A Framework for Online Document Verification Using Self-Sovereign Identity Technology
Abstract
1. Introduction
2. Background
2.1. Self-Sovereign Identity
2.2. Decentralized Identifiers
2.3. Verifiable Credentials
2.4. Distributed Ledger Technology
2.5. Digital Wallet and Agent
3. Related Works
4. Methodology
4.1. Use Case
4.2. Design Objectives
- Objective 1: EfficiencyThere is a long time involved in carrying out document verification and it is especially more challenging if it is cross-border. From the user’s standpoint, organizations that provide quick and easy document verification are more attractive. This also provides companies with a competitive advantage. Furthermore, there are several procedures involving data validation, such as determining if the document’s validity has expired, which are performed manually in many existing systems and create longer waiting times for users [43]. Thus, the automation of this manual process is also an important requirement.
- Objective 2: DecentralizationCustomer data silos are honeypots for hackers, thus securing valuable information is costly and not the core business of financial institutions such as banks. Similarly, any error can have serious ramifications in terms of reputation, sanctions, or both, as is also discussed in [25]. Multiple revelations of data breaches in businesses, particularly financial institutions [44,45], have resulted in major ramifications for the organization’s brand, consumer confidence in the architecture, societal trust, and personal safety. In general, consumers have lost faith in central authorities in recent years as a result of situations in which large corporations purposefully abused user data for financial or political gain [46]. This is regulated to some extent in financial institutions, but we cannot be fully confident that there is no chance of this happening in the future. As a result, data decentralization was chosen as another need.
- Objective 3: PrivacyUsers should be able to share their documents and credentials in a privacy-preserving way by minimizing the amount of personal information that needs to be disclosed. For example, in the case of loan processing, one may only have to prove that their salary is beyond a certain number but not an exact value. It is also important that the user has control over their documents, data, and its flow. In addition, the verification of the document must not involve contacting the issuer, because the issuer of the certificate would otherwise know where the user has been and may be able to track them. Data protection regulations (e.g., the GDPR) provide strict legal rules on storing and processing personal data. It should not be stored on the blockchain and records need to be deleted at users’ request [23].
- Objective 4: TrustAuthenticity and integrity are important aspects of document verification and the documents that are submitted must be trusted by the verifiers. The digital document should not have been tampered with after being issued and it should be feasible to verify and validate it. There must exist a complete trust between different actors in the system and the user should be able to convince the verifier that their document is not stolen, sold, or shared. The submitted documents must have a higher level of assurance in a completely digital setting.
- Objective 5: InteroperabilityIt is important that the system is based on open standards and relies on open data structures and technologies. The proposed document verification solution should be applicable across different institutions, organizations, and borders. In addition, it is also important that it can be integrated into existing systems.
- Objective 6: TransparencyTransparency means that the systems and algorithms must be transparent [5]. It enables us to make an informed decision and improves accountability [47]. Both in terms of how they function and how they are controlled and updated, it is important that the technologies used to administer and operate document verification systems be easily accessible. The architecture should be open, well-known, and independent allowing anyone to examine how different components operate.
5. System Architecture and Design
5.1. Architecture Overview
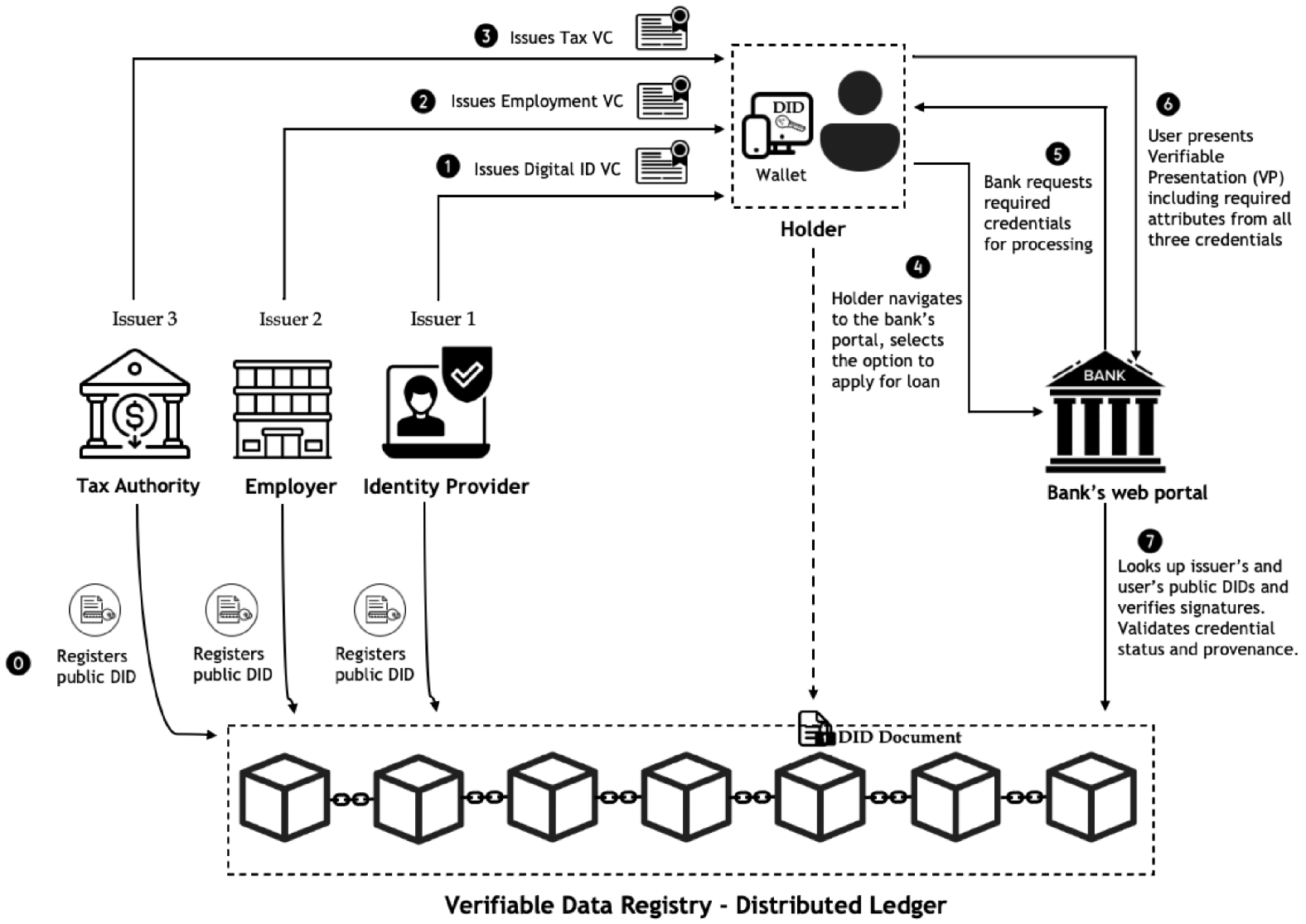
- The holder applies for a VC from a trusted identity provider (IdP), which allows them to authenticate themselves to the bank’s web portal. The bank itself could act as an IdP and issue a corresponding VC to the user. The holder also needs employment and tax certificates which are issued in the form of VCs by their employer and the tax authority, respectively. The VC contains a set of tamper-evident claims about a user and metadata that cryptographically prove who issued it. When an organization issues a VC, they attach their public DID to that credential. That same public DID is also stored on the blockchain. When someone wants to verify the authenticity of the credential, they can check the public DID on the blockchain to see who issued it without having to contact the issuing party. The blockchain acts as a verifiable data registry, a “phonebook” that anyone can consult to verify what organization a specific public DID belongs to.
- The holder consents to accept/decline the issued credential. If the user accepts, they can now receive this credential and store it in their wallet which could be a web wallet or a mobile wallet. The holder stores the private key for the DID in their digital wallet, while the public keys are registered to the blockchain by the issuing authority.
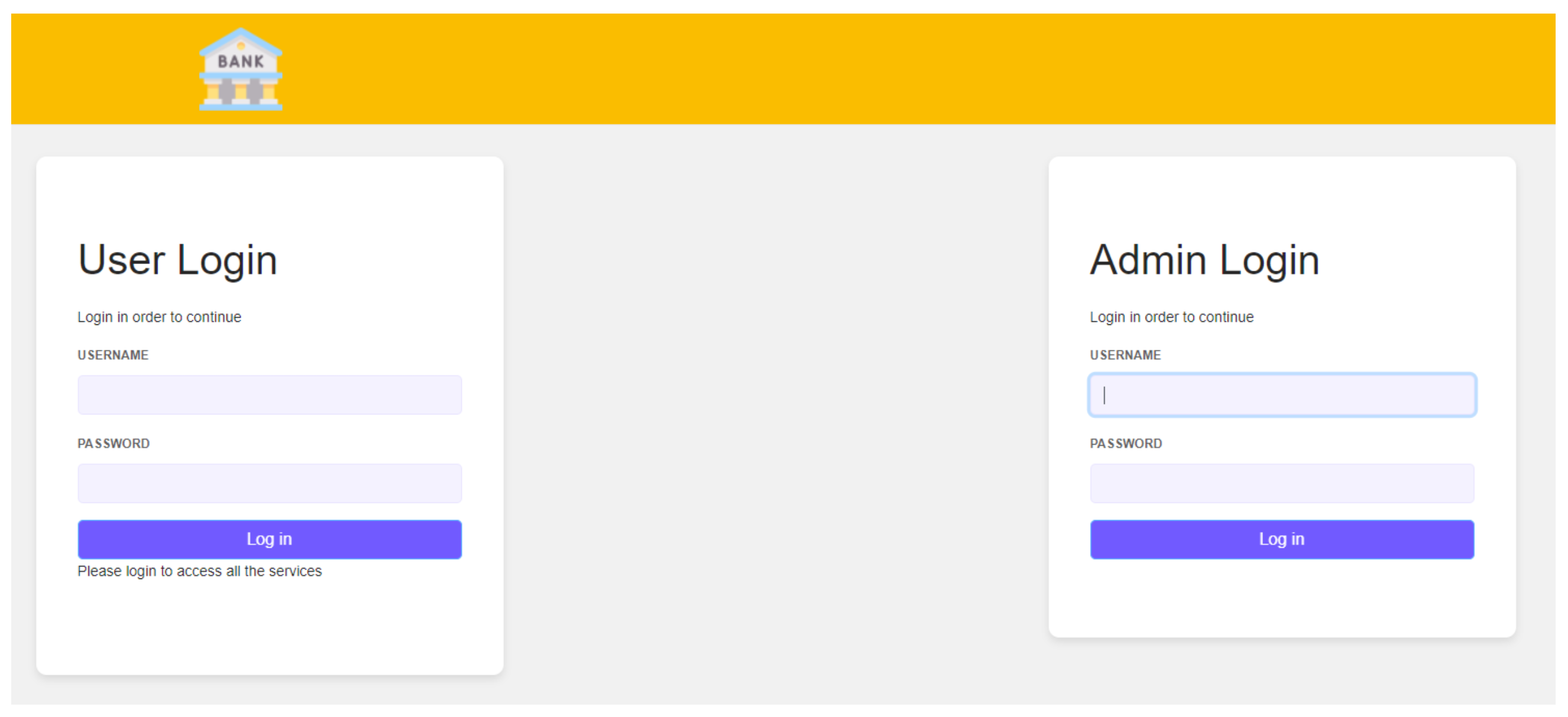
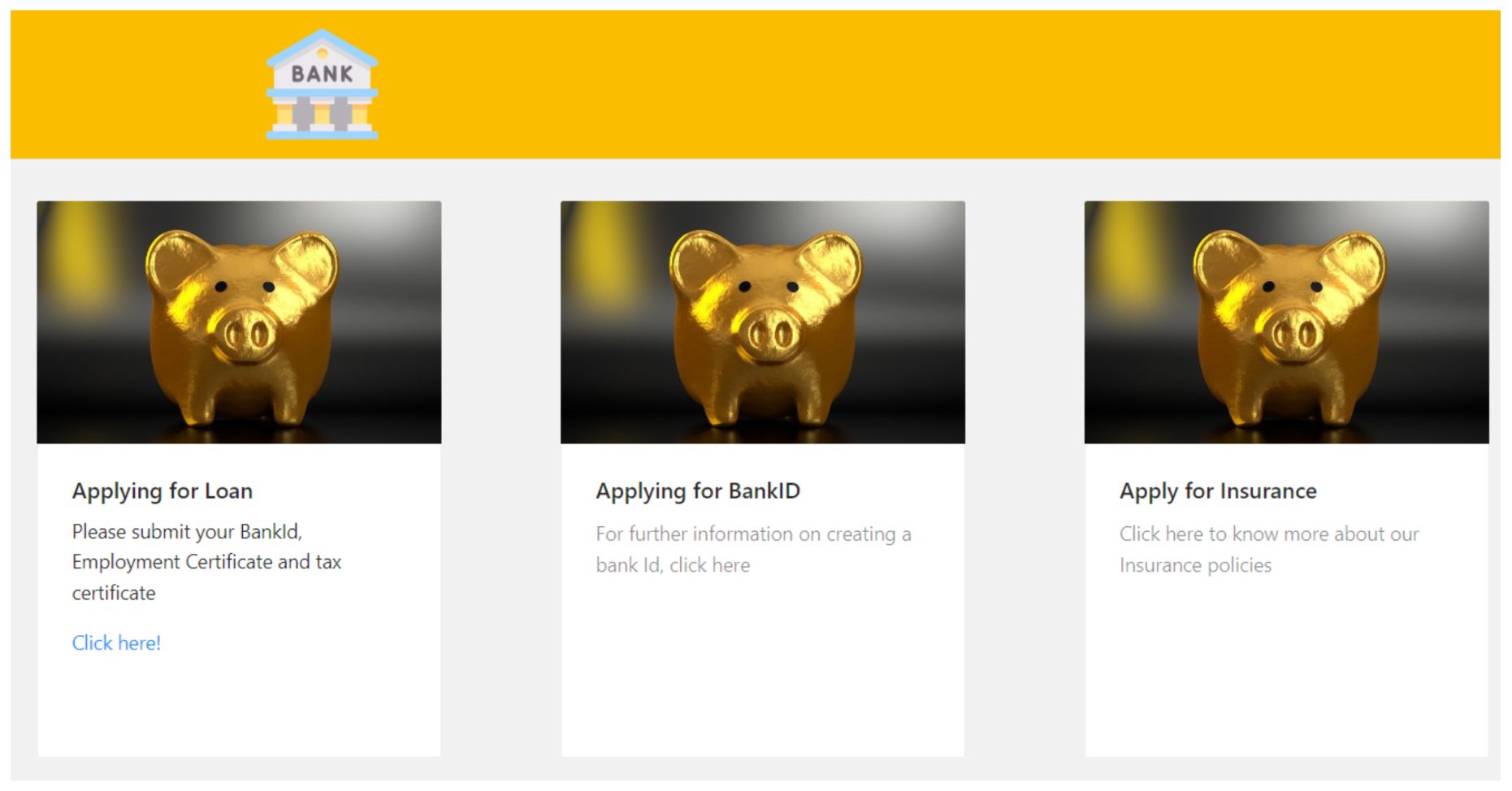
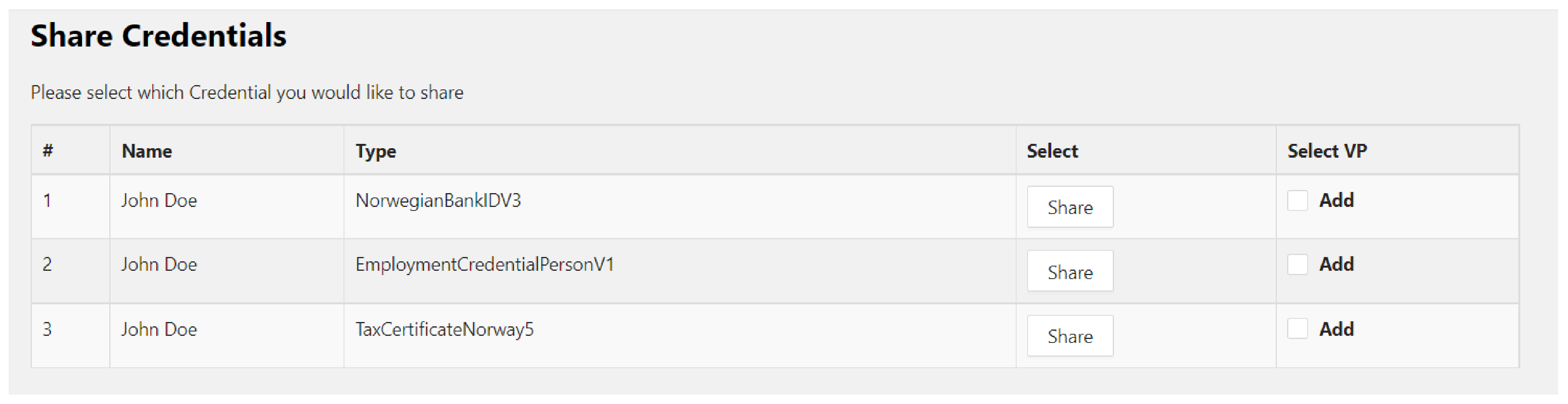
- The holder/user now visits the website of the bank, authenticates with a digital ID VC stored in a wallet, and finds the relevant page for the online loan application. The bank defines the list of required documents to process the loan and sends a proof of request to the holder. The holder receives the credential share request from the bank, reviews the proof request, and determines whether the relevant credential and/or claims exist in the wallet. If the holder has all of the qualifying credentials, they can make a verifiable presentation (VP) that includes all of the required credentials. As also discussed in Section 2.3, a VP is a packaging mechanism to cryptographically prove that the holder is sending the VCs. This way the user does not have to send each credential separately but all in one transaction.
- The bank then looks up public key material from the distributed ledger and verifies signatures. The bank is capable of verifying all the electronic information (i.e., the validity of the credential, status, issuer, presenter, and claims) against the blockchain network without having to contact the original issuer. The status of a VC is checked by the verifier to ensure that it is still valid. From an implementation standpoint, W3C’s specification has a property called the property that contains information about the current status of a VC.
5.2. Enabling Technologies
5.2.1. SSI Standards
5.2.2. SSI Frameworks
- Mattr is an SSI platform which is actively engaged in the SSI standards and open-source community across a range of different forums [37]. The framework offers a comprehensive set of APIs and tools that take care of all the logic and could be used to manage DIDs, private keys, VCs, and VPs. Mattr was found to have well-documented APIs and tutorials. However, when we tried to reach for developer support through the given contacts on the website, we did not receive an active support.
- Trinsic is another player in the SSI space which provides a set of lightweight APIs for sending verifiable data. According to their website, they are tech-agnostic and based on open standards [18]. It was found that Trinsic has an active developer support and an open API as was also reported by Lalchandani et al. [53]. It has a comparatively large community and support with over 1000 developers and multiple organizations. It also has an active community on Slack and a chatbot online that offers active support for developers and anyone interested in understanding the SSI technology better. Trinsic has reduced the complexity of open-source technologies (Aries Framework .NET and Hyperledger Indy [54]) by building on top of them and exposing APIs. On the other hand, relying on Trinsic limits the potential that open frameworks could offer and provides less flexibility when implementing our PoC.
- Affinidi is one of the leading players in the SSI space working to enable the creation and sharing of trusted digital identities and credentials [55]. They are open-source and released under the Apache license. The Affinidi APIs were among the most well-documented, comprehensive, and purpose-built APIs available. Affinidi has an active discord server with over 400 members. Its infrastructure consists of SidetreeJS [17] integrated into the DID registry with IPFS as the content-addressable storage. In comparison to other DID approaches, Sidetree has some distinct advantages, such as a low cost, high throughput, and the built-in portability of the identifier [56]. Furthermore, MongoDB serves as the long-term cache and the Ethereum blockchain via ChainStack serves as the ledger address. The team at Affinidi is highly involved in working groups for SSI standards.
- Veramo is a JavaScript framework that allows developers to create and manage decentralized identifiers and verifiable credentials [36]. It claims to work closely with the W3C and DIF in order to build compatibility across different projects and initiatives in the SSI space. Similar to Mattr and Trinsic, the Veramo agent exposes all of its functionalities via a REST API with OpenAPI documentation. All functions can also be accessed on unsupported platforms via HTTP queries. The CLI implementation could be used as a guide but the API implementation has a very thorough documentation hard to follow for developers. Thus, although Veramo bootstraps the process of issuing verifiable credentials with minimal configuration while running on multiple platforms, it is not very developer-friendly from the authors’ personal experience and also backed by [57].
5.2.3. Web Platform
6. Implementation
6.1. Designing Credential Schema
- BankID schema: Based on the feedback and discussion with experts from Signicat, the schema was designed according to an OpenID Connect (OIDC) (Listing 1) response that is received when a BankID verification is requested through Signicat, which is the leading provider of Norwegian BankID in Norway. Since one of the objectives of our proposed system was to be able to integrate with current systems and coexist until the SSI system is fully developed, this option looked the best for our use case.
| Listing 1: OIDC response after BankID Verification (Source [61]). |
{ "sub": "6ofVBM_uxebykmPnAYo3ORHGGYhFXRae", "signicat.certificate_not_after": "2022-06-27T22:59:59.000Z", "signicat.certificate_issuer_dn": "TestBank", "signicat.certificate_unique_id": "9578-6000-4-361384", "signicat.certificate_not_before": "2022-06-12T23:00:00.000Z", "name": "John Doe", "signicat.national_id": "199002171234", "birth_date": "1990-02-17" "given_name": "John", "family_name": "Doe" "country": "NO", } |
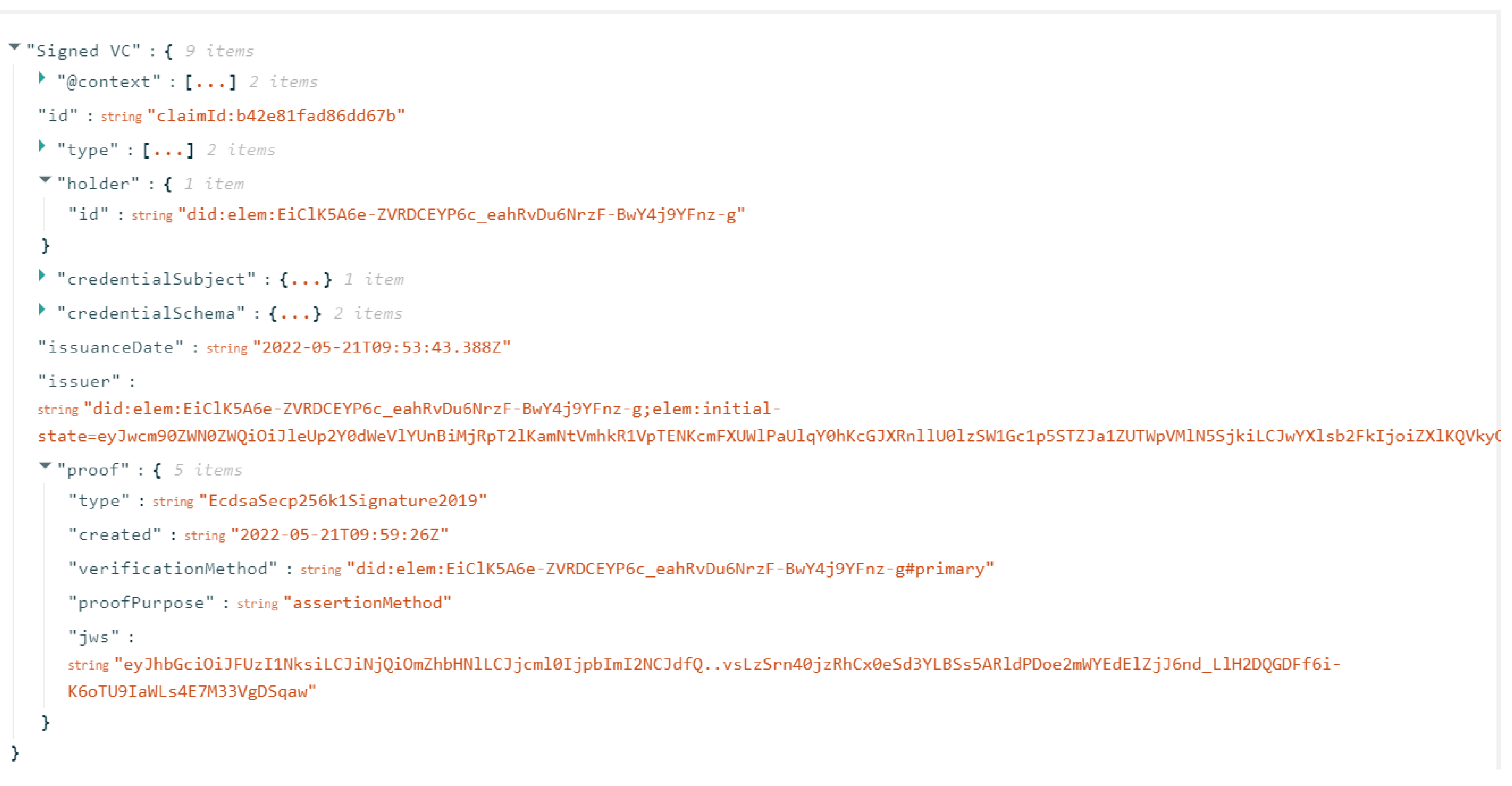
- The BankID VC schema (Listing 2) was created based on the Norwegian BankID attributes received from the OIDC response [61]. The schema followed the VC data model and JSON-LD data syntax. Two required properties of JSON-LD that consistently showed up in the VC, namely and , were defined. Contexts mapped terms that were used in VCs and VPs to URIs that explained what those terms meant in that context while the type property expressed what kind of information was in the document. Moreover, several other parameters were added that were required for decentralized verification. This included the DIDs for the holder and issuer, and the information about the status of the credential. The W3C spec [7] references the status property in Section 4.9 which states that using the property, the current status of a verifiable credential can be discovered, such as if it has been suspended or revoked. It is populated with a status API which can be accessed by verifiers to check the status of the credential. The final schema designed for the BankID VC can be seen below.
| Listing 2: BankID Schema. |
{ "@context": [ "https://www.w3.org/2018/credentials/v1", "https://schema.affinidi.com/NorwegianBankIDV1V1-0.jsonld" ], "id": "claimId:cba42389c33e5a45", "type": [ "VerifiableCredential", "NorwegianBankIDV1" ], "holder": { "id": "did:elem:EiAMDI8BotTYFl4DNw-x_xNQ4H8XpEN2LaWAcv0MmNASJA" }, "issuer": "https://www.signicat.com", "issuanceDate": "2022-06-12T23:00:00.000Z" "credentialSubject": { "data": { "@type": [ "Person", ], "birthDate": { "@type": "Date", "date": "1990-02-17", } "name": { "@type": "Name", "name": "John Doe", "givenName": "John", "familyName": "Doe" } "nationalID": "199002171234" }, "certificate": { "certificateIssuer": "TestBank", "certificateUniqueID": "9578-6000-4-361384", "certificateExpiryDate": ""2022-06-27T22:59:59.000Z"", "country": "NO" }, "credentialStatus": { "id": "https://www.signicat.com/status/100, "type": "CredentialStatusList2017" }, "credentialSchema": { "id": "https://schema.affinidi.com/NorwegianBankIDV1V1-0.json", "type": "JsonSchemaValidator2018" }, "proof": { "type": "RsaSignature2018", "created": "2022-06-15T14:21:10Z", "proofPurpose": "assertionMethod", "verificationMethod": "https://signicat.com/issuers/144223#key-1", "jws": "eyJhbGciOiJSUzI1NiIsImI2NCI6ZmFsc2UsImNyaXQiOlsiYjY0Il19..kTCYt5 XsITJX1CxPCT8yAV-TVIw5WEuts01mq-pQy7UJiN5mgREEMGlv50aqzpqh4Qq_PbChOMqs LfRoPsnsgxD-WUcX16dUOqV0G_zS245-kronKb78cPktb3rk-BuQy72IFLN25DYuNzVBAh 4vGHSrQyHUGlcTwLtjPAnKb78" } } |
- Employment schema: Affinidi provides an online portal that contains schemas applicable to a variety of use cases. It already offers a certificate of employment schema (Listing 3) that serves a similar purpose as in our proposed system. Thus, the schema defined in the Affinidi portal was reused instead of creating it ourselves so that the implementation based on this schema would be interoperable with other systems. The schema manager can be accessed here: https://ui.schema.affinidi.com/schemas. The schema used for the employment certificate from NTNU is shown below.
| Listing 3: Employment Schema. |
| { "@context": [ "https://www.w3.org/2018/credentials/v1", "https://schema.affinidi.com/EmploymentCredentialPersonV1V1-0.jsonld" ], "id": "claimId:fbd51289d18e5e29", "type": [ "VerifiableCredential", "EmploymentCredentialPersonV1" ], "holder": { "id": "did:elem:EiBAYArpk_r7L8EzR1YqKe4tK0n9S6_VxpT-FLOymmx-AQ" }, "issuer": "https://www.ntnu.no/", "issuanceDate": "2022-06-23T09:04:04.059Z" "credentialSubject": { "data": { "@type": [ "Person", "EmploymentPerson" ], "worksFor": { "@type": [ "Organization", "Education" ], "name": "Norwegian Institute of Science and Technology" }, "reference": { "@type": "ContactPoint", "name": "Alex Jorgen", "email": "alex.jorgen@no" }, "skills": [ "Administrative work", "Human resource manager" ], "offerLetter": "https://dropbox.com/offerLetter", "experienceLetter": "https://dropbox.com/experienceLetter", "salary": { "@type": [ "Salary" ], "gross": { "@type": "MonetaryAmount", "value": 518000, "currency": "NOK" }, "net": { "@type": "MonetaryAmount", "value": 30000, "currency": "NOK" }, "frequency": "Monthly" } }, "name": "John Doe" } }, "credentialStatus": { "id": "https://ntnu.no/status/24, "type": "CredentialStatusList2017" }, "credentialSchema": { "id": "https://schema.affinidi.com/EmploymentCredentialPersonV1V1-0.json", "type": "JsonSchemaValidator2018" }, "proof": { "type": "RsaSignature2018", "created": "2022-06-28T11:29:10Z", "proofPurpose": "assertionMethod", "verificationMethod": "https://ntnu.no/issuers/565049#key-1", "jws": "eyJhbGciOiJSUzI1NiIsImI2NCI6ZmFsc2UsImNyaXQiOlsiYjY0Il19..kTCYt5 XsITJX1CxPCT8yAV-TVIw5WEuts01mq-pQy7UJiN5mgREEMGlv50aqzpqh4Qq_PbChOMqs LfRoPsnsgxD-WUcX16dUOqV0G_zS245-kronKb78cPktb3rk-BuQy72IFLN25DYuNzVBAh 4vGHSrQyHUGlcTwLtjPAnKb78" } } |
- Tax schema: An existing schema for a verifiable credential serving a similar purpose could not be found online so the tax assessment document offered by the NTA [68] was used as a reference to create a new tax VC schema (Listing 4). NTA provides the individual with a tax assessment document that includes various attributes regarding personal finances over the last year. The relevant attributes were selected and the VC schema for the tax certificate was created.
| Listing 4: Distance constraint algorithm. |
| { "@context": [ "https://www.w3.org/2018/credentials/v1", "https://schema.affinidi.com/TaxCertificateNorwayV1-1.jsonld" ], "id": "claimId:ae6164eda5b8a10a", "type": [ "VerifiableCredential", "TaxCertificateNorway" ], "holder": { "id": "did:elem:EiBwTbgxIYnXt8H6XuiVHig_w_hNL2vynZcOLUHuOaQVzw" }, "issuer": "https://www.skatteetaten.no/", "issuanceDate": "2022-06-28T06:02:10.639Z", "credentialSubject": { "data": { "personalIncomeAndNetIncome": { "salariesAndPayments": "518000", "interestOnBankDeposits": "1000", "totalIncome": "551000" }, "deductions": { "minimumDeductionFromOwnIncome": "106750", "premiumForPensionScheme": "10263", "totalDeductions": "117013" }, "totalBasisForIncomeTax": "402000", "wealth": { "assets": "100000", "bankDeposits": "152000", "grossCapital": "252000", "netWealth": "252000" }, "name": "John Doe", "year": "2021", "nationalID": "199002171234", "settlement": { "withholdingTax": "134800", "additionalAdvance": "2500", } } }, "credentialStatus": { "id": "https://www.skatteetaten.no//status/11, "type": "CredentialStatusList2017" }, "credentialSchema": { "id": "https://schema.affinidi.com/TaxCertificateNorwayV1-1.json", "type": "JsonSchemaValidator2018" }, "proof": { "type": "RsaSignature2018", "created": "2022-07-18T21:19:10Z", "proofPurpose": "assertionMethod", "verificationMethod": "https://www.skatteetaten.no/issuers/565049#key-1", "jws": "eyJhbGciOiJSUzI1NiIsImI2NCI6ZmFsc2UsImNyaXQiOlsiYjY0Il19..TCYt5X sITJX1CxPCT8yAV-TVkIEq_PbChOMqsLfRoPsnsgw5WEuts01mq-pQy7UJiN5mgRxD-WUc X16dUEMGlv50aqzpqh4Qktb3rk-BuQy72IFLOqV0G_zS245-kronKb78cPN25DGlcTwLtj PAYuNzVBAh4vGHSrQyHUdBBPM" } } |
6.2. PoC Design and Development
6.2.1. Issuer
6.2.2. Holder
6.2.3. Verifier
7. Evaluation and Discussion
- Privacy, user control, and consent. Our artifact supports verifiable credentials with a selective disclosure feature. Users can share only the required attributes in a document and hide optional ones, which minimizes data and enhances user control and privacy. Moreover, users manage their data independently with their identity wallet, giving them full control over their digital identities. Users get an overview in their digital wallet of which data they have shared and with whom. Furthermore, no personal data are stored at other parties or on a blockchain. Thus, compliance with the GDPR’s fundamental objectives can likely be achieved. In addition, by implementing our approach, user interactions are not trackable by issuing organizations because a verifier does not have to directly contact an issuer during the verification process.
- Decentralization. In our solution, users use a personal digital wallet to manage their keys and data, which means that unlike typical systems that store data centrally, credentials would be saved in digital wallets that would be distributed all over the edges of the network giving individual users full control over their personal data. This would also vastly increase the complexity of any kind of attack, and even if certain systems were penetrated, it would no longer be a massive honeypot containing millions of individuals’ personal information. It is undeniable that the existing standards and technologies have their limits. Equifax [70], Cambridge Analytica [71], and First American Financial [72] are the most recent examples of data breaches in which the identity information of millions of people was exposed. In addition, the use of distributed ledger technology as a verifiable data registry improves data reconciliation. Each time the user data are transformed, it opens up opportunities for data loss or incorrect data to enter the workstream. By having a decentralized data store, every entity has access to a real-time, shared view of the data. However, great consideration should be given to wallet and agent security, due to their critical role in holding and processing client identity information.
- Authenticity and integrity. Verifiable credentials play a major role in building the strength of the proposed system in terms of authenticity and integrity. Documents issued as VCs such as in our artifact are tamper-proof and authentic through the issuer’s digital signature. Any issuer-signed verifiable credential can be cryptographically checked, and information about who issued it and if it has been tampered with can be found in real time. Easy-counterfeit identification would help businesses find genuine applicants with authentic information about them and could turn away possible fraudulent users.
- Transparency. The decentralized method of online loan processing and document verification also makes the process transparent. It is important that the system used to administer and operate the process be open in regard to how it functions and how it is managed. Since the implemented system is based on open-source protocols and development tools, it provides more flexibility to examine how it works and if there are loopholes that one must be aware of. Further, it allows anyone to examine how different components operate, making the overall system transparent and trustworthy.
- Interoperability. The existing methods of document verification are mostly done through collaborative networks, but the process is not ideal in a sense that these require a preconnection with one another to be able to be fully functional. This process is expensive to service users and adds an overhead of financial burden instead of focusing on their core business idea. Similarly, a solution cannot be called interoperable if it only works for a certain collaborative network. In existing systems, there is no common methodology for validating and verifying electronic documents acceptable across multiple domains, as a result, systems are either siloed, fragmented, or limited to collaboration networks [3,73]. SSI on the other hand, is based on open standards and protocols and holds the possibility to be interoperable. Interoperability in SSI means that the credential should be used as widely as possible. The majority of SSI solution creators already base their work on two open W3C standards. As our solution is based on these open-standard specifications and vendor-neutral technology components, it maximizes interoperability and transitive trust while minimizing the possibility of vendor lock-in [5]. Moreover, the proposed process includes putting schema definitions based on JSON-LD on a public blockchain that all verifiers can access and examine to determine semantic interoperability. The capacity of computer systems to exchange data with a clear, shared meaning is known as semantic interoperability. In addition to data packaging (syntax), semantic interoperability is concerned with the simultaneous transmission of meaning and data (semantics). This is done by including metadata, which link each data element to a controlled, common vocabulary.One most notable feature in the proposed system is its integration with a trusted electronic authentication system such as BankID. Creating a verifiable credential based on BankID would bootstrap the initial trust and make the system interoperable with the existing traditional solutions. Financial organizations can verify any documents issued by various organizations easily in a secure way as long as they trust the issuer of the organization. This enables any credential to be used as widely as possible and across multiple domains while being completely secure and user-centric.
- Efficiency. Compared to existing methods, the potential efficiencies of the proposed method of online loan processing and document verification is far-ranging. There is usually a certain waiting time involved in verifying the authenticity of documents. This is because the verification is either done manually, through collaborative networks, or by verifying documents against different registries that may take a few days to multiple weeks, since financial institutions are heavy with regulations and this process is critical. Moreover, the verifier has to have some kind of connection with the issuer, i.e., when a user presents their documents to a verifier, it connects to the issuer through an API call or by using other ways of communication and then returns the response. This requires a handshake at different levels, taking more time and resources for the verifier.On the other hand, authenticity in the proposed method can be digitally verified in seconds, taking business efficiency to a new level. As credentials are cryptographically verifiable in real time, this would also improve user experience. In other words, it reduces the friction between the organization and the customer. In addition, in the proposed system, unlike collaborative networks, different levels of handshakes are limited to two levels, i.e., between holder and verifier, significantly improving the time for processing an application. Further, reducing the number intermediaries also reduces costs as financial institutions do not need to pay a third party for the verification services.
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Imam, I.T.; Arafat, Y.; Alam, K.S.; Shahriyar, S.A. DOC-BLOCK: A Blockchain Based Authentication System for Digital Documents. In Proceedings of the 2021 Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV), Tirunelveli, India, 4–6 February 2021; pp. 1262–1267. [Google Scholar] [CrossRef]
- Roychoudhury, S.; Bellarykar, N.; Kulkarni, V. A NLP Based Framework to Support Document Verification-as-a-Service. In Proceedings of the 2016 IEEE 20th International Enterprise Distributed Object Computing Conference (EDOC), Vienna, Austria, 5–9 September 2016; pp. 1–10. [Google Scholar] [CrossRef]
- Lakmal, C.; Dangalla, S.; Herath, C.; Wickramarathna, C.; Dias, G.; Fernando, S. IDStack—The common protocol for document verification built on digital signatures. In Proceedings of the 2017 National Information Technology Conference (NITC), Colombo, Sri Lanka, 14–15 September 2017; pp. 96–99. [Google Scholar] [CrossRef]
- Arner, D.W.; Zetzsche, D.A.; Buckley, R.P.; Barberis, J.N. The identity challenge in finance: From analogue identity to digitized identification to digital KYC utilities. Eur. Bus. Organ. Law Rev. 2019, 20, 55–80. [Google Scholar] [CrossRef]
- Preukschat, A.; Reed, D. Self-Sovereign Identity; Manning Publications: Shelter Island, NY, USA, 2021. [Google Scholar]
- Stokkink, Q.; Ishmaev, G.; Epema, D.; Pouwelse, J. A Truly Self-Sovereign Identity System. In Proceedings of the 2021 IEEE 46th Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 4–7 October 2021; pp. 1–8. [Google Scholar] [CrossRef]
- The World Wide Web Consortium (W3C). Verifiable Credentials Data Model v1.1. 2022. Available online: https://www.w3.org/TR/vc-data-model/ (accessed on 8 June 2022).
- W3C Credential Community Group. Decentralized Identifiers. 2022. Available online: https://www.w3.org/TR/did-core/ (accessed on 13 May 2022).
- The World Wide Web Consortium (W3C). JSON-LD 1.1. 2020. Available online: https://www.w3.org/TR/json-ld11/ (accessed on 28 May 2022).
- Fdhila, W.; Stifter, N.; Kostal, K.; Saglam, C.; Sabadello, M. Methods for Decentralized Identities: Evaluation and Insights. Int. Conf. Bus. Process. Manag. 2021, 428, 119–135. [Google Scholar]
- Decentralized Identity Foundation (DIF). DIF Presentation Exchange. 2022. Available online: https://identity.foundation/presentation-exchange/ (accessed on 18 September 2022).
- Tykn. Self-Sovereign Identity: The Ultimate Beginners Guide! 2021. Available online: https://tykn.tech/self-sovereign-identity/ (accessed on 20 June 2022).
- Mühle, A.; Grüner, A.; Gayvoronskaya, T.; Meinel, C. A survey on essential components of a self-sovereign identity. Comput. Sci. Rev. 2018, 30, 80–86. [Google Scholar] [CrossRef]
- Evernym. 2022. Available online: https://www.evernym.com/ (accessed on 18 September 2022).
- Sovrin. Sovrin Glossary v2. 2020. Available online: https://sovrin.org/library/glossary/ (accessed on 23 July 2022).
- Serto: Trust with Control. 2022. Available online: https://www.serto.id/ (accessed on 13 October 2022).
- ION: Decentralized Layer 2 Open Permissionless Identity Network. 2022. Available online: https://identity.foundation/ion/ (accessed on 13 October 2022).
- Trinsic: A Full-Stack Self-Sovereign Identity (SSI) Platform. 2022. Available online: https://trinsic.id/ (accessed on 23 July 2022).
- SpruceID: Your Keys, Your Data. 2022. Available online: https://www.spruceid.com/ (accessed on 13 October 2022).
- Stokkink, Q.; Pouwelse, J. Deployment of a blockchain-based self-sovereign identity. In Proceedings of the 2018 IEEE international conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1336–1342. [Google Scholar]
- Ferdous, M.S.; Chowdhury, F.; Alassafi, M.O. In search of self-sovereign identity leveraging blockchain technology. IEEE Access 2019, 7, 103059–103079. [Google Scholar] [CrossRef]
- Shuaib, M.; Alam, S.; Alam, M.S.; Nasir, M.S. Self-sovereign identity for healthcare using blockchain. Mater. Today Proc. 2021. [Google Scholar] [CrossRef]
- Kondova, G.; Erbguth, J. Self-sovereign identity on public blockchains and the GDPR. In Proceedings of the 35th Annual ACM Symposium on Applied Computing, Brno, Czech Republic, 30 March–3 April 2020; pp. 342–345. [Google Scholar]
- Dong, C.; Wang, Z.; Chen, S.; Xiang, Y. BBM: A blockchain-based model for open banking via self-sovereign identity. Int. Conf. Blockchain 2020, 12404, 61–75. [Google Scholar]
- Schlatt, V.; Sedlmeir, J.; Feulner, S.; Urbach, N. Designing a Framework for Digital KYC Processes Built on Blockchain-Based Self-Sovereign Identity. Inf. Manag. 2021, 59, 103553. [Google Scholar] [CrossRef]
- Marella, V.; Vijayan, A. Document Verification using Blockchain for Trusted CV Information. In Proceedings of the 2020 Advances in Information Systems Research (AMCIS), Virtual Conference, 10–14 August 2020; Volume 12. [Google Scholar]
- Hyperledger Foundation. Hyperledger Fabric. 2022. Available online: https://www.hyperledger.org/use/fabric (accessed on 12 October 2022).
- Soltani, R.; Trang Nguyen, U.; An, A. A New Approach to Client Onboarding Using Self-Sovereign Identity and Distributed Ledger. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1129–1136. [Google Scholar] [CrossRef]
- Parra Moyano, J.; Ross, O. KYC optimization using distributed ledger technology. Bus. Inf. Syst. Eng. 2017, 59, 411–423. [Google Scholar] [CrossRef]
- Hyperledger Foundation. Hyperledger Indy. 2022. Available online: https://www.hyperledger.org/use/hyperledger-indy (accessed on 12 October 2022).
- Bartolomeu, P.C.; Vieira, E.; Hosseini, S.M.; Ferreira, J. Self-Sovereign Identity: Use-cases, Technologies, and Challenges for Industrial IoT. In Proceedings of the 2019 24th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Zaragoza, Spain, 10–13 September 2019; pp. 1173–1180. [Google Scholar] [CrossRef]
- Othman, A.; Callahan, J. The Horcrux protocol: A method for decentralized biometric-based self-sovereign identity. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018; pp. 1–7. [Google Scholar]
- Wang, F.; De Filippi, P. Self-Sovereign Identity in a Globalized World: Credentials-Based Identity Systems as a Driver for Economic Inclusion. Front. Blockchain 2020, 2, 28. [Google Scholar] [CrossRef]
- De Cristo, F.S.; Shbair, W.M.; Trestioreanu, L.; State, R.; Malhotra, A. Self-Sovereign Identity for the Financial Sector: A Case Study of PayString Service. In Proceedings of the 2021 IEEE International Conference on Blockchain (Blockchain), Melbourne, Australia, 6–8 December 2021; pp. 213–220. [Google Scholar] [CrossRef]
- Affinidi. Protecting Your Driver’s License—A Use Case for Verifiable Credentials. 2021. Available online: https://academy.affinidi.com/protecting-your-drivers-license-a-use-case-for-verifiable-credentials-25d22aeac05b (accessed on 18 August 2022).
- Veramo. 2022. Available online: https://veramo.io/ (accessed on 13 June 2022).
- Mattr. A New World of Data and Digital Trust. 2022. Available online: https://mattr.global/ (accessed on 23 July 2022).
- Civic. Civic Secure Identity Ecosystem. 2022. Available online: https://www.civic.com (accessed on 12 October 2022).
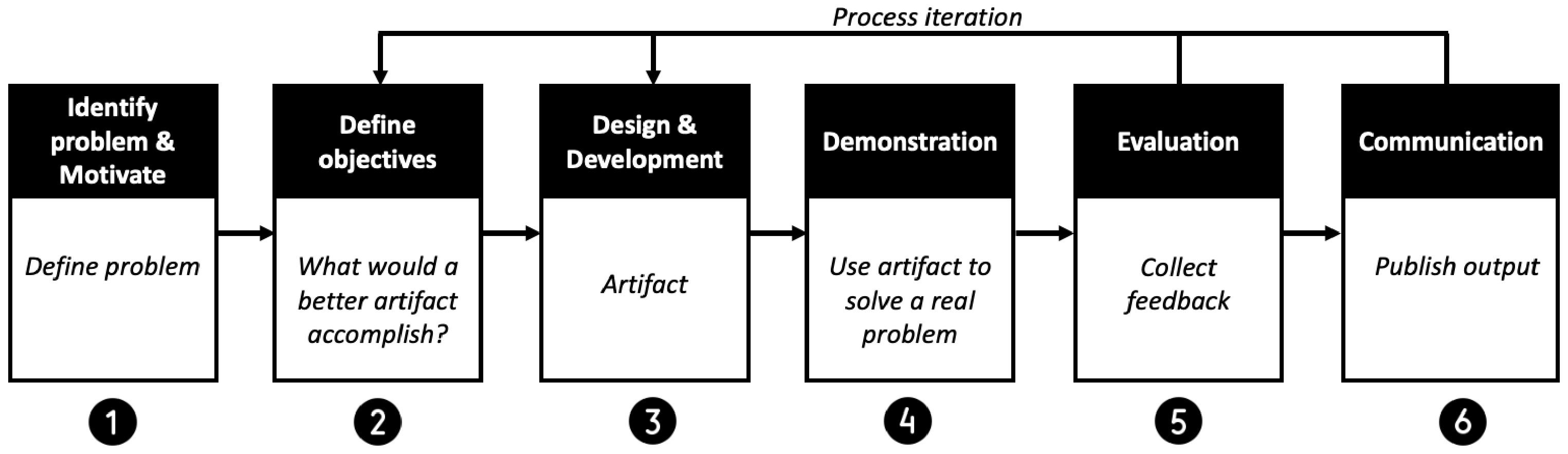
- Peffers, K.; Tuunanen, T.; Rothenberger, M.A.; Chatterjee, S. A design science research methodology for information systems research. J. Manag. Inf. Syst. 2007, 24, 45–77. [Google Scholar] [CrossRef]
- Bisandu, D.B. Design science research methodology in computer science and information systems. Int. J. Inf. Technol. 2016, 5, 55–60. [Google Scholar]
- Wieringa, R. Design science methodology: Principles and practice. In Proceedings of the 32nd ACM/IEEE International Conference on Software Engineering-Volume 2, Cape Town, South Africa, 1–8 May 2010; pp. 493–494. [Google Scholar]
- Peffers, K.; Rothenberger, M.; Tuunanen, T.; Vaezi, R. Design science research evaluation. In Proceedings of the International Conference on Design Science Research in Information Systems, Las Vegas, NV, USA, 14–15 May 2012; pp. 398–410. [Google Scholar]
- Zetzsche, D.A.; Buckley, R.P.; Arner, D.W. Digital ID and AML/CDD/KYC utilities for financial inclusion, integrity and competition. J. Econ. Transform. 2018, 47, 133–142. [Google Scholar]
- Cheng, L.; Liu, F.; Yao, D. Enterprise data breach: Causes, challenges, prevention, and future directions. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2017, 7, e1211. [Google Scholar] [CrossRef]
- Holtfreter, R.E.; Harrington, A. Data breach trends in the United States. J. Financ. Crime 2015, 22, 242–260. [Google Scholar] [CrossRef]
- Confessore, N. Cambridge Analytica and Facebook: The Scandal and the Fallout So Far. The New York Times, 2018; Volume 4. [Google Scholar]
- Vishwanath, T.; Kaufmann, D. Towards Transparency in Finance and Governance. 1999. Available online: https://ssrn.com/abstract=258978 (accessed on 28 May 2022).
- International Telecommunication Union (ITU). X.509. 2020. Available online: https://www.itu.int/rec/T-REC-X.509 (accessed on 28 May 2022).
- López, M.A. The Future of Identity: Self Sovereignity, Digital Wallets and Blockchain. Available online: shorturl.at/bR146 (accessed on 20 June 2022).
- Corrado, E. The Importance of Open Access, Open Source, and Open Standards for Libraries. Available online: http://www.istl.org/05-spring/article2.html (accessed on 24 September 2022).
- Cerri, D.; Fuggetta, A. Open standards, open formats, and open source. J. Syst. Softw. 2007, 80, 1930–1937. [Google Scholar] [CrossRef]
- Jacobson, D.; Brail, G.; Woods, D. APIs: A Strategy Guide; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2012. [Google Scholar]
- Lalchandani, N.; Jiang, F.; Jeong, J.J.; Zolotavkin, Y.; Doss, R. Evaluating the Current State of Application Programming Interfaces for Verifiable Credentials. In Proceedings of the 2021 18th International Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 13–15 December 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Hyperledger Foundation. Hyperledger: Open Source Blockchain Technologies. 2022. Available online: https://www.hyperledger.org/ (accessed on 12 June 2022).
- Affinidy. 2022. Available online: https://www.affinidi.com/ (accessed on 12 June 2022).
- Helmy, N. Adding DID ION to MATTR VII. 2021. Available online: https://medium.com/mattr-global/adding-did-ion-to-mattr-vii-d56bdb7a2fde (accessed on 12 June 2022).
- Bolte, P. Self-Sovereign Identity: Development of an Implementation-Based Evaluation Framework for Verifiable Credential SDKs. Available online: https://bolte.cloud/assets/ssi_master_thesis.pdf (accessed on 12 June 2022).
- Affinidi. Schema Manager Portal. 2022. Available online: https://ui.schema.affinidi.com/schemas (accessed on 13 May 2022).
- React—A JavaScript Library for Building User Interfaces. 2022. Available online: https://reactjs.org/ (accessed on 15 July 2022).
- Gackenheimer, C. What is react? In Introduction to React; Springer: Berlin/Heidelberg, Germany, 2015; pp. 1–20. [Google Scholar]
- Signicat. Norwegian BankID. Available online: https://developer.signicat.com/enterprise/identity-methods/norwegian-bankid.html#oidc-response-example (accessed on 20 August 2022).
- Lan pa Nett. 2021. Available online: https://www.lane-penger.com/lan-pa-minuttet/ (accessed on 15 July 2022).
- Signicat. Digital Identity Solutions for the Full Customer Journey. 2022. Available online: https://www.signicat.com/ (accessed on 28 May 2022).
- NTA. Norwegian Tax Administration. 2022. Available online: https://www.skatteetaten.no/ (accessed on 28 May 2022).
- NTNU. Norwegian University of Science and Technology. 2022. Available online: https://www.ntnu.no/ (accessed on 28 May 2022).
- Seabury, C. The Cost of Free Markets. 2022. Available online: https://www.investopedia.com/articles/economics/08/free-market-regulation.asp (accessed on 12 June 2022).
- Ruff, T. Verifiable Credentials 101 for SSI with Tyler Ruff- Decentralized Digital Identity. 2018. Available online: https://www.youtube.com/watch?v=6O_iJnhIh5o (accessed on 15 June 2022).
- Norwegian Tax Administration. Tax assessment. 2022. Available online: https://www.skatteetaten.no/en/person/taxes/tax-assessment/ (accessed on 28 June 2022).
- DIF. Decentralized Identity Foundation. 2022. Available online: https://identity.foundation (accessed on 10 June 2022).
- Equifax Data Breach Settlement: Am I affected? Available online: https://www.equifaxbreachsettlement.com/ (accessed on 13 June 2022).
- Criddle, C. Facebook Sued over Cambridge Analytica Data Scandal. 2020. Available online: https://www.bbc.com/news/technology-54722362 (accessed on 19 August 2022).
- Supra, J. First American Financial Corporation Settles SEC Case for $487,616 for Cybersecurity Data Breach and Disclosure Failures. 2021. Available online: https://www.jdsupra.com/legalnews/first-american-financial-corporation-1557953 (accessed on 19 August 2022).
- Hou, J.L.; Huang, C.H. A model for document validation using concurrent authentication processes. J. Comput. Inf. Syst. 2008, 49, 65–80. [Google Scholar]

| DocBlock | IDStack | Marella and Vijayan | Schlatt et al. | Soltani et al. | |
|---|---|---|---|---|---|
| Year | 2021 | 2017 | 2020 | 2022 | 2018 |
| Use case | Document verification | Document verification | Document verification | eKYC | eKYC |
| Aligns with SSI standards | No | No | No | Yes | Yes |
| User control | No | No | No | Yes | Yes |
| User authentication | Yes | No | No | Yes | Yes |
| Validation (authenticity and integrity) | SHA-256 hashing, ECDSA signatures | Text extraction, self-signed certificates | SHA-256 hashing, digital signatures | Cryptographic proofs in the form of VCs | Secure DID connections and VCs |
| Verification process | Automated | Manual | Automated | Automated | Automated |
| Use of blockchain | Yes (Ethereum) | No | Yes (Hyperledger Fabric) | Yes | Yes (Hyperledger Indy) |
| Data storage | IPFS | Local database (SQL) | Blockchain (hashes), local database (NoSQL) | Mobile and cloud wallets | Mobile and cloud wallets |
| Technologies | Smart contracts, Metamask wallet | APIs, JSON documents | Smart contracts, APIs | DIDs, VCs | DIDs, VCs |
| Proof of concept | Yes | Yes | Yes | No | Yes |
| Mattr | Trinsic | Affinidi | Veramo | |
|---|---|---|---|---|
| Well-documented APIs | Yes (website and Postman) | Yes (website) | Yes (website and Postman) | No (hard to follow) |
| Developer Support | Yes (Slack) | Good (chatbot and Slack) | Yes (Discord) | Yes (GitHub) |
| Aligns with SSI standards | Yes | Yes | Yes | Yes |
| Availability of fully functional demo app | No | Yes | Yes | No |
| Regularly maintained | Yes | Yes | Yes | Yes |
| Supported DID | did-key, did:ion, did:web | did:sov, did:peer, did:key, did:web | did-elem, did:jolo | did:ethr, did:web, did:key |
| Distributed Ledgers | Bitcoin | Sovrin | Etherium | Etherium |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Satybaldy, A.; Subedi, A.; Nowostawski, M. A Framework for Online Document Verification Using Self-Sovereign Identity Technology. Sensors 2022, 22, 8408. https://doi.org/10.3390/s22218408
Satybaldy A, Subedi A, Nowostawski M. A Framework for Online Document Verification Using Self-Sovereign Identity Technology. Sensors. 2022; 22(21):8408. https://doi.org/10.3390/s22218408
Chicago/Turabian StyleSatybaldy, Abylay, Anushka Subedi, and Mariusz Nowostawski. 2022. "A Framework for Online Document Verification Using Self-Sovereign Identity Technology" Sensors 22, no. 21: 8408. https://doi.org/10.3390/s22218408
APA StyleSatybaldy, A., Subedi, A., & Nowostawski, M. (2022). A Framework for Online Document Verification Using Self-Sovereign Identity Technology. Sensors, 22(21), 8408. https://doi.org/10.3390/s22218408







