Underwater Sensor Network Redeployment Algorithm Based on Wolf Search
Abstract
:1. Introduction
2. Related Works
- (1)
- the underwater deployment scenarios consider real obstacle factors;
- (2)
- in order to achieve a better effect, when faced with obstacles, the nodes can avoid obstacles;
- (3)
- the obstacle avoidance mechanism avoids node failure due to external force. From a certain extent, it reduces the network energy consumption and guarantees the stability of network topology.
3. System Model
3.1. Network Model
- (1)
- In addition to the sink nodes, all nodes in the network have the same communication and sensing radii.
- (2)
- When the network is initialized, the nodes are distributed randomly in the 3D monitoring space, and the nodes can sense their own location information and their neighbors.
- (3)
- The obstacles (irregular and polyhedral) are distributed randomly in the underwater 3D monitoring space. If a node hits an underwater obstacle in the process of moving, node communication will break down.
3.2. Node Perception Model
3.3. Underwater Energy Consumption Model
4. RAWS Algorithm
4.1. RAWS Basic Principle
4.2. RAWS Algorithm Description and Process
5. Simulation and Performance Analysis
5.1. Introduction of an Algorithm for Comparison and an Evaluation Indicator
- (1)
- each node is independent in the process of the search event. Expanding the search range reduces the internal node mobility and communication;
- (2)
- if a node encounters obstacles in the process of moving, it will avoid them in time and jump out of the local optimal situation;
- (3)
- the algorithm is combined with congestion control, which is conducive to node coverage.
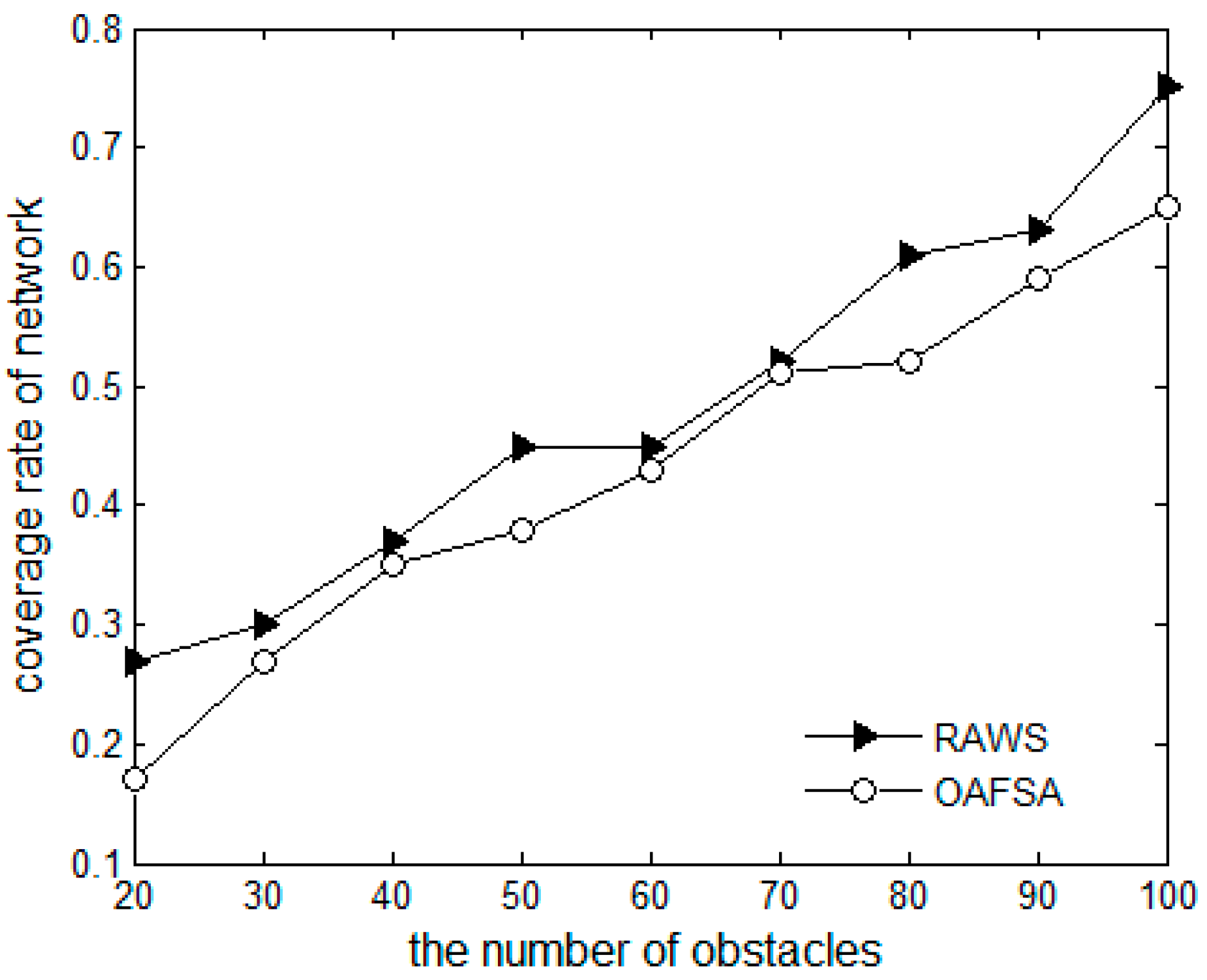
5.2. Simulation Results and Analysis
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Akyildiz, I.F.; Pompili, D.; Melodia, T. Underwater acoustic sensor networks: Research challenges. Ad hoc Netw. 2005, 3, 257–279. [Google Scholar] [CrossRef]
- BHAMBRI, H.; SWAROOP, A. Underwater sensor network: Architectures, challenges and applications. In Proceedings of the IEEE International Conference on Computing for Sustainable Global Development, New Delhi, India, 5–7 March 2014; pp. 915–920.
- Garcia, M.; Sendra, S.; Atenas, M.; Lloret, J. Underwater wireless ad-hoc networks: A survey. In Mobile Ad Hoc Networks: Current Status and Future Trends; CRC Press: Boca Raton, FL, USA, 2011; pp. 379–411. [Google Scholar]
- Lloret, J. Underwater sensor nodes and networks. Sensors 2013, 13, 11782–11796. [Google Scholar] [CrossRef] [PubMed]
- Hong, F.; Zhang, Y.L.; Yang, B.Z.; Guo, Y.; Guo, Z.W. Review on Time Synchronization Techniques in Underwater Acoustic Sensor Networks. Acta Electron. Sin. 2013, 41, 960–965. [Google Scholar]
- Hong, C.J.; Wu, W.J.; Tang, P.P. Dynamic Layered Clustering Routing Algorithm in Underwater Sensor Networks. J. Electron. Inf. Technol. 2015, 37, 1291–1297. (In Chinese) [Google Scholar]
- Kishigami, W.; Tanigawa, Y.; Tode, H. Robust data gathering method using controlled mobility in underwater sensor network. In Proceedings of the 2014 Eleventh Annual IEEE International Conference on Sensing, Communication, and Networking, Singapore, 30 June–3 July 2014; pp. 176–178.
- Mahboubi, H.; Habibi, J.; Aghdam, G. Distributed deployment strategies for improved coverage in a network of mobile sensors with prioritized sensing field. IEEE Trans. Ind. Inf. 2013, 9, 451–461. [Google Scholar] [CrossRef] [Green Version]
- Gkikopouli, A.; Nikolakopoulos, G.; Manesis, S. A survey on Underwater Wireless Sensor Networks and applications. In Proceedings of the 2012 20th Mediterranean Conference on Control & Automation (MED), 3–6 July 2012; pp. 1147–1154.
- Akkaya, K.; Newell, A. Self-deployment of sensors for maximized coverage in underwater acoustic sensor networks. Comput. Commun. 2009, 32, 1233–1244. [Google Scholar] [CrossRef]
- Liu, H.; Chai, Z.J.; Du, J.Z. Sensor Redeployment Algorithm Based on Combined Virtual Forces in Three Dimensional Space. Acta Autom. Sin. 2011, 37, 713–723. [Google Scholar]
- Luo, X.; Feng, L.; Yan, J.; Guan, X.P. Dynamic coverage with wireless sensor and actor networks in underwater environment. IEEE/CAA J. Autom. Sin. 2015, 2, 274–281. [Google Scholar]
- Liu, L. A deployment algorithm for underwater sensor networks in ocean environment. J. Circuit Syst. Comp. 2011, 20, 1051–1066. [Google Scholar] [CrossRef]
- Abo-Zahhad, M.; Ahmed, S.M.; Sabor, N.; Sasaki, S. Rearrangement of mobile wireless sensor nodes for coverage maximization based on immune node deployment algorithm. Elsevier 2015, 43, 76–89. [Google Scholar] [CrossRef]
- Hua, C.B.; Wei, Z.; Nan, C.Z. Underwater Acoustic Sensor Networks Deployment Using Improved Self-Organize Map Algorithm. Cybern. Inf. Technol. 2014, 14, 63–77. [Google Scholar] [CrossRef]
- Bonabeau, E.; Dorigo, M.; Theraulaz, G. Swarm Intelligence: From Natural to Artificial System; Oxford University Press: New York, NY, USA, 1999. [Google Scholar]
- Yang, S.Y.; Zhang, H. Swarm Intelligence and Bionic Computing-Matlab Technology; Publishing House of Electronic Industry: Beijing, China, 2000. [Google Scholar]
- Liu, X. Sensor deployment of wireless sensor networks based on ant colony optimization with three classes of ant transitions. IEEE Trans. Commun. Lett. 2012, 16, 1604–1607. [Google Scholar] [CrossRef]
- Du, H.Z.; Xia, N.; Zheng, R. Particle Swarm Inspired Underwater Sensor Self-Deployment. Sensors 2014, 14, 15262–15281. [Google Scholar] [CrossRef] [PubMed]
- Iyer, S.; Rao, D.V. Genetic algorithm based optimization technique for underwater sensor network positioning and deployment. In Proceedings of the 2015 IEEE Conference on Underwater Technology, Chennai, India, 23–25 February 2015; pp. 1–6.
- Wang, Y.Y.; Liao, H.M.; Hu, H.Y. Wireless sensor network deployment using an optimized artificial fish swarm algorithm. In Proceedings of the 2012 International Conference on Computer Science and Electronics Engineering, Hangzhou, China, 23–25 March 2012; pp. 90–94.
- Xia, N.; Wang, C.S.; Zheng, R.; Jiang, J.G. Fish Swarm Inspired Underwater Sensor Deployment. Acta Autom. Sin. 2012, 38, 295–302. [Google Scholar] [CrossRef]
- Singh, S.; Chand, S.; Kumar, B.; Kumar, R. A heterogeneous network model for prolonging lifetime in 3-D WSNs. In Proceedings of the Confluence 2013: The Next Generation Information Technology Summit (4th International Conference), 26–27 September 2013; pp. 257–262.
- Felamban, M.; Shihada, B.; Jamshaid, K. Optimal node placement in underwater wireless sensor networks. In Proceedings of the 2013 IEEE 27th International Conference on Advanced Information Networking and Applications (AINA), 25–28 March 2013; pp. 492–499.
- Detweiler, C.; Doniec, M.; Vasilescu, I.; Rus, D. Autonomous depth adjustment for underwater sensor networks: Design and applications. IEEE/ASME Trans. Mechatron. 2012, 17, 16–24. [Google Scholar] [CrossRef]
- Huang, J.J.; Sun, L.J.; Wang, R.C. Virtual potential field and covering factor based coverage-enhancing algorithm for three-dimensional wireless sensor networks. J. Chin. Inst. Commun. 2010, 31, 16–21. [Google Scholar]
- Rossi, P.S.; Ciuonzo, D.; Ekman, T.; Dong, H.F. Energy detection for MIMO decision fusion in underwater sensor networks. IEEE Sens. J. 2015, 15, 1630–1640. [Google Scholar] [CrossRef]
- Ahmed, S.; Javaid, N.; Khan, F.A.; Durrani, M.Y.; Ali, A.; Shaukat, A.; Sandhu, M.M.; Khan, Z.A.; Qasim, U. Co-UWSN: Cooperative Energy-Efficient Protocol for Underwater WSNs. Int. J. Distrib. Sens. Netw. 2015, 2015. [Google Scholar] [CrossRef] [PubMed]
- Sozer, E.M.; Stojanovic, M.; Proakis, J.G. Underwater acoustic networks. IEEE J. Oceanic Eng. 2000, 25, 72–83. [Google Scholar] [CrossRef]
- Tang, R.; Fong, S.; Yang, X.S.; Deb, S. Wolf search algorithm with ephemeral memory. In Proceedings of the 2012 Seventh International IEEE Conference on Digital Information Management, Macau, China, 22–24 August 2012; pp. 165–172.










| Parameter | Value |
|---|---|
| Sensing radius R (m) | 30 |
| Communication radius r (m) | 60 |
| Initial energy consumption Eint (J) | 10 |
| Carrier frequency f (KHZ) | 25 |
| Energy consumption of data reception Pr (mW) | 3 |
| Uncertainty factor Re (m) | 15 |
| Moving step length s (m) | 0 < s < 30 |
| Moving speed (m/s) | 1 |
| Relevant measuring equipment parameters α | 0.2 |
| Relevant measuring equipment parameters β | 2 |
| Obstacle number Obs | 20 |
| Common node number Nod | 100 |
| Energy diffusion factor (Khz) | 2 |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, P.; Feng, Y.; Wu, F. Underwater Sensor Network Redeployment Algorithm Based on Wolf Search. Sensors 2016, 16, 1754. https://doi.org/10.3390/s16101754
Jiang P, Feng Y, Wu F. Underwater Sensor Network Redeployment Algorithm Based on Wolf Search. Sensors. 2016; 16(10):1754. https://doi.org/10.3390/s16101754
Chicago/Turabian StyleJiang, Peng, Yang Feng, and Feng Wu. 2016. "Underwater Sensor Network Redeployment Algorithm Based on Wolf Search" Sensors 16, no. 10: 1754. https://doi.org/10.3390/s16101754





