Abstract
Blockchain, also known as a distributed ledger technology, stores different transactions/operations in a chain of blocks in a distributed manner without needing a trusted third-party. Blockchain is proven to be immutable, which helps with integrity and accountability, and, to some extent, confidentiality through a pair of public and private keys. Blockchain has been in the spotlight after successful boom of the Bitcoin. There have been efforts to leverage salient features of Blockchain for different applications and use cases. This paper presents a comprehensive survey of applications and use cases of Blockchain technology for making smart systems secure and trustworthy. Specifically, readers of this paper can have thorough understanding of applications and use cases of Blockchain technology.
1. Introduction and Overview of Blockchain
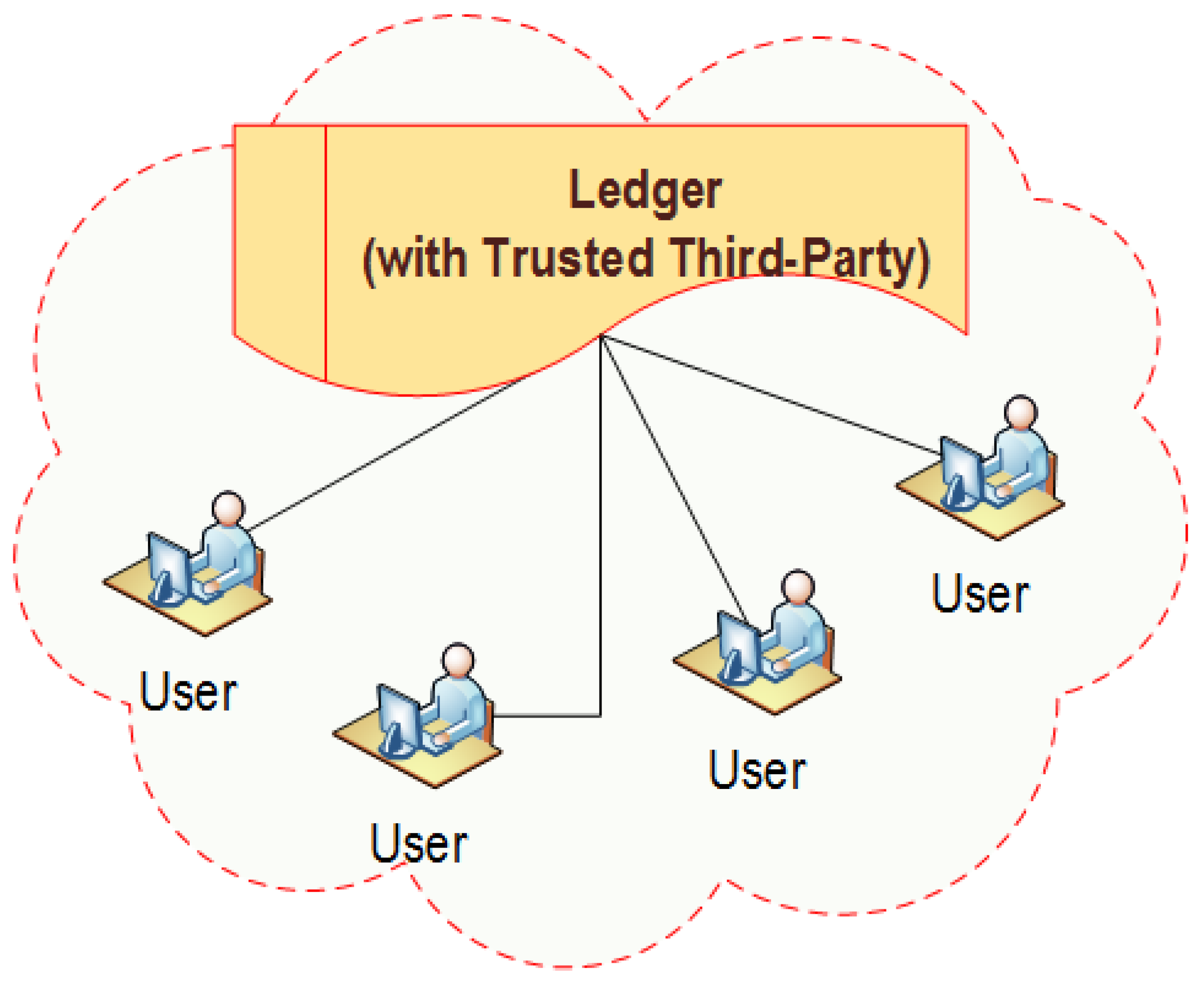
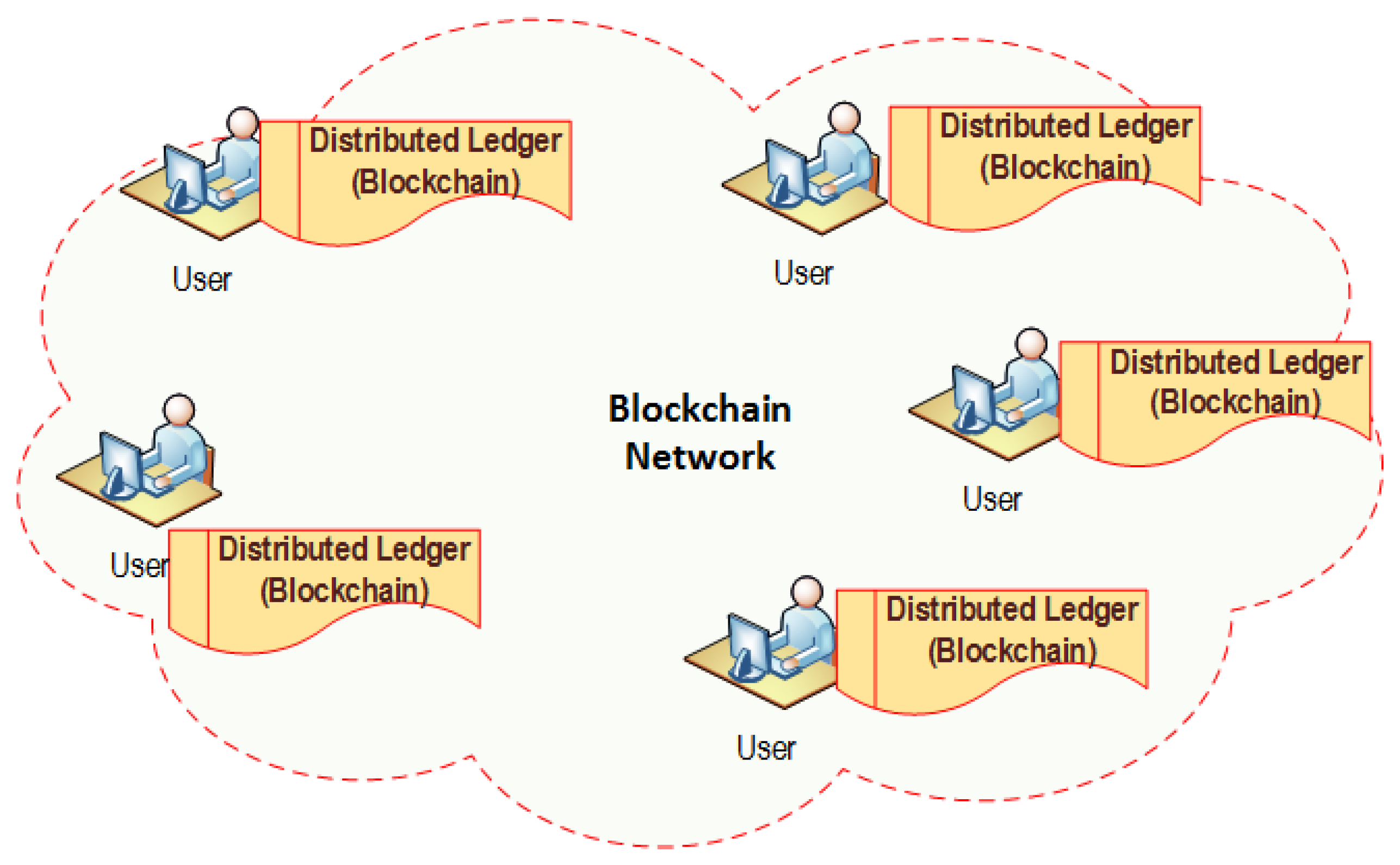
Blockchain technology is the underlying mechanism for cryptocurrencies such as Bitcoin [1]. Bitcoin, the cryptocurrency introduced in 2009, peaked a record high valuation in the December of 2017 [2] and created a hype around digital currency. Since the debut of Bitcoin, there has been several cryptocurrencies in the market holding a market cap in billions of dollars [3]. Blockchain was first introduced in 2008 and implemented as the infrastructure of Bitcoin in 2009 by Satoshi Nakamoto, an unknown person or a group [1]. Blockchain is essentially a “distributed ledger or database” where all the transactions are documented regarding all the participating parties. Blockchain is a chronological chain of blocks, where each block can be considered as a page in a ledger. The chain grows continuously as miners discover new blocks that they append to the existing Blockchain. Each transaction is broadcasted in the network via cryptographic communication while miners would try to collect as many transactions as they can and verify them using “proof-of-work” and create a new block. Miners would compete with each other to create such blocks. Once a winning block is appended to the Blockchain, a new copy of the block is broadcasted to the entire network, thus, creating a decentralized public ledger. While miners are responsible to verify transactions and update the Blockchain, they are incentivized with rewards. Note that the traditional ledger technologies need a trusted third-party such as a bank, as shown in Figure 1. However, the Blockchain-based technology runs on peer-to-peer network, as shown in Figure 2, where a centralized trusted third party is not needed for managing the transactions. As issues such as double-spending are mitigated through consensus of miners, this system does not require an intermediary, that is, a centralized trusted third party, as shown in Figure 2.
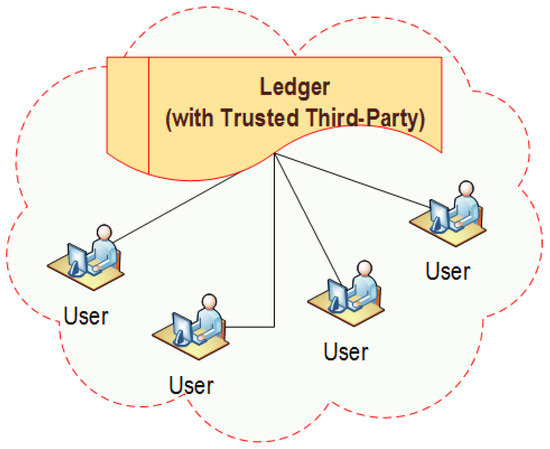
Figure 1.
Traditional centralized ledger technology with a trusted third-party.
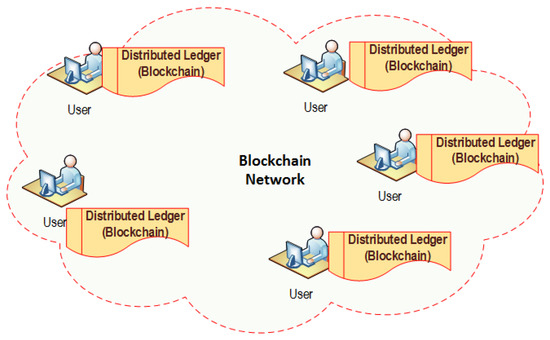
Figure 2.
A typical example of Blockchain technology—distributed ledger technology—without a trusted third-party.
Although Blockchain is widely used for cryptocurrencies such as Bitcoin, this technology can also be applied to other applications. The Blockchain technology enables financial services without having financial institutions such as a bank or other intermediary involved, as shown in Figure 2. It can be implemented to conduct services such as online payment, digital assets, and remittance [4]. The key features of Blockchain technology—decentralization, immutability, integrity, and anonymity—make it applicable to non-financial domains such as smart contracts [5], the Internet-of-Things [6], reputation systems [7], security services [8,9,10,11], wireless network virtualization [12], and other different applications [13,14,15,16,17,18,19,20,21,22].
In this paper, we briefly discuss the history and architecture of Blockchain followed by its applications and use cases in different domains. Although the technology has been widely praised and discussed in academia and industry for different applications, a comprehensive documentation of its emerging applications and use cases are rarely found in the literature. We note that there are several survey papers [23,24,25,26] that cover either part of huge range of applications, security challenges or one application only.
2. Brief History of Blockchain Technology
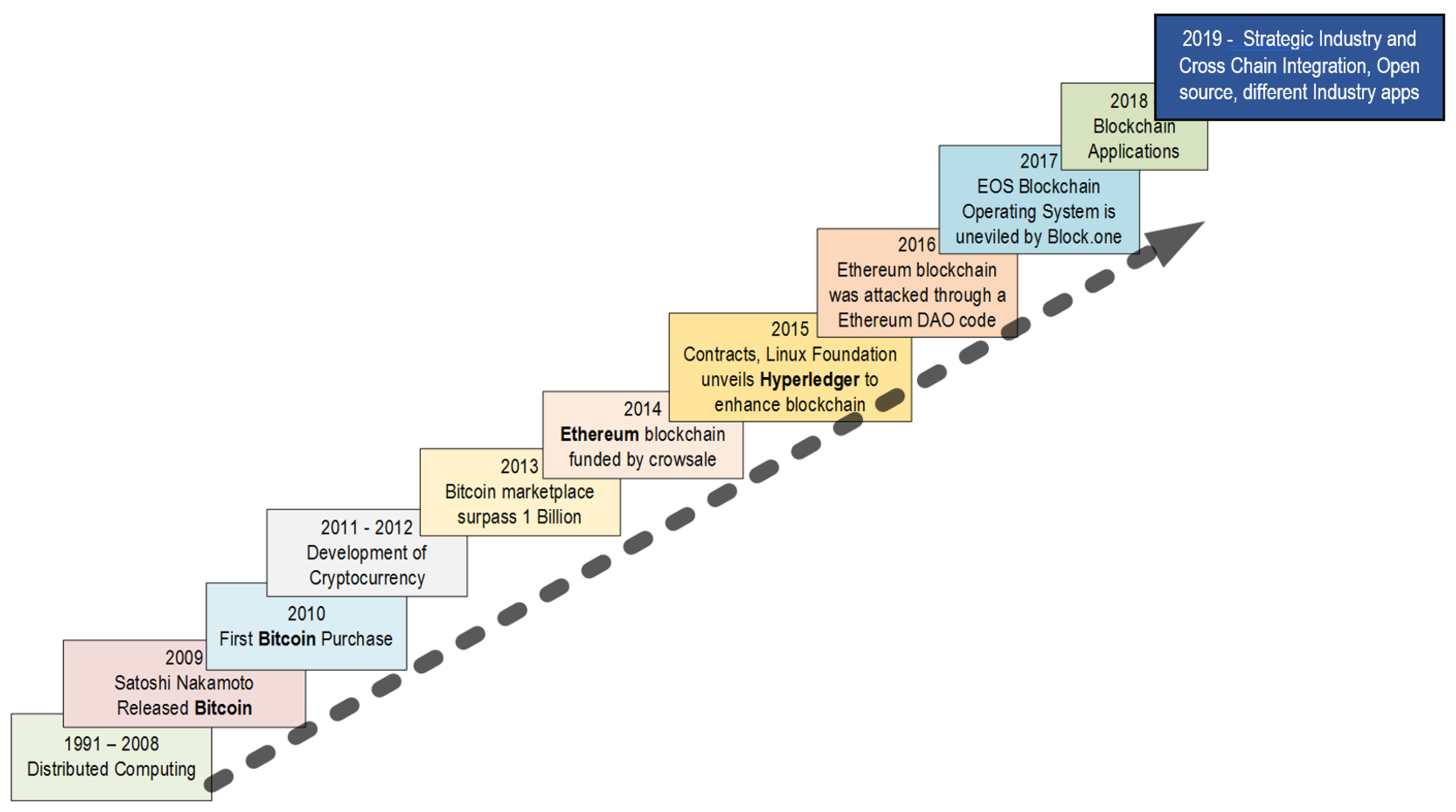
Although the technologies involved in Blockchain such as cryptographically secured chain of blocks [27] and Merkle trees [28] were developed in the early 1990s, the first Blockchain was conceptualized and implemented Satoshi Nakamoto in 2008 [1]. The history and key milestones of Blockchain technology are depicted in Figure 3. The work was published on a paper entitled “Bitcoin: A Peer-to-Peer Electronic Cash System”. The paper introduced a peer-to-peer version of digital cash that can function with having any central authority such as bank to verify transactions. Bitcoin was the first implementation of this technology. After the publication of [1], an open source program was published by the same author that began with the Genesis block of 50 coins.
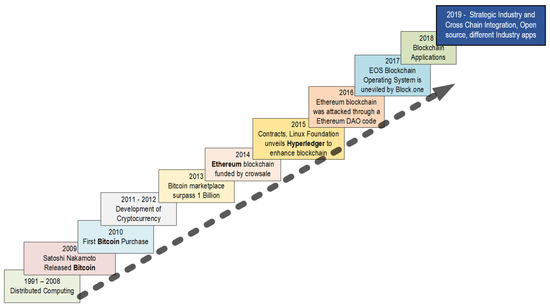
Figure 3.
The history and milestones of Blockchain technology.
3. Types of Blockchain and Consensus Mechanisms, and Block Architecture
3.1. Types of Blockchain and Consensus Mechanisms
Typical blockchain could be implemented either as permissioned or permissionless [1,29].
- Permissioned blockchain: In Permissioned blockchain, networks will not be be open to all but participants are preapproved by a designated authority. Quorum-based blockchain is a permissioned one [29] where the consensus protocol is called QuorumChain and the majority voting protocol is used. Quorum is fast as it is based on majority voting.
- Permissionless blockchain: In Permission-less blockchain, networks will be open to all participants. Blockchain used in Bitcoin is permissionless [1]. The Consensus protocol used in permissionless blockchain is poof of work. The poof of work makes the permissionless blockchain slow as all participants will have to reach to consensus to make a decision.
Note when more than 50% participants are malicious, blockchain is vulnerable to attacks [1,29]. Moreover, to make blockchain fast, directed acyclic graph (DAG)-based technology has been proposed that consumes less time for proof of work [30].
Note that the typical blockchain has following three components: Distributed Ledger, Smart Contacts, and Distributed Applications.
- Distributed Ledger using distributed digital ledger technology (DLT).
- Smart Contacts that provide a way to express transctions stored in the Distributed Ledger.
- Distributed Applications that are built for end users.
3.2. Block Structure
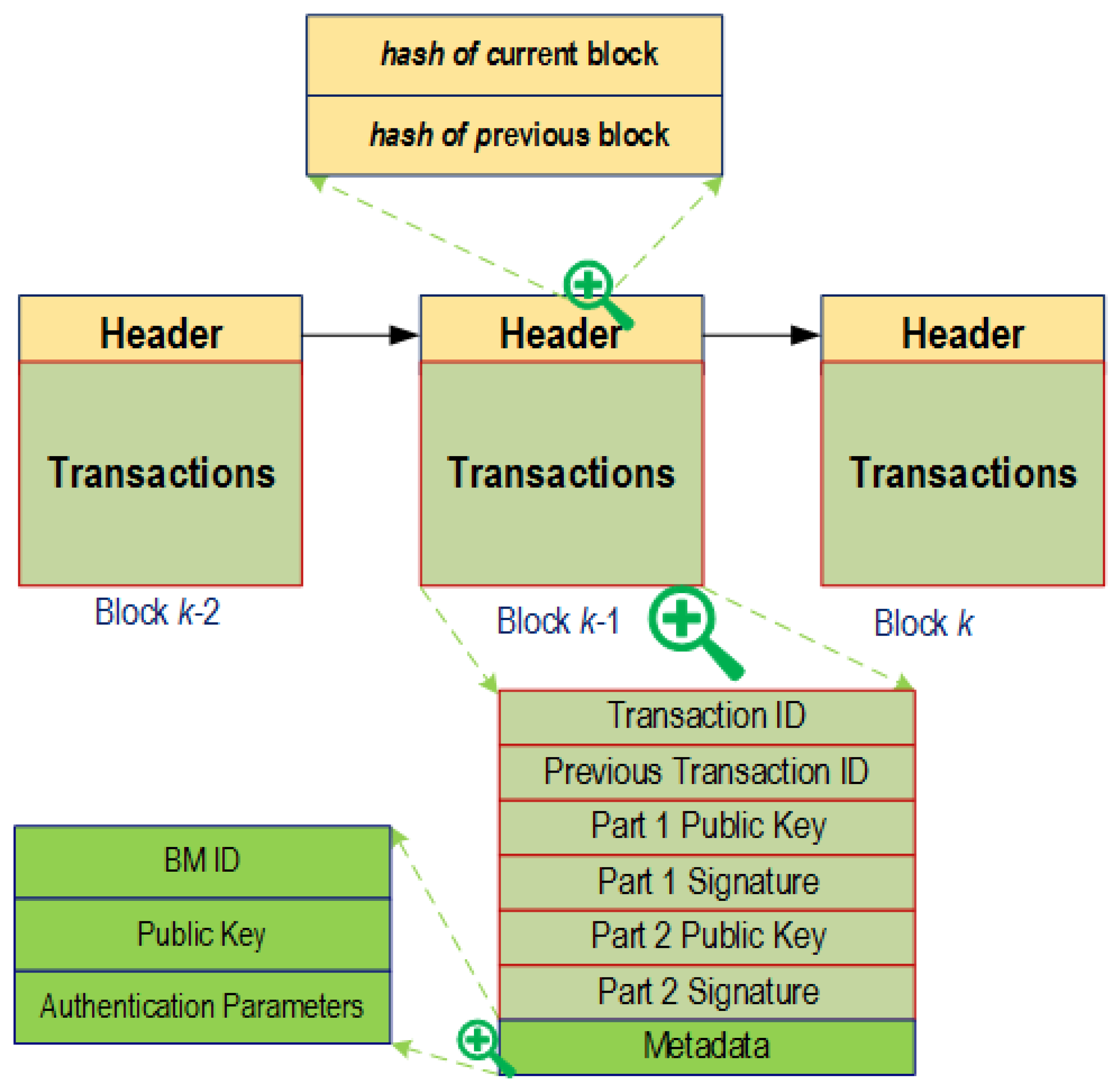
Blockchain is a chronological sequence of block where each block holds a complete list of transactions, as shown in Figure 4. It follows the data structure of linked list, where each block points to a previous block through the reference of the hash value of the previous block, also called parent block. The first block of a Blockchain, the genesis block, has no block to point to. A block is composed of metadata (block header) and list of transactions (block body). The metadata includes block version, parent block hash, Merkle tree root hash, timestamp, and nonce. Nonce is an arbitrary number which is used in the cryptographic communication within the user network.
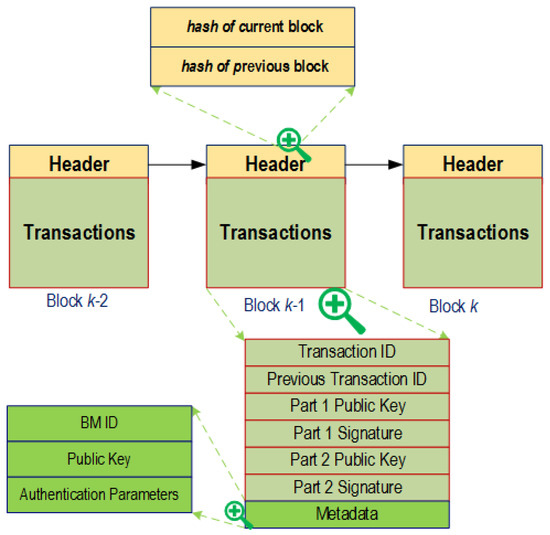
Figure 4.
Typical Blocks with header and transactions in Blockchain technology.
Digital signature is required to establish a secure communication between the users in Blockchain network. Each user is assigned with a public and a private key. When a user broadcasts a transaction to the network, the user signs the transaction using the private key. Later, the recipients use the user’s public key to verify the transaction. Such cryptographic communication preserves the integrity of the transaction within the network.
In a blockchain, a nonce (number only used once) is a number added to a hashed/encrypted block when rehashed to meet the difficulty level restrictions. As in general cryptography, finding nonce is difficult in blockchain and is considered a way to weed out the unrelated/incapable miners.
4. Applications and Use Cases of Blockchain
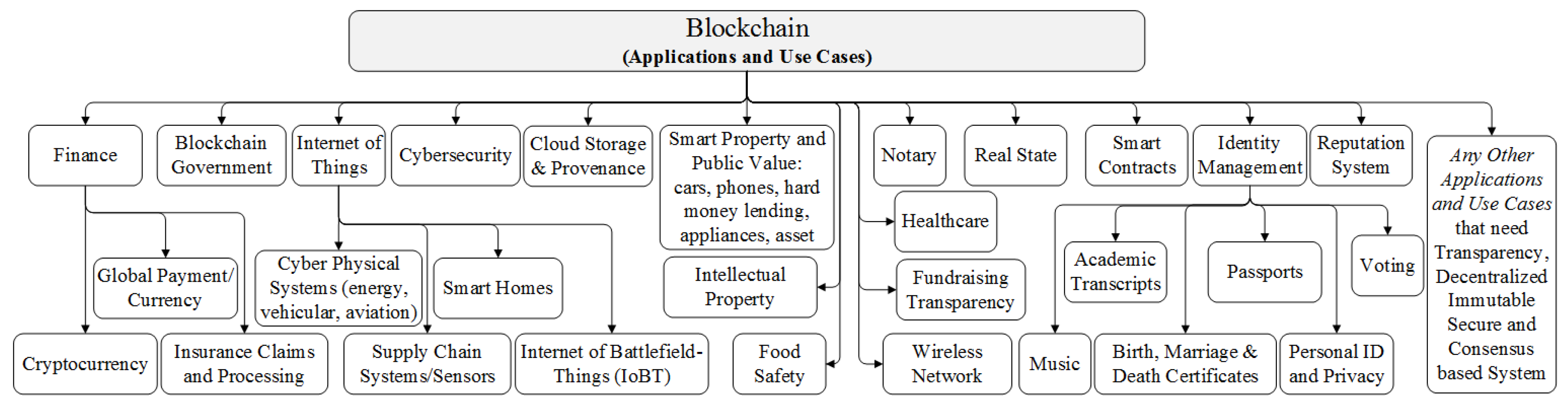
After successful implementation of Blockchain in Bitcoin [1] because of its salient features, Blockchain has been proposed to be used in different applications and use cases, as shown in Figure 5. We present a brief overview of each domain in the following section.
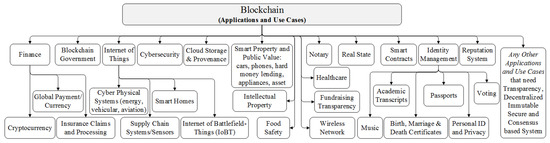
Figure 5.
Different Blockchain applications and use cases.
4.1. Finance
Conventionally, an intermediary such as a bank, verifies and processes the financial transactions. Having such a centralized system puts immense work in the hand of intermediaries, meanwhile the transactions are prone to errors as multiple uncoordinated parties are required to keep the record and adjust them. Thus, the entire process is time-consuming and costly. The Blockchain simplifies such complications associated with financial services by introducing a distributed public ledger, where the transactions are verified by the miners using “proof-of-work” [2]. As each node in the Blockchain network has a copy of the updated Blockchain, there is transparency regarding the transactions, as shown in Figure 2. As the blocks are chronologically arranged, once a block is added to the Blockchain with a verified transaction, the entire Blockchain is immutable. Thus, attackers cannot manipulate the transactions once it is registered into the system. In case of a conflicting Blockchain where branching might occur, miners always go for the longest chain, as the longest chain is more reliable. With such secured communication protocol and robust verification method, it creates an effective system to improve our existing financial services.
4.1.1. Cryptocurrency
Cryptocurrency, which holds a market cap in the billions of dollars [3], has been possible with the help of Blockchain [1]. Specifically, the bitcoin, proposed by a programmer known as Satoshi Nakamoto, is based on cryptographic techniques that allows the recipient to receive money securely/genuinely without requiring a trusted third party, such as a bank or a company like PayPal [3]. The Bitcoin network relies on a Blockchain—a distributed transaction public ledger—where a new block is generated by executing a consensus algorithm such as Proof-of-Work [3]. It has been noted in [3] that it is practically impossible to get the someone’s private key from his/her public key which prevents users from impersonating attacks. To do a transaction, the Bitcoin client software performs a mathematical operation to combine the recipient’s public key and sender’s (i.e., your own) private key along with the amount of Bitcoins that you want to pay/send. Then the transaction is sent out to distributed Bitcoin network so as to verify by Bitcoin software clients/users other than the sender and recipient. All Bitcoin users that are on-line—other than sender and recipient—check (1) whether a true owner sent the money by exploiting mathematical relationship between its public and private keys; (2) the public transaction log stored on the computer of every Bitcoin user to make sure that sender has the Bitcoins to spend. It is reported in [1] that it is practically impossible to generate malicious transactions to spend another person’s Bitcoins.
4.1.2. Global Payments (Global Currency)
Global payments become complicated and time-consuming because there are many intermediaries involved to verify the transactions. The entire process can be prone to error and costly. These issues arise essentially due to the centralization of the monetary transactions where institutions such as banks and other financial firms dictate processes, and they are responsible to verify the transactions. The Blockchain technology reduces such complexities by introducing the decentralized public ledger and robust verification method to verify the transactions. Within this peer-to-peer network, global payments are quicker, verifiable, immutable, and safer. There are several remittance companies [31] such as Abra and Bitspark that are already using Blockchain technology for remittance services.
4.1.3. Insurance Claims and Processing
Insurance claim has been dealing with several fraudulent claims. Moreover, there must be updated policies and data associated with each claim to properly process an insurance claim which is difficult to handle in traditional approaches. With Blockchain technology, the process can be handled through Blockchain (distributed ledger technology) efficiently in a secure manner. Similarly, any fraudulent claims/transactions can be detected and dropped with a good confidence as multiple participants/miners need to agree on the validity of each transaction. This makes sure the insurers settle their claim which they deserve quickly and effectively.
4.2. Blockchain Government
In order to build trustworthy and effective government operations through collaborative and transparent networks, different government organizations and units can use Blockchain technology. Blockchain technology with its salient features will help provide accountability, transparency and trust among stake holders such as citizens, leaders, government officials, and their different operations [4,32]. Government is required to make its affairs transparent in order to address the accountability of its bodies. In order to do so, government might have to make a great amount of data open to the public [32]. As per the report from McKinsey [33], open data made available to the public in the Internet can benefit the people in an order of trillions of dollars. Several entities can use open data to expose illegitimate doings. The public can question the quality of health-care, and food supplies with given open data which eventually makes the system more fair and trust [33]. Therefore, releasing the data to the public is helpful for the economy, but it also has its own challenges to make the data public. When the data is released only once a year, it is largely left unnoticed by the public. Thus, an alternative to this can be a Blockchain government, where the data is distributed in the public ledger, and is open to the public all the time. Moreover, smart contracts can be used to ensure the electorates work in the favor of the electors. The contracts can be based on the manifesto of the electorates, and they only get paid once they meet the demand of the electors via the smart contracts. This kind of technology can put the electorates in check and possibly enforce them to fulfill their promises.
4.3. Internet of Things (IoT)
The number of electronic devices getting connected to the Internet is rapidly increasing every year [34]. With the massive number of devices interlinked to each other creates the Internet-of-Things (IoT). The IoT is expected to transform the way of lives where ideas like smart homes is feasible. While this new phenomenon is likely to make lives easier, having massive number of heterogeneous devices connected to the Internet creates graves issues regarding cyber security and privacy. The Blockchain can be an important technology to secure IoT. Having millions of devices connected to each other and communicating, it is important to ensure that the information flowing through IoT remains secured and makes the participants accountable.
4.3.1. Energy Cyber Physical System
Smart energy grid systems are becoming complex cyber-physical systems (CPS) where complex interactions among power generation, distribution, utility offices and users happen in a bidirectional manner [35]. Salient features of Blockchain technology provide a secure and verifiable environment to support interactions in energy CPS [36].
4.3.2. Vehicular Cyber Physical System
Vehicular cyber physical system is regarded as the backbone technology for intelligent transportation systems, unmanned aerial vehicle (UAV) [37] networks, and autonomous driving [35,38] for improving road safety and traffic efficiency. Security and privacy in vehicular cyber physical system are always central issues since vehicles are ties to the private information of their owner, driver, or renter. Blockchain, with its features such as decentralization, immutability, integrity, and anonymity through a pair of public and private keys, can be leveraged to build a smart and secure autonomous intelligent transportation system [37,39].
4.3.3. Blockchain in Aviation Systems
Blockchain in the aviation industry can offer robust collaborative partnerships among service and product providers to offer travel services as well as products in a distributed secure way. Smart contracts could streamline the interactions among businesses and different units within the business [40].
4.3.4. Supply Chain Systems/Sensors
Smart sensors can be helpful for the companies to gather information regarding the supply chain as they are transported around the globe. Several leading supply chain companies are reported to use smart sensors to track supplies. Therefore, the number of such sensors is expected to grow rapidly in near future. Having such a massive distribution of sensors, there will be enormous amount of data to be collected and analyzed. Blockchain technology can be used for disruptive transformation for efficient and secure supply chains and network [41].
4.3.5. Smart Homes
Blockchain in the context of smart homes with IoT devices can help to have secure and reliable operations for smart home operations [42]. However, implementation of Blockchain in such resource constrained IoT systems is not straightforward because of high resource demand required for proof-of-work, limited storage capacity, low latency, and low scalability [42].
4.3.6. Internet of Battle-Field Things (IoBT)
Internet-of-Battle-field Things (IoBT) is regarded as the backbone for smart defense and warfare applications where Battle-field Things such as combat equipment, unnamed aerial vehicles, ground vehicles, and fighters with sensors can collect intelligent information to enable informed decision real-time in a secure and immutable manner. Note that the IoBT is so diverse that it consists of different devices (combat equipment, unnamed aerial vehicles, ground vehicles, and fighters), platforms, networks, and connectivity. This diversity poses several challenges for secure, privacy-aware, and trustworthy battlefield operations such as communication and computing. Blockchain technology can help to have secure and reliable operations for IoBT [43].
4.4. Cybersecurity
Another application of Blockchain is cybersecurity to combat future attacks, where threat information can be shared by using Blockchain among participants/organizations to combat future cyber-attacks [9,11]. For instance, different organizations or countries are hesitant to share their cyber attack or threat information to others since competitors could misuse the information to take advantage unilaterally when information is shared with identifiable information. However, using blockchain with the help of public and private key pair (like in Bitcoin [3]) information can be shared without revealing identifiable information except public key (like in Bitcoin [3]). This ensures that the organizations or countries could share threat information sharing without worrying about the competitors misusing the shared information to take advantage unilaterally. However, Blockchain will not be able to fix everything but its features can be leveraged to harden the systems against multitude of cyber threats.
4.5. Smart Property and Public Value
All entities/property such as house, land, automobiles, stocks, etc. can be represented in the ledger technology and Blockchain can be used to keep the track of all operations and property records. Once the records are kept in the Blockchain they are shared with all the concerned or participating parties which can easily be used to establish contracts and verify them. Thus, with a decentralized ledger, any lost record can be duplicated from the network and immediately can be used to recover the loss [44].
4.5.1. Hard Money Lending
Hard money lending serves people to mitigate financial burdens in the short term. It requires the borrower to have property such as real estate as a collateral. Thus, it is important that the collateral is legit and trustworthy. Lenders can lose money if the collateral is not redeemable. Similarly, the borrower might also lose its property if the lender uses fraudulent policies as part of the agreement. With Blockchain, both the property and the policies can be encoded in the ledger and distributed among the users. This will create a healthy setting where people can trade with complete strangers due to the transparency and security of the Blockchain. Smart contracts can be deployed using Blockchain for this kind of scenarios.
4.5.2. Cars and Phones
Personal devices such as phones are protected using authentication keys. Similarly, cars are only accessible to the owners using smart keys. This kind of technology is possible with cryptography, and yet, such methods can fail if the authentication key is stolen or copied or transferred. Such issues can be fixed in the Blockchain ledger where users/miners can replace and replicate lost credentials.
4.5.3. Smart Appliances
Smart appliances are essentially electronic devices aided with cyber system such that the cyber portion can communicate information regarding environment around the device and the device itself. It is essentially about the idea of a “talking toaster” where a toaster can give its user information relevant to its usage. A home connected with smart appliances can be considered a smart home, where the cyber physical system tries to optimize the functionalities of the smart devices, providing maximum utilities to its users. With so many devices involved as part of smart appliances, we can encode them in the Blockchain as smart property. Such practice could easily ensure the ownership of a user over these devices.
4.5.4. Asset Management
Asset management involves multiple parties where each party is required to keep the transactions. While keeping the same transaction in different places can make the entire process inefficient and prone to errors. To make matters worse, asset management might also involve cross-border transactions, adding more complexity to verify the transactions. Such issues can be dealt with a distributed ledger where each party can have a copy of the entire transactions and get updated about each transaction using cryptographic communications [45]. This improves the efficiency and reduces the cost as there would be no intermediary to verify the transactions.
4.6. Cloud Storage and Provenance
Metadata that records the history of the creation and all operations including file/data accessing activities can be kept in the Blockchain which then be shared with all stakeholders. Data provenance through Blockchain is important for applications like accountability and forensics [46]. For instance, when different users access and make changes in the collaborative documents such as files shared through Google document, users could make changes and those changes are stored in the blockchain. By storing all edits and changes that are made are saved in the blockchain. Again, using features of blockchain and provenance, integrity and accountability in cloud storage and processing can be maintained. Similarly, in cloud storage, when multiple users accessing and changing the contents, it will be easy to keep track of the edits/changes in the cloud for integrity and accountability.
4.7. Intellectual Property
Intellectual Property management system could leverage the Blockchain technology to enforce provable intellectual property rights [47] where verifiable, immutable and secure operations in Blockchain could help any disputes.
4.8. Food Safety
Food safety is one of the most critical issues to be addressed since over 0.6 billion (equivalently 1 in 10 people) in the world become ill after consuming bad food every year [48]. About 1167 people die every day [48]. To prevent these issues, Blockchain technology can help to prevent counterfeiting issues for food to have visibility across food supply chain and help to access any information such as food content, its origins, expiration, etc. in seconds. Food consumers will better control over food and information with high accuracy and transparency for food safety [48].
4.9. Blockchain Notary
Blockchain using distributed ledger technology with cryptography replaces trusted third parties such as a notary (trust third party in the traditional systems). Blockchain helps the entire notary process by automatically executing process in a cost-effective, transparent, and secure manner [49]
4.10. Blockchain Health-Care
Personal health records are sensitive information and needs to be dealt with high security. Such personal records can be encoded and stored using Blockchain and provide a private key which would allow only specific individuals to access the records. Similarly, the same protocol can be applied to conduct research where personal records are used via Health Insurance Portability and Accountability Act (HIPAA) laws to ensure confidentiality of the data. Patients records in the Blockchain can be automatically sent to the insurance providers or the doctor can send the health records to the concerned parties securely [50].
4.11. Fundraising and Transparency
Transparency is one of the issues to be addressed in fund-raising activities to make the process trustworthy. Blockchain as a distributed ledger technology can ensure the transparency, security, and integrity in fund-raising activities by leveraging Blockchain features such as immutability, verifiability, and security [51].
4.12. Wireless Networks and Virtualization
Wireless network is suffering from explosive growth of IoT and CPS applications and there have been different approach studied to enhance the network capacity and coverage [52,53] Blockchain can be used to sublease wireless resources such as RF slices to network service providers or third-party like mobile virtual network operators (MVNOs) in a verifiable way so that quality of service of the users would be met by preventing double spending/subleasing of same wireless resource to multiple parties in a distributed manner [12,54].
4.13. Real State
Blockchain technology as a distributed ledger database system can offer benefit for the real estate industry. Property title recording can be done using blocks with transactions in Blockchain rather than using traditional/current record keeping system [55].
4.14. Smart Contracts
Smart contracts digital entity written in a Turing-complete byte language, called Ethereum Virtual Machine (EVM) bytecode [56]. They are essentially a set of functions where each function is a sequence of instructions. Such contracts are embedded with conditional statements which enables them to self-execute. Smart contracts can be a replacement to intermediaries which make sure that all parties are obliged by the agreed terms. Thus, with Blockchain, such regulatory bodies become redundant. Smart contracts based on Blockchain ensures that the participants know the contract details and the agreement are automatically implemented once the conditions are fulfilled. In order to make the smart contracts work, there is a group of mutually “untrusted” peers called miners who verify the transactions related to the contract. Each transaction broadcast to the Blockchain network is collected by the miners and verified before they are encoded to a new block and appended to the Blockchain. Any potential conflict is resolved through the consensus protocol which is based on “proof-of-work”. Thus, a smart contract only works if there is no bias or a majority in the computational power of the network, thus ensuring the decentralization in the network. The miners are rewarded for creating new blocks under the protocol everyone miners are required to follow. Any miner’s work is discredited by other miners if he/she does not follow the protocol, thus there is an incentive for each miner to follow the rules.
4.15. Identity Management
In this section, we present brief overview of different identity management-based applications and how they could benefit from Blockchain technology.
4.15.1. Academic Records
Blockchain can be used to store academic records for students and universities in a decentralized ledgers [7]. This academic record keeping system will be tamper-proof, verifiable, immutable, and secure [7].
4.15.2. Blockchain Music
In music industry, it is a huge challenge to own products via ownership rights, and benefit from royalty distribution. In order to monetize digital music products, ownership rights are required. The Blockchain and smart contracts technology can be used to create a comprehensive and accurate decentralized database of music rights. Meanwhile, the ledger can be used to provide a transparent information regarding the artist royalties and real time distributions to all the labels involved. Digital currency can be deployed to make the payments as per the terms of contracts.
4.15.3. Birth, Marriage, and Death Certificates
The record of birth, marriage and death are important records of a citizen as they are used to confirm citizenship of citizens, and grant rights as per their status such as voting rights and work permits. While keeping such records in a conventional method can be slow and prone to error, such issues can be fixed with the public ledger such as Blockchain. The Blockchain can make such records more reliable by encrypting the records [57,58].
4.15.4. Passports
The first digital passport was launched in 2014 [59] which could help the owners to identify themselves online and offline. With this Blockchain technology, a user can take a picture and share it via cryptograpphic communication, which can be used to share the picture and verify among the users via digital signatures. In the Blockchain based passport system, passports are stored in the distributed ledger, which is confirmed/verified by the users as well as government.
4.15.5. Personal Identity and Privacy
We perform several transactions that are based on our personal information. For instance, we can only buy alcoholic beverages, or get into bars, and several other public places depending on our age. Similarly, there is some level of personal profiling done via companies we interact with through online shopping, or personalized web surfing. Thus, there is a notion of personal identity that is being traded in the market to the advertiser so that they can target essential products to users as per their need. While such personal identity is fairly being traded in the market, it is essential to protect the privacy of the users. Therefore, the Blockchain can be used to protect the identity of the users by encrypting the data and securing it from attackers [4,9,60].
Personal ID: There are several personal identifications we carry around such as our driver’s license, student identity cards, keys, social security number card, state identification card, etc. Blockchain can be used to store these identifications as digital form of IDs that will replace all forms of traditional physical identifications. Essentially, one Blockchain ID could be used for all kind of identifications used identify the same subject or object [61].
4.15.6. Voting
Blockchain could offer many tangible benefits for verifiable secure voting system in coming years. Current voting system has flaws and hard to verify votes and votes. Thus, Blockchain with its features could provide immutable, verifiable and secure voting system where voter can cast their votes with highest confidence from anywhere in the world [62,63].
4.16. Reputation System
Reputation system is an important measure on how much a community trusts a person. Such a system plays an important role to assess a person through their reputation, which is evaluated on his/her past transactions and interactions with the community. The credit system can be thought of as a reputation system, where users are given credit scores based on their financial activities and, later, they are used to make decision regarding other financial transactions. There can be falsification of such system if the integrity of the data is compromised. Thus, it is important to securely keep the record of past transaction and fairly evaluate the reputation of the users. Here, Blockchain can be a really important technology as it keeps a distributed public ledger which is scrutinized by the consensus of users in the network.
4.17. Other Applications and Use Cases
Blockchain technology can be used in any scenarios when a trusted third-party is not needed or peer-to-peer system is needed for managing the transactions, as shown in Figure 2, with features like transparency, decentralization, integrity, immutability, security and privacy. However, Blockchain has some limitations such as high delay introduced by consensus process, large size of the blocks in Blockchain, etc.
5. Some Challenges
Blockchain offers good solution for many applications that need transparency, decentralization, integrity, immutability, and security without requiring trusted third party. However, there are several challenges to be addressed to realize the full potential of blockchain for different applications and use cases. Typical challenges to be addressed include the following.
- Throughput and bandwidth in the blockchain network: Is existing network bandwidth enough for blockchain transactions and updates to do real-time updates in the systems? We need to more research to address this challenge.
- Latency/delay in blockchain network: How often the ledger should be updated in the blockchain and what is the least tolerable updating delay that is acceptable? Furthermore, adversary can disallow a miner’s block from reaching all other miners for a long time. How can we address these types of attacks more effectively?
- Energy consumption in blockchain: What could be the minimum/optimal energy consumption for such computationally complex operations in blockchain?
6. Summary
In this paper, we have summarized not only how Blockchain works, but also its different emerging applications and use cases. We have also presented types of blockchain and structure of typical chain of blocks in blockchain. We have presented some open challenges to be addressed to fully utilize the salient features of the blockchain in different applications. By reading this paper, readers can have better understanding of what is a Blockchain and what are its different applications and use cases.
Author Contributions
Conceptualization, D.B.R. and R.D.; methodology, D.B.R. and V.C.; formal analysis, D.B.R. and V.C.; investigation, D.B.R. and V.C.; data curation, D.B.R., R.D. and V.C.; writing—original draft preparation, D.B.R. and V.C.; project administration, D.B.R. and R.D.; funding acquisition, D.B.R. All authors have read and agreed to the published version of the manuscript.
Funding
This work is partly supported by the U.S. Air Force Research Lab (AFRL), U.S. National Science Foundation (NSF) under grants CNS 1650831 and HRD 1828811, and by the U.S. Department of Homeland Security (DHS) under grant award number 2017-ST-062-000003. However, any opinion, finding, and conclusions or recommendations expressed in this document are those of the authors and should not be interpreted as necessarily representing the official policies, either expressed or implied, of the funding agencies.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 10 September 2020).
- Morris, D.Z. Bitcoin Hits a New Record High, But Stops Short of USD 20,000. 17 December 2017. Available online: http://fortune.com/2017/12/17/bitcoin-record-high-short-of-20000/ (accessed on 10 September 2020).
- Top 100 Cryptocurrencies by Market Capitalization. Available online: https://coinmarketcap.com/ (accessed on 10 September 2020).
- Rawat, D.B.; Ghafoor, K.Z. Smart Cities Cybersecurity and Privacy; Elsevier: Amsterdam, The Netherlands, 2018. [Google Scholar]
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. Hawk: The blockchain model of cryptography and privacy-preserving smart contracts. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 839–858. [Google Scholar]
- Zhang, Y.; Wen, J. An IoT electric business model based on the protocol of bitcoin. In Proceedings of the 2015 18th International Conference on Intelligence in Next Generation Networks, Paris, France, 17–19 February 2015; pp. 184–191. [Google Scholar]
- Sharples, M.; Domingue, J. The blockchain and kudos: A distributed system for educational record, reputation and reward. In European Conference on Technology Enhanced Learning; Springer: Berlin/Heidelberg, Germany, 2016; pp. 490–496. [Google Scholar]
- Noyes, C. Bitav: Fast anti-malware by distributed blockchain consensus and feedforward scanning. arXiv 2016, arXiv:1601.01405. [Google Scholar]
- Rawat, D.B.; Njilla, L.; Kwiat, K.; Kamhoua, C. iShare: Blockchain-based privacy-aware multi-agent information sharing games for cybersecurity. In Proceedings of the 2018 IEEE International Conference on Computing, Networking and Communications (ICNC), Maui, HI, USA, 5–8 March 2018; pp. 425–431. [Google Scholar]
- Malomo, O.O.; Rawat, D.B.; Garuba, M. Next-generation cybersecurity through a blockchain-enabled federated cloud framework. J. Supercomput. 2018, 74, 5099–5126. [Google Scholar] [CrossRef]
- Adebayo, A.; Rawat, D.B.; Njilla, L.; Kamhoua, C.A. Blockchain-enabled Information Sharing Framework for Cybersecurity. Blockchain Distrib. Syst. Secur. 2019. Chapter 7. [Google Scholar] [CrossRef]
- Rawat, D.B.; Alshaikhi, A. Leveraging Distributed Blockchain-based Scheme for Wireless Network Virtualization with Security and QoS Constraints. In Proceedings of the 2018 International Conference on Computing, Networking and Communications (ICNC), Maui, HI, USA, 5–8 March 2018; pp. 332–336. [Google Scholar]
- Divya, M.; Biradar, N.B. IOTA-next generation block chain. Int. J. Eng. Comput. Sci. 2018, 7, 23823–23826. [Google Scholar]
- Shrestha, R.; Bajracharya, R.; Shrestha, A.P.; Nam, S.Y. A new type of blockchain for secure message exchange in VANET. Digit. Commun. Netw. 2020, 6, 177–186. [Google Scholar] [CrossRef]
- Syed, T.A.; Alzahrani, A.; Jan, S.; Siddiqui, M.S.; Nadeem, A.; Alghamdi, T. A comparative analysis of blockchain architecture and its applications: Problems and recommendations. IEEE Access 2019, 7, 176838–176869. [Google Scholar] [CrossRef]
- Shrestha, R.; Nam, S.Y. Regional blockchain for vehicular networks to prevent 51% attacks. IEEE Access 2019, 7, 95021–95033. [Google Scholar] [CrossRef]
- Velliangiri, S.; Karunya, P.K. Blockchain Technology: Challenges and Security issues in Consensus algorithm. In Proceedings of the 2020 IEEE International Conference on Computer Communication and Informatics (ICCCI), Nagoya, Japan, 25–27 June 2020; pp. 1–8. [Google Scholar]
- Somy, N.B.; Kannan, K.; Arya, V.; Hans, S.; Singh, A.; Lohia, P.; Mehta, S. Ownership preserving AI Market Places using Blockchain. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 156–165. [Google Scholar]
- Vyas, S.; Gupta, M.; Yadav, R. Converging blockchain and machine learning for healthcare. In Proceedings of the 2019 IEEE Amity International Conference on Artificial Intelligence (AICAI), Dubai, UAE, 4–6 February 2019; pp. 709–711. [Google Scholar]
- Shrestha, R.; Nam, S.Y.; Bajracharya, R.; Kim, S. Evolution of V2X Communication and Integration of Blockchain for Security Enhancements. Electronics 2020, 9, 1338. [Google Scholar] [CrossRef]
- Shrivastava, V.; Kumar, S. Utilizing Block Chain Technology in Various Application Areas of Machine Learning. In Proceedings of the 2019 IEEE International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon), Faridabad, India, 14–16 February 2019; pp. 167–171. [Google Scholar]
- Shrestha, R.; Kim, S. Integration of IoT with blockchain and homomorphic encryption: Challenging issues and opportunities. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2019; Volume 115, pp. 293–331. [Google Scholar]
- Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on blockchain for Internet of Things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and iot integration: A systematic survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef] [PubMed]
- Lin, I.C.; Liao, T.C. A survey of blockchain security issues and challenges. IJ Netw. Secur. 2017, 19, 653–659. [Google Scholar]
- Haber, S.; Stornetta, W.S. How to time-stamp a digital document. In Conference on the Theory and Application of Cryptography; Springer: Berlin/Heidelberg, Germany, 1990; pp. 437–455. [Google Scholar]
- Narayanan, A.; Bonneau, J.; Felten, E.; Miller, A.; Goldfeder, S. Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction; Princeton University Press: Princeton, NJ, USA, 2016. [Google Scholar]
- Polge, J.; Robert, J.; Le Traon, Y. Permissioned blockchain frameworks in the industry: A comparison. ICT Express 2020. [Google Scholar] [CrossRef]
- Benčić, F.M.; Žarko, I.P. Distributed ledger technology: Blockchain compared to directed acyclic graph. In Proceedings of the 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS), Vienna, Austria, 2–5 July 2018; pp. 1569–1570. [Google Scholar]
- Amit Goel. 11 Money Transfer Companies Using Blockchain Technology. Available online: https://gomedici.com/11-money-transfer-companies-using-blockchain-technology-2/ (accessed on 10 September 2020).
- Rawat, D.B.; Doku, R.; Garuba, M. Cybersecurity in Big Data Era: From Securing Big Data to Data-Driven Security. IEEE Trans. Serv. Comput. 2019. [Google Scholar] [CrossRef]
- Manyika, J.; Chui, M.; Farrell, D.; Van Kuiken, S.; Groves, P.; Doshi, E.A. Open Data: Unlocking Innovation and Performance with Liquid Information. 2013. Available online: https://www.mckinsey.com/business-functions/digital-mckinsey/our-insights/open-data-unlocking-innovation-and-performance-with-liquid-information (accessed on 10 September 2020).
- Cisco Visual Networking Index: Forecast and Trends, 2017–2022 White Paper. 27 February 2019. Document ID:1551296909190103. Available online: https://www.cisco.com/c/en/us/solutions/collateral/service-provider/visual-networking-index-vni/white-paper-c11-741490.html (accessed on 10 September 2020).
- Rawat, D.B.; Rodrigues, J.J.; Stojmenovic, I. Cyber-Physical Systems: From Theory to Practice; CRC Press: Boca Raton, FL, USA, 2015. [Google Scholar]
- Zhaoyang, D.; Fengji, L.; Liang, G. Blockchain: A secure, decentralized, trusted cyber infrastructure solution for future energy systems. J. Mod. Power Syst. Clean Energy 2018, 6, 958–967. [Google Scholar]
- Alladi, T.; Chamola, V.; Sahu, N.; Guizani, M. Applications of blockchain in unmanned aerial vehicles: A review. Veh. Commun. 2020, 100249. [Google Scholar] [CrossRef]
- Rawat, D.B.; Bajracharya, C. Vehicular Cyber Physical Systems: Adaptive Connectivity and Security; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Sharma, P.K.; Moon, S.Y.; Park, J.H. Block-VN: A Distributed Blockchain Based Vehicular Network Architecture in Smart City. J. Inf. Process. Syst. 2017, 13, 184–195. [Google Scholar]
- Akmeemana, C. Blockchain Takes Off. 2017. Available online: https://s3.us-east-2.amazonaws.com/brightline-website/downloads/reports/Brightline_Akmeemana_Blockchain-Takes-Off_Blockchain-Research-Institute.pdf?utm_source=resource-page&utm_medium=button (accessed on 10 September 2020).
- Korpela, K.; Hallikas, J.; Dahlberg, T. Digital supply chain transformation toward blockchain integration. In Proceedings of the 50th Hawaii International Conference on System Sciences, Waikoloa Village, HI, USA, 4–7 January 2017. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Seattle, WA, USA, 21–25 March 2017; pp. 618–623. [Google Scholar]
- Tosh, D.K.; Shetty, S.; Foytik, P.; Njilla, L.; Kamhoua, C.A. Blockchain-Empowered Secure Internet-of-Battlefield Things (IoBT) Architecture. In Proceedings of the MILCOM 2018-2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018; pp. 593–598. [Google Scholar]
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain technology: Beyond bitcoin. Appl. Innov. 2016, 2, 71. [Google Scholar]
- Notheisen, B.; Cholewa, J.B.; Shanmugam, A.P. Trading real-world assets on blockchain. Bus. Inf. Syst. Eng. 2017, 59, 425–440. [Google Scholar] [CrossRef]
- Liang, X.; Shetty, S.; Tosh, D.; Kamhoua, C.; Kwiat, K.; Njilla, L. Provchain: A blockchain-based data provenance architecture in cloud environment with enhanced privacy and availability. In Proceedings of the 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, Madrid, Spain, 14–17 May 2017; pp. 468–477. [Google Scholar]
- Martin, Z. Digital art as ‘monetised graphics’: Enforcing intellectual property on the blockchain. Philos. Technol. 2018, 31, 15–41. [Google Scholar]
- Galvin, D. IBM and Walmart: Blockchain for Food Safety. Available online: https://www-01.ibm.com/events/wwe/grp/grp308.nsf/vLookupPDFs/6%20Using%20Blockchain%20for%20Food%20Safe%202/$file/6%20Using%20Blockchain%20for%20Food%20Safe%202.pdf (accessed on 10 September 2020).
- Nofer, M.; Gomber, P.; Hinz, O.; Schiereck, D. Blockchain. Bus. Inf. Syst. Eng. 2017, 59, 183–187. [Google Scholar] [CrossRef]
- Mettler, M. Blockchain technology in healthcare: The revolution starts here. In Proceedings of the 2016 IEEE 18th International Conference on e-Health Networking, Applications and Services (Healthcom), Munich, Germany, 14–16 September 2016; pp. 1–3. [Google Scholar]
- Zhu, H.; Zhou, Z.Z. Analysis and outlook of applications of blockchain technology to equity crowdfunding in China. Financ. Innov. 2016, 2, 29. [Google Scholar] [CrossRef]
- Rawat, D.B.; Song, M.; Shetty, S. Dynamic Spectrum Access for Wireless Networks; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Rawat, D.B.; Alshaikhi, A.; Alshammari, A.; Bajracharya, C.; Song, M. Payoff optimization through wireless network virtualization for IoT applications: A three layer game approach. IEEE Internet Things J. 2018. [Google Scholar] [CrossRef]
- Rawat, D.B.; Parwez, M.S.; Alshammari, A. Edge computing enabled resilient wireless network virtualization for Internet of Things. In Proceedings of the 2017 IEEE 3rd International Conference on Collaboration and Internet Computing (CIC), San Jose, CA, USA, 15–17 October 2017; pp. 155–162. [Google Scholar]
- Spielman, A. Blockchain: Digitally Rebuilding the Real Estate Industry. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2016. [Google Scholar]
- Buterin, V. A Next-Generation Smart Contract and Decentralized Application Platform; White Paper; 2014; Available online: ethereum.org (accessed on 10 September 2020).
- Sullivan, C.; Burger, E. E-residency and blockchain. Comput. Law Secur. Rev. 2017, 33, 470–481. [Google Scholar] [CrossRef]
- Dovey, M. Love on the Block. MONEYL B. p. 64. Available online: https://networkcultures.org/wp-content/uploads/2018/01/07-maxdovey.pdf (accessed on 10 September 2020).
- World Citizenship—Creating Affordable Decentralised Passport Services Using Available Cryptographic Tools. Available online: https://github.com/MrChrisJ/World-Citizenship (accessed on 10 September 2020).
- Jacobovitz, O. Blockchain for identity management. In The Lynne and William Frankel Center for Computer Science Department of Computer Science. Ben-Gurion University, Beer Sheva; Ben-Gurion University: Beersheba, Israel, 2016. [Google Scholar]
- Andrade, M. Systems and Methods for Personal Identification and Verification. U.S. Patent Appilication No. 14/940,142, 29 September 2016. [Google Scholar]
- Ernest, A.; Hourt, N.; Larimer, D. Blockchain Electronic Voting System and Method. U.S. Patent Appilication No. 15/298,177, 20 April 2016. [Google Scholar]
- Osgood, R. The future of democracy: Blockchain voting. In COMP116: Information Security; Tuft University: Boston, MA, USA, 2016; Available online: http://www.cs.tufts.edu/comp/116/archive/fall2016/rosgood.pdf (accessed on 20 September 2020).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).