Data generated by TA and used by MSh to authenticate CN |
| XBh | Public data generated by MSh and used by CN to compute Bh |
| Bh | Elliptic Curve Diffie-Hellman Problem |
| Fh | Data utilized to retrieve fh in P-II |
| EPi | Data stored on CN and used to retrieve CIDi in P-II |
| Lk2 | Data that CN uses in P-II to authenticate MSh |
| SKi-h | Session key between CN and MSh in P-I |
| SKh-i | Session key between MSh and CN in P-II |
| P | A base point on an elliptic curve |
| q | Large prime number |
| * | Scalar multiplication operation |
| Zq* | The nonzero positive integers modulus q |
| ⊕ | XOR operation |
| h | Hash function |
| || | Concatenation operation |
| → | Public channel |
| ⇢ | Secure channel |
| Scheme | S01 | S02 | S03 | S04 | S05 | S06 | S07 | S08 | S09 | S10 | S11 | S12 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [29] | ✘ | ✓ | ✓ | ~ | ✘ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✘ |
| [33] | ✘ | ✓ | ✓ | ✘ | ✓ | ✓ | ✓ | ~ | ✓ | ✘ | ~ | ✘ |
| [40] | ✘ | ✓ | ~ | ✘ | ✘ | ✓ | ✓ | ~ | ✓ | ✘ | ~ | ✘ |
| [43] | ✘ | ✓ | ✓ | ✘ | ✘ | ✓ | ✓ | ~ | ✓ | ✘ | ~ | ✘ |
| [45] | ✘ | ~ | ✘ | ✓ | ✘ | ✓ | ✓ | ✘ | ✘ | ✓ | ✘ | ✘ |
| [48] | ✘ | ✘ | ✓ | ✓ | ✘ | ✓ | ✓ | ✓ | ✓ | ✓ | ✘ | ✘ |
| [51] | ✘ | ✓ | ✓ | ✓ | ✘ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✘ |
| Proposed | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Notation | Description |
|---|---|
| P, Q | Two principals |
| X1, X2 | Two statements |
| SK | The session key |
| P|≡ X1 | P believes X1, if X1 is true |
| P ⊲ X1 | P sees X1, i.e., P receives X1 contained within a message, but P does not necessarily believe X1 |
| P| ∼X1 | P once says X1, i.e., P transmits a message including X1. It is unknown if P sent the message recently or a long time ago, but P believes X1 when P sends it |
| P| ⇒ X1 | P controls X1, and P should trust X1 |
| #(X1) | X1 is fresh, i.e., X1 has never been sent before |
| (X1) K | X1 is combined with K |
| Q | P and Q have the same key K |
| If P is true, then Q is also true |
| Scheme | Computation Cost | ||
|---|---|---|---|
| CN | MSh | Total (ms) | |
| [48] | 1Tbp + 2Thp + 3Tmul + 1Trng + 1Ted + 4Th | 1Tbp + 2Thp + 4Tmul + 1Trng + 1Ted + 2Th | 77.977 |
| [33] | 1Thp + 6Tmul + 1Trng + 2Tadd + 4Th | 1Thp + 6Tmul + 1Trng + 2Tadd + 4Th | 52.7596 |
| [29] | 8 Tmul + 1Trng + 8Th | 2Tbp + 5 Tmul + 1Trng + 5Th | 41.6679 |
| [43] | 1Texp + 5Tmul + 1Trng + 1Ted + 1Tadd + 4Th | 1Tbp + 4Tmul + 1Trng + 1Ted + 2Tadd + 4Th | 30.887 |
| [45] | 5Tmul + 1Trng + 1Tadd + 7Th | 1Tbp + 1Texp + 3Tmul + 1Trng + 1Tadd + 6Th | 28.6345 |
| [51] | 3Tmul + 1Trng + 11Th | 3Tmul + 1Trng + 7Th | 14.4754 |
| [40] | 2Tmul + 2Trng + 3Ted | 1Tmul + 1Trng + 3Ted | 8.3226 |
| P-I | 4Tmul + 1Trng + 7Th | 3Tmul + 2Trng + 6Th | 17.2289 |
| P-II | 2Tmul + 7Th | 2Tmul + 2Trng + 4Th | 10.0073 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almuhaideb, A.M.; Alghamdi, H.A. Design of Inter-BAN Authentication Protocols for WBAN in a Cloud-Assisted Environment. Big Data Cogn. Comput. 2022, 6, 124. https://doi.org/10.3390/bdcc6040124
Almuhaideb AM, Alghamdi HA. Design of Inter-BAN Authentication Protocols for WBAN in a Cloud-Assisted Environment. Big Data and Cognitive Computing. 2022; 6(4):124. https://doi.org/10.3390/bdcc6040124
Chicago/Turabian StyleAlmuhaideb, Abdullah M., and Huda A. Alghamdi. 2022. "Design of Inter-BAN Authentication Protocols for WBAN in a Cloud-Assisted Environment" Big Data and Cognitive Computing 6, no. 4: 124. https://doi.org/10.3390/bdcc6040124






