1. Introduction
Aerial drone technology may be utilized for a variety of reasons to improve our lives due to its rapid invention and modification as well as the shrinking of integrated sensors, CPU processing speed, and widespread connectivity of wireless systems. Moreover, UAVs are known as drones used in numerous applications ranging from civilian to military platforms [
1]. There has been a significant improvement in the number of drone applications, as the advancement in drone technology increases. Drone application in the field of the military is boundless, as they are a vital asset on the modern battlefield. Internet-connected drones provide accurate and efficient flying strategies to ensure the quality of service. Using the drone’s sensors, the assigning field’s physical parameters are collected [
2]. In addition, the drone’s cameras and microphones transmit real-time video to the service provider or user via a wireless medium. By controlling a drone, a service provider/user can obtain real-time information from a remote location [
3]. A drone’s data collection poses new security and privacy risks as technology advances.
Manpower is saved when the drones are used to deliver packages via airways. Moreover, for short-distance delivery of goods, drones are very obliging. Drones can be used to record video, which was previously impossible due to the need for expensive aircraft and scaffolding to capture the images. The current pandemic situation can be addressed with the help of drones as they are used to transport medicine and necessary items to the contaminated zones. The Internet of Drones (IoD) environment helps to monitor crops and provide the required water facilities frequently, thus helping in smart farming. During the occurrence of any natural calamities, drones will be helpful for collecting the required disaster information. Further, drones are used to monitor a large group of people during public meetings/gatherings as a surveillance and to record the data to guarantee public safety. Drones are not only useful for searching operations but also help to rescue a person in danger from war fields and provide them with food, clothing, and medicine. Moreover, the vital role of safeguarding each country’s border surveillance can be also performed by drones.
In addition to the above-mentioned applications, a drone’s location and other sensitive data are also to be collected and preserved [
4]. An adversary can easily intercept the information sent by a drone due to IoD’s public, insecure network connection. Wireless networks are more vulnerable to cyber-attacks than wired networks due to their open nature. To reduce this risk in MANET, predominantly in the IoD environment, various approaches based on single or combined security mechanisms have been proposed. Currently, drones face several issues related to security, privacy, and authentication, which makes them an appealing research topic [
5]. IoD is susceptible to several kinds of security attacks. Before exchanging confidential data via an unreliable channel, security precautions should be taken [
6]. In this paper, drones are used for providing information related to obstruction on pathways in hilly and other highly populated areas. Roadside infrastructure is desperately required for the sake of safety to help quickly transmit and livestream necessary details about the path ahead in real time. Some of the services that drones can provide include monitoring of low-altitude, disaster relief, and data transmission assistance. It is believed that drones have the greatest potential for providing connectivity and solutions because of their ease of access. A blended wireless protocol is used in mountain ranges and rural places where there are weak signals or interferences. Moreover, if any fault occurs in the current existing drone, it should be replaced with another drone exactly at the same position. Hence, the current location of the drone should be preserved from adversaries.
Authentication and privacy are two of the prevalent security issues with IoD communications [
7,
8,
9]. Drones are attractive targets for adversaries because they are used for sensitive applications. Along with drone data, adversaries may also try to track down geographic location to obtain confidential data. The main challenge is the security between the users and drones during the exchange of information. Due to the open nature of the communication medium, an adversary can read, alter, or respond to the message communicated and send fake information. Moreover, another important vital challenge is to preserve the privacy of the user/drone from an adversary [
10]. If the real identity of the drone is revealed, then there may be a possibility for an adversary to perform an impersonation attack and steal the original confidential information of the drone. Though most of the currently existing schemes provide authentication, these are vulnerable to several possible attacks.
Drones are mainly used for aerial surveillance and monitoring operations. During natural disasters and emergency periods, drones play a significant role. The integrity of the collected sensitive data should be preserved without any modification. In addition, privacy of the drone and end user should be preserved. Thus, the main significance of the proposed scheme is that the drone and the end user should be authenticated anonymously without revealing its privacy. Therefore, a simple cryptographic pairing and hashing operations are used for privacy preservation in our work during both mutual and batch authentication. Thus, the computational cost, communication cost, and storage cost are reduced significantly when compared to the prevailing existing works. Moreover, to avoid tracing of the authenticated drones, a location privacy scheme is proposed in this work. The proposed scheme is applicable in the following ways: privacy and anonymity are preserved and the computational cost for verifying a group of drones is significantly reduced. Finally, an intruder will be unable to track the authenticated drones’ location.
The research impact of this manuscript are as follows:
To develop a privacy-preserving anonymous mutual authentication scheme between a drone and a user.
To authenticate a group of drones anonymously based on batch authentication protocol to reduce the total computational overhead.
To ensure the privacy of the confidential information from the authenticated drone to the authenticated user.
To guarantee location privacy for the authenticated drones from an adversary.
The systematic flow of a research article is as follows.
Section 2 deals with the related prevailing works which deal with security and privacy. The overview of the entire system is described in
Section 3. This section describes the basic system model, bilinear pairing, and security measures of the proposed work.
Section 4 explains the proposed scheme. This section explains the initialization of the system, registration of the end-user and drone, key exchange protocol, mutual and batch authentication, integrity preservation, and location privacy. Some conceivable security attacks are described in
Section 5. Performance analysis is explained in
Section 6. This section deals with the analysis of computational cost, communication cost, storage cost, and drone service providing capability. Finally,
Section 7 concludes the work.
2. Related Work
Security and privacy are the major concern in the IoD environment [
11,
12,
13,
14]. There are many works focused on security issues concerning drones [
15], but this work not only discusses the security issues but also focuses on the location privacy of the drones. Turkanovic et al. [
16] suggested a mutual authentication framework between the drones and the end-user without the involvement of any third-party node. However, the scheme suffers from several security threats such as the man in the middle attack and the impersonation attack. Amin et al. [
17] suggested a strong authentication protocol based on the smart card. However, this scheme suffers from password guessing attacks and damage to smart cards, etc. Challa et al. [
18] suggested a signature-based authentication scheme using elliptic curve cryptography (ECC). Though ECC is used in this scheme, this work suffers from increased computational and storage costs for storing the required keys. A certificateless scheme was suggested by Won et al. [
19] for the security of drones. In this scheme, three scenarios for communication are taken into consideration. They are one-to-one, many-to-one, and one-to-many communication between drones and smart devices. Moreover, the conditional tracking mechanism is also adopted in this scheme. However, the scheme lacks location privacy and has increased communication cost during batch authentication.
Tai et al. [
20] suggested a two-factor authentication scheme. This work is mainly based on user passwords and smart card systems. It generally uses a hash function based on cryptography. However, this work fails to provide resistance against several well-known attacks such as replay attack, privileged-insider attack, etc. Wazid et al. [
21] recommended a three-factor authentication scheme. This scheme is based on three parameters such as biometrics, smart card, and password. Though a one-way hash function is used, it lacks conditional tracking and revocability. Yue et al. [
22] suggested a technique based on AI for drone surveillance. This work focused on wireless networking protocol. Different features of the drone and the exact location of the drone are traced using this scheme. However, this work does not focus on security issues and latency. Bouman et al. [
23] proposed a traveling salesman problem based on a drone. A solution was achieved based on dynamic programming for this problem. The communication cost of this work is significantly lower but it has high computational complexity. Hong et al. [
24] suggested a new model of recharging station for the spatial drone. A heuristic algorithm was used in this work which for maximum coverage and to avoid range restriction. There was no analysis regarding the storage cost and security threats. Shavarani et al. [
25] proposed an effective method for the delivery of the essential components with less time. A mathematical model based on a biobjective was designed in this work. The drawback of this work is the non-deterministic polynomial time-hard problem and computational complexity. Aggarwal et al. [
26] suggested an authentication scheme based on blockchain topology. The framework focuses on etherem based protocol. Though this work ensures privacy and security, the computational complexity of this work is very high. Huang et al. [
27] proposed a new method of implementing the charging stations for the drones. A triangular-based approach was used in this work. Moreover, the charging stations with less or no customers were recursively removed. This work does not focus on the communication and storage cost. Shavarani et al.’s [
28] work deals with reducing the transportation cost during the delivery time of the goods by drones. A fuzzy logic-based approach was used in this work. Security and privacy concerns were not discussed in this work. Automated swapping of the battery method was suggested by Cokyasar et al. [
29]. This work focused on the selection of optimal automated battery swapping machine location and minimized the delivery cost. Although communication cost was reduced in this work, it increased the computational cost. This work does not deal with major security threats. A secure authentication framework was presented from the human-centered industrial internet of things (IIoT) perspective by Singh et al. [
30]. When a node first joins the network, a registration hub generates the required credentials for the node. Moreover, nodes are involved in further complex operations such as mutual authentication, exchange of keys, etc., and the registration hub is no longer required to perform these functions. However, this scheme writhes from hefty computational cost, and there is no location privacy. Tian et al. [
31] proposed an authentication protocol that integrates both efficiency and security. This framework relies on a compact online/offline signature layout, and it can be deployed on resource-restricted small-scale unmanned aerial vehicles. Moreover, in this work, due to the high mobility of UAVs, the investigation of an extrapolative authentication approach using mobile edge computing (MEC) was performed to decrease authentication costs for possible authentication accomplishments. However, this work suffers from high computational and storage costs.
Gope et al. [
32] suggested a scheme that ensures the physical security of the drone. Physically unclonable function and hash operations are used in this scheme. Though the physical security of drones is ensured, it lacks location privacy. Zhang et al. [
33] suggested a compact authentication and key agreement (AKA) scheme that relies solely on a one-way secure hash function where drones and users authenticate one another mutually. Though this scheme is robust to different security threats, it lacks location privacy and physical threats. Ever et al. [
34] suggested a secure authentication framework based on ECC. Though several potential attacks were defended using this work, it lacks preservation of the location privacy and involves high communication cost. Hussain et al. [
35] proposed a three-factor authentication scheme. This work mainly compares the drawback of Wazid et al. [
21] but it involved high computational time.
Table 1 shows the summary of the different existing approaches.
3. System Overview
In this section, system model, bilinear pairing, and security measures are described in detail.
3.1. System Model
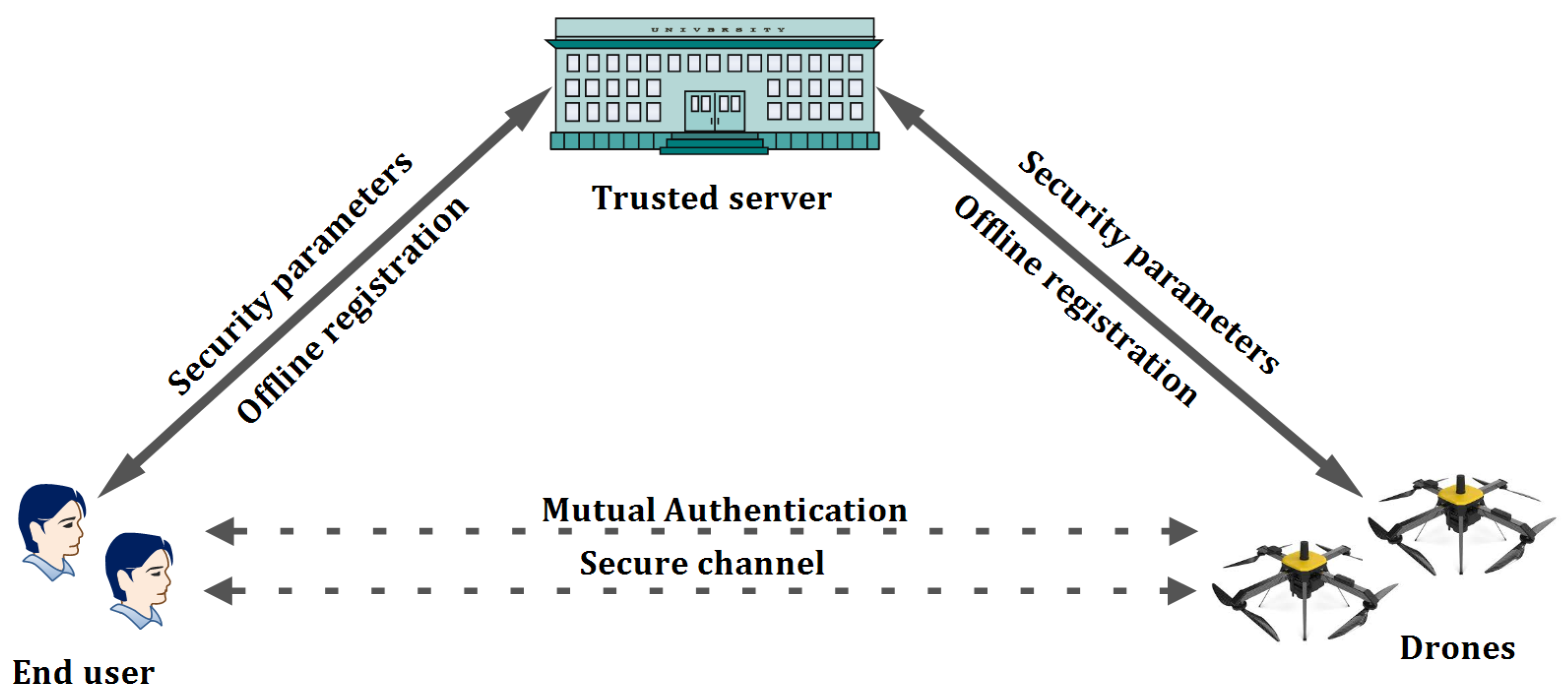
The proposed work’s system model comprises of three major entities, namely, trusted server, end user, and drone [
36].
Figure 1 portrays the system model of the proposed work. The role of each entity is described as follows.
Trusted server ()
is the key entity in our proposed work. Initialization, secret key generation, drone and end-user registrations are performed by . Moreover, unique keys are generated during the key generation process to avoid collision attacks. Initially, both the drone and the end-user should register to the through an offline registration. Only after the successful registration, provides the required credentials to the drone and end-user.
End-user (
is the participant in the FANET network. The required credentials for the to participate in the network are provided by . The is able to communicate with the control device of the drone through the specialized equipment with him. This highly sophisticated equipment of is capable of performing the computational operations efficiently. Moreover, the information collected from the controlling device of the drone is stored in the specialized equipment .
Drone ()
The is embedded with a control device which has high computational competence. Moreover, specialized sensors are implanted in the controlling device which helps to capture the image of long-distance. The control device of is capable of generating the short life session keys during key exchange protocol. In addition, the controlling device of is provided with a large storage capability to store the secret keys provided by during the initial registration.
3.2. Bilinear Pairing
Let , and be the cyclic multiplicative group of prime order . Moreover, let be the asymmetric bilinear map that gratifies the condition
Bi-linearity: = , and , where
Non-degeneracy: .
Computability: The bilinear map is computable.
No effective isomorphism between and .
3.3. Security Measures
Four security measures must be met by a proposed system to ensure secure communications in FANET.
Mutual authentication: To protect the FANET system from impersonation attacks, the and controlling device of should authenticate each other. Moreover, during the exchange of confidential information from to , mutual authentication between vehicle users and RSUs is indispensable.
Exchange of session key: The session key should be shared in an efficient anonymous way between the and to maintain confidentiality. Secure communication can be ensured only with the help of the short life session key.
Privacy preservation: The unique identity of and should be preserved during the exchange of data. Here, anonymous identity is used during mutual authentication which helps to protect the real identity of both and from the adversary.
Performance analysis: This mainly depends on communication and computational cost. The proposed work mainly focuses on a faster message verification time (shorter delay) for the with less communication and computational cost.
4. Proposed Scheme
In this article, a proficient anonymous mutual and batch authentication with location privacy is presented. System initialization,
registration,
registration, key exchange, mutual and batch authentication, integrity preservation, and location privacy are the stages in our proposed scheme.
Table 2 describes the list of notations and descriptions used in this work.
4.1. System Initialization
The selects the master key from a large prime number . The private key for the is chosen as such that, , where = [1,2,…,a−1]. Here, is the non-zero elements of a finite field and it forms the group under the modulo multiplication . The corresponding public key for is calculated as . Here, ,, and are the multiplicative cyclic groups and are the corresponding generators of the group and , respectively. The secure hash function chosen by is and the bilinear mapping is given by . Then, the publishes the parameters (,,, , ) as the required credentials after computing .
4.2. Registration
The provides his required credentials to during his initial offline registration. The genuine credentials provided by are verified by Once the offline registration is completed, the private key for the is chosen by as from the random number such that . Moreover, the public key and the fake identity for the are calculated as and , respectively. To perform batch authentication, the batch authentication key is calculated as . Moreover, to trace the exact location of the , the provides the secret key , such that to the .
4.3. Registration
The chooses the private key for the as such that . Based on the private key, the public key is calculated as . The fake identity for the is calculated as . During batch authentication process, to authenticate a large number of drones, the drone batch key and the drone tracking key are calculated as and , respectively.
4.4. Mutual Authentication
Anonymous mutual authentication must be conceded in an efficient way between the and the to perform effective communication. The following steps are to be followed.
Step 1: If an requires a specific service from the , then the calculates . Moreover, after calculating the value of , the parameters ,,) are sent to .
Step 2: The controlling device in the checks .,. If the condition is gratified, then the request is accepted, else the request from the is rejected.
Step 3: Similarly, the controlling device in the calculates the value of and sends the parameters ,,) to the .
Step 4: Then, the checks ., If the condition is gratified, the communication with is accepted, else it is rejected.
4.5. Session Key Exchange Protocol
In this phase, session key generation request, session key integrity preservation, and session key exchange are discussed. Once the mutual authentication scheme is successfully performed, the key exchange should be carried out between the and . The session key generation request is carried out as follows:
Step 1: Initially, the chooses a random number such that and calculates and respectively, where , and
Step 2: Finally, sends to the where is the timestamp.
Step 3: Initially, the controlling device of checks for the validity of the , if it holds then the controlling device of calculates . If , the session key generation request is accepted.
Step 4: Moreover, the integrity of session key is verified by checking . The value of is calculated by the controlling device of as .
Step 5: By using , the value of is calculated. Thus , then the integrity is preserved, else request is discarded.
Step 6: Once the session key generation request is accepted and session key integrity is preserved, the session key is generated by the controlling device of as and sends to .
Step 7: The first checks the validity of the timestamp . Once, the validity is validated, checks . If the condition is satisfied, then the session key exchange is performed between the and for effective communication of data.
4.6. Batch Authentication
The end user cannot rely on only one for gathering the required information. If the requires more data, then a greater number of drones should be authenticated at the same time to reduce the computational cost and to increase the performance. The steps involved in batch authentication are as follows
Step 1: Initially, the controlling device of picks a random number as its short life private key such that . The short life public key is calculated as . Moreover, if there are number of drones, their short life private keys are calculated as .
Step 2: To make an effective communication, the controlling device of calculates and where is the batch authentication key for .
Step 3: Moreover, the controlling device of computes the to preserve the integrity of the confidential information. Then, the quadruple is calculated as (, where is the drone tracking key, and it is sent to the .
Step 4: To validate the number of individual messages sent by each , the first checks the integrity of each message by calculating the hash value of and .
Step 5: If the integrity is verified, then the gathers as . Similarly, are accumulated as .
Step 6: Finally, checks . If this condition is satisfied, then the messages send by number of drones are batch authenticated.
4.7. Location Privacy
In case of any energy loss or fault in the current active
, it should be replaced by the
. However, the real location of the is anonymous. Therefore, in order to retrieve the actual real location, the
sends the real location of the
to the authenticated
anonymously. To perform the location privacy, the three coordinates of the
location are to be known. The three coordinates are generally represented as latitude, longitude, and altitude. Since the
is placed at a certain distance from the ground surface, the altitude is to be incorporated as the third coordinate.
Figure 2 shows the schematic location of drone in the three-coordinate system.
For instance, let us consider the geographic location as (15.92,80.18,400). Here, , and represent latitude (), longitude (), and altitude (), respectively. The executes the following steps as follows, calculates
Finally, the value of
is provided to the
. The value of secret key
is provided to the
by
during initial offline registration. The
calculates
as
. By decrypting
with the public key of the
, the three required coordinates can be retrieved by the
. This protocol is mainly based on Chinese remainder theorem (CRT) [
37].
5. Security Analysis
Analysis of some conceivable security attacks is described in this section.
5.1. Impersonation Attack
When an adversary efficaciously imitates a legitimate
or
in the FANET, it is called an impersonation attack. In our suggested scheme, security parameters such as private key (
, fake identity (
, end-user batch key (
, and the secret key for finding the exact location
are provided by the
during offline registration. To regenerate the exact replica of the keys, an adversary should have knowledge regarding the master key and private key of
. However, the confidentiality of these keys is high, and it is hard for an attacker to compute these keys. Moreover, to compute the value of the public key
, the value of the private key of the
(
should be known. However, it is a randomly chosen number, and the computation involves a discrete logarithm problem (DLP) [
38].
5.2. Bogus Message Attack
The adversary should be capable of sending a bogus message in place of the real message to the . To perform this task, the adversary should compromise the controlling device of the . However, this is practically not possible since the drone is registered with and any misbehavior of the leads to its revocation from the network by . Thus, our suggested work shows resistance against fake message attack.
5.3. Message Modification Attack
The collected confidential information/data from the to are3 transferred in a secured way. Here, short time session keys are generated for transferring the information to the . It is very difficult for an adversary to generate the equivalent short life session key and to perform the message modification attack. Moreover, the integrity of the session key is also ensured in our suggested work. As a result, our scheme is resistant to message alteration attack.
5.4. Reply Attack
When an adversary is capable of capturing the transferred information, modifying it and sending to the in the same stipulated time, it is called a reply attack. However, in this proposed work, timestamps are attached during the session key exchange. During initial session key generation request, sends to the ; here, checks the validity of the current timestamp (. If the minimum delay is not satisfied, then the request is discarded. Moreover, after the session key generation, sends to . Here also, the validity of is checked to ensure the legitimacy of the session key. Since the information is transferred with the assistance of the session key, without capturing the session key, it is hard for an adversary to perform a reply attack. Thus, our scheme is resistant to reply attack.
5.5. Privacy Preservation
Anonymous dummy identities are used to hide the real identities of the and the in this proposed scheme. Mutual authentication uses only the dummy identity and dummy identity. Therefore, even if the adversary discovers the dummy identity of the /, it is difficult for the adversary to determine the original identity of the /. In addition, the fake identity of and are calculated as and , which involves the master key, the private key of , and the private key of and . Tracing of the private keys of / is hard due to DLP. As a result, privacy is preserved in this suggested work.
5.6. Repudiation Attack
In this suggested framework, repudiation of the is not possible. Here, the is registered with the offline. Only after the successful authentication, the security parameters are transferred to and the authenticated becomes the part of the network. As a result, only the authenticated can request information/data from the authenticated drone. Therefore, on receiving the confidential data from the controlling device of , the cannot repudiate.
5.7. Unlinkability
Confidential information is transferred using the short life session key. These session keys have a limited life span. As a result, once the information is transferred with this short life session key, the validity of this session key expires. During the next/successive information transfer, a new session key is to be generated for efficient transfer of information. Thus, there exists an unlinkability between the two successive messages. Therefore, it is hard for an adversary to link the two messages from the same user.
5.8. Man in Middle Attack
If an adversary is capable of deceiving both the and the , a man in the middle attack is possible. In our suggested work, even if an adversary captures ,,) from , it is difficult for an adversary to alter the parameters in the list. Even if the adversary modifies the credentials, checks the condition .,. If the condition is not gratified, then the current authentication request is aborted. Thus, our work is resistant to man in the middle attack.
5.9. Privileged Insider Attack
The required credentials for the and are provided by during the initial offline registration in a secure way. Therefore, it is impossible for an inside attacker to generate fake credentials for /. Moreover, is a completely trusted authority and it is difficult for an inside attacker to compromise it. The validity of the session key generated is only for a limited period and it is hard for an inside attacker to crack it. Thus, our proposed work is resistant to insider attack.