An Outline of Data Aggregation Security in Heterogeneous Wireless Sensor Networks
Abstract
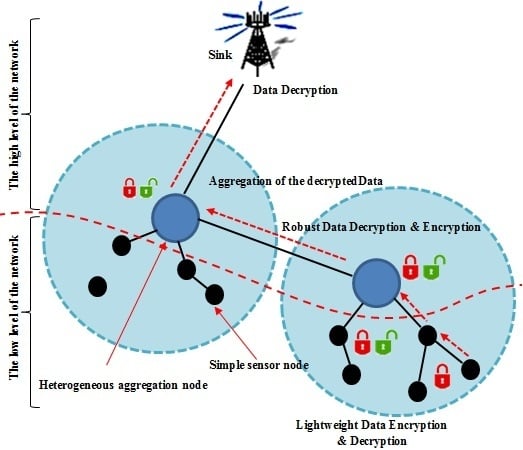
:1. Introduction
- Exploitation of the high capacities of the heterogeneous sensor nodes.
- Respect of the resources constraints of the simple homogeneous sensor nodes.
- Optimization of the data aggregation process while ensuring high data accuracy.
2. Data Aggregation Security Mechanisms for Heterogeneous Wireless Sensor Networks
2.1. End to End Secure Data Aggregation Protocols
2.1.1. Concealed Data Aggregation in Heterogeneous Sensor Networks Using Privacy Homomorphism (CDAP)
Protocol Presentation
- The public key of the base station is assigned to the AGGNODEs and the network is deployed.
- Pair-wise keys are shared between the AGGNODEs and their neighbouring nodes.
- Each node encrypts data using the symmetric encryption algorithm (RC5) [8] and sends the encrypted data to its neighbor AGGNODE.
- Each AGGNODE decrypts the received data, applies the aggregation function and encrypts the result using the privacy homomorphism encryption algorithm described as follows: Let E be the encryption function and D the decryption function. + and * indicate the addition and the multiplication functions applied on the data set Q. Assuming that the private and the public keys of the base station are respectively and , a transformation encryption is additively homomorphic if:where a, b belong to Q. This transformation is multiplicatively homomorphic if:
- The encrypted data are transmitted and the AGGNODEs aggregate hierarchically the encrypted data during the transmission.
- Only the base station can decrypt the aggregated data using its private key.
Evaluation
2.1.2. Privacy-Preserving Integrity-Assured Data Aggregation (PIA)
Protocol Presentation
- The first solution uses the privacy homomorphism encryption to conceal data. The homomorphism combined with authentication message MAC are used to construct an authenticated encryption protocol for the aggregation model [10]. However, the homomorphism allows a limited number of aggregation functions such as sum or average.
- The second solution uses the Order Preserving Encryption Scheme or OPES [11] which maintains the data fusion confidentiality. As an example, OPES preserves the encrypted order so that any data pair and where are encrypted to and so that. However, this scheme is only required for the aggregation functions which can be approximated with uniform sampling. It is also exclusively based on the comparison operation.
- The third solution uses the Secure Hierarchical In-networking Aggregation (SHIA) protocol [12], which supports all the possible aggregation functions to adapt a distributed integrity. However, the communication cost that corresponds to this protocol is messages per sensor node where N is the total number of the nodes in the network.
- To insure data confidentiality and integrity, the third solution is improved by introducing a logical aggregation tree in the aggregation node. This solution is the latest one in which the communication cost is. However, this solution supports only a limited number of aggregation functions such as average, and Min/Max.
Evaluation
2.1.3. Secure-Encrypted Data Aggregation for Wireless Sensor Networks (SEDA)
Protocol Presentation
- Encryption phase: The encryption phase insures data confidentiality with lower costs. During this phase, each sensor node randomly generates a new key, and changes periodically the encryption keys.
- Aggregation phase: The aggregation mechanism enables the identification of two identical readings. All redundant readings of n encrypted packets are thus eliminated. If n identical readings are encrypted and transmitted to the aggregation node, the aggregation node must verify these entries times and save packet transmissions.
Evaluation
2.1.4. Secure Aggregation with Key Management (SDKAM)
Protocol Presentation
- (1)
- Encryption Mechanism
- A random encryption matrix A Є Ml × l and an initialization vector u Є Vl are chosen.
- Set and, where m is the vector Vl Є unencrypted data.
- For 0 ≤ i <k, calculate
- The encrypted data is represented by:
- (2)
- Decryption Mechanism
- Effective key management system: The authors propose an efficient key management in heterogeneous WSNs. This system is based on a decentralized algorithm for key pre-distribution and revocation, which includes the following phases:
- Key Pre-distribution: In this phase, the keys are chosen from pools of keys and then pre-distributed.
- Shared key discovery phase: A common key between the neighboring nodes is chosen among the pre-distributed keys.
- Key path establishment phase: After the secret key is revealed, a secure data transmission path, including encryption and decryption, is established.
- Key revocation phase: If a node is compromised, the shared keys are revoked through a voting algorithm. Compromised nodes are identified according to their behavior, and are isolated.
Evaluation
2.1.5. Recoverable Concealed Data Aggregation for Data Integrity in Wireless Sensor Networks (RCDA)
Protocol Presentation
Evaluation
2.1.6. Recoverable Concealed Data Aggregation for Data Integrity in Wireless Sensor Networks (Sen-SDA)
Protocol Presentation
- -
- The BS generates the system parameter which is preloaded in each sensor node.
- -
- The BS keeps a master secret key for the extraction of the private key and a secret key for the decryption of the ciphertexts.
- -
- Each sensor node encrypts a message using the public key of the BS and obtains a ciphertext through EC-ElGamal+.
- -
- The node uses then the private key to generate a signature.
- -
- The CH uses the batch verification technique to find and reject the invalid signatures.
- -
- The CH then aggregates the received messages with the private key, generates a new signature and sends the signed messages to the BS.
- -
- The BS uses the batch verification technique with BQS until the batch verification is completed successfully.
- -
- If the batch verification is completed successfully, the BS recovers the message using the secret key corresponding to the public key.
Evaluation
2.2. Hop by Hop Secure Data Aggregation Protocols
2.2.1. Secure Reference-Based Data Aggregation Protocol for Wireless Sensor Networks (SRDA)
Protocol Presentation
- A node, which can be a sensor node or an aggregation node, transmits the results to a higher level, forwards the packet containing the pure sensed data at time t for the first packet in the session.
- The group leader creates a reference input for this node.
- For subsequent readings , j > 1, the sensor node sends differential data instead of the pure sensed data .
- When the session is finished, the group leader removes the reference input of the node.
- Decrypt data and calculate the number of hops to the base station.
- Execute the aggregation function, and then encrypt the obtained result using RC6 algorithm (block cipher) [21]. The number of hops NS is calculated as follows:
- Transmit the encrypted result to the base station.
- The base station decrypts the received data using the corresponding decryption key.
Evaluation
2.3. Two Levels Secure Data Aggregation Protocols
2.3.1. A Watermarking-Based Mechanism for Data Aggregation Security in Heterogeneous WSNs
Secure Data Aggregation Watermarking-Based Scheme in Homogeneous WSNs (SDAW)
Cross-Layer Watermarking-Based Mechanism for Data Aggregation Integrity in Heterogeneous WSNs algorithm (CLDWA)
Evaluation
3. Heterogeneous Data Aggregation Security Approaches Evaluation and Discussion
4. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Simmons, G.J. Symmetric and Asymmetric Encryption. ACM Comput. Surv. CSUR 1979, 11, 305–330. [Google Scholar] [CrossRef]
- Jueneman, R.R.; Matyas, S.M.; Meyer, C.H. Message Authentication. IEEE Commun. Mag. 1985, 23, 29–40. [Google Scholar] [CrossRef]
- Rivest, R.L.; Adleman, L.; Dertouzos, M.L. On data banks and privacy homomorphisms. Found. Secur. Comput. 1978, 4, 169–179. [Google Scholar]
- Yu, L.; Wang, N.; Zhang, W.; Zheng, C. Deploying A Heterogeneous Wireless Sensor Network. In Proceedings of the International Conference on Wireless Communications, Networking and Mobile Computing, Shanghai, China, 21–25 September 2007; pp. 2588–2591.
- Mlaih, E.; Aly, S.A. Secure Hop-by-Hop Aggregation of End-to-End Concealed Data in Wireless Sensor Networks. In Proceedings of the IEEE INFOCOM Workshops, Phoenix, AZ, USA, 13–18 April 2008.
- Josna, J.; Joyce, J.; Fijo, J. A Survey on Secure Data Aggregation Protocols in Wireless Sensor Networks. Int. J. Comput. Appl. 2012, 55, 17–21. [Google Scholar]
- Ozdemir, S. Concealed data aggregation in heterogeneous sensor networks using privacy homomorphism. In Proceedings of the IEEE International Conference on Pervasive Services, Istanbul, Turkey, 15–20 July 2007; pp. 165–168.
- Rivest, R.L. The RC5 Encryption Algorithm. In Proceeding of the Second International Workshop, Leuven, Belgium, 14–16 December 1994.
- Taban, G.; Gligor, V.D. Privacy-preserving integrity-assured data aggregation in sensor networks. In Proceeding of International Symposium on Secure Computing, SecureCom, Vancouver, BC, Canada, 29–31 August 2009; pp. 168–175.
- Bellare, M.; Canetti, R.; Krawczyk, H. Keying hash functions for message authentication. In Proceedings of Annual International Cryptology Conference, Crypto, Santa Barbara, CA, USA, 18–21 August 1996; pp. 1–16.
- Agrawal, R.; Kiernan, J.; Srikant, R.; Xu, Y. Order preserving encryption for numeric data. In Proceedings of the 2004 ACM SIGMOD International Conference on Management of Data, Paris, France, 13–18 June 2004; pp. 563–574.
- Chan, H.; Perrig, A.; Song, D. Secure hierarchical in-network aggregation in sensor networks. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 278–287.
- Huang, S.I.; Shieh, S.; Tygar, J.D. Secure encrypted-data aggregation for wireless sensor networks. Wirel. Netw. 2010, 16, 915–927. [Google Scholar] [CrossRef]
- Lloret, J.; Garcia, M.; Tomas, J.; Boronat, F. GBP-WAHSN: A Group-Based Protocol for Large Wireless Ad Hoc and Sensor Networks. J. Comput. Sci. Technol. 2008, 23, 461–480. [Google Scholar] [CrossRef]
- Sandhya, M.K.; Murugan, K. Secure Framework for Data Centric Heterogeneous Wireless Sensor Networks. In Proceeding of the Recent Trends in Network Security and Applications—Third International Conference, CNSA 2010, Chennai, India, 23–25 July 2010.
- Chan, A.C.-F. Symmetric-Key Homomorphic Encryption for Encrypted Data Processing. In Proceeding of the IEEE International Conference ICC’09, Dresden, Germany, 14–18 June 2009.
- Chen, C.M.; Lin, Y.H.; Lin, Y.C.; Sun, H.M. RCDA: Recoverable concealed data aggregation for data integrity in wireless sensor networks. IEEE Trans Parallel Distrib. Syst. 2012, 23, 727–734. [Google Scholar] [CrossRef]
- Kyung, S.; Cheol, P. A secure data aggregation scheme based on appropriate cryptographic primitives in heterogeneous wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 2128–2139. [Google Scholar]
- Law, L.; Matt, B.J. Finding invalid signatures in pairingbasedbatches. In Proceedings of the 11th IMA International Conference, Cirencester, UK, 18–20 December 2007; pp. 35–43.
- Sanli, H.O.; Ozdemir, S.; Cam, H. SRDA: Secure reference-based data aggregation protocol for wireless sensor networks. In Proceeding of the 60th IEEE Vehicular Technology Conference, Los Angeles, CA, USA, 26–29 September 2004; Volume 7, pp. 4650–4654.
- Rivest, R.L.; Robshaw, M.J.B.; Sidney, R.; Yin, Y.L. The RC6 Block Cipher, AES Submission. June 1998. Available online: http://theory.lcs.mit.edu/ rivest/rc6.pdf (accessed on 13 March 2016).
- Boubiche, D.E.; Boubiche, S.; Bilami, A. A Cross-layer Watermarking-based Mechanism for Data Aggregation Integrity in Heterogeneous WSNs. IEEE Commun. Lett. 2015, 19, 823–826. [Google Scholar] [CrossRef]
- Boubiche, D.E.; Boubiche, S.; Homero, T.; Al-Sakib, K.P.; Bilami, A.; Athmani, S. SDAW: Secure Data Aggregation Watermarking-Based Scheme in Homogeneous WSNs. J. Telecommun. Syst. 2015, 59. [Google Scholar] [CrossRef]
- Eastlake, D.; Jones, P. RFC3174-US Secure Hash Algorithm-I (SHA1); Network Working Group. 2001; Available online: http://www.hjp.at/doc/rfc/rfc3174.html (accessed on 13 March 2016).
- Mahimkar, A.; Rappaport, T.S. SecureDAV: A Secure Data Aggregation and Verification Protocol for Sensor Networks. In Proceedings of the IEEE Global Telecommunications Conference, Dallas, TX, USA, 29 November–3 December 2004; pp. 2175–2179.
- Wang, S.; Cao, Z.; Strangio, M.A.; Wang, L. Cryptanalysis and improvement of an elliptic curve Diffie-Hellman key agreement protocol. IEEE Commun. Lett. 2008, 12, 149–151. [Google Scholar] [CrossRef]










| Protocol | Advantages | Limits |
|---|---|---|
| CDAP | - Improves the security between the base station and the AGGNODEs. | - Only addition and multiplication aggregation functions are allowed. - Computation overhead on resource limited sensor nodes |
| PIA | - A hybrid protocol combining different solutions to increase security. | - Due to privacy homomorphism and OPES, the protocol is confronted to the limited allowed aggregation function. |
| SEDA | - Improves security by offering a random key generation. | - Improves security by offering a random key generation. |
| SDKAM | - Uses an effective keys management system to strength the security. | - Encryption IHC is limited in terms of allowed aggregation functions. |
| RCDA | - Uses digital signatures to guarantee data integrity and authentication. - The base station has the possibility to recover all sensed data even if they were already aggregated. | - The network is not scalable. - The key generation and distribution mechanisms are not presented. |
| Sen-SDA | - Insures end-to-end confidentiality. - Insures hop by hop authentication. - Reduces the computational cost through the use of efficient pairing free identity based signature scheme. | - The homomorphic encryption limits the aggregation functions to only addition and multiplication. - Computation overhead on resource limited sensor nodes due to the use of asymmetric encryption. |
| MAC Authentication | Symmetric Encryption | Asymmetric Encryption | Privacy Homomorphism | |
|---|---|---|---|---|
| CDAP | No | RC5 | Okamoto and Uchiyama public-key cryptosystem | Okamoto and Uchiyama public-key cryptosystem |
| PIA | MAC message | Order Preserving Encryption Scheme OPES | No | SHIA SUM algorithm |
| SEDA | No | One-time pad method | No | No |
| SDKAM | No | Yes | Yes | IHC |
| RCDA | MAC message | KeyGen of Boneh et al.’s scheme KeyGen of Mykletun et al.’s scheme | No | No |
| Sen-SDA | No | No | EC-El Gamal+ | EC-El Gamal+ |
| Confidentiality | Integrity | Freshness | Authentication | |
|---|---|---|---|---|
| CDAP | Yes | No | No | No |
| PIA | Yes | Yes | No | Yes |
| SEDA | Yes | Yes | No | No |
| SDKAM | Yes | Yes | Yes | No |
| RCDA | Yes | Yes | No | Yes |
| Sen-SDA | Yes | Yes | Yes | No |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Boubiche, S.; Boubiche, D.E.; Bilami, A.; Toral-Cruz, H. An Outline of Data Aggregation Security in Heterogeneous Wireless Sensor Networks. Sensors 2016, 16, 525. https://doi.org/10.3390/s16040525
Boubiche S, Boubiche DE, Bilami A, Toral-Cruz H. An Outline of Data Aggregation Security in Heterogeneous Wireless Sensor Networks. Sensors. 2016; 16(4):525. https://doi.org/10.3390/s16040525
Chicago/Turabian StyleBoubiche, Sabrina, Djallel Eddine Boubiche, Azzedine Bilami, and Homero Toral-Cruz. 2016. "An Outline of Data Aggregation Security in Heterogeneous Wireless Sensor Networks" Sensors 16, no. 4: 525. https://doi.org/10.3390/s16040525
APA StyleBoubiche, S., Boubiche, D. E., Bilami, A., & Toral-Cruz, H. (2016). An Outline of Data Aggregation Security in Heterogeneous Wireless Sensor Networks. Sensors, 16(4), 525. https://doi.org/10.3390/s16040525