A Robust Quasi-Quantum Walks-based Steganography Protocol for Secure Transmission of Images on Cloud-based E-healthcare Platforms
Abstract
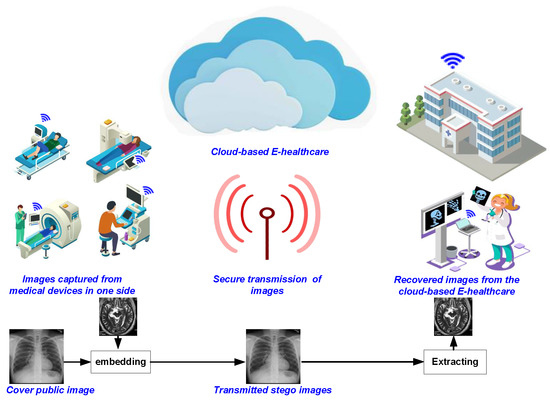
:1. Introduction
2. IoT-Based Healthcare and Quantum Walks
2.1. Framework for Secure Transmission of Images on Cloud-Based E-Healthcare Platforms
2.2. Quantum Walks
3. Proposed Image Steganography Scheme
| Algorithm 1: Embedding process |
| Input: Carrier image (CIm), Confidential image (SIm), and Initial key parameters () |
| Output: Stego image (Stgo) |
| P← CAQWs () // Operate CAQWs using initial key parameters |
| [h, w, c] ← size (CIm) // Obtain the size of the carrier image |
| D← resize (P, [h, w × c ]) // Resize the matrix P to the dimension of the cover image |
| E← order (D) // Order the elements of D in decreasing order |
| K= index (D, E) // Obtain the index of each element of D in E |
| ESIm ← expand (SIm) // Expand the 8-bit and dimensional confidential image SIm to a 2-bit image of h × w dimension. |
| // Transform the expanded secret image ESIm and the carrier image CIm into vectors |
| SVec← reshape (ESIm, 1, h × w × c) |
| CVec← reshape (CIm, 1, h × w × c) |
| // Embedding process |
| for i←1 to h × w × c |
| StgoVec(k(i))←Replace 2LSBs of CVec(k(i)) with 2bits of SVec(i); |
| end |
| // Transform the vector StgoVec into an image |
| Stgo←reshape (StgoVec, h, w, c) |
4. Simulation-Based Experiments
4.1. Image Quality Analysis
4.1.1. Peak Signal to Noise Ratio (PSNR)
4.1.2. Structural Similarity Index Metric (SSIM)
4.1.3. Universal Image Quality (UIQ)
4.1.4. Normalised Cross Correlation (NCC)
4.1.5. Normalised Absolute Error (NAE)
4.1.6. Image Fidelity (IF)
4.1.7. Average Difference (AD)
4.1.8. Maximum Difference (MD)
4.1.9. Structural Content (SC)
4.2. Data Loss Analyses
4.3. Payload Capacity
4.4. Security Analysis
4.5. Discussion
5. Concluding Remarks
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Zhang, C.; Zhu, L.; Xu, C.; Lu, R. PPDP: An efficient and privacy-preserving disease prediction scheme in cloud-based e-Healthcare system. Futur. Gener. Comput. Syst. 2018, 79, 16–25. [Google Scholar] [CrossRef]
- Al Omar, A.; Alam Bhuiyan, Z.; Basu, A.; Kiyomoto, S.; Rahman, M.S. Privacy-friendly platform for healthcare data in cloud based on blockchain environment. Futur. Gener. Comput. Syst. 2019, 95, 511–521. [Google Scholar] [CrossRef]
- Abd-El-Atty, B.; El-Latif, A.A.A.; E Venegas-Andraca, S. An encryption protocol for NEQR images based on one-particle quantum walks on a circle. Quantum Inf. Process. 2019, 18, 272. [Google Scholar] [CrossRef]
- El-Latif, A.A.A.; Abd-El-Atty, B.; Abou-Nassar, E.M.; E Venegas-Andraca, S. Controlled alternate quantum walks-based privacy preserving healthcare images in Internet of Things. Opt. Laser Technol. 2020, 124, 105942. [Google Scholar] [CrossRef]
- Miyake, S.; Nakamae, K. A quantum watermarking scheme using simple and small-scale quantum circuits. Quantum Inf. Process. 2016, 15, 1849–1864. [Google Scholar] [CrossRef]
- Peng, J.; Abd-El-Atty, B.; Khalifa, H.S.; El-Latif, A.A.A. Image watermarking algorithm based on quaternion and chaotic Lorenz system. In Proceedings of the Eleventh International Conference on Digital Image Processing (ICDIP 2019), Guangzhou, China, 10–13 May 2019; International Society for Optics and Photonics: Bellingham, WA, USA, 2019; Volume 11179, p. 111790W. [Google Scholar]
- Muhammad, K.; Sajjad, M.; Mehmood, I.; Rho, S.; Baik, S. Image steganography using uncorrelated color space and its application for security of visual contents in online social networks. Futur. Gener. Comput. Syst. 2018, 86, 951–960. [Google Scholar] [CrossRef]
- Tao, J.; Li, S.; Zhang, X.; Wang, Z. Towards Robust Image Steganography. IEEE Trans. Circuits Syst. Video Technol. 2018, 29, 594–600. [Google Scholar] [CrossRef]
- Zhang, X.; Peng, F.; Long, M. Robust Coverless Image Steganography Based on DCT and LDA Topic Classification. IEEE Trans. Multimed. 2018, 20, 3223–3238. [Google Scholar] [CrossRef]
- Sharma, V.K.; Srivastava, D.K.; Mathur, P.; Shrivastava, D. Efficient image steganography using graph signal processing. IET Image Process. 2018, 12, 1065–1071. [Google Scholar] [CrossRef]
- Sharif, A.; Mollaeefar, M.; Nazari, M. A novel method for digital image steganography based on a new three-dimensional chaotic map. Multimed. Tools Appl. 2016, 76, 7849–7867. [Google Scholar] [CrossRef]
- El-Latif, A.A.A.; Abd-El-Atty, B.; Venegas-Andraca, S.E. A novel image steganography technique based on quantum substitution boxes. Opt. Laser Technol. 2019, 116, 92–102. [Google Scholar] [CrossRef]
- Peng, J.; Abd-El-Atty, B.; Khalifa, H.S.; El-Latif, A.A.A. Image steganography algorithm based on key matrix generated by quantum walks. In Proceedings of the Eleventh International Conference on Digital Image Processing (ICDIP 2019), Guangzhou, China, 10–13 May 2019; International Society for Optics and Photonics: Bellingham, WA, USA, 2019; Volume 11179, p. 1117905. [Google Scholar]
- Li, P.; Liu, X. A novel quantum steganography scheme for color images. Int. J. Quantum Inf. 2018, 16, 1850020. [Google Scholar] [CrossRef]
- Zhou, R.-G.; Luo, J.; Liu, X.; Zhu, C.; Wei, L.; Zhang, X. A Novel Quantum Image Steganography Scheme Based on LSB. Int. J. Theor. Phys. 2018, 57, 1848–1863. [Google Scholar] [CrossRef]
- Hussain, M.; Wahab, A.W.A.; Bin Idris, Y.I.; Ho, A.T.; Jung, K.-H. Image steganography in spatial domain: A survey. Signal Process. Image Commun. 2018, 65, 46–66. [Google Scholar] [CrossRef]
- Li, D.; Zhang, J.; Guo, F.-Z.; Huang, W.; Wen, Q.-Y.; Chen, H. Discrete-time interacting quantum walks and quantum Hash schemes. Quantum Inf. Process. 2012, 12, 1501–1513. [Google Scholar] [CrossRef]
- Yang, Y.-G.; Xu, P.; Yang, R.; Zhou, Y.-H.; Shi, W.-M. Quantum Hash function and its application to privacy amplification in quantum key distribution, pseudo-random number generation and image encryption. Sci. Rep. 2016, 6, 19788. [Google Scholar] [CrossRef] [Green Version]
- Iliyasu, A.M. Roadmap to Talking Quantum Movies: A Contingent Inquiry. IEEE Access 2018, 7, 23864–23913. [Google Scholar] [CrossRef]
- Iliyasu, A.M.; Le, P.Q.; Dong, F.; Hirota, K. Restricted geometric transformations and their applications for quantum image watermarking and authentication. In Proceedings of the 10th Asian Conference on Quantum Information Science (AQIS 2010), Tokyo, Japan, 18–19 August 2010; pp. 212–214. [Google Scholar]
- El-Latif, A.A.A.; Abd-El-Atty, B.; Amin, M.; Iliyasu, A.M. Quantum-inspired cascaded discrete-time quantum walks with induced chaotic dynamics and cryptographic applications. Sci. Rep. 2020, 10, 1–16. [Google Scholar] [CrossRef]
- Li, D.; Yang, Y.-G.; Bi, J.-L.; Yuan, J.-B.; Xu, J. Controlled Alternate Quantum Walks based Quantum Hash Function. Sci. Rep. 2018, 8, 225. [Google Scholar] [CrossRef] [Green Version]
- El-Latif, A.A.A.; Abd-El-Atty, B.; Hossain, M.S.; Rahman, A.; Alamri, A.; Gupta, B.B. Efficient Quantum Information Hiding for Remote Medical Image Sharing. IEEE Access 2018, 6, 21075–21083. [Google Scholar] [CrossRef]
- Zhou, L.; Wang, Q.; Sun, X.; Kulicki, P.; Castiglione, A. Quantum technique for access control in cloud computing II: Encryption and key distribution. J. Netw. Comput. Appl. 2018, 103, 178–184. [Google Scholar] [CrossRef]
- Varghese, B.; Buyya, R. Next generation cloud computing: New trends and research directions. Futur. Gener. Comput. Syst. 2018, 79, 849–861. [Google Scholar] [CrossRef] [Green Version]
- Chen, D.; Zhao, H. Data Security and Privacy Protection Issues in Cloud Computing. In Proceedings of the 2012 International Conference on Computer Science and Electronics Engineering, Zhejiang, China, 23–25 March 2012; Volume 1, pp. 647–651. [Google Scholar]
- El-Latif, A.A.A.; Abd-El-Atty, B.; E Venegas-Andraca, S.; Mazurczyk, W. Efficient quantum-based security protocols for information sharing and data protection in 5G networks. Futur. Gener. Comput. Syst. 2019, 100, 893–906. [Google Scholar] [CrossRef]
- Yan, X.; Wang, S.; El-Latif, A.A.A.; Niu, X. New approaches for efficient information hiding-based secret image sharing schemes. Signal Image Video Process. 2013, 9, 499–510. [Google Scholar] [CrossRef]
- MedPix. Available online: https://medpix.nlm.nih.gov/home (accessed on 30 May 2020).
- Salama, A.S.; Mokhtar, M.A.; Tayel, M.B. A Triple-Layer Encryption-Based Watermarking Technique for Improving Security of Medical Images. J. Med. Imaging Health Inform. 2019, 9, 610–619. [Google Scholar] [CrossRef]
- Iliyasu, A.M.; Yan, F.; Fatichah, C. A Special Section on Hybrid Intelligent Systems and Applications in Medical Imaging and Health Informatics. J. Med. Imaging Health Inform. 2019, 9, 599–601. [Google Scholar] [CrossRef]
- Higham, N. Accuracy and Stability of Numerical Algorithms (PDF), 2nd ed.; SIAM: Philadelphia, PA, USA, 2002. [Google Scholar]













| Mechanism | Description | Capacity | Requirements for Extraction of Secret Image from Stego Image |
|---|---|---|---|
| Proposed | Designed as a quasi-quantum-inspired scheme where a secret colour (or greyscale) image is embedded onto a cover colour (or greyscale) image based on CAQWs. The role of CAQWs is used to determine the location of pixels in the carrier image to suffuse secret bits. | 2-bit/8-bit | Control parameters for running CAQWs |
| Miyake et al. [5] | Simulation-based circuit model quantum image processing (QIP) [20] implementation of quantum greyscale image watermarking based on SWAP and CNOT gates. | 2-bit/8-bit | Original carrier image and the key used in the scrambling process. |
| El-Latif et al. [12] | Simulation-based QIP protocol where a secret colour (or greyscale) image is embedded onto a cover colour (or greyscale) image based on quantum substitution boxes. The construction of quantum substitution boxes is based on 1D 2-Particle QWs, which requires more resources than CAQWs. | 2-bit/8-bit | Quantum substitution boxes |
| Peng et al. [13] | Simulation-based implementation of 1D 2-Particle quantum walks to embed a secret greyscale image onto a cover colour image. 1D 2-Particle QWs is used to select one channel from (RGB) of the cover image to implant the secret bits. | 2-bit/24-bit | Control parameters for running 1D 2-Particle QWs. |
| Li et al. [14] | A QIP protocol where a greyscale image is embedded onto a quantum colour image based on quantum Gray code. | 2-bit/24-bit | Quantum Gray code |
| Zhou et al. [15] | A QIP scheme where greyscale images are embedded onto greyscale images based on Bit-plane, Swap gates, and Arnold image scrambling. | 0.5-bit/8-bit | Original cover image and three types of keys (K, K1, and K2) each the size of the secret message. |
| El-Latif et al. [23] | A QIP data hiding mechanism suffusing greyscale images onto greyscale images based on the logistic chaotic map. | 2-bit/8-bit | Control parameters for running the logistic map as well the key matrix generated from the embedding process whose size is the same size as the secret message. |
| Measurement | Cover Image | Secret Image | ||||
|---|---|---|---|---|---|---|
| MDG01 | MDG02 | MDG03 | MDG04 | MDG05 | ||
| PSNR | MDG01 | - | 44.3009 | 44.0536 | 44.3985 | 44.3903 |
| MDG02 | 44.1068 | - | 44.0039 | 44.4310 | 44.4251 | |
| MDG03 | 44.1238 | 44.3526 | - | 44.4266 | 44.4110 | |
| MDG04 | 44.1346 | 44.3555 | 44.0179 | - | 44.4008 | |
| MDG05 | 44.1059 | 44.3497 | 44.0078 | 44.4238 | - | |
| SSIM | MDG01 | - | 0.9331 | 0.9318 | 0.9338 | 0.9338 |
| MDG02 | 0.9470 | - | 0.9471 | 0.9491 | 0.9491 | |
| MDG03 | 0.9556 | 0.9574 | - | 0.9572 | 0.9573 | |
| MDG04 | 0.9594 | 0.9603 | 0.9593 | - | 0.9607 | |
| MDG05 | 0.9674 | 0.9684 | 0.9675 | 0.9689 | - | |
| UIQ | MDG01 | - | 0.9299 | 0.9288 | 0.9306 | 0.9306 |
| MDG02 | 0.9463 | - | 0.9464 | 0.9484 | 0.9484 | |
| MDG03 | 0.9548 | 0.9566 | - | 0.9564 | 0.9566 | |
| MDG04 | 0.9588 | 0.9596 | 0.9587 | - | 0.9601 | |
| MDG05 | 0.9673 | 0.9683 | 0.9673 | 0.9688 | - | |
| NCC | MDG01 | - | 0.9991 | 0.9999 | 0.9996 | 0.9997 |
| MDG02 | 0.9999 | - | 0.9999 | 0.9999 | 0.9999 | |
| MDG03 | 0.9999 | 0.9992 | - | 0.9997 | 0.9997 | |
| MDG04 | 0.9999 | 0.9991 | 0.9999 | - | 0.9999 | |
| MDG05 | 0.9999 | 0.9993 | 0.9999 | 0.9998 | - | |
| NAE | MDG01 | - | 0.0074 | 0.0076 | 0.0073 | 0.0073 |
| MDG02 | 0.0111 | - | 0.0113 | 0.0107 | 0.0107 | |
| MDG03 | 0.0061 | 0.0059 | - | 0.0059 | 0.0059 | |
| MDG04 | 0.0109 | 0.0106 | 0.0110 | - | 0.0106 | |
| MDG05 | 0.0099 | 0.0096 | 0.0100 | 0.0096 | - | |
| IF | MDG01 | - | 0.9999 | 0.9999 | 0.9999 | 0.9999 |
| MDG02 | 0.9998 | - | 0.9998 | 0.9998 | 0.9998 | |
| MDG03 | 0.9999 | 0.9999 | - | 0.9999 | 0.9999 | |
| MDG04 | 0.9998 | 0.9998 | 0.9998 | - | 0.9998 | |
| MDG05 | 0.9998 | 0.9999 | 0.9998 | 0.9999 | - | |
| AD | MDG01 | - | 0.1220 | −0.3018 | 0.0705 | 0.0362 |
| MDG02 | −0.2475 | - | −0.3654 | 0.0069 | −0.0274 | |
| MDG03 | −0.2187 | 0.0872 | - | 0.0357 | 0.0014 | |
| MDG04 | −0.2315 | 0.0744 | −0.3494 | - | −0.0114 | |
| MDG05 | −0.2387 | 0.0672 | −0.3566 | 0.0157 | - | |
| MD | MDG01 | - | 3 | 3 | 3 | 3 |
| MDG02 | 3 | - | 3 | 3 | 3 | |
| MDG03 | 3 | 3 | - | 3 | 3 | |
| MDG04 | 3 | 3 | 3 | - | 3 | |
| MDG05 | 3 | 3 | 3 | 3 | - | |
| SC | MDG01 | - | 1.0015 | 0.9970 | 1.0009 | 1.0006 |
| MDG02 | 0.9965 | - | 0.9948 | 1.0001 | 0.9996 | |
| MDG03 | 0.9979 | 1.0008 | - | 1.0003 | 1.0000 | |
| MDG04 | 0.9962 | 1.0009 | 0.9943 | - | 0.9996 | |
| MDG05 | 0.9965 | 1.0007 | 0.9947 | 1.0001 | - | |
| Measurement | Cover Image | Secret Image | ||||
|---|---|---|---|---|---|---|
| MDG06 | MDG07 | MDG08 | MDG09 | MDG10 | ||
| PSNR | MDG06 | - | 44.0579 | 44.0589 | 44.0722 | 44.5901 |
| MDG07 | 44.3288 | - | 44.0589 | 44.0744 | 44.5852 | |
| MDG08 | 44.3354 | 44.0870 | - | 44.0485 | 44.5606 | |
| MDG09 | 44.2275 | 44.0000 | 44.0360 | - | 44.4522 | |
| MDG10 | 44.3232 | 44.0541 | 44.0407 | 44.0439 | - | |
| SSIM | MDG06 | - | 0.9398 | 0.9412 | 0.9400 | 0.9449 |
| MDG07 | 0.9762 | - | 0.9759 | 0.9754 | 0.9774 | |
| MDG08 | 0.9535 | 0.9520 | - | 0.9507 | 0.9544 | |
| MDG09 | 0.9351 | 0.9342 | 0.9356 | - | 0.9361 | |
| MDG10 | 0.9295 | 0.9269 | 0.9280 | 0.9259 | - | |
| UIQ | MDG06 | - | 0.9386 | 0.9400 | 0.9387 | 0.9436 |
| MDG07 | 0.9749 | - | 0.9746 | 0.9742 | 0.9759 | |
| MDG08 | 0.9516 | 0.9501 | - | 0.9490 | 0.9524 | |
| MDG09 | 0.9342 | 0.9333 | 0.9345 | - | 0.9352 | |
| MDG10 | 0.9283 | 0.9257 | 0.9267 | 0.9247 | - | |
| NCC | MDG06 | - | 0.9988 | 0.9978 | 0.9999 | 0.9999 |
| MDG07 | 0.9994 | - | 0.9972 | 0.9999 | 0.9999 | |
| MDG08 | 0.9996 | 0.9984 | - | 0.9999 | 0.9999 | |
| MDG09 | 0.9998 | 0.9989 | 0.9982 | - | 0.9999 | |
| MDG10 | 0.9998 | 0.9987 | 0.9978 | 0.9999 | - | |
| NAE | MDG06 | - | 0.0109 | 0.0109 | 0.0108 | 0.0102 |
| MDG07 | 0.0151 | - | 0.0155 | 0.0155 | 0.0147 | |
| MDG08 | 0.0160 | 0.0165 | - | 0.0166 | 0.0156 | |
| MDG09 | 0.0078 | 0.0080 | 0.0079 | - | 0.0077 | |
| MDG10 | 0.0094 | 0.0097 | 0.0097 | 0.0097 | - | |
| IF | MDG06 | - | 0.9998 | 0.9998 | 0.9998 | 0.9999 |
| MDG07 | 0.9998 | - | 0.9998 | 0.9998 | 0.9998 | |
| MDG08 | 0.9998 | 0.9997 | - | 0.9997 | 0.9998 | |
| MDG09 | 0.9999 | 0.9999 | 0.9999 | - | 0.9999 | |
| MDG10 | 0.9999 | 0.9999 | 0.9999 | 0.9999 | - | |
| AD | MDG06 | - | 0.1738 | 0.3014 | −0.0558 | −0.0623 |
| MDG07 | 0.0270 | - | 0.3116 | −0.0456 | −0.0521 | |
| MDG08 | -0.0350 | 0.1220 | - | −0.1076 | −0.1141 | |
| MDG09 | -0.0837 | 0.0733 | 0.2009 | - | −0.1629 | |
| MDG10 | 0.0272 | 0.1842 | 0.3118 | −0.0454 | - | |
| MD | MDG06 | - | 3 | 3 | 3 | 3 |
| MDG07 | 3 | - | 3 | 3 | 3 | |
| MDG08 | 3 | 3 | - | 3 | 3 | |
| MDG09 | 3 | 3 | 3 | - | 3 | |
| MDG10 | 3 | 3 | 3 | 3 | - | |
| SC | MDG06 | - | 1.0023 | 1.0042 | 0.9990 | 0.9989 |
| MDG07 | 1.0009 | - | 1.0053 | 0.9995 | 0.9996 | |
| MDG08 | 1.0006 | 1.0030 | - | 0.9993 | 0.9993 | |
| MDG09 | 1.0003 | 1.0020 | 1.0035 | - | 0.9994 | |
| MDG10 | 1.0003 | 1.0025 | 1.0043 | 0.9992 | - | |
| Mechanism | PSNR | SSIM | UIQ | Capacity |
|---|---|---|---|---|
| Proposed | 44.2314 | 0.9499 | 0.9487 | 2-bit/8-bit |
| [12] | 43.5284 | 0.9698 | 0.9695 | 2-bit/8-bit |
| [5] | 44.0267 | -- | -- | 2-bit/8-bit |
| [20] | 46.3353 | -- | -- | 2-bit/8-bit |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abd-El-Atty, B.; Iliyasu, A.M.; Alaskar, H.; Abd El-Latif, A.A. A Robust Quasi-Quantum Walks-based Steganography Protocol for Secure Transmission of Images on Cloud-based E-healthcare Platforms. Sensors 2020, 20, 3108. https://doi.org/10.3390/s20113108
Abd-El-Atty B, Iliyasu AM, Alaskar H, Abd El-Latif AA. A Robust Quasi-Quantum Walks-based Steganography Protocol for Secure Transmission of Images on Cloud-based E-healthcare Platforms. Sensors. 2020; 20(11):3108. https://doi.org/10.3390/s20113108
Chicago/Turabian StyleAbd-El-Atty, Bassem, Abdullah M. Iliyasu, Haya Alaskar, and Ahmed A. Abd El-Latif. 2020. "A Robust Quasi-Quantum Walks-based Steganography Protocol for Secure Transmission of Images on Cloud-based E-healthcare Platforms" Sensors 20, no. 11: 3108. https://doi.org/10.3390/s20113108