Fog-Based Two-Phase Event Monitoring and Data Gathering in Vehicular Sensor Networks
Abstract
:1. Introduction
- By integrating the concept of fog nodes and VANETs, we propose an efficient scheme to efficiently monitor the events and gather data based on VANETs. The sensing operators are roughly classified into the low cost sensing (LCS) mode and the high cost sensing (HCS) mode, and by taking full advantage of the fog nodes, our scheme strikes a good balance between these two modes to achieve better efficiency;
- The “two-level threshold adjustment” (2LTA) is proposed to avoid unnecessary event-checking and data upload. At the node level, only readings with a larger weight are sent to the RSU for further processing. The RSU then checks the confidence/probability of an event and initiates an event-checking procedure when the confidence exceeds a threshold. No event-checking procedure is needed if the confidence is within the range of thresholds;
- Extensive experiments were conducted to demonstrate the effectiveness of the proposed algorithm. TPEG reduces more than 84% of data transmissions compared to other algorithms, while at the same time, it detects the events and gathers the event data.
2. Related Work
2.1. Event Monitoring and Data Gathering
2.2. VANETs and Fog Computing
3. Preliminaries
3.1. Network and Data Gathering
- Continuous monitoring: the network is monitored through low-cost collection of sensing data so that ITS is informed when an event occurs. This task is represented by the event-checking procedure;
- Data gathering: more detailed data are gathered to the ITS cloud, and the data uploaded are time-limited and delay-constrained;
- Event verification: the ITS system verifies whether an event occurs and gives feedbacks to the VANETs.
3.2. Event and Weight of Data
4. TPEG Framework
4.1. Overview
- Data monitoring: Nodes work in LCS mode, and they sense the environment and generate the data. The data have a relatively low generation rate and confidence and are uploaded to the RSU through V2I or V2V communications.
- Event checking: RSU checks the confidence/probability of an event, and it initiates an event-checking procedure when the event probability is high. When the confidence is low, nodes just keep silent, and no event-checking procedures are needed.
- Deep sensing: Some nodes are selected to transfer to “deep sensing”, where they work in HCS mode and sense more accurate data about the environment.
- Data upload: The data generated in HCS mode are uploaded to the RSU for final event verification. Data could be uploaded directly, forwarded to neighboring nodes or wait until encountering a new RSU. Nodes would adaptively decide their strategy for data upload based on whether they are within the coverage of an RSU or encountered nodes.
- Event decision: The ITS cloud process the gathered data and make a decision about the events. Some data are archived on the cloud, and some feedback is sent back to the RSUs.
4.2. Low Cost Monitoring
4.3. Event Checking and Node Selection
4.4. Adaptive Data Upload
- When the node is within the coverage area of RSU, is directly scheduled for uploading, which is denoted as:where s is the node that holds and returns if node s is within the coverage of an RSU.
- When there is no RSU coverage or node-to-node connections, is stored locally, and the upload is suppressed, which is denoted as:where denotes the set of neighbors of node s.
- When a node moves out of the RSU coverage and encounters a neighboring node, it would decide its forwarding strategy based on the current node s and the encountered node . might be forwarded to or be stored at s and waits for other transmission opportunities. This is denoted as:where denotes the feasibility of forwarding data from node s to . returns if the data are forwarded to , and node would go into an RSU coverage area and upload the data before a predefined deadline. In more detail, is if it satisfies the following condition:Here, is the time constraint of data to be uploaded to the ITS system, is the expected time interval for node to enter an RSU coverage area and is the time duration of data uploading, which could be easily calculated by dividing the data size by the bandwidth: . is the expected contact duration of node s and .
4.5. Threshold Adjustment
- Events are assumed to be uncommon phenomenon. When events do not occur, the network should avoid unnecessary event-checking procedures.
- Unlike some monitoring and detection scenarios where events are transient, events at VANETs would usually last for a period of time. Therefore, when an event occurs, it is important for nodes not to be triggered by HCS mode and not to upload the redundant data to the RSU.
4.5.1. Node Level Adjustment
4.5.2. RSU Level Adjustment
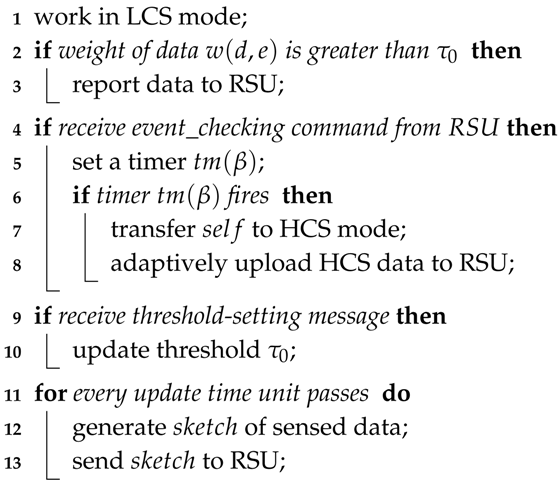
4.6. Algorithm Descriptions
| Algorithm 1: Handling messages at ordinary nodes. |
 |
| Algorithm 2: Handling messages at RSUs and the cloud. |
 |
5. Experimental Study
5.1. Environmental Setup
5.2. Metrics and Compared Algorithms
5.3. Overall Performance
5.4. Impact of Factors
5.4.1. Number of Nodes
5.4.2. Size of Cache
5.4.3. Sensing Frequency
5.4.4. Threshold Adjustment
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Al-Sultan, S.; Al-Doori, M.M.; Al-Bayatti, A.H.; Zedan, H. A comprehensive survey on vehicular Ad Hoc Network. J. Netw. Comput. Appl. 2014, 37, 380–392. [Google Scholar] [CrossRef]
- Dua, A.; Kumar, N.; Bawa, S. A systematic review on routing protocols for vehicular Ad Hoc Networks. Veh. Commun. 2014, 1, 33–52. [Google Scholar] [CrossRef]
- Xu, Y.; Chen, X.; Liu, A.; Hu, C. A latency and coverage optimized data collection scheme for smart cities based on vehicular Ad-hoc networks. Sensors 2017, 17, 888. [Google Scholar] [CrossRef] [PubMed]
- Jiang, D.; Delgrossi, L. IEEE 802.11 p: Towards an International Standard for Wireless access in Vehicular Environments. In Proceedings of the Vehicular Technology Conference (VTC Spring 2008), Singapore, 11–14 May 2008; pp. 2036–2040. [Google Scholar]
- Kosch, T.; Adler, C.; Eichler, S.; Schroth, C.; Strassberger, M. The scalability problem of vehicular Ad Hoc Networks and how to solve it. IEEE Wirel. Commun. 2006, 13, 22–28. [Google Scholar] [CrossRef]
- Lai, Y.; Xie, J.; Lin, Z.; Wang, T.; Liao, M. Adaptive data-gathering in mobile sensor networks using speedy mobile elements. Sensors 2015, 15, 23218–23248. [Google Scholar] [CrossRef] [PubMed]
- Lai, Y.; Gao, X.; Liao, M.; Xie, J.; Lin, Z.; Zhang, H. Data gathering and offloading in delay tolerant mobile networks. Wirel. Netw. 2016, 22, 959–973. [Google Scholar] [CrossRef]
- Wang, T.; Zeng, J.; Lai, Y.; Cai, Y.; Tian, H.; Chen, Y.; Wang, B. Data collection from WSNs to the cloud based on mobile Fog elements. Future Gener. Comput. Syst. 2017, in press. [Google Scholar] [CrossRef]
- Lee, U.; Magistretti, E.; Gerla, M.; Bellavista, P.; Corradi, A. Dissemination and harvesting of urban data using vehicular sensing platforms. IEEE Trans. Veh. Technol. 2009, 58, 882–901. [Google Scholar]
- Intel. Technology and Computing Requirements for Self-Driving Cars. Available online: https://www.intel.com/content/www/us/en/automotive/driving-safety-advanced-driver-assistance-systems-self-driving-technology-paper.html (accessed on 26 December 2017).
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog Computing and its Role in the Internet of Things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; Association for Computing Machinery: New York, NY, USA, 2012; pp. 13–16. [Google Scholar]
- Zeng, J.; Wang, T.; Lai, Y.; Liang, J.; Chen, H. Data Delivery from WSNs to Cloud based on a Fog Structure. In Proceedings of the Fourth IEEE International Conference on Advanced Cloud and Big Data, Chengdu, China, 13–16 August 2016; pp. 959–973. [Google Scholar]
- Hao, Z.; Novak, E.; Yi, S.; Li, Q. Challenges and software architecture for fog computing. IEEE Internet Comput. 2017, 21, 44–53. [Google Scholar] [CrossRef]
- Aazam, M.; Huh, E.N. Fog Computing and Smart Gateway based Communication for Cloud of Things. In Proceedings of the 2014 International Conference on Future Internet of Things and Cloud (FiCloud), Barcelona, Spain, 27–29 August 2014; pp. 464–470. [Google Scholar]
- Lee, U.; Zhou, B.; Gerla, M.; Magistretti, E.; Bellavista, P.; Corradi, A. Mobeyes: Smart mobs for urban monitoring with a vehicular sensor network. IEEE Wirel. Commun. 2006, 13, 52–57. [Google Scholar] [CrossRef]
- Hull, B.; Bychkovsky, V.; Zhang, Y.; Chen, K.; Goraczko, M.; Miu, A.; Shih, E.; Balakrishnan, H.; Madden, S. CarTel: A Distributed Mobile Sensor Computing System. In Proceedings of the 4th International Conference on Embedded Networked Sensor Systems, Boulder, CO, USA, 31 October–3 November 2006; Association for Computing Machinery: New York, NY, USA, 2006; pp. 125–138. [Google Scholar]
- Palazzi, C.E.; Pezzoni, F.; Ruiz, P.M. Delay-bounded data-gathering in urban vehicular sensor networks. Pervasive Mob. Comput. 2012, 8, 180–193. [Google Scholar] [CrossRef]
- Delot, T.; Mitton, N.; Ilarri, S.; Hien, T. Decentralized Pull-based Information Gathering in Vehicular Networks Using GeoVanet. In Proceedings of the 2011 IEEE 12th International Conference on Mobile Data Management, Lulea, Sweden, 6–9 June 2011; Volume 1, pp. 174–183. [Google Scholar]
- PÅĆaczek, B. Selective data collection in vehicular networks for traffic control applications. Transp. Res. Part C Emerg. Technol. 2012, 23, 14–28. [Google Scholar] [CrossRef]
- Skordylis, A.; Trigoni, N. Efficient data propagation in traffic-monitoring vehicular networks. IEEE Trans. Intell. Transp. Syst. 2011, 12, 680–694. [Google Scholar] [CrossRef]
- Zekri, D.; Defude, B.; Delot, T. Building, sharing and exploiting spatio-temporal aggregates in vehicular networks. Mob. Inf. Syst. 2014, 10, 259–285. [Google Scholar] [CrossRef]
- Li, X.; Huang, H.; Yu, X.; Shu, W.; Li, M.; Wu, M.Y. A new paradigm for urban surveillance with vehicular sensor networks. Comput. Commun. 2011, 34, 1159–1168. [Google Scholar] [CrossRef]
- Xie, K.; Luo, W.; Wang, X.; Xie, D.; Cao, J.; Wen, J.; Xie, G. Decentralized Context Sharing in Vehicular Delay Tolerant Networks with Compressive Sensing. In Proceedings of the 2016 IEEE 36th International Conference on Distributed Computing Systems (ICDCS), Nara, Japan, 27–30 June 2016; pp. 169–178. [Google Scholar]
- Satyanarayanan, M.; Schuster, R.; Ebling, M.; Fettweis, G.; Flinck, H.; Joshi, K.; Sabnani, K. An open ecosystem for mobile-cloud convergence. IEEE Commun. Mag. 2015, 53, 63–70. [Google Scholar] [CrossRef]
- Sharma, S.K.; Wang, X. Live data analytics with collaborative edge and cloud processing in wireless IoT networks. IEEE Access 2017, 5, 4621–4635. [Google Scholar] [CrossRef]
- Tang, B.; Chen, Z.; Hefferman, G.; Pei, S.; Tao, W.; He, H.; Yang, Q. Incorporating intelligence in fog computing for big data analysis in smart cities. IEEE Trans. Ind. Inform. 2017, 13, 2140–2150. [Google Scholar] [CrossRef]
- Eltoweissy, M.; Olariu, S.; Younis, M. Towards Autonomous Vehicular Clouds. In Proceedings of the International Conference on Ad Hoc Networks, Victoria, BC, Canada, 18–20 August 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 1–16. [Google Scholar]
- Hussain, R.; Rezaeifar, Z.; Oh, H. A paradigm shift from vehicular Ad Hoc Networks to VANET-based clouds. Wirel. Pers. Commun. 2015, 83, 1131–1158. [Google Scholar] [CrossRef]
- Mershad, K.; Artail, H. Finding a STAR in a vehicular cloud. IEEE Intell. Transp. Syst. Mag. 2013, 5, 55–68. [Google Scholar] [CrossRef]
- Vaquero, L.M.; Rodero-Merino, L. Finding your way in the fog: Towards a comprehensive definition of fog computing. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 27–32. [Google Scholar] [CrossRef]
- Kai, K.; Cong, W.; Tao, L. Fog computing for vehicular Ad-hoc networks: Paradigms, scenarios, and issues. J. China Univ. Posts Telecommun. 2016, 23, 56–96. [Google Scholar] [CrossRef]
- Wang, T.; Peng, Z.; Wen, S.; Lai, Y.; Jia, W.; Cai, Y.; Tian, H.; Chen, Y. Reliable wireless connections for fast-moving rail users based on a chained fog structure. Inf. Sci. 2017, 379, 160–176. [Google Scholar] [CrossRef]
- Wang, T.; Zeng, J.; Bhuiyan, M.Z.A.; Tian, H.; Cai, Y.; Chen, Y.; Zhong, B. Trajectory privacy preservation based on a fog structure in cloud location services. IEEE Access 2017, 5, 7692–7701. [Google Scholar] [CrossRef]
- Menard, S. Applied Logistic Regression Analysis; Sage: Newcastle, UK, 2002; Volume 106. [Google Scholar]
- Crevier, D.; Lepage, R. Knowledge-based image understanding systems: A survey. Comput. Vis. Image Underst. 1997, 67, 161–185. [Google Scholar] [CrossRef]
- Lai, Y.; Lin, Z. Data gathering in opportunistic wireless sensor networks. Int. J. Distrib. Sens. Netw. 2012, 8, 230198. [Google Scholar] [CrossRef]
- Keränen, A.; Ott, J.; Kärkkäinen, T. The ONE Simulator for DTN Protocol Evaluation. In Proceedings of the 2nd International Conference on Simulation Tools and Techniques (SIMUTools ’09), Rome, Italy, 2–6 March 2009; ICST: New York, NY, USA, 2009. [Google Scholar]
- Lindgren, A.; Doria, A.; Schelén, O. Probabilistic routing in intermittently connected networks. In Service Assurance with Partial and Intermittent Resources; Springer: Berlin/Heidelberg, Germany, 2004; pp. 239–254. [Google Scholar]
- Koubek, M.; Rea, S.; Pesch, D. Event Suppression for Safety Message Dissemination in VANETs. In Proceedings of the 2010 IEEE 71st Vehicular Technology Conference (VTC 2010-Spring), Taipei, Taiwan, 16–19 May 2010; pp. 1–5. [Google Scholar]
- Zhao, J.; Cao, G. VADD: Vehicle-assisted data delivery in vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2008, 57, 1910–1922. [Google Scholar] [CrossRef]













| Parameter | Value | Description |
|---|---|---|
| n | 60 | number of vehicular nodes |
| n_RSU | 6 | number of RSU nodes |
| n_time | 43,200 s | simulation duration |
| L | 3000 m | length of road segment |
| d_time | ∼[25–35] s | interval of sensing |
| 60 m | sensing radius of RSU nodes | |
| speed | ∼[5, 10] m/s | speed of nodes |
| data | 50,500 KB | size of sensing data at LCS/HCS |
| cache_size | 300 MB | cache size of nodes |
| e_length | ∼[1000, 5000] s | life span of events |
| 200 s | interval of events (Poisson distribution) | |
| m | 3 | number of readings at RSU for event-checking |
| 0.05 | predefined increment factor for | |
| 10,000 s | unit of time for threshold adjustment | |
| ∼[0,0.5], ∼[0.0.1] | range of noise in LCS and HCS | |
| 0.1, 0.05 | standard deviation of weight in LCS and HCS |
| Algorithm | NAIVE | PROPHET | ESSMD | TPEG |
|---|---|---|---|---|
| True Positive (#/ratio) | 42.2/0.2497 | 147.62/0.8242 | 150.63/0.8389 | 147.47/0.8317 |
| True Negative (#/ratio) | 7.51/0.0444 | 17.32/0.0967 | 16.68/0.0929 | 14.66/0.0827 |
| False Positive (#/ratio) | 2.11/0.0125 | 3.47/0.0194 | 2.4/0.0134 | 2.81/0.0158 |
| False Negative (#/ratio) | 117.19/0.6934 | 10.69/0.0597 | 9.84/0.0548 | 12.38/0.0698 |
| Recall Rate (p1) | 0.2648 | 0.9325 | 0.9387 | 0.9226 |
| Precision (p2) | 0.9524 | 0.977 | 0.9843 | 0.9813 |
| Transmissions () | 2.34 | 3421.98 | 2583.36 | 403.26 |
| Average Time (minute) | 36.29 | 28.83 | 30.6 | 33.69 |
| Incremental Factor () | 0.03 | 0.05 | 0.07 | 0.1 |
|---|---|---|---|---|
| Recall Rate () | 0.9554 | 0.9265 | 0.9091 | 0.8929 |
| Precision () | 0.9350 | 0.9403 | 0.9459 | 0.9346 |
| Transmissions () | 618.77 | 578.38 | 556.78 | 532.22 |
| Average Time (minute) | 24.73 | 25.65 | 30.12 | 37.55 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lai, Y.; Yang, F.; Su, J.; Zhou, Q.; Wang, T.; Zhang, L.; Xu, Y. Fog-Based Two-Phase Event Monitoring and Data Gathering in Vehicular Sensor Networks. Sensors 2018, 18, 82. https://doi.org/10.3390/s18010082
Lai Y, Yang F, Su J, Zhou Q, Wang T, Zhang L, Xu Y. Fog-Based Two-Phase Event Monitoring and Data Gathering in Vehicular Sensor Networks. Sensors. 2018; 18(1):82. https://doi.org/10.3390/s18010082
Chicago/Turabian StyleLai, Yongxuan, Fan Yang, Jinsong Su, Qifeng Zhou, Tian Wang, Lu Zhang, and Yifan Xu. 2018. "Fog-Based Two-Phase Event Monitoring and Data Gathering in Vehicular Sensor Networks" Sensors 18, no. 1: 82. https://doi.org/10.3390/s18010082






