Multilevel Central Trust Management Approach for Task Scheduling on IoT-Based Mobile Cloud Computing
Abstract
1. Introduction
- IoT and mobile devices tasks must be scheduled through MCC due to their energy and time constraints. During task scheduling, trustworthiness is one of the important elements because we need to offload only those trustworthiness tasks. This research article focused on this problem faced by the MCC during task offloading. Trust is required to offload the tasks because they execute MCC. The main contributions address time, packet delivery ratio, trustworthiness, and power consumption. The main contributions are the main objectives to adopt in trustable task scheduling in mobile cloud computing through organized algorithms.
- The proposed technique predicts trustable task scheduling to enhance the efficiency of the proposed system.
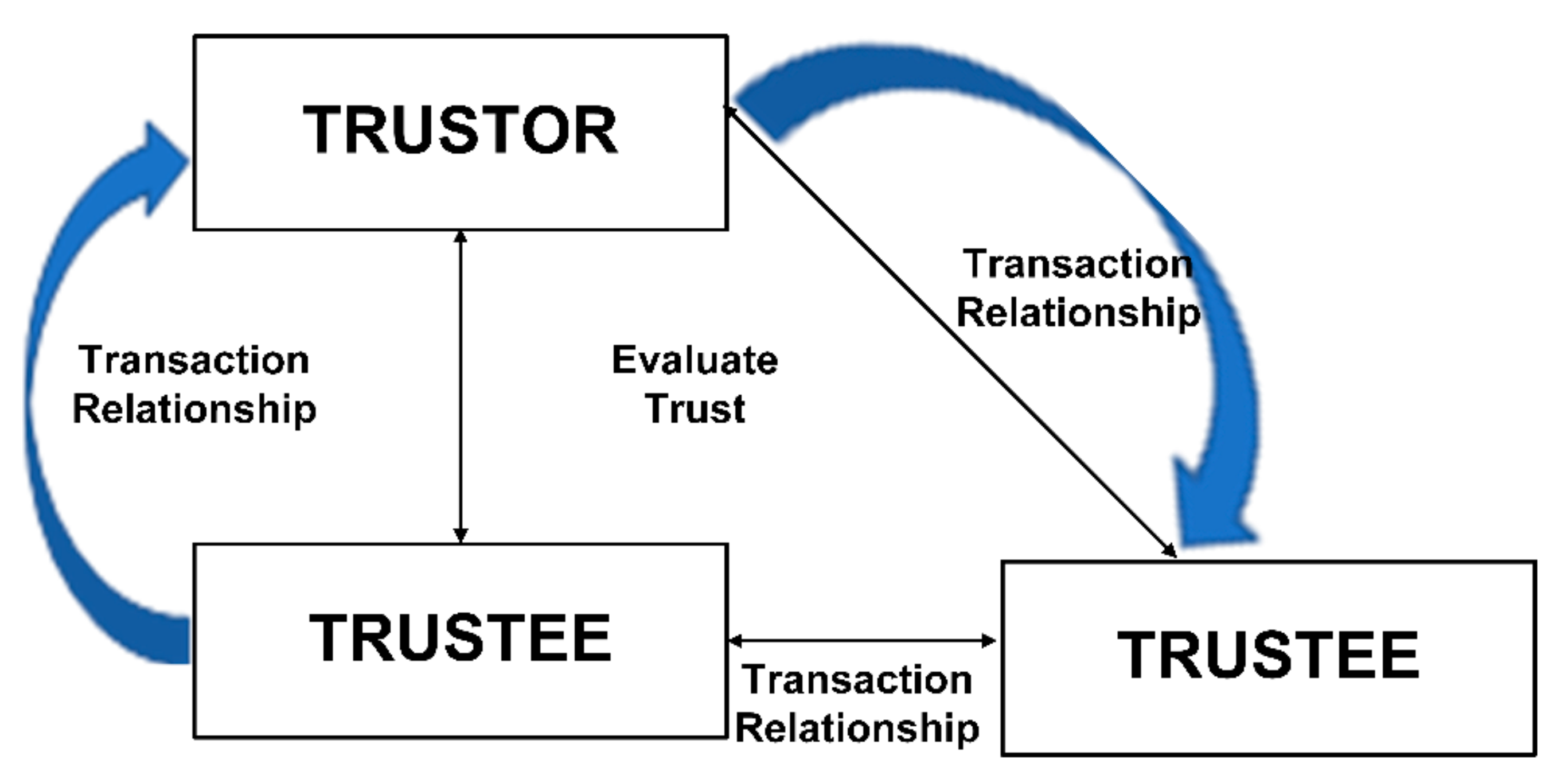
- Task scheduler updates from trustee and trustor to communicate with each other to exchange trust boundaries and then decides through trust computational algorithm for dynamic decision-making.
- Dynamic trust manager uses trust-based certification to execute and offload only trusted tasks passed from trusted computational models.
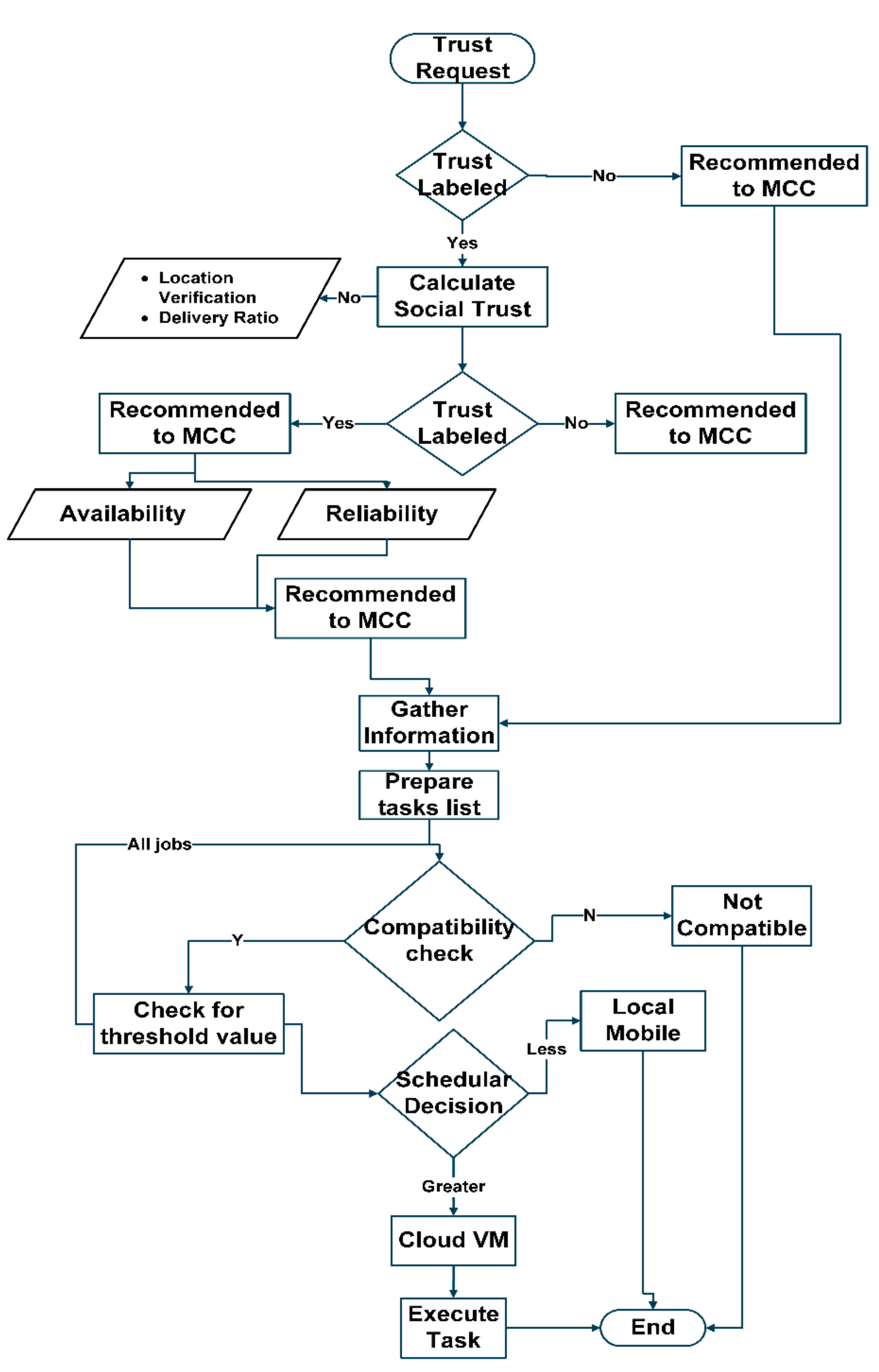
- Trust evaluation and development are handled through Algorithm 1, and correspondence and addition of new mobile node for trust evaluation is checked through Algorithm 2.
- Trustable task offloading through Algorithms 3 and 4 effectively offloads the task through effective decision-making.
- We effectively enhance the quality of service (QoS) through a multilevel central trust management approach for task scheduling on IoT-based MCC.
- Finally, to evaluate the system performance, we analyze the results using mobile offloading through simulation. Our proposed technique indicates that the trust development algorithm and task offloading decision algorithm effectively improves the system decision-making, and less power is consumed through the proposed approach.
2. Related Work
3. Methodology
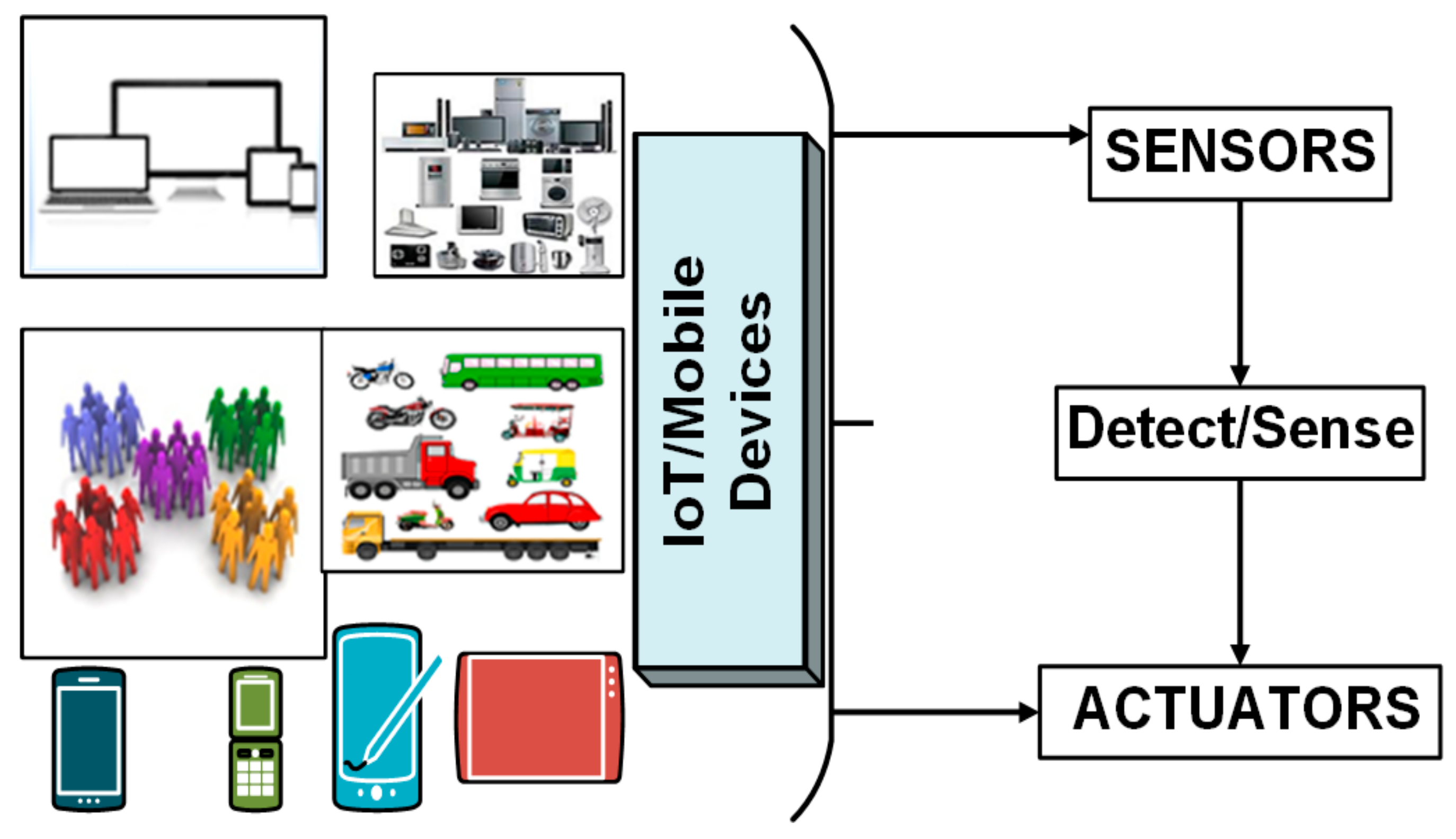
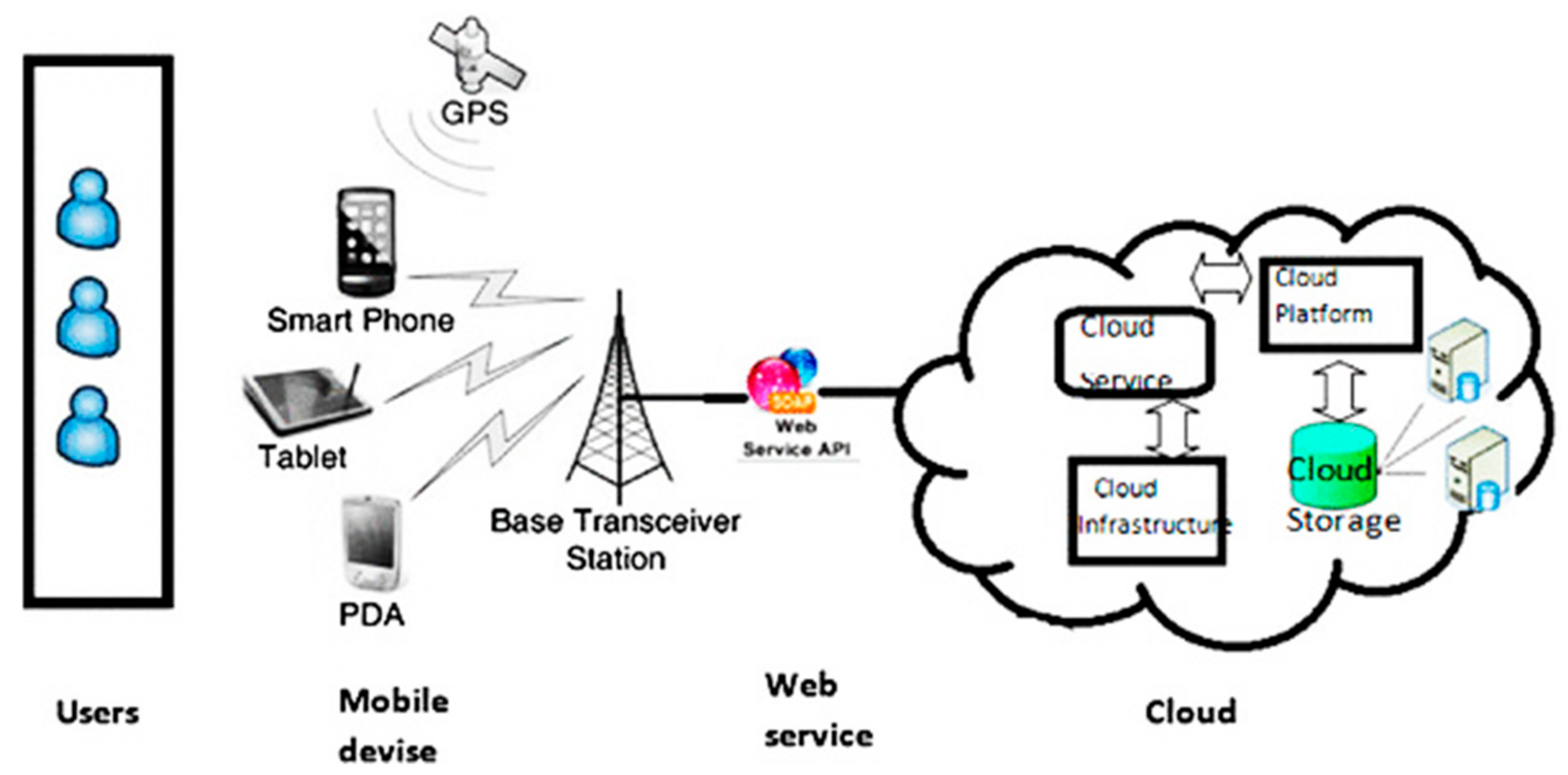
3.1. Model Structure
| Algorithm 1. QoS Trust Evaluation and Development. |
| Input: Mobile Nodes, Sensors, and IoT Devices Output: Trust Validate 1: trust_evolution(I ← j) 2: jID // Trust Identification 3: Jreq←I // Send Request to Trustee i 4: check: I ← j (ID +Li) 5: if (j! = Li) Go to Algorithm 2 else go to Algorithm 3 end if 6: Tavi: i←j(avi I ← j, rel I ← j) // Availability and Reliability 7: Tf: T_avi: i←j(avii ← j, reli ← j) 8: if (Tf > 90%) service_provider (Ti ← j) else if (Tf > 50% && Tf < 90%) network_comm (Ti ← j) else dumble_terminal (Ti ← j) end if 9: trust I ← j ( ) ← published () |
| Algorithm 2. New Trustee. |
| Input: New Node(Mobile Device, Sensor, IoT De vice) Output: Trustable new Entered Node 2: Start 1: j(i) 2: if( j! = Li) permission_grant(Fn) go to Algorithm 1 step 8 else 3: Go to Algorithm 3 4: End |
| Algorithm 3. Social Trust Adaptation Technique. |
| Input: Nodes (trustor, Trustee, Adaptation) Output: Calculated Social Trust 1: Start 2: social_trust(I ← j) 3: j(i) 4: if(j! = hr) // Checked through adaptation technique [X. Liu, et al. [16]] request_refuse() 5: else Go to Algorithm 1 step 8 6: social_trustcalculate( ) 7: End |
| Algorithm 4. Task Scheduling Decision. |
| Input: Input from Table 1 (LEGENDS Table) Output: Job Scheduling 1: (B, T, L, App, S) 2: (m) 3: (n) 4: (T) 5: (VM, N, Schedular) 6: Execution of Algorithms 1–3. 6: (T, D, C) Schedular( ) 7: for (T ≥ 0) do calculateexe_time( ) F ← ΔTm/ΔTexc end for 8: while (job_size ≤ threshold) do C(B, F, Mb, Mloc, Mstorage) if (C ≤ M) then job_exeM( ) else activeCloud(VM) submitC(J)( ) exejob( ) end if end while 9: Job_stateStore( ) |
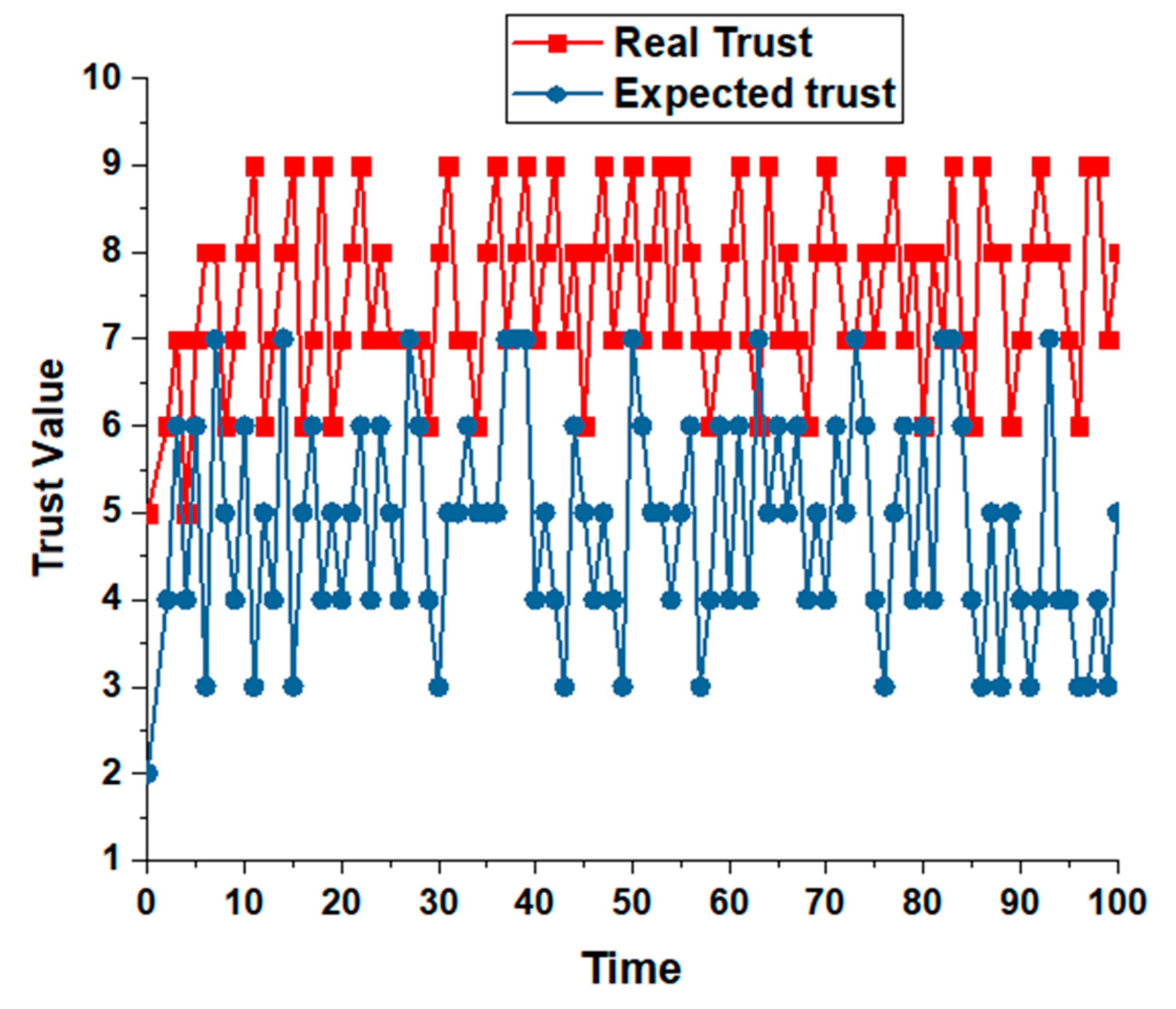
3.2. Trust Factors
3.3. Reliability
3.4. Availability
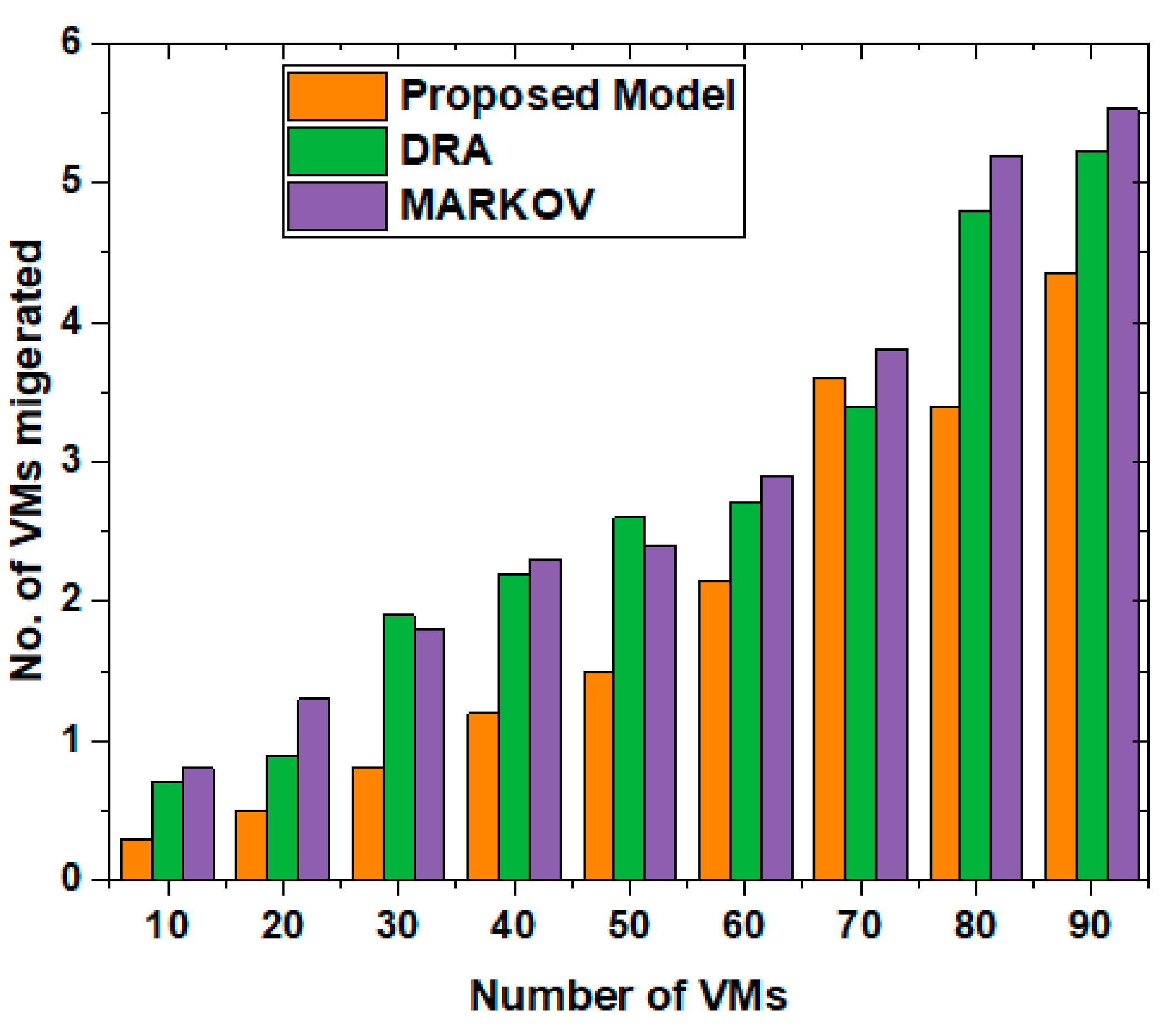
4. Results and Discussion
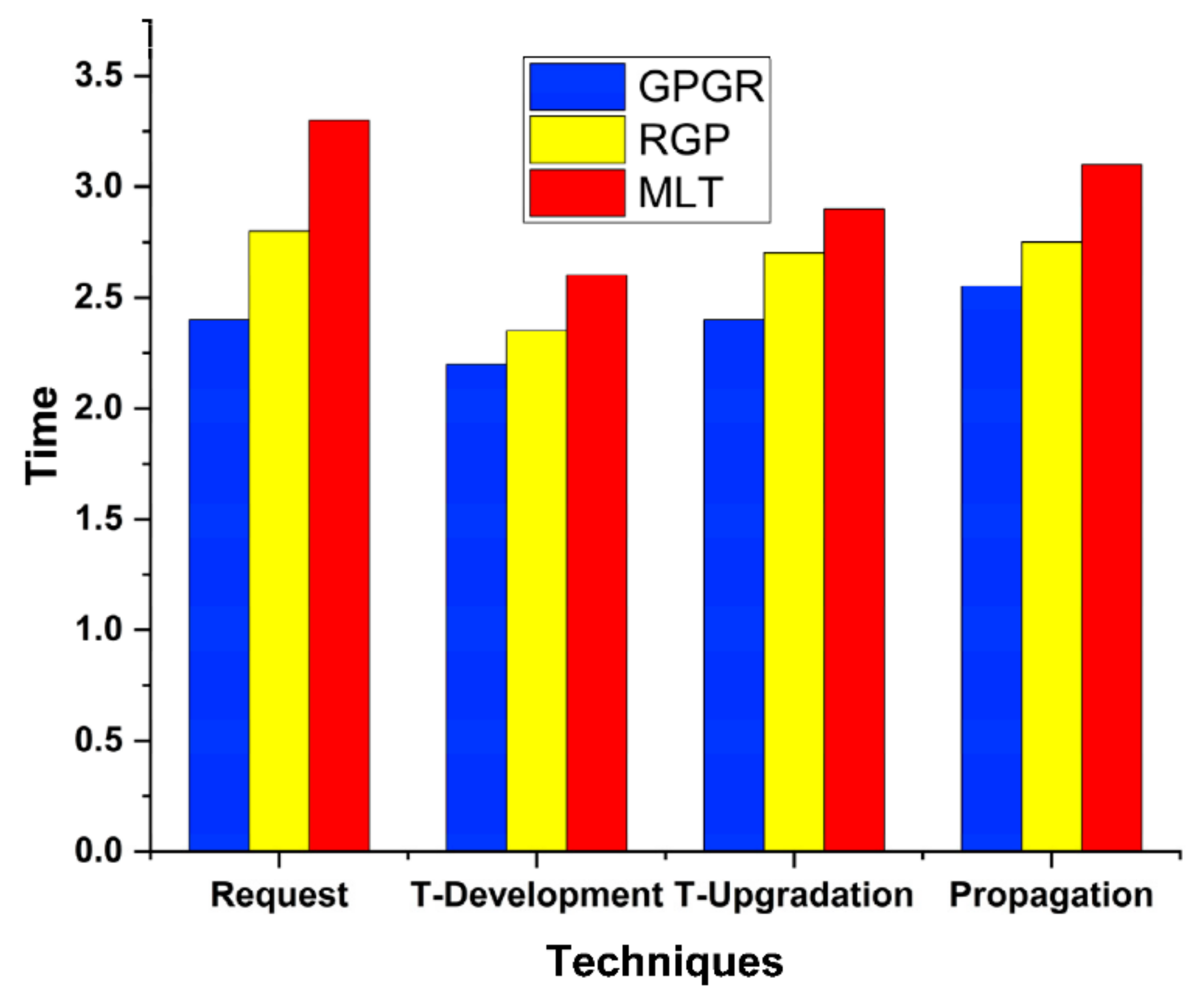
4.1. Time
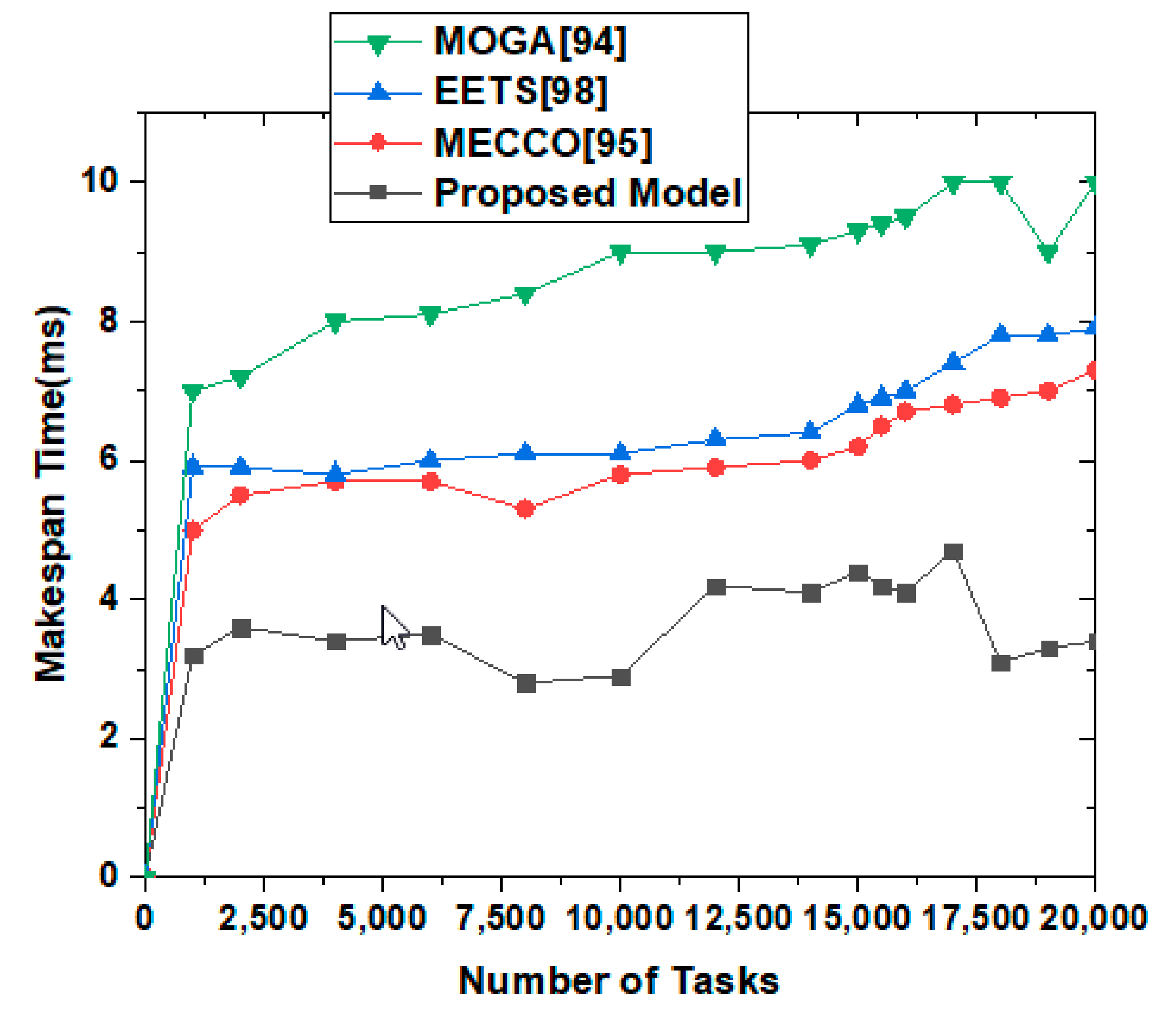
4.2. Packet Delivery Ratio
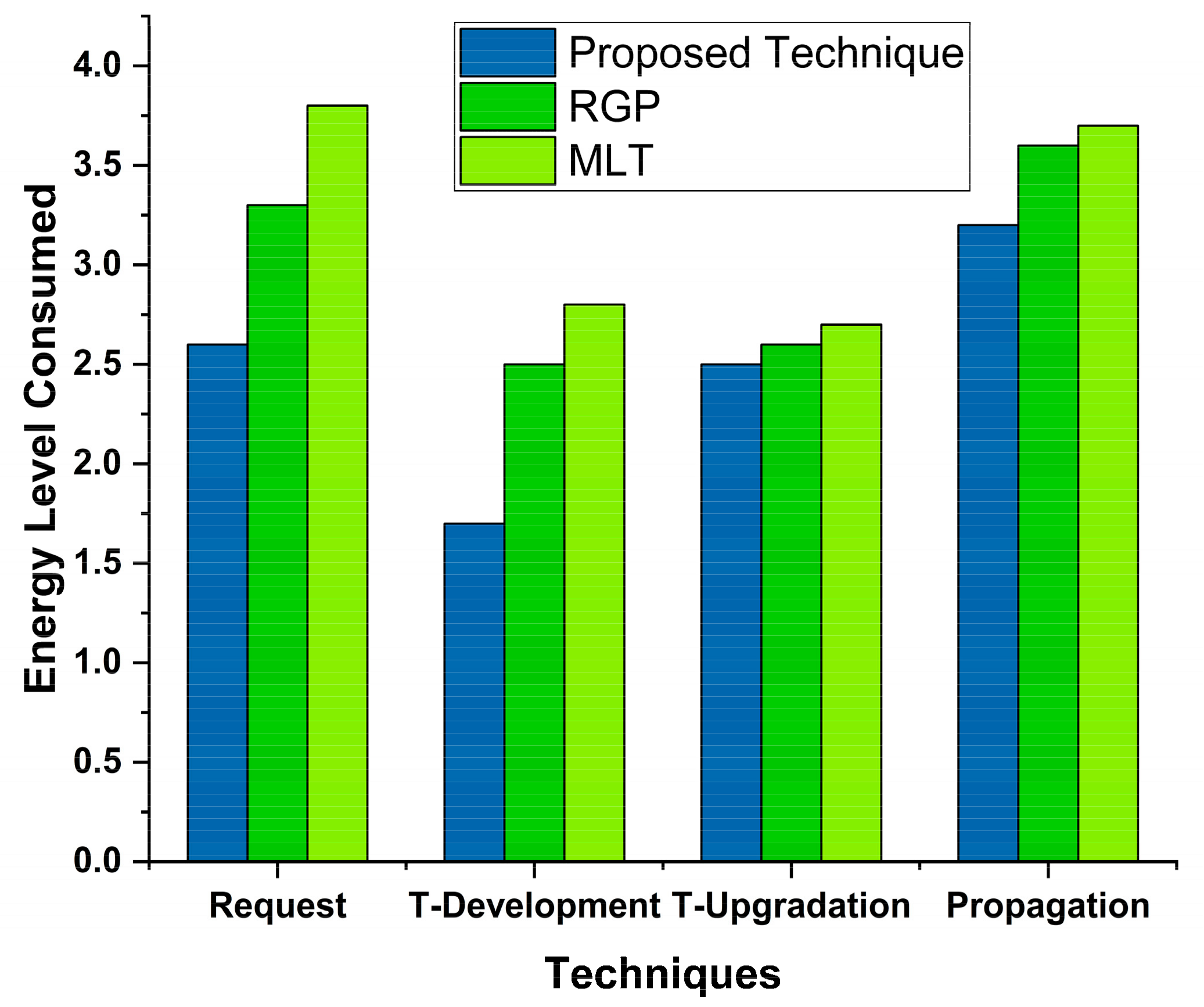
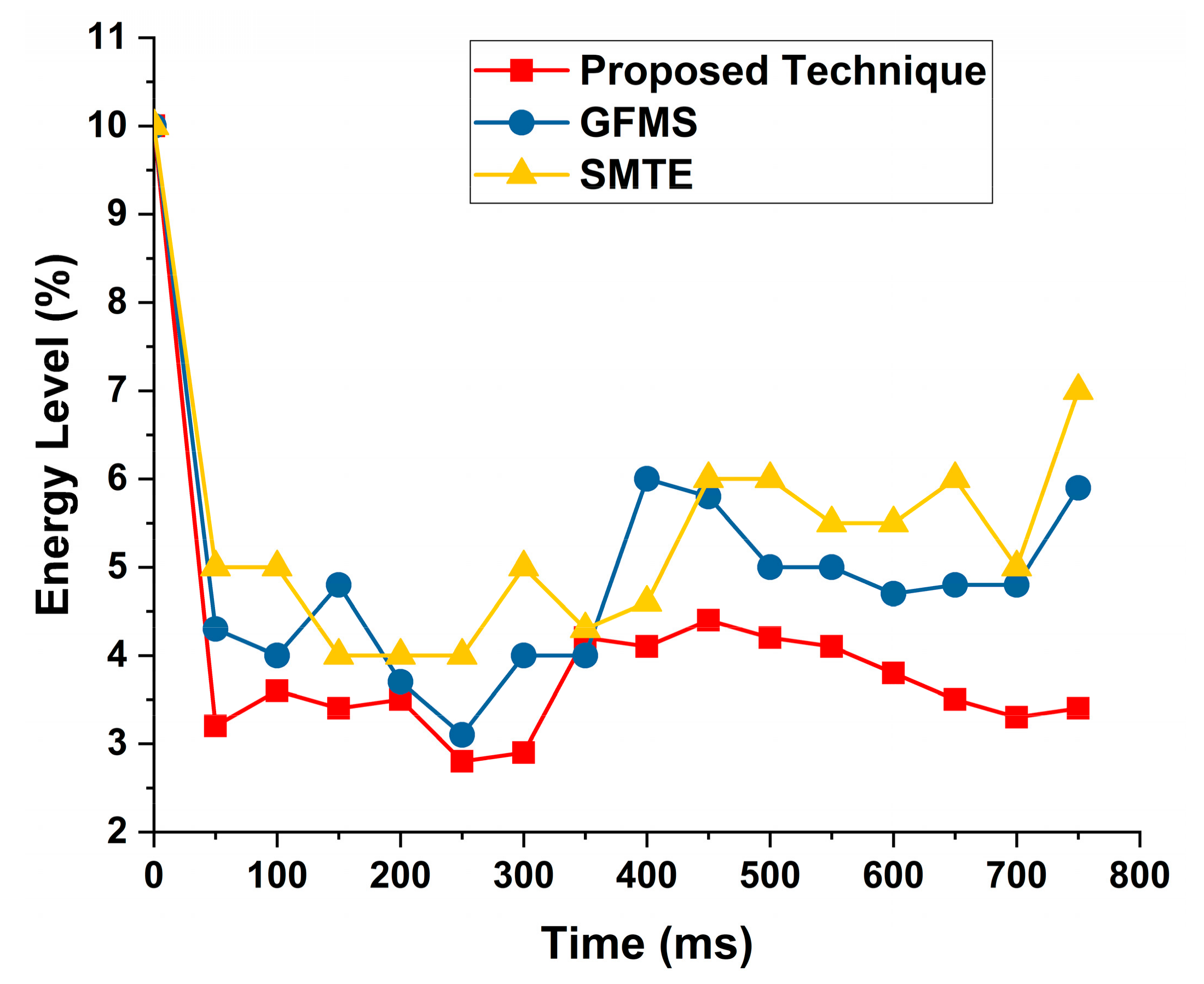
4.3. Energy Consumption
5. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Parajuli, N.; Alsadoon, A.; Prasad, P.W.C.; Ali, R.S.; Alsadoon, O.H. A recent review and a taxonomy for multimedia application in Mobile cloud computing based energy efficient transmission. Multimed. Tools Appl. 2020, 79, 31567–31594. [Google Scholar] [CrossRef]
- Ali, A.; Iqbal, M.M.; Jamil, H.; Qayyum, F.; Jabbar, S.; Cheikhrouhou, O.; Baz, M.; Faisal, J. An Efficient Dynamic-Decision Based Task Scheduler for Task Offloading Optimization and Energy Management in Mobile Cloud Computing. Sensors 2021, 21, 4527. [Google Scholar] [CrossRef] [PubMed]
- Huh, S.; Cho, S.; Kim, S. Managing IoT devices using blockchain platform. In Proceedings of the 2017 19th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Korea, 19–22 February 2017; pp. 464–467. [Google Scholar]
- Meneghello, F.; Calore, M.; Zucchetto, D.; Polese, M.; Zanella, A. IoT: Internet of threats? A survey of practical security vulnerabilities in real IoT devices. IEEE Internet Things J. 2019, 6, 8182–8201. [Google Scholar] [CrossRef]
- Xiao, L.; Wan, X.; Lu, X.; Zhang, Y.; Wu, D. IoT security techniques based on machine learning: How do IoT devices use AI to enhance security? IEEE Signal Process. Mag. 2018, 35, 41–49. [Google Scholar] [CrossRef]
- Vaiyapuri, T.; Parvathy, S.V.; Manikandan, V.; Krishnaraj, N.; Gupta, D.; Shankar, K. A Novel Hybrid Optimization for Cluster-Based Routing Protocol in Information-Centric Wireless Sensor Networks for IoT Based Mobile Edge Computing. Wirel. Pers. Commun. 2021, 1–24. [Google Scholar] [CrossRef]
- Kumar, D.; Shen, K.; Case, B.; Garg, D.; Alperovich, G.; Kuznetsov, D.; Gupta, R.; Durumeric, Z. All things considered: An analysis of IoT devices on home networks. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; pp. 1169–1185. [Google Scholar]
- Meidan, Y.; Bohadana, M.; Shabtai, A.; Ochoa, M.; Tippenhauer, N.O.; Guarnizo, J.D.; Elovici, Y. Detection of unauthorized IoT devices using machine learning techniques. arXiv 2017, arXiv:1709.04647. [Google Scholar]
- Liu, S.; Yao, S.; Huang, Y.; Liu, D.; Shao, H.; Zhao, Y.; Li, J.; Wang, T.; Wang, R.; Yang, C.; et al. Handling Missing Sensors in Topology-Aware IoT Applications with Gated Graph Neural Network. In Proceedings of the ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies; ACM: New York, NY, USA, 2020; Volume 4, pp. 1–31. [Google Scholar]
- Al-Fatlawi, A.H.; Fatlawi, H.K.; Ling, S.H. Recognition physical activities with optimal number of wearable sensors using data mining algorithms and deep belief network. In Proceedings of the 2017 39th Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC), Jeju Island, Korea, 11–15 July 2017; pp. 2871–2874. [Google Scholar]
- Ali, A.; Haseeb, M. Radio frequency identification (RFID) technology as a strategic tool towards higher performance of supply chain operations in textile and apparel industry of Malaysia. Uncertain Supply Chain. Manag. 2019, 7, 215–226. [Google Scholar] [CrossRef]
- Ratnadewi, R.; Adhie, R.P.; Hutama, Y.; Ahmar, A.S.; Setiawan, M. Implementation cryptography data encryption standard (DES) and triple data encryption standard (3DES) method in communication system based near field communication (NFC). J. Phys. Conf. Ser. 2018, 954, 012009. [Google Scholar] [CrossRef]
- Fong, T. Wireless sensor networks. In Internet of Things and Data Analytics Handbook; Wiley: Hoboken, NJ, USA, 2017; pp. 197–213. [Google Scholar]
- Varghese, B.; Buyya, R. Next generation cloud computing: New trends and research directions. Future Gener. Comput. Syst. 2018, 79, 849–861. [Google Scholar] [CrossRef]
- Malik, S.U.; Akram, H.; Gill, S.S.; Pervaiz, H.; Malik, H. EFFORT: Energy efficient framework for offload communication in mobile cloud computing. Softw. Pract. Exp. 2021, 51, 1896–1909. [Google Scholar] [CrossRef]
- Liang, W.; Huang, W.; Long, J.; Zhang, K.; Li, K.-C.; Zhang, D. Deep reinforcement learning for resource protection and real-time detection in IoT environment. IEEE Internet Things J. 2020, 7, 6392–6401. [Google Scholar] [CrossRef]
- Bhowmik, A.; De, D. mTrust: Call Behavioral Trust Predictive Analytics Using Unsupervised Learning in Mobile Cloud Computing. Wirel. Pers. Commun. 2021, 117, 483–501. [Google Scholar] [CrossRef]
- Elazhary, H. Applications Internet of Things (IoT), mobile cloud, cloudlet, mobile IoT, IoT cloud, fog, mobile edge, and edge emerging computing paradigms: Disambiguation and research directions. J. Netw. Comput. Appl. 2019, 128, 105–140. [Google Scholar] [CrossRef]
- Dinh, T.; Kim, Y.; Lee, H.J.S. A location-based interactive model of internet of things and cloud (IoT-Cloud) for mobile cloud computing applications. Sensors 2017, 17, 489. [Google Scholar] [CrossRef] [PubMed]
- Yuan, J.; Li, X. A reliable and lightweight trust computing mechanism for IoT edge devices based on multi-source feedback information fusion. IEEE Access 2018, 6, 23626–23638. [Google Scholar] [CrossRef]
- Kalkan, K.; Rasmussen, K. TruSD: Trust framework for service discovery among IoT devices. Comput. Netw. 2020, 178, 107318. [Google Scholar] [CrossRef]
- Mollah, M.B.; Azad, M.A.K.; Vasilakos, A. Security and privacy challenges in mobile cloud computing: Survey and way ahead. J. Netw. Comput. Appl. 2017, 84, 38–54. [Google Scholar] [CrossRef]
- Wang, Z.; McNally, R.; Lenihan, H. The role of social capital and culture on social decision-making constraints: A multilevel investigation. Eur. Manag. J. 2019, 37, 222–232. [Google Scholar] [CrossRef]
- Noor, T.H.; Zeadally, S.; Alfazi, A.; Sheng, Q.Z. Mobile cloud computing: Challenges and future research directions. J. Netw. Comput. Appl. 2018, 115, 70–85. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, Y.; Ling, J.; Liu, Z. Secure and fine-grained access control on e-healthcare records in mobile cloud computing. Future Gener. Comput. Syst. 2018, 78, 1020–1026. [Google Scholar] [CrossRef]
- Sundararaj, V. Optimal task assignment in mobile cloud computing by queue based ant-bee algorithm. Wirel. Pers. Commun. 2019, 104, 173–197. [Google Scholar] [CrossRef]
- Almusaylim, Z.A.; Jhanjhi, N.Z. Comprehensive review: Privacy protection of user in location-aware services of mobile cloud computing. Wirel. Pers. Commun. 2020, 111, 541–564. [Google Scholar] [CrossRef]
- Walia, A.S. Security Vulnerability in Mobile Cloud Computing (MCC). Int. J. Adv. Res. Comput. Sci. 2017, 8, 277–281. [Google Scholar]
- Tawalbeh, L.A.; Ababneh, F.; Jararweh, Y.; AlDosari, F. Trust delegation-based secure mobile cloud computing framework. Int. J. Inf. Comput. Secur. 2017, 9, 36–48. [Google Scholar] [CrossRef]
- Surridge, M.; Correndo, G.; Meacham, K.; Papay, J.; Phillips, S.C.; Wiegand, S.; Wilkinson, T. Trust Modelling in 5G mobile networks. In Proceedings of the 2018 Workshop on Security in Softwarized Networks: Prospects and Challenges, Budapest, Hungary, 24 August 2018; pp. 14–19. [Google Scholar]
- Li, W.; Cao, J.; Hu, K.; Xu, J.; Buyya, R. A trust-based agent learning model for service composition in mobile cloud computing environments. IEEE Access 2019, 7, 34207–34226. [Google Scholar] [CrossRef]
- Chen, R.; Guo, J.; Wang, D.-C.; Tsai, J.J.P.; Al-Hamadi, H.; You, I. Trust-based service management for mobile cloud IoT systems. IEEE Trans. Netw. Serv. Manag. 2018, 16, 246–263. [Google Scholar] [CrossRef]
- Stergiou, C.; Psannis, K.E.; Kim, B.-G.; Gupta, B. Secure integration of IoT and cloud computing. Future Gener. Comput. Syst. 2018, 78, 964–975. [Google Scholar] [CrossRef]
- Subramanian, N.; Jeyaraj, A. Recent security challenges in cloud computing. Comput. Electr. Eng. 2018, 71, 28–42. [Google Scholar] [CrossRef]
- Sunyaev, A. Cloud computing. In Internet Computing; Springer: Berlin/Heidelberg, Germany, 2020; pp. 195–236. [Google Scholar]
- De Donno, M.; Tange, K.; Dragoni, N. Foundations and evolution of modern computing paradigms: Cloud, iot, edge, and fog. IEEE Access 2019, 7, 150936–150948. [Google Scholar] [CrossRef]
- Fulmer, A.; Dirks, K. Multilevel Trust: A Theoretical and Practical Imperative; Taylor & Francis: Abingdon, UK, 2018. [Google Scholar]
- Mozumder, N.A. A multilevel trust-based model of ethical public leadership. J. Bus. Ethics 2018, 153, 167–184. [Google Scholar] [CrossRef]
- Rezvani, A.; Khosravi, P.; Ashkanasy, N.M. Examining the interdependencies among emotional intelligence, trust, and performance in infrastructure projects: A multilevel study. Int. J. Proj. Manag. 2018, 36, 1034–1046. [Google Scholar] [CrossRef]
- Li, J.J.; Kim, W.G.; Zhao, X.R. Multilevel model of management support and casino employee turnover intention. Tour. Manag. 2017, 59, 193–204. [Google Scholar] [CrossRef]
- Friend, S.B.; Johnson, J.S.; Sohi, R.S. Propensity to trust salespeople: A contingent multilevel-multisource examination. J. Bus. Res. 2018, 83, 1–9. [Google Scholar] [CrossRef]
- Costa, A.C.; Fulmer, C.A.; Anderson, N.R. Trust in work teams: An integrative review, multilevel model, and future directions. J. Organ. Behav. 2018, 39, 169–184. [Google Scholar] [CrossRef]
- Yu, Y.; Hao, J.-X.; Dong, X.-Y.; Khalifa, M. A multilevel model for effects of social capital and knowledge sharing in knowledge-intensive work teams. Int. J. Inf. Manag. 2013, 33, 780–790. [Google Scholar] [CrossRef]
- Chong, S.-K.; Abawajy, J.; Hamid, I.R.A.; Ahmad, M. A multilevel trust management framework for service oriented environment. Procedia Soc. Behav. Sci. 2014, 129, 396–405. [Google Scholar] [CrossRef][Green Version]
- Dinh, H.T.; Lee, C.; Niyato, D.; Wang, P. A survey of mobile cloud computing: Architecture, applications, and approaches. Wirel. Commun. Mob. Comput. 2013, 13, 1587–1611. [Google Scholar] [CrossRef]
- Gupta, P.; Gupta, S. Mobile cloud computing: The future of cloud. Int. J. Adv. Res. Electr. Electron. Instrum. Eng. 2012, 1, 134–145. [Google Scholar]
- Liu, Q.; Jian, X.; Hu, J.; Zhao, H.; Zhang, S. An optimized solution for mobile environment using mobile cloud computing. In Proceedings of the 2009 5th International Conference on Wireless Communications, Networking and Mobile Computing, Beijing, China, 24–26 September 2009; pp. 1–5. [Google Scholar]
- Guo, S.; Liu, J.; Yang, Y.; Xiao, B.; Li, Z. Energy-efficient dynamic computation offloading and cooperative task scheduling in mobile cloud computing. IEEE Trans. Mob. Comput. 2018, 18, 319–333. [Google Scholar] [CrossRef]
- Tang, C.; Xiao, S.; Wei, X.; Hao, M.; Chen, W. Energy efficient and deadline satisfied task scheduling in mobile cloud computing. In Proceedings of the 2018 IEEE International Conference on Big Data and Smart Computing (BigComp), Shanghai, China, 15–17 January 2018; pp. 198–205. [Google Scholar]
- Lee, J.; Gil, J. Adaptive fault-tolerant scheduling strategies for mobile cloud computing. J. Supercomput. 2019, 75, 4472–4488. [Google Scholar] [CrossRef]
- Raju, D.N.; Saritha, V. Architecture for fault tolerance in mobile cloud computing using disease resistance approach. Int. J. Commun. Netw. Inf. Secur. 2016, 8, 112. [Google Scholar]
- Abd, S.K.; Al-Haddad, S.A.R.; Hashim, F.; Abdullah, A.B.; Yussof, S. Energy-aware fault tolerant task offloading of mobile cloud computing. In Proceedings of the 2017 5th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), San Francisco, CA, USA, 6–8 April 2017; pp. 161–164. [Google Scholar]
- Park, J.; Yu, H.; Kim, H.; Lee, E. Dynamic group-based fault tolerance technique for reliable resource management in mobile cloud computing. Concurr. Comput. Pract. Exp. 2016, 28, 2756–2769. [Google Scholar] [CrossRef]
- Al-Sayed, M.M.; Khattab, S.; Omara, F.A. Prediction mechanisms for monitoring state of cloud resources using Markov chain model. J. Parallel Distrib. Comput. 2016, 96, 163–171. [Google Scholar] [CrossRef]
- Keshanchi, B.; Souri, A.; Navimipour, N.J. An improved genetic algorithm for task scheduling in the cloud environments using the priority queues: Formal verification, simulation, and statistical testing. J. Syst. Softw. 2017, 124, 1–21. [Google Scholar] [CrossRef]
- Peng, H.; Wen, W.-S.; Tseng, M.-L.; Li, L.-L. Joint optimization method for task scheduling time and energy consumption in mobile cloud computing environment. Appl. Soft Comput. 2019, 80, 534–545. [Google Scholar] [CrossRef]
- Tang, C.; Hao, M.; Wei, X.; Chen, W. Energy-aware task scheduling in mobile cloud computing. Distrib. Parallel Databases 2018, 36, 529–553. [Google Scholar] [CrossRef]
- Lin, X.; Wang, Y.; Xie, Q.; Pedram, M. Energy and performance-aware task scheduling in a mobile cloud computing environment. In Proceedings of the 2014 IEEE 7th International Conference on Cloud Computing, Anchorage, AK, USA, 27 June–2 July 2014; pp. 192–199. [Google Scholar]
- Guo, S.; Xiao, B.; Yang, Y.; Yang, Y. Energy-efficient dynamic offloading and resource scheduling in mobile cloud computing. In Proceedings of the IEEE INFOCOM 2016—The 35th Annual IEEE International Conference on Computer Communications, San Francisco, CA, USA, 10–14 April 2016; pp. 1–9. [Google Scholar]
- Wei, X.; Fan, J.; Lu, Z.; Ding, K. Application scheduling in mobile cloud computing with load balancing. J. Appl. Math. 2013, 2013, 409539. [Google Scholar] [CrossRef]






| Proposed Papers | Fault Rate | Time | Energy Optimization | Offload | Heterogeneity | Control Messages | Storage | % of Task Executed |
|---|---|---|---|---|---|---|---|---|
| Lee et al. [50] | ✓ | ✓ | - | ✓ | ✓ | ✓ | - | - |
| Raju et al. [51] | ✓ | ✓ | - | - | ✓ | - | - | ✓ |
| Abd et al. [52] | ✓ | ✓ | ✓ | - | ✓ | - | - | ✓ |
| Park et al. [53] | ✓ | ✓ | ✓ | ✓ | - | ✓ | ✓ | ✓ |
| Al-Sayed et al. [54] | ✓ | ✓ | - | - | - | - | - | - |
| Kashanchi et al. [55] | ✓ | - | - | ✓ | - | - | ✓ | - |
| Peng et al. [56] | ✓ | - | ✓ | - | ✓ | - | ✓ | - |
| Tang et al. [57] | ✓ | - | ✓ | - | - | - | - | ✓ |
| Lin, Xue, et al. [58] | - | - | ✓ | ✓ | - | - | - | ✓ |
| Guo et al. [59] | - | - | ✓ | ✓ | - | ✓ | - | - |
| Wei et al. [60] | - | ✓ | - | - | ✓ | - | - | - |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, A.; Iqbal, M.M.; Jamil, H.; Akbar, H.; Muthanna, A.; Ammi, M.; Althobaiti, M.M. Multilevel Central Trust Management Approach for Task Scheduling on IoT-Based Mobile Cloud Computing. Sensors 2022, 22, 108. https://doi.org/10.3390/s22010108
Ali A, Iqbal MM, Jamil H, Akbar H, Muthanna A, Ammi M, Althobaiti MM. Multilevel Central Trust Management Approach for Task Scheduling on IoT-Based Mobile Cloud Computing. Sensors. 2022; 22(1):108. https://doi.org/10.3390/s22010108
Chicago/Turabian StyleAli, Abid, Muhammad Munawar Iqbal, Harun Jamil, Habib Akbar, Ammar Muthanna, Meryem Ammi, and Maha M. Althobaiti. 2022. "Multilevel Central Trust Management Approach for Task Scheduling on IoT-Based Mobile Cloud Computing" Sensors 22, no. 1: 108. https://doi.org/10.3390/s22010108
APA StyleAli, A., Iqbal, M. M., Jamil, H., Akbar, H., Muthanna, A., Ammi, M., & Althobaiti, M. M. (2022). Multilevel Central Trust Management Approach for Task Scheduling on IoT-Based Mobile Cloud Computing. Sensors, 22(1), 108. https://doi.org/10.3390/s22010108







