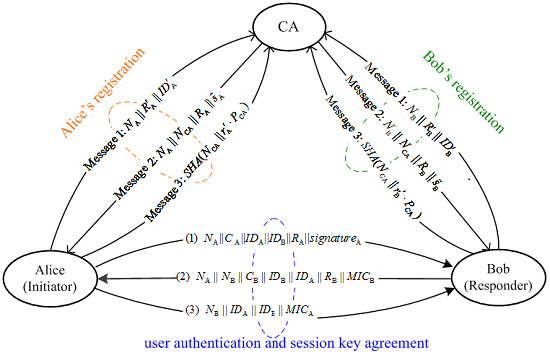
The security of the proposed user authentication scheme is based on the intractability of reversing ECDLP and one-way hash function problem (OWHFP).
4.1. Security Analysis in User Registration Phase
Theorem 1.
The proposed user authentication scheme is secure against user masquerade attack, message-forgery attack, impersonate attack from CA in user registration phase.
Proof.
(1) User masquerade attack resistance
We assume that an adversary (Eve) intercepts the legal user’s registration information and attempts to masquerade the legal user () to join in the network. However, Eve will be faced with some difficulties in following scenarios.
Although Eve intercepts
, he cannot masquerade the valid user. Because
’s identity is hidden in
. If Eve wants to obtain
from
, he must first obtain
which is protected under the OWHFP and ECDLP.
Although Eve intercepts message
and wants to masquerade the valid user, he should derive
from
. It is not possible because solving the ECDLP is computationally infeasible. Meantime, he cannot return Message 3 () to CA without the knowledge of
.
Although Eve gets
, he attempts to re-register with CA on the purpose of masquerading a valid user. Even if this attack is successful, the attack can be easily detected. This is because CA is convinced that the user has verified the authenticity of his public key since receiving Message 3. And CA stores the user’s registration information in the registration file. As a registration request is accepted, CA will check the submitted user’s identity information of the user in the registration file to prevent the re-registration attempt.
Therefore, our proposed scheme can resist the user masquerade attack.
(2) Message-forgery attack resistance
We assume that Eve intercepts
when CA returns it to
and attempts to forge
.
verifies the condition
. The verification does not hold because Eve needs to have the private key of CA, PCA. Hence, Eve should compute
from
. It is not possible because solving the ECDLP is computationally infeasible. Therefore, our proposed scheme can resist the message-forgery attack.
(3) Resistance of the impersonate attack from CA
We assume that CA generates another pair of valid private/public key, (), satisfying (9), CA can impersonate
. However, this fraud can be detected by
because two different valid keys exist. It can prove that CA is cheating. Therefore, our proposed scheme can resist the impersonate attack from CA.
4.2. Security Analysis in User Authentication Phase
Theorem 2.
The proposed user authentication scheme achieves mutual trust, and is secure against man-in-the-middle attack, replay attack, masquerading and tampering attacks in user authentication phase.
Proof.
(1) Mutual trust
The signature of the message sent by Alice is generated in Step 1, which is verified by Bob in Step 2. In this way, Bob authenticates Alice’s identity.
Moreover, a message integrity code of the message sent by Bob,
, is applied in Step 2. This provides the evidence of authentication and integrity for the message received by Alice. In the proposed scheme,
contains
generated by Bob’s private key. Hence,
can be used to authenticate Bob’s identity.
Therefore, the proposed scheme provides the two-way authentication between Alice and Bob.
(2) Man-in-the-middle attack resistance
In the user registration phase, it prevents from the re-registration attempt so that adversaries can hardly masquerade other valid users to perform the man-in-the-middle attack.
In the user authentication phase, the proposed scheme exchanges
and
along with
and
, and generates the session keys,
and
, using the private keys,
and
, and two random values,
and
. Man-in-the-middle attack is only possible if an adversary (Eve) can forge
and
. Hence, Eve must compute
and
from the pair (,
) = (,
). It is not possible because solving the ECDLP is computationally infeasible.
Therefore, the proposed scheme can resist man-in-the-middle attack.
(3) Replay attack resistance
Two types of replay attacks are considered. Type-I replay attack is defined as an adversary intercepts an authentication message and attempts to masquerade as a sender by replaying it without modifying any content of the authentication message. Type-II replay attack is defined as an adversary intercepts an authentication message and replays a forged authentication message modified from the original one.
Since the proposed scheme uses the nonce to ensure the fresh of message, the type-I replay attack will be excluded by checking the nonce. If Eve intercepts the message
and replays it to impersonate Alice, Bob checks whether the message is fresh or not according to NA. If the nonce has been received, Bob discards the message.
In order to pass the authentication of Alice, Eve must change the nonce. It is assumed that Eve only changes the nonce from NA to
in
to forge the authentication message. Bob verifies
. The message verification does not hold since Eve needs to have the private key of Alice, PA, to generate a new signature. It is not possible because solving the ECDLP is intractable. In the same way, an adversary impersonating Bob cannot pass the authentication. Hence, the nonce cannot be forged in the proposed scheme, which means that the proposed scheme is also resistant to the type-II replay attack.
Therefore, the proposed scheme can resist the replay attack.
(4) Masquerading and tampering attacks resistance
It is assumed that an adversary (Eve) intercepts an authentication message and replays it to masquerade as a valid user.
Eve intercepts an authentication message sent by Alice and attempts to masquerade as Alice by launching the type-I replay attack. After Bob receives the authentication message, he will check whether the message is fresh or not according to NA. If the nonce has been received, Bob discards the message. On the other hand, Eve intercepts an authentication message and launches the type-II replay attack. It is difficult to succeed since Eve needs to use PA to generate a new signature. Computing
from
is not possible because solving the ECDLP is computationally infeasible.
It is assumed that an adversary (Eve) intercepts the message
and attempts to tamper the message. This action will not pass the user authentication of Alice. As explained in the replay attack resistance, Eve needs to use PA to generate a new signature. Hence, Eve encounters the intractability of solving the ECDLP. In addition, the one-way hash function is adopted in the user authentication phase to guarantee the integrity of message, which contains the session key generated by Alice and Bob’s private keys. Computing (,
) from (,
) is not possible because solving the ECDLP is computationally infeasible.
Therefore, the proposed scheme can resist the masquerading and tampering attacks.
Theorem 3.
Based on the difficulty in solving the ECDLP, the proposed user authentication scheme provides perfect forward secrecy, backward secrecy, key compromise impersonation attack resistance, known-key security, unknown key-share resistance, and known session-specific temporary information attack resistance.
Proof.
(1) Perfect forward secrecy and backward secrecy
It is assumed that the private keys,
and
, are compromised, and an adversary (Eve) attempts to compute the key
. Here, the forward secrecy is achieved by means of the term
. However, in order to compute the session key, Eve needs the knowledge of the random values,
and
. Solving
and
to get
and
is equivalent to the problem of solving ECDLP.
In addition, the session key relies on the random values,
and
, which are generated in each session independently and changed for each authentication phase.
Furthermore, another important aspect of our proposed scheme is that the session key is protected by the secure hash function. Although an adversary obtains a certain period session key, he/she cannot use the current session key to get forward and backward session keys. Hence, the session key in the proposed scheme achieves perfect forward secrecy and backward secrecy.
(2) Key compromise impersonation attack resistance
As defined in [
15], the key compromise impersonation attack resistance is that an adversary (Eve) can masquerade as Alice if Alice’s private key is compromised, while Eve cannot masquerade as another user to interact with Alice.
It is assumed that the long-term private key of Alice,
, is compromised and known to Eve. Obviously, Eve can impersonate Alice using
. However, to impersonate any other user (Bob) to interact with Alice, Eve would need the session key,
. Thus, Eve needs to have the private key of Bob,
, or the random value generated by Alice,
. Solving PB and CA to get
and
is equivalent to the problem of solving ECDLP. In addition, in most circumstances, the private key of a user is updated periodically.
Hence, the key compromise impersonation vulnerability can be limited to some considerably low extent.
(3) Known-key security
The proposed scheme achieves the known-key security if the knowledge of previous generated session keys does not allow an adversary to compromise the past or future session keys.
It is assumed that a session key generated by the proposed scheme is obtained by an adversary (Eve). Eve cannot derive all past and future session keys from the knowledge of the compromised session key. To derive a session key, Eve has to compute (,
) and (,
) from (,
) and (,
), respectively. It is not possible because solving the ECDLP is computationally infeasible.
(4) Unknown key-share resistance
A key agreement protocol achieves unknown key-share attack resistance if a user cannot be forced to share a session key with a different user rather than the one intended without their knowledge. That is, Alice cannot be forced to share a key with Eve when Alice believes that the key is shared with Bob.
In the user authentication phase of the proposed scheme, Bob sends a message to Alice,
. And MICB contains
generated by Bob’s private key,
. Similarly, Alice responds to Bob with the message,
. And MICA contains
generated by Alice’s private key
. The verification of MICB and MICA at Alice and Bob confirms the generation of same session key.
Therefore, the proposed scheme resists the unknown key-share attack.
(5) Known session-specific temporary information attack resistance
The security of the generated session key should not be compromised even if two random values are compromised by an adversary (Eve).
In the proposed scheme, Eve cannot derive the session key
and
even if
and
are compromised. This is because Eve does not know Alice’s private key and Bob’s private key,
and
. Moreover, Eve cannot derive from (,
)=(,
) because solving the ECDLP is computationally infeasible.
Therefore, the proposed scheme resists the known session-specific temporary information attack.