Lightweight Secure Communication Supporting Batch Authentication for UAV Swarm
Abstract
1. Introduction
1.1. Related Work
1.2. Contribution
- A layered secure communication model for UAV swarm is designed, which not only ensures real-time identity authentication but also prevents the invasion of malicious drones;
- To ensure the secure transmission of communication data, a secure transmission protocol is implemented by using elliptic curves, which not only reduces the number of encryptions but also ensures the randomness and one-time use of the session key;
- An identity authentication scheme supporting batch signature verification is proposed. The receiver can independently choose single signature verification or batch signature verification according to different scenarios, which improves the efficiency of identity authentication;
- The effectiveness and feasibility of this scheme are demonstrated via experiments. Under the same conditions, the proposed scheme has lower communication and computation costs, which is more suitable for UAV swarm with limited computing power.
2. Preliminaries
2.1. Elliptic Curve Cryptography
2.2. Chosen Plaintext Attack Security Model
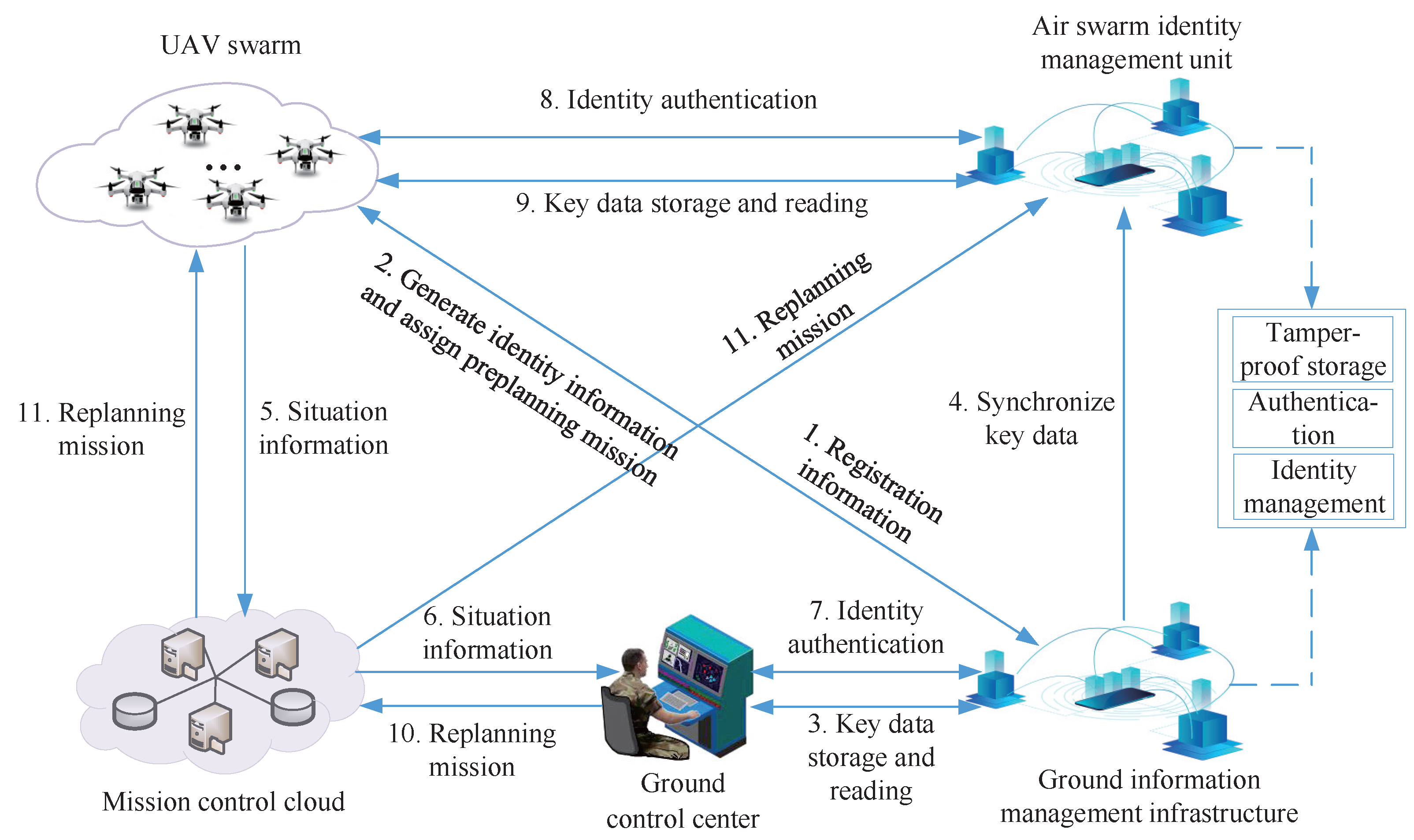
3. System Model
3.1. Model Design
- The ground control center mainly generates pre-planning missions and dynamically adjusts them based on the latest situation information. Moreover, it can detect the operation of the UAV swarm in real time to ensure the smooth execution of the mission;
- The UAV swarm performs the missions of the ground control center and sends the collected situation information to the mission control cloud;
- The mission control cloud receives situation information sent by the drone and sends the replanning mission of the ground control center to the drone and the ASIMU;
- The GIMI is a distributed system composed of organizations involved in UAV swarm application and is deployed on the ground, which is used to store key information such as the identity of the UAV, complete the identity authentication of the mission control cloud and the UAV, and provide key data to the ground control center;
- The ASIMU is a distributed system composed of multiple reliable UAVs, which is deployed between UAV swarm to store key information such as the drone’s identity and realize identity authentication between drones. When two drones communicate with each other, they first verify each other’s identities through ASIMU to prevent the invasion of malicious drones.
3.2. System Initialization
4. Scheme Design
4.1. Secure Communication Protocol
- The sender sends message:
- The receiver processes message:
| Algorithm 1 Ciphertext processing algorithm |
| Require: Ensure:
|
| Algorithm 2 Receiver information processing algorithm |
| Require: Ensure:
|
4.2. Identity Authentication
| Algorithm 3 Signature algorithm |
| Require: Ensure:
|
| Algorithm 4 Single signature verification algorithm |
| Require: Ensure:
|
| Algorithm 5 Batch signature verification algorithm |
| Require: Ensure:
|
5. Performance Analysis and Evaluation
5.1. Communication Cost and Computation Cost Analysis
5.1.1. Communication Cost Analysis
5.1.2. Computation Cost Analysis
5.2. Communication Cost and Computation Cost Evaluation
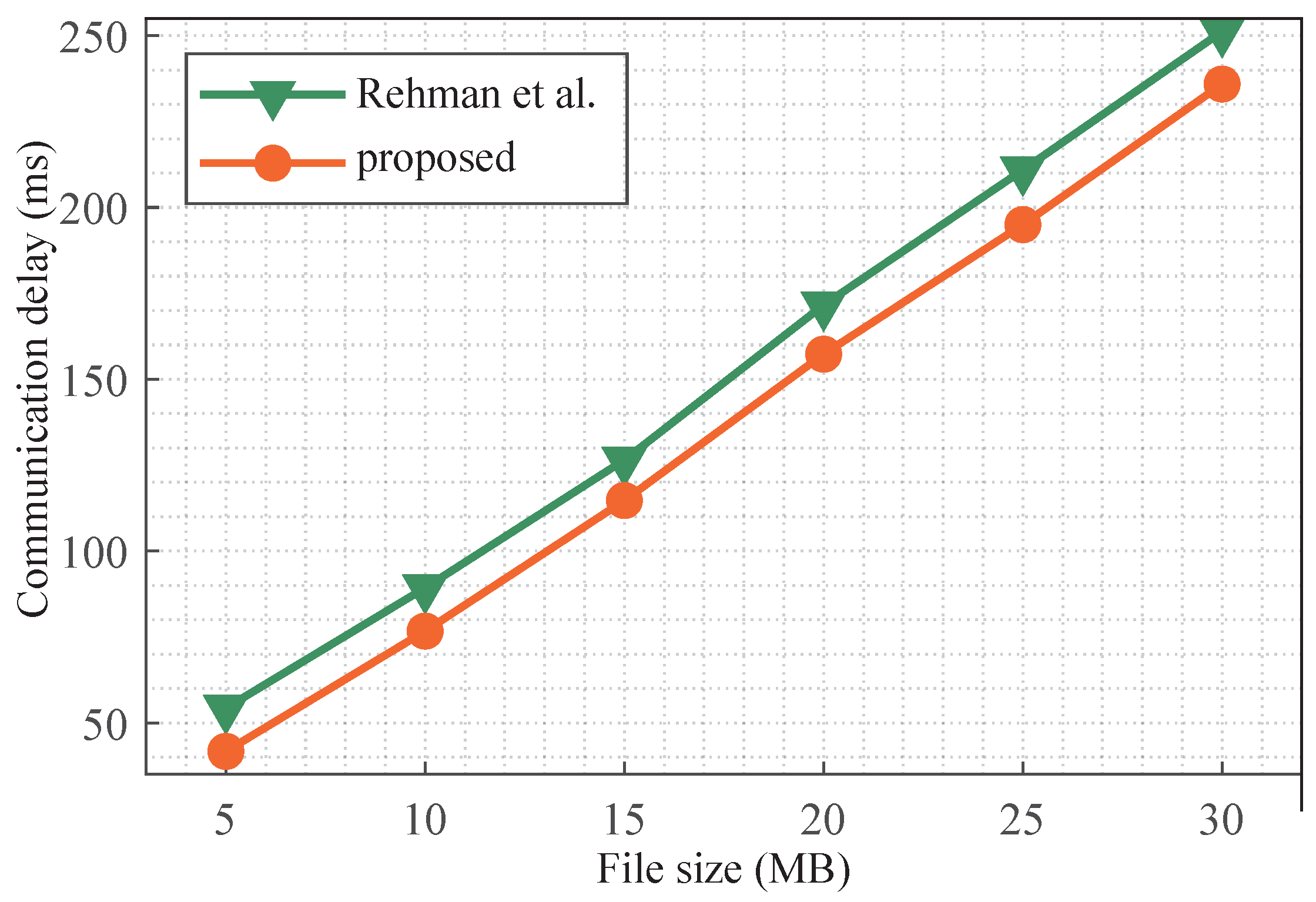
5.2.1. Communication Cost Evaluation
5.2.2. Computation Cost Evaluation
6. Security Analysis
6.1. Confidentiality
- The information transmitted by each entity over the public channel can be easily intercepted by the adversary;
- The transmitted information intercepted by the adversary can be stored, deleted, modified, and replayed;
- The adversary can obtain the information stored in the device after obtaining the user device;
- The adversary knows all the steps of the authentication protocol.
6.2. Man-in-the-Middle Attacks
6.3. Replay Attacks
6.4. Impersonation Attacks
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Khan, A.A.; Khan, M.M.; Khan, K.M.; Arshad, J.; Ahmad, F. A blockchain-based decentralized machine learning framework for collaborative intrusion detection within UAVs. Comput. Netw. 2021, 196, 108217. [Google Scholar] [CrossRef]
- Deng, H.; Huang, J.; Liu, Q.; Zhao, T.; Zhou, C.; Gao, J. A Distributed Collaborative Allocation Method of Reconnaissance and Strike Tasks for Heterogeneous UAVs. Drones 2023, 7, 138. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Sutrala, A.K.; Das, A.K.; Park, Y. LAKA-UAV: Lightweight authentication and key agreement scheme for cloud-assisted Unmanned Aerial Vehicle using blockchain in flying ad-hoc networks. Comput. Netw. 2023, 224, 109612. [Google Scholar] [CrossRef]
- Zhang, S.; Li, Y.; Tian, Y.; Zhou, Z.; Geng, X.; Shi, T. Dynamic redeployment of UAV base stations in large-scale and unreliable environments. Internet Things 2023, 24, 100985. [Google Scholar] [CrossRef]
- Liu, S.; Zhu, M.; Tao, R.; Ren, H. Fine-Grained Feature Perception for Unmanned Aerial Vehicle Target Detection Algorithm. Drones 2024, 8, 181. [Google Scholar] [CrossRef]
- Tlili, F.; Ayed, S.; Fourati, L.C. Advancing UAV security with artificial intelligence: A comprehensive survey of techniques and future directions. Internet Things 2024, 27, 101281. [Google Scholar] [CrossRef]
- Qiao, G.; Zhuang, Y.; Ye, T.; Qiao, Y. BCDAIoD: An Efficient Blockchain-Based Cross-Domain Authentication Scheme for Internet of Drones. Drones 2023, 7, 302. [Google Scholar] [CrossRef]
- Kumari, A.; Gupta, R.; Tanwar, S.; Kumar, N. A taxonomy of blockchain-enabled softwarization for secure UAV network. Comput. Commun. 2020, 161, 304–323. [Google Scholar] [CrossRef]
- Pauu, K.T.; Wu, J.; Fan, Y.; Pan, Q. Differential Privacy and Blockchain-Empowered Decentralized Graph Federated Learning Enabled UAVs for Disaster Response. IEEE Internet Things J. 2023, 11, 20930–20947. [Google Scholar] [CrossRef]
- Ranjitha, K.; Pathak, D.; Tammana, P.; Alladi, T. Accelerating PUF-based UAV authentication protocols using programmable switch. In Proceedings of the 2022 14th International Conference on COMmunication Systems & NETworkS (COMSNETS), Bangalore, India, 4–8 January 2022; pp. 309–313. [Google Scholar]
- Nawaz, H.; Ali, H.M.; Laghari, A.A. UAV communication networks issues: A review. Arch. Comput. Methods Eng. 2021, 28, 1349–1369. [Google Scholar] [CrossRef]
- Ogunbunmi, S.; Chen, Y.; Blasch, E.; Chen, G. A Survey on Reputation Systems for UAV Networks. Drones 2024, 8, 253. [Google Scholar] [CrossRef]
- Mehta, P.; Gupta, R.; Tanwar, S. Blockchain envisioned UAV networks: Challenges, solutions, and comparisons. Comput. Commun. 2020, 151, 518–538. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Sahu, N.; Guizani, M. Applications of blockchain in unmanned aerial vehicles: A review. Veh. Commun. 2020, 23, 100249. [Google Scholar] [CrossRef]
- He, D.; Chan, S.; Guizani, M. Communication security of unmanned aerial vehicles. IEEE Wirel. Commun. 2016, 24, 134–139. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J. Design and analysis of secure lightweight remote user authentication and key agreement scheme in internet of drones deployment. IEEE Internet Things J. 2018, 6, 3572–3584. [Google Scholar] [CrossRef]
- Hua, M.; Wang, Y.; Wu, Q.; Dai, H.; Huang, Y.; Yang, L. Energy-efficient cooperative secure transmission in multi-UAV-enabled wireless networks. IEEE Trans. Veh. Technol. 2019, 68, 7761–7775. [Google Scholar] [CrossRef]
- Alladi, T.; Bansal, G.; Chamola, V.; Guizani, M. SecAuthUAV: A novel authentication scheme for UAV-ground station and UAV-UAV communication. IEEE Trans. Veh. Technol. 2020, 69, 15068–15077. [Google Scholar] [CrossRef]
- Fotohi, R.; Nazemi, E.; Shams Aliee, F. An agent-based self-protective method to secure communication between UAVs in unmanned aerial vehicle networks. Veh. Commun. 2020, 26, 100267. [Google Scholar] [CrossRef]
- Ko, Y.; Kim, J.; Duguma, D.G.; Astillo, P.V.; You, I.; Pau, G. Drone Secure Communication Protocol for Future Sensitive Applications in Military Zone. Sensors 2021, 21, 2057. [Google Scholar] [CrossRef]
- Tan, Y.; Wang, J.; Liu, J.; Kato, N. Blockchain-assisted distributed and lightweight authentication service for industrial unmanned aerial vehicles. IEEE Internet Things J. 2022, 9, 16928–16940. [Google Scholar] [CrossRef]
- Wani, A.R.; Gupta, S.K.; Khanam, Z.; Rashid, M.; Alshamrani, S.S.; Baz, M. A novel approach for securing data against adversary attacks in UAV embedded HetNet using identity based authentication scheme. IET Intell. Transp. Syst. 2023, 17, 2171–2189. [Google Scholar] [CrossRef]
- Wang, J.; Jiao, Z.; Chen, J.; Hou, X.; Yang, T.; Lan, D. Blockchain-aided secure access control for UAV computing networks. IEEE Trans. Netw. Sci. Eng. 2023, 11, 5267–5279. [Google Scholar] [CrossRef]
- Bansal, G.; Sikdar, B. Achieving Secure and Reliable UAV Authentication: A Shamir’s Secret Sharing Based Approach. IEEE Trans. Netw. Sci. Eng. 2024, 11, 3598–3610. [Google Scholar] [CrossRef]
- Rehman, S.; Talat Bajwa, N.; Shah, M.A.; Aseeri, A.O.; Anjum, A. Hybrid AES-ECC Model for the Security of Data over Cloud Storage. Electronics 2021, 10, 2673. [Google Scholar] [CrossRef]
- Maria, A.; Rajasekaran, A.S.; Al-Turjman, F.; Altrjman, C.; Mostarda, L. BAIV: An Efficient Blockchain-Based Anonymous Authentication and Integrity Preservation Scheme for Secure Communication in VANETs. Electronics 2022, 11, 488. [Google Scholar] [CrossRef]
- Maurya, C.; Chaurasiya, V.K. Efficient anonymous batch authentication scheme with conditional privacy in the Internet of Vehicles (IoV) applications. IEEE Trans. Intell. Transp. Syst. 2023, 24, 9670–9683. [Google Scholar] [CrossRef]
- Wang, C.; Huo, P.; Ma, M.; Zhou, T.; Zhang, Y. A provable secure and lightweight ECC-based authenticated key agreement scheme for edge computing infrastructure in smart grid. Computing 2023, 105, 2511–2537. [Google Scholar] [CrossRef]
- Tan, H.; Zheng, W.; Vijayakumar, P. Secure and efficient authenticated key management scheme for UAV-assisted infrastructure-less IoVs. IEEE Trans. Intell. Transp. Syst. 2023, 24, 6389–6400. [Google Scholar] [CrossRef]
- Tan, H.; Chung, I. Secure authentication and key management with blockchain in VANETs. IEEE Access 2020, 8, 2482–2498. [Google Scholar] [CrossRef]
- Feng, X.; Shi, Q.; Xie, Q. P2BA: A privacy-preserving protocol with batch authentication against semi-trusted RSUs in vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2021, 8, 3888–3899. [Google Scholar] [CrossRef]
- Bagga, P.; Sutrala, A.K.; Das, A.K.; Vijayakumar, P. Blockchain-based batch authentication protocol for Internet of Vehicles. J. Syst. Archit. 2021, 113, 101877. [Google Scholar] [CrossRef]
- Vijayakumar, P.; Azees, M.; Kozlov, S.A.; Rodrigues, J.J. An anonymous batch authentication and key exchange protocols for 6 G enabled VANETs. IEEE Trans. Intell. Transp. Syst. 2021, 23, 1630–1638. [Google Scholar] [CrossRef]
- Jan, S.U.; Abbasi, I.A.; Algarni, F.; Khan, A.S. A verifiably secure ECC based authentication scheme for securing IoD using FANET. IEEE Access 2022, 10, 95321–95343. [Google Scholar] [CrossRef]
- Chen, Y.; Yin, F.; Hu, S.; Sun, L.; Li, Y.; Xing, B.; Guo, B. ECC-based authenticated key agreement protocol for industrial control system. IEEE Internet Things J. 2022, 10, 4688–4697. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theorys 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Guo, J.; Du, Y.; Zhang, Y.; Li, M. A provably secure ECC-based access and handover authentication protocol for space information networks. J. Netw. Comput. Appl. 2021, 193, 103183. [Google Scholar] [CrossRef]
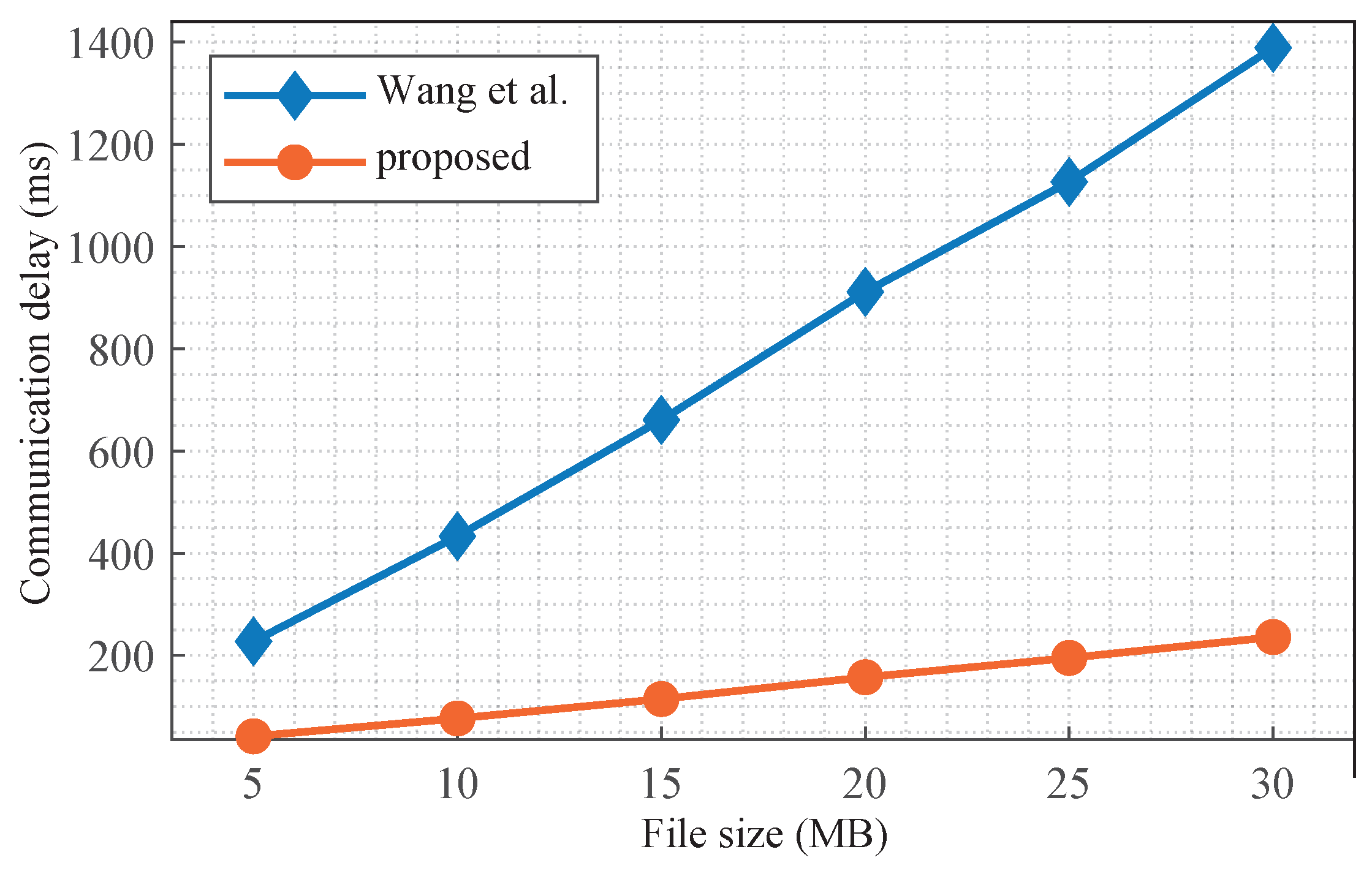

| Symbol | Description |
|---|---|
| UAV’s that identifies the document | |
| Publickey | UAV’s public key required for authentication and establishing communication |
| Timestamp | The timestamp when the document was created |
| Event | The record of important UAV event |
| UpdateTimestamp | The timestamp of the last update of the document |
| Role | UAV’s role |
| PhysicalID | UAV’s physical ID |
| Sign | Integrity proof of the document, i.e., the signature of the GIMI |
| Author | Verifying Single Signature | Verifying n Signatures |
|---|---|---|
| Maria et al. [26] | 2080 | 2080n |
| Maurya et al. [27] | 1628 | 1472n |
| Tan et al. [30] | 3936 | 2368n + 1568 |
| Feng et al. [31] | 6144 | 6144n |
| Bagga et al. [32] | 4544 | 4544n |
| Vijayakumar et al. [33] | 2208 | 2208n |
| Proposed | 928 | 928n |
| Author | Computation Delay in Batch Signature Verification |
|---|---|
| Maria et al. [26] | |
| Maurya et al. [27] | |
| Tan et al. [30] | |
| Feng et al. [31] | |
| Bagga et al. [32] | |
| Vijayakumar et al. [33] | |
| Proposed |
| Indicator | Maximum Time (ms) | Minimum Time (ms) | Average Time (ms) |
|---|---|---|---|
| 5.1 | 4.4 | 4.8 | |
| 1.6 | 0.9 | 1.1 | |
| 0.02 | 0.008 | 0.014 | |
| 0.001 | 0.0002 | 0.0006 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Han, P.; Sui, A.; Wu, J. Lightweight Secure Communication Supporting Batch Authentication for UAV Swarm. Drones 2025, 9, 139. https://doi.org/10.3390/drones9020139
Han P, Sui A, Wu J. Lightweight Secure Communication Supporting Batch Authentication for UAV Swarm. Drones. 2025; 9(2):139. https://doi.org/10.3390/drones9020139
Chicago/Turabian StyleHan, Pengbin, Aina Sui, and Jiang Wu. 2025. "Lightweight Secure Communication Supporting Batch Authentication for UAV Swarm" Drones 9, no. 2: 139. https://doi.org/10.3390/drones9020139
APA StyleHan, P., Sui, A., & Wu, J. (2025). Lightweight Secure Communication Supporting Batch Authentication for UAV Swarm. Drones, 9(2), 139. https://doi.org/10.3390/drones9020139








