Development, Implementation and Evaluation of An Epidemic Communication System
Abstract
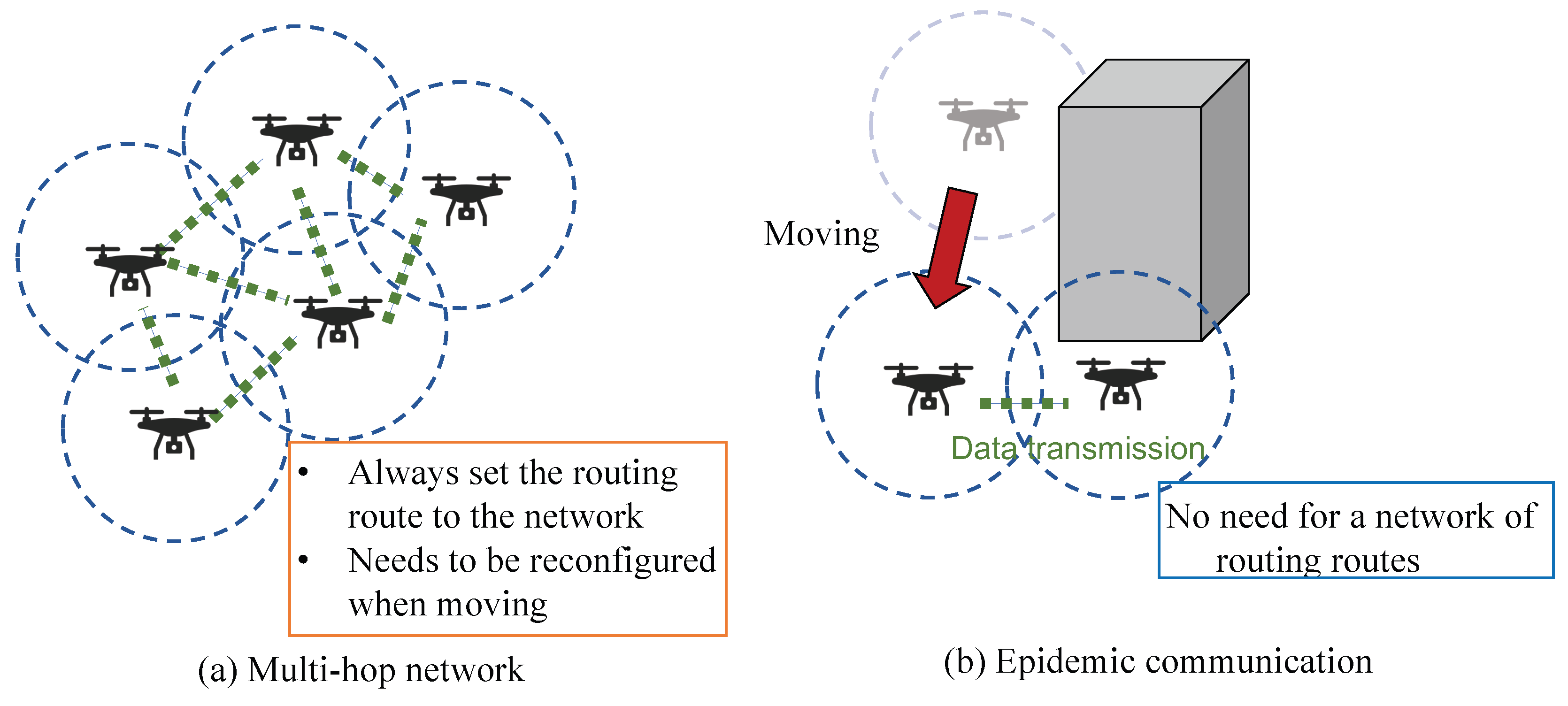
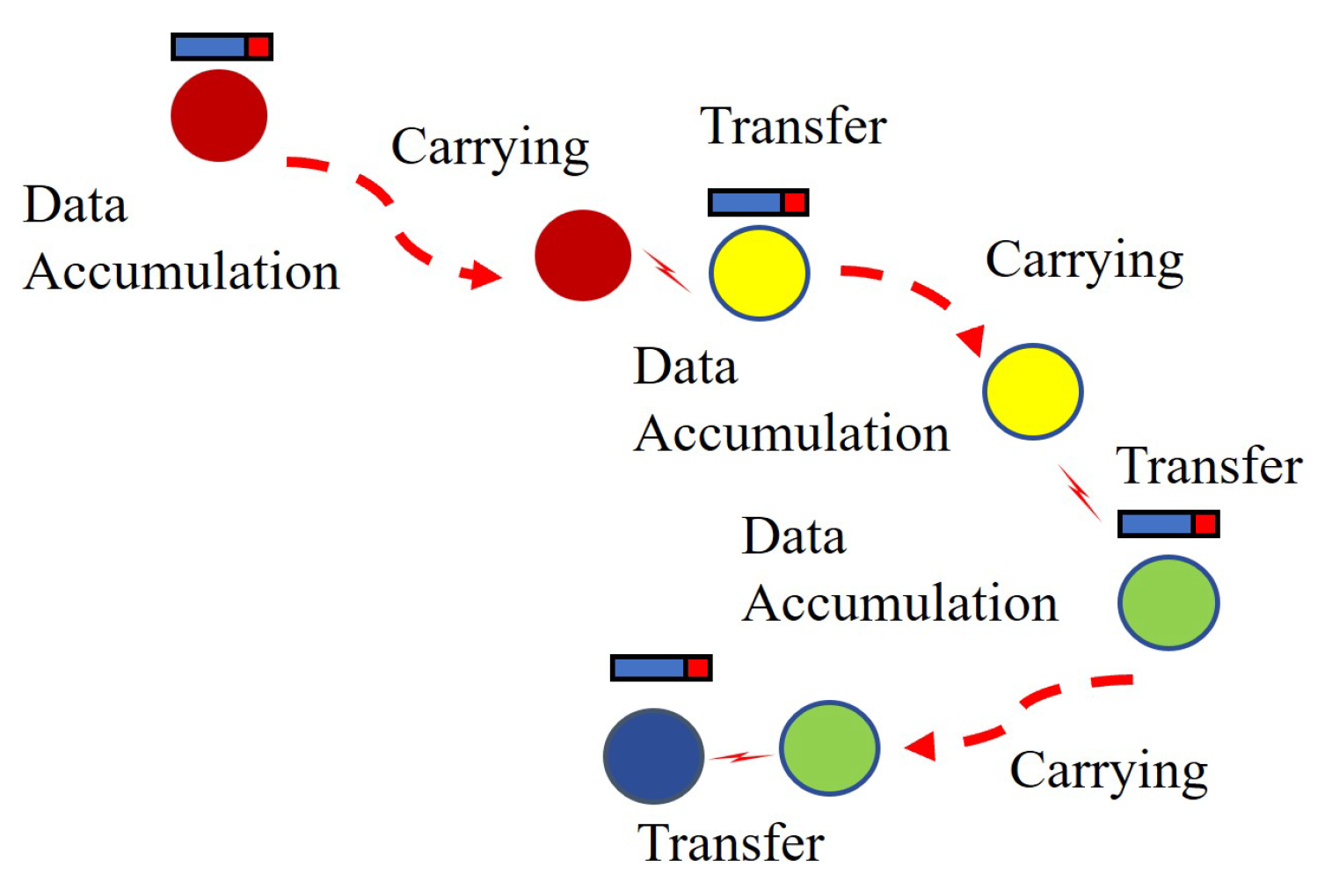
:1. Introduction
- #1
- The system is designed for practical use, since there are various theoretical studies on epidemic communication, but their applications are not clear.
- #2
- The main problem solved is to analyze the effect of between-drone interference on the infection rate (data transmission rate), and to propose the optimal transmission method according to the flight speed.
- #3
- Based on the results of these analyses, we designed functions to be implemented in drones, developed wireless devices, and confirmed their operation through demonstration tests.
2. Related Works and Issues
- (A)
- Numerous theoretical studies have been conducted and various technical applications have been proposed. However, few examples of actual system implementations have been realized. The requirement for wireless devices with various functions such as relaying, connecting, disconnecting, and storing data is a challenge for construction of these systems.
- (B)
- The designs of actual communication systems are difficult to optimize with respect to specific communication distances and interferences between radio stations. In addition, the amount of data that can be transmitted must be calculated when nodes pass each other.
- (C)
- The system is assumed to be unsuitable from the viewpoint of information security for communications that may include personal information, such as handheld tablets, and few systems have been used practically or commercialized because of such problems. That is, no dedicated device has been developed because establishing it as a service is difficult.
3. Implementation Method for Epidemic Communication
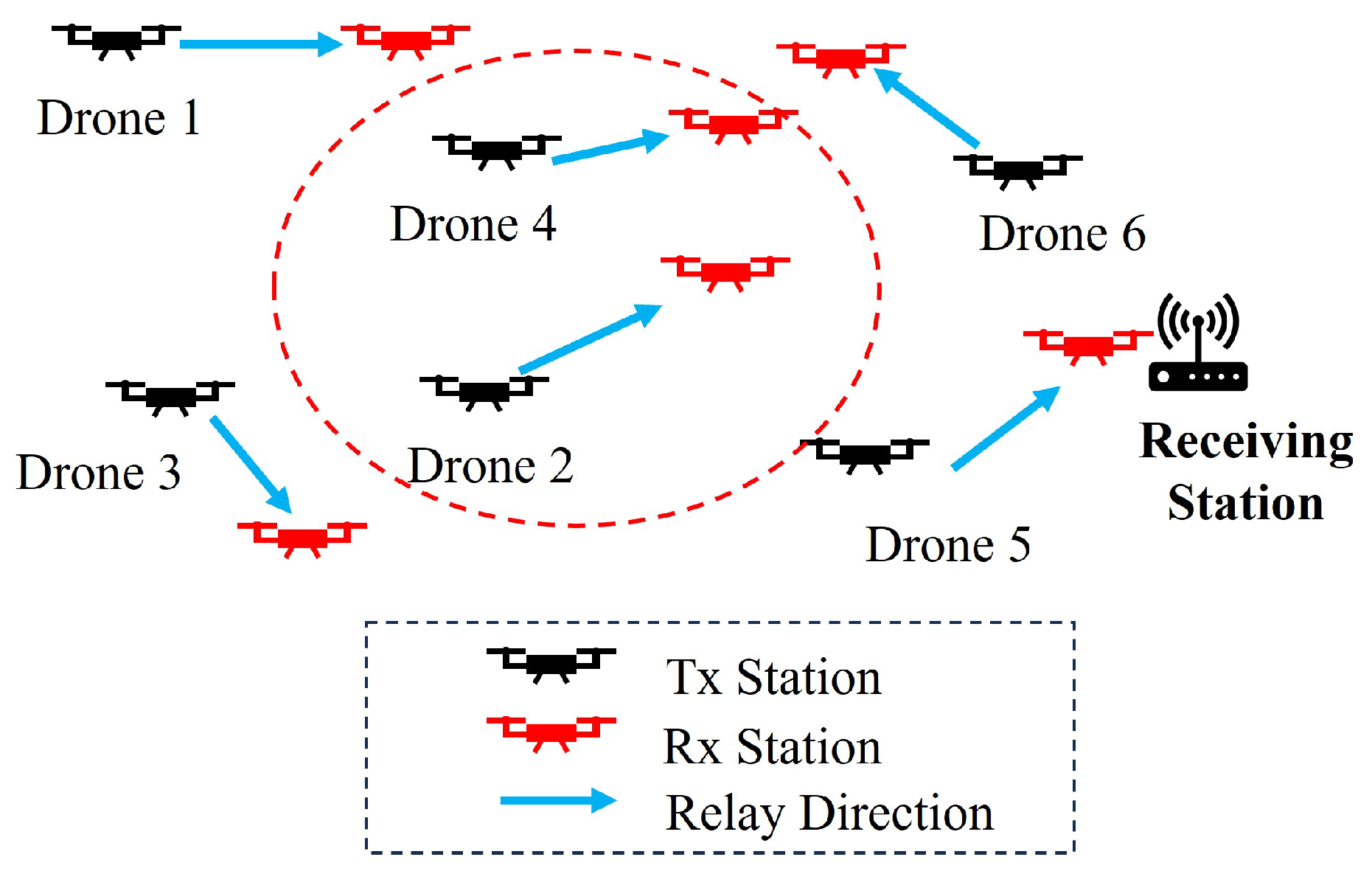
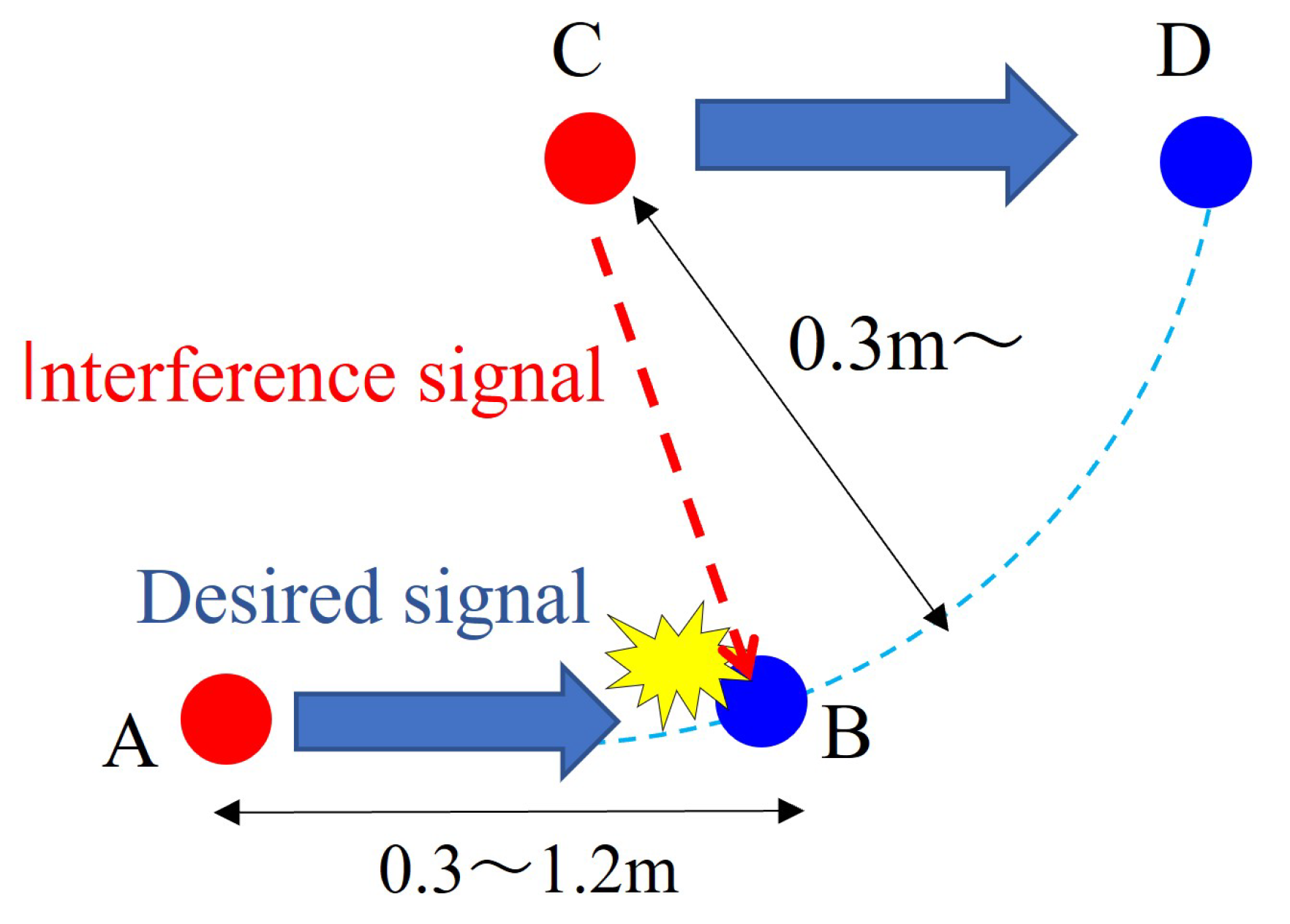
3.1. Interference between Multiple Nodes and Transmission Area
3.2. Interference Model Evaluation Method and Selection of Received Power Threshold
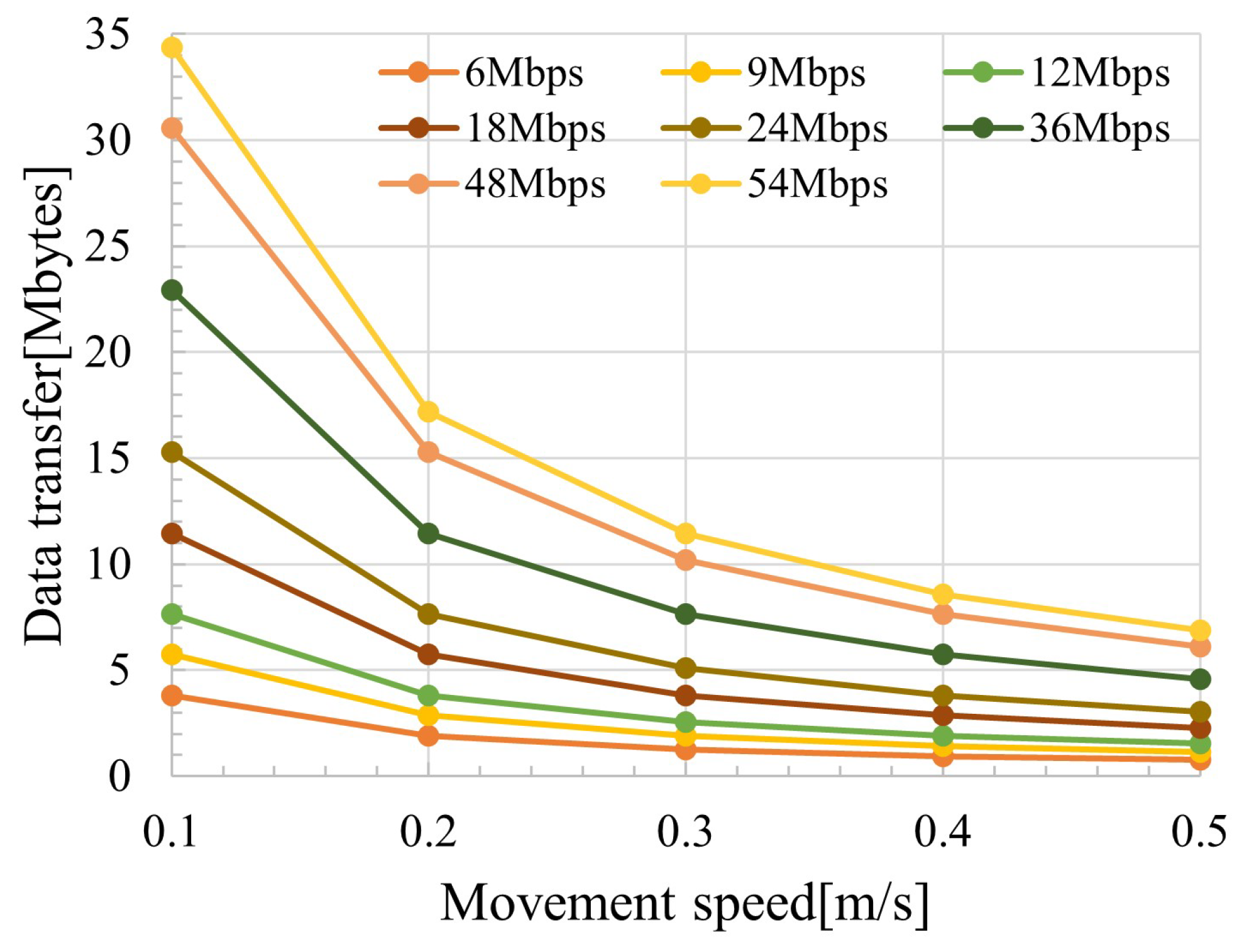
3.3. Change in Amount of Data Transferred Due to Movement of Radio Stations
3.4. Evaluation of the Amount of Data That Can Be Sent
4. Development of the Epidemic Communication System
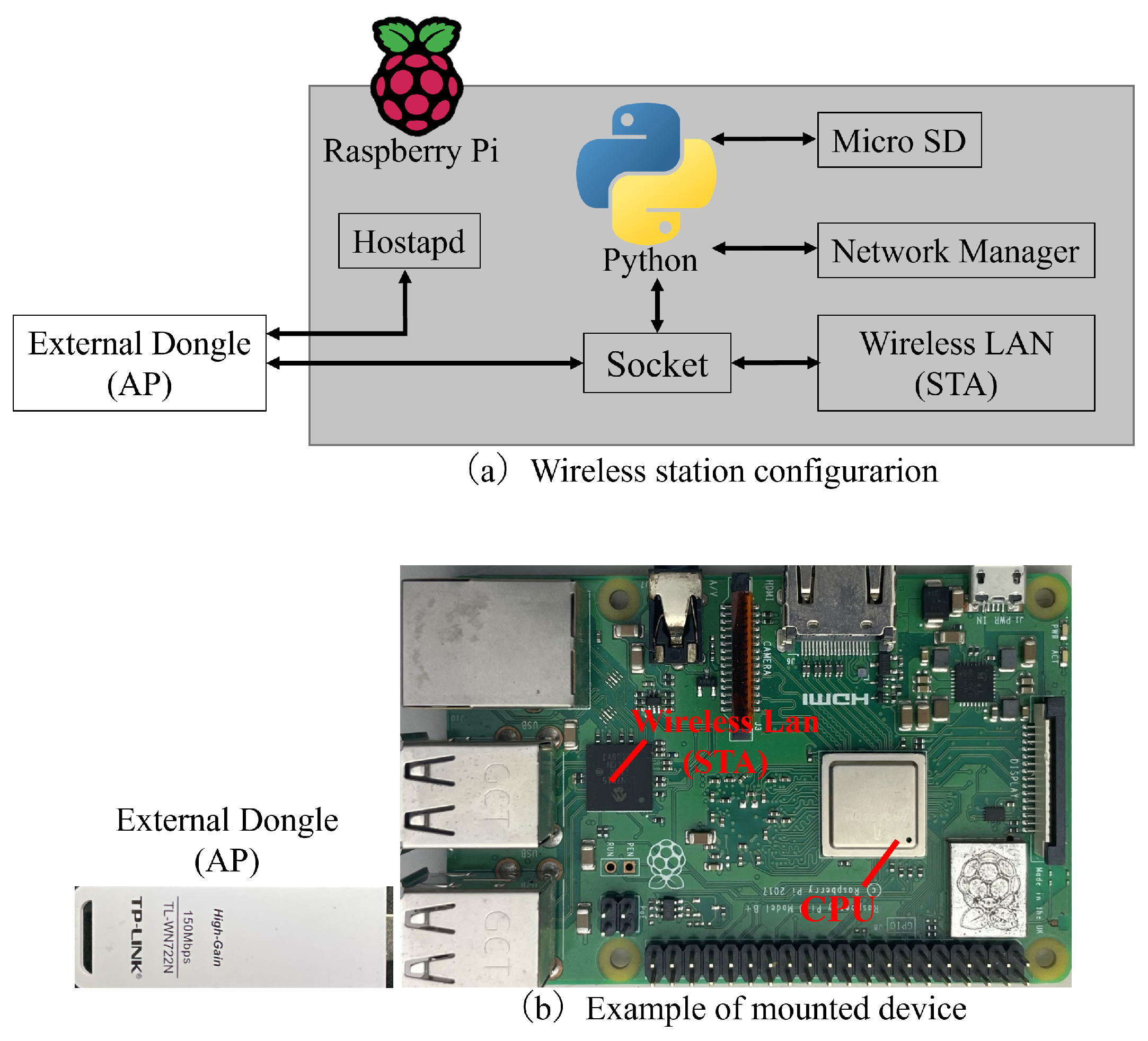
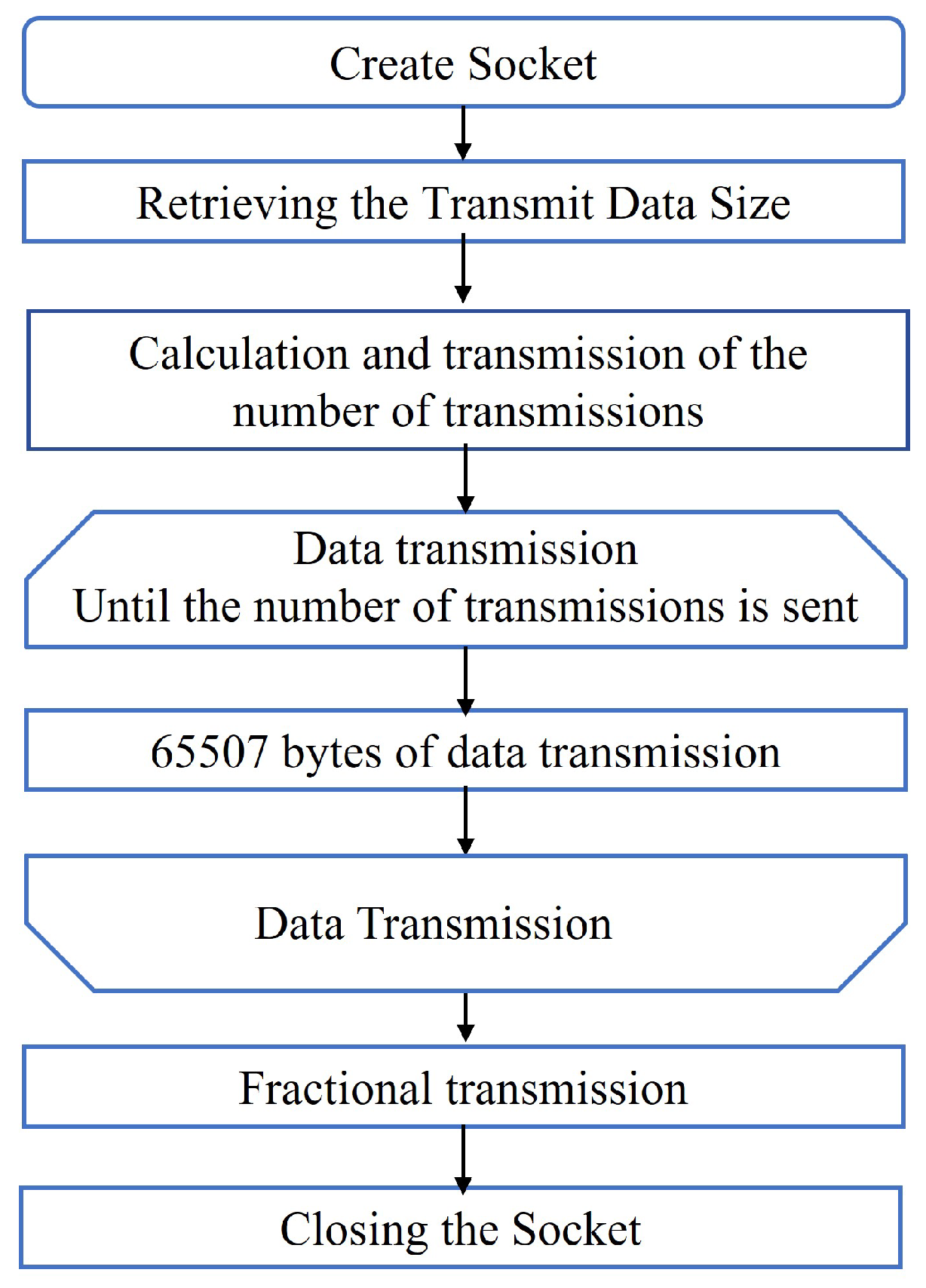
4.1. Device Implementation
4.2. Evaluation of Epidemic Communication Systems through Experiments
5. Conclusions
Supplementary Materials
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Perkins, C.E. Ad Hoc Networking; Pearson Education India: Hoboken, NJ, USA, 2008. [Google Scholar]
- Kleinrock, L.; Silvester, J. Optimum transmission radii for packet radio networks or why six is a magic number. In Proceedings of the IEEE National Telecommunications Conference, Birmingham, Alabama, 3–6 December 1978; Volume 4, pp. 1–4. [Google Scholar]
- Takagi, H.; Kleinrock, L. Optimal transmission ranges for randomly distributed packet radio terminals. IEEE Trans. Commun. 1984, 32, 246–257. [Google Scholar] [CrossRef]
- Royer, E.M.; Perkins, C.E. An implementation study of the AODV routing protocol. In Proceedings of the 2000 IEEE Wireless Communications and Networking Conference. Conference Record (Cat. No. 00TH8540), Chicago, IL, USA, 23–28 September 2000; IEEE: Piscataway, NJ, USA, 2000; Volume 3, pp. 1003–1008. [Google Scholar]
- Clausen, T.; Jacquet, P. RFC3626: Optimized Link State Routing Protocol (OLSR), Nternet Eng; Tech. Rep. RFC 3626; Task Force (IETF): Fremont, CA, USA, October 2003; Available online: http://www.rfc-editor.org/rfc/rfc3626.txt (accessed on 14 May 2024).
- Burleigh, S.; Hooke, A.; Torgerson, L.; Fall, K.; Cerf, V.; Durst, B.; Scott, K.; Weiss, H. Delay-tolerant networking: An approach to interplanetary internet. IEEE Commun. Mag. 2003, 41, 128–136. [Google Scholar] [CrossRef]
- Fall, K. A delay-tolerant network architecture for challenged internets. In Proceedings of the 2003 conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Karlsruhe, Germany, 25–29 August 2003; pp. 27–34. [Google Scholar]
- Castro, A.A.V.; Serugendo, G.D.M.; Konstantas, D. Hovering information–self-organizing information that finds its own storage. In Autonomic Communication; Springer: Boston, MA, USA, 2009; pp. 111–145. [Google Scholar]
- Virtamo, J.; Hyytiä, E.; Lassila, P. Criticality condition for information floating with random walk of nodes. Perform. Eval. 2013, 70, 114–123. [Google Scholar] [CrossRef]
- Matsuda, T.; Takine, T. (p, q)-Epidemic routing for sparsely populated mobile ad hoc networks. IEEE J. Sel. Areas Commun. 2008, 26, 783–793. [Google Scholar] [CrossRef]
- De Abreu, C.S.; Salles, R.M. Modeling message diffusion in epidemical DTN. Ad Hoc Netw. 2014, 16, 197–209. [Google Scholar] [CrossRef]
- Alenazi, M.J.; Cheng, Y.; Zhang, D.; Sterbenz, J.P. Epidemic routing protocol implementation in ns-3. In Proceedings of the 2015 Workshop on ns-3, Barcelona, Spain, 13–14 May 2015; pp. 83–90. [Google Scholar]
- Hiraguri, T.; Kimura, T.; Endo, K.; Ohya, T.; Takanashi, T.; Shimizu, H. Shape classification technology of pollinated tomato flowers for robotic implementation. Sci. Rep. 2023, 13, 2159. [Google Scholar] [CrossRef] [PubMed]
- Kurosawa, T.; Kimura, T.; Shimizu, H.; Hiraguri, T. Epidemic communication control methods suitable for inter-drone relay in pollination systems. IEICE Commun. Express 2023, 12, 236–241. [Google Scholar] [CrossRef]
- Keita, E.; Kimura, T.; Nobuhiko, I.; Hiraguri, T. Semantic segmentation based field detection using drones. In Proceedings of the 2022 IEEE International Conference on Consumer Electronics-Taiwan, Taipei, Taiwan, 6–8 July 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 213–214. [Google Scholar]
- Yamada, N.; Hiraguri, T.; Shimizu, H.; Kimura, T.; Shimada, T.; Shibasaki, A.; Takemura, Y. Drone Flight Experiment using RTK Positioning for Pear Pollination. In Proceedings of the 2023 International Conference on Consumer Electronics-Taiwan (ICCE-Taiwan), Taipei, Taiwan, 6–8 July 2022; IEEE: Piscataway, NJ, USA, 2023; pp. 655–656. [Google Scholar]
- IEEE 802.11 p Working Group IEEE Standard for Information Technology—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 6: Wireless Access in Vehicular Environments. Available online: https://ieeexplore.ieee.org/document/5514475 (accessed on 14 May 2024).
- Rashidi, L.; Towsley, D.; Mohseni-Kabir, A.; Movaghar, A. On the performance analysis of epidemic routing in non-sparse delay tolerant networks. IEEE Trans. Mob. Comput. 2022, 22, 4134–4149. [Google Scholar] [CrossRef]
- Rashidi, L.; Dalili-Yazdi, A.; Entezari-Maleki, R.; Sousa, L.; Movaghar, A. Modeling epidemic routing: Capturing frequently visited locations while preserving scalability. IEEE Trans. Veh. Technol. 2021, 70, 2713–2727. [Google Scholar] [CrossRef]
- Hu, Y.; Tian, T.; Zhang, F.; Chen, Q.; Yu, G.; Ma, D. Restricted epidemic routing method in large-scale delay-tolerant networks. In Proceedings of the 2021 IEEE 21st International Conference on Communication Technology (ICCT), Tianjin, China, 13–16 October 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 380–386. [Google Scholar]
- Prasad, A.O.; Mishra, P.; Jain, U.; Pandey, A.; Sinha, A.; Yadav, A.S.; Kumar, R.; Sharma, A.; Kumar, G.; Salem, K.H.; et al. Design and development of software stack of an autonomous vehicle using robot operating system. Robot. Auton. Syst. 2023, 161, 104340. [Google Scholar] [CrossRef]
- Tomic, T.; Schmid, K.; Lutz, P.; Domel, A.; Kassecker, M.; Mair, E.; Grixa, I.L.; Ruess, F.; Suppa, M.; Burschka, D. Toward a fully autonomous UAV: Research platform for indoor and outdoor urban search and rescue. IEEE Robot. Autom. Mag. 2012, 19, 46–56. [Google Scholar] [CrossRef]
- Anggraeni, P.; Mrabet, M.; Defoort, M.; Djemai, M. Development of a wireless communication platform for multiple-mobile robots using ROS. In Proceedings of the 2018 6th International Conference on Control Engineering & Information Technology (CEIT), Istanbul, Turkey, 25–27 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Trautman, P.; Ma, J.; Murray, R.M.; Krause, A. Robot navigation in dense human crowds: The case for cooperation. In Proceedings of the 2013 IEEE International Conference on Robotics and Automation, Karlsruhe, Germany, 6–10 May 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 2153–2160. [Google Scholar]
- Prassler, E.; Scholz, J.; Fiorini, P. A robotics wheelchair for crowded public environment. IEEE Robot. Autom. Mag. 2001, 8, 38–45. [Google Scholar] [CrossRef]
- Xuexi, Z.; Guokun, L.; Genping, F.; Dongliang, X.; Shiliu, L. SLAM algorithm analysis of mobile robot based on lidar. In Proceedings of the 2019 Chinese Control Conference (CCC), Guangzhou, China, 27–30 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 4739–4745. [Google Scholar]
- Malavazi, F.B.; Guyonneau, R.; Fasquel, J.B.; Lagrange, S.; Mercier, F. LiDAR-only based navigation algorithm for an autonomous agricultural robot. Comput. Electron. Agric. 2018, 154, 71–79. [Google Scholar] [CrossRef]
- Gatesichapakorn, S.; Takamatsu, J.; Ruchanurucks, M. ROS based autonomous mobile robot navigation using 2D LiDAR and RGB-D camera. In Proceedings of the 2019 First International Symposium on Instrumentation, Control, Artificial Intelligence, and Robotics (ICA-SYMP), Bangkok, Thailand, 16–18 January 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 151–154. [Google Scholar]
- Cardieri, P. Modeling interference in wireless ad hoc networks. IEEE Commun. Surv. Tutor. 2010, 12, 551–572. [Google Scholar] [CrossRef]
- Dhanik, S.; Vijai, C.; Reddy, Y.M.; Dutt, A.; Shaaker, A.M.; Raj, V.H. Ad Hoc Networks: Adaptable Connectivity for Contemporary Business Needs. In Proceedings of the 2023 10th IEEE Uttar Pradesh Section International Conference on Electrical, Electronics and Computer Engineering (UPCON), Greater Noida, India, 1–3 December 2023; IEEE: Piscataway, NJ, USA, 2023; Volume 10, pp. 1694–1698. [Google Scholar]
- Noda, M. Proposal for IEEE802. 15.3 e-Single Carrier PHY; IEEE Doc; IEEE: Piscataway, NJ, USA, 2015; p. 15. [Google Scholar]
- Toshimitsu, K.; Hiraga, K.; Lee, J.; Maekawa, I.; Noda, M. Proposal for IEEE802. 15.3 e-MAC: Superframe and Association; IEEE Doc; IEEE: Piscataway, NJ, USA, 2015; p. 15. [Google Scholar]
- Noda, A.; Shinoda, H. Inter-IC for Wearables (I 2 We): Power and data transfer over double-sided conductive textile. IEEE Trans. Biomed. Circuits Syst. 2018, 13, 80–90. [Google Scholar] [CrossRef] [PubMed]
- Fukui, Y.; Noda, A.; Shinoda, H. Noise factor of active-tile for two-dimensional communication. IEICE Commun. Express 2017, 6, 160–165. [Google Scholar] [CrossRef]
- Alliance, W.F. Wi-Fi Direct Services Draft Technical Specification. version 0.1, Wi-Fi Alliance Technical Committee, Wi-Fi Direct Services Task Group. 2013; 1–86. [Google Scholar]
- Pozar, D.M. Microwave Engineering; John Wiley & Sons: Hoboken, NJ, USA, 2011. [Google Scholar]
- Vizmuller, P. RF Design Guide: Systems, Circuits, and Equations; Artech House: London, UK, 1995. [Google Scholar]
- Raspberry Pi 3 Model B+. Available online: https://www.raspberrypi.com/products/raspberry-pi-3-model-b-plus/ (accessed on 13 December 2023).
- Raspberry Pi 3 Model B+ Benchmark. Available online: https://community.element14.com/products/raspberry-pi/w/documents/3459/a-comprehensive-raspberry-pi-3-model-b-plus-benchmark (accessed on 14 May 2024).
- Scott, K.; Burleigh, S. Bundle Protocol Specification; Technical Report. 2007. Available online: https://www.rfc-editor.org/rfc/rfc5050 (accessed on 14 May 2024).
- Kalita, L. Socket programming. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 4802–4807. [Google Scholar]
- Hiraguri, T.; Shimizu, H.; Kimura, T.; Matsuda, T.; Maruta, K.; Takemura, Y.; Ohya, T.; Takanashi, T. Autonomous drone-based pollination system using AI classifier to replace bees for greenhouse tomato cultivation. IEEE Access 2023, 11, 99352–99364. [Google Scholar] [CrossRef]









| Transmission Rate [Mbps] | Receiver Sensitivity Level [dBm] | SINR [dB] |
|---|---|---|
| 6 | 8.82 | |
| 9 | 9.82 | |
| 12 | 11.82 | |
| 18 | 13.82 | |
| 24 | 16.82 | |
| 36 | 20.82 | |
| 48 | 24.82 | |
| 54 | 25.82 |
| Transmission Rate | Distance between A and B | |||
|---|---|---|---|---|
| 0.3 m | 0.6 m | 0.9 m | 1.2 m | |
| 6 Mbps | 0.9 m | 1.7 m | 2.5 m | 3.4 m |
| 9 Mbps | 1.0 m | 1.9 m | 2.8 m | 3.8 m |
| 12 Mbps | 1.2 m | 2.4 m | 3.6 m | 4.7 m |
| 18 Mbps | 1.5 m | 3.0 m | 4.5 m | 5.9 m |
| 24 Mbps | 2.1 m | 4.2 m | 6.3 m | 8.4 m |
| 36 Mbps | 3.3 m | 6.6 m | 9.9 m | 13.2 m |
| 48 Mbps | 5.3 m | 10.5 m | 15.7 m | 21.0 m |
| 54 Mbps | 5.9 m | 11.8 m | 17.6 m | 23.5 m |
| Setting Item | Setting Value |
|---|---|
| Transmission power | 0 dBm |
| Antenna gain | 0 dBi |
| Communications standards | IEEE802.11g |
| Use channel | 1 ch–2412 MHz |
| Communication distance | 0.3 m |
| Movement speed | 0.1∼0.5 m/s |
| Protocol | UDP |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yamada, N.; Hiraguri, T.; Kimura, T.; Shimizu, H.; Takemura, Y.; Matsuda, T. Development, Implementation and Evaluation of An Epidemic Communication System. IoT 2024, 5, 271-289. https://doi.org/10.3390/iot5020014
Yamada N, Hiraguri T, Kimura T, Shimizu H, Takemura Y, Matsuda T. Development, Implementation and Evaluation of An Epidemic Communication System. IoT. 2024; 5(2):271-289. https://doi.org/10.3390/iot5020014
Chicago/Turabian StyleYamada, Naoki, Takefumi Hiraguri, Tomotaka Kimura, Hiroyuki Shimizu, Yoshihiro Takemura, and Takahiro Matsuda. 2024. "Development, Implementation and Evaluation of An Epidemic Communication System" IoT 5, no. 2: 271-289. https://doi.org/10.3390/iot5020014
APA StyleYamada, N., Hiraguri, T., Kimura, T., Shimizu, H., Takemura, Y., & Matsuda, T. (2024). Development, Implementation and Evaluation of An Epidemic Communication System. IoT, 5(2), 271-289. https://doi.org/10.3390/iot5020014






