A Comprehensive Survey on Knowledge-Defined Networking
Abstract
:1. Introduction
1.1. Objectives and Key Issues Addressed
1.2. Contributions to the Existing Literature
- We are the first to review on knowledge-defined networking, which will provide a useful reference for future researchers who investigate more in this area;
- We compare traditional networking with SDN and KDN;
- Each plane of the KDN architecture is discussed in detail with reference to the existing literature;
- Benefits, challenges, design guidelines, and ongoing research on the KDN architecture are discussed.
1.3. Research Methodology
2. Overview of Knowledge-Defined Networking (KDN)
2.1. A Nutshell on Data, Information, and Knowledge
2.2. KDN System Architecture
- Knowledge Plane—The knowledge plane consists of three sub-planes. The knowledge generation plane generates knowledge using data/information, either by using heuristic model-based methods or machine learning methods. In the knowledge composition plane, generated knowledge and universal knowledge are composed using an ontology editor to produce composed knowledge, which can be used to generate rules by orchestration with user intent. The knowledge distribution and management plane is responsible for storing knowledge and rules using a knowledge base and performing the inserting, updating, deletion, and exchange of knowledge and rules using languages and protocols [25];
- Management Plane—The management plane (also referred to as the measurement plane) operates in parallel with the KDN controller and is responsible for collecting the processes and data/information from the network devices, monitoring the network device status, and configuring the network device. Note that, in KDN, the management plane can be influenced by the application plane to implement configuration policies and by the knowledge plane to aid in real-time network monitoring, whose monitoring output can be used to dynamically configure the network [57,58];
- Data plane—The data plane is composed of forwarding devices that can store, forward, or process data according to the flow rules sent by the control plane. In KDN, the data plane is required to send data requested by the management and control planes [59];
- Control plane—The control plane consists of one or more SDN controllers based on the architecture and is responsible for sending flow rules, access control rules, QoS-based traffic prioritization rules, etc. to the data plane. Control in KDN is driven by both application policies and real-time rules or knowledge generated from the knowledge plane [60];
- Application plane—This plane provides a platform for network applications to communicate requirements to the underlying network infrastructure. It also enables network administrators to define network policies specific to applications and define network configuration policies that are more aligned with high-level business needs and objectives in a centralized manner, where the application logic is decoupled from hardware. In KDN, application policies can be dynamically updated based on knowledge [61].
2.3. KDN vs. SDN vs. Conventional Network
2.3.1. Decoupling of Logical Planes
2.3.2. Network Programmability
2.3.3. Control Plane
2.3.4. Management Plane
2.3.5. Knowledge Plane
2.3.6. Application Plane
2.3.7. Network Architecture
2.3.8. Operational Cost
2.3.9. Security Features
3. Knowledge Plane
3.1. Introduction to Knowledge Plane
3.2. Architecture of the Knowledge Plane
- Knowledge generation plane—Generates descriptive knowledge from raw data using a knowledge generation model;
- Knowledge composition plane—Identifies the relationship between different pieces of knowledge to compose knowledge using an ontology editor, which can be used to generate rules considering user intent;
- Knowledge distribution and management plane—Manages and exchanges raw data (within the knowledge plane), descriptive knowledge, rules, and control messages between the knowledge plane and other planes.
3.3. Knowledge Generation Plane
3.3.1. Generating Knowledge Using Heuristic Model-Based Methods
3.3.2. Generating Knowledge Using Machine Learning Methods
- Supervised learning—In supervised learning, a training data set contains labeled inputs with corresponding labeled outputs for the supervised machine learning algorithm for training (fitting). During training, the ML algorithm learns the underlying patterns in the input data to retrieve the outputs. Supervised learning involves either a classification or regression problem. A classification problem has discrete output variables producing qualitative outputs, whereas a regression problem has continuous output variables producing quantitative outputs [93];
- Unsupervised learning—Unsupervised learning develops knowledge by choosing a cluster of related items from the provided input data set (no supervision is required). It does not train using a labeled data set [94];
- Semi-supervised learning—In this method of learning, both labeled and unlabeled datasets are used to train the machine learning model [95];
- Integration of supervised with supervised, unsupervised, or semi-supervised learning approaches—In this integrated method, at least two machine learning models are used to complete a specific job [96];
- Reinforcement learning—With reinforcement learning, an agent in a given state acts to maximize potential rewards from the surrounding environment in the future [97].
| Task | Learning Class | Learning Technique | Special Purpose | Performance |
|---|---|---|---|---|
| Packet classification (PC) | Heuristic model | ABV algorithm | Parallelize ABV algorithm on GPU for PC [68] | 99.9 times speedup, 65 times enhancement in throughput |
| Lookup and BCAM | Packet classification using BCAM [69] | 5 times fewer CAM bits than TCAM-based scheme | ||
| Data structure RQ-RMI | Multi-field packet classification [70] | High compression factor, improvement in throughput | ||
| DDBS algorithm | Multi-tuple packet classification [71] | Throughput: Over 10 Gbps on Cavium, 135 Gbps Xilinx | ||
| Cross product, linear search | Packet classification [72] | Feasible, scalable, take less time and space | ||
| TSS assisted algorithm | Packet classification [73] | Comparable update, high classifi. performance wrt. TSS | ||
| Interval valued fuzzy logic | Classify video streams [74] | Reasonable accuracy, flexible, low computational cost | ||
| Supervised ML | Deep neural network | Packet classification [104] | More than 90% classification accuracy | |
| Decision tree | CutSplit: DT combining cutting, splitting for PC [118] | 10× memory reduction, 3× impro. of memory accesses | ||
| Decision tree | Bitcuts: Bit level cutting for PC [119] | 2× throughput, 42–59% memory accesses wrt. others | ||
| Decision tree | Hypercuts: Bit level cutting for PC [120] | 2–10 less mem., 50–500% better search time wrt. HiCuts | ||
| Support Vector machines | PC based on action/flow [129] | Less memory consumption, inferior accuracy than RF | ||
| K-nearest neighbor | packet classification [104] | Accuracy inferior to DNN | ||
| Routing | Heuristic model | Extended Dijkstra algorithm | Find shortest path between source, destination [75] | Low end-to-end latency |
| MO particle swarm optimization | Optimization based segment routing [76] | Reduce path consumption, better load balancing | ||
| Greedy flow routing algorithm | Allocate path to flows using perform. thresholds [77] | Computationally complex, flexibly provides flow requirements | ||
| Multi-path routing algorithm | Packet loss, time delay, bandwidth constrained routing [78] | 35–70% improvement in quality-of-service | ||
| QoS optimization routing algorithm | Routing satisfying video QoS requirements [79] | Low packet loss, good bandwidth utilization, high QoE | ||
| Ant colony optimization algorithm | Dynamic routing [80] | Throughput, delay better than Dijkstra | ||
| ILP maximizing energy ratio | Energy efficient routing [81] | Savings in 30% energy ratio, 14.7 W per switch, 38% link | ||
| Supervised ML | Deep neural network | Find most reliable route in a SON [45] | 90% accurate forecast in reliability prediction | |
| Deep neural network | To replace optimization models for routing [110] | Achieve quasi-optimal performance | ||
| Deep neural network | 3D two space division, forwarding for FANETs [111] | Better performance in packet delivery rate, energy-saving | ||
| Deep neural network | Hybrid stable delay and distance based routing [112,200] | High packet delivery ratio, low latency and communication cost | ||
| Deep neural network | Predicts a traffic matrix in real-time [113] | Similar perform. to heuristic routing, less execution time | ||
| Reinforcement learning (RL) | Deep RL to train GNN | Prioritize experience replay to predict opt. path [181] | Good performance compared to Q learning, shortest path routing | |
| Deep RL with DDPG | Closed loop control for automatic routing [44] | Improved throughput, reduced packet delay | ||
| Deep RL to train GNN | Routing with goal of load balancing [182] | Improved network performance | ||
| Reinforcement learning | Aid link-state info. for making routing decisions[184] | Outperform Dijkstra by stretch, throughput, packet loss, delay | ||
| Deep RL | Agent learns a routing policy by experience, reward [185] | Obtain higher rewards, transfer large files faster | ||
| MDP and Q learning | Multi-path routing for different QoS flows [187] | Good jitter, packet loss rate wrt. ECMP, SP routing | ||
| Reinforcement learning | Global load balanced routing scheme [188] | Outperform existing approaches wrt. delay, network utilization | ||
| Deep Q-learning, optimization | Generate multicast tree for installing flow rules [189] | Better bandwidth, delay, packet loss rate | ||
| Reinforcement learning | Critical flow rerouting [190] | Near-optimal performance by rerouting 10–21.3% of traffic | ||
| Deep Q-learning, optimization | Critical links weight dynamically adjusted by RL [191] | Scalable, reduces transmission delay up to 39% | ||
| Reinforcement learning | Select routing algorithm for QoS-based traffic flows [195] | Best trade off between QoS vs. QoE of a TC | ||
| Security | Heuristic model | Optimization algorithm | Traffic sampling to inspect malicious network traffic [82] | Significantly outperforms equal rate all switch sampling |
| Fuzzy logic-based algorithm | Security management, IDS [83] | More accurate results than algorithms used alone | ||
| Attack detection algorithm | Kangaroo—Flow and packet based IDS [84] | Good attack detection rate, scalable | ||
| Lion optimization | Detect DDoS attacks [85] | 96% accuracy | ||
| Fuzzy logic with InfoGain FS | Anomaly-based intrusion detection [86] | 91.1%—true-positive rate, 0.006%—false-positive rate | ||
| Evolving fuzzy system | Network anomaly detection [87] | 81%—binary classification, 80% multiclass classification accuracy | ||
| Supervised ML | Deep neural network | Network intrusion and anomaly detection [101] | Better throughput, latency, resource utilization | |
| Convolutional neural network | To detect DDoS attack [103] | High detection rate—DNS amplification, NTP, TCP-SYN | ||
| GRU–LSTM-based DNN | Flow-based anomaly detection [107] | Accuracy—87.9%, precision—99.8%, recall—99.4%, F1-score—99.2% | ||
| Decision tree | To detect DDoS attack [117] | Better performance compared to SVM and Naïve Bayes | ||
| Decision tree | Vulnerability detection using traffic classification [121]. | Good accuracy, training time, prediction speed | ||
| Support Vector Machine | Flooding-based multiclass DDoS detection [125] | 97% accuracy with fastest training, testing time | ||
| Support Vector Machine | Hierarchical flow, packet-based anomaly detect [126]. | Good detection rates, minimal extra overhead | ||
| Random forest | Detect DDoS attack [133] | High false positive rate, low accuracy wrt. SVM | ||
| Random forest | Intrusion detection system [134] | Superior performance to NN and Naive Bayes | ||
| K-nearest neighbor | Detect DDoS attacks [138] | Lower classification performance wrt. to J48 classifier | ||
| K-nearest neighbor | Detect TCP-SYN, ICMP flood attacks [140] | Highest F1-score wrt. NN, DT. Mitigate 98% attacks | ||
| K-nearest neighbor | Detect known, unknown saturation attacks [141] | For 1 min TW: precision: 96%, recall: 95%, F1 score: 95% | ||
| K-nearest neighbor | Classify devices and detect DDoS attacks [144] | Accuracy 97%: device classification, 98%: DDoS detection, latency: 1.18 ms | ||
| Unsupervised ML | K means clustering | Anomaly detection in smart grid KDN [148] | High accuracy (96.9%) | |
| K means clustering | Detect DDoS attacks [149] | Recall < 90%, CPU utilization—12%, Maximum packet loss rate—7.5% | ||
| Isolation forest | Classify traffic anomalies in a NFV environment [151]. | TPR—0.8708, FPR—0.0258 | ||
| Isolation forest | Detect network security threats [152] | High accuracy, detection rate, low computational complexity | ||
| Isolation forest | Malware detection supported by a whitelist [153] | TPR—0.9998, FPR—0.0325 | ||
| Semi-supervised ML | Variational autoencoder | Abnormal traffic detection [155] | Accuracy rate of 87.27% | |
| Variational autoencoder | Detect DoS and DDoS attacks [156] | Benign traffic—97%, Malicious traffic—93% accurate | ||
| Generative adversarial networks | Synthesize and train to detect attacks [160] | 0.51 detection rate after 95 epochs | ||
| Generative adversarial networks | Adversarial training to detect DDoS attacks [161] | Accuracy—99.8%, Precision—99.8%, Recall—99.9%, F1score—99.9% | ||
| Integrated ML | KNN, Variational autoencoder | Detect known, unknown DDoS attacks [166] | Precision—0.85, Recall—0.97, F1-score—0.91 | |
| Autoencoder, 1-class SVM | Intrusion detection [167] | Detection accuracy of 97% | ||
| Conditional VAE, random forest | Attacks classification with generalized training [168] | Precision above 99%, better performance than SVM + RF | ||
| Conditional variational AE, DNN | IDS including minority and unknown attacks [169] | Accuracy of 89.08%, DR of 95.68% | ||
| AE, 1-class SVM | DDoS detection under imbalanced, unlabeled data [170] | Average accuracy of 99.35% | ||
| GAN, Reinforcement learning | Detection of attacks including adversar. attacks [171] | Average accuracy of 85.40% | ||
| GAN, DNN | Detecting DDoS attacks with adversarial training [172] | Adversarial training improves detection performance | ||
| AE, CGAN, ensemble learning | Intrusion detection [173] | Fast classification with high detection accuracy | ||
| K means, SVM | Detect and categorize traffic anomalies [175] | Accuracy of 88.7%, precision of 82.3% | ||
| K means++, fast KNN | Modular DDoS attack detection [176] | High efficiency, precision, and stability | ||
| Isolation forest, X-means | Anomaly detection [177] | Average AUC 8.1%, ADR 19.5% better than iForest, others | ||
| KNN, NB, SVM, SOM | Anomaly detection [178] | SVM-SOM: 98.1% accuracy, 97.1% DR, FPR—2.7% | ||
| Reinforcement learning | RL with DAG | Routing optimization preventing rank attacks [183] | PDR—85%, delay—1.5–2.9 s, prevent ranking attacks satisfactorily | |
| Deep reinforcement learning | QoS-aware secure routing [186] | QoS performance gains when network under attack | ||
| DDPG based DRL | Joint routing optimization and DDoS detection [193] | MA-better packet delay, jitter, packet loss, detection rate | ||
| Neural fitted Q-learning | ATMoS: Autonomous threat mitigation [192] | The model converges, can detect and mitigate actors of APTs | ||
| Reinforcement learning | Anomaly detection [194] | Detect attacks, state representation has a high storage cost | ||
| Controller Placement (CP) | Heuristic model | Evolutionary algorithm | Multi-objective controller placement [88] | Needs less memory, computation time, higher coverage |
| Heuristic optimization algorithm | Reliable fault-tolerant controller placement [89] | Computation time < 2 min, controller number, location vary on topology | ||
| Binary ILP, heuristic algorithm | Energy aware controller placement [90] | BILP is computationally complex, heuristic algorithmic solution is near optimal | ||
| Particle swarm optimization, firefly algorithm | CP considering latency, multipath connectivity [91] | Minimizes average delay during single link failure | ||
| Unsupervised ML | Optimized K-means | Partition algorithm for controller placement [146] | Maximum latency 2.437× less than standard K-means | |
| Optimized K-means | Controller placement minimizing latency [147] | Latency less than standard K-means, high availability | ||
| Traffic Classification (TC) | Supervised ML | Deep neural network | TC for energy efficiency optimization [106] | 47.71% energy consumption reduction, good load balancing |
| Decision tree | Online TC using flow-level features [122] | 97.92% accuracy, 7500+ Million Classes | ||
| DT in Hadoop platform | Big data traffic classification [123] | Faster and accurate than C4.5 decision tree | ||
| Support Vector Machines | Application-/service-wise traffic classification [128] | Classify 28 applications with 85.98% accuracy | ||
| Support Vector Machines | Traffic classification using traffic statistics [130] | Accuracy over 95%, 4% F1-score for attacks | ||
| Random forest | Internet protocol traffic classification [135] | Classification accuracy varied 73–96% for different apps | ||
| Random forest | Classify application QoS from switch statistics [136] | Prediction error less than 10% | ||
| Semi-supervised ML | Generative adversarial networks | ByteSGAN-Encrypted traffic classification [158] | Accuracy more than 90% and better than CNN | |
| Self-learning | Application-wise traffic classification [165] | 20% LD: Accuracy—60%. High recall, similar precision wrt. supervised learning | ||
| Integrated ML | Ensemble learning with RF and GB | VPN (secure) network traffic classification [179] | 93.80% accuracy, Precision—91.80%, recall—96.20%, F1-score—94% | |
| Fault/Failure diagnosis | Supervised ML | Deep neural network | Detect link failures [108] | 85% accuracy in identification of failures |
| LSTM-based DNN | Detect link handover failures in advance [109] | 99% TPR, predict a link failure before 1–2 s | ||
| K nearest neighbor | Harmful long-term load prediction [142] | Accuracy—96.2%, Precision—91.2%, F1-score—94.6% | ||
| QoS/QoE prediction | Supervised ML | GRU-DNN | Temporal-aware service QoS prediction [114] | Superior accuracy wrt. other approaches |
| DNN | Multiple attributes QoS prediction [115] | Low mean absolute error wrt. other approaches | ||
| K nearest neighbor | Predict QoE in video data [143] | k = 1, Pearson Correlation Coefficient—0.75, long testing time | ||
| Semi-supervised ML | Laplacian SVM | Classifies network traffic based on QoS requirements [163]. | Accuracy exceeds 90% and better than K-means | |
| WL handover | Supervised ML | K nearest neighbor | Adaptive cell selection for mm Wave HetNets [139] | Better handovers—45.83%, throughput—17.2%, EE—16.7% |
| Network slicing | Semi-super. ML | Conditional Generative adversarial networks | CGAN augment data used in creating network slices [159] | Accuracy range in 0.40–0.65 |
3.4. Knowledge Composition Plane
3.4.1. Composed Knowledge Representation
3.4.2. Rule Generation
3.4.3. Examples Using Composed Knowledge in the Existing Literature
3.5. Knowledge Distribution and Management Plane
3.5.1. Review on Existing Work on Flow Scheduling and Prioritization to Apply Knowledge and Rule Dissemination
3.5.2. Knowledge and Rule Exchange and Management Protocols/Languages
- RETE is an algorithm used for rule evaluation and pattern matching that builds a network of nodes that represent the conditions and actions of rules, where nodes are connected in a way to allow efficient evaluation of the rules [233];
- Drools is a Java-based open-sourced rule engine that supports advanced features such as query capabilities, rule chaining (forward and backward), and rule templating, which uses RETE as the algorithm for pattern matching [234];
- VLog is a rule-based reasoner with a platform-independent Java API that supports reasoning using existential rules or knowledge represented in RDF or OWL formats [235];
- Bossam is a rule engine that can reason from OWL ontologies and also provides support for forward and backward chaining [236];
- The C Language Integrated Production System (CLIPS) is a rule-based programming language. The CLIPS rule engine can handle large rule sets and can evaluate rules using a forward chaining algorithm to derive conclusions [237];
- Jess is a rule engine for the Java platform that infers conclusions/decisions from rules, similar to other rule engines [238].
- SPARQL Protocol and RDF Query Language (SPARQL) is a query language for RDF to query knowledge models that appear in the form of RDF format. As generated knowledge can be modeled using RDF and ontologies derived from such knowledge are based on OWL, which is based on RDF, SPARQL can be used to query knowledge contained in those forms. SPARQL further has an update language extension, which includes commands such as insert, delete, and update for modifying RDF-based knowledge [239];
- SQWRL is an extension of SWRL (Semantic Web Rule Language) that adds support for querying OWL ontologies. SQWRL allows users to query OWL ontologies using a combination of SWRL rules and OWL axioms. SQWRL also supports complex queries that combine multiple conditions using logical operators such as AND and OR. However, SQWRL is designed specifically for querying OWL ontologies and does not provide any opportunity to modify ontologies [240];
- Knowledge Graph Query Language (KGQL) is a query language specifically designed for querying knowledge graphs that allows users to write complex queries over knowledge graphs using a simple and instinctive syntax. KGQL supports pattern matching, filtering, sorting, aggregation, path traversal, etc. KGQL also does not support knowledge modification; thus, it is a read-only query language [241];
- Knowledge Query and Manipulation Language (KQML) is a message-passing protocol that allows agents to exchange knowledge and perform tasks in a distributed AI system, regardless of their underlying implementation. In KQML, a simple text-based syntax is used to represent different message types such as queries, assertions, and requests for action that can be exchanged using KQML. KQML is supposed to exchange knowledge and does not explicitly support knowledge modification [242];
- GraphQL is another language that can be used to not only retrieve knowledge from knowledge graphs, but also modify knowledge using insert, update, and delete operations. Similar to other query languages used to retrieve knowledge, GraphQL also allows the agents/developer to specify the knowledge in the form of a knowledge graph that needs to be retrieved, allowing fast and efficient data retrieval [243].
4. Management Plane
4.1. Introduction to Management Plane
4.2. Architecture of the Management Plane
4.3. Network Management Protocols/Interfaces
4.4. Network Monitoring Frameworks
4.5. Network Data Collection
4.5.1. Data Collection Methods (DCMs)
4.5.2. Types of Data
4.5.3. Data Representation Models
5. Control Plane
5.1. Introduction to Control Plane
5.2. Interfaces and Sub-Planes Connected with the Controller
5.2.1. Northbound Interface
5.2.2. Southbound Interface
5.2.3. East- and Westbound Interfaces
5.2.4. Management API
5.2.5. Network Hypervisors
5.2.6. Network Operating System
5.3. Control Models
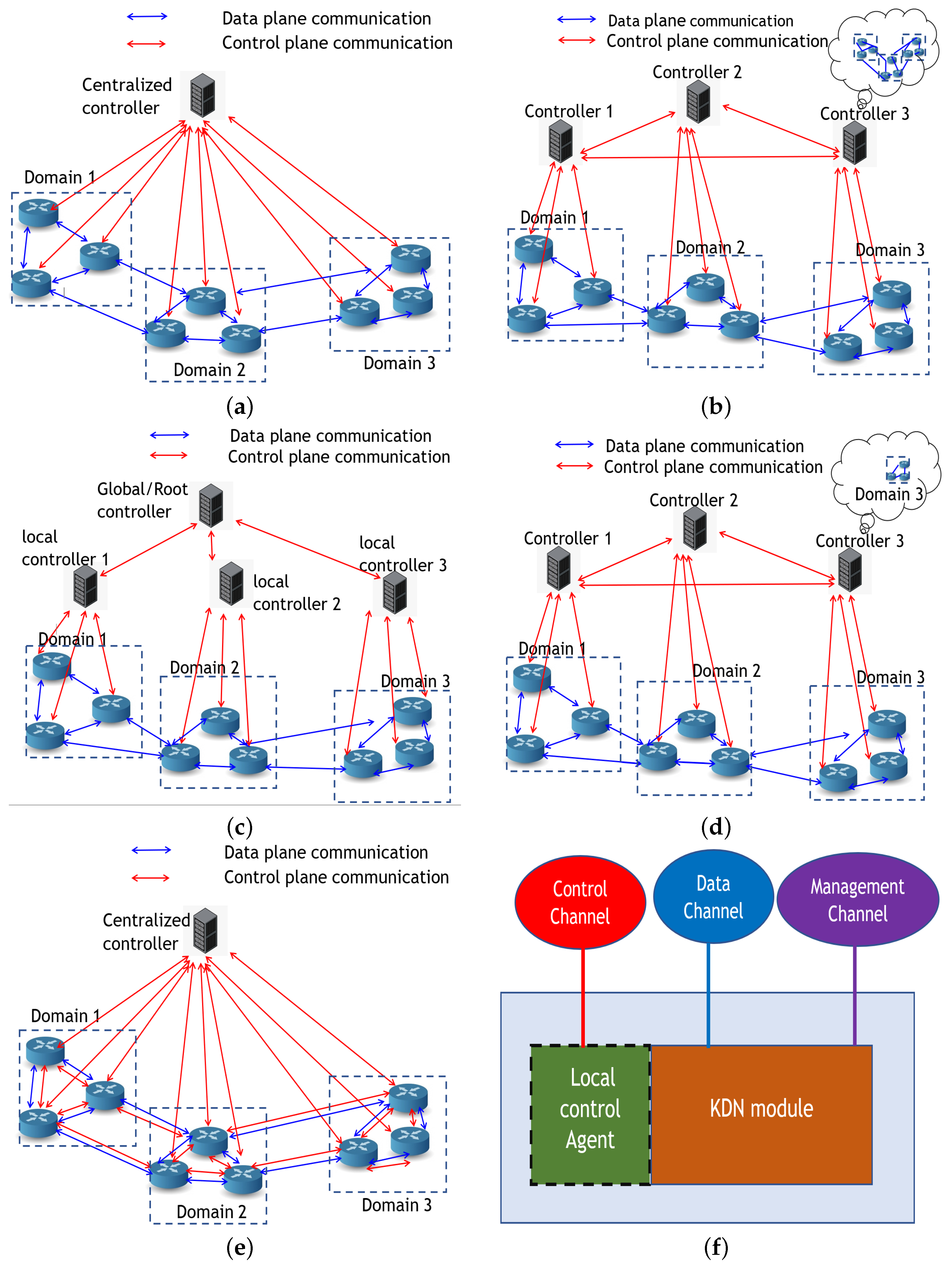
5.3.1. Centralized vs. Distributed vs. Hybrid Control
- Logically and physically centralized control model;
- Logically centralized and physically distributed with flat control model;
- Logically centralized and physically distributed with hierarchical control model;
- Logically and physically distributed control model;
- Hybrid control model.
5.3.2. Packet vs. Flow Control
5.3.3. Reactive vs. Proactive Control
5.3.4. Fully Consistent vs. Eventually Consistent Control
5.4. Controller Functions
5.4.1. Data Collection
5.4.2. Path Computation
5.4.3. Policy Enforcement
5.4.4. Traffic Engineering
5.4.5. Network Virtualization
5.4.6. Service Chaining
6. Data Plane
6.1. Introduction to Data Plane
6.2. Forwarding Devices
6.2.1. Architecture of a Forwarding Device
6.2.2. Physical Switches
6.2.3. Virtual Switches
6.2.4. Optical Switches
6.2.5. Wireless Access Points, Base-Stations, and Vehicles
6.3. Transmission Media
6.3.1. Wired Media
6.3.2. Optical Media
6.3.3. Wireless Media
7. Application Plane
7.1. Introduction to Application Plane
7.2. Architecture of the Application Plane
7.3. Application Scenarios
7.3.1. Traffic Engineering
- Static load-balancing: Static load-balancing refers to distributing network traffic using multiple paths using fixed rules or policies, such as routing network traffic using source or destination IP addresses, based on the type of application used, etc. However, this approach is not the ideal approach for load-balancing, as the traffic load in a real network scenario can be highly dynamic and fluctuating [445]. This approach is totally application-based, where the load-balancing is determined by high-level application policies;
- Dynamic load-balancing: Dynamic load-balancing adjusts the load-balancing rules based on real-time network conditions without any influence from any high-level policies. Dynamic load-balancing algorithms can use various metrics such as packet loss, latency, and throughput to decide on how to distribute traffic on multiple paths. For example, in [446], an algorithm for finding alternative best paths that have minimum link cost and low traffic flow is found when network congestion occurs on a certain path. Even though dynamic load-balancing may achieve better performance compared to static load-balancing, load-balancing entirely relying on real-time data may be problematic in some instances. For instance, if, for some data, the machine learning model predicts an erroneous output, then it can affect the load-balancing process negatively. However, if application policies were also involved, the effect of the erroneous knowledge could be reduced to some extent;
- Adaptive load-balancing: Adaptive load-balancing is the best approach suitable to be deployed in knowledge-defined networks, as it combines both static and dynamic load-balancing techniques to achieve optimum load distribution by considering present network status and application policies. For instance, in [447], the load status and dynamic weight of each controller are considered along with pre-defined load thresholds to adaptively achieve load-balancing. Some have used machine learning to predict link state and then used the predictions as weights to calculate the optimum path between network hosts [448]. A mechanism for load-balancing for distributed controllers that monitors the imbalance state of the entire network and uses resource consumption metrics for load-balancing to reduce communication among controllers is presented in [449]. The service-oriented load-balancing concept is a type of adaptive load-balancing scheme. In [450], data are collected in a cloud environment to measure the delay of packets, which are used to spread the workload equitably by comparing it with the round-robin scheduling policy of the applications. An application is used to classify services, and load is balanced with the objective of maximizing resource utilization and minimizing the response time of users, which is an adaptive load-balancing approach [451].
7.3.2. Network Management
7.3.3. Security
7.3.4. Network Virtualization
7.3.5. Big Data
7.3.6. Cloud Computing
7.3.7. Data Center Networking
7.3.8. Business Applications
7.3.9. Configuration
8. Discussion
8.1. Benefits
8.1.1. Enhanced Automation and Intelligence
8.1.2. Higher Adaptability
8.1.3. Reduced Downtime
8.1.4. Improved Security
8.1.5. Simplified Network Management
8.1.6. Better Network Performance
8.1.7. Enhanced User Experience
8.1.8. Improved Network Visibility
8.2. Challenges
8.2.1. Data
8.2.2. Integration with Legacy Systems
8.2.3. Privacy
8.2.4. Interoperability
8.2.5. Scalability
8.2.6. Reliability
8.2.7. Consistency
8.2.8. Implementation and Maintenance Cost
8.2.9. Lack of Transparency
8.2.10. Additional Resources
8.3. Design Guidelines
8.3.1. Switch Design
8.3.2. Data Collection
8.3.3. Management Plane Design
8.3.4. Control Plane Design
8.3.5. Knowledge Plane Design
8.3.6. Application Plane Design
8.3.7. Different Network Scenarios
8.4. Ongoing Research
9. Conclusions, Recommendations, and Future Research
- Attention from experts is recommended to make sure KDN systems collect large quantities of high-quality data in terms of relevancy, completeness, unbiasedness, consistency, and non-outdatedness;
- In instances where legacy systems cannot be directly converted to pure KDN, a hybrid KDN approach that implements a blend of legacy and pure KDN is recommended;
- In order to secure data, knowledge, and machine learning models, robust data protection techniques such as access control, encryption, and intrusion detection systems should be used. Furthermore, for secure data, knowledge, and model sharing, KDN systems can integrate distributed secure blockchain technology;
- It is recommended to implement interoperable APIs to improve the interoperability of KDN systems that may use different standards to implement the KDN;
- Distributed knowledge generation (federated learning) and dissemination are recommended to improve the scalability of KDN systems;
- In order to improve the reliability of KDN systems, the machine learning models are recommended to be trained using high-quality data and tested thoroughly, evaluating performance evaluation metrics such as accuracy, error, F1-score, etc., before deployment in the network;
- Explainable machine learning is recommended to make sure that the ML models are accountable and explainable for the decisions they make and to aid in identifying the root causes of issues when such models make errors;
- Transfer learning and active learning are recommended to fine-tune the machine learning models’ training.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Haji, S.H.; Zeebaree, S.R.; Saeed, R.H.; Ameen, S.Y.; Shukur, H.M.; Omar, N.; Sadeeq, M.A.; Ageed, Z.S.; Ibrahim, I.M.; Yasin, H.M. Comparison of software defined networking with traditional networking. Asian J. Res. Comput. Sci. 2021, 9, 1–18. [Google Scholar] [CrossRef]
- Mishra, S.; AlShehri, M.A.R. Software defined networking: Research issues, challenges and opportunities. Indian J. Sci. Technol. 2017, 10, 1–9. [Google Scholar] [CrossRef]
- Bhatia, J.; Modi, Y.; Tanwar, S.; Bhavsar, M. Software defined vehicular networks: A comprehensive review. Int. J. Commun. Syst. 2019, 32, e4005. [Google Scholar] [CrossRef]
- Zhu, M.; Cai, Z.P.; Xu, M.; Cao, J.N. Software-defined vehicular networks: Opportunities and challenges. In Energy Science and Applied Technology; CRC Press: Boca Raton, FL, USA, 2015; pp. 247–251. [Google Scholar]
- Nunes, B.A.A.; Mendonca, M.; Nguyen, X.N.; Obraczka, K.; Turletti, T. A survey of software-defined networking: Past, present, and future of programmable networks. IEEE Commun. Surv. Tutor. 2014, 16, 1617–1634. [Google Scholar] [CrossRef] [Green Version]
- Fonseca, P.C.; Mota, E.S. A survey on fault management in software-defined networks. IEEE Commun. Surv. Tutor. 2017, 19, 2284–2321. [Google Scholar] [CrossRef]
- Akhunzada, A.; Khan, M.K. Toward secure software defined vehicular networks: Taxonomy, requirements, and open issues. IEEE Commun. Mag. 2017, 55, 110–118. [Google Scholar] [CrossRef]
- Zhao, L.; Li, J.; Al-Dubai, A.; Zomaya, A.Y.; Min, G.; Hawbani, A. Routing schemes in software-defined vehicular networks: Design, open issues and challenges. IEEE Intell. Transp. Syst. Mag. 2020, 13, 217–226. [Google Scholar] [CrossRef] [Green Version]
- Quan, W.; Cheng, N.; Qin, M.; Zhang, H.; Chan, H.A.; Shen, X. Adaptive transmission control for software defined vehicular networks. IEEE Wirel. Commun. Lett. 2018, 8, 653–656. [Google Scholar] [CrossRef]
- Nisar, K.; Jimson, E.R.; Hijazi, M.H.A.; Welch, I.; Hassan, R.; Aman, A.H.M.; Sodhro, A.H.; Pirbhulal, S.; Khan, S. A survey on the architecture, application, and security of software defined networking: Challenges and open issues. Internet Things 2020, 12, 100289. [Google Scholar] [CrossRef]
- Islam, M.M.; Khan, M.T.R.; Saad, M.M.; Kim, D. Software-defined vehicular network (SDVN): A survey on architecture and routing. J. Syst. Archit. 2021, 114, 101961. [Google Scholar] [CrossRef]
- Adbeb, T.; Wu, D.; Ibrar, M. Software-defined networking (SDN) based VANET architecture: Mitigation of traffic congestion. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 706–714. [Google Scholar] [CrossRef] [Green Version]
- Liu, K.; Xu, X.; Chen, M.; Liu, B.; Wu, L.; Lee, V.C. A hierarchical architecture for the future internet of vehicles. IEEE Commun. Mag. 2019, 57, 41–47. [Google Scholar] [CrossRef]
- Toufga, S.; Abdellatif, S.; Assouane, H.T.; Owezarski, P.; Villemur, T. Towards dynamic controller placement in software defined vehicular networks. Sensors 2020, 20, 1701. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Fontes, R.D.R.; Campolo, C.; Rothenberg, C.E.; Molinaro, A. From theory to experimental evaluation: Resource management in software-defined vehicular networks. IEEE Access 2017, 5, 3069–3076. [Google Scholar] [CrossRef]
- Wang, K.; Yin, H.; Quan, W.; Min, G. Enabling collaborative edge computing for software defined vehicular networks. IEEE Netw. 2018, 32, 112–117. [Google Scholar] [CrossRef]
- Shah, S.A.A.; Ahmed, E.; Imran, M.; Zeadally, S. 5G for vehicular communications. IEEE Commun. Mag. 2018, 56, 111–117. [Google Scholar] [CrossRef]
- Cardona, N.; Coronado, E.; Latré, S.; Riggio, R.; Marquez-Barja, J.M. Software-defined vehicular networking: Opportunities and challenges. IEEE Access 2020, 8, 219971–219995. [Google Scholar] [CrossRef]
- Deveaux, D.; Higuchi, T.; Uçar, S.; Härri, J.; Altintas, O. A definition and framework for vehicular knowledge networking: An application of knowledge-centric networking. IEEE Veh. Technol. Mag. 2021, 16, 57–67. [Google Scholar] [CrossRef]
- Ucar, S.; Higuchi, T.; Wang, C.H.; Deveaux, D.; Härri, J.; Altintas, O. Vehicular knowledge networking and application to risk reasoning. In Proceedings of the Twenty-First International Symposium on Theory, Algorithmic Foundations, and Protocol Design for Mobile Networks and Mobile Computing, Virtual Event, 11–14 October 2020; pp. 351–356. [Google Scholar]
- Ucar, S.; Higuchi, T.; Wang, C.H.; Deveaux, D.; Altintas, O.; Härri, J. Vehicular Knowledge Networking and Mobility-Aware Smart Knowledge Placement. In Proceedings of the 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2022; pp. 593–598. [Google Scholar]
- Ruta, M.; Scioscia, F.; Gramegna, F.; Ieva, S.; Di Sciascio, E.; De Vera, R.P. A knowledge fusion approach for context awareness in vehicular networks. IEEE Internet Things J. 2018, 5, 2407–2419. [Google Scholar] [CrossRef]
- Khan, M.I.; Aubet, F.X.; Pahl, M.O.; Härri, J. Deep learning-aided resource orchestration for vehicular safety communication. In Proceedings of the 2019 Wireless Days (WD), Manchester, UK, 24–26 April 2019; pp. 1–8. [Google Scholar]
- Wijesekara, P.A.D.S.N. Deep 3D Dynamic Object Detection towards Successful and Safe Navigation for Full Autonomous Driving. Open Transp. J. 2022, 16, e187444782208191. [Google Scholar] [CrossRef]
- Wu, D.; Li, Z.; Wang, J.; Zheng, Y.; Li, M.; Huang, Q. Vision and challenges for knowledge centric networking. IEEE Wirel. Commun. 2019, 6, 117–123. [Google Scholar] [CrossRef]
- Liu, J.; Xu, Q. Machine learning in software defined network. In Proceedings of the 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019; pp. 1114–1120. [Google Scholar]
- Clark, D.D.; Partridge, C.; Ramming, J.C.; Wroclawski, J.T. A knowledge plane for the internet. In Proceedings of the 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Las Vegas, NV, USA, 25–29 August 2003; pp. 3–10. [Google Scholar]
- Mestres, A.; Rodriguez-Natal, A.; Carner, J.; Barlet-Ros, P.; Alarcón, E.; Solé, M.; Muntés-Mulero, V.; Meyer, D.; Barkai, S.; Hibbett, M.J.; et al. Knowledge-defined networking. ACM SIGCOMM Comput. Commun. Rev. 2017, 47, 2–10. [Google Scholar] [CrossRef] [Green Version]
- Yao, H.; Mai, T.; Xu, X.; Zhang, P.; Li, M.; Liu, Y. NetworkAI: An intelligent network architecture for self-learning control strategies in software defined networks. IEEE Internet Things J. 2018, 5, 4319–4327. [Google Scholar] [CrossRef] [Green Version]
- Alzahrani, A.O.; Alenazi, M.J. Designing a network intrusion detection system based on machine learning for software defined networks. Future Internet 2021, 13, 111. [Google Scholar] [CrossRef]
- Polat, H.; Polat, O.; Cetin, A. Detecting DDoS attacks in software-defined networks through feature selection methods and machine learning models. Sustainability 2020, 12, 1035. [Google Scholar] [CrossRef] [Green Version]
- Dey, S.K.; Rahman, M.M. Effects of machine learning approach in flow-based anomaly detection on software-defined networking. Symmetry 2019, 12, 7. [Google Scholar] [CrossRef] [Green Version]
- Vulpe, A.; Girla, I.; Craciunescu, R.; Berceanu, M.G. Machine learning based software-defined networking traffic classification system. In Proceedings of the 2021 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Bucharest, Romania, 24–28 May 2021; pp. 1–5. [Google Scholar]
- Lim, H.K.; Kim, J.B.; Kim, K.; Hong, Y.G.; Han, Y.H. Payload-based traffic classification using multi-layer lstm in software defined networks. Appl. Sci. 2019, 9, 2550. [Google Scholar] [CrossRef] [Green Version]
- Bao, K.; Matyjas, J.D.; Hu, F.; Kumar, S. Intelligent software-defined mesh networks with link-failure adaptive traffic balancing. IEEE Trans. Cogn. Commun. Netw. 2018, 4, 266–276. [Google Scholar] [CrossRef]
- Awad, M.K.; Ahmed, M.H.H.; Almutairi, A.F.; Ahmad, I. Machine learning-based multipath routing for software defined networks. J. Netw. Syst. Manag. 2021, 29, 18. [Google Scholar] [CrossRef]
- Toufga, S.; Abdellatif, S.; Owezarski, P.; Villemur, T.; Relizani, D. Effective prediction of V2I link lifetime and vehicle’s next cell for software defined vehicular networks: A machine learning approach. In Proceedings of the 2019 IEEE Vehicular Networking Conference (VNC), Los Angeles, CA, USA, 4–6 December 2019; pp. 1–8. [Google Scholar]
- Amari, H.; Louati, W.; Khoukhi, L.; Belguith, L.H. Securing software-defined vehicular network architecture against ddos attack. In Proceedings of the 2021 IEEE 46th Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 4–7 October 2021; pp. 653–656. [Google Scholar]
- Zhang, D.; Yu, F.R.; Yang, R. A machine learning approach for software-defined vehicular ad hoc networks with trust management. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Latah, M.; Toker, L. Artificial intelligence enabled software-defined networking: A comprehensive overview. IET Netw. 2019, 8, 79–99. [Google Scholar] [CrossRef] [Green Version]
- Kaloxylos, A.; Gavras, A.; Camps, D.; Ghoraishi, M.; Hrasnica, H. AI and ML—Enablers for beyond 5G Networks; Zenodo: Geneve, Switzerland, 2021. [Google Scholar]
- Lu, W.; Liang, L.; Kong, B.; Li, B.; Zhu, Z. AI-assisted knowledge-defined network orchestration for energy-efficient data center networks. IEEE Commun. Mag. 2020, 58, 86–92. [Google Scholar] [CrossRef]
- Hyun, J.; Van Tu, N.; Hong, J.W.K. Towards knowledge-defined networking using in-band network telemetry. In Proceedings of the NOMS 2018–2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018; pp. 1–7. [Google Scholar]
- Hu, Y.; Li, Z.; Lan, J.; Wu, J.; Yao, L. EARS: Intelligence-driven experiential network architecture for automatic routing in software-defined networking. China Commun. 2020, 17, 149–162. [Google Scholar] [CrossRef]
- Gosh, S.; El Boudani, B.; Dagiuklas, T.; Iqbal, M. SO-KDN: A Self-Organised Knowledge Defined Networks Architecture for Reliable Routing. In Proceedings of the 4th International Conference on Information Science and Systems, Edinburgh, UK, 17–19 March 2021; pp. 160–166. [Google Scholar]
- Rafiq, A.; Rehman, S.; Young, R.; Song, W.C.; Khan, M.A.; Kadry, S.; Srivastava, G. Knowledge defined networks on the edge for service function chaining and reactive traffic steering. Clust. Comput. 2023, 26, 613–634. [Google Scholar] [CrossRef]
- Duque-Torres, A.; Amezquita-Suárez, F.; Caicedo Rendon, O.M.; Ordóñez, A.; Campo, W.Y. An approach based on knowledge-defined networking for identifying heavy-hitter flows in data center networks. Appl. Sci. 2019, 9, 4808. [Google Scholar] [CrossRef] [Green Version]
- Herrera, L.M.C.; Torres, A.D.; Munoz, W.Y.C. An approach based on knowledge-defined networking for identifying video streaming flows in 5G networks. IEEE Latin Am. Trans. 2021, 19, 1737–1744. [Google Scholar] [CrossRef]
- Li, Y.; Su, X.; Ding, A.Y.; Lindgren, A.; Liu, X.; Prehofer, C.; Riekki, J.; Rahmani, R.; Tarkoma, S.; Hui, P. Enhancing the internet of things with knowledge-driven software-defined networking technology: Future perspectives. Sensors 2020, 20, 3459. [Google Scholar] [CrossRef]
- Kreutz, D.; Ramos, F.M.; Verissimo, P.E.; Rothenberg, C.E.; Azodolmolky, S.; Uhlig, S. Software-defined networking: A comprehensive survey. Proc. IEEE 2014, 103, 14–76. [Google Scholar] [CrossRef]
- Zhao, Y.; Li, Y.; Zhang, X.; Geng, G.; Zhang, W.; Sun, Y. A survey of networking applications applying the software defined networking concept based on machine learning. IEEE Access 2019, 7, 95397–95417. [Google Scholar] [CrossRef]
- Xie, J.; Yu, F.R.; Huang, T.; Xie, R.; Liu, J.; Wang, C.; Liu, Y. A survey of machine learning techniques applied to software defined networking (SDN): Research issues and challenges. IEEE Commun. Surv. Tutor. 2018, 21, 393–430. [Google Scholar] [CrossRef]
- Faezi, S.; Shirmarz, A. A Comprehensive Survey on Machine Learning using in Software Defined Networks (SDN). Hum.-Centric Intell. Syst. 2023, 1–32. [Google Scholar] [CrossRef]
- Ashtari, S.; Zhou, I.; Abolhasan, M.; Shariati, N.; Lipman, J.; Ni, W. Knowledge-defined networking: Applications, challenges and future work. Array 2022, 14, 100136. [Google Scholar] [CrossRef]
- Safwat, M.; Elgammal, A.; AbdAllah, E.G.; Azer, M.A. Survey and taxonomy of information-centric vehicular networking security attacks. Ad Hoc Netw. 2022, 124, 102696. [Google Scholar] [CrossRef]
- Zins, C. Conceptual approaches for defining data, information, and knowledge. J. Am. Soc. Inf. Sci. Technol. 2007, 58, 479–493. [Google Scholar] [CrossRef]
- Trammell, B.; Casas, P.; Rossi, D.; Bär, A.; Houidi, Z.B.; Leontiadis, I.; Szemethy, T.; Mellia, M. mPlane: An intelligent measurement plane for the internet. IEEE Commun. Mag. 2014, 52, 148–156. [Google Scholar] [CrossRef] [Green Version]
- Sieber, C.; Blenk, A.; Basta, A.; Hock, D.; Kellerer, W. Towards a programmable management plane for SDN and legacy networks. In Proceedings of the 2016 IEEE NetSoft Conference and Workshops (NetSoft), Seoul, Republic of Korea, 6–10 June 2016; pp. 319–327. [Google Scholar]
- Atutxa, A.; Franco, D.; Sasiain, J.; Astorga, J.; Jacob, E. Achieving low latency communications in smart industrial networks with programmable data planes. Sensors 2021, 21, 5199. [Google Scholar] [CrossRef]
- Hasan, K.; Ahmed, K.; Biswas, K.; Islam, M.S.; Kayes, A.S.M.; Islam, S.R. Control plane optimisation for an SDN-based WBAN framework to support healthcare applications. Sensors 2020, 20, 4200. [Google Scholar] [CrossRef]
- Ahvar, E.; Ahvar, S.; Raza, S.M.; Manuel Sanchez Vilchez, J.; Lee, G.M. Next generation of SDN in cloud-fog for 5G and beyond-enabled applications: Opportunities and challenges. Network 2021, 1, 28–49. [Google Scholar] [CrossRef]
- Lewis, D.; Keeney, J.; O’Sullivan, D.; Guo, S. Towards a managed extensible control plane for knowledge-based networking. In Large Scale Management of Distributed Systems: 17th IFIP/IEEE International Workshop on Distributed Systems: Operations and Management, DSOM, Dublin, Ireland, 23–25 October 2006; Proceedings 17; Springer: Berlin/Heidelberg, Germany, 2006; pp. 98–111. [Google Scholar]
- Keeney, J.; Lewis, D.; O’Sullivan, D. Ontological semantics for distributing contextual knowledge in highly distributed autonomic systems. J. Netw. Syst. Manag. 2007, 15, 75–86. [Google Scholar] [CrossRef]
- Jevsikova, T.; Berniukevičius, A.; Kurilovas, E. Application of resource description framework to personalise learning: Systematic review and methodology. Inf. Educ. 2017, 16, 61–82. [Google Scholar]
- Wijesekara, P.A.D.S.N.; Wang, Y.K. A Mathematical Epidemiological Model (SEQIJRDS) to Recommend Public Health Interventions Related to COVID-19 in Sri Lanka. COVID 2022, 2, 793–826. [Google Scholar] [CrossRef]
- Wijesekara, P.A.D.S.N. A study in University of Ruhuna for investigating prevalence, risk factors and remedies for psychiatric illnesses among students. Sci. Rep. 2022, 12, 12763. [Google Scholar] [CrossRef]
- Seneviratne, C.; Wijesekara, P.A.D.S.N.; Leung, H. Performance analysis of distributed estimation for data fusion using a statistical approach in smart grid noisy wireless sensor networks. Sensors 2020, 20, 567. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Abbasi, M.; Tahouri, R.; Rafiee, M. Enhancing the performance of the aggregated bit vector algorithm in network packet classification using GPU. PeerJ Comput. Sci. 2019, 5, e185. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Liu, A.X.; Meiners, C.R.; Torng, E. Packet classification using binary content addressable memory. IEEE/ACM Trans. Netw. 2016, 24, 1295–1307. [Google Scholar] [CrossRef] [Green Version]
- Rashelbach, A.; Rottenstreich, O.; Silberstein, M. A computational approach to packet classification. In Proceedings of the Annual conference of the ACM Special Interest Group on Data Communication on the Applications, Technologies, Architectures, and Protocols for Computer Communication, Virtual Event, 10–14 August 2020; pp. 542–556. [Google Scholar]
- Yang, B.; Fong, J.; Jiang, W.; Xue, Y.; Li, J. Practical multituple packet classification using dynamic discrete bit selection. IEEE Trans. Comput. 2012, 63, 424–434. [Google Scholar] [CrossRef]
- Wang, P.C. Scalable packet classification with controlled cross-producting. Comput. Netw. 2009, 53, 821–834. [Google Scholar] [CrossRef]
- Li, W.; Yang, T.; Rottenstreich, O.; Li, X.; Xie, G.; Li, H.; Vamanan, B.; Li, D.; Lin, H. Tuple space assisted packet classification with high performance on both search and update. IEEE J. Sel. Areas Commun. 2020, 38, 1555–1569. [Google Scholar] [CrossRef]
- Monks, E.M.; de Moura, B.M.P.; Schneider, G.B.; Santos, H.S.; Yamin, A.C.; Reiser, R.H.S. Towards Interval-Valued Fuzzy Approach to Video Streaming Traffic Classification. In Proceedings of the 2022 IEEE International Conference on Fuzzy Systems (FUZZ-IEEE), Padua, Italy, 18–23 July 2022; pp. 1–8. [Google Scholar]
- Jiang, J.R.; Huang, H.W.; Liao, J.H.; Chen, S.Y. Extending Dijkstra’s shortest path algorithm for software defined networking. In Proceedings of the 16th Asia-Pacific Network Operations and Management Symposium, Hsinchu, Taiwan, 17–19 September 2014; pp. 1–4. [Google Scholar]
- Hou, X.; Wu, M.; Zhao, M. An optimization routing algorithm based on segment routing in software-defined networks. Sensors 2018, 19, 49. [Google Scholar] [CrossRef] [Green Version]
- Shirmarz, A.; Ghaffari, A. An adaptive greedy flow routing algorithm for performance improvement in software-defined network. Int. J. Numer. Modell. Electron. Netw. Devices Fields 2020, 33, e2676. [Google Scholar] [CrossRef]
- Wu, J.; Qiao, X.; Nan, G. Dynamic and adaptive multi-path routing algorithm based on software-defined network. Int. J. Distrib. Sens. Netw. 2018, 14, 1550147718805689. [Google Scholar]
- Elbasheer, M.O.; Aldegheishem, A.; Lloret, J.; Alrajeh, N. A QoS-Based routing algorithm over software defined networks. J. Netw. Comput. Appl. 2021, 194, 103215. [Google Scholar] [CrossRef]
- Shreya, T.; Mulla, M.M.; Shinde, S.; Narayan, D.G. Ant colony Optimization-based dynamic routing in Software defined networks. In Proceedings of the 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kharagpur, India, 1–3 July 2020; pp. 1–7. [Google Scholar]
- Assefa, B.G.; Özkasap, Ö. RESDN: A novel metric and method for energy efficient routing in software defined networks. IEEE Trans. Netw. Serv. Manag. 2020, 17, 736–749. [Google Scholar] [CrossRef] [Green Version]
- Ha, T.; Kim, S.; An, N.; Narantuya, J.; Jeong, C.; Kim, J.; Lim, H. Suspicious traffic sampling for intrusion detection in software-defined networks. Comput. Netw. 2016, 109, 172–182. [Google Scholar] [CrossRef]
- Dotcenko, S.; Vladyko, A.; Letenko, I. A fuzzy logic-based information security management for software-defined networks. In Proceedings of the 16th International Conference on Advanced Communication Technology, Pyeong Chang, Republic of Korea, 14–19 February 2014; pp. 167–171. [Google Scholar]
- Yazdinejadna, A.; Parizi, R.M.; Dehghantanha, A.; Khan, M.S. A kangaroo-based intrusion detection system on software-defined networks. Comput. Netw. 2021, 184, 107688. [Google Scholar] [CrossRef]
- Arivudainambi, D.; K.A., V.K.; Sibi Chakkaravarthy, S. LION IDS: A meta-heuristics approach to detect DDoS attacks against Software-Defined Networks. Neural Comput. Appl. 2019, 31, 1491–1501. [Google Scholar] [CrossRef]
- Almseidin, M.; Al-Sawwa, J.; Alkasassbeh, M. Anomaly-based intrusion detection system using fuzzy logic. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; pp. 290–295. [Google Scholar]
- Abdullah, S.A.; Al-Hashmi, A.S. TiSEFE: Time series evolving fuzzy engine for network traffic classification. Int. J. Commun. Netw. Inf. Secur. 2018, 10, 116–124. [Google Scholar] [CrossRef]
- Ahmadi, V.; Khorramizadeh, M. An adaptive heuristic for multi-objective controller placement in software-defined networks. Comput. Electr. Eng. 2018, 66, 204–228. [Google Scholar] [CrossRef]
- Ros, F.J.; Ruiz, P.M. On reliable controller placements in software-defined networks. Comput. Commun. 2016, 77, 41–51. [Google Scholar] [CrossRef]
- Hu, Y.; Luo, T.; Beaulieu, N.C.; Deng, C. The energy-aware controller placement problem in software defined networks. IEEE Commun. Lett. 2016, 21, 741–744. [Google Scholar] [CrossRef]
- Sahoo, K.S.; Puthal, D.; Obaidat, M.S.; Sarkar, A.; Mishra, S.K.; Sahoo, B. On the placement of controllers in software-defined-WAN using meta-heuristic approach. J. Syst. Softw. 2018, 145, 180–194. [Google Scholar] [CrossRef]
- Zelaya, C.V.G. Towards explaining the effects of data preprocessing on machine learning. In Proceedings of the 2019 IEEE 35th International Conference on Data Engineering (ICDE), Macao, 8–11 April 2019; pp. 2086–2090. [Google Scholar]
- Ahmad, A.; Ostrowski, K.A.; Maślak, M.; Farooq, F.; Mehmood, I.; Nafees, A. Comparative study of supervised machine learning algorithms for predicting the compressive strength of concrete at high temperature. Materials 2021, 14, 4222. [Google Scholar] [CrossRef] [PubMed]
- Ceriotti, M. Unsupervised machine learning in atomistic simulations, between predictions and understanding. J. Chem. Phys. 2019, 150, 150901. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Van Engelen, J.E.; Hoos, H.H. A survey on semi-supervised learning. Mach. Learn. 2020, 109, 373–440. [Google Scholar] [CrossRef] [Green Version]
- Comar, P.M.; Liu, L.; Saha, S.; Tan, P.N.; Nucci, A. Combining supervised and unsupervised learning for zero-day malware detection. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 2022–2030. [Google Scholar]
- Nian, R.; Liu, J.; Huang, B. A review on reinforcement learning: Introduction and applications in industrial process control. Comput. Chem. Eng. 2020, 139, 106886. [Google Scholar] [CrossRef]
- Herath, H.M.D.P.M.; Weraniyagoda, W.A.S.A.; Rajapaksha, R.T.M.; Wijesekara, P.A.D.S.N.; Sudheera, K.L.K.; Chong, P.H.J. Automatic Assessment of Aphasic Speech Sensed by Audio Sensors for Classification into Aphasia Severity Levels to Recommend Speech Therapies. Sensors 2022, 22, 6966. [Google Scholar] [CrossRef] [PubMed]
- Wijesekara, P.A.D.S.N.; Gunawardena, S. A Review of Blockchain Technology in Knowledge-Defined Networking, Its Application, Benefits, and Challenges. Network, 2023; submitted. [Google Scholar]
- Wijesekara, P.A.D.S.N. An Accurate Mathematical Epidemiological Model (SEQIJRDS) to Recommend Public Health Interventions Related to COVID-19 in Sri Lanka. Prepr. Res. Sq. 2021. [Google Scholar]
- Tang, T.A.; Mhamdi, L.; McLernon, D.; Zaidi, S.A.R.; Ghogho, M.; El Moussa, F. DeepIDS: Deep learning approach for intrusion detection in software defined networking. Electronics 2020, 9, 1533. [Google Scholar] [CrossRef]
- Li, Z.; Liu, F.; Yang, W.; Peng, S.; Zhou, J. A survey of convolutional neural networks: Analysis, applications, and prospects. IEEE Trans. Neural Netw. Learn. Syst. 2021, 33, 6999–7019. [Google Scholar] [CrossRef]
- Fouladi, R.F.; Ermiş, O.; Anarim, E. A novel approach for distributed denial of service defense using continuous wavelet transform and convolutional neural network for software-defined network. Comput. Secur. 2022, 112, 102524. [Google Scholar] [CrossRef]
- Indira, B.; Valarmathi, K.; Devaraj, D. An approach to enhance packet classification performance of software-defined network using deep learning. Soft Comput. 2019, 23, 8609–8619. [Google Scholar] [CrossRef]
- Mohammed, A.R.; Mohammed, S.A.; Shirmohammadi, S. Machine learning and deep learning based traffic classification and prediction in software defined networking. In Proceedings of the 2019 IEEE International Symposium on Measurements & Networking (M&N), Catania, Italy, 8–10 July 2019; pp. 1–6. [Google Scholar]
- Chen, X.; Wang, X.; Yi, B.; He, Q.; Huang, M. Deep learning-based traffic prediction for energy efficiency optimization in software-defined networking. IEEE Syst. J. 2020, 15, 5583–5594. [Google Scholar] [CrossRef]
- Dey, S.K.; Rahman, M.M. Flow based anomaly detection in software defined networking: A deep learning approach with feature selection method. In Proceedings of the 2018 4th International Conference on Electrical Engineering and Information & Communication Technology (iCEEiCT), Dhaka, Bangladesh, 13–15 September 2018; pp. 630–635. [Google Scholar]
- Shimizu, D.Y.; Mayer, K.S.; Soares, J.A.; Arantes, D.S. A deep neural network model for link failure identification in multi-path ROADM based networks. In Proceedings of the 2020 Photonics North (PN), Niagara Falls, ON, Canada, 26–28 May 2020; p. 1. [Google Scholar]
- Khunteta, S.; Chavva, A.K.R. Deep learning based link failure mitigation. In Proceedings of the 2017 16th IEEE International Conference on Machine Learning and Applications (ICMLA), Cancun, Mexico, 18–21 December 2017; pp. 806–811. [Google Scholar]
- Reis, J.; Rocha, M.; Phan, T.K.; Griffin, D.; Le, F.; Rio, M. Deep neural networks for network routing. In Proceedings of the 2019 International Joint Conference on Neural Networks (IJCNN), Budapest, Hungary, 14–19 July 2019; pp. 1–8. [Google Scholar]
- Zhang, H.; Wang, T.; Liu, T.; Zhang, Q.; Liu, Y. Deep Neural Network Routing with Dynamic Space Division for 3D UAV FANETs. Wirel. Pers. Commun. 2022, 125, 2003–2028. [Google Scholar] [CrossRef]
- Wijesekara, P.A.D.S.N.; Gunawardena, S. A Machine Learning-Aided Network Contention-Aware Link Lifetime- and Delay-Based Hybrid Routing Framework for Software-Defined Vehicular Networks. Telecom 2023, 4, 393–458. [Google Scholar] [CrossRef]
- Azzouni, A.; Boutaba, R.; Pujolle, G. NeuRoute: Predictive dynamic routing for software-defined networks. In Proceedings of the 2017 13th International Conference on Network and Service Management (CNSM), Tokyo, Japan, 26–30 November 2017; pp. 1–6. [Google Scholar]
- Zou, G.; Li, T.; Jiang, M.; Hu, S.; Cao, C.; Zhang, B.; Gan, Y.; Chen, Y. DeepTSQP: Temporal-aware service QoS prediction via deep neural network and feature integration. Knowl.-Based Syst. 2022, 241, 108062. [Google Scholar] [CrossRef]
- Wu, H.; Zhang, Z.; Luo, J.; Yue, K.; Hsu, C.H. Multiple attributes QoS prediction via deep neural model with contexts. IEEE Trans. Serv. Comput. 2018, 14, 1084–1096. [Google Scholar] [CrossRef]
- Priyanka; Kumar, D. Decision tree classifier: A detailed survey. Int. J. Inf. Decis. Sci. 2020, 12, 246–269. [Google Scholar] [CrossRef]
- Kousar, H.; Mulla, M.M.; Shettar, P.; Narayan, D.G. Detection of DDoS attacks in software defined network using decision tree. In Proceedings of the 2021 10th IEEE International Conference on Communication Systems and Network Technologies (CSNT), Bhopal, India, 24–25 April 2021; pp. 783–788. [Google Scholar]
- Li, W.; Li, X.; Li, H.; Xie, G. Cutsplit: A decision-tree combining cutting and splitting for scalable packet classification. In Proceedings of the IEEE INFOCOM 2018—IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; pp. 2645–2653. [Google Scholar]
- Liu, Z.; Sun, S.; Zhu, H.; Gao, J.; Li, J. BitCuts: A fast packet classification algorithm using bit-level cutting. Comput. Commun. 2017, 109, 38–52. [Google Scholar] [CrossRef]
- Singh, S.; Baboescu, F.; Varghese, G.; Wang, J. Packet classification using multidimensional cutting. In Proceedings of the 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Karlsruhe, Germany, 25–28 August 2003; pp. 213–224. [Google Scholar]
- Ahakonye, L.A.C.; Nwakanma, C.I.; Lee, J.M.; Kim, D.S. Efficient classification of enciphered SCADA network traffic in smart factory using decision tree algorithm. IEEE Access 2021, 9, 154892–154901. [Google Scholar] [CrossRef]
- Tong, D.; Qu, Y.R.; Prasanna, V.K. Accelerating decision tree based traffic classification on FPGA and multicore platforms. IEEE Trans. Parallel Distrib. Syst. 2017, 28, 3046–3059. [Google Scholar] [CrossRef]
- Yuan, Z.; Wang, C. An improved network traffic classification algorithm based on Hadoop decision tree. In Proceedings of the 2016 IEEE International Conference of Online Analysis and Computing Science (ICOACS), Chongqing, China, 28–29 May 2016; pp. 53–56. [Google Scholar]
- Achirul Nanda, M.; Boro Seminar, K.; Nandika, D.; Maddu, A. A comparison study of kernel functions in the support vector machine and its application for termite detection. Information 2018, 9, 5. [Google Scholar] [CrossRef] [Green Version]
- Myint Oo, M.; Kamolphiwong, S.; Kamolphiwong, T.; Vasupongayya, S. Advanced support vector machine-(ASVM-) based detection for distributed denial of service (DDoS) attack on software defined networking (SDN). J. Comput. Netw. Commun. 2019, 2019, 8012568. [Google Scholar] [CrossRef] [Green Version]
- Schueller, Q.; Basu, K.; Younas, M.; Patel, M.; Ball, F. A hierarchical intrusion detection system using support vector machine for SDN network in cloud data center. In Proceedings of the 2018 28th International Telecommunication Networks and Applications Conference (ITNAC), Sydney, Australia, 21–23 November 2018; pp. 1–6. [Google Scholar]
- Raikar, M.M.; Meena, S.M.; Mulla, M.M.; Shetti, N.S.; Karanandi, M. Data traffic classification in software defined networks (SDN) using supervised-learning. Procedia Comput. Sci. 2020, 171, 2750–2759. [Google Scholar] [CrossRef]
- Liu, C.C.; Chang, Y.; Tseng, C.W.; Yang, Y.T.; Lai, M.S.; Chou, L.D. SVM-based classification mechanism and its application in SDN networks. In Proceedings of the 2018 10th International Conference on Communication Software and Networks (ICCSN), Chengdu, China, 6–9 July 2018; pp. 45–49. [Google Scholar]
- Indira, B.; Valarmathi, K. A Perspective of the Machine Learning Approach for the Packet Classification in the Software Defined Network. Intell. Autom. Soft Comput. 2020, 26, 795–805. [Google Scholar] [CrossRef]
- Fan, Z.; Liu, R. Investigation of machine learning based network traffic classification. In Proceedings of the 2017 International Symposium on Wireless Communication Systems (ISWCS), Bologna, Italy, 28–31 August 2017; pp. 1–6. [Google Scholar]
- Speiser, J.L.; Miller, M.E.; Tooze, J.; Ip, E. A comparison of random forest variable selection methods for classification prediction modeling. Expert Syst. Appl. 2019, 134, 93–101. [Google Scholar] [CrossRef]
- Resende, P.A.A.; Drummond, A.C. A survey of random forest based methods for intrusion detection systems. ACM Comput. Surv. 2018, 51, 1–36. [Google Scholar] [CrossRef]
- Kokila, R.T.; Selvi, S.T.; Govindarajan, K. DDoS detection and analysis in SDN-based environment using support vector machine classifier. In Proceedings of the 2014 Sixth International Conference on Advanced Computing (ICoAC), Chennai, India, 17–19 December 2014; pp. 205–210. [Google Scholar]
- Primartha, R.; Tama, B.A. Anomaly detection using random forest: A performance revisited. In Proceedings of the 2017 International Conference on Data and Software Engineering (ICoDSE), Palembang, Indonesia, 1–2 November 2017; pp. 1–6. [Google Scholar]
- Amaral, P.; Dinis, J.; Pinto, P.; Bernardo, L.; Tavares, J.; Mamede, H.S. Machine learning in software defined networks: Data collection and traffic classification. In Proceedings of the 2016 IEEE 24th International Conference on Network Protocols (ICNP), Singapore, 8–11 November 2016; pp. 1–5. [Google Scholar]
- Pasquini, R.; Stadler, R. Learning end-to-end application qos from openflow switch statistics. In Proceedings of the 2017 IEEE Conference on Network Softwarization (NetSoft), Bologna, Italy, 3–7 July 2017; pp. 1–9. [Google Scholar]
- Fan, G.F.; Guo, Y.H.; Zheng, J.M.; Hong, W.C. Application of the weighted k-nearest neighbor algorithm for short-term load forecasting. Energies 2019, 12, 916. [Google Scholar] [CrossRef] [Green Version]
- Rahman, O.; Quraishi, M.A.G.; Lung, C.H. DDoS attacks detection and mitigation in SDN using machine learning. In Proceedings of the 2019 IEEE World Congress on Services (SERVICES), Milan, Italy, 8–13 July 2019; Volume 2642, pp. 184–189. [Google Scholar]
- Alablani, I.A.; Arafah, M.A. An SDN/ML-Based Adaptive Cell Selection Approach for HetNets: A Real-World Case Study in London, UK. IEEE Access 2021, 9, 166932–166950. [Google Scholar] [CrossRef]
- Tuan, N.N.; Hung, P.H.; Nghia, N.D.; Tho, N.V.; Phan, T.V.; Thanh, N.H. A DDoS attack mitigation scheme in ISP networks using machine learning based on SDN. Electronics 2020, 9, 413. [Google Scholar] [CrossRef] [Green Version]
- Khamaiseh, S.; Serra, E.; Li, Z.; Xu, D. Detecting saturation attacks in SDN via machine learning. In Proceedings of the 2019 4th International Conference on Computing, Communications and Security (ICCCS), Rome, Italy, 10–12 October 2019; pp. 1–8. [Google Scholar]
- Bouacida, N.; Alghadhban, A.; Alalmaei, S.; Mohammed, H.; Shihada, B. Failure mitigation in software defined networking employing load type prediction. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–7. [Google Scholar]
- Abar, T.; Letaifa, A.B.; El Asmi, S. Machine learning based QoE prediction in SDN networks. In Proceedings of the 2017 13th International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; pp. 1395–1400. [Google Scholar]
- Gordon, H.; Batula, C.; Tushir, B.; Dezfouli, B.; Liu, Y. Securing smart homes via software-defined networking and low-cost traffic classification. In Proceedings of the 2021 IEEE 45th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, 12–16 July 2021; pp. 1049–1057. [Google Scholar]
- Ahmed, M.; Seraj, R.; Islam, S.M.S. The k-means algorithm: A comprehensive survey and performance evaluation. Electronics 2020, 9, 1295. [Google Scholar] [CrossRef]
- Wang, G.; Zhao, Y.; Huang, J.; Duan, Q.; Li, J. A K-means-based network partition algorithm for controller placement in software defined network. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Babayiğit, B.; Banu, U.L.U. A High Available Multi-Controller Structure for SDN and Placement of Multi-Controllers of SDN with Optimized K-means Algorithm. J. Inst. Sci. Technol. 2021, 11, 2456–2466. [Google Scholar] [CrossRef]
- Starke, A.; McNair, J.; Trevizan, R.; Bretas, A.; Peeples, J.; Zare, A. Toward resilient smart grid communications using distributed SDN with ML-based anomaly detection. In Wired/Wireless Internet Communications: 16th IFIP WG 6.2 International Conference, WWIC 2018, Boston, MA, USA, 18–20 June 2018; Proceedings; Springer International Publishing: Cham, Switzerland, 2018; pp. 83–94. [Google Scholar]
- Cui, J.; Zhang, J.; He, J.; Zhong, H.; Lu, Y. DDoS detection and defense mechanism for SDN controllers with K-Means. In Proceedings of the 2020 IEEE/ACM 13th International Conference on Utility and Cloud Computing (UCC), Leicester, UK, 7–10 December 2020; pp. 394–401. [Google Scholar]
- Heigl, M.; Anand, K.A.; Urmann, A.; Fiala, D.; Schramm, M.; Hable, R. On the improvement of the isolation forest algorithm for outlier detection with streaming data. Electronics 2021, 10, 1534. [Google Scholar] [CrossRef]
- Shahzadi, S.; Ahmad, F.; Basharat, A.; Alruwaili, M.; Alanazi, S.; Humayun, M.; Rizwan, M.; Naseem, S. Machine learning empowered security management and quality of service provision in SDN-NFV environment. Comput. Mater. Contin. 2021, 66, 2723–2749. [Google Scholar] [CrossRef]
- Abou El Houda, Z.; Hafid, A.S.; Khoukhi, L. A novel machine learning framework for advanced attack detection using SDN. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Nakahara, M.; Okui, N.; Kobayashi, Y.; Miyake, Y. Malware Detection for IoT Devices using Automatically Generated White List and Isolation Forest. In Proceedings of the IoTBDS, Online, 23–25 April 2021; pp. 38–47. [Google Scholar]
- Zhu, J.; Jiang, M.; Liu, Z. Fault Detection and Diagnosis in Industrial Processes with Variational Autoencoder: A Comprehensive Study. Sensors 2021, 22, 227. [Google Scholar] [CrossRef]
- Dong, S.; Su, H.; Liu, Y. A-CAVE: Network abnormal traffic detection algorithm based on variational autoencoder. ICT Express 2022, 1–7. [Google Scholar] [CrossRef]
- Bårli, E.M.; Yazidi, A.; Viedma, E.H.; Haugerud, H. DoS and DDoS mitigation using variational autoencoders. Comput. Netw. 2021, 199, 108399. [Google Scholar] [CrossRef]
- Park, S.W.; Ko, J.S.; Huh, J.H.; Kim, J.C. Review on generative adversarial networks: Focusing on computer vision and its applications. Electronics 2021, 10, 1216. [Google Scholar] [CrossRef]
- Wang, P.; Wang, Z.; Ye, F.; Chen, X. Bytesgan: A semi-supervised generative adversarial network for encrypted traffic classification in SDN edge gateway. Comput. Netw. 2021, 200, 108535. [Google Scholar] [CrossRef]
- Falahatraftar, F.; Pierre, S.; Chamberland, S. A Conditional Generative Adversarial Network Based Approach for Network Slicing in Heterogeneous Vehicular Networks. Telecom 2021, 2, 141–154. [Google Scholar] [CrossRef]
- AlEroud, A.; Karabatis, G. Sdn-gan: Generative adversarial deep nns for synthesizing cyber attacks on software defined networks. In On the Move to Meaningful Internet Systems: OTM 2019 Workshops: Confederated International Workshops: EI2N, FBM, ICSP, Meta4eS and SIAnA, Rhodes, Greece, 21–25 October 2019; Springer Nature: Cham, Switzerland, 2019; pp. 211–220. [Google Scholar]
- Novaes, M.P.; Carvalho, L.F.; Lloret, J.; Proença, M.L., Jr. Adversarial Deep Learning approach detection and defense against DDoS attacks in SDN environments. Future Gener. Comput. Syst. 2021, 125, 156–167. [Google Scholar] [CrossRef]
- Shi, W.; Li, Z.; Lv, W.; Wu, Y.; Chang, J.; Li, X. Laplacian support vector machine for vibration-based robotic terrain classification. Electronics 2020, 9, 513. [Google Scholar] [CrossRef] [Green Version]
- Wang, P.; Lin, S.C.; Luo, M. A framework for QoS-aware traffic classification using semi-supervised machine learning in SDNs. In Proceedings of the 2016 IEEE International Conference on Services Computing (SCC), San Francisco, CA, USA, 27 June–2 July; pp. 760–765.
- Livieris, I.E.; Kanavos, A.; Tampakas, V.; Pintelas, P. An auto-adjustable semi-supervised self-training algorithm. Algorithms 2018, 11, 139. [Google Scholar] [CrossRef] [Green Version]
- Amaral, P.; Pinto, P.F.; Bernardo, L.; Mazandarani, A. Application aware SDN architecture using semi-supervised traffic classification. In Proceedings of the 2018 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Verona, Italy, 27–29 November 2018; pp. 1–6. [Google Scholar]
- Khamaiseh, S.; Al-Alaj, A.; Adnan, M.; Alomari, H.W. The Robustness of Detecting Known and Unknown DDoS Saturation Attacks in SDN via the Integration of Supervised and Semi-Supervised Classifiers. Future Internet 2022, 14, 164. [Google Scholar] [CrossRef]
- Guo, X.; Bai, W. ML-SDNIDS: An attack detection mechanism for SDN based on machine learning. Int. J. Inf. Comput. Secur. 2022, 19, 118–141. [Google Scholar] [CrossRef]
- Monshizadeh, M.; Khatri, V.; Gamdou, M.; Kantola, R.; Yan, Z. Improving data generalization with variational autoencoders for network traffic anomaly detection. IEEE Access 2021, 9, 56893–56907. [Google Scholar] [CrossRef]
- Yang, Y.; Zheng, K.; Wu, C.; Yang, Y. Improving the classification effectiveness of intrusion detection by using improved conditional variational autoencoder and deep neural network. Sensors 2019, 19, 2528. [Google Scholar] [CrossRef] [Green Version]
- Mhamdi, L.; McLernon, D.; Zaidi, S.A.R.; Tang, T. A deep learning approach combining autoencoder with one-class SVM for DDoS attack detection in SDNs. In Proceedings of the 2020 IEEE Eighth International Conference on Communications and Networking (ComNet), Virtual Event, 28–30 October 2020; pp. 1–6. [Google Scholar]
- Tu, J.; Ogola, W.; Xu, D.; Xie, W. Intrusion Detection Based on Generative Adversarial Network of Reinforcement Learning Strategy for Wireless Sensor Networks. Int. J. Circuits Syst. Signal Process. 2022, 16, 478–482. [Google Scholar] [CrossRef]
- Nugraha, B.; Kulkarni, N.; Gopikrishnan, A. Detecting adversarial DDoS attacks in software-defined networking using deep learning techniques and adversarial training. In Proceedings of the 2021 IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 26–28 July 2021; pp. 448–454. [Google Scholar]
- Le, L.T.; Thinh, T.N. On the improvement of machine learning based intrusion detection system for SDN networks. In Proceedings of the 2021 8th NAFOSTED Conference on Information and Computer Science (NICS), Hanoi, Vietnam, 21–22 December 2021; pp. 464–469. [Google Scholar]
- Comaneci, D.; Dobre, C. Securing networks using SDN and machine learning. In Proceedings of the 2018 IEEE International Conference on Computational Science and Engineering (CSE), Bucharest, Romania, 28–31 October 2018; pp. 194–200. [Google Scholar]
- Da Silva, A.S.; Wickboldt, J.A.; Granville, L.Z.; Schaeffer-Filho, A. ATLANTIC: A framework for anomaly traffic detection, classification, and mitigation in SDN. In Proceedings of the NOMS 2016—2016 IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; pp. 27–35. [Google Scholar]
- Xu, Y.; Sun, H.; Xiang, F.; Sun, Z. Efficient DDoS detection based on K-FKNN in software defined networks. IEEE Access 2019, 7, 160536–160545. [Google Scholar] [CrossRef]
- Feng, Y.; Cai, W.; Yue, H.; Xu, J.; Lin, Y.; Chen, J.; Hu, Z. An improved X-means and isolation forest based methodology for network traffic anomaly detection. PLoS ONE 2022, 17, e0263423. [Google Scholar] [CrossRef]
- Deepa, V.; Sudar, K.M.; Deepalakshmi, P. Design of ensemble learning methods for DDoS detection in SDN environment. In Proceedings of the 2019 International Conference on Vision towards Emerging Trends in Communication and Networking (ViTECoN), Vellore, India, 30–31 March 201; pp. 1–6.
- Afuwape, A.A.; Xu, Y.; Anajemba, J.H.; Srivastava, G. Performance evaluation of secured network traffic classification using a machine learning approach. Comput. Stand. Interfaces 2021, 78, 103545. [Google Scholar] [CrossRef]
- Vithayathil Varghese, N.; Mahmoud, Q.H. A survey of multi-task deep reinforcement learning. Electronics 2020, 9, 1363. [Google Scholar] [CrossRef]
- Swaminathan, A.; Chaba, M.; Sharma, D.K.; Ghosh, U. GraphNET: Graph neural networks for routing optimization in software defined networks. Comput. Commun. 2021, 178, 169–182. [Google Scholar] [CrossRef]
- He, Q.; Wang, Y.; Wang, X.; Xu, W.; Li, F.; Yang, K.; Ma, L. Routing Optimization with Deep Reinforcement Learning in Knowledge Defined Networking. IEEE Trans. Mob. Comput. 2023, 1–12. [Google Scholar] [CrossRef]
- Miranda, C.; Kaddoum, G.; Boukhtouta, A.; Madi, T.; Alameddine, H.A. Intrusion Prevention Scheme Against Rank Attacks for Software-Defined Low Power IoT Networks. IEEE Access 2022, 10, 129970–129984. [Google Scholar] [CrossRef]
- Casas-Velasco, D.M.; Rendon, O.M.C.; da Fonseca, N.L. Intelligent routing based on reinforcement learning for software-defined networking. IEEE Trans. Netw. Serv. Manag. 2020, 18, 870–881. [Google Scholar] [CrossRef]
- Chen, Y.R.; Rezapour, A.; Tzeng, W.G.; Tsai, S.C. RL-routing: An SDN routing algorithm based on deep reinforcement learning. IEEE Trans. Netw. Sci. Eng. 2020, 7, 3185–3199. [Google Scholar] [CrossRef]
- Guo, X.; Lin, H.; Li, Z.; Peng, M. Deep-reinforcement-learning-based QoS-aware secure routing for SDN-IoT. IEEE Internet Things J. 2019, 7, 6242–6251. [Google Scholar] [CrossRef]
- Chen, C.; Xue, F.; Lu, Z.; Tang, Z.; Li, C. RLMR: Reinforcement Learning Based Multipath Routing for SDN. Wirel. Commun. Mob. Comput. 2022, 2022, 5124960. [Google Scholar] [CrossRef]
- Huong, T.T.; Khoa, N.D.D.; Dung, N.X.; Thanh, N.H. A global multipath load-balanced routing algorithm based on Reinforcement Learning in SDN. In Proceedings of the 2019 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 16–18 October 2019; pp. 1336–1341. [Google Scholar]
- Zhao, C.; Ye, M.; Xue, X.; Lv, J.; Jiang, Q.; Wang, Y. DRL-M4MR: An intelligent multicast routing approach based on DQN deep reinforcement learning in SDN. Phys. Commun. 2022, 55, 101919. [Google Scholar] [CrossRef]
- Zhang, J.; Ye, M.; Guo, Z.; Yen, C.Y.; Chao, H.J. CFR-RL: Traffic engineering with reinforcement learning in SDN. IEEE J. Sel. Areas Commun. 2020, 38, 2249–2259. [Google Scholar] [CrossRef]
- Sun, P.; Guo, Z.; Lan, J.; Li, J.; Hu, Y.; Baker, T. ScaleDRL: A scalable deep reinforcement learning approach for traffic engineering in SDN with pinning control. Comput. Netw. 2021, 190, 107891. [Google Scholar] [CrossRef]
- Akbari, I.; Tahoun, E.; Salahuddin, M.A.; Limam, N.; Boutaba, R. ATMoS: Autonomous threat mitigation in SDN using reinforcement learning. In Proceedings of the NOMS 2020—2020 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 20–24 April 2020; pp. 1–9. [Google Scholar]
- Dake, D.K.; Gadze, J.D.; Klogo, G.S.; Nunoo-Mensah, H. Multi-agent reinforcement learning framework in sdn-iot for transient load detection and prevention. Technologies 2021, 9, 44. [Google Scholar] [CrossRef]
- Sampaio, L.S.; Faustini, P.H.; Silva, A.S.; Granville, L.Z.; Schaeffer-Filho, A. Using NFV and reinforcement learning for anomalies detection and mitigation in SDN. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 June 2018; pp. 432–437. [Google Scholar]
- Al-Jawad, A.; Comşa, I.S.; Shah, P.; Gemikonakli, O.; Trestian, R. An innovative reinforcement learning-based framework for quality of service provisioning over multimedia-based sdn environments. IEEE Trans. Broadcast. 2021, 67, 851–867. [Google Scholar] [CrossRef]
- Xiong, Z.; Zhang, Y.; Niyato, D.; Deng, R.; Wang, P.; Wang, L.C. Deep reinforcement learning for mobile 5G and beyond: Fundamentals, applications, and challenges. IEEE Veh. Technol. Mag. 2019, 14, 44–52. [Google Scholar] [CrossRef]
- Karamplias, T.; Spantideas, S.T.; Giannopoulos, A.E.; Gkonis, P.; Kapsalis, N.; Trakadas, P. Towards Closed-Loop Automation in 5G Open RAN: Coupling an Open-Source Simulator with XApps. In Proceedings of the 2022 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Grenoble, France, 7–10 June 2022; pp. 232–237. [Google Scholar]
- Li, J.; Zhang, X. Deep reinforcement learning-based joint scheduling of eMBB and URLLC in 5G networks. IEEE Wirel. Commun. Lett. 2020, 9, 1543–1546. [Google Scholar] [CrossRef]
- Sapra, D.; Pimentel, A.D. Deep learning model reuse and composition in knowledge centric networking. In Proceedings of the 2020 29th International Conference on Computer Communications and Networks (ICCCN), Honolulu, HI, USA, 3–8 August 2020; pp. 1–11. [Google Scholar]
- Wijesekara, P.A.D.S.N.; Sudheera, K.L.K.; Sandamali, G.G.N.; Chong, P.H.J. Machine Learning Based Link Stability Prediction for Routing in Software Defined Vehicular Networks. In Proceedings of the 20th Academic Sessions, Matara, Sri Lanka, 7 June 2023; p. 60. [Google Scholar]
- Tudorache, T.; Nyulas, C.; Noy, N.F.; Musen, M.A. WebProtégé: A collaborative ontology editor and knowledge acquisition tool for the web. Semant. Web 2013, 4, 89–99. [Google Scholar] [CrossRef] [PubMed]
- Futia, G.; Vetrò, A. On the integration of knowledge graphs into deep learning models for a more comprehensible AI—Three challenges for future research. Information 2020, 11, 122. [Google Scholar] [CrossRef] [Green Version]
- McBride, B. The resource description framework (RDF) and its vocabulary description language RDFS. In Handbook on Ontologies; Springer: Berlin/Heidelberg, Germany, 2004; pp. 51–65. [Google Scholar]
- Antoniou, G.; Harmelen, F.V. Web ontology language: Owl. In Handbook on Ontologies; Springer: Berlin/Heidelberg, Germany, 2009; pp. 91–110. [Google Scholar]
- Fensel, D.; Van Harmelen, F.; Horrocks, I.; McGuinness, D.L.; Patel-Schneider, P.F. OIL: An ontology infrastructure for the semantic web. IEEE Intell. Syst. 2001, 16, 38–45. [Google Scholar] [CrossRef]
- Yang, Y.; Calmet, J. Ontobayes: An ontology-driven uncertainty model. In Proceedings of the International Conference on Computational Intelligence for Modelling, Control and Automation and International Conference on Intelligent Agents, Web Technologies and Internet Commerce (CIMCA-IAWTIC’06), Vienna, Austria, 28–30 November 2005; Volume 1, pp. 457–463. [Google Scholar]
- Hayes, P.; Menzel, C. A semantics for the knowledge interchange format. In Proceedings of the IJCAI 2001 Workshop on the IEEE Standard Upper Ontology, Seattle, WA, USA, 4 August 2001; Volume 145, p. 145. [Google Scholar]
- Jarvis, M.P.; Nuzzo-Jones, G.; Heffernan, N.T. Applying machine learning techniques to rule generation in intelligent tutoring systems. In Intelligent Tutoring Systems: 7th International Conference, ITS, Maceió, Brazil, 30 August–3 September 2004; Proceedings 7; Springer: Berlin/Heidelberg, Germany, 2004; pp. 541–553. [Google Scholar]
- Boley, H.; Tabet, S.; Wagner, G. Design rationale for RuleML: A markup language for semantic web rules. In Proceedings of the SWWS, Stanford, CA, USA, 30 July–1 August 2001; Volume 1, pp. 381–401. [Google Scholar]
- Horrocks, I.; Patel-Schneider, P.F.; Boley, H.; Tabet, S.; Grosof, B.; Dean, M. SWRL: A semantic web rule language combining OWL and RuleML. W3C Memb. Submiss. 2004, 21, 1–31. [Google Scholar]
- Kifer, M. Rule interchange format: The framework. In Web Reasoning and Rule Systems: Second International Conference, RR 2008, Karlsruhe, Germany, 31 October–1 November 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 1–11. [Google Scholar]
- Inoue, T.; Mano, T.; Mizutani, K.; Minato, S.I.; Akashi, O. Rethinking packet classification for global network view of software-defined networking. In Proceedings of the 2014 IEEE 22nd International Conference on Network Protocols, Raleigh, NC, USA, 21–24 October 2014; pp. 296–307. [Google Scholar]
- Li, C.; Li, T.; Li, J.; Shi, Z.; Wang, B. Enabling packet classification with low update latency for SDN switch on FPGA. Sustainability 2020, 12, 3068. [Google Scholar] [CrossRef] [Green Version]
- Wang, P.; Ye, F.; Chen, X.; Qian, Y. Datanet: Deep learning based encrypted network traffic classification in sdn home gateway. IEEE Access 2018, 6, 55380–55391. [Google Scholar] [CrossRef]
- Malik, A.; de Fréin, R.; Al-Zeyadi, M.; Andreu-Perez, J. Intelligent SDN traffic classification using deep learning: Deep-SDN. In Proceedings of the 2020 2nd International Conference on Computer Communication and the Internet (ICCCI), Nagoya, Japan, 26–29 June 2020; pp. 184–189. [Google Scholar]
- Chen, X.F.; Yu, S.Z. CIPA: A collaborative intrusion prevention architecture for programmable network and SDN. Comput. Secur. 2016, 58, 1–19. [Google Scholar] [CrossRef]
- Pratama, R.F.; Suwastika, N.A.; Nugroho, M.A. Design and implementation adaptive Intrusion Prevention System (IPS) for attack prevention in software-defined network (SDN) architecture. In Proceedings of the 2018 6th International Conference on Information and Communication Technology (ICoICT), Bandung, Indonesia, 3–5 May 2018; pp. 299–304. [Google Scholar]
- Siregar, B.; Purba, R.F.D.; Fahmi, F. Intrusion Prevention System Against Denial of Service Attacks Using Genetic Algorithm. In Proceedings of the 2018 IEEE International Conference on Communication, Networks and Satellite (Comnetsat), Medan, Indonesia, 15–17 November 2018; pp. 55–59. [Google Scholar]
- Girdler, T.; Vassilakis, V.G. Implementing an intrusion detection and prevention system using Software-Defined Networking: Defending against ARP spoofing attacks and Blacklisted MAC Addresses. Comput. Electr. Eng. 2021, 90, 106990. [Google Scholar] [CrossRef]
- Bera, S.; Misra, S.; Jamalipour, A. FlowStat: Adaptive flow-rule placement for per-flow statistics in SDN. IEEE J. Sel. Areas Commun. 2019, 37, 530–539. [Google Scholar] [CrossRef]
- Yahyaoui, H.; Aidi, S.; Zhani, M.F. On using flow classification to optimize traffic routing in SDN networks. In Proceedings of the 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2020; pp. 1–6. [Google Scholar]
- Xu, S.; Wang, X.; Yang, G.; Ren, J.; Wang, S. Routing optimization for cloud services in SDN-based Internet of Things with TCAM capacity constraint. J. Commun. Netw. 2020, 22, 145–158. [Google Scholar] [CrossRef]
- Wang, M.; Liu, J.; Mao, J.; Cheng, H.; Chen, J.; Qi, C. RouteGuardian: Constructing secure routing paths in software-defined networking. Tsinghua Sci. Technol. 2017, 22, 400–412. [Google Scholar] [CrossRef]
- Yan, B.; Liu, Q.; Shen, J.; Liang, D. Flowlet-level multipath routing based on graph neural network in OpenFlow-based SDN. Future Gener. Comput. Syst. 2022, 134, 140–153. [Google Scholar] [CrossRef]
- Saha, N.; Misra, S.; Bera, S. Q-flag: QoS-aware flow-rule aggregation in software-defined IoT networks. IEEE Internet Things J. 2021, 9, 4899–4906. [Google Scholar] [CrossRef]
- Mondal, A.; Misra, S.; Maity, I. AMOPE: Performance analysis of OpenFlow systems in software-defined networks. IEEE Syst. J. 2019, 14, 124–131. [Google Scholar] [CrossRef]
- Guo, Y.; Hu, G.; Shao, D. QOGMP: QoS-oriented global multi-path traffic scheduling algorithm in software defined network. Sci. Rep. 2022, 12, 14600. [Google Scholar] [CrossRef]
- Alishahi, M.; Yaghmaee Moghaddam, M.H.; Pourreza, H.R. Multi-class routing protocol using virtualization and SDN-enabled architecture for smart grid. Peer-to-Peer Netw. Appl. 2018, 11, 380–396. [Google Scholar] [CrossRef]
- Kim, W.; Sharma, P.; Lee, J.; Banerjee, S.; Tourrilhes, J.; Lee, S.J.; Yalagandula, P. Automated and Scalable QoS Control for Network Convergence. In Proceedings of the INM/WREN’10: Proceedings of the 2010 Internet Network Management Conference on Research on Enterprise Networking, San Jose, CA, USA, 27 April 2010; Volume 10, p. 1. [Google Scholar]
- Bagci, K.T.; Tekalp, A.M. SDN-enabled distributed open exchange: Dynamic QoS-path optimization in multi-operator services. Comput. Netw. 2019, 162, 106845. [Google Scholar] [CrossRef]
- Khan, S.; Hussain, F.K.; Hussain, O.K. Guaranteeing end-to-end QoS provisioning in SOA based SDN architecture: A survey and Open Issues. Future Gener. Comput. Syst. 2021, 119, 176–187. [Google Scholar] [CrossRef]
- Cao, B.; Sun, Z.; Zhang, J.; Gu, Y. Resource allocation in 5G IoV architecture based on SDN and fog-cloud computing. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3832–3840. [Google Scholar] [CrossRef]
- Liu, D.; Gu, T.; Xue, J.P. Rule engine based on improvement rete algorithm. In Proceedings of the 2010 International Conference on Apperceiving Computing and Intelligence Analysis Proceeding, Chengdu, China, 17–19 December 2010; pp. 346–349. [Google Scholar]
- Proctor, M. Drools: A rule engine for complex event processing. In Applications of Graph Transformations with Industrial Relevance: 4th International Symposium, AGTIVE 2011, Budapest, Hungary, 4–7 October 2011; Revised Selected and Invited Papers 4; Springer: Berlin/Heidelberg, Germany, 2022; p. 2. [Google Scholar]
- Carral, D.; Dragoste, I.; González, L.; Jacobs, C.; Krötzsch, M.; Urbani, J. Vlog: A rule engine for knowledge graphs. In The Semantic Web—ISWC 2019: 18th International Semantic Web Conference, Auckland, New Zealand, 26–30 October 2019; Proceedings, Part II 18; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; pp. 19–35. [Google Scholar]
- Jang, M.; Sohn, J.C. Bossam: An extended rule engine for OWL inferencing. In Rules and Rule Markup Languages for the Semantic Web: Third International Workshop, RuleML, Hiroshima, Japan, 8 November 2004; Proceedings 3; Springer: Berlin/Heidelberg, Germany, 2004; pp. 128–138. [Google Scholar]
- Wygant, R.M. CLIPS—A powerful development and delivery expert system tool. Comput. Ind. Eng. 1989, 7, 546–549. [Google Scholar] [CrossRef]
- Friedman-Hill, E. Jess, the Rule Engine for the Java Platform; Sandia National Laboratories: Albuquerque, NM, USA, 2008. [Google Scholar]
- Barbieri, D.F.; Braga, D.; Ceri, S.; Valle, E.D.; Grossniklaus, M. C-SPARQL: A continuous query language for RDF data streams. Int. J. Semant. Comput. 2010, 4, 3–25. [Google Scholar] [CrossRef] [Green Version]
- O’Connor, M.J.; Das, A.K. SQWRL: A query language for OWL. OWLED 2009, 529, 1–8. [Google Scholar]
- Liu, P.; Wang, X.; Fu, Q.; Yang, Y.; Li, Y.F.; Zhang, Q. KGVQL: A knowledge graph visual query language with bidirectional transformations. Knowl.-Based Syst. 2022, 250, 108870. [Google Scholar] [CrossRef]
- Finin, T.; McKay, D.P.; Fritzson, R.; McEntire, R. KQML: An information and knowledge exchange protocol. In Knowledge Building and Knowledge Sharing; IOS Press: Amsterdam, The Netherlands, 1994. [Google Scholar]
- Taelman, R.; Vander Sande, M.; Verborgh, R. GraphQL-LD: Linked data querying with GraphQL. In Proceedings of the ISWC2018, the 17th International Semantic Web Conference, Monterey, CA, USA, 8–12 October 2018; pp. 1–4. [Google Scholar]
- Bjorklund, M. YANG—A Data Modeling Language for the Network Configuration Protocol (NETCONF); No. rfc6020; Internet Engineering Task Force: Fremont, CA, USA, 2010. [Google Scholar]
- Uslar, M.; Specht, M.; Rohjans, S.; Trefke, J.; González, J.M. The Common Information Model CIM: IEC 61968/61970 and 62325—A Practical Introduction to the CIM; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Sieber, C.; Blenk, A.; Hock, D.; Scheib, M.; Höhn, T.; Köhler, S.; Kellerer, W. Network configuration with quality of service abstractions for SDN and legacy networks. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; IEEE: Toulouse, France, 2015; p. 11351136. [Google Scholar]
- Xu, C.; Li, P.; Luo, Y. A programmable policy engine to facilitate time-efficient science DMZ management. Future Gener. Comput. Syst. 2018, 89, 515–524. [Google Scholar] [CrossRef]
- Tuncer, D.; Charalambides, M.; Clayman, S.; Pavlou, G. Adaptive resource management and control in software defined networks. IEEE Trans. Netw. Serv. Manag. 2015, 12, 18–33. [Google Scholar] [CrossRef] [Green Version]
- Ballani, H.; Francis, P. Conman: A step towards network manageability. ACM SIGCOMM Comput. Commun. Rev. 2007, 37, 205–216. [Google Scholar] [CrossRef]
- Chen, X.; Mao, Z.M.; Van der Merwe, J. PACMAN: A platform for automated and controlled network operations and configuration management. In Proceedings of the 5th International Conference on Emerging Networking Experiments and Technologies, Rome, Italy, 1 December 2009; pp. 277–288. [Google Scholar]
- Narisetty, R.; Dane, L.; Malishevskiy, A.; Gurkan, D.; Bailey, S.; Narayan, S.; Mysore, S. OpenFlow configuration protocol: Implementation for the of management plane. In Proceedings of the 2013 Second GENI Research and Educational Experiment Workshop, Salt Lake, UT, USA, 20–22 March 2013; IEEE: Toulouse, France, 2013; pp. 66–67. [Google Scholar]
- Martinez, A.; Yannuzzi, M.; de Vergara, J.L.; Serral-Gracià, R.; Ramírez, W. An ontology-based information extraction system for bridging the configuration gap in hybrid sdn environments. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; IEEE: Toulouse, France, 2015; pp. 441–449. [Google Scholar]
- Lu, H.; Arora, N.; Zhang, H.; Lumezanu, C.; Rhee, J.; Jiang, G. Hybnet: Network manager for a hybrid network infrastructure. In Proceedings of the Industrial Track of the 13th ACM/IFIP/USENIX International Middleware Conference, Beijing, China, 11–13 December 2013; pp. 1–6. [Google Scholar]
- Safrianti, E.; Sari, L.O.; Sari, N.A. Real-Time Network Device Monitoring System with Simple Network Management Protocol (SNMP) Model. In Proceedings of the 2021 3rd International Conference on Research and Academic Community Services (ICRACOS), Virtual Event, 9–10 October 2021; IEEE: Toulouse, France, 2021; pp. 122–127. [Google Scholar]
- Chowdhury, S.R.; Bari, M.F.; Ahmed, R.; Boutaba, R. Payless: A low cost network monitoring framework for software defined networks. In Proceedings of the 2014 IEEE Network Operations and Management Symposium (NOMS), Krakow, Poland, 5–9 May 2014; IEEE: Toulouse, France, 2014. [Google Scholar]
- Suh, J.; Kwon, T.T.; Dixon, C.; Felter, W.; Carter, J. Opensample: A low-latency, sampling-based measurement platform for commodity sdn. In Proceedings of the 2014 IEEE 34th International Conference on Distributed Computing Systems, Madrid, Spain, 30 June–3 July 2014; IEEE: Toulouse, France, 2014; pp. 228–237. [Google Scholar]
- Van Adrichem, N.L.; Doerr, C.; Kuipers, F.A. Opennetmon: Network monitoring in openflow software-defined networks. In Proceedings of the 2014 IEEE Network Operations and Management Symposium (NOMS), Krakow, Poland, 5–9 May 2014; IEEE: Toulouse, France, 2014. [Google Scholar]
- Sun, P.; Yu, M.; Freedman, M.J.; Rexford, J.; Walker, D. Hone: Joint host-network traffic management in software-defined networks. J. Netw. Syst. Manag. 2015, 23, 374–399. [Google Scholar] [CrossRef]
- Fan, Y.; Zhang, N. A survey on software-defined vehicular networks. J. Comput. 2017, 28, 236–244. [Google Scholar]
- Wijesekara, P.A.D.S.N.; Sudheera, K.L.K.; Sandamali, G.G.N.; Chong, P.H.J. An Optimization Framework for Data Collection in Software Defined Vehicular Networks. Sensors 2023, 23, 1600. [Google Scholar] [CrossRef] [PubMed]
- Wette, P.; Karl, H. Which flows are hiding behind my wildcard rule? Adding packet sampling to OpenFlow. In Proceedings of the ACM SIGCOMM 2013 Conference on SIGCOMM, Hong Kong, China, 12–16 August 2013; ACM: New York, NY, USA, 2013; pp. 541–542. [Google Scholar]
- Zhou, D.; Yan, Z.; Liu, G.; Atiquzzaman, M. An adaptive network data collection system in sdn. IEEE Trans. Cogn. Commun. Netw. 2019, 6, 562–574. [Google Scholar] [CrossRef] [Green Version]
- Liao, W.H.; Kuai, S.C. An energy-efficient sdn-based data collection strategy for wireless sensor networks. In Proceedings of the 2017 IEEE 7th International Symposium on Cloud and Service Computing (SC2), Kanazawa, Japan, 22–25 November 2017; IEEE: Toulouse, France, 2017; pp. 91–97. [Google Scholar]
- Jiao, Z.; Ding, H.; Dang, M.; Tian, R.; Zhang, B. Predictive big data collection in vehicular networks: A software defined networking based approach. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; IEEE: Toulouse, France, 2016; pp. 1–6. [Google Scholar]
- Wang, R.; Gu, C.; He, S.; Shi, Z.; Meng, W. An interoperable and flat Industrial Internet of Things architecture for low latency data collection in manufacturing systems. J. Syst. Archit. 2022, 129, 102631. [Google Scholar] [CrossRef]
- Sugadev, M.; Rayen, S.J.; Harirajkumar, J.; Rathi, R.; Anitha, G.; Ramesh, S.; Ramaswamy, K. Implementation of Combined Machine Learning with the Big Data Model in IoMT Systems for the Prediction of Network Resource Consumption and Improving the Data Delivery. Comput. Intell. Neurosci. 2022, 2022, 6510934. [Google Scholar] [CrossRef]
- Tian, Y.; Chen, W.; Lea, C.T. An SDN-based traffic matrix estimation framework. IEEE Trans. Netw. Serv. Manag. 2018, 15, 1435–1445. [Google Scholar] [CrossRef]
- Hadem, P.; Saikia, D.K.; Moulik, S. An SDN-based intrusion detection system using SVM with selective logging for IP traceback. Comput. Netw. 2021, 191, 108015. [Google Scholar] [CrossRef]
- Tarnaras, G.; Haleplidis, E.; Denazis, S. SDN and ForCES based optimal network topology discovery. In Proceedings of the 2015 1st IEEE Conference on Network Softwarization (NetSoft), London, UK, 13–17 April 2015; IEEE: Toulouse, France, 2015; pp. 1–6. [Google Scholar]
- Khalid, A.; Rehman, R.A.; Burhan, M. CBILEM: A novel energy aware mobility handling protocol for SDN based NDN-MANETs. Ad Hoc Netw. 2023, 140, 103049. [Google Scholar] [CrossRef]
- Trivisonno, R.; Guerzoni, R.; Vaishnavi, I.; Frimpong, A. Network resource management and QoS in SDN-enabled 5G systems. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; IEEE: Toulouse, France, 2015; pp. 1–7. [Google Scholar]
- Sezer, S.; Scott-Hayward, S.; Chouhan, P.K.; Fraser, B.; Lake, D.; Finnegan, J.; Viljoen, N.; Miller, M.; Rao, N. Are we ready for SDN? Implementation challenges for software-defined networks. IEEE Commun. Mag. 2013, 51, 36–43. [Google Scholar] [CrossRef] [Green Version]
- Gude, N.; Koponen, T.; Pettit, J.; Pfaff, B.; Casado, M.; McKeown, N.; Shenker, S. NOX: Towards an operating system for networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 105–110. [Google Scholar] [CrossRef]
- Song, P.; Liu, Y.; Liu, C.; Qian, D. ParaFlow: Fine-grained parallel SDN controller for large-scale networks. J. Netw. Comput. Appl. 2017, 87, 46–59. [Google Scholar] [CrossRef]
- Shin, S.; Song, Y.; Lee, T.; Lee, S.; Chung, J.; Porras, P.; Yegneswaran, V.; Noh, J.; Kang, B.B. Rosemary: A robust, secure, and high-performance network operating system. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; ACM: New York, NY, USA, 2014; pp. 78–89. [Google Scholar]
- Li, L.; Chou, W.; Zhou, W.; Luo, M. Design patterns and extensibility of REST API for networking applications. IEEE Trans. Netw. Serv. Manag. 2016, 13, 154–167. [Google Scholar] [CrossRef]
- Cajas, C.D.; Budanov, D.O. SDN applications and plugins in the opendaylight controller. In Proceedings of the 2020 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), St. Petersburg and Moscow, Russia, 27–30 January 2020; IEEE: Toulouse, France, 2020; pp. 9–13. [Google Scholar]
- Rowshanrad, S.; Abdi, V.; Keshtgari, M. Performance evaluation of SDN controllers: Floodlight and OpenDaylight. IIUM Eng. J. 2016, 17, 47–57. [Google Scholar] [CrossRef]
- Uddin, R.; Monir, M.F. Performance analysis of SDN based firewalls: POX vs. ODL. In Proceedings of the 2019 5th International Conference on Advances in Electrical Engineering (ICAEE), Dhaka, Bangladesh, 26–28 September 2019; IEEE: Toulouse, France, 2019; pp. 691–698. [Google Scholar]
- Sanvito, D.; Moro, D.; Gulli, M.; Filippini, I.; Capone, A.; Campanella, A. ONOS Intent Monitor and Reroute service: Enabling plug&play routing logic. In Proceedings of the 2018 4th IEEE Conference on Network Softwarization and Workshops (NetSoft), Montreal, QC, Canada, 25–29 June 2018; IEEE: Toulouse, France, 2018; pp. 272–276. [Google Scholar]
- Tuncer, D.; Charalambides, M.; Tangari, G.; Pavlou, G. A northbound interface for software-based networks. In Proceedings of the 2018 14th International Conference on Network and Service Management (CNSM), Rome, Italy, 5–9 November 2018; IEEE: Toulouse, France, 2018; pp. 99–107. [Google Scholar]
- Casey, C.J.; Sutton, A.; Sprintson, A. tinyNBI: Distilling an API from essential OpenFlow abstractions. In Proceedings of the Third Workshop on Hot Topics in Software Defined Networking, Chicago, IL, USA, 22 August 2014; pp. 37–42. [Google Scholar]
- Hinrichs, T.L.; Gude, N.S.; Casado, M.; Mitchell, J.C.; Shenker, S. Practical declarative network management. In Proceedings of the 1st ACM workshop on Research on Enterprise Networking, Barcelona, Spain, 21 August 2009; ACM: New York, NY, USA, 2009; pp. 1–10. [Google Scholar]
- Voellmy, A.; Agarwal, A.; Hudak, P. Nettle: Functional Reactive Programming for Openflow Networks; Yale University New Haven Ct Department of Computer Science: New Haven, CT, USA, 2010. [Google Scholar]
- Voellmy, A.; Kim, H.; Feamster, N. Procera: A language for high-level reactive network control. In Proceedings of the First Workshop on Hot Topics in Software Defined Networks, Helsinki, Finland, 13 August 2012; pp. 43–48. [Google Scholar]
- Foster, N.; Freedman, M.J.; Harrison, R.; Rexford, J.; Meola, M.L.; Walker, D. Frenetic: A high-level language for OpenFlow networks. In Proceedings of the Workshop on Programmable Routers for Extensible Services of Tomorrow, Philadelphia, PA, USA, 30 November 2010; ACM: New York, NY, USA, 2010; pp. 1–6. [Google Scholar]
- Kim, H.; Reich, J.; Gupta, A.; Shahbaz, M.; Feamster, N.; Clark, R. Kinetic: Verifiable dynamic network control. In Proceedings of the 12th USENIX Symposium on Networked Systems Design and Implementation (NSDI, Oakland, CA, USA, 4–6 May 2015; pp. 59–72. [Google Scholar]
- Batista, B.L.A.; Fernandez, M.P. Ponderflow: A new policy specification language to sdn openflow-based networks. Int. J. Adv. Netw. Serv. 2014, 7, 163–172. [Google Scholar]
- Voellmy, A.; Wang, J.; Yang, Y.R.; Ford, B.; Hudak, P. Maple: Simplifying SDN programming using algorithmic policies. ACM SIGCOMM Comput. Commun. Rev. 2013, 43, 87–98. [Google Scholar] [CrossRef]
- Soulé, R.; Basu, S.; Marandi, P.J.; Pedone, F.; Kleinberg, R.; Sirer, E.G.; Foster, N. Merlin: A language for managing network resources. IEEE/ACM Trans. Netw. 2018, 26, 2188–2201. [Google Scholar] [CrossRef]
- Shalimov, A.; Zuikov, D.; Zimarina, D.; Pashkov, V.; Smeliansky, R. Advanced study of SDN/OpenFlow controllers. In Proceedings of the 9th Central & Eastern European Software Engineering Conference in Russia, Moscow, Russia, 24–25 October 2013; ACM: New York, NY, USA, 2013; pp. 1–6. [Google Scholar]
- Haleplidis, E.; Salim, J.H.; Halpern, J.M.; Hares, S.; Pentikousis, K.; Ogawa, K.; Wang, W.; Denazis, S.; Koufopavlou, O. Network programmability with ForCES. IEEE Commun. Surv. Tutor. 2015, 17, 1423–1440. [Google Scholar] [CrossRef]
- Paliwal, M.; Shrimankar, D.; Tembhurne, O. Controllers in SDN: A review report. IEEE Access 2018, 6, 36256–36270. [Google Scholar] [CrossRef]
- Li, S.; Hu, D.; Fang, W.; Ma, S.; Chen, C.; Huang, H.; Zhu, Z. Protocol oblivious forwarding (POF): Software-defined networking with enhanced programmability. IEEE Netw. 2017, 31, 58–66. [Google Scholar] [CrossRef]
- Eadala, S.Y.; Nagarajan, V. A review on deployment architectures of path computation element using software defined networking paradigm. Indian J. Sci. Technol. 2016, 9, 1–10. [Google Scholar] [CrossRef]
- Bianchi, G.; Bonola, M.; Capone, A.; Cascone, C. Openstate: Programming platform-independent stateful openflow applications inside the switch. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 44–51. [Google Scholar] [CrossRef]
- Rotsos, C.; King, D.; Farshad, A.; Bird, J.; Fawcett, L.; Georgalas, N.; Gunkel, M.; Shiomoto, K.; Wang, A.; Mauthe, A.; et al. Network service orchestration standardization: A technology survey. Comput. Stand. Interfaces 2017, 54, 203–215. [Google Scholar] [CrossRef]
- Bannour, F.; Souihi, S.; Mellouk, A. Distributed SDN control: Survey, taxonomy, and challenges. IEEE Commun. Surv. Tutor. 2017, 20, 333–354. [Google Scholar] [CrossRef]
- Berde, P.; Gerola, M.; Hart, J.; Higuchi, Y.; Kobayashi, M.; Koide, T.; Lantz, B.; O’Connor, B.; Radoslavov, P.; Snow, W.; et al. ONOS: Towards an open, distributed SDN OS. In Proceedings of the third workshop on Hot topics in software defined networking, Chicago, IL, USA, 22 August 2014; ACM: New York, NY, USA, 2014; pp. 1–6. [Google Scholar]
- Koponen, T.; Casado, M.; Gude, N.; Stribling, J.; Poutievski, L.; Zhu, M.; Ramanathan, R.; Iwata, Y.; Inoue, H.; Hama, T.; et al. Onix: A distributed control platform for large-scale production networks. OSDI 2010, 10, 6. [Google Scholar]
- Kurniawan, M.T.; Moszardo, I.; Almaarif, A. Network Slicing On Software Defined Network Using Flowvisor and POX Controller To Flowspace Isolation Enforcement. In Proceedings of the 2022 10th International Conference on Smart Grid (icSmartGrid), Istanbul, Turkey, 27–29 June 2022; pp. 29–34. [Google Scholar]
- Nurkahfi, G.N.; Mitayani, A.; Mardiana, V.A.; Dinata, M.M.M. Comparing flowvisor and open virtex as SDN-based site-to-site VPN services solution. In Proceedings of the 2019 International Conference on Radar, Antenna, Microwave, Electronics, and Telecommunications (ICRAMET), Tangerang, Indonesia, 23–24 October 2019; IEEE: Toulouse, France, 2019; pp. 142–147. [Google Scholar]
- Drutskoy, D.A. Software-Defined Network Virtualization with FlowN. Ph.D. Thesis, Princeton University, Princeton, NJ, USA, 2012. [Google Scholar]
- Blenk, A.; Basta, A.; Kellerer, W. HyperFlex: An SDN virtualization architecture with flexible hypervisor function allocation. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; IEEE: Toulouse, France, 2015; pp. 397–405. [Google Scholar]
- Yoo, Y.; Yang, G.; Lee, J.; Shin, C.; Kim, H.; Yoo, C. TeaVisor: Network Hypervisor for Bandwidth Isolation in SDN-NV. IEEE Trans. Cloud Comput. 2022, 1–17. [Google Scholar] [CrossRef]
- Ijari, P. Comparison between Cisco ACI and VMWARE NSX. IOSR J. Comput. Eng. (IOSR-JCE) 2017, 19, 70–72. [Google Scholar] [CrossRef]
- Tello, A.M.D.; Abolhasan, M. SDN controllers scalability and performance study. In Proceedings of the 2019 13th International conference on signal processing and communication systems (ICSPCS), Gold Coast, QLD, 16–18 December 2019; pp. 1–10. [Google Scholar]
- Hassas Yeganeh, S.; Ganjali, Y. Kandoo: A framework for efficient and scalable offloading of control applications. In Proceedings of the First Workshop on Hot Topics in Software Defined Networks, Helsinki, Finland, 13 August 2012; ACM: New York, NY, USA, 2012; pp. 19–24. [Google Scholar]
- Santos, M.A.; Nunes, B.A.; Obraczka, K.; Turletti, T.; De Oliveira, B.T.; Margi, C.B. Decentralizing SDN’s control plane. In Proceedings of the 39th Annual IEEE Conference on Local Computer Networks, Edmonton, AB, Canada, 8–11 September 2014; IEEE: Toulouse, France, 2014; pp. 402–405. [Google Scholar]
- Curtis, A.R.; Mogul, J.C.; Tourrilhes, J.; Yalagandula, P.; Sharma, P.; Banerjee, S. DevoFlow: Scaling flow management for high-performance networks. In Proceedings of the ACM SIGCOMM 2011 Conference, Toronto, ON, Canada, 15–19 August 2011; ACM: New York, NY, USA, 2011; pp. 254–265. [Google Scholar]
- Ku, I.; Lu, Y.; Gerla, M.; Gomes, R.L.; Ongaro, F.; Cerqueira, E. Towards software-defined VANET: Architecture and services. In Proceedings of the 2014 13th annual Mediterranean Ad Hoc Networking Workshop (MED-HOC-NET), Piran, Slovenia, 2–4 June 2014; IEEE: Toulouse, France, 2014; pp. 103–110. [Google Scholar]
- Salman, O.; Elhajj, I.H.; Kayssi, A.; Chehab, A. SDN controllers: A comparative study. In Proceedings of the 2016 18th Mediterranean Electrotechnical Conference (MELECON), Lemesos, Cyprus, 18–20 April 2016; IEEE: Toulouse, France, 2016; pp. 1–6. [Google Scholar]
- Erickson, D. The beacon openflow controller. In Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, Hong Kong, China, 16 August 2015; ACM: New York, NY, USA, 2013; pp. 13–18. [Google Scholar]
- Al-Alaj, A.; Sandhu, R.; Krishnan, R. A formal access control model for se-floodlight controller. In Proceedings of the ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, Richardson, TX, USA, 27 March 2019; ACM: New York, NY, USA, 2019; pp. 1–6. [Google Scholar]
- Vahlenkamp, M.; Schneider, F.; Kutscher, D.; Seedorf, J. Enabling information centric networking in IP networks using SDN. In Proceedings of the 2013 IEEE SDN for Future Networks and Services (SDN4FNS), Trento, Italy, 11–13 November 2013; IEEE: Toulouse, France, 2013; pp. 1–6. [Google Scholar]
- Sheikh, M.N.A.; Halder, M. SDN-Based approach to evaluate the best controller: Internal controller NOX and external controllers POX, ONOS, RYU. Glob. J. Comput. Sci. Technol. 2019, 19, 21–32. [Google Scholar] [CrossRef]
- Banikazemi, M.; Olshefski, D.; Shaikh, A.; Tracey, J.; Wang, G. Meridian: An SDN platform for cloud network services. IEEE Commun. Mag. 2013, 51, 120–127. [Google Scholar] [CrossRef]
- Vladyko, A.; Muthanna, A.; Kirichek, R. Comprehensive SDN testing based on model network. In Internet of Things, Smart Spaces, and Next Generation Networks and Systems: 16th International Conference, NEW2AN 2016, and 9th Conference, ruSMART, St. Petersburg, Russia, 26–28 September 2016; Proceedings 16; Springer International Publishing: Berlin/Heidelberg, Germany, 2016; pp. 539–549. [Google Scholar]
- Botelho, F.; Bessani, A.; Ramos, F.M.; Ferreira, P. On the design of practical fault-tolerant SDN controllers. In Proceedings of the 2014 Third European Workshop on Software Defined Networks, Budapest, Hungary, 1–3 September 2014; IEEE: Toulouse, France, 2014; pp. 73–78. [Google Scholar]
- Katta, N.; Zhang, H.; Freedman, M.; Rexford, J. Ravana: Controller fault-tolerance in software-defined networking. In Proceedings of the 1st ACM SIGCOMM Symposium on Software Defined Networking Research, Santa Clara, CA, USA, 17–18 June 2015; ACM: New York, NY, USA, 2015; pp. 1–12. [Google Scholar]
- Cowen, L.J. Compact routing with minimum stretch. J. Algorithms 2001, 38, 170–183. [Google Scholar] [CrossRef]
- Fu, Y.; Bi, J.; Gao, K.; Chen, Z.; Wu, J.; Hao, B. Orion: A hybrid hierarchical control plane of software-defined networking for large-scale networks. In Proceedings of the 2014 IEEE 22nd International Conference on Network Protocols, Raleigh, NC, USA, 21–24 October 2014; IEEE: Toulouse, France, 2014; pp. 569–576. [Google Scholar]
- Marconett, D.; Yoo, S.B. Flowbroker: A software-defined network controller architecture for multi-domain brokering and reputation. J. Netw. Syst. Manag. 2015, 23, 328–359. [Google Scholar] [CrossRef]
- Jain, S.; Kumar, A.; Mandal, S.; Ong, J.; Poutievski, L.; Singh, A.; Venkata, S.; Wanderer, J.; Zhou, J.; Zhu, M.; et al. B4: Experience with a globally-deployed software defined WAN. ACM SIGCOMM Comput. Commun. Rev. 2013, 43, 3–14. [Google Scholar] [CrossRef]
- Yap, K.K.; Motiwala, M.; Rahe, J.; Padgett, S.; Holliman, M.; Baldus, G.; Hines, M.; Kim, T.; Narayanan, A.; Jain, A.; et al. Taking the edge off with espresso: Scale, reliability and programmability for global internet peering. In Proceedings of the Conference of the ACM Special Interest Group on Data Communication, Los Angeles, CA, USA, 21–25 August 2017; ACM: New York, NY, USA, 2017; pp. 432–445. [Google Scholar]
- McCauley, J.; Panda, A.; Casado, M.; Koponen, T.; Shenker, S. Extending SDN to large-scale networks. Open Netw. Summit 2013, 1–2. [Google Scholar]
- Schriegel, S.; Kobzan, T.; Jasperneite, J. Investigation on a distributed SDN control plane architecture for heterogeneous time sensitive networks. In Proceedings of the 2018 14th IEEE International Workshop on Factory Communication Systems (WFCS), Imperia, Italy, 13–15 June 2018; IEEE: Toulouse, France, 2018; pp. 1–10. [Google Scholar]
- Phemius, K.; Bouet, M.; Leguay, J. DISCO: Distributed SDN controllers in a multi-domain environment. In Proceedings of the 2014 IEEE Network Operations and Management Symposium (NOMS), Krakow, Poland, 5–9 May 2014; IEEE: Toulouse, France, 2014. [Google Scholar]
- Gupta, A.; Vanbever, L.; Shahbaz, M.; Donovan, S.P.; Schlinker, B.; Feamster, N.; Rexford, J.; Shenker, S.; Clark, R.; Katz-Bassett, E. Sdx: A software defined internet exchange. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 551–562. [Google Scholar] [CrossRef]
- Stringer, J.; Pemberton, D.; Fu, Q.; Lorier, C.; Nelson, R.; Bailey, J.; Corrêa, C.N.; Rothenberg, C.E. Cardigan: SDN distributed routing fabric going live at an Internet exchange. In Proceedings of the 2014 IEEE Symposium on Computers and Communications (ISCC), Funchal, Portugal, 23–26 June 2014; IEEE: Toulouse, France, 2014; pp. 1–7. [Google Scholar]
- Chung, J.; Cox, J.; Ibarra, J.; Bezerra, J.; Morgan, H.; Clark, R.; Owen, H. AtlanticWave-SDX: An international SDX to support science data applications. In Proceedings of the Software Defined Networking (SDN) for Scientific Networking Workshop, Online, 20 November 2015; Volume 15, pp. 1–7. [Google Scholar]
- Dey, P.K.; Yuksel, M. Hybrid cloud integration of routing control & data planes. In Proceedings of the 2016 ACM Workshop on Cloud-Assisted Networking, Irvine, CA, USA, 12 December 2016; ACM: New York, NY, USA, 2016; pp. 25–30. [Google Scholar]
- Wang, W.; He, W.; Su, J. Enhancing the effectiveness of traffic engineering in hybrid SDN. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; IEEE: Toulouse, France, 2017; pp. 1–6. [Google Scholar]
- Yu, M.; Rexford, J.; Freedman, M.J.; Wang, J. Scalable flow-based networking with DIFANE. ACM SIGCOMM Comput. Commun. Rev. 2010, 40, 351–362. [Google Scholar] [CrossRef] [Green Version]
- Feng, T.; Bi, J. OpenRouteFlow: Enable legacy router as a software-defined routing service for hybrid SDN. In Proceedings of the 2015 24th International Conference on Computer Communication and Networks (ICCCN), Las Vegas, NV, USA, 3–6 August 2015; IEEE: Toulouse, France, 2015; pp. 1–8. [Google Scholar]
- Vissicchio, S.; Vanbever, L.; Rexford, J. Sweet little lies: Fake topologies for flexible routing. In Proceedings of the 13th ACM Workshop on Hot Topics in Networks, Los Angeles, CA, USA, 27–28 October 2014; ACM: New York, NY, USA, 2014; pp. 1–7. [Google Scholar]
- Kaur, S.; Singh, J.; Ghumman, N.S. Network programmability using POX controller. In ICCCS International Conference on Communication, Computing & Systems; IEEE: Toulouse, France, 2014; Volume 138, p. 70. [Google Scholar]
- Huang, S.; Zhao, J.; Wang, X. HybridFlow: A lightweight control plane for hybrid SDN in enterprise networks. In Proceedings of the 2016 IEEE/ACM 24th International Symposium on Quality of Service (IWQoS), Beijing, China, 20–21 June 2016; IEEE: Toulouse, France, 2016; pp. 1–2. [Google Scholar]
- Kandoi, R.; Antikainen, M. Denial-of-service attacks in OpenFlow SDN networks. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; IEEE: Toulouse, France, 2015; pp. 1322–1326. [Google Scholar]
- Gonzalez, C.; Flauzac, O.; Nolot, F.; Jara, A. A novel distributed SDN-secured architecture for the IoT. In Proceedings of the 2016 International Conference on Distributed Computing in Sensor Systems (DCOSS), Washington, DC, USA, 26–28 May 2016; IEEE: Toulouse, France, 2016; pp. 244–249. [Google Scholar]
- Nguyen, T.G.; Phan, T.V.; Hoang, D.T.; Nguyen, T.N.; So-In, C. Efficient SDN-based traffic monitoring in IoT networks with double deep Q-network. In Proceedings of the Computational Data and Social Networks: 9th International Conference, CSoNet 2020, Dallas, TX, USA, 11–13 December 2020; Springer International Publishing: Cham, Switzerland, 2021; pp. 26–38. [Google Scholar]
- Li, F.; Cao, J.; Wang, X.; Sun, Y.; Pan, T.; Liu, X. Adopting SDN switch buffer: Benefits analysis and mechanism design. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 2171–2176. [Google Scholar]
- Zhang, C.; Hu, G.; Chen, G.; Sangaiah, A.K.; Zhang, P.A.; Yan, X.; Jiang, W. Towards a SDN-based integrated architecture for mitigating IP spoofing attack. IEEE Access 2017, 6, 22764–22777. [Google Scholar] [CrossRef]
- Achleitner, S.; La Porta, T.; Jaeger, T.; McDaniel, P. Adversarial network forensics in software defined networking. In Proceedings of the Symposium on SDN Research, Santa Clara, CA, USA, 3–4 April 2017; pp. 8–20. [Google Scholar]
- Jin, C.; Lumezanu, C.; Xu, Q.; Mekky, H.; Zhang, Z.L.; Jiang, G. Magneto: Unified fine-grained path control in legacy and openflow hybrid networks. In Proceedings of the Symposium on SDN Research, Santa Clara, CA, USA, 3–4 April 2017; pp. 75–87. [Google Scholar]
- Lorenz, C.; Hock, D.; Scherer, J.; Durner, R.; Kellerer, W.; Gebert, S.; Gray, N.; Zinner, T.; Tran-Gia, P. An SDN/NFV-enabled enterprise network architecture offering fine-grained security policy enforcement. IEEE Commun. Mag. 2017, 55, 217–223. [Google Scholar] [CrossRef]
- Wang, Y.; Bi, J.; Lin, P.; Lin, Y.; Zhang, K. SDI: A multi-domain SDN mechanism for fine-grained inter-domain routing. Ann. Telecommun. 2016, 71, 625–637. [Google Scholar] [CrossRef]
- Huang, J.; He, Y.; Duan, Q.; Yang, Q.; Wang, W. Admission control with flow aggregation for QoS provisioning in software-defined network. In Proceedings of the 2014 IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 1182–1186. [Google Scholar]
- Zhang, X.; Cheng, Z.; Lin, R.; He, L.; Yu, S.; Luo, H. Local fast reroute with flow aggregation in software defined networks. IEEE Commun. Lett. 2016, 21, 785–788. [Google Scholar] [CrossRef]
- Lu, Y.; Fu, B.; Xi, X.; Zhang, Z.; Wu, H. An SDN-based flow control mechanism for guaranteeing QoS and maximizing throughput. Wirel. Pers. Commun. 2017, 97, 417–442. [Google Scholar] [CrossRef]
- Ajaeiya, G.A.; Adalian, N.; Elhajj, I.H.; Kayssi, A.; Chehab, A. Flow-based intrusion detection system for SDN. In Proceedings of the 2017 IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017; pp. 787–793. [Google Scholar]
- Huang, N.; Li, Q.; Lin, D.; Lit, X.; Shen, G.; Jiang, Y. Software-defined label switching: Scalable per-flow control in SDN. In Proceedings of the 2018 IEEE/ACM 26th International Symposium on Quality of Service (IWQoS), Banff, AB, Canada, 4–6 June 2018; pp. 1–10. [Google Scholar]
- Kosugiyama, T.; Tanabe, K.; Nakayama, H.; Hayashi, T.; Yamaoka, K. A flow aggregation method based on end-to-end delay in SDN. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Dridi, L.; Zhani, M.F. SDN-guard: DoS attacks mitigation in SDN networks. In Proceedings of the 2016 5th IEEE International Conference on Cloud Networking (Cloudnet), Pisa, Italy, 3–5 October 2016; pp. 212–217. [Google Scholar]
- Malboubi, M.; Wang, L.; Chuah, C.N.; Sharma, P. Intelligent SDN based traffic (de) aggregation and measurement paradigm (iSTAMP). In Proceedings of the IEEE INFOCOM 2014—IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 934–942. [Google Scholar]
- Hyder, M.F.; Ismail, M.A. Securing control and data planes from reconnaissance attacks using distributed shadow controllers, reactive and proactive approaches. IEEE Access 2021, 9, 21881–21894. [Google Scholar] [CrossRef]
- Bianco, A.; Giaccone, P.; Mashayekhi, R.; Ullio, M.; Vercellone, V. Scalability of ONOS reactive forwarding applications in ISP networks. Comput. Commun. 2017, 102, 130–138. [Google Scholar] [CrossRef] [Green Version]
- Dusi, M.; Bifulco, R.; Gringoli, F.; Schneider, F. Reactive logic in software-defined networking: Measuring flow-table requirements. In Proceedings of the 2014 International Wireless Communications and Mobile Computing Conference (IWCMC), Nicosia, Cyprus, 4–8 August 2014; pp. 340–345. [Google Scholar]
- Petroulakis, N.E.; Fysarakis, K.; Askoxylakis, I.; Spanoudakis, G. Reactive security for SDN/NFV-enabled industrial networks leveraging service function chaining. Trans. Emerg. Telecommun. Technol. 2018, 29, e3269. [Google Scholar] [CrossRef] [Green Version]
- Zerkane, S.; Espes, D.; Le Parc, P.; Cuppens, F. Software defined networking reactive stateful firewall. In ICT Systems Security and Privacy Protection: 31st IFIP TC 11 International Conference, SEC 2016, Ghent, Belgium, 30 May–1 June 2016; Proceedings 31; Springer International Publishing: Cham, Switzerland, 2016; pp. 119–132. [Google Scholar]
- Hamza, A.; Gharakheili, H.H.; Sivaraman, V. Combining MUD policies with SDN for IoT intrusion detection. In Proceedings of the 2018 Workshop on IoT Security and Privacy, Budapest, Hungary, 20 August 2018; pp. 1–7. [Google Scholar]
- Singh, M.P.; Bhandari, A. New-flow based DDoS attacks in SDN: Taxonomy, rationales, and research challenges. Comput. Commun. 2020, 154, 509–527. [Google Scholar] [CrossRef]
- Thakur, A.K.S.; Rawat, S. Utility Based Framework for Reactive and Proactive Congestion Control in SDN. In Proceedings of the 2021 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Hyderabad, India, 13–16 December 2021; pp. 396–401. [Google Scholar]
- Braun, W.; Menth, M. Software-defined networking using OpenFlow: Protocols, applications and architectural design choices. Future Internet 2014, 6, 302–336. [Google Scholar] [CrossRef]
- Abou El Houda, Z.; Khoukhi, L.; Hafid, A. Chainsecure-a scalable and proactive solution for protecting blockchain applications using sdn. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Azab, M.; Fortes, J.A. Towards proactive SDN-controller attack and failure resilience. In Proceedings of the 2017 International Conference on Computing, Networking and Communications (ICNC), Santa Clara, CA, USA, 26–29 January 2017; pp. 442–448. [Google Scholar]
- Zhou, Y.; Cheng, G.; Yu, S. An SDN-enabled proactive defense framework for DDoS mitigation in IoT networks. IEEE Trans. Inf. Forensics Secur. 2021, 16, 5366–5380. [Google Scholar] [CrossRef]
- Shakeri, S.; Parsaeefard, S.; Derakhshani, M. Proactive admission control and dynamic resource management in SDN-based virtualized networks. In Proceedings of the 2017 8th International Conference on the Network of the Future (NOF), London, UK, 22–24 November 2017; pp. 46–51. [Google Scholar]
- Nadar, S.; Chaudhari, S. Proactive-routing path update in Software Defined Networks (SDN). In Proceedings of the 2017 International Conference on Intelligent Computing and Control (I2C2), Coimbatore, India, 23–24 June 2017; pp. 1–3. [Google Scholar]
- Padma, V.; Yogesh, P. Proactive failure recovery in OpenFlow based software defined networks. In Proceedings of the 2015 3rd International Conference on Signal Processing, Communication and Networking (ICSCN), Chennai, India, 26–28 March 2015; pp. 1–6. [Google Scholar]
- Aslan, M.; Matrawy, A. Adaptive consistency for distributed SDN controllers. In Proceedings of the 2016 17th International Telecommunications Network Strategy and Planning Symposium (Networks), Warsaw, Poland, 27–30 September 2016; pp. 150–157. [Google Scholar]
- Semong, T.; Maupong, T.; Anokye, S.; Kehulakae, K.; Dimakatso, S.; Boipelo, G.; Sarefo, S. Intelligent load balancing techniques in software defined networks: A survey. Electronics 2020, 9, 1091. [Google Scholar] [CrossRef]
- Hanmer, R.; Jagadeesan, L.; Mendiratta, V.; Zhang, H. Friend or foe: Strong consistency vs. overload in high-availability distributed systems and SDN. In Proceedings of the 2018 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW), Memphis, TN, USA, 15–18 October 2018; pp. 59–64. [Google Scholar]
- Bannour, F.; Souihi, S.; Mellouk, A. Adaptive state consistency for distributed onos controllers. In Proceedings of the 2018 IEEE Global Communications Conference (Globecom), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–7. [Google Scholar]
- Sakic, E.; Sardis, F.; Guck, J.W.; Kellerer, W. Towards adaptive state consistency in distributed SDN control plane. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–7. [Google Scholar]
- Ahmad, S.; Mir, A.H. Scalability, consistency, reliability and security in SDN controllers: A survey of diverse SDN controllers. J. Netw. Syst. Manag. 2021, 29, 9. [Google Scholar] [CrossRef]
- Nougnanke, K.B.; Bruyere, M.; Labit, Y. Low-overhead near-real-time flow statistics collection in SDN. In Proceedings of the 2020 6th IEEE Conference on Network Softwarization (NetSoft), Ghent, Belgium, 29 June–3 July 2020; pp. 155–159. [Google Scholar]
- Miguel, C.J.; Neto, F.J.; Santos, J.A.; Sampaio, P.N. Data collection in sdn networks with contextual analysis. In Proceedings of the 2019 14th Iberian Conference on Information Systems and Technologies (CISTI), Coimbra, Portugal, 19–22 June 2019; pp. 1–6. [Google Scholar]
- Lin, H.; Yan, Z.; Chen, Y.; Zhang, L. A survey on network security-related data collection technologies. IEEE Access 2018, 6, 18345–18365. [Google Scholar] [CrossRef]
- EL-Garoui, L.; Pierre, S.; Chamberland, S. A new SDN-based routing protocol for improving delay in smart city environments. Smart Cities 2020, 3, 1004–1021. [Google Scholar] [CrossRef]
- Zhu, M.; Cao, J.; Pang, D.; He, Z.; Xu, M. SDN-based routing for efficient message propagation in VANET. In Wireless Algorithms, Systems, and Applications: 10th International Conference, WASA 2015, Qufu, China, 10–12 August 2015; Proceedings 10; Springer International Publishing: Cham, Switzerland, 2015; pp. 788–797. [Google Scholar]
- Amokrane, A.; Langar, R.; Boutaba, R.; Pujolle, G. Flow-based management for energy efficient campus networks. IEEE Trans. Netw. Serv. Manag. 2015, 12, 565–579. [Google Scholar] [CrossRef]
- Dutra, D.L.C.; Bagaa, M.; Taleb, T.; Samdanis, K. Ensuring end-to-end QoS based on multi-paths routing using SDN technology. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Muthumanikandan, V.; Valliyammai, C. Link failure recovery using shortest path fast rerouting technique in SDN. Wirel. Pers. Commun. 2017, 97, 2475–2495. [Google Scholar] [CrossRef]
- Moghaddam, F.F.; Wieder, P.; Yahyapour, R. Policy Engine as a Service (PEaaS): An approach to a reliable policy management framework in cloud computing environments. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria, 22–24 August 2016; pp. 137–144. [Google Scholar]
- Polčák, L.; Caldarola, L.; Choukir, A.; Cuda, D.; Dondero, M.; Ficara, D.; Franková, B.; Holkovič, M.; Muccifora, R.; Trifilo, A. High level policies in SDN. In E-Business and Telecommunications: 12th International Joint Conference, ICETE 2015, Colmar, France, 20–22 July 2015; Revised Selected Papers 12; Springer International Publishing: Cham, Switzerland, 2016; pp. 39–57. [Google Scholar]
- Maldonado-Lopez, F.A.; Calle, E.; Donoso, Y. Detection and prevention of firewall-rule conflicts on software-defined networking. In Proceedings of the 2015 7th International Workshop on Reliable Networks Design and Modeling (RNDM), Munich, Germany, 5–7 October 2015; pp. 259–265. [Google Scholar]
- Bari, M.F.; Chowdhury, S.R.; Ahmed, R.; Boutaba, R. PolicyCop: An autonomic QoS policy enforcement framework for software defined networks. In Proceedings of the 2013 IEEE SDN for Future Networks and Services (SDN4FNS), Trento, Italy, 11–13 November 2013; pp. 1–7. [Google Scholar]
- Sevilla, M.A.; Maltzahn, C.; Alvaro, P.; Nasirigerdeh, R.; Settlemyer, B.W.; Perez, D.; Rich, D.; Shipman, G.M. Programmable caches with a data management language and policy engine. In Proceedings of the 2018 18th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGRID), Washington, DC, USA, 1–4 May 2018; pp. 203–212. [Google Scholar]
- Kao, M.T.; Huang, B.X.; Kao, S.J.; Tseng, H.W. An effective routing mechanism for link congestion avoidance in software-defined networking. In Proceedings of the 2016 International Computer Symposium (ICS), Chiayi, Taiwan, 15–17 December 2016; pp. 154–158. [Google Scholar]
- Zehra, U.; Shah, M.A. A survey on resource allocation in software defined networks (SDN). In Proceedings of the 2017 23rd International Conference on Automation and Computing (ICAC), Huddersfield, UK, 7–8 September 2017; pp. 1–6. [Google Scholar]
- Henni, D.E.; Ghomari, A.; Hadjadj-Aoul, Y. A consistent QoS routing strategy for video streaming services in SDN networks. Int. J. Communic. Syst. 2020, 33, e4177. [Google Scholar] [CrossRef] [Green Version]
- Capone, A.; Cascone, C.; Nguyen, A.Q.; Sanso, B. Detour planning for fast and reliable failure recovery in SDN with OpenState. In Proceedings of the 2015 11th International Conference on the Design of Reliable Communication Networks (DRCN), Vilanova, Spain, 28–31 March 2015; pp. 25–32. [Google Scholar]
- Reich, J.; Monsanto, C.; Foster, N.; Rexford, J.; Walker, D. Modular SDN Programming with Pyretic; Technical Reprot of USENIX; USENIX: Berkeley, CA, USA, 2013; 30p. [Google Scholar]
- Yang, G.; Jin, H.; Kang, M.; Moon, G.J.; Yoo, C. Network monitoring for SDN virtual networks. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications, Virtual, 6–9 July 2020; pp. 1261–1270. [Google Scholar]
- Li, Y.; Chen, M. Software-defined network function virtualization: A survey. IEEE Access 2015, 3, 2542–2553. [Google Scholar]
- Chen, Y.J.; Wang, L.C.; Lin, F.Y.; Lin, B.S.P. Deterministic quality of service guarantee for dynamic service chaining in software defined networking. IEEE Trans. Netw. Serv. Manag. 2017, 14, 991–1002. [Google Scholar] [CrossRef]
- Martini, B.; Paganelli, F.; Mohammed, A.A.; Gharbaoui, M.; Sgambelluri, A.; Castoldi, P. SDN controller for context-aware data delivery in dynamic service chaining. In Proceedings of the 2015 1st IEEE Conference on Network Softwarization (NetSoft), London, UK, 13–17 April 2015; pp. 1–5. [Google Scholar]
- Da Costa Cordeiro, W.L.; Marques, J.A.; Gaspary, L.P. Data plane programmability beyond openflow: Opportunities and challenges for network and service operations and management. J. Netw. Syst. Manag. 2017, 25, 784–818. [Google Scholar] [CrossRef]
- Tseng, J.; Wang, R.; Tsai, J.; Edupuganti, S.; Min, A.W.; Woo, S.; Junkins, S.; Tai, T.Y.C. Exploiting integrated GPUs for network packet processing workloads. In Proceedings of the 2016 IEEE NetSoft Conference and Workshops (NetSoft), Seoul, Republic of Korea, 6–10 June 2016; pp. 161–165. [Google Scholar]
- Dane, L.; Gurkan, D. GENI with a network processing unit: Enriching SDN application experiments. In Proceedings of the 2014 Third GENI Research and Educational Experiment Workshop, Atlanta, GA, USA, 19–20 March 2014; pp. 9–14. [Google Scholar]
- Han, S.; Jang, K.; Park, K.; Moon, S. PacketShader: A GPU-accelerated software router. ACM SIGCOMM Comput. Commun. Rev. 2010, 40, 195–206. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Bohlooli, A.; Jamshidi, K. Performance improvement and hardware implementation of open flow switch using FPGA. In Proceedings of the 2019 5th Conference on Knowledge Based Engineering and Innovation (KBEI), Tehran, Iran, 28 February–1 March 2019; pp. 515–520. [Google Scholar]
- Khattak, M.K.; Tang, Y.; Khan, U.S. TOSwitch: Programmable and high-throughput switch using hybrid switching chips. IEEE Commun. Lett. 2019, 23, 2266–2270. [Google Scholar] [CrossRef]
- Lu, G.; Miao, R.; Xiong, Y.; Guo, C. Using cpu as a traffic co-processing unit in commodity switches. In Proceedings of the First Workshop on Hot Topics in Software Defined Networks, Helsinki, Finland, 13 August 2012; pp. 31–36. [Google Scholar]
- Csikor, L.; Szalay, M.; Rétvári, G.; Pongrácz, G.; Pezaros, D.P.; Toka, L. Transition to SDN is HARMLESS: Hybrid architecture for migrating legacy ethernet switches to SDN. IEEE/ACM Trans. Netw. 2020, 28, 275–288. [Google Scholar] [CrossRef] [Green Version]
- Rahimi, R.; Veeraraghavan, M.; Nakajima, Y.; Takahashi, H.; Okamoto, S.; Yamanaka, N. A high-performance OpenFlow software switch. In Proceedings of the 2016 IEEE 17th International Conference on High Performance Switching and Routing (HPSR), Yokohama, Japan, 14–17 June 2016; pp. 93–99. [Google Scholar]
- Chen, T.S.; Lee, D.Y.; Liu, T.T.; Wu, A.Y. Dynamic reconfigurable ternary content addressable memory for OpenFlow-compliant low-power packet processing. IEEE Trans. Circuits Syst. I Regul. Pap. 2016, 63, 1661–1672. [Google Scholar] [CrossRef]
- Lee, D.Y.; Wang, C.C.; Wu, A.Y. Bundle-updatable SRAM-based TCAM design for openflow-compliant packet processor. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2019, 27, 1450–1454. [Google Scholar] [CrossRef]
- Zhu, H.; Fan, H.; Luo, X.; Jin, Y. Intelligent timeout master: Dynamic timeout for SDN-based data centers. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 734–737. [Google Scholar]
- Luo, S.; Yu, H.; Li, L. Practical flow table aggregation in SDN. Comput. Netw. 2015, 92, 72–88. [Google Scholar] [CrossRef]
- Dong, M.; Li, H.; Ota, K.; Xiao, J. Rule caching in SDN-enabled mobile access networks. IEEE Netw. 2015, 29, 40–45. [Google Scholar] [CrossRef] [Green Version]
- Kanizo, Y.; Hay, D.; Keslassy, I. Palette: Distributing tables in software-defined networks. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 545–549. [Google Scholar]
- Tanyingyong, V.; Hidell, M.; Sjödin, P. Improving pc-based openflow switching performance. In Proceedings of the 6th ACM/IEEE Symposium on Architectures for Networking and Communications Systems, La Jolla, CA, USA, 25–26 October 2010; pp. 1–2. [Google Scholar]
- Tanyingyong, V.; Hidell, M.; Sjödin, P. Using hardware classification to improve pc-based openflow switching. In Proceedings of the 2011 IEEE 12th International Conference on High Performance Switching and Routing, Cartagena, Spain, 4–6 July 2011; pp. 215–221. [Google Scholar]
- Emmerich, P.; Raumer, D.; Wohlfart, F.; Carle, G. Assessing soft- and hardware bottlenecks in PC-based packet forwarding systems. In Proceedings of the ICN 2015—The Fourteenth International Conference on Networks, Barcelona, Spain, 19–24 April 2015; Volume 90. [Google Scholar]
- Lockwood, J.W.; McKeown, N.; Watson, G.; Gibb, G.; Hartke, P.; Naous, J.; Raghuraman, R.; Luo, J. NetFPGA—An open platform for gigabit-rate network switching and routing. In Proceedings of the 2007 IEEE International Conference on Microelectronic Systems Education (MSE’07), San Diego, CA, USA, 3–4 June 2007; pp. 160–161. [Google Scholar]
- Ghaffar, Z.; Alshahrani, A.; Fayaz, M.; Alghamdi, A.M.; Gwak, J. A topical review on machine learning, software defined networking, internet of things applications: Research limitations and challenges. Electronics 2021, 10, 880. [Google Scholar]
- Barrett, R.; Facey, A.; Nxumalo, W.; Rogers, J.; Vatcher, P.; St-Hilaire, M. Dynamic traffic diversion in SDN: Testbed vs. mininet. In Proceedings of the 2017 International Conference on Computing, Networking and Communications (ICNC), Santa Clara, CA, USA, 26–29 January 2017; pp. 167–171. [Google Scholar]
- Tu, W.; Wei, Y.H.; Antichi, G.; Pfaff, B. Revisiting the open vSwitch dataplane ten years later. In Proceedings of the 2021 ACM SIGCOMM 2021 Conference, Virtual Event, 23–27 August 2021; pp. 245–257. [Google Scholar]
- Poutievski, L.; Mashayekhi, O.; Ong, J.; Singh, A.; Tariq, M.; Wang, R.; Zhang, J.; Beauregard, V.; Conner, P.; Gribble, S.; et al. Jupiter evolving: Transforming google’s datacenter network via optical circuit switches and software-defined networking. In Proceedings of the ACM SIGCOMM 2022 Conference, Amsterdam, The Netherlands, 22–26 August 2022; pp. 66–85. [Google Scholar]
- Das, S.; Parulkar, G.; McKeown, N.; Singh, P.; Getachew, D.; Ong, L. Packet and circuit network convergence with OpenFlow. In Proceedings of the 2010 Conference on Optical Fiber Communication (OFC/NFOEC), Collocated National Fiber Optic Engineers Conference, San Diego, CA, USA, 21–25 March 2010; pp. 1–3. [Google Scholar]
- Azodolmolky, S.; Nejabati, R.; Escalona, E.; Jayakumar, R.; Efstathiou, N.; Simeonidou, D. Integrated OpenFlow—GMPLS control plane: An overlay model for software defined packet over optical networks. In Proceedings of the 2011 37th European Conference and Exhibition on Optical Communication, Geneva, Switzerland, 18–22 September 2011; pp. 1–3. [Google Scholar]
- Dizdarević, S.; Dizdarević, H.; Škrbić, M.; Hadžiahmetović, N. A survey on transition from GMPLS control plane for optical multilayer networks to SDN control plane. In Proceedings of the 2016 39th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 30 May–3 June 2016; pp. 537–544. [Google Scholar]
- Xue, X.; Nakamura, F.; Prifti, K.; Pan, B.; Yan, F.; Wang, F.; Guo, X.; Tsuda, H.; Calabretta, N. SDN enabled flexible optical data center network with dynamic bandwidth allocation based on photonic integrated wavelength selective switch. Opt. Express 2020, 28, 8949–8958. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Khan, I.; Tunesi, L.; Masood, M.U.; Ghillino, E.; Bardella, P.; Carena, A.; Curri, V. Automatic management of N × N photonic switch powered by machine learning in software-defined optical transport. IEEE Open J. Commun. Soc. 2021, 2, 1358–1365. [Google Scholar] [CrossRef]
- Wijesekara, P.A.D.S.N.; Sangeeth, W.M.A.K.; Perera, H.S.C.; Jayasundere, N.D. Underwater Acoustic Digital Communication Channel for an UROV. In Proceedings of the 5th Annual Research Symposium (ARS2018), Hapugala, Sri Lanka, 4 January 2018; p. E17. [Google Scholar]
- Wijesekara, P.A.D.S.N.; Sudheera, K.L.K.; Sandamali, G.G.N.; Chong, P.H.J. Data Gathering Optimization in Hybrid Software Defined Vehicular Networks. In Proceedings of the 20th Academic Sessions, Matara, Sri Lanka, 7 June 2023; p. 59. [Google Scholar]
- Chiper, F.L.; Martian, A.; Vladeanu, C.; Marghescu, I.; Craciunescu, R.; Fratu, O. Drone detection and defense systems: Survey and a software-defined radio-based solution. Sensors 2022, 22, 1453. [Google Scholar] [CrossRef]
- Zhang, K.; Zheng, G.; Wang, H.; Zhang, C.; Yu, X. Channel Model and Performance Analysis for MIMO Systems with Single Leaky Coaxial Cable in Tunnel Scenarios. Sensors 2022, 22, 5776. [Google Scholar] [CrossRef] [PubMed]
- Grzechca, D.; Zieliński, D.; Filipowski, W. What is the effect of outer jacket degradation on the communication parameters? A case study of the twisted pair cable applied in the railway industry. Energies 2021, 14, 972. [Google Scholar] [CrossRef]
- Aleksic, S. A survey on optical technologies for IoT, smart industry, and smart infrastructures. J. Sens. Actuator Netw. 2019, 8, 47. [Google Scholar] [CrossRef] [Green Version]
- Burdin, V.A.; Dashkov, M.V.; Demidov, V.V.; Dukelskii, K.V.; Evtushenko, A.S.; Kuznetsov, A.A.; Matrosova, A.S.; Morozov, O.G.; Ter-Nersesyants, E.V.; Vasilets, A.A.; et al. New silica laser-optimized multimode optical fibers with extremely enlarged 100-μm core diameter for gigabit onboard and industrial networks. Fibers 2020, 8, 18. [Google Scholar] [CrossRef] [Green Version]
- Morana, A.; Campanella, C.; Vidalot, J.; De Michele, V.; Marin, E.; Reghioua, I.; Boukenter, A.; Ouerdane, Y.; Paillet, P.; Girard, S. Extreme radiation sensitivity of ultra-low loss pure-silica-core optical fibers at low dose levels and infrared wavelengths. Sensors 2020, 20, 7254. [Google Scholar] [CrossRef]
- Atzeni, D.; Bacciu, D.; Mazzei, D.; Prencipe, G. A Systematic Review of Wi-Fi and Machine Learning Integration with Topic Modeling Techniques. Sensors 2022, 22, 4925. [Google Scholar] [CrossRef]
- Imoize, A.L.; Adedeji, O.; Tandiya, N.; Shetty, S. 6G enabled smart infrastructure for sustainable society: Opportunities, challenges, and research roadmap. Sensors 2021, 21, 1709. [Google Scholar] [CrossRef] [PubMed]
- Alsharif, M.H.; Kelechi, A.H.; Albreem, M.A.; Chaudhry, S.A.; Zia, M.S.; Kim, S. Sixth generation (6G) wireless networks: Vision, research activities, challenges and potential solutions. Symmetry 2020, 12, 676. [Google Scholar] [CrossRef]
- Li, T.; Chen, J.; Fu, H. Application scenarios based on SDN: An overview. J. Phys. Conf. Ser. 2019, 1187, 052067. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Lee, A.; Wang, P.; Luo, M.; Chou, W. A roadmap for traffic engineering in SDN-OpenFlow networks. Comput. Netw. 2014, 71, 1–30. [Google Scholar] [CrossRef]
- Yoo, Y.; Yang, G.; Kang, M.; Yoo, C. Adaptive control channel traffic shaping for virtualized SDN in clouds. In Proceedings of the 2020 IEEE 13th International Conference on Cloud Computing (CLOUD), Beijing, China, 19–23 October 2020; pp. 22–24. [Google Scholar]
- Veisi, F.; Montavont, J.; Theoleyre, F. SDN-TSCH: Enabling Software Defined Networking for Scheduled Wireless Networks with Traffic Isolation. In Proceedings of the 2022 IEEE Symposium on Computers and Communications (ISCC), Rhodes, Greece, 30 June–3 July 2022; pp. 1–7. [Google Scholar]
- Pasca, S.T.V.; Kodali, S.S.P.; Kataoka, K. AMPS: Application aware multipath flow routing using machine learning in SDN. In Proceedings of the 2017 Twenty-third National Conference on Communications (NCC), Chennai, India, 2–4 March 2017; pp. 1–6. [Google Scholar]
- Pham, T.A.Q.; Hadjadj-Aoul, Y.; Outtagarts, A. Deep reinforcement learning based qos-aware routing in knowledge-defined networking. In Quality, Reliability, Security and Robustness in Heterogeneous Systems: 14th EAI International Conference, Ho Chi Minh City, Vietnam, 3–4 December 2018; Proceedings 14; Springer International Publishing: Cham, Switzerland, 2019; pp. 14–26. [Google Scholar]
- Cheng, L.C.; Wang, K.; Hsu, Y.H. Application-aware routing scheme for SDN-based cloud datacenters. In Proceedings of the 2015 Seventh International Conference on Ubiquitous and Future Networks, Sapporo, Japan, 7–10 July 2015; pp. 820–825. [Google Scholar]
- Chahlaoui, F.; Dahmouni, H. A taxonomy of load balancing mechanisms in centralized and distributed SDN architectures. SN Comput. Sci. 2020, 1, 268. [Google Scholar] [CrossRef]
- Zakia, U.; Yedder, H.B. Dynamic load balancing in SDN-based data center networks. In Proceedings of the 2017 8th IEEE Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 3–5 October 2017; pp. 242–247. [Google Scholar]
- Hai, N.T.; Kim, D.S. Efficient load balancing for multi-controller in SDN-based mission-critical networks. In Proceedings of the 2016 IEEE 14th International Conference on Industrial Informatics (INDIN), Poitiers, France, 19–21 July 2016; pp. 420–425. [Google Scholar]
- Chen, J.; Wang, Y.; Huang, X.; Xie, X.; Zhang, H.; Lu, X. ALBLP: Adaptive load-balancing architecture based on link-state prediction in software-defined networking. Wirel. Commun. Mob. Comput. 2022, 2022, 8354150. [Google Scholar] [CrossRef]
- Duy, P.T.; Qui, H.P.; Pham, V.H. Aloba: A mechanism of adaptive load balancing and failure recovery in distributed SDN controllers. In Proceedings of the 2019 IEEE 19th International Conference on Communication Technology (ICCT), Xi’an, China, 16–19 October 2019; pp. 1322–1326. [Google Scholar]
- Kang, B.; Choo, H. An SDN-enhanced load-balancing technique in the cloud system. J. Supercomput. 2018, 74, 5706–5729. [Google Scholar] [CrossRef]
- Abdelltif, A.A.; Ahmed, E.; Fong, A.T.; Gani, A.; Imran, M. SDN-based load balancing service for cloud servers. IEEE Commun. Mag. 2018, 56, 106–111. [Google Scholar] [CrossRef]
- Yu, T.F.; Wang, K.; Hsu, Y.H. Adaptive routing for video streaming with QoS support over SDN networks. In Proceedings of the 2015 International Conference on Information Networking (ICOIN), Siem Reap, Cambodia, 12–14 January 2015; pp. 318–323. [Google Scholar]
- Zheng, W.; Yang, M.; Zhang, C.; Zheng, Y.; Wu, Y.; Zhang, Y.; Li, J. Application-aware QoS routing in SDNs using machine learning techniques. Peer-to-Peer Netw. Appl. 2022, 15, 529–548. [Google Scholar] [CrossRef]
- Nde, G.N.; Khondoker, R. SDN testing and debugging tools: A survey. In Proceedings of the 2016 5th International Conference on Informatics, Electronics and Vision (ICIEV), Dhaka, Bangladesh, 13–14 May 2016; pp. 631–635. [Google Scholar]
- Zhang, Y.; Beheshti, N.; Manghirmalani, R. NetRevert: Rollback recovery in SDN. In Proceedings of the Third Workshop on Hot Topics in Software Defined Networking, Chicago, IL, USA, 22 August 2014; pp. 231–232. [Google Scholar]
- Cascone, C.; Pollini, L.; Sanvito, D.; Capone, A.; Sanso, B. SPIDER: Fault resilient SDN pipeline with recovery delay guarantees. In Proceedings of the 2016 IEEE NetSoft Conference and Workshops (NetSoft), Seoul, Republic of Korea, 6–10 June 2016; pp. 296–302. [Google Scholar]
- Chandrasekaran, B.; Tschaen, B.; Benson, T. Isolating and tolerating SDN application failures with LegoSDN. In Proceedings of the Symposium on SDN Research, Santa Clara, CA, USA, 14–15 March 2016; pp. 1–12. [Google Scholar]
- Li, Y.; Wang, Z.; Yao, J.; Yin, X.; Shi, X.; Wu, J.; Zhang, H. MSAID: Automated detection of interference in multiple SDN applications. Comput. Netw. 2019, 153, 49–62. [Google Scholar] [CrossRef]
- Gheorghe, G.; Avanesov, T.; Palattella, M.R.; Engel, T.; Popoviciu, C. SDN-RADAR: Network troubleshooting combining user experience and SDN capabilities. In Proceedings of the 2015 1st IEEE Conference on Network Softwarization (NetSoft), London, UK, 13–17 April 2015; pp. 1–5. [Google Scholar]
- Reitblatt, M.; Canini, M.; Guha, A.; Foster, N. Fattire: Declarative fault tolerance for software-defined networks. In Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, Hong Kong, China, 16 August 2013; pp. 109–114. [Google Scholar]
- Bi, Y.; Han, G.; Lin, C.; Guizani, M.; Wang, X. Mobility management for intro/inter domain handover in software-defined networks. IEEE J. Sel. Areas Commun. 2019, 37, 1739–1754. [Google Scholar] [CrossRef]
- Yao, D.; Su, X.; Liu, B.; Zeng, J. A mobile handover mechanism based on fuzzy logic and MPTCP protocol under SDN architecture. In Proceedings of the 2018 18th International Symposium on Communications and Information Technologies (ISCIT), Bangkok, Thailand, 26–28 September 2018; pp. 141–146. [Google Scholar]
- Vieira, J.L.; Passos, D. An SDN-based access point virtualization solution for multichannel IEEE 802.11 networks. In Proceedings of the 2019 10th International Conference on Networks of the Future (NoF), Rome, Italy, 1–3 October 2019; pp. 122–125. [Google Scholar]
- Lei, J.; Wang, Y.; Xia, Y. SDN-based centralized downlink scheduling with multiple aps cooperation in wlans. Wirel. Commun. Mob. Comput. 2019, 2019, 4015262. [Google Scholar] [CrossRef] [Green Version]
- El Azaly, N.M.; Badran, E.F.; Kheirallah, H.N.; Farag, H.H. Centralized dynamic channel reservation mechanism via SDN for CR networks spectrum allocation. IEEE Access 2020, 8, 192493–192505. [Google Scholar] [CrossRef]
- Yang, G.; Cao, Y.; Esmailpour, A.; Wang, D. SDN-Based Hierarchical Agglomerative Clustering Algorithm for Interference Mitigation in Ultra-Dense Small Cell Networks. ETRI J. 2018, 40, 227–236. [Google Scholar] [CrossRef]
- Cheng, R.S.; Huang, C.M.; Pan, S.Y. WiFi offloading using the device-to-device (D2D) communication paradigm based on the software defined network (SDN) architecture. J. Netw. Comput. Appl. 2018, 112, 18–28. [Google Scholar] [CrossRef]
- Rahimi, P.; Chrysostomou, C.; Pervaiz, H.; Vassiliou, V.; Ni, Q. Joint radio resource allocation and beamforming optimization for industrial internet of things in software-defined networking-based virtual fog-radio access network 5G-and-beyond wireless environments. IEEE Trans. Ind. Inform. 2021, 18, 4198–4209. [Google Scholar] [CrossRef]
- Shantharama, P.; Thyagaturu, A.S.; Karakoc, N.; Ferrari, L.; Reisslein, M.; Scaglione, A. LayBack: SDN management of multi-access edge computing (MEC) for network access services and radio resource sharing. IEEE Access 2018, 6, 57545–57561. [Google Scholar] [CrossRef]
- Bansal, M.; Mehlman, J.; Katti, S.; Levis, P. Openradio: A programmable wireless dataplane. In Proceedings of the First Workshop on Hot Topics in Software Defined Networks, Helsinki, Finland, 13 August 2012; pp. 109–114. [Google Scholar]
- Arnaz, A.; Lipman, J.; Abolhasan, M.; Hiltunen, M. Towards Integrating Intelligence and Programmability in Open Radio Access Networks: A Comprehensive Survey. IEEE Access 2022, 10, 67747–67770. [Google Scholar] [CrossRef]
- Wang, Y.; Chen, H.; Wu, X.; Shu, L. An energy-efficient SDN based sleep scheduling algorithm for WSNs. J. Netw. Comput. Appl. 2016, 59, 39–45. [Google Scholar] [CrossRef]
- Huang, H.; Guo, S.; Wu, J.; Li, J. Green datapath for TCAM-based software-defined networks. IEEE Commun. Mag. 2016, 54, 194–201. [Google Scholar] [CrossRef]
- Huin, N.; Rifai, M.; Giroire, F.; Pacheco, D.L.; Urvoy-Keller, G.; Moulierac, J. Bringing energy aware routing closer to reality with SDN hybrid networks. IEEE Trans. Green Commun. Netw. 2018, 2, 1128–1139. [Google Scholar] [CrossRef] [Green Version]
- De Assunção, M.D.; Carpa, R.; Lefévre, L.; Glück, O. On designing SDN services for energy-aware traffic engineering. In Testbeds and Research Infrastructures for the Development of Networks and Communities: 11th International Conference, TRIDENTCOM, Hangzhou, China, 14–15 June 2016; Revised Selected Papers; Springer International Publishing: Cham, Switzerland, 2017; pp. 14–23. [Google Scholar]
- Pham, M.; Hoang, D.B.; Chaczko, Z. Congestion-aware and energy-aware virtual network embedding. IEEE/ACM Trans. Netw. 2019, 28, 210–223. [Google Scholar] [CrossRef]
- Islam, M.J.; Rahman, A.; Kabir, S.; Karim, M.R.; Acharjee, U.K.; Nasir, M.K.; Band, S.S.; Sookhak, M.; Wu, S. Blockchain-SDN-based energy-aware and distributed secure architecture for IoT in smart cities. IEEE Internet Things J. 2021, 9, 3850–3864. [Google Scholar] [CrossRef]
- Saha, D.; Shojaee, M.; Baddeley, M.; Haque, I. An energy-aware SDN/NFV architecture for the internet of things. In Proceedings of the 2020 IFIP Networking Conference (Networking), Paris, France, 22–25 June 2020; pp. 604–608. [Google Scholar]
- Sellami, B.; Hakiri, A.; Yahia, S.B.; Berthou, P. Energy-aware task scheduling and offloading using deep reinforcement learning in SDN-enabled IoT network. Comput. Netw. 2022, 210, 108957. [Google Scholar] [CrossRef]
- Klaedtke, F.; Karame, G.O.; Bifulco, R.; Cui, H. Access control for SDN controllers. In Proceedings of the Third Workshop on Hot Topics in Software Defined Networking, Chicago, IL, USA, 22 August 2014; pp. 219–220. [Google Scholar]
- Alsmadi, I. The integration of access control levels based on SDN. Int. J. High Perform. Comput. Netw. 2016, 9, 281–290. [Google Scholar] [CrossRef]
- Tseng, Y.; Pattaranantakul, M.; He, R.; Zhang, Z.; Naït-Abdesselam, F. Controller DAC: Securing SDN controller with dynamic access control. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Hu, T.; Zhang, Z.; Yi, P.; Liang, D.; Li, Z.; Ren, Q.; Hu, Y.; Lan, J. SEAPP: A secure application management framework based on REST API access control in SDN-enabled cloud environment. J. Parallel Distrib. Comput. 2021, 147, 108–123. [Google Scholar] [CrossRef]
- Chang, D.; Sun, W.; Yang, Y.; Wang, T. An E-ABAC-based SDN access control method. In Proceedings of the 2019 6th International Conference on Information Science and Control Engineering (ICISCE), Shanghai, China, 20–22 December 2019; pp. 668–672. [Google Scholar]
- Weng, J.S.; Weng, J.; Zhang, Y.; Luo, W.; Lan, W. BENBI: Scalable and dynamic access control on the northbound interface of SDN-based VANET. IEEE Trans. Veh. Technol. 2018, 68, 822–831. [Google Scholar] [CrossRef]
- Ren, W.; Sun, Y.; Luo, H.; Guizani, M. SILedger: A blockchain and ABE-based access control for applications in SDN-IoT networks. IEEE Trans. Netw. Serv. Manag. 2021, 18, 4406–4419. [Google Scholar] [CrossRef]
- Bhattacharya, A.; Rana, R.; Datta, S.; Venkanna, U. P4-sKnock: A Two Level Host Authentication and Access Control Mechanism in P4 based SDN. In Proceedings of the 2022 27th Asia Pacific Conference on Communications (APCC), Jeju Island, Republisc of Korea, 19–21 October 2022; pp. 278–283. [Google Scholar]
- Al-Alaj, A.; Sandhu, R.; Krishnan, R. A Model for the Administration of Access Control in Software Defined Networking using Custom Permissions. In Proceedings of the 2020 Second IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (TPS-ISA), Atlanta, GA, USA, 28–31 October 2020; pp. 169–178. [Google Scholar]
- Khalid, M.; Hameed, S.; Qadir, A.; Shah, S.A.; Draheim, D. Towards SDN-based smart contract solution for IoT access control. Comput. Commun. 2023, 198, 1–31. [Google Scholar] [CrossRef]
- Toshniwal, B.; Joshi, K.D.; Shrivastava, P.; Kataoka, K. BEAM: Behavior-based access control mechanism for SDN applications. In Proceedings of the 2019 28th International Conference on Computer Communication and Networks (ICCCN), Valencia, Spain, 29 July–1 August 2019; pp. 1–2. [Google Scholar]
- Chattaraj, D.; Bera, B.; Das, A.K.; Rodrigues, J.J.; Park, Y. Designing fine-grained access control for software-defined networks using private blockchain. IEEE Internet Things J. 2021, 9, 1542–1559. [Google Scholar] [CrossRef]
- Bensalah, F.; El Kamoun, N. A novel approach for improving MPLS VPN security by adopting the software defined network paradigm. Procedia Comput. Sci. 2019, 160, 831–836. [Google Scholar] [CrossRef]
- Shif, L.; Wang, F.; Lung, C.H. Improvement of security and scalability for IoT network using SD-VPN. In Proceedings of the NOMS 2018—2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018; pp. 1–5. [Google Scholar]
- Hauser, F.; Häberle, M.; Schmidt, M.; Menth, M. P4-ipsec: Site-to-site and host-to-site vpn with ipsec in p4-based sdn. IEEE Access 2020, 8, 139567–139586. [Google Scholar] [CrossRef]
- Morzhov, S.; Alekseev, I.; Nikitinskiy, M. Firewall application for Floodlight SDN controller. In Proceedings of the 2016 International Siberian Conference on Control and Communications (SIBCON), Moscow, Russia, 12–14 May 2016; pp. 1–5. [Google Scholar]
- Bakker, J.N.; Welch, I.; Seah, W.K. Network-wide virtual firewall using SDN/OpenFlow. In Proceedings of the 2016 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Palo Alto, CA, USA, 7–10 November 2016; pp. 62–68. [Google Scholar]
- Monir, M.F.; Pan, D. Application and Assessment of Click Modular Firewall vs. POX Firewall in SDN/NFV Framework. In Proceedings of the 2020 IEEE Region 10 Conference (Tencon), Osaka, Japan, 16–19 November 2020; pp. 991–996. [Google Scholar]
- Prabakaran, S.; Ramar, R.; Hussain, I.; Kavin, B.P.; Alshamrani, S.S.; AlGhamdi, A.S.; Alshehri, A. Predicting attack pattern via machine learning by exploiting stateful firewall as virtual network function in an SDN network. Sensors 2022, 22, 709. [Google Scholar] [CrossRef]
- Tran, T.V.; Ahn, H. FlowTracker: A SDN stateful firewall solution with adaptive connection tracking and minimized controller processing. In Proceedings of the 2016 International Conference on Software Networking (ICSN), Jeju Island, Republic of Korea, 23–26 May 2016; pp. 1–5. [Google Scholar]
- Kavin, B.P.; Srividhya, S.R.; V, R.; Lai, W.C. Performance Evaluation of Stateful Firewall-Enabled SDN with Flow-Based Scheduling for Distributed Controllers. Electronics 2022, 11, 3000. [Google Scholar]
- Shirali-Shahreza, S.; Ganjali, Y. Protecting home user devices with an SDN-based firewall. IEEE Trans. Consum. Electron. 2018, 64, 92–100. [Google Scholar] [CrossRef]
- Steichen, M.; Hommes, S.; State, R. ChainGuard—A firewall for blockchain applications using SDN with OpenFlow. In Proceedings of the 2017 Principles, Systems and Applications of IP Telecommunications (IPTComm), Chicago, IL, USA, 25–28 September 2017; pp. 1–8. [Google Scholar]
- Chang, Y.W.; Lin, T.N. An efficient dynamic rule placement for distributed firewall in sdn. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar]
- Datta, R.; Choi, S.; Chowdhary, A.; Park, Y. P4guard: Designing p4 based firewall. In Proceedings of the MILCOM 2018—2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018; pp. 1–6. [Google Scholar]
- Wijesekara, P.A.D.S.N. Prevalence, Risk Factors and Remedies for Psychiatric Illnesses among Students in Higher Education: A Comprehensive Study in University of Ruhuna. Prepr. Res. Sq. 2022, 1–33. [Google Scholar]
- Birkinshaw, C.; Rouka, E.; Vassilakis, V.G. Implementing an intrusion detection and prevention system using software-defined networking: Defending against port-scanning and denial-of-service attacks. J. Netw. Comput. Appl. 2019, 136, 71–85. [Google Scholar] [CrossRef] [Green Version]
- Latah, M.; Toker, L. Towards an efficient anomaly-based intrusion detection for software-defined networks. IET Netw. 2018, 7, 453–459. [Google Scholar] [CrossRef] [Green Version]
- Zeleke, E.M.; Melaku, H.M.; Mengistu, F.G. Efficient intrusion detection system for SDN orchestrated Internet of Things. J. Comput. Netw. Commun. 2021, 2021, 5593214. [Google Scholar] [CrossRef]
- Segura, G.A.N.; Chorti, A.; Margi, C.B. Centralized and distributed intrusion detection for resource-constrained wireless SDN networks. IEEE Internet Things J. 2021, 9, 7746–7758. [Google Scholar] [CrossRef]
- Li, W.; Wang, Y.; Jin, Z.; Yu, K.; Li, J.; Xiang, Y. Challenge-based collaborative intrusion detection in software-defined networking: An evaluation. Dig. Commun. Netw. 2021, 7, 257–263. [Google Scholar] [CrossRef]
- Shu, J.; Zhou, L.; Zhang, W.; Du, X.; Guizani, M. Collaborative intrusion detection for VANETs: A deep learning-based distributed SDN approach. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4519–4530. [Google Scholar] [CrossRef]
- Ujjan, R.M.A.; Pervez, Z.; Dahal, K. Snort based collaborative intrusion detection system using blockchain in SDN. In Proceedings of the 2019 13th International Conference on Software, Knowledge, Information Management and Applications (SKIMA), Island of Ulkulhas, Maldives, 26–28 August 2019; pp. 1–8. [Google Scholar]
- Hurley, T.; Perdomo, J.E.; Perez-Pons, A. HMM-based intrusion detection system for software defined networking. In Proceedings of the 2016 15th IEEE International Conference on Machine Learning and Applications (ICMLA), Anaheim, CA, USA, 18–20 December 2016; pp. 617–621. [Google Scholar]
- Tang, T.A.; McLernon, D.; Mhamdi, L.; Zaidi, S.A.R.; Ghogho, M. Intrusion detection in sdn-based networks: Deep recurrent neural network approach. In Deep Learning Applications for Cyber Security; Springer: Cham, Switzerland, 2019; pp. 175–195. [Google Scholar]
- Bhatia, A.; Haribabu, K.; Gupta, K.; Sahu, A. Realization of flexible and scalable VANETs through SDN and virtualization. In Proceedings of the 2018 International conference on information networking (ICOIN), Bangkok, Thailand, 10–12 January 2018; pp. 280–282. [Google Scholar]
- Kurniawan, M.T.; Fathinuddin, M.; Widiyanti, H.A.; Simanjuntak, G.R. Network Slicing on SDN using FlowVisor and POX Controller to Traffic Isolation Enforcement. In Proceedings of the 2021 International Conference on Engineering and Emerging Technologies (ICEET), Istanbul, Turkey, 27–28 October 2021; IEEE: Toulouse, France, 2021; pp. 1–6. [Google Scholar]
- Chen, C.H.; Chen, C.; Lu, S.H.; Tseng, C.C. Role-based campus network slicing. In Proceedings of the 2016 IEEE 24th International Conference on Network Protocols (ICNP), Singapore, 8–11 November 201; pp. 1–6.
- Zhang, N.; Yang, P.; Zhang, S.; Chen, D.; Zhuang, W.; Liang, B.; Shen, X.S. Software defined networking enabled wireless network virtualization: Challenges and solutions. IEEE Netw. 2017, 31, 42–49. [Google Scholar] [CrossRef] [Green Version]
- Ma, Y.W.; Chen, J.L.; Chang, C.C.; Nakao, A.; Yamamoto, S. A novel dynamic resource adjustment architecture for virtual tenant networks in SDN. J. Syst. Softw. 2018, 143, 100–115. [Google Scholar] [CrossRef]
- Wang, Q.; Shou, G.; Liu, Y.; Hu, Y.; Guo, Z.; Chang, W. Implementation of multipath network virtualization with SDN and NFV. IEEE Access 2018, 6, 32460–32470. [Google Scholar] [CrossRef]
- Han, Y.; Vachuska, T.; Al-Shabibi, A.; Li, J.; Huang, H.; Snow, W.; Hong, J.W.K. ONVisor: Towards a scalable and flexible SDN-based network virtualization platform on ONOS. Int. J. Netw. Manag. 2018, 28, e2012. [Google Scholar] [CrossRef]
- Shi, J.; Chung, S.H. A traffic-aware quality-of-service control mechanism for software-defined networking-based virtualized networks. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717697984. [Google Scholar] [CrossRef]
- Rawat, D.B. Fusion of software defined networking, edge computing, and blockchain technology for wireless network virtualization. IEEE Commun. Mag. 2019, 57, 50–55. [Google Scholar] [CrossRef]
- Cui, L.; Yu, F.R.; Yan, Q. When big data meets software-defined networking: SDN for big data and big data for SDN. IEEE Netw. 2016, 30, 58–65. [Google Scholar] [CrossRef]
- Aujla, G.S.; Kumar, N.; Zomaya, A.Y.; Ranjan, R. Optimal decision making for big data processing at edge-cloud environment: An SDN perspective. IEEE Trans. Ind. Inform. 2017, 14, 778–789. [Google Scholar] [CrossRef] [Green Version]
- Cho, J.; Chang, H.; Mukherjee, S.; Lakshman, T.V.; Van der Merwe, J. Typhoon: An SDN enhanced real-time big data streaming framework. In Proceedings of the 13th International Conference on Emerging Networking EXperiments and Technologies, Incheon, Republic of Korea, 12–15 November 2017; pp. 310–322. [Google Scholar]
- Alwasel, K.; Calheiros, R.N.; Garg, S.; Buyya, R.; Pathan, M.; Georgakopoulos, D.; Ranjan, R. BigDataSDNSim: A simulator for analyzing big data applications in software-defined cloud data centers. Softw. Pract. Exp. 2021, 51, 893–920. [Google Scholar] [CrossRef]
- Shah, S.A.R.; Wu, W.; Lu, Q.; Zhang, L.; Sasidharan, S.; DeMar, P.; Guok, C.; Macauley, J.; Pouyoul, E.; Kim, J.; et al. AmoebaNet: An SDN-enabled network service for big data science. J. Netw. Comput. Appl. 2018, 119, 70–82. [Google Scholar] [CrossRef] [Green Version]
- Jain, S.; Khandelwal, M.; Katkar, A.; Nygate, J. Applying big data technologies to manage QoS in an SDN. In Proceedings of the 2016 12th International Conference on Network and Service Management (CNSM), Montreal, QC, Canada, 31 October–4 November 2016; pp. 302–306. [Google Scholar]
- Trevisan, M.; Drago, I.; Mellia, M.; Song, H.H.; Baldi, M. AWESoME: Big data for automatic Web service management in SDN. IEEE Trans. Netw. Serv. Manag. 2017, 15, 13–26. [Google Scholar] [CrossRef]
- Le, L.V.; Sinh, D.; Lin, B.S.P.; Tung, L.P. Applying big data, machine learning, and SDN/NFV to 5G traffic clustering, forecasting, and management. In Proceedings of the 2018 4th IEEE Conference on Network Softwarization and Workshops (NetSoft), Montreal, QC, Canada, 25–29 June 2018; pp. 168–176. [Google Scholar]
- Le, L.V.; Lin, B.S.P.; Tung, L.P.; Sinh, D. SDN/NFV, machine learning, and big data driven network slicing for 5G. In Proceedings of the 2018 IEEE 5G World Forum (5GWF), Silicon Valley, CA, USA, 9–11 July 2018; pp. 20–25. [Google Scholar]
- Lv, Z.; Xiu, W. Interaction of edge-cloud computing based on SDN and NFV for next generation IoT. IEEE Internet Things J. 2019, 7, 5706–5712. [Google Scholar] [CrossRef]
- Mayoral, A.; Vilalta, R.; Muñoz, R.; Casellas, R.; Martínez, R. SDN orchestration architectures and their integration with cloud computing applications. Opt. Switch. Netw. 2017, 26, 2–13. [Google Scholar] [CrossRef]
- Rawas, S. Energy, network, and application-aware virtual machine placement model in SDN-enabled large scale cloud data centers. Multimed. Tools Appl. 2021, 80, 15541–15562. [Google Scholar] [CrossRef]
- Li, F.; Cao, J.; Wang, X.; Sun, Y.; Sahni, Y. Enabling software defined networking with qos guarantee for cloud applications. In Proceedings of the 2017 IEEE 10th International Conference on Cloud Computing (CLOUD), Honolulu, HI, USA, 25–30 June 2017; pp. 130–137. [Google Scholar]
- Conti, M.; Kaliyar, P.; Lal, C. CENSOR: Cloud-enabled secure IoT architecture over SDN paradigm. Concurr. Comput. Pract. Exp. 2019, 31, e4978. [Google Scholar] [CrossRef]
- Rahman, A.; Islam, M.J.; Khan, M.S.I.; Kabir, S.; Pritom, A.I.; Karim, M.R. Block-sdotcloud: Enhancing security of cloud storage through blockchain-based sdn in iot network. In Proceedings of the 2020 2nd International Conference on Sustainable Technologies for Industry 4.0 (STI), Dhaka, Bangladesh, 19–20 December 2020; pp. 1–6. [Google Scholar]
- Gargees, R.; Morago, B.; Pelapur, R.; Chemodanov, D.; Calyam, P.; Oraibi, Z.; Duan, Y.; Seetharaman, G.; Palaniappan, K. Incident-supporting visual cloud computing utilizing software-defined networking. IEEE Trans. Circuits Syst. Video Technol. 2016, 27, 182–197. [Google Scholar] [CrossRef]
- Liu, Y.; Gu, H.; Yan, F.; Calabretta, N. Highly-efficient switch migration for controller load balancing in elastic optical inter-datacenter networks. IEEE J. Sel. Areas Commun. 2021, 39, 2748–2761. [Google Scholar] [CrossRef]
- Song, P.; Liu, Y.; Liu, T.; Qian, D. Controller-proxy: Scaling network management for large-scale SDN networks. Comput. Commun. 2017, 108, 52–63. [Google Scholar] [CrossRef]
- Lu, Y.; Ling, Z.; Zhu, S.; Tang, L. SDTCP: Towards datacenter TCP congestion control with SDN for IoT applications. Sensors 2017, 17, 109. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Paliwal, M.; Shrimankar, D. Effective resource management in SDN enabled data center network based on traffic demand. IEEE Access 2019, 7, 69698–69706. [Google Scholar] [CrossRef]
- Pham, M.; Hoang, D.B. SDN applications—The intent-based Northbound Interface realisation for extended applications. In Proceedings of the 2016 IEEE NetSoft Conference and Workshops (NetSoft), Seoul, Republic of Kprea, 6–10 June 2016; pp. 372–377. [Google Scholar]
- Siniarski, B.; Murphy, J.; Delaney, D. FlowVista: Low-bandwidth SDN monitoring driven by business application interaction. In Proceedings of the 2017 25th International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 21–23 September 2017; pp. 1–6. [Google Scholar]
- Krishna, S.V.; Shrivastava, A.; Wagh, S.J. SDN in high performance computing for scien. In Proceedings of the 2017 International Conference on Computational Intelligence in Data Science (ICCIDS), Chennai, India, 2–3 June 2017; pp. 1–8. [Google Scholar]
- Rauf, B.; Abbas, H.; Sheri, A.M.; Iqbal, W.; Khan, A.W. Enterprise integration patterns in SDN: A reliable, fault-tolerant communication framework. IEEE Internet Things J. 2020, 8, 6359–6371. [Google Scholar] [CrossRef]
- Rauf, B.; Abbas, H.; Sheri, A.M.; Iqbal, W.; Bangash, Y.A.; Daneshmand, M.; Amjad, M.F. CACS: A context-aware and anonymous communication framework for an enterprise network using SDN. IEEE Internet Things J. 2021, 9, 11725–11736. [Google Scholar] [CrossRef]
- Van Adrichem, N.L.; Iqbal, F.; Kuipers, F.A. Backup rules in software-defined networks. In Proceedings of the 2016 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Palo Alto, CA, USA, 7–10 November 2016; pp. 179–185. [Google Scholar]
- Zhang, P.; Li, H.; Hu, C.; Hu, L.; Xiong, L. Stick to the script: Monitoring the policy compliance of SDN data plane. In Proceedings of the 2016 Symposium on Architectures for Networking and Communications Systems, Santa Clara, CA, USA, 17–18 March 2016; pp. 81–86. [Google Scholar]
- Dangovas, V.; Kuliesius, F. SDN-driven authentication and access control system. In Proceedings of the International Conference on Digital Information, Networking, and Wireless Communications (DINWC2014), Ostrava, Czech Republic, 24–26 June 2014; pp. 20–23. [Google Scholar]
- Wen, X.; Yang, B.; Chen, Y.; Li, L.E.; Bu, K.; Zheng, P.; Yang, Y.; Hu, C. RuleTris: Minimizing rule update latency for TCAM-based SDN switches. In Proceedings of the 2016 IEEE 36th International Conference on Distributed Computing Systems (ICDCS), Nara, Japan, 27–30 June 2016; pp. 179–188. [Google Scholar]
- Wani, M.A.; Bhat, F.A.; Afzal, S.; Khan, A.I. Advances in Deep Learning; Springer: Singapore, 2020. [Google Scholar]
- Khan, P.W.; Byun, Y.C.; Park, N. IoT-blockchain enabled optimized provenance system for food industry 4.0 using advanced deep learning. Sensors 2020, 20, 2990. [Google Scholar] [CrossRef]
- Luo, Y.; Cascon, P.; Murray, E.; Ortega, J. Accelerating OpenFlow switching with network processors. In Proceedings of the 5th ACM/IEEE Symposium on Architectures for Networking and Communications Systems, Princeton, NJ, USA, 19–20 October 2009; pp. 70–71. [Google Scholar]
- Hang, Z.; Wen, M.; Shi, Y.; Zhang, C. Programming protocol-independent packet processors high-level programming (P4HLP): Towards unified high-level programming for a commodity programmable switch. Electronics 2019, 8, 958. [Google Scholar] [CrossRef] [Green Version]
- Isyaku, B.; Mohd Zahid, M.S.; Bte Kamat, M.; Abu Bakar, K.; Ghaleb, F.A. Software defined networking flow table management of openflow switches performance and security challenges: A survey. Future Internet 2020, 12, 147. [Google Scholar] [CrossRef]
- Chica, J.C.C.; Imbachi, J.C.; Vega, J.F.B. Security in SDN: A comprehensive survey. J. Netw. Comput. Appl. 2020, 159, 102595. [Google Scholar] [CrossRef]
- Diogo, M.; Cabral, B.; Bernardino, J. Consistency models of NoSQL databases. Future Internet 2019, 11, 43. [Google Scholar] [CrossRef] [Green Version]
- Filip, I.D.; Iliescu, C.M.; Pop, F. Assertive, Selective, Scalable IoT-Based Warning System. Sensors 2022, 22, 1015. [Google Scholar] [CrossRef] [PubMed]
- Bakarić, R.; Korenčić, D.; Hršak, D.; Ristov, S. SFQ: Constructing and Querying a Succinct Representation of FASTQ Files. Electronics 2022, 11, 1783. [Google Scholar] [CrossRef]
- Saeed, A.S.M.; George, L.E. Data deduplication system based on content-defined chunking using bytes pair frequency occurrence. Symmetry 2020, 12, 1841. [Google Scholar] [CrossRef]
- Voellmy, A.; Wang, J. Scalable software defined network controllers. In Proceedings of the ACM SIGCOMM 2012 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communication, Helsinki, Finland, 13–17 August 2012; pp. 289–290. [Google Scholar]
- Blenk, A.; Basta, A.; Reisslein, M.; Kellerer, W. Survey on network virtualization hypervisors for software defined networking. IEEE Commun. Surv. Tutor. 2015, 18, 655–685. [Google Scholar] [CrossRef] [Green Version]
- Horvath, T.; Munster, P.; Oujezsky, V.; Bao, N.H. Passive optical networks progress: A tutorial. Electronics 2020, 9, 1081. [Google Scholar] [CrossRef]
- Hoebeke, J.; Moerman, I.; Dhoedt, B.; Demeester, P. An overview of mobile ad hoc networks: Applications and challenges. J.-Commun. Netw. 2004, 3, 60–66. [Google Scholar]
- Chlamtac, I.; Conti, M.; Liu, J.J.N. Mobile ad hoc networking: Imperatives and challenges. Ad Hoc Netw. 2003, 1, 13–64. [Google Scholar] [CrossRef]
- Majid, M.; Habib, S.; Javed, A.R.; Rizwan, M.; Srivastava, G.; Gadekallu, T.R.; Lin, J.C.W. Applications of wireless sensor networks and internet of things frameworks in the industry revolution 4.0: A systematic literature review. Sensors 2022, 22, 2087. [Google Scholar] [CrossRef]
- Gupta, C.; Johri, I.; Srinivasan, K.; Hu, Y.C.; Qaisar, S.M.; Huang, K.Y. A systematic review on machine learning and deep learning models for electronic information security in mobile networks. Sensors 2022, 22, 2017. [Google Scholar] [CrossRef]
- IEEE P2302-2021; Standard for Intercloud Interoperability and Federation (SIIF): Reference Architecture and Taxonomy Framework. IEEE Standards Association: Piscataway, NJ, USA, 2021. Available online: https://standards.ieee.org/ieee/2302/7056/ (accessed on 14 March 2023).
- IEEE P2413-2019; Standard for an Architectural Framework for the Internet of Things (IoT). IEEE Standards Association: Piscataway, NJ, USA, 2019. Available online: https://standards.ieee.org/ieee/2413/6226/ (accessed on 14 March 2023).
- Novo, O.; Francesco, M.D. Semantic interoperability in the IoT: Extending the web of things architecture. ACM Trans. Internet Things 2020, 1, 1–25. [Google Scholar] [CrossRef] [Green Version]
- Open Network Foundation. Stratum. Available online: https://opennetworking.org/stratum/ (accessed on 14 March 2023).
- Metro Ethernet Forum. LSO SONATA. Available online: https://www.mef.net/service-automation/lso-apis/inter-provider-apis/lso-sonata/ (accessed on 14 March 2023).
- International Telecommunication Union. Study Group 13 at a Glance. Available online: https://www.itu.int/en/ITU-T/about/groups/Pages/sg13.aspx (accessed on 14 March 2023).
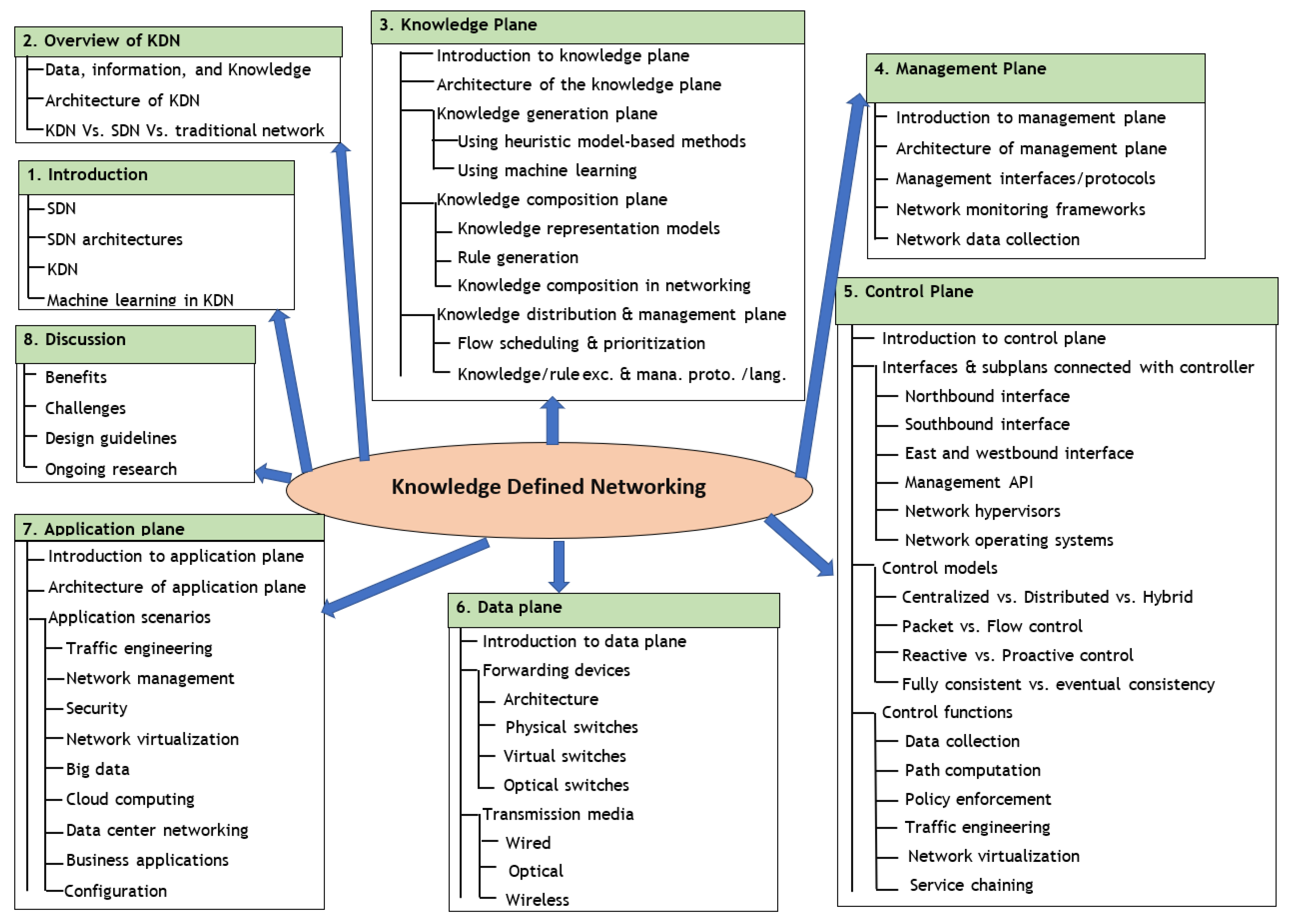




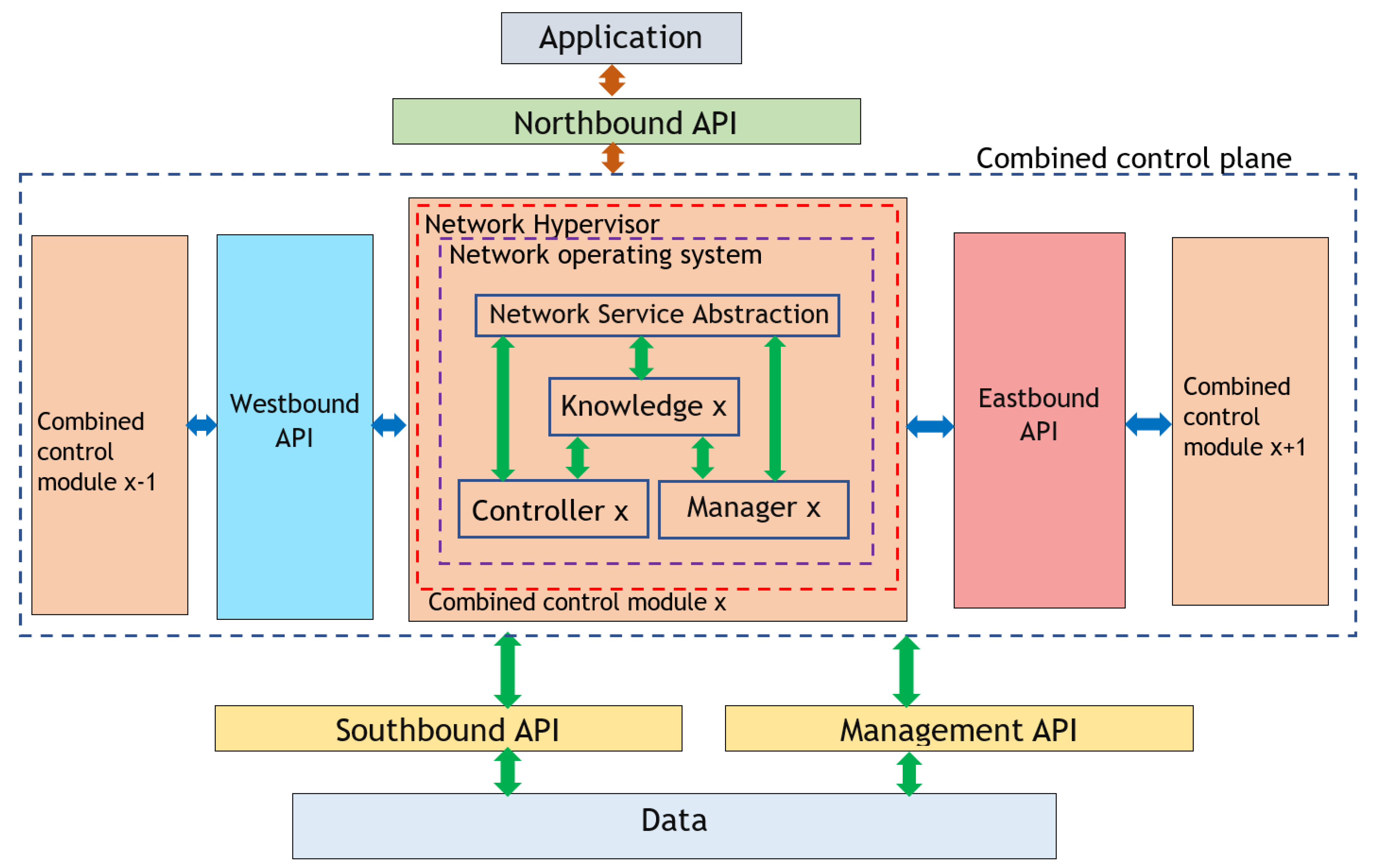

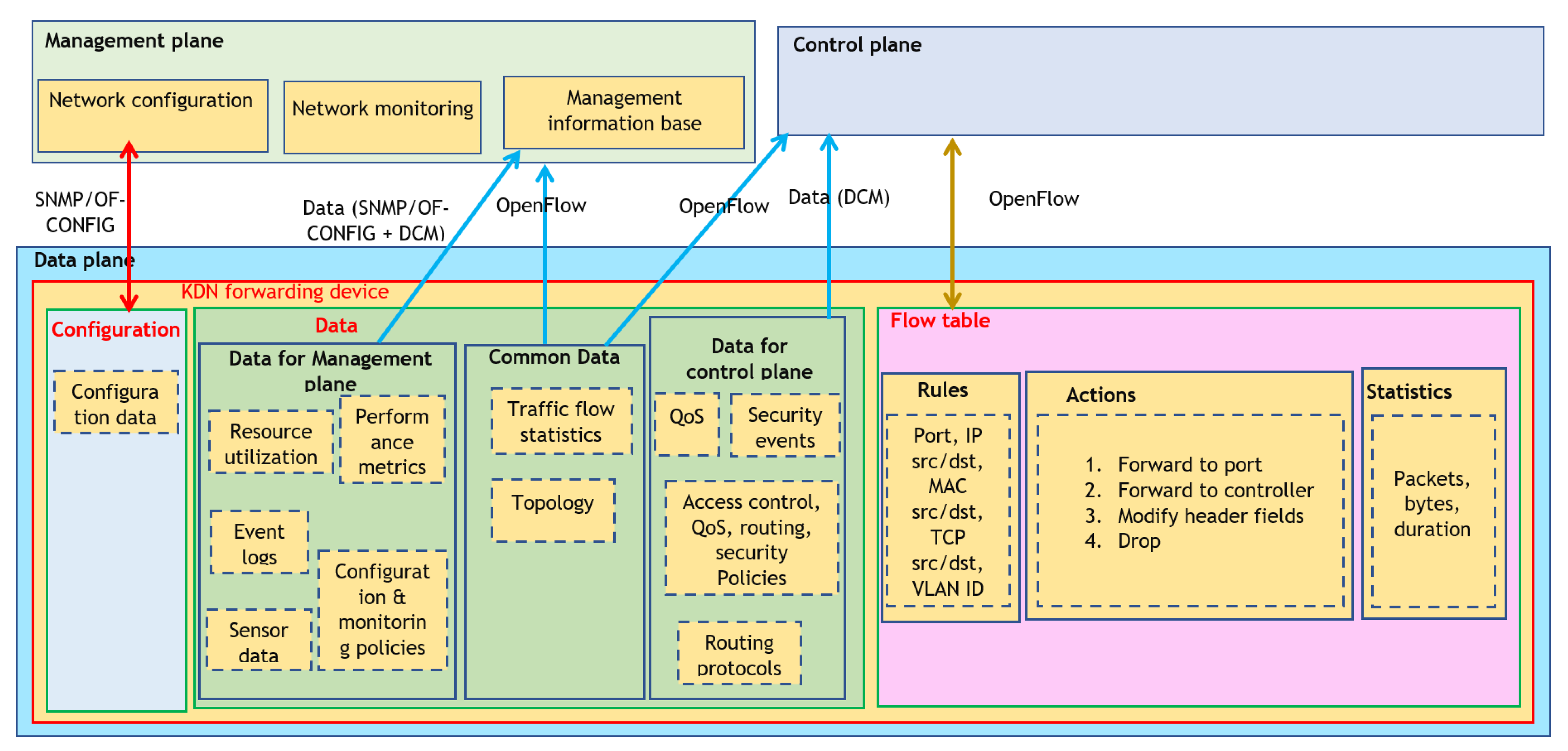


| Parameter/Feature | Traditional Network | SDN | KDN |
|---|---|---|---|
| Logical planes | Data, control, and application coupled | Data, control, and application decoupled | Data, control, management, knowledge, and application decoupled |
| Network programmability | Manual and complex | Manual and simple | Hybrid and simple |
| Control plane | Distributed across devices | Logically centralized and driven by application policies | Logically centralized and self learning driven by application policies and knowledge |
| Management plane | Manual and distributed | Manual and centralized coupled with control plane | Hybrid and centralized decoupled from control plane |
| Knowledge plane | Totally knowledge ignorant | Knowledge ignorant. However, make use of global network information in arriving at decisions | Generate knowledge, compose knowledge, generate rules, store and disseminate them to other planes |
| Application plane | Tightly coupled with infrastructure and inflexible | Decoupled with infrastructure and can be redefined dynamically based on service needs | Decoupled from infrastructure, can be redefined and optimized based on service needs and network performance |
| Network architecture | Static | Flexible | Flexible, self learning, and automated |
| Operational cost | High | Medium | Low |
| Implementation cost | Low | Medium | High |
| Security features | Low | Medium | High |
| Category | Language/Protocol/Model | Purpose | Developer |
|---|---|---|---|
| Knowledge representation | Resource description framework (RDF) [64] | Represent knowledge as (subject, predicate, object) triplets | W3C |
| RDF schema (RDFS) [203] | Represent knowledge using a knowledge graph having entities and relationships | W3C | |
| Web Ontology Language (OWL) [204] | Represent ontology using classes, properties, individuals, restrictions, annotations | W3C | |
| Ontology Inference Layer (OIL) [205] | Represent ontology using classes, properties, individuals, restrictions, inference rules | Dieter Fensel et al. | |
| Knowledge Interchange Format (KIF) [207] | Represent knowledge using complex logical relationship between objects and concepts | Genesereth et al. | |
| Rule representation, storage and exchange | RuleML [209] | Markup language to represent rules | H. Boley et al. |
| Semantic Web Rule Language (SWRL) [210] | Express rules and constraints | W3C, RIF | |
| Rule Interchange Format (RIF) [211] | Rule language to represent and exchange rules between systems | W3C, RIF | |
| Query and modify knowledge | SPARQL [239] | Query and modify knowledge which appears in RDF | W3C |
| GraphQL [243] | Query and modify knowledge in knowledge graphs | Huahai He et al. | |
| Query knowledge | SQWRL [240] | Query OWL ontologies | W3C |
| Knowledge Graph Query Language (KGQL) [241] | Query knowledge graphs | P. Liu et al. | |
| Knowledge Query and Manipulation Language (KQML) [242] | Exchange messages such as queries, assertions, and requests | T. Finin et al. | |
| Data representation | YANG [244] | Describe state data of network devices and their configurations | Bjorklund |
| Common Information Model (CIM) [245] | Representing information about network infrastructure and services of devices | Uslar M. et al. | |
| Rules/knowledge evaluation | RETE [233] | Rule evaluation and pattern matching | A. Gupta et al. |
| Drools [234] | Rule pattern matching supporting querying, rule chaining | M. Proctor | |
| VLog [235] | Reasoning for rules or knowledge represented in RDF or OWL | D. Carral et al. | |
| Bossam [236] | Reason from OWL ontology, support chaining | M. Jang et al. | |
| CLIPS [237] | Evaluate rules using a forward chaining algorithm | F. M. Lopez | |
| Jess [238] | Rule engine for the Java platform | F.H. Ernest |
| Category | Protocol/Framework/Method | Purpose | Developer |
|---|---|---|---|
| Network management | CONMan [249] | Complexity oblivious network management with minimum protocol specific data | H. Ballani et al. |
| PACMAN [250] | Network configuration management using active documents | X. Chen et al. | |
| OF-CONFIG [251] | A protocol for configuring and monitoring OpenFlow switches | R. Narisetty et al. | |
| Ontology based configuration [252] | Automatic configuration of switches using an OWL-based ontology | A. Martinez et al. | |
| HybNET [253] | Automated network management framework in hybrid KDN and legacy networks | H. Lu et al. | |
| SNMP [254] | A protocol for monitoring and configuration of network devices | J.D. Case et al. | |
| Network monitoring frameworks | Payless [255] | Network monitoring with adaptive network statistics collection | S.R. Chowdhury et al. |
| OpenSample [256] | Sample based network load and flow statistics monitoring | J. Suh et al. | |
| OpenNetMon [257] | Monitoring using adaptive rate polling to collect per flow metrics | N.L.V.Adrichem et al. | |
| HONE [258] | Traffic monitoring using traffic measurement data | P. Sun et al. | |
| Data collection | IQP [260] | Data collection minimizing communication cost, delay, and overhead | S.N. Wijesekara et al. |
| Packet sampling [261] | Collect sampled wild card flow entries | P. Wette et al. | |
| Adaptive data collection [262] | Dynamically selects data collection nodes and samples network traffic based on flow characteristics | D. Zhou et al. | |
| Sensor measurements collection [263] | Collects sensor measurements in an energy efficient manner | W.H. Liao et al. | |
| Predictive data collection [264] | Predicts and uses multihop routing using ad hoc and cellular interfaces for data collection | Z. Jiao et al. |
| KDN Language | Paradigm | Policy Definition | Flow Installation | Network Monitoring Policy | Birth Year | Base Language |
|---|---|---|---|---|---|---|
| FML [283] | Declarative (Logical) | Static | Reactive | Access data collected from other resources | 2009 | C++, Python |
| Nettle [284] | Declarative (Functional reactive) | Dynamic and static | Reactive | N/A | 2010 | Haskell |
| Procera [285] | Declarative (Functional reactive) | Dynamic and static | Reactive | Data-Windowed history, other resources | 2012 | Haskell |
| Frenetic [286] | Declarative (Functional reactive) | Dynamic and static | Reactive | Data-Windowed history, Query language | 2010 | Python |
| Kinetic [287] | Declarative (Event driven) | Dynamic and static | Reactive, proactive | Data-Windowed history, other resources | 2014 | Python |
| PonderFlow [288] | Declarative (Event driven) | Dynamic and static | Reactive | N/A | 2014 | Java |
| Maple [289] | Imperative | Dynamic and static | Reactive, proactive | Access information collected from other resources | 2013 | Python |
| Merlin [290] | Declarative (Functional) | Dynamic and static | Reactive | Windowed history of data | 2013 | OCaml |
| Architecture | Name | Northbound IF | Developer | Found Year | Open-Source | Consistency | Scalability | Progr. Lang. |
|---|---|---|---|---|---|---|---|---|
| Logically and physically centralized control | NOX [273] | Ad Hoc-API | Nicira networks | 2008 | Yes | Strong | Low | C++ |
| NOX–MT [312] | Ad Hoc-API | Nicira networks | 2012 | Yes | Strong | Low | C++ | |
| POX [337] | Ad Hoc-API | Nicira networks | 2013 | Yes | Strong | Low | Python | |
| Beacon [313] | Ad Hoc-API | Stanford University | 2013 | Yes | Strong | Low | Java | |
| Floodlight [278] | RESTful-API | Big-switch networks | 2012 | Yes | Strong | Low | Java | |
| SE-Floodlight [314] | RESTful-API | Big-switch networks | 2013 | Yes | Strong | Low | Java | |
| Trema [315] | Ad Hoc-API | NEC corporation | 2012 | Yes | Strong | Low | C, Ruby | |
| Ryu [316] | Ad Hoc-API | NTT labs | 2013 | Yes | Strong | Low | Python | |
| Meridian [317] | Extensible-API | ONF | 2013 | Yes | Strong | Low | Java | |
| Rosemary [275] | Ad Hoc-API | ON Lab | 2014 | Yes | Strong | Low | C | |
| Maestro [318] | Ad Hoc-API | Rice University | 2011 | Yes | Strong | Low | Java | |
| ParaFlow [274] | Abstract-API | Beihang University | 2017 | Yes | Strong | Low | C++ | |
| Logically centralized, physically distributed with flat control | SMaRtLight [319] | RESTful-API | University of Lisbon | 2014 | No | Strong | High | Java |
| HyperFlow [298] | N/S | University of Toronto | 2010 | No | Weak | High | C++ | |
| ONOS [280] | Intent, REST API | Open Networking lab | 2014 | Yes | Weak, Strong | High | Java | |
| OpenDaylight [277] | Intent, REST API | Linux foundation | 2013 | Yes | Weak, Strong | High | Java | |
| Onix [300] | NVP NBAPI | Nicira Networks | 2010 | Yes | Weak, Strong | High | Python, C | |
| Ravana [320] | N/A | Princeton University | 2015 | No | Strong | Low | Python | |
| Logically centralized, physically distributed with Hierarchical control | Kandoo [308] | Java RPC | University of Toronto | 2012 | Yes | Strong | High | C, C++, Python |
| Orion [322] | N/A | Tsinghua University | 2014 | Yes | Weak | High | Java | |
| B4 [324] | RESTful-API | 2013 | No | Strong | High | Python, C | ||
| Espresso [325] | RESTful-API | 2017 | No | Strong | High | Python, C | ||
| Logically and physically distributed control | DISCO [328] | RESTful-API | Thales communication and security | 2014 | No | Strong | High | Java |
| SDX [329] | RESTful-API | Princeton University | 2014 | Yes | Strong | High | Python | |
| Cardigan [330] | RESTful-API | Victoria university of Wellington | 2013 | Yes | Strong | High | Java | |
| AtlanticWave [331] | RESTful-API | FIU, GIT | 2015 | No | Strong | High | Python | |
| Hybrid control | DevoFlow [310] | RESTful-API | University of Waterloo | 2011 | No | Strong | High | Java |
| DIFANE [334] | RESTful-API | Princeton University, AT&T labs | 2010 | Yes | Strong | High | Python | |
| OpenRouteFlow [335] | RESTful-API | Tsinghua University | 2015 | Yes | Strong | High | Python | |
| Fibbing [336] | N/A | Princeton University | 2014 | No | Strong | High | Python, C | |
| HybridFlow [338] | RESTful-API | Fudan University | 2016 | Yes | Strong | High | Java |
| Protocol | Architecture | Forwarding Model | Message Types | Open-Source | Version |
|---|---|---|---|---|---|
| OpenFlow [291] | Control plane physically, logically decoupled from data plane | Flow table | Feature request, packet-in, FlowMod, packet-out | Yes | v1.5 |
| ForCES [292] | Control and data planes logically decoupled, physically together | Logical functioning block | Configuration, notification, query, response | Yes | v1.4 |
| OpFlex [293] | Part of control plane redistributed in data plane | Policy based forwarding | Policy requests, responses, updates, withdrawals | Yes | v1.0 |
| POF [294] | Forwarding plane oblivious of the protocol | Flow instruction sets | Configuration, packet-in, packet-out, query | Yes | v1.0 |
| PCEP [295] | Logically decoupled control and data planes | Computed paths | Open, request, close, reply | Yes | v1.0 |
| OpenState [296] | Decentralize some control to forwarding plane using FSM | Stateful Flow table | Packet-in, FlowMod, packet-out, StateMod | Yes | v1.0 |
| Parameter | Wired | Optical | Wireless |
|---|---|---|---|
| Transmission range | Low (Cat6a—around 100 m) | High (single mode—2 km to 40 km, multi mode—300 m to 2 km) | Vary (4G—up to 10 km, 5G—up to few km, Wi-Fi6—50 m indoor and 200 m outdoor) |
| Attenuation | Medium (Cat6a—0.02 to 0.10 dB/m) | Low (single mode—0.0002 to 0.0004 dB/m, multi mode—0.0030 to 0.0100 dB/m) | Vary (4G—0.0005 to 0.0050 dB/m, 5G—0.0005 to 0.0200 dB/m, Wi-Fi6—0.10 to 10 dB/m) |
| Propagation delay | Medium (Cat6a—5.3 s/km) | Vary (single mode—around 5 s/km, multi mode—6.7 s/km) | Low (4G—3.5 s/km, 5G—3.5 s/km, Wi-Fi6—4.4 s/km) |
| Maximum throughput | Medium (Cat6a—10 Gbps) | High (single mode—100 Gbps, multi mode—10 Gbps) | Vary (4G—1 Gbps, 5G—20 Gbps, WiFi6—9.6 Gbps) |
| Maximum bandwidth | Low (Cat6a—500 MHz) | High (single mode—10 GHz, multi mode—2 GHz) | Vary (4G—20 MHz, 5G—400 MHz, Wi-Fi6—160 MHz) |
| Error rate | Medium (Cat6a—) | Low (single mode—, multi mode—) | High (4G—, 5G— to , Wi-Fi6— to ) |
| Communication cost | Low | Medium | High |
| Installation and maintenance cost | Low | High | High |
| Flexibility | Medium | Low | High |
| Security | Medium | High | Low |
| Electromagnetic interference | Medium | Low | High |
| Group | Sub-Group | Name | Purpose | Controller | Performance |
|---|---|---|---|---|---|
| Traffic Engineering | Policies | Roadmap [439] | Reconfiguring policies for traffic patterns | SOX, Maestro | Discuss performance of traffic engineering |
| Sincon [440] | Traffic shaping | ONOS, POX | CC throughput, forwarding times increased by 3.8, 2.86 | ||
| TSCH [441] | Traffic isolation | — | High reliability in best effort traffic | ||
| Routing | AMPS [442] | Application specific multipath flow routing | AMPS | High availability of high priority flow unloaded path | |
| DRL-QoS [443] | Application QoS aware routing | ― | Improved routing performance in complex networks | ||
| App-RS [444] | Application based routing parameters | Floodlight | Better performance for all application classes than CORouting | ||
| Load-balancing | DLB [446] | Dynamic load-balancing considering congestion | Floodlight | High throughput, low delay, packet loss in fat-tree DCN | |
| ELB-MC [447] | Controller load status, weight based balancing | Floodlight | Low communication overhead in control plane | ||
| ALBLP [448] | Use link state prediction to compute paths | Ryu | 23.7%, 11.7% better than OSPF, Q-learning | ||
| Aloba [449] | Use resource consumption metrics | Floodlight | Low overhead while reaching network requirements | ||
| S-ICM [450] | Uses measured network delay of packets | Onix | Better at avoiding system saturation than HFA, RR | ||
| SBLB [451] | Maximize resource utilization, minimize user response time | Floodlight | Significant reduction in average response, reply time | ||
| QoS provisioning | RL-QoS [195] | Select routing algorithm for QoS traffic flow | Floodlight | Best trade-off between QoS vs. QoE | |
| ARVS [452] | 2 QoS levels for base, enhancement layer packets | Floodlight | Reduce 77.3% PLR, 51.4% coverage against OpenQoS | ||
| Q-flag [225] | Flow rule aggregation based on application QoS | POX | Reduce average delay, QoS-violated flows by 22%, 30% | ||
| QAR [453] | Finds paths based on application QoS requirements | ― | Better blocking probability, dimension reduction | ||
| Network management | Fault management | NetRevert [455] | Network checkpointing and rollback | ― | Improvements on affected delay during failure |
| SPIDER [456] | Detects link failures using stateful switches | Ryu | Losses are always lesser than OpenFlow | ||
| LegoSDN [457] | To recover from application failures | Floodlight | Recover failed apps 3× faster than controller reboot | ||
| MSAID [458] | Application interference detection, mitigation | Floodlight, ONOS | Detect known and unknown interference within minutes | ||
| RADAR [459] | Traffic monitoring for network troubleshooting | OpenDaylight | Reduced cost and ties into business metrics | ||
| FatTire [460] | Write fault tolerant programs | ― | Able to respond extremely rapidly to failures | ||
| Mobility management | MM [461] | Inter- and intra-domain handover | ― | Improved handover and resource utilization efficiency | |
| SVHAF [462] | Fuzzy logic, MPTCP for handover | ― | No ping-pong effect, high QoS, low undesired handover | ||
| APV [463] | Using LVAPs for handover | ― | Handover resulted less significant delays or packet losses | ||
| CCT [464] | Channel scheduling cooperation for downlink | Ryu | Good throughput, channel utilization, packet loss rate | ||
| DCR-CRN [465] | Decide optimal number of reserved channels | ― | Reduced SU cost, network unserviceable probability | ||
| HAC [466] | HAC to mitigate interference | ― | Improves system payoff, less interference, high SE | ||
| WiFi-D2D [467] | Wi-Fi device-to-device offloading | ― | Improved offloading performance | ||
| JRRA-BO [468] | Radio resource allocation, beamforming optimization | ― | High achievable sumrate, low power consumption | ||
| LayBack [469] | Resource sharing among wireless technologies | ― | Increased revenue rate compared to CRAN | ||
| Openradio [470] | Decouple wireless protocol definition from hardware | ― | Can modify the PHY, MAC layers to implement protocols | ||
| Energy management | ECCKN [472] | Policies to shutdown/sleep links, devices | ― | Improved network lifetime, number of alive, solo nodes | |
| DVFS [473] | Dynamic Voltage and Frequency Scaling | ― | Low power consumption at any operating frequency | ||
| SENAtoR [474] | Energy aware routing and services | Floodlight | Reduce energy consumption by 5% to 35% | ||
| GETB [475] | Services to test energy aware traffic engineering | ONOS | Provides a platform to evaluate energy efficiencies | ||
| CHS-NFV [477] | Save energy using blockchain, NFV, CHS algorithm | Floodlight | High throughput, low response time, gas consumption | ||
| ILP-NFV [478] | Optimize energy consumption using NFV nodes | Contiki | Reduced communication energy consumption, high PDR | ||
| EATS-DRL [479] | Application based task scheduling to reduce energy | Ryu | Upto 50% less time delay, 87% energy saving | ||
| Security | Access control | AC [480] | Resources, security, reconfiguration conflicts aware AC | ― | Easier to detect and resolve conflicts |
| AC-Integrate [481] | User and flow level AC | ― | Design and feasibility of a global AC system is studied | ||
| Controller-DAC [482] | Application level dynamic AC | ODL, ONOS, FL, Ryu | Prevent API abuse—less than 0.5% performance overhead | ||
| SEAPP [483] | Secure application management framework for AC | Floodlight | Effective security with negligible overhead | ||
| E-ABAC [484] | Extended attributes based AC | POX | Effective access control with little impact on response time | ||
| BENBI [485] | Dynamic AC using broadcast encryption | Floodlight | Scalable as cost is independent of SDN entities | ||
| SILedger [486] | Decentralized AC using blockchain, encryption | ― | Effective AC with negligible overhead | ||
| P4-sKnock [487] | P4-based 2-level host authentication, AC | ONOS | Authenticate a new host within 500 ms, prevent attacks | ||
| RBAC [488] | Role-based AC using custom permissions | Floodlight | Feasibility of custom permissions enabling AC is studied | ||
| SC [489] | Use blockchain for creating AC policies | SDN-WISE | Node size does not affect resource access delay, throughput | ||
| BEAM [490] | Behavior-based AC | ― | No performance analysis presented | ||
| PBAC [491] | Encryption, certificate based AC using blockchain | ― | Prevent several potential attacks, better performance | ||
| VPN | MPLS-VPN [492] | Update IPSec policy of the MPLS VPN tunnels | ― | Results in QoS improvement | |
| SD-VPN [493] | Each application is allocated with own overlay VPN | OpenDaylight | Improves scalability of overlay VPN, security, low cost | ||
| P4-ipsec [494] | P4 switch-based concept for IpSec VPN | ODL, ONOS | Security use cases have benefit from P4 | ||
| Firewall | Pre-Firewall [495] | Monitor firewall rules to avoid collision, redundancy | Floodlight | No performance evaluation presented | |
| ACLSwitch [496] | Filter traffic at switch domains | Ryu | Control network behavior holistically, compartmentally | ||
| FlowTracker [499] | A stateful firewall with adaptive connection tracking | POX | Low controller processing and overhead, latency increment | ||
| SFE-SBS [500] | Context aware stateful firewall | POX | Distributed controllers perform better than centralized | ||
| FleXight [501] | Detect horizontal port scans | ― | Detects 99% susceptible victims with 0.75% overhead | ||
| ChainGuard [502] | Filter traffic based on source legitimacy for BCs | Floodlight | Mitigate DoS and DDoS flooding attacks | ||
| DRP [503] | Firewall rule updating policy using ILP | Ryu | Less computation time to have optimized rule placement | ||
| P4guard [504] | Protocol independent, platform agnostic P4 firewall | ClickOS | Faster packet processing time, lower network latency | ||
| Anomaly/ Attack/ Intrusion detection | IDPS-PB [506] | Behavior-based intrusion detection:port scanning, DoS | POX | False positive rate decrease with threshold increment | |
| ABID-ML [507] | Anomaly-based intrusion detection using ML | ― | Decision tree ML classifier has the best performance | ||
| EID [508] | Signature-based intrusion detection for DoS | ― | Classification accuracy reaches 99.7% for random forest | ||
| CDID [509] | Attack and source identifying anomaly detection | ― | Identifying probability 0.89, 0.93 for centralized, distributed architectures | ||
| CIDN [510] | Challenge-based collaborative intrusion detection | POX | Resist the newcomer attack and betrayal attack | ||
| CIDS [511] | Collaborative intrusion detection using ML | ― | Good precision, recall, accuracy, F1-score | ||
| SBCIDN [512] | Blockchain for trust-based communication in CID | Ryu | 96% true positive rate for detection | ||
| HMM-NIDS [513] | Self-learning IDS using HMM | Floodlight | Packet flagged percentage for different datasets are shown | ||
| ML-NIDS [514] | Self-learning IDS using GRU-RNN | POX | 89% and 99% accuracy for NSL–KDD, CICIDS2017 | ||
| Network virtualization | ― | FS-VANET [515] | Multi-tenancy in multiple service provider networks | ― | No performance analysis is presented |
| FlowVisor [516] | Network slicing using MAC | POX | Results on tenant isolation is presented | ||
| FlowVisor-RB [517] | Role-based network slicing using VLAN tags | Floodlight | Flow setup latency reduced by 14% to 60% | ||
| VeRTIGO [518] | Advanced and dynamic network slicing | ― | No performance analysis presented | ||
| DRA-VTN [519] | Routing and resource planning in a VTN | ― | High routing assignment efficiency, bandwidth utilization increment | ||
| MNFV [520] | Multipath network function virtualization | ― | Superior performance wrt. load balancing | ||
| ONVisor [521] | Network virtualization framework | ONOS | Low control plane, similar data plane performance | ||
| T-AQoS-VN [522] | QoS control in virtual networks | ― | 1.6 times performance improvement vs. other approaches | ||
| ECB-WNV [523] | Secure network virtualization with blockchain | ― | High per user throughput when network is overloaded | ||
| Big data | ― | SDB–BDS [524] | Management of big data | ONIX, POX, Ryu, FL | Use cases are discussed |
| ODM-BD [525] | Decision making for big data processing | ― | Low energy consumption, delay, cost | ||
| Typhoon [526] | Big data streaming framework | Floodlight | Better throughput, management of running applications | ||
| BigDataSDN-Sim [527] | A simulator for analyzing big data applications | Floodlight | Improve performance of MapReduce applications | ||
| AmoebaNet [528] | QoS guaranteed network service for big data | ONOS | Solves last mile and scalability problems in big data | ||
| BD-QoS [529] | Big data technologies to manage QoS | POX | Used ML to discover correlations, make predictions | ||
| AWESoME [530] | A web service manager application for BD | ― | Scalable, negligible load, reproducible | ||
| BD-ML-NFV [531] | Apply ML, NFV for big data traffic clustering | ― | High accuracy in traffic clustering, forecasting | ||
| BD-ML-NFVS [532] | Apply ML, NFV for big data network slicing | ― | High accuracy in traffic classification, took 5.7 min | ||
| Cloud computing | ― | NFV-C [533] | NFV in cloud computing | ― | Reduce server response time, improve QoE |
| CC-O [534] | Orchestration integration with cloud computing | OpenDaylight | Setup delay time varies in range 2.5–5 s | ||
| ENA-VM [535] | Energy, apps, network aware VM placement | ― | Minimizes energy consumption, placement cost, communication traffic | ||
| CENSOR [537] | QoS guaranteed routing for cloud applications | ― | Feasible and effective for a SmartCity usecase | ||
| Blk-sdotcloud [538] | Blockchain-based security for clouds | OpenDaylight | Better throughput, response time, fast file transformation | ||
| IS-VCC [539] | Incident supporting visual cloud computing solution | ― | High QoE, throughput, low latency, congestion | ||
| Data center networking | ― | HESM [540] | Switch migration for controller load balancing | Ryu | Reduce migration cost, improved load-balancing |
| Cont-proxy [541] | Network management of data centers | Floodlight | Reduce controller workload, improve scalability | ||
| SDTCP [542] | Congestion control of large data centers | Floodlight | Burst flows: High tolerance, Short flows: better flow completion time | ||
| ERM-DC [543] | Resource management application in data center | ODL, POX, NOX | 77%, 37%, 63%—energy saving, RT delay, bandwidth utilization | ||
| Business | ― | IBA [544] | Intent-based business applications | ONOS | Appropriate, effective, realizable, practical for business applications |
| FlowVista [545] | Translate business policies to network flows | OpenDaylight | Portability, low bandwidth, integratability | ||
| HPC-BE [546] | High performance computing for business environment | ― | 60–80% bandwidth utilization, 45–60% throughput | ||
| EIP-CF [547] | Enterprise integration pattern communication framework | Ryu | Improved security, efficiency, reliability of enterprise networks | ||
| CACS [548] | Context aware communication framework for business | Ryu | Protects anonymity, computationally complexity is O(N) |
| Name | Research Area | Organization | Site Address |
|---|---|---|---|
| IEEE P2302 SIIF: Reference architecture and taxonomy framework | Interoperability, security, service orchestration, governance, and taxonomy for different types of cloud services and environments | IEEE | https://standards.ieee.org/ieee/2302/7056/ (accessed on 7 April 2023) |
| IEEE P2413 Standard for an Architectural Framework for the Internet of Things (IoT)—Semantic interoperability | Semantic interoperability, semantic models, semantic data representation and exchange, data interoperability and integration, metadata and annotations, security and privacy, service discovery and composition, context modeling and management, ontology engineering, knowledge representation and reasoning, machine learning and data analytics, standardization, and governance of IoT | IEEE, AIOTI, oneM2M, and W3C | https://standards.ieee.org/ieee/2413/6226/ (accessed on 7 April 2023), https://standards.ieee.org/news/semantic_interoperability/ (accessed on 7 April 2023) |
| Stratum project | Programmable data plane, intent-based networking, network automation, network security, network telemetry | ONF | https://opennetworking.org/stratum/ (accessed on 8 April 2023) |
| LSO Sonata | AI/ML network service orchestration, network slicing, intent-based networking, edge computing | MEF | https://www.mef.net/service-automation/lso-apis/inter-provider-apis/lso-sonata/ (accessed on 8 April 2023) |
| ITU-T group 13 | Next-generation networks, future networks and emerging technologies, cloud computing | ITU-T | https://www.itu.int/en/ITU-T/about/groups/Pages/sg13.aspx (accessed on 8 April 2023) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wijesekara, P.A.D.S.N.; Gunawardena, S. A Comprehensive Survey on Knowledge-Defined Networking. Telecom 2023, 4, 477-596. https://doi.org/10.3390/telecom4030025
Wijesekara PADSN, Gunawardena S. A Comprehensive Survey on Knowledge-Defined Networking. Telecom. 2023; 4(3):477-596. https://doi.org/10.3390/telecom4030025
Chicago/Turabian StyleWijesekara, Patikiri Arachchige Don Shehan Nilmantha, and Subodha Gunawardena. 2023. "A Comprehensive Survey on Knowledge-Defined Networking" Telecom 4, no. 3: 477-596. https://doi.org/10.3390/telecom4030025
APA StyleWijesekara, P. A. D. S. N., & Gunawardena, S. (2023). A Comprehensive Survey on Knowledge-Defined Networking. Telecom, 4(3), 477-596. https://doi.org/10.3390/telecom4030025







