New DoS Defense Method Based on Strong Designated Verifier Signatures
Abstract
:1. Introduction
2. The Problem and Related Work
2.1. The Adversarial Model
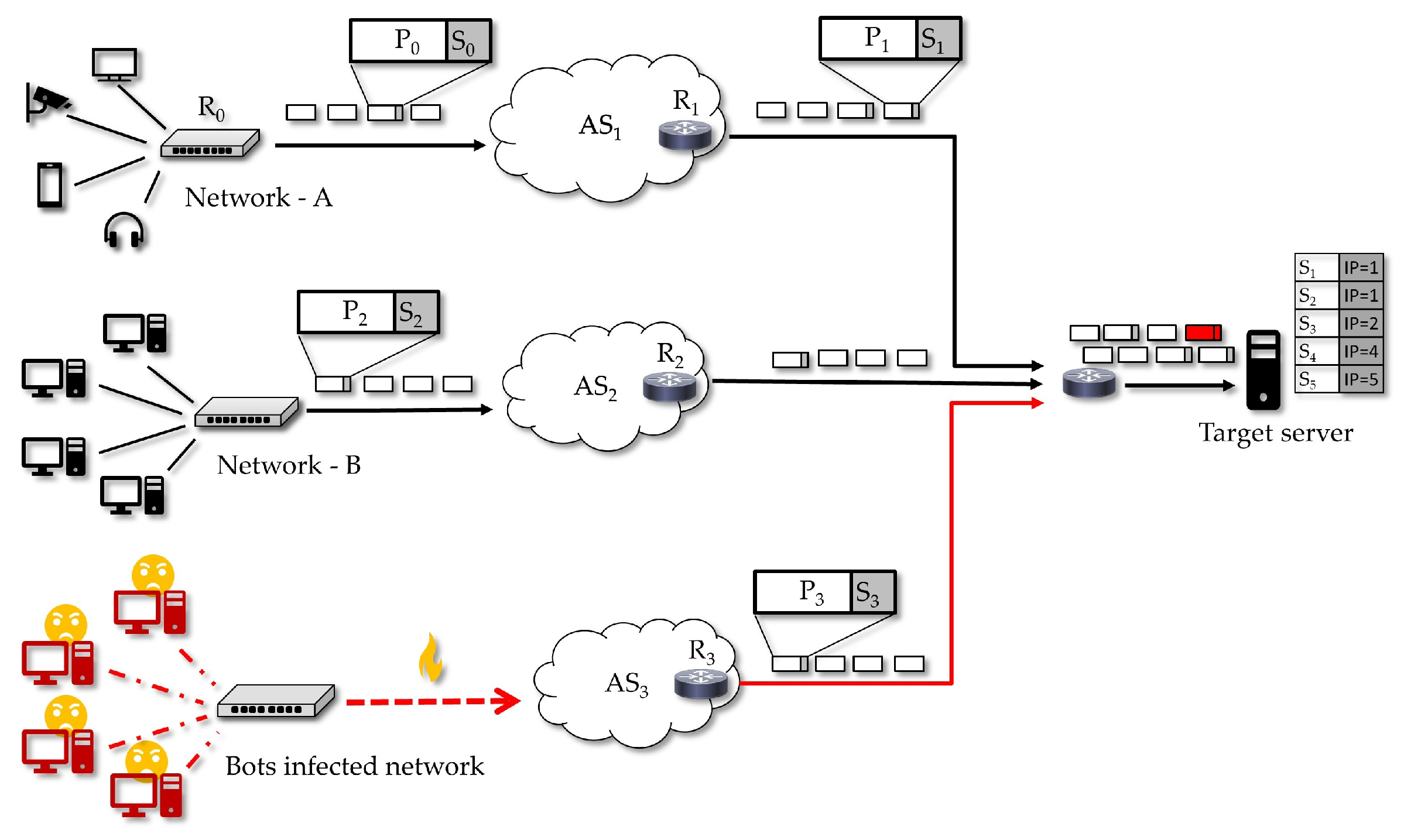
2.2. DoS Attacks in the IoT Scenario
2.3. Denial of Service Countermeasure Techniques
2.3.1. Packet Filtering
2.3.2. Cryptography, IPSec and VPN
2.3.3. Bloom Filter Forwarding
2.3.4. Cryptographic Puzzles
2.4. DoS Defenses in IoT Scenarios
2.5. Contribution and Overview
- Deployment in network and transport layers: Our solution can be fit in IP packets or in TCP segments. It can also be used as an authentication/identification tool in other protocols or services that establish a network flow.
- Agility: Current solutions are based on heavy cryptographic machinery in routers [15,16,37,38,39,40] or assign to the routers some filtering task with high computing overhead per packet [19,20,21,22,24]. Our proposal can provide on demand validation of a packet stream with very low computing complexity.
- Our proposal does not require modifying the network infrastructure: Apart from most known solutions from the literature, our scheme does not change the IP or TCP architecture.
- Low communications complexity: Our solution does not overburden the communications, and our protocol does not require any interaction among the parties and certification authority servers. In addition, it does not rely on key exchange protocols that demand a previous setup of confidential channels between parties. Our proposal adds merely a short signature in a fraction of the transmitted packets, a quantity defined as a security parameter, and therefore does not interfere in the traffic load.
- Accurate traceback to the sender: The proposed mechanism allows the identification of the sender, an attribute that can be used by the receiver to throw out malicious packet streams. When integrated to other security measures, this feature helps to detect ongoing attacks, allowing the receiver and other network elements to be alerted when a DoS attack is in course.
- Resilient to the interference of active adversaries: We give a formal proof of the resilience of our identification mechanism, showing how much resistant is the protocol face a malicious party controlling the network, and that can interfere in the messages used to establish the proposed scheme.
3. Cryptographic Tools and Assumptions
3.1. Digital Signature and Message Authentication
- A signer can efficiently create a signature of any document, and everyone can efficiently check the validity of a given signature.
- It is not feasible to forge a signature in the name of another user, that is, one cannot create a signature to a document that the other did not sign.
- Each of the communicating parties can efficiently create an authenticating tag to any message of its choice.
- Each communicating party can efficiently verify an authentication tag of a given message.
- It is infeasible to any external party (not in the communicating set) to create an authenticating tag.
- A key generation algorithm : the algorithm produces the respective secret and public keys, and it considers the security parameter k, where is the unary representation of the intended security level. is probabilistic in the sense that it considers some random value to process the keys generation.
- The signature algorithm : The signer, by owning both secret and public keys, can execute algorithm to produce the signature of a given message m. The signature algorithm can be probabilistic, making use of a random value as an input.
- The verification algorithm : The verifier takes the signature and the public key and checks if is a valid signature of the message m.
3.2. Proof of Security Paradigms
3.2.1. Simulation-Based Formulation
3.2.2. Proof by Reduction
3.2.3. Random Oracle Model
3.3. Secure Digital Signature Definitions
- Setup: The challenger calls the key-generation algorithm and gets keys pair and ; the adversary receives the public key .
- Queries: Adversary chooses n messages of his choice and requests the challenger the correspondent signatures , where .
- : Adversary wins the game when he eventually outputs a pair , where M was not asked in the previous step.
3.4. Undeniable Signature
3.5. Designated Verifier Signature—DVS
3.6. Strong Designated Verifier Signature —SDVS
4. Description of Our Scheme
4.1. Tagging Packets
4.2. Design Details and Parameters of the Proposed Scheme
- n: the size of the sequence of packets to be considered when a set of signatures must be inserted;
- : the total number of packets in which some signature will be inserted, i.e., for each n packets sequence, have a signature (valid or dummy), have no one;
- : the total number of valid signatures in a set of signatures inserted in an n-packet segment; and
- : the threshold number of n-packet segments without valid signatures, i.e., the receiver will expect at most received packets with no valid signature. Otherwise, the authentication status is switched off for that sender.
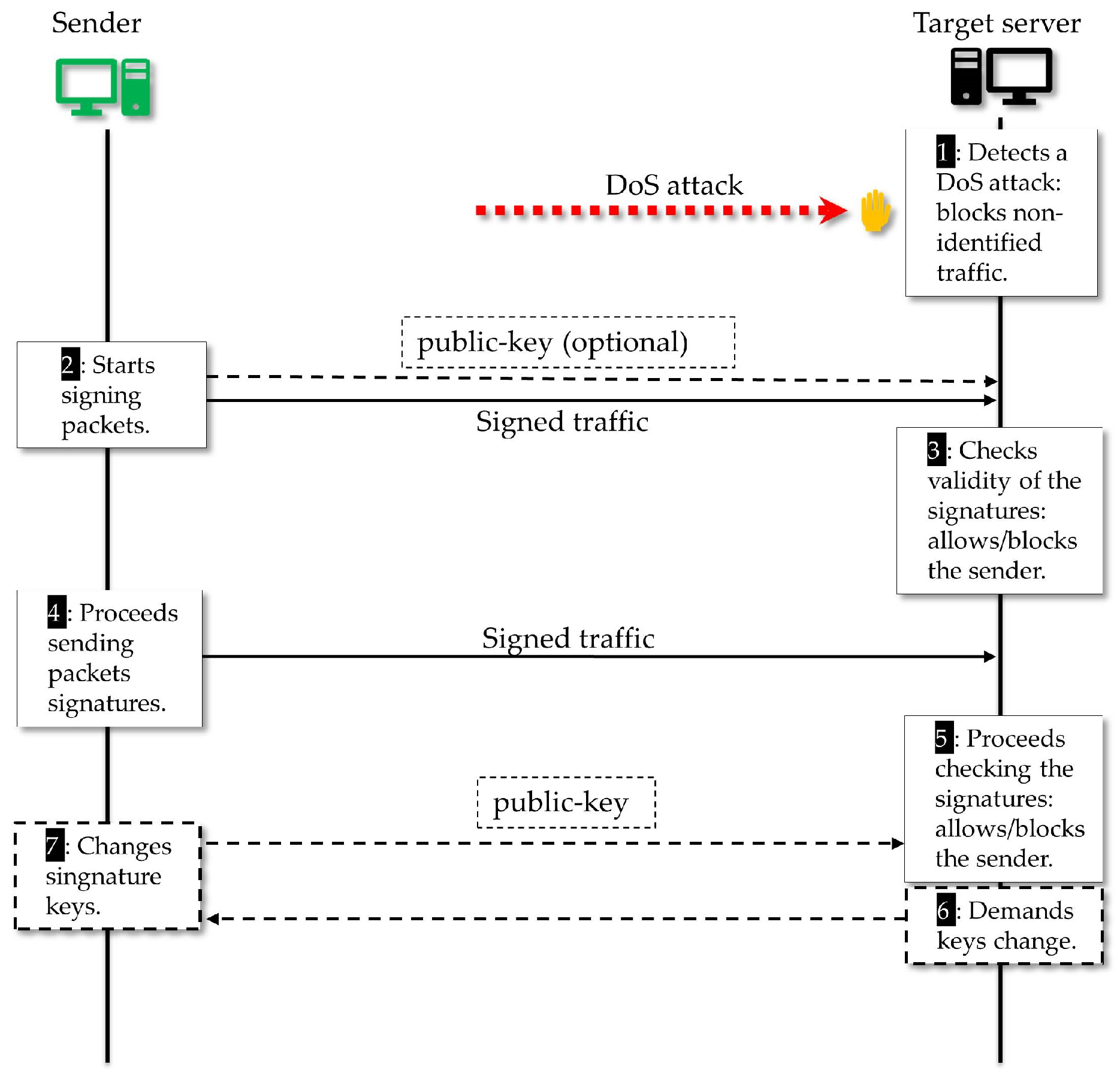
- Initialization: This phase starts with the parties openly agreeing about the security parameter and then calculating their respective secret and public keys using the key generation algorithm . The parties make their public keys openly accessible. That is described in the Algorithm 1.
Algorithm 1: Initialization begin
Alice gets
Bob gets
end - Signature: After that initial phase, the signer Alice, for a round that must be executed for every n packets to be transmitted, must randomly choose the subset among them, the ones in which she will fit some signature. In addition, inside this subset, she must at random choose the packets that will receive valid designated signature that can effectively be verified by the receiver Bob. The code in Algorithm 2 describes this signature process.
Algorithm 2: Alice (sender/signer). begin
for do
Generates dummy keys:
Randomly chooses:
Randomly chooses:
for do
Append()
end
for do
Append()
end
end
end - Signature verification: For each signed packet, Bob must verify if the inserted signature is valid and counts to find at least one valid signature in every sequence of received packets. thus, for Bob, if the source of the packet is not able to put a valid designated packet in such intervals, it is assumed that with a good probability (we will give a formal description of this in Section 6) the source is not authentic, or someone is trying to cheat. All this process is as the code in Algorithm 3.
Algorithm 3: Bob (receiver/verifier). begin
for every received signed packet: do
if is True then
update the threshold authentication
end
else
update the threshold authentication
end
end
end - Simulator: Similar to proofs in SDVS schemes in [61,62], here a simulator takes an important role in the proof of security of the protocol. In the security proof of the SDVS, the existence a simulator that allows mimicking the transcript of an authentic conversation is used as an argument of the hardness to anyone, except the designated verifier, to distinguish what is a valid designated signature and a random one. The simulator will drop some coins to get some randomness, take as inputs the public keys and the packet to be signed, and uses a simulator Simul of the underlying SDVS (because as the SDVS is supposed to be secure, it is required that a simulator exists for it) and with some scheme will return a signature that by the correspondent properties will give guarantees that the returned signature is indistinguishable from the valid one, except for the designated verifier. The simulator heuristic is described in Algorithm 4.
Algorithm 4: Simulator. Input: n packets:
begin
for do
end
end
5. Envisaged Application Scenarios
5.1. Application in a General Network Scenario
5.2. Application within an IoT Network Scenario
6. Resilience of Our Scheme in Face of DoS Attacks
6.1. Spoofing Attacks
6.2. Flooding Attacks
6.3. Denial of Capability Attacks
6.4. Content Forgery Attack
7. Finite State Analysis Regarding the Resilience of the Proposed Protocol
7.1. Finite State Automata
7.2. The Invariant Principle
7.3. Proving the Protocol Secure by Means of an FSA
- Describe the entire protocol regarding honest players and adversary behavior, showing a list of states of the running protocol and the transition rules.
- Model the adversary behavior, considering what he can do to drive the protocol to an insecure state.
- Demonstrate the resilience of the protocol showing how the honest parties run to keep the invariants true, despite the dishonest participants, thus presenting the probability of these adversaries violating that invariant.
7.3.1. The Protocol as a State Automata
7.3.2. The FSA States for the Players
| States for the receiver | |
| The initial state of the protocol, no transmission done yet; | |
| This represents the state of no authentication. If the sender has tried to send network communications to establish the authentication, it was not successful; | |
| The receiver recognizes the authentication signal sent by the sender and keeps this information in his internals variables; | |
| The receiver was waiting for a new authentication signal because there were i sequences of n packets with no valid signature; | |
| Threshold limit was reached without the valid recognizable communications from the sender that could keep the authenticated status on. | |
| States for the sender | |
| The initial state of the protocol, no transmission done yet; | |
| This represents the state of no authentication awareness. If the sender has tried to send network communications to be identified, it was not successful; | |
| Represents the states of being authenticated. | |
| Adversary states | |
| Initial state of the protocol, no transmission done yet; | |
| Represents the state of no authentication; | |
| Represents the states where the adversary reaches a successful authentication. | |
7.3.3. The Transition Rules for the Players
| Receiver rules | |
| = Then | |
| = Then | |
| = Then | |
| = Then | |
| = Then | |
| = Then | |
| Sender rules | |
| = Then | |
| = Then | |
| = Then | |
7.3.4. The Proposed Protocol Invariants
7.3.5. How Depends on the Sender Signing Mechanism
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and Other Botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Bertino, E.; Islam, N. Botnets and Internet of Things Security. Computer 2017, 50, 76–79. [Google Scholar] [CrossRef]
- Lyu, M.; Sherratt, D.; Sivanathan, A.; Gharakheili, H.H.; Radford, A.; Sivaraman, V. Quantifying the Reflective DDoS Attack Capability of Household IoT Devices. In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks, WiSec ’17, Boston, MA, USA, 18–20 July 2017; ACM: New York, NY, USA, 2017; pp. 46–51. [Google Scholar]
- Osanaiye, O.A.; Alfa, A.S.; Hancke, G.P. Denial of Service Defence for Resource Availability in Wireless Sensor Networks. IEEE Access 2018, 6, 6975–7004. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Int. Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. The Emperor’s New Password Creation Policies. In Proceedings of the European Symposium on Research in Computer Security ESORICS 2015, Vienna, Austria, 21–25 September 2015; pp. 456–477. [Google Scholar]
- Wang, D.; Zhang, Z.; Wang, P.; Yan, J.; Huang, X. Targeted Online Password Guessing: An Underestimated Threat. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, CCS ’16, Vienna, Austria, 24–28 October 2016; ACM: New York, NY, USA, 2016; pp. 1242–1254. [Google Scholar]
- Cheyenne, M.; Abigail, B. Passwords Used in the Biggest Ever Cyberattack Revealed—and ‘12345’ and ‘Password’ Were Top. Available online: http://www.dailymail.co.uk/sciencetech/article-3825740/ (accessed on 14 August 2018).
- US-CERT. Heightened DDoS Threat Posed by Mirai and Other Botnets—Alert TA16-288A. Available online: www.us-cert.gov/ncas/alerts/TA16-288A (accessed on 11 May 2018).
- Brachmann, M.; Keoh, S.L.; Morchon, O.G.; Kumar, S.S. End-to-End Transport Security in the IP-Based Internet of Things. In Proceedings of the 21st International Conference on Computer Communications and Networks (ICCCN), Munich, Germany, 30 July–2 August 2012; pp. 1–5. [Google Scholar]
- Ferreira, H.G.C.; Junior, R.T.S. Security analysis of a proposed internet of things middleware. Clust. Comput. 2017, 20, 651–660. [Google Scholar] [CrossRef]
- Kalkan, K.; Gür, G.; Alagöz, F. Filtering-Based Defense Mechanisms Against DDoS Attacks: A Survey. IEEE Syst. J. 2017, 11, 2761–2773. [Google Scholar] [CrossRef]
- Bonguet, A.; Bellaiche, M. A Survey of Denial-of-Service and Distributed Denial of Service Attacks and Defenses in Cloud Computing. Future Internet 2017, 9, 43. [Google Scholar] [CrossRef]
- Zargar, S.T.; Joshi, J.; Tipper, D. A Survey of Defense Mechanisms Against Distributed Denial of Service (DDoS) Flooding Attacks. IEEE Commun. Surv. Tutor. 2013, 15, 2046–2069. [Google Scholar] [CrossRef] [Green Version]
- Andersen, D.G.; Balakrishnan, H.; Feamster, N.; Koponen, T.; Moon, D.; Shenker, S. Accountable Internet Protocol (AIP). In Proceedings of the ACM SIGCOMM 2008, Seattle, WA, USA, 17–22 August 2008; pp. 339–350. [Google Scholar]
- Haeberlen, A.; Rodrigues, R.; Gummadi, K.; Druschel, P. Pretty Good Packet Authentication. In Proceedings of the Fourth Conference on Hot topics in System Dependability (HotDep’08), San Diego, CA, USA, 8–10 December 2008. [Google Scholar]
- Ferguson, P.; Senie, D. Network Ingress Filtering: Defeating Denial of Service Attacks that Employ IP Source Address Spoofing. Available online: https://tools.ietf.org/html/rfc2827 (accessed on 21 October 2017).
- Kent, S.; Atkinson, R. Security Architecture for the Internet Protocol. Available online: https://tools.ietf.org/html/rfc1825 (accessed on 10 November 2017).
- Abdelsayed, S.; Glimsholt, D.; Leckie, C.; Ryan, S.; Shami, S. An Efficient Filter for Denial–of–Service Bandwidth Attacks. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM ’03), San Francisco, CA, USA, 1–5 December 2003; pp. 1353–1357. [Google Scholar]
- Mirkovic, J.; Prier, G.; Reihe, P. Source–End DDoS Defense. In Proceedings of the 2nd IEEE International Symposium on Network Computing and Applications, Cambridge, MA, USA, 18 April 2003; pp. 171–178. [Google Scholar]
- Song, D.; Perrig, A. Advanced and Authenticated Marking Schemes for IP Traceback. In Proceedings of the Twentieth Annual Joint Conference of the IEEE Computer and Communications Societies (INFOCOM 2001), Anchorage, AK, USA, 22–26 April 2001; pp. 878–886. [Google Scholar]
- Parno, B.; Wendlandt, D.; Shi, E.; Perrig, A.; Maggs, B.; Hu, Y. Portcullis: Protecting Connection Setup from Denial–of–Capability Attacks. In Proceedings of the 2007 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications (SIGCOMM ’07), New York, NY, USA, 27–31 August 2007; pp. 289–300. [Google Scholar]
- Pimenta Rodrigues, G.A.; de Oliveira Albuquerque, R.; Gomes de Deus, F.E.; de Sousa, R.T., Jr.; de Oliveira Júnior, G.A.; García Villalba, L.J.; Kim, T.-H. Cybersecurity and Network Forensics: Analysis of Malicious Traffic towards a Honeynet with Deep Packet Inspection. Appl. Sci. 2017, 7, 1082. [Google Scholar] [CrossRef]
- Peng, T.; Leckie, C.; Ramamohanarao, K. Protection from Distributed Denial of Service Attacks Using History–Based IP Filtering. In Proceedings of the IEEE International Conference on Communications (ICC’03), Anchorage, AK, USA, 11–15 May 2003; pp. 482–486. [Google Scholar]
- Yaar, A.; Perrig, A.; Song, D. Pi: A Path Identification Mechanism to Defend against DDoS Attacks. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 11–14 May 2003. [Google Scholar]
- Bellovin, S. Problem Areas for the IP Security Protocols. In Proceedings of the Sixth Usenix Unix Security Symposium, San Jose, CA, USA, 22–25 July 1996; pp. 1–16. [Google Scholar]
- Paterson, K.G.; Yau, A.K.L. Cryptography in Theory and Practice: The Case of Encryption in IPsec. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques (Eurocrypt’06), St. Petersburg, Russia, 28 May–1 June 2006; pp. 12–29. [Google Scholar]
- Bellare, M.; Namprempre, C. Authenticated Encryption: Relations among Notions and Analysis of the Generic Composition Paradigm. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security (ASIACRYPT 2000), Kyoto, Japan, 3–7 December 2000; pp. 531–545. [Google Scholar]
- Bloom, B.H. Space/Time Trade–offs in Hash Coding with Allowable Errors. Commun. ACM 1970, 13, 422–426. [Google Scholar] [CrossRef]
- Antikainen, M.; Aura, T.; Särelä, M. Denial–of–Service Attacks in Bloom–Filter–Based Forwarding. Cluster 2014, 22, 1463–1476. [Google Scholar] [CrossRef]
- Mullin, J.K. A Second Look at Bloom Filters. Commun. ACM 1983, 26, 570–571. [Google Scholar] [CrossRef]
- Qian, J.; Zhu, Q.; Wang, Y. Bloom Filter Based Associative Deletion. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1986–1998. [Google Scholar] [CrossRef]
- Kirsch, A.; Mitzenmacher, M. Less Hashing, Same Performance: Building a Better Bloom Filter. In Proceedings of the European Symposium on Algorithms, Zurich, Switzerland, 11–13 September 2006; pp. 456–467. [Google Scholar]
- Rottenstreich, O.; Keslassy, I. The Bloom Paradox: When Not to Use a Bloom Filter. IEEE ACM Trans. Netw. 2014, 23, 703–716. [Google Scholar] [CrossRef]
- Merkle, R.C. Secure communications over insecure channels. Commun. ACM 1978, 21, 294–299. [Google Scholar] [CrossRef] [Green Version]
- Dwork, C.; Naor, M. Pricing via Processing or Combatting Junk Mail. In Proceedings of the 12th Annual International Cryptology Conference on Advances in Cryptology (CRYPTO’92), Santa Barbara, CA, USA, 16–20 August 1992; pp. 139–147. [Google Scholar]
- Juels, A.; Brainard, J. Client Puzzles: A Cryptographic Defense Against Connection Depletion. In Proceedings of the Network and Distributed System Security Symposium (NDSS’99), San Diego, CA, USA, 24–27 February 1999; pp. 151–165. [Google Scholar]
- Dean, D.; Stubblefield, A. Using Client Puzzles to Protect TLS. In Proceedings of the 10th Conference on USENIX Security Symposium (SSYM’01), Washington, DC, USA, 13–17 August 2001. [Google Scholar]
- Aura, T.; Nikander, P.; Leiwo, J. DoS-Resistant Authentication with Client Puzzles. In Proceedings of the Security Protocols: 8th International Workshop, Cambridge, UK, 3–5 April 2001; pp. 170–177. [Google Scholar]
- Wang, X.; Reiter, M. Defending Against Denial-of-Service Attacks with Puzzle Auctions. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 11–14 May 2003; pp. 78–93. [Google Scholar]
- Feng, W.; Kaiser, E.; Luu, A. The Design and Implementation of Network Puzzles. In Proceedings of the IEEE 24th Annual Joint Conference of the IEEE Computer and Communications Societies, Miami, FL, USA, 13–17 March 2005; pp. 2372–2382. [Google Scholar]
- Feng, W. The Case for TCP/IP Puzzles. In Proceedings of the ACM SIGCOMM workshop on Future directions in Network Architecture, Karlsruhe, Germany, 25–27 August 2003; pp. 322–327. [Google Scholar] [CrossRef]
- Gendreau, A.A.; Moorman, M. Survey of Intrusion Detection Systems towards an End to End Secure Internet of Things. In Proceedings of the IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria, 22–24 August 2016; pp. 84–90. [Google Scholar]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Pa, Y.M.P.; Suzuki, S.; Yoshioka, K.; Matsumoto, T.; Kasama, T.; Rossow, C. IoTPOT: A Novel Honeypot for Revealing Current IoT Threats. J. Inf. Process. 2016, 24, 522–533. [Google Scholar] [CrossRef] [Green Version]
- Gupta, N.; Naik, V.; Sengupta, S. A Firewall for Internet of Things. In Proceedings of the 9th International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 4–8 January 2017; pp. 411–412. [Google Scholar]
- Jang, S.; Lim, D.; Kang, J.; Joe, I. An Efficient Device Authentication Protocol Without Certification Authority for Internet of Things. Wirel. Pers. Commun. 2016, 91, 1681–1695. [Google Scholar] [CrossRef]
- Porambage, P.; Schmitt, C.; Kumar, P.; Gurtov, A.; Ylianttila, M. Two-Phase Authentication Protocol for Wireless Sensor Networks in Distributed IoT Applications. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 2728–2733. [Google Scholar]
- Salmon, H.M.; De Farias, C.M.; Loureiro, P.; Pirmez, L.; Rossetto, S.; Rodrigues, P.H.; Pirmez, R.; Delicato, F.C.; da Costa Carmo, L.F. Intrusion Detection System for Wireless Sensor Networks Using Danger Theory Immune-Inspired Techniques. Int. J. Wirel. Inf. Netw. 2013, 20, 39–66. [Google Scholar] [CrossRef]
- Argyraki, K.; Cheriton, D.R. Network Capabilities: The Good, the Bad and the Ugly. In Proceedings of the Fourth Workshop on Hot Topics in Networks (HotNets-IV), College Park, MD, USA, 14–15 November 2005; ACM Press: Bel Air, MD, USA, 2005. [Google Scholar]
- Argyraki, K.; Cheriton, D.R. Scalable Network-Layer Defense Against Internet Bandwidth-Flooding Attacks. IEEE/ACM Trans. Netw. 2009, 17, 1284–1297. [Google Scholar] [CrossRef] [Green Version]
- Goldreich, O. Foundations of Cryptography: Volume 2, Basic Applications; Cambridge University Press: New York, NY, USA, 2004; ISBN 052111991X. [Google Scholar]
- Katz, J.; Lindell, Y. Introduction to Modern Cryptography, 1st ed.; Chapman & Hall/CRC: Boca Raton, FL, USA, 2007; ISBN 9781466570269. [Google Scholar]
- Lindell, Y. How to Simulate It—A Tutorial on the Simulation Proof Technique. Available online: https://eprint.iacr.org/2016/046 (accessed on 8 February 2018).
- Bellare, M.; Rogaway, P. Random Oracles are Practical: A Paradigm for Designing Efficient Protocols. In Proceedings of the ACM Conference on Computer and Communications Security (CCS’93), Fairfax, VA, USA, 3–5 November 1993; pp. 62–73. [Google Scholar]
- Koblitz, N.; Menezes, A.J. The random oracle model: A twenty–year retrospective. Des. Codes Cryptogr. 2015, 77, 587–610. [Google Scholar] [CrossRef]
- Pointcheval, D.; Stern, J. Security Arguments for Digital Signatures and Blind Signatures. J. Cryptol. 2000, 13, 361–396. [Google Scholar] [CrossRef] [Green Version]
- Pointcheval, D.; Stern, J. Provably Secure Blind Signature Schemes. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security (ASIACRYPT’96), Kyongju, Korea, 3–7 November 1996; pp. 252–265. [Google Scholar]
- Pointcheval, D.; Stern, J. Security Proofs for Signature Schemes. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques (Eurocrypt ’96), Saragossa, Spain, 12–16 May 1996; pp. 387–398. [Google Scholar]
- Chaum, D.; Antwerpen, H.V. Undeniable Signatures. In Proceedings of the Conference on the Theory and Application of Cryptology (CRYPTO’89), Santa Barbara, CA, USA, 20–24 August 1989; pp. 212–216. [Google Scholar]
- Jakobsson, M.; Sako, K.; Impagliazzo, R. Designated Verifier Proofs and Their Applications. In Proceedings of the 15th Annual International Conference on Theory and Application of Cryptographic Techniques (EUROCRYPT’96), Saragossa, Spain, 12–16 May 1996; pp. 143–154. [Google Scholar]
- Saeednia, S.; Kremer, S.; Markowitch, O. An Efficient Strong Designated Verifier Signature Scheme. In Proceedings of the International Conference on Information Security and Cryptology (ICISC 2003), Seoul, Korea, 27–28 November 2003; pp. 40–54. [Google Scholar]
- Jokela, P.; Zahemszky, A.; Rothenberg, C.E.; Arianfar, S.; Nikander, P. LIPSIN: Line speed publish/subscribe inter–networking. In Proceedings of the ACM SIGCOMM 2009 Conference on Data Communication (SIGCOMM ’09), Barcelona, Spain, 16–21 August 2009; pp. 195–206. [Google Scholar]
- Rothenberg, C.E.; Jokela, P.; Nikander, P.; Sarela, M.S.; Ylitalo, J. Self-Routing Denial-of-Service Resistant Capabilities Using In-Packet Bloom Filters. In Proceedings of the 2009 European Conference on Computer Network Defense (EC2ND ’09), Milan, Italy, 9–10 November 2009; pp. 46–51. [Google Scholar]
- oneM2M Partners. TS-0001 Functional Architecture (V2.18.1). Available online: http://www.onem2m.org/component/rsfiles/ (accessed on 9 July 2018).
- oneM2M Partners. TS-0003 Security Solutions (V2.12.1). Available online: http://www.onem2m.org/component/rsfiles/ (accessed on 9 July 2018).
- Angrishi, K. Turning Internet of Things (IoT) into Internet of Vulnerabilities (IoV): IoT Botnets. arXiv, 2017; arXiv:1702.03681v1. [Google Scholar]
- Puttini, R.S.; Percher, J.-M.; Me, L.; Sousa, R.T., Jr. A Fully Distributed IDS for MANET. In Proceedings of the Ninth International Symposium on Computers and Communications (ISCC 2004), Alexandria, Egypt, 28 June–1 July 2004; pp. 331–338. [Google Scholar]
- Paxson, V. End-to-End Internet Packet Dynamics. In Proceedings of the ACM SIGCOMM ’97 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communication, Cannes, France, 14–18 September 1997; pp. 139–152. [Google Scholar] [CrossRef]
- Shmatikov, V.; Stern, U. Efficient Finite-State Analysis for Large Security Protocols. In Proceedings of the 11th IEEE Computer Security Foundations Workshop, Rockport, MA, USA, 11 June 1998; pp. 106–115. [Google Scholar]
- Shmatikov, V.; Mitchell, J.C. Finite-state analysis of two contract signing protocols. Theor. Comput. Sci. 2002, 283, 419–450. [Google Scholar] [CrossRef]
- Mitchell, J.C.; Shmatikov, V.; Stern, U. Finite State Analysis of SSL 3.0. In Proceedings of the 7th conference on USENIX Security Symposium (SSYM’98), San Antonio, TX, USA, 26–29 January 1998; pp. 201–215. [Google Scholar]
- Bolignano, D. Towards a Mechanization of Cryptographic Protocol Verification. In Proceedings of the International Conference on Computer Aided Verification, Haifa, Israel, 22–25 June 1997; pp. 131–142. [Google Scholar]
- Mitchell, J.C.; Mitchell, M.; Stern, U. Automated Analysis of Cryptographic Protocols Using Murϕ. In Proceedings of the IEEE Symposium on Security and Privacy, Oakland, CA, USA, 4–7 May 1997; pp. 141–151. [Google Scholar]
- Sipser, M. Introduction to the Theory of Computation, 2nd ed.; International Thomson Publishing: Boston, MA, USA, 1996. [Google Scholar]














| Old State | Symbol | New State |
|---|---|---|
| ‘c’ | ||
| ‘c’ | ||
| ‘c’ | ||
| ‘c’ | ||
| ‘c’ | ||
| ‘c’ |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
De Almeida, M.P.; De Sousa Júnior, R.T.; García Villalba, L.J.; Kim, T.-H. New DoS Defense Method Based on Strong Designated Verifier Signatures. Sensors 2018, 18, 2813. https://doi.org/10.3390/s18092813
De Almeida MP, De Sousa Júnior RT, García Villalba LJ, Kim T-H. New DoS Defense Method Based on Strong Designated Verifier Signatures. Sensors. 2018; 18(9):2813. https://doi.org/10.3390/s18092813
Chicago/Turabian StyleDe Almeida, Marcone Pereira, Rafael Timóteo De Sousa Júnior, Luis Javier García Villalba, and Tai-Hoon Kim. 2018. "New DoS Defense Method Based on Strong Designated Verifier Signatures" Sensors 18, no. 9: 2813. https://doi.org/10.3390/s18092813
APA StyleDe Almeida, M. P., De Sousa Júnior, R. T., García Villalba, L. J., & Kim, T.-H. (2018). New DoS Defense Method Based on Strong Designated Verifier Signatures. Sensors, 18(9), 2813. https://doi.org/10.3390/s18092813








