Secure and Privacy-Preserving Body Sensor Data Collection and Query Scheme
Abstract
:1. Introduction

2. Related Work
3. Models and Design Goals
3.1. System Model
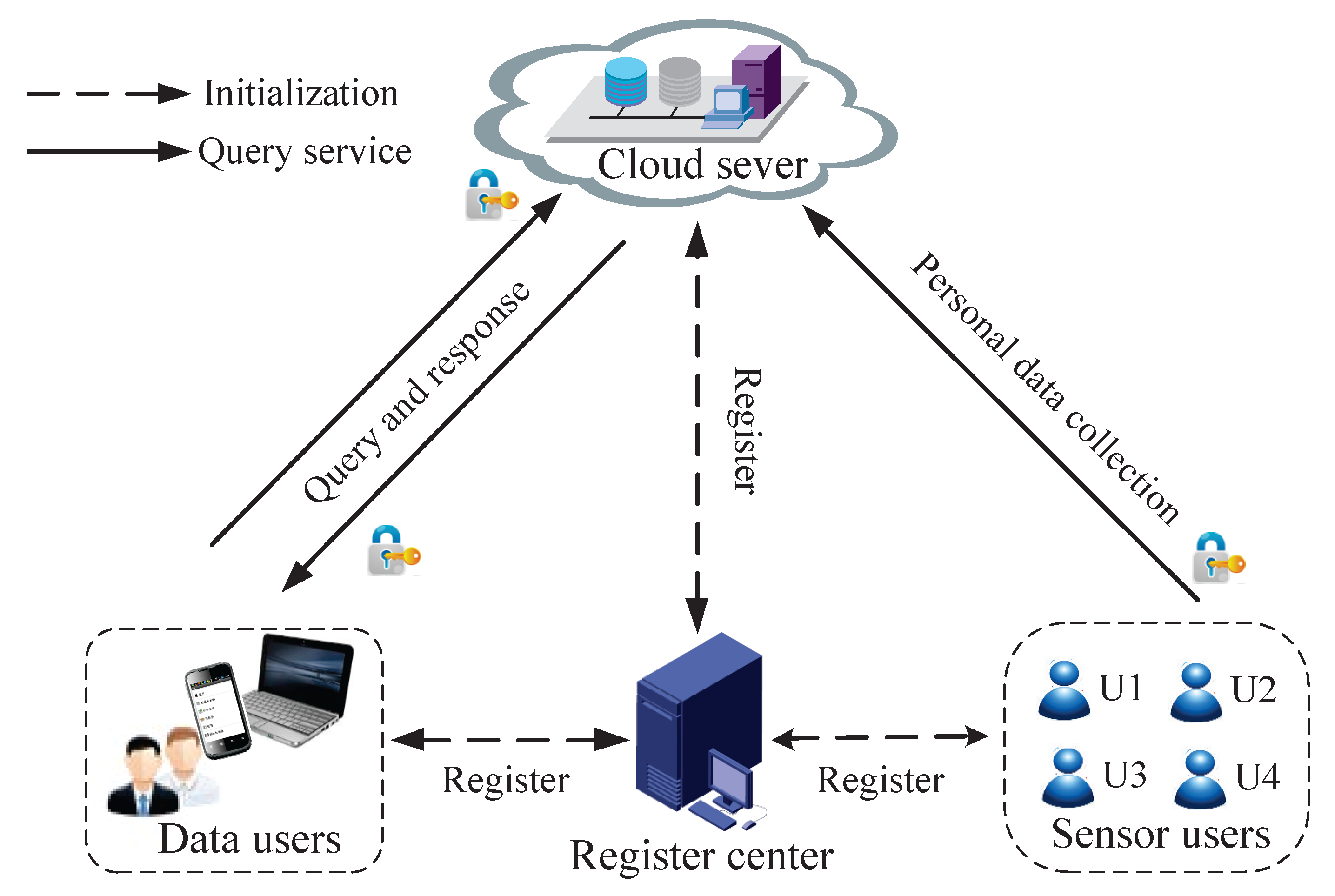
- RC is a trusted third party, which bootstraps the system initialization by generating system parameters and providing a registration system for SU, DU and CS.
- SU collects real-time personal data by body sensors, and all SUs’ personal data will be uploaded to CS. To guarantee the data confidentiality, SU will perform some encryption operations before uploading data to CS.
- DU (e.g., the researcher), who is registered in RC, can send query request to CS for analysis of the accurate personal data items stored in it. To guarantee the privacy of DU’s query information, DU will perform some encryption operations during the process of the query. Meanwhile, SUs’ personal data should be kept secret from unauthorized users.
- CS is composed of many data storage nodes and computing nodes, stores more than a billion encrypted personal data items from SUs and provides accurate query services to DUs over encrypted personal data. CS mainly performs two functions: authentication and computing over encrypted data. The authentication component is used to check the identity of SUs and DUs, while the computing in encryption component is used to search and compute encrypted data items with DUs’ encrypted query request.
3.2. Security Requirements
- Confidentiality. SUs’ sensitive personal data should be kept secret from CS, i.e., even if CS stores all personal data from SUs, it cannot identify any data item. In this circumstance, the confidentiality of the personal data can be guaranteed.
- Privacy. DU’s query information should be secrete from CS, i.e., even if CS obtains all DUs’ queries and corresponding responses, it cannot identify DUs’ query information accurately. Additionally, other users (e.g., SUs and other DUs) cannot get any information of DU. In this circumstance, the privacy-preserving requirements of DU’s query information can be guaranteed. In addition, the privacy requirement also includes CS’s responses, i.e., only legal DU can decrypt the corresponding response.
- Authentication. Authenticating an encrypted query that is really sent by a legal DU and has not been altered during the transmission, i.e., if an illegal DU forges a query, this malicious operation should be detected, and only correct queries can be received by CS. The responses from CS should also be authenticated so that DUs can receive authentic and reliable query results. Moreover, the encrypted personal data from SUs can be authenticated by CS.
3.3. Design Goals
- The Security Requirements Should be Guaranteed. If the personal data collection and query scheme does not consider the security, SUs’ data assets and DU’s actual query information could be disclosed. Then, the data collection and query service cannot jump in popularity. Therefore, the proposed scheme should achieve the confidentiality, privacy and authentication simultaneously.
- A Personal Data query Service with High Accuracy Should be Guaranteed. The user experience is one of the most critical aspects of data query service, and it is important that the precision of Euclidean distance query service cannot be lowered when protecting DU’s privacy. Therefore, the proposed scheme should also provide highly precise and reliable query service.
- The Effectiveness in Computation and Communication Should be Achieved for Various Terminal Devices. The personal data may be collected by different terminal devices, such as smart phone, embedded device, etc. Although the performance of terminal devices is continuously improved today, the battery is still limited. The proposed scheme should also consider the effectiveness in terms of computation and communication to reduce the power consumption of different terminals. Moreover, data users can access the data query service by mobile terminals, in order to lower the energy cost, the efficiency of the query service is very important. Furthermore, although CS is featured with high performance in storage and computation, since thousands of DUs will query the data at the same time, the efficiencies of computation and communication are still challenging.
4. Preliminaries
4.1. Bilinear Pairing of Composite Order
- (1)
- Bilinearity. holds for all and ;
- (2)
- Non-degeneracy. ;
- (3)
- Computability. For all can be computed efficiently.
4.2. Euclidean Distance
4.3. 2DNF Cryptosystem
- Key generation . Given a security parameter , two prime numbers and are first chosen, and is computed. Two groups of the same order N are generated, g and u are two generators of . Then, is computed as a random generator of ’s subgroup with order . Finally, the public key and private key are generated.
- Encryption. We assume the message space consists of integers in the set with . Then, to encrypt a message m with public key PK, a random number r is selected from , and the ciphertext is computed.
- Decryption. To decrypt ciphertext C with private key , notice that ; let . To recover the corresponding message m, we need to compute the discrete log of , where . Since , it only takes expected time using Pollard’s lambda method [35] to get the message m.
5. Proposed SPCQ
| Notation | Definition |
|---|---|
| μ | the system security parameter |
| two big prime numbers | |
| the product of and | |
| the bilinear groups with order N | |
| e, g ,h | the parameters of bilinear groups |
| the asymmetric encryption algorithm, i.e., ECC | |
| H() | the secure cryptographic hash function |
| HPS | the evaluation dataset |
| the feature parameters of a data item | |
| the weighted number of different dimensions | |
| d | the weighted Euclidean search range of DU’s query |
| the encrypted search index of a data item | |
| DU’s encrypted query parameters |
5.1. System Initialization
5.2. Secure Data Collection
- SU computes , , where is only known by registered SUs and DUs; this operation can resist the exhaustive attack.
- SU chooses n random numbers and computes the encrypted search index , which can be implicitly formed as follows.
- SU makes a signature using the private key , where is the current timestamp to resist potential replay attack, and ID is the identify number of SU. Then, SU sends the signed data item to CS.
- After receiving the signed data item from SU, CS first checks the timestamp and verifies the signature by computing whether . If it does hold, the signature is accepted, since . Then, CS stores the data item .
5.3. Privacy-Preserving Query Service
5.3.1. User Query Generation
- first decides a data item with n feature parameters that he or she is willing to query and computes to increase the sample space.
- determines the weighted Euclidean distance search range d from the data item that he or she wants to query and computes encrypted query as follows.
- uses the public key of CS to compute .
- makes a signature using his or her private key , where is the current timestamp to resist potential replay attack. Then, sends the encrypted data query request to CS.
5.3.2. Search and Response
- CS first checks the timestamp and verifies the signature by computing whether . If it does hold, the signature is accepted, since .
- CS uses its secret key to decrypt Q and obtain . Then, CS executes the proposed WEDC algorithm as follows.
- -
- For each data item stored in it, CS computes the search criteria as follows.
- -
- CS computes and searches within the evaluation dataset HPS by binary search algorithm to confirm whether belongs to it. If belongs to HPS, it means that data item satisfies DU’s query condition; add one to , where denotes the number of data items that meets the query condition; otherwise, data item does not meet DU’s query condition.
- -
- After traversing through all data items, CS gets the number of data items that satisfy DU’s query condition and the number of all data items , which can help DU to achieve the statistical query of the personal data. Then, CS encrypts and with the asymmetric encryption algorithm E() and the public key of and uses its private key to make a signature .
- -
- Finally, CS sends to .
5.3.3. Query Result Reading
6. Security Analysis
- The Proposed SPCQ Can Achieve Confidential Personal Data. In our proposed SPCQ, personal data are secret from CS and DUs, although CS stores all encrypted data items and receives all query requests. First, since feature parameters collected by body sensors usually cover a smaller scope, to avoid the exhaustive attack against by Pollard’s lambda method, feature parameters are disturbed by calculating . In this way, the sample space is increased to more than 512 bits, which can prevent exhaustive attack efficiently. Before uploading to CS, feature parameters are encrypted to corresponding search index by computing , etc., where is a random number to guarantee that for the same feature parameter, different SUs can obtain different search indexes. The above operations can achieve data perturbation and substitution and prevent CS from directly accessing SUs’ personal data. Moreover, to avoid the guessing attacks for in the evaluation dataset HPS, the relationship between and is hidden by a secure hash function H(), where . Therefore, from the above three aspects, CS cannot obtain the feature parameters of personal data according to uploaded data items. In addition, since DUs only can get the query statistic result from CS, SUs’ personal data are secret from DUs.
- DU’s Query Information is Privacy-Preserving in the Proposed SPCQ. In our proposed SPCQ, similarly, DU’s query condition is encrypted before being sent to CS. Specifically, DU’s query information is disturbed by calculating which can resist the exhaustive attack by Pollard’s lambda method. Then, the query condition is encrypted by calculating , which can prevent CS from directly accessing the query data item and search range d. Since and are only known by SUs and DUs, and the collusion attack is not considered in the current security model, CS cannot obtain query information from the query request during the query process. Specifically, encrypted request and encrypted data are computed in CS to obtain the result, which will be sent back to DU, and CS also cannot obtain any useful information of DUs’ queries, even in the continuous search queries environment. Meanwhile, CS still can provide accurate query service to DUs by the proposed WEDC algorithm. Concretely, CS traverses all stored data items to compute the search criteria and find out all data items that satisfy the query condition, then it achieves the query statistic result and sends it to DU. It is notable that the result does not have particular meaning without any other useful information of DUs’ queries. Moreover, SUs are not involved in the query process, and DU’s query request is encrypted by CS’s public key before being sent to CS, so SUs cannot get DU’s query information even if they steal the request by eavesdropping. In addition, the response is encrypted by DU’s public key before being sent by CS, and thus, SUs and other registered DUs cannot decrypt the response. Therefore, from the above four aspects, DU’s query information is privacy-preserving in the proposed SPCQ.
- The Authentication of the Personal Data, Query Request and Response are Achieved in the Proposed SPCQ. In the proposed SPCQ, personal data from SUs, registered DU’s query request and the response of CS are signed by the BLS [36] short signature. Since the BLS short signature is provably secure under the CDH problem in the random oracle model, the source authentication can be guaranteed. Specifically, personal data from SU is signed by computing , where is the current timestamp to resist potential replay attack and SK is SU’s private key to make sure only itself can make the signature. After receiving the signed data item, CS computes whether to verify the source of the signature. Similarly, the registered DU’s query request and the response of CS are signed by the above operations. Moreover, since the unregistered user (such as SU and DU) does not have secret keys and , he or she cannot upload personal data item or submit valid query request to CS. Therefore, personal data and the query request from the unregistered user and the response from the mendacious CS can be detected in the proposed SPCQ.
7. Performance Evaluation
7.1. Computation and Communication Costs
| Phase of Scheme | SPCQ | PPRQ |
|---|---|---|
| SU | ||
| DU | ||
| CS |

| Phase of Scheme | SPCQ | PPRQ |
|---|---|---|
| Communication length in DU | 164 ∗ n bytes | 512 ∗ n bytes |
| Communication length in CS | 256 bytes | 1024 ∗ n bytes |
| Communication times | 2 | 2 |
7.2. Simulation and Evaluation
7.2.1. SU

7.2.2. DU
7.2.3. CS
7.2.4. Integrated Performance in a Real Environment
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Yang, G.Z.; Yacoub, M. Body Sensor Networks; Springer London: London, UK, 2006. [Google Scholar]
- Ullah, S.; Higgins, H.; Braem, B.; Latre, B.; Blondia, C.; Moerman, I.; Saleem, S.; Rahman, Z.; Kwak, K.S. A comprehensive survey of wireless body area networks. J. Med. Syst. 2012, 36, 1065–1094. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Sun, W.; Zhang, Z.; Ji, L.; Wong, W.C. An optimized handover scheme with movement trend awareness for body sensor networks. Sensors 2013, 13, 7308–7322. [Google Scholar] [CrossRef] [PubMed]
- Yu, R.; Yang, G.Z.; Lo, B.P.L. Autonomic body sensor networks. In Proceedings of the 2014 IEEE MTT-S International Microwave Workshop Series on RF and Wireless Technologies for Biomedical and Healthcare Applications (IMWS-Bio), London, UK, 8–10 December 2014; pp. 1–3.
- Moshaddique, A.A.; Jingwei, L.; Kyungsup, K. Security and Privacy Issues in Wireless Sensor Networks for Healthcare Applications. J. Med. Syst. 2012, 36, 93–101. [Google Scholar]
- Ren, Y.; Oleshchuk, V.; Li, F.Y.; Ge, X. Security in Mobile Wireless Sensor Networks—A Survey. J. Commun. 2011, 34, 1302–1325. [Google Scholar] [CrossRef]
- Movassaghi, S.; Abolhasan, M.; Lipman, J.; Smith, D.; Jamalipour, A. Wireless body area networks: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 1658–1686. [Google Scholar] [CrossRef]
- Sun, W.; Ge, Y.; Zhang, Z.; Wong, W.C. Performance Evaluation of Wearable Sensor Systems: A Case Study in Moderate-Scale Deployment in Hospital Environment. Sensors 2015, 15, 24977–24995. [Google Scholar] [CrossRef] [PubMed]
- Horvitz, E.; Mulligan, D. Data, privacy, and the greater good. Science 2015, 349, 253–255. [Google Scholar] [CrossRef] [PubMed]
- Barlow, M. Migrating Big Data Analytics into the Cloud; O’Reilly: Fairfield, CT, USA, 2014. [Google Scholar]
- Lien, I.T.; Lin, Y.H.; Shieh, J.R.; Wu, J.L. A Novel Privacy Preserving Location-Based Service Protocol With Secret Circular Shift for K-NN Search. IEEE Trans. Inf. Forensics Secur. 2013, 8, 863–873. [Google Scholar] [CrossRef]
- Shao, J.; Lu, R.; Lin, X. FINE: A Fine-Grained Privacy-Preserving Location-Based Service Framework for Mobile Devices. In Proceedings of the 2014 Proceedings IEEE INFOCOM, Toronto, ON, Canada, 27 April–2 May 2014; pp. 1452–1461.
- Liu, J.K.; Au, M.H.; Susilo, W.; Liang, K.; Lu, R.; Srinivasan, B. Secure sharing and searching for real-time video data in mobile cloud. IEEE Netw. 2015, 29, 46–50. [Google Scholar] [CrossRef]
- Juliadotter, N.V.; Choo, K.K.R. Cloud Attack and Risk Assessment Taxonomy. IEEE Cloud Comput. 2015, 2, 14–20. [Google Scholar] [CrossRef]
- Ab Rahman, N.H.; Choo, K.K.R. A survey of information security incident handling in the cloud. Comput. Secur. 2015, 49, 45–69. [Google Scholar] [CrossRef]
- Dwork, C. Differential Privacy; Springer US: Venice, Italy, 2006; pp. 1–12. [Google Scholar]
- Rivest, R.L.; Adleman, L.; Dertouzos, M.L. On data banks and privacy homomorphisms. Found. Secur. Comput. 1978, 4, 169–180. [Google Scholar]
- Song, D.X.; Wagner, D.; Perrig, A. Practical techniques for searches on encrypted data. In Proceedings of the 2000 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 14–17 May 2000; pp. 44–55.
- Rushanan, M.; Rubin, A.D.; Kune, D.F.; Swanson, C.M. SoK: Security and Privacy in Implantable Medical Devices and Body Area Networks. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–21 May 2014; pp. 524–539.
- Li, C.; Raghunathan, A.; Jha, N.K. Hijacking an insulin pump: Security attacks and defenses for a diabetes therapy system. In Proceedings of the 2011 13th IEEE International Conference on E-Health Networking Applications and Services (Healthcom), Columbia, MO, USA, 13–15 June 2011; pp. 150–156.
- Barthe, G.; Köpf, B.; Olmedo, F.; Zanella Béguelin, S. Probabilistic relational reasoning for differential privacy. In Proceedings of the 39th Annual ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, Philadelphia, PA, USA, 25–27 January 2012; Volome 47, pp. 97–110.
- Tschantz, M.C.; Kaynar, D.; Datta, A. Formal Verification of Differential Privacy for Interactive Systems. Electron. Notes Theor. Comput. Sci. 2011, 276, 61–79. [Google Scholar] [CrossRef]
- Eigner, F.; Maffei, M. Differential Privacy by Typing in Security Protocols. In Proceedings of the 2013 IEEE 26th Computer Security Foundations Symposium (CSF), New Orleans, LA, USA, 26–28 June 2013; pp. 272–286.
- Goldwasser, S.; Micali, S. Probabilistic encryption and how to play mental poker keeping secret all private information. In Proceedings of the 14th Annual ACM Symposium on Theory of Computing, San Francisco, CA, USA, 5–7 May 1982; pp. 365–377.
- Benaloh, J.D.C. Verifiable Secret-Ballot Elections; Department of Computer Science, Yale University: New Haven, CT, USA, 1987. [Google Scholar]
- Okamoto, T.; Uchiyama, S. A new public-key cryptosystem as secure as factoring. In Advances in Cryptology—EUROCRYPT’98; Springer Heidelberg: Berlin, Germany, 1998; pp. 308–318. [Google Scholar]
- Paillier, P. Public-key cryptosystems based on composite degree residuosity classes. In Advances in Cryptology–EUROCRYPT’99; Springer Heidelberg: Berlin, Germany, 1999; pp. 223–238. [Google Scholar]
- Gentry, C. Fully homomorphic encryption using ideal lattices. In Proceedings of the Forty-First Annual ACM Symposium on Theory of Computing, Bethesda, Maryland, 31 May–2 June 2009; Volume 9, pp. 169–178.
- Smart, N.P.; Vercauteren, F. Fully homomorphic encryption with relatively small key and ciphertext sizes. In Public Key Cryptography–PKC 2010; Springer Heidelberg: Berlin, Germany, 2010; pp. 420–443. [Google Scholar]
- Xiao, L.; Bastani, O.; Yen, I.L. An Efficient Homomorphic Encryption Protocol for Multi-User Systems. IACR Cryptol. ePrint Archive 2012, 2012, 193. [Google Scholar]
- Kamara, S.; Lauter, K. Cryptographic cloud storage. In Financial Cryptography and Data Security; Springer Heidelberg: Berlin, Germany, 2010; pp. 136–149. [Google Scholar]
- Boneh, D.; di Crescenzo, G.; Ostrovsky, R.; Persiano, G. Public key encryption with keyword search. In Advances in Cryptology-Eurocrypt 2004; Springer Heidelberg: Berlin, Germany, 2004; pp. 506–522. [Google Scholar]
- Cao, N.; Wang, C.; Li, M.; Ren, K.; Lou, W. Privacy-preserving multi-keyword ranked search over encrypted cloud data. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 222–233. [Google Scholar] [CrossRef]
- Boneh, D.; Goh, E.J.; Nissim, K. Evaluating 2-DNF formulas on ciphertexts. In Theory of Cryptography; Springer Heidelberg: Berlin, Germany, 2005; pp. 325–341. [Google Scholar]
- Menezes, A.J.; van Oorschot, P.C.; Vanstone, S.A. Handbook of Applied Cryptography; CRC Press: Boca Raton, FL, USA, 2010. [Google Scholar]
- Boneh, D.; Lynn, B.; Shacham, H. Short signatures from the Weil pairing. In Advances in Cryptology—ASIACRYPT 2001; Springer Heidelberg: Berlin, Germany, 2001; pp. 514–532. [Google Scholar]
- Clore, J.; Cios, K.J.; DeShazo, J.; Strack, B. Diabetes 130-US hospitals for years 1999-2008 Data Set. Available onine: http://archive.ics.uci.edu/ml/datasets/Diabetes+130-US+hospitals+for+years+1999-2008 (accessed on 3 September 2015).
- Samanthula, B.K.; Jiang, W. Efficient privacy-preserving range queries over encrypted data in cloud computing. In Proceedings of the 2013 IEEE Sixth International Conference on Cloud Computing (CLOUD), Santa Clara, CA, USA, 28 June–3 July 2013; pp. 51–58.
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhu, H.; Gao, L.; Li, H. Secure and Privacy-Preserving Body Sensor Data Collection and Query Scheme. Sensors 2016, 16, 179. https://doi.org/10.3390/s16020179
Zhu H, Gao L, Li H. Secure and Privacy-Preserving Body Sensor Data Collection and Query Scheme. Sensors. 2016; 16(2):179. https://doi.org/10.3390/s16020179
Chicago/Turabian StyleZhu, Hui, Lijuan Gao, and Hui Li. 2016. "Secure and Privacy-Preserving Body Sensor Data Collection and Query Scheme" Sensors 16, no. 2: 179. https://doi.org/10.3390/s16020179






