Biserial Miyaguchi–Preneel Blockchain-Based Ruzicka-Indexed Deep Perceptive Learning for Malware Detection in IoMT
Abstract
:1. Introduction
1.1. Research Gap
1.2. Objective
- To enhance malware application detection with lesser time consumption, the BCMPB-RIDMPL technique is introduced;
- To minimize the malware detection time, the BCMPB-RIDMPL technique uses Point biserial correlative feature matching to select the relevant feature and remove the unnecessary malware features;
- To generate the hash value with maximum security, the Miyaguchi–Preneel cryptographic hash-based Blockchain is applied in the BCMPB-RIDMPL technique;
- To match the hash value, the Ruzicka similarity index is applied for categorizing the malware and benign applications in BCMPB-RIDMPL.
1.3. Contribution of This Study
- The BCMPB-RIDMPL technique is shown to improve the detection of malware applications through the choice of the processes of feature selection, blockchain technology, and classification;
- The method is shown to match the point biserial correlative feature to select the relevant feature and remove the malware;
- The novelty of the point biserial correlation coefficient is employed to estimate the correlation among the features. The maximum correlations among the features are chosen and other features are eliminated. It is used for minimizing the dimensionality of data and malware detection time;
- The Miyaguchi–Preneel cryptographic hash-based blockchain is applied to create the hash value for each selected feature;
- The novelty of the blockchain technology Miyaguchi–Preneel compression function is used for creating the hash value. This helps to ensure security by avoiding unauthorized access;
- The novelty of the Ruzicka similarity index is used to verify the hash value of malware and other test features and classifies malware and benign applications;
- Lastly, the paper explains the extensive experimental evaluations that have been performed in various performance metrics to highlight the benefit of the proposed BCMPB-RIDMPL method over conventional classification techniques.
1.4. Organization of Paper
2. Related Work
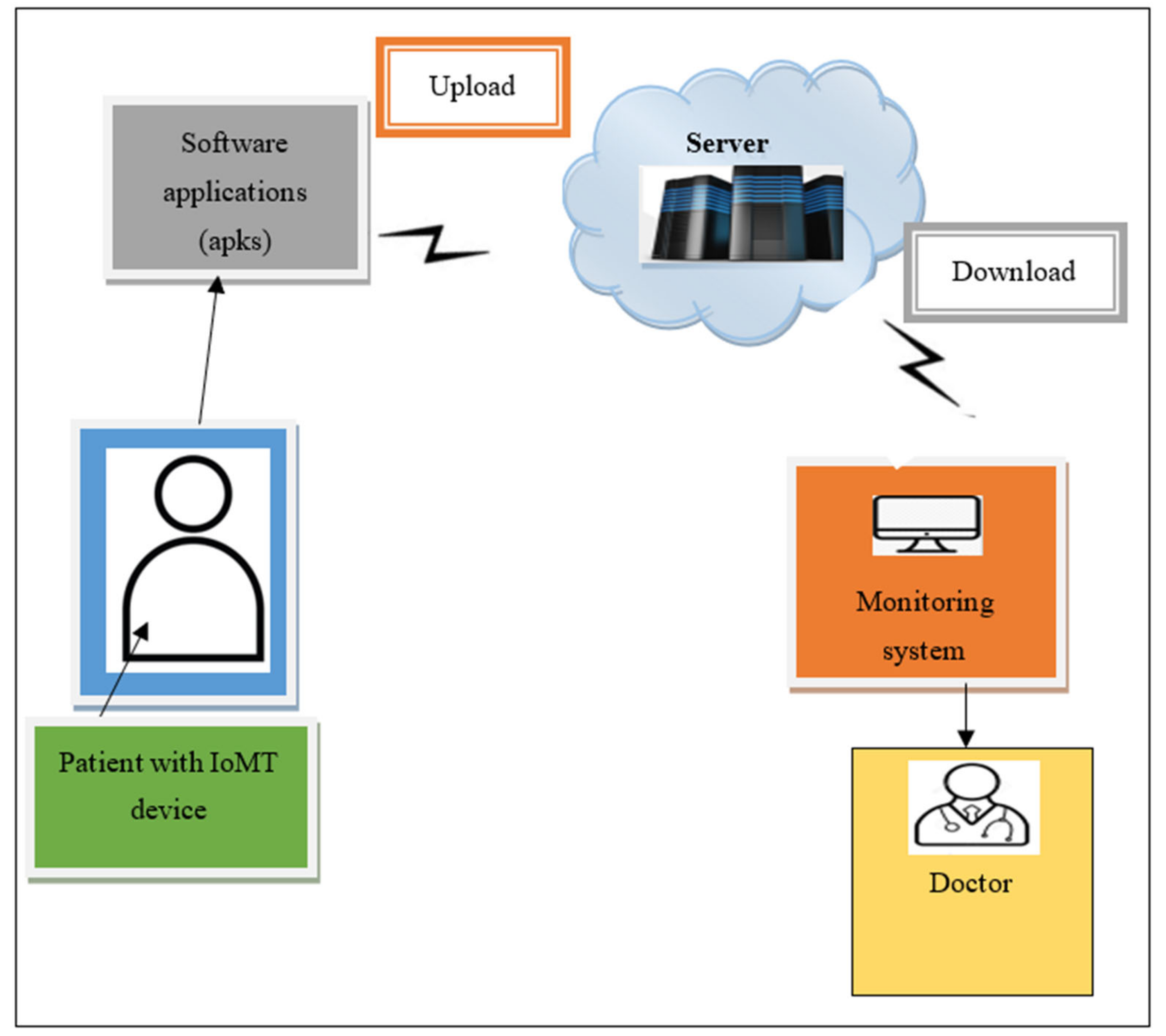
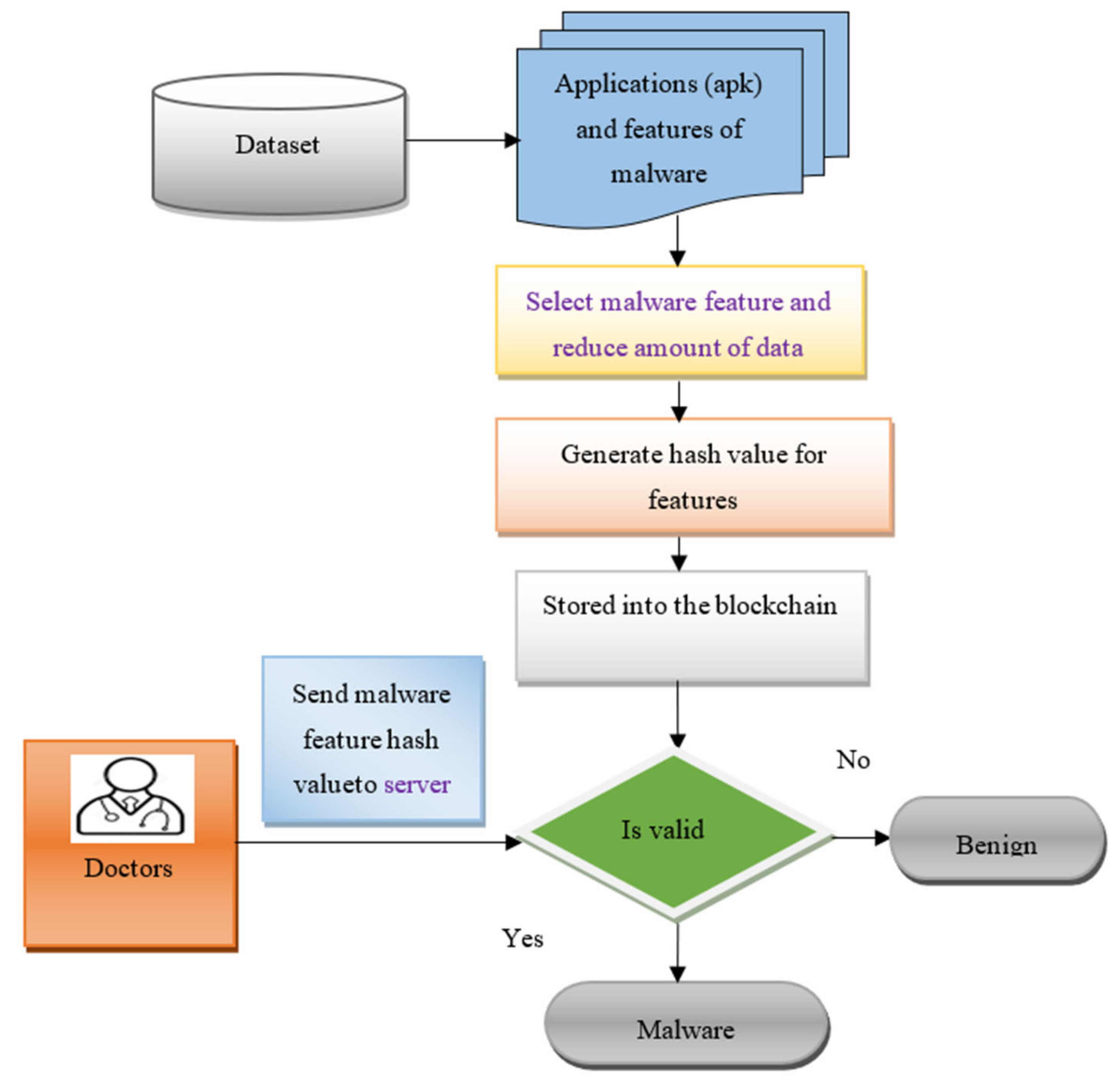
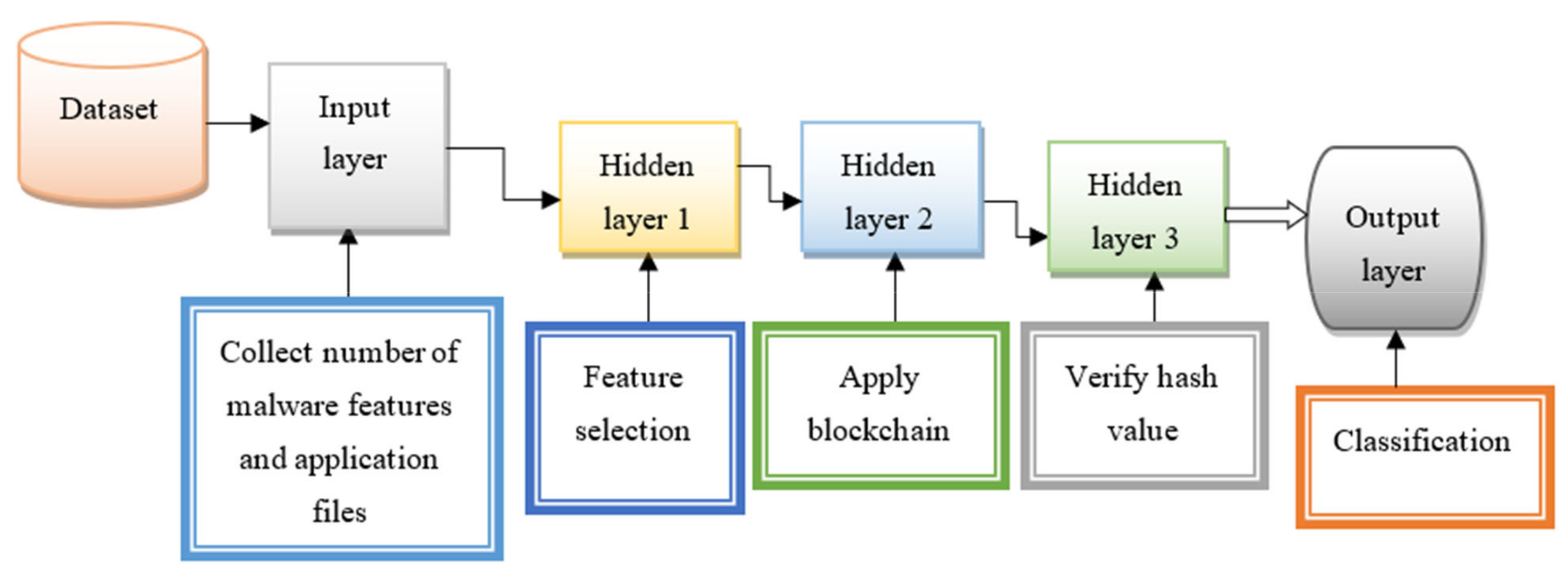
3. Methodology of Current Work
3.1. Point Biserial Correlative Feature Matching
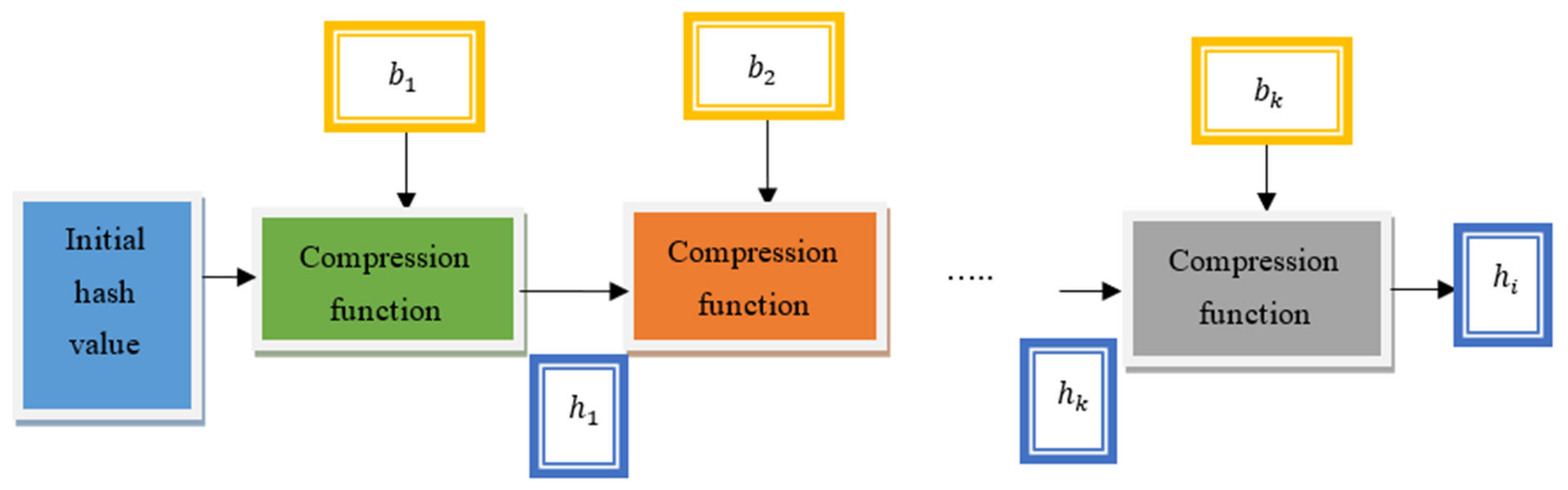
3.2. Miyaguchi–Preneel Cryptographic Hash-Based Blockchain Technology
| Algorithm 1: Biserial correlative Miyaguchi–Preneel blockchain-based Ruzicka index deep multilayer perceptive learning. |
| Input: Dataset, malware features , applications Output: Improve the malware detection accuracy |
| Begin Step 1: Collect the malware features , application files [input layer] Step 2: For each feature [hidden layer 1] Step 3: Measure correlation Step 4: Select highly correlated features Step 5: Remove other features Step 6: End for Step 7: Construct blockchain [hidden layer 2] Step 8: For each selected feature Step 9: Partition into k message blocks Step 10: For each block Step 11: Generate a hash value Step 12: End for Step 13: Obtain the final hash Step 14: End for Step 15: Store the hash in the blockchain Step 16: Perform hash verification [hidden layer 3] Step 17: Measure similarity Step 18: If (arg max ) then Step 19: Classified as malware application Step 20: Else Step 21: Classified as benign application Step 22: End if End |
4. Experimental Settings
Simulation Setup
5. Evaluation Measures
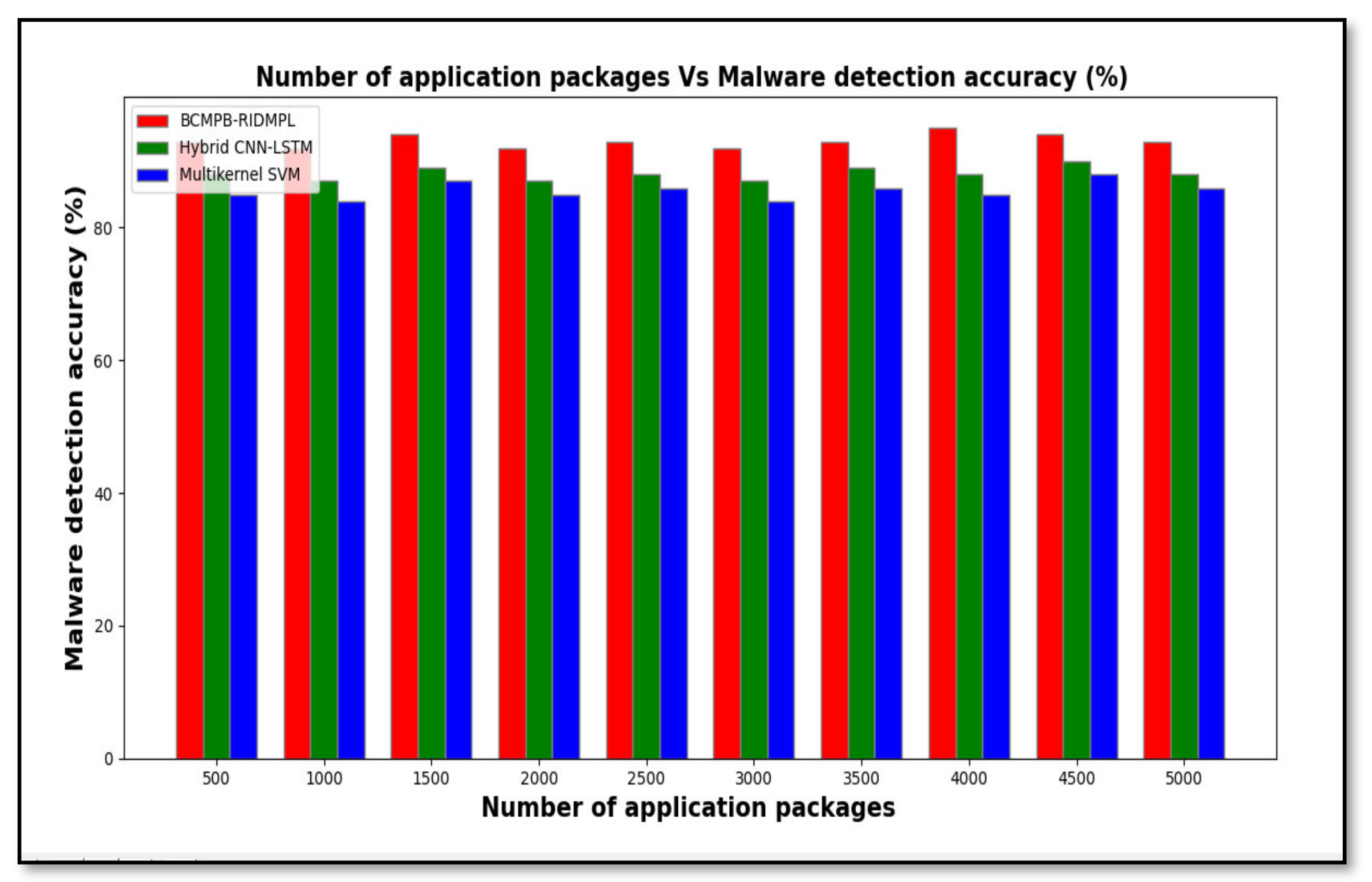
5.1. Malware Detection Accuracy
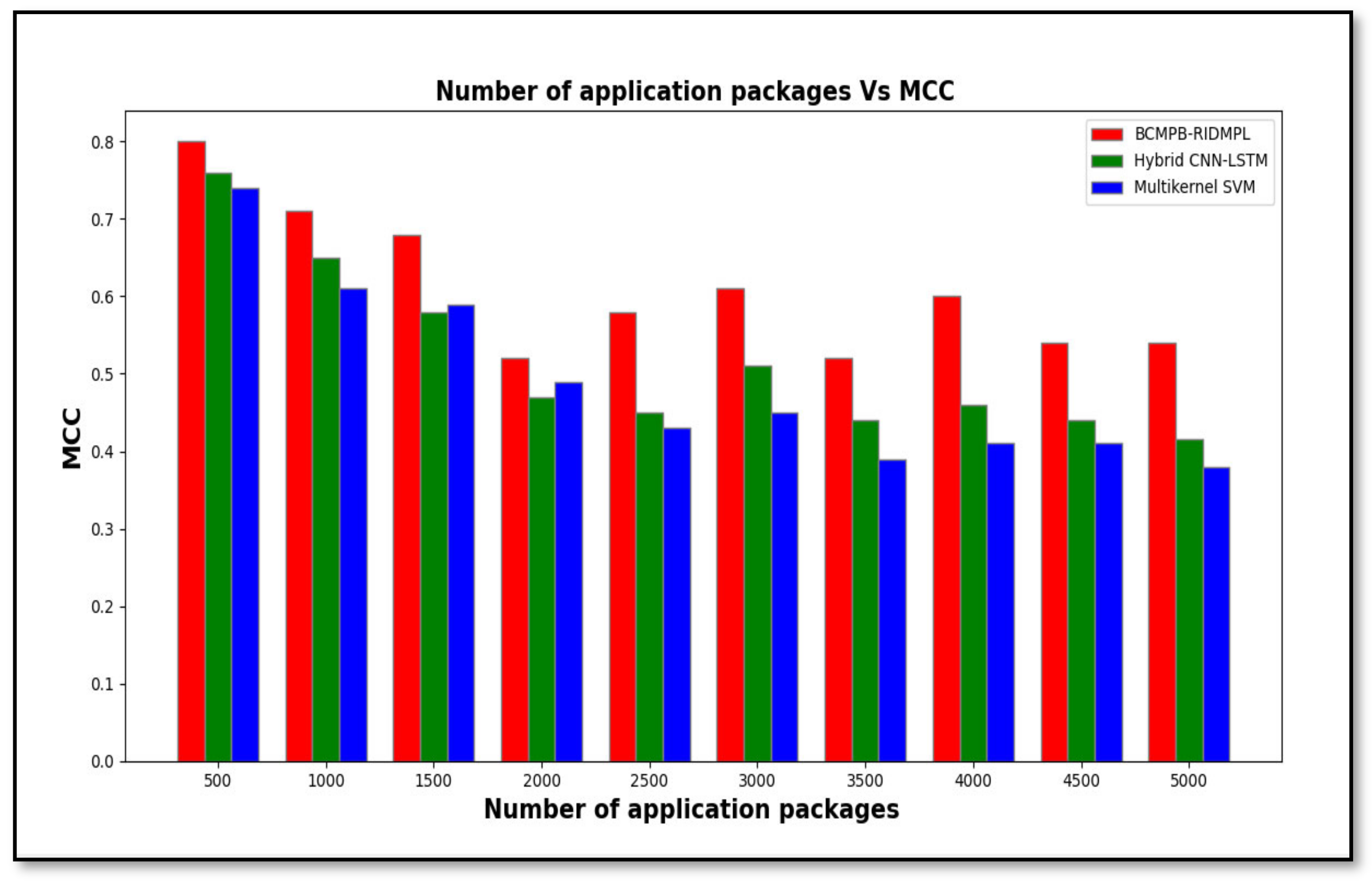
5.2. Measurement of Matthews Correlation Coefficient
5.3. Malware Detection Time
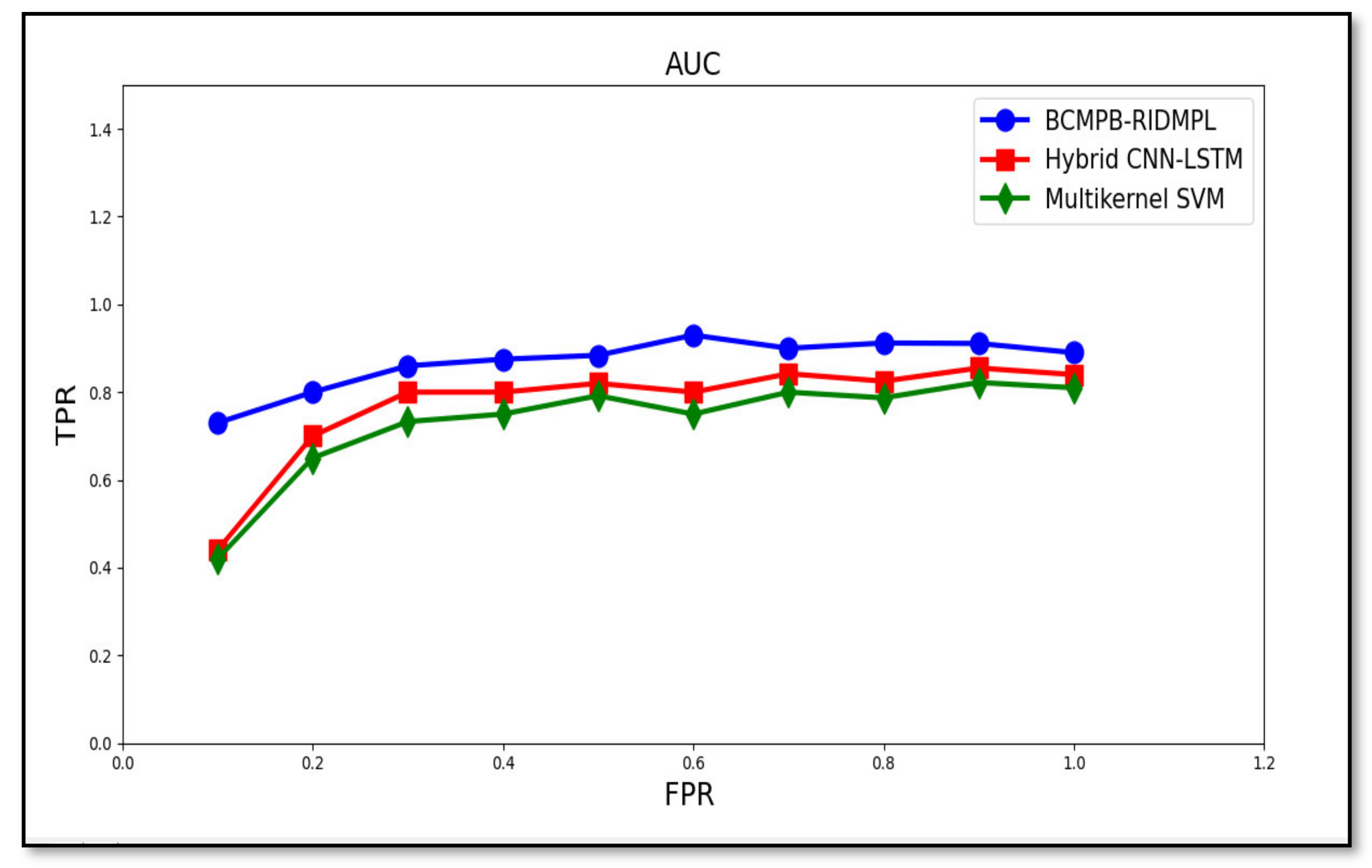
5.4. AUC Curve for BCMPB-RIDMPL Technique
6. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Khan, S.; Akhunzada, A. A hybrid DL-driven intelligent SDN-enabled malware detection framework for Internet of Medical Things (IoMT). Comput. Commun. 2021, 170, 209–216. [Google Scholar] [CrossRef]
- Haddadpajouh, H.; Mohtadi, A.; Dehghantanaha, A.; Karimipour, H.; Lin, X.; Choo, K.K.R. A multikernel and metaheuristic feature selection approach for IoT malware threat hunting in the edge layer. IEEE Internet Things J. 2021, 8, 4540–4547. [Google Scholar]
- Kumar, R.; Zhang, X.; Wang, W.; Khan, R.U.; Kumar, J.; Sharif, A. A multimodal malware detection technique for android IoT devices using various features. IEEE Access 2019, 7, 64411–64430. [Google Scholar] [CrossRef]
- Jahromi, A.N.; Hashemi, S.; Dehghantanha, A.; Choo, K.K.R.; Karimipour, H.; Newton, D.E.; Parizi, R.M. An improved two-hidden-layer extreme learning machine for malware hunting. Comput. Secur. 2020, 89, 101655. [Google Scholar] [CrossRef]
- Jahromi, A.N.; Hashemi, S.; Dehghantanha, A.; Parizi, R.M.; Choo, K.K.R. An enhanced stacked LSTM method with no random initialization for malware threat hunting in safety and time-critical systems. IEEE Trans. Emerg. Top. Comput. Intell. 2020, 4, 630–640. [Google Scholar] [CrossRef]
- Ren, Z.; Wu, H.; Ning, Q.; Hussain, I.; Chen, B. End-to-end malware detection for android IoT devices using deep learning. Ad. Hoc. Netw. 2020, 101, 102098. [Google Scholar] [CrossRef]
- Taheri, R.; Javidan, R.; Pooranian, Z. Adversarial android malware detection for mobile multimedia applications in IoT environments. Multimed. Tools Appl. 2021, 19, 974. [Google Scholar] [CrossRef]
- Namanya, A.P.; Awan, I.U.; Disso, J.P.; Younas, M. Similarity hash based scoring of portable executable files for efficient malware detection in IoT. Future Gener. Comput. Syst. 2020, 110, 824–832. [Google Scholar] [CrossRef]
- Takase, H.; Kobayashi, R.; Kato, M.; Ohmura, R. A prototype implementation and evaluation of the malware detection mechanism for IoT devices using the processor information. Int. J. Inf. Secur. 2020, 19, 71–81. [Google Scholar] [CrossRef]
- Jeon, J.; Park, J.H.; Jeong, Y.S. Dynamic analysis for IoT malware detection with convolution neural network model. IEEE Access 2020, 8, 96899–96911. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Rodrigues, J.J.P.C.; Shetty, S.; Park, Y. IoMT malware detection approaches: Analysis and research challenges. IEEE Access 2019, 7, 182459–182476. [Google Scholar] [CrossRef]
- Imtiaz, S.I.; Rehman, S.U.; Javed, A.R.; Jalil, Z.; Liu, X.; Alnumay, W.S. Deep AMD: Detection and identification of Android malware using high-efficient Deep Artificial Neural Network. Future Gener. Comput. Syst. 2021, 115, 844–856. [Google Scholar] [CrossRef]
- Vasan, D.; Alazab, M.; Venkatraman, S.; Akram, J.; Qin, Z. MTHAEL: Cross-architecture IoT malware detection based on neural network advanced ensemble learning. IEEE Trans. Comput. 2020, 69, 1654–1667. [Google Scholar] [CrossRef]
- Yazdinejad, A.; HaddadPajouh, H.; Dehghantanha, A.; Parizi, R.M.; Srivastava, G.; Chen, M.Y. Cryptocurrency malware hunting: A deep Recurrent Neural Network approach. Appl. Soft Comput. 2020, 96, 106630. [Google Scholar] [CrossRef]
- Lei, T.; Qin, Z.; Wang, Z.; Li, Q.; Ye, D. EveDroid: Event-aware android malware detection against model degrading for IoT devices. IEEE Internet Things J. 2019, 6, 6668–6680. [Google Scholar] [CrossRef]
- Suaboot, J.; Tari, Z.; Mahmood, A.; Zomaya, A.Y.; Li, W. Sub-curve HMM: A malware detection approach based on partial analysis of API call sequences. Comput. Secur. 2020, 92, 101773. [Google Scholar] [CrossRef]
- Guizani, N.; Ghafoor, A. A network function virtualization system for detecting malware in large IoT based networks. IEEE J. Sel. Areas Commun. 2020, 38, 1218–1228. [Google Scholar] [CrossRef]
- Lu, X.; Li, J.; Wang, W.; Gao, Y.; Zhao, W. Towards improving detection performance for malware with correntropy-based deep learning method. Digit. Commun. Netw. 2021, 1–13. [Google Scholar]
- Liu, X.; Lin, Y.; Li, H.; Zhang, J. A novel method for malware detection on ML-based visualization technique. Comput. Secur. 2020, 89, 101682. [Google Scholar] [CrossRef]
- Wozniak, M.; Silka, J.; Wieczorek, M.; Alrashoud, M. Recurrent Neural Network model for IoT and networking malware threads detection. IEEE Trans. Ind. Inform. 2020, 17, 5583–5594. [Google Scholar] [CrossRef]
- Bolton, T.; Dargahi, T.; Belguith, S.; Al-Rakhami, M.S.; Sodhro, A.H. On the Security and Privacy Challenges of Virtual Assistants. Sensors 2021, 21, 2312. [Google Scholar] [CrossRef] [PubMed]
- Ma, X.; Guo, S.; Bai, W.; Chen, J.; Xia, S.; Pan, Z. An API Semantics-Aware Malware Detection Method Based on Deep Learning. Security and Privacy in Internet of Medical Things (IoMT). Secur. Commun. Netw. 2019, 2019, 1315047. [Google Scholar] [CrossRef] [Green Version]
- Xiao, F.; Lin, Z.; Sun, Y.; Ma, Y. Malware Detection Based on Deep Learning of Behavior Graphs. Mathematical Problems in Engineering. Math. Probl. Eng. 2019, 2019, 8195395. [Google Scholar] [CrossRef] [Green Version]
- Haseeb, K.; Ahmad, I.; Awan, I.I.; Lloret, J.; Bosch, I. A Machine Learning SDN-Enabled Big Data Model for IoMT Systems. Electronics MDPI 2021, 10, 2228. [Google Scholar] [CrossRef]
- Anand, A.; Rani, S.; Anand, D.; Aljahdali, H.M.; Kerr, D. An Efficient CNN-Based Deep Learning Model to DetectMalware Attacks (CNN-DMA) in 5G-IoT Healthcare Applications. Sensors MDPI 2021, 21, 6346. [Google Scholar] [CrossRef] [PubMed]
- Talat, R.; Obaidat, M.S.; Muzammal, M.; Sodhro, A.H.; Luo, Z.; Pirbhulal, S. A decentralised approach to privacy preserving trajectory mining’. Future Gener. Comput. Appl. 2020, 102, 382–392. [Google Scholar] [CrossRef]



| Hardware | Specification |
|---|---|
| Operating system | Windows 10 |
| Processor | core i3-4130 3.40 GHZ |
| RAM | 4GB RAM |
| Hard disk | 1TB (1000 GB) |
| Motherboard | ASUSTek P5G41C-M |
| Protocol | Internet |
| Number of Applications | Malware Detection Accuracy (%) | ||
|---|---|---|---|
| BCMPB-RIDMPL | Hybrid CNN-LSTM | Multi-kernel SVM | |
| 500 | 93 | 88 | 85 |
| 1000 | 92 | 87 | 84 |
| 1500 | 94 | 89 | 87 |
| 2000 | 92 | 87 | 85 |
| 2500 | 93 | 88 | 86 |
| 3000 | 92 | 87 | 84 |
| 3500 | 93 | 89 | 86 |
| 4000 | 95 | 88 | 85 |
| 4500 | 94 | 90 | 88 |
| 5000 | 93 | 88 | 86 |
| Number of Application Packages | MCC | ||
|---|---|---|---|
| BCMPB-RIDMPL | Hybrid CNN-LSTM | Multi-Kernel SVM | |
| 500 | 0.80 | 0.76 | 0.74 |
| 1000 | 0.71 | 0.65 | 0.61 |
| 1500 | 0.68 | 0.58 | 0.59 |
| 2000 | 0.52 | 0.47 | 0.49 |
| 2500 | 0.58 | 0.45 | 0.43 |
| 3000 | 0.61 | 0.51 | 0.45 |
| 3500 | 0.52 | 0.44 | 0.39 |
| 4000 | 0.60 | 0.46 | 0.41 |
| 4500 | 0.54 | 0.44 | 0.41 |
| 5000 | 0.54 | 0.416 | 0.38 |
| Number of Applications | Malware Detection Time (ms) | ||
|---|---|---|---|
| BCMPB-RIDMPL | Hybrid CNN-LSTM | Multi-Kernel SVM | |
| 500 | 15 | 18 | 20 |
| 1000 | 20 | 23 | 25 |
| 1500 | 23 | 25 | 27 |
| 2000 | 24 | 26 | 28 |
| 2500 | 26 | 28 | 30 |
| 3000 | 28 | 30 | 33 |
| 3500 | 30 | 32 | 35 |
| 4000 | 32 | 34 | 36 |
| 4500 | 34 | 36 | 38 |
| 5000 | 35 | 38 | 40 |
| FPR | AUC Curve | ||
|---|---|---|---|
| TPR | |||
| BCMPB-RIDMPL | Hybrid CNN-LSTM | Multi-Kernel SVM | |
| 0.1 | 0.73 | 0.44 | 0.42 |
| 0.2 | 0.8 | 0.7 | 0.65 |
| 0.3 | 0.86 | 0.8 | 0.733 |
| 0.4 | 0.875 | 0.8 | 0.75 |
| 0.5 | 0.884 | 0.82 | 0.792 |
| 0.6 | 0.93 | 0.8 | 0.75 |
| 0.7 | 0.9 | 0.842 | 0.8 |
| 0.8 | 0.912 | 0.825 | 0.787 |
| 0.9 | 0.911 | 0.855 | 0.822 |
| 1 | 0.89 | 0.84 | 0.81 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alotaibi, A.S. Biserial Miyaguchi–Preneel Blockchain-Based Ruzicka-Indexed Deep Perceptive Learning for Malware Detection in IoMT. Sensors 2021, 21, 7119. https://doi.org/10.3390/s21217119
Alotaibi AS. Biserial Miyaguchi–Preneel Blockchain-Based Ruzicka-Indexed Deep Perceptive Learning for Malware Detection in IoMT. Sensors. 2021; 21(21):7119. https://doi.org/10.3390/s21217119
Chicago/Turabian StyleAlotaibi, Abdullah Shawan. 2021. "Biserial Miyaguchi–Preneel Blockchain-Based Ruzicka-Indexed Deep Perceptive Learning for Malware Detection in IoMT" Sensors 21, no. 21: 7119. https://doi.org/10.3390/s21217119






