Exploring the Full Potentials of IoT for Better Financial Growth and Stability: A Comprehensive Survey
Abstract
:1. Introduction
- In-depth examination of IoT developments and architecture: By thoroughly studying the developments in IoT and its intricate architecture, this paper offers valuable insights into the current state of IoT technology, setting a strong foundation for further research and innovation.
- Rigorous analysis of trials and challenges: Through a careful analysis of the associated trials and challenges faced in the implementation of IoT, this study provides a clear understanding of the obstacles and potential roadblocks in IoT adoption, enabling stakeholders to proactively address these issues.
- Holistic assessment of orientations and motivations driving IoT adoption: The comprehensive analysis of the orientations and motivations behind IoT adoption across diverse domains offers a rich understanding of the driving forces behind the rapid growth of IoT applications, empowering decision-makers to align their strategies with market trends.
- Investigation of IoT technology adoption: By delving into the adoption of IoT technologies, this paper uncovers the transformative potential of IoT across various sectors, revealing the opportunities and applications that can revolutionize businesses and industries.
- Forward-looking insights on future research challenges and open issues: With a careful review of future research challenges and thoughtful discussions on open issues, this study provides a roadmap for future researchers and practitioners to explore untapped possibilities and forge new frontiers in IoT advancements.
2. IoT Foundations: Literature Review
2.1. A Comprehensive Review of the Foundational Concepts of IoT
- Scalability and Flexibility: The versatility of IoT allows seamless expansion and integration of new devices and technologies. The scalability of IoT systems ensures that they can adapt and accommodate diverse use cases [37].
- Real-Time Responsiveness: The real-time nature of IoT enables immediate actions and responses. IoT systems can react promptly to changing conditions, making them ideal for applications requiring quick decision-making and response times [28].
- Energy Efficiency: IoT devices are designed with energy efficiency in mind, ensuring prolonged battery life and reduced energy consumption. This characteristic is particularly vital for IoT applications that rely on battery-powered devices [41].
- Ubiquitous Access: IoT extends beyond traditional computing devices and offers ubiquitous access to data and services. Users can interact with IoT systems through smartphones, wearables, and other connected devices from anywhere at any time [28].
- Sensors: Sensors are crucial components in IoT devices as they enable the collection of real-time data from the physical environment [42,43]. Various types of sensors, such as temperature sensors, humidity sensors, motion sensors, light sensors, and proximity sensors, provide valuable insights into the surrounding conditions [44,45].
- Smart Home Devices: Smart home devices include smart thermostats, smart lights, smart locks, and smart appliances that can be controlled remotely or automated to optimize energy usage and enhance home security and comfort [11].
- Connected Vehicles: IoT has revolutionized the automotive industry with connected vehicles that gather data and provide real-time insights on vehicle performance, maintenance needs, and driver behavior [31].
- Industrial IoT (IIoT) Devices: In industrial settings, IoT devices play a crucial role in monitoring and optimizing manufacturing processes, predictive maintenance, and ensuring worker safety [42].
- Agricultural IoT Devices: IoT is transforming agriculture with devices like smart irrigation systems, soil sensors, and livestock monitoring systems, enabling precision farming and maximizing crop yields [13].
- Connected Consumer Electronics: Many everyday consumer electronics, such as smart TVs, smart speakers, and smart home assistants, are IoT devices that provide a seamless user experience and connectivity [43].
- IoT-A (Internet of Things—Architecture): IoT-A is a research project that aims to define a reference architecture for IoT systems. It provides a scalable and flexible framework, focusing on interoperability. The architecture is divided into three main views: the Application View, the Information View, and the Communication View. IoT-A emphasizes modularity and reusability of components, making it easier to design and deploy IoT solutions across various domains.
- AWS IoT Architecture: Amazon Web Services (AWS) offers a comprehensive IoT architecture that leverages its cloud services. AWS IoT provides a scalable and secure platform for connecting devices, managing data, and building applications. It includes components like AWS IoT Core for device management and connectivity, AWS IoT Greengrass for edge computing capabilities, and AWS IoT Analytics for data processing and insights.
- Microsoft Azure IoT Reference Architecture: Microsoft Azure provides a robust IoT reference architecture to help developers design scalable and secure IoT solutions. It incorporates various Azure services, such as Azure IoT Hub for device connectivity, Azure IoT Edge for edge computing, and Azure IoT Central for simplified device management.
- IBM IoT Reference Architecture: IBM offers an IoT reference architecture that covers the entire IoT ecosystem, from edge devices to cloud-based applications. It emphasizes integration with the IBM Watson IoT Platform for device management, data processing, and AI-powered insights.
- IoTivity: IoTivity is an open-source IoT framework developed by the Open Connectivity Foundation (OCF). It aims to provide a standardized and interoperable approach to IoT device connectivity and communication. IoTivity supports various IoT protocols, enabling seamless interoperability between different devices and ecosystems.
- Google Cloud IoT Architecture: Google Cloud Platform (GCP) offers an IoT architecture that leverages Google Cloud IoT Core, Google Cloud Pub/Sub, and other GCP services. It provides a robust platform for device management, data ingestion, and analytics in IoT applications.
- Hyperledger Caliper: Hyperledger Caliper is an open-source project under the Linux Foundation’s Hyperledger umbrella. While not a full IoT architecture, it allows benchmarking different blockchain frameworks for IoT use cases, focusing on performance evaluation.
- ARM mbed: ARM’s mbed platform aims to provide a scalable and secure foundation for IoT devices and applications. It offers a suite of tools, operating systems, and device management capabilities that make it easier for developers to create IoT solutions.
- OpenFog Consortium Architecture: The OpenFog Consortium focuses on edge computing in IoT. It has developed an architecture that addresses the challenges of deploying IoT and AI solutions at the edge of the network, emphasizing low-latency processing, data security, and scalability.
2.2. The Historical Development and Evolution of IoT Technologies
- Early Concepts (1980s–1990s): The foundational ideas of IoT can be traced back to the 1980s and 1990s when researchers and technologists began envisioning a world where devices could be interconnected and communicate with each other. At this stage, the focus was mainly on machine-to-machine (M2M) communication and remote monitoring of industrial systems [21,43,54].
- Emergence of RFID (Radio Frequency Identification) (1990s–2000s): The development of RFID technology marked a significant step in the evolution of IoT. RFID tags enabled the identification and tracking of objects and assets using radio waves, laying the groundwork for the idea of a connected world where objects and devices could be uniquely identified and accessed [42,50,51,52,53,54].
- Proliferation of Internet Connectivity (2000s): The widespread adoption of the Internet in the early 2000s paved the way for the expansion of IoT technologies. The increasing availability of internet connectivity allowed devices and sensors to connect and transmit data over the web, creating the basis for IoT applications [22,43].
- Advancements in Sensor Technology (2000s): The improvement and miniaturization of sensors during this period enabled the integration of various types of sensors into devices, making them capable of capturing data from their environment. These sensors became essential components of IoT devices, enabling them to collect real-time data [47,54].
- Smart Home and Wearable Devices (2010s): The 2010s saw the rise of consumer-oriented IoT devices, such as smart home appliances and wearable devices. Smart thermostats, smart speakers, fitness trackers, and smartwatches gained popularity, showcasing the potential of IoT in enhancing daily life and user experiences [11,12].
- Industrial IoT (IIoT) and Industry 4.0 (2010s): The convergence of IoT with industrial applications, known as the Industrial Internet of Things (IIoT) or Industry 4.0, became prominent. IIoT revolutionized manufacturing and industrial processes by enabling real-time monitoring, predictive maintenance, and data-driven decision-making [42].
- Cloud Computing and Big Data (2010s): The advent of cloud computing and big data analytics provided the necessary infrastructure and tools to process and analyze the vast amounts of data generated by IoT devices. Cloud platforms allow for scalable and flexible data storage and processing, enhancing the capabilities of IoT applications [28,33,38,52].
- Edge Computing (2010s): As IoT applications grew, the limitations of relying solely on cloud computing for data processing became apparent. Edge computing emerged as a solution, enabling data processing and analysis to occur closer to the data source, reducing latency, and improving real-time responsiveness [33,52].
- Connectivity Advancements and 5G (2010s–2020s): The deployment of 5G networks and other connectivity advancements further accelerated the growth of IoT technologies. The high-speed, low-latency, and massive connectivity capabilities of 5G opened up new possibilities for IoT applications in various domains [56].
- AI and Machine Learning Integration (2020s): The integration of artificial intelligence (AI) and machine learning (ML) with IoT technologies has unlocked powerful insights and automation capabilities. AI-driven analytics enable more sophisticated data processing and predictive decision-making in IoT applications [16,32,34].
3. Materials and Methods
3.1. Related Literature and Research Contributions
- Real-time Insights into the latest advancements, case studies, and practical applications of IoT technologies, to provide up-to-date information empower researchers, engineers, and innovators to make informed decisions and stay ahead of emerging trends.
- Accelerating Innovation by sharing early-stage prototypes, experimental results, and proof-of-concept projects, grey literature fosters a culture of innovation.
- Practical Implementation Guidance to provide valuable assistance to practitioners looking to deploy IoT systems effectively.
- Use Case Exploration to inspire new use case ideas and encourage cross-industry collaboration.
- Addressing Challenges by enabling researchers and practitioners to share their approaches to overcoming these challenges, thus fostering a collective effort to find viable solutions.
3.2. Formulation of Research Questions
- Q1.
- How extensive is the body of published papers focused on IoT?
- Q2.
- What are the defining characteristics of IoT architecture?
- Q3.
- Which cutting-edge technologies are currently being employed for IoT simulation and implementation?
- Q4.
- What are the foremost challenges of IoT that researchers have diligently investigated?
- Q5.
- What are the most crucial and groundbreaking applications of IoT?
- Q6.
- What pertinent issues persist and remain open for further investigation?
3.3. PRISMA Systematic Searching Strategy
3.3.1. Identification: Selection Criteria
- C1: Papers published before 2013 were excluded.
- C2: Incomplete papers or papers presenting only a table of contents, abstracts of conferences, tutorials, keynote talks, technical reports, editorial papers, or short papers were excluded, as were papers not written in English.
- C3: Papers lacking abstracts or full-text availability were omitted.
- C4: Papers not directly aligned with the proposed research questions were also excluded, ensuring a laser-focused approach to our study.
3.3.2. Screening Stage
- Title and Abstract Screening: In the initial stage, researchers diligently review the titles and abstracts of all retrieved studies, carefully identifying those that align with the research question. Studies that do not meet the inclusion criteria or lack relevance to the topic of interest are expeditiously excluded at this stage.
- Full-Text Screening: Following the title and abstract screening, the remaining studies undergo in-depth scrutiny of their full texts. This comprehensive step involves an extensive examination of the study content to ascertain whether it satisfies the predetermined inclusion criteria. Studies that fail to meet the criteria or lack sufficient information are systematically excluded from the final selection.
3.3.3. Eligibility
3.4. Quality Assessment
3.5. Data Extraction
4. Study Results
4.1. Results Related to IoT Technologies
4.1.1. Hardware-Level
4.1.2. Network-Level
- Personal Area Network (PAN): PAN is the smallest network type, designed for connecting devices close to each other, typically within a range of a few meters. It is commonly used for communication between personal devices, such as smartphones, smartwatches, and other wearable gadgets.
- Local Area Network (LAN): LAN covers a relatively small geographic area, such as a home, office, or campus. It enables devices to communicate within a confined space and is often used to connect IoT devices within a specific location, like smart thermostats, security cameras, and printers.
- Wide Area Network (WAN): WAN encompasses a larger geographic area and is used to connect devices across broader regions. Cellular networks and satellite connections are examples of WAN technologies that facilitate communication between IoT devices spread over significant distances.
- Wireless Sensor Network (WSN): WSN consists of interconnected sensors that collaborate to collect and transmit data. These networks are often used for monitoring and control applications, such as environmental sensing, agriculture, and industrial automation.
- Industrial IoT (IIoT) Network: IIoT networks are tailored for industrial settings and involve connecting various devices and systems in manufacturing, energy, transportation, and other sectors. IIoT optimizes processes, enhances productivity, and enables predictive maintenance.
- Mesh Network: In a mesh network, IoT devices are interconnected, creating multiple pathways for data to travel. This redundancy enhances network reliability and coverage, making it suitable for applications requiring high resilience and extensive coverage.
- Cellular Network: Cellular networks leverage existing telecommunications infrastructure to provide IoT connectivity. They offer reliable, widespread coverage, making them suitable for applications like fleet management, asset tracking, and smart cities.
- Satellite Network: Satellite networks provide global IoT coverage, particularly in remote or inaccessible areas. They are vital for applications such as maritime tracking, remote environmental monitoring, and disaster response.
- LPWAN (Low Power Wide Area Network): LPWAN technologies, like LoRaWAN and Sigfox, enable long-range communication with minimal power consumption. They are ideal for connecting battery-operated devices like smart meters and agricultural sensors.
- Networks (5G): The introduction of 5G networks brings higher data speeds, lower latency, and increased device connectivity. It enhances IoT applications that demand real-time responsiveness, such as autonomous vehicles and augmented reality.
4.1.3. Software Level
4.1.4. Storage Level
4.2. Results Related to IoT Challenges
4.2.1. Security and Privacy Challenges
- Confidentiality: At the heart of data security lies the principle of confidentiality. These imperative delegates the imposition of stringent controls on data access, achieved through a harmonious blend of physical and logical restrictions. Failing to uphold confidentiality casts a dire shadow, potentially leading to unauthorized data exposure, undermining trust, and paving the way for cyber espionage.
- Integrity: The integrity of data forms the backbone of accurate decision-making and seamless operations. Ensuring data remains unadulterated and up to date is critical. Any compromise to data integrity can sow the seeds of misinformation, fueling erroneous actions, and eroding stakeholders’ confidence in the system’s veracity.
- Availability: The unimpeded accessibility of data to authorized individuals is a linchpin of operational efficacy. Delays or interruptions in data availability can cripple critical processes, hinder informed decision-making, and stifle the timely execution of actions, potentially leading to operational breakdowns.
- Authenticity: The assurance of authentic communication within the IoT ecosystem is essential to avoid fraudulent interactions. The ability to unequivocally verify the identity of communication partners establishes the bedrock of trust and ensures that data exchanges occur with the intended entities. Failure to ensure authenticity opens the door to impersonation and unauthorized access.
- Privacy: The preservation of individual privacy stands as a cardinal principle, shielding individuals from intrusive intrusions and unwarranted disruptions. Neglecting privacy not only infringes upon personal rights but also invites breaches that can tarnish the reputation of the system’s operators, potentially leading to legal repercussions.
- Non-repudiation: Warranting the veracity of messages or transactions is integral to a secure IoT ecosystem. Non-repudiation precludes the possibility of a sender denying their involvement or the occurrence of a transaction. Its absence leaves room for malicious repudiation, complicating dispute resolution and eroding trust.
- Key Management: The management of cryptographic keys is an essential aspect of data security, ensuring compliance with established standards and regulations. Inadequate key management can result in unauthorized access, compromised data, and regulatory non-compliance, bearing far-reaching legal and financial consequences.
- Symmetric Encryption: A swiftness characterizes symmetric encryption, where both encryption and decryption pivot upon a singular key—the cryptic “secret key.” While speed is its hallmark, this technique mandates a critical prelude—an accord between sender and receiver on the elusive shared key. A delicate choice, this key’s dissemination necessitates utmost care, as an ill-fated misplacement can lead to the key’s possession by unauthorized entities, thus compromising the very tenets of confidentiality.
- Asymmetric Encryption: In contrast, asymmetric encryption is a system of duality, orchestrated through a key pair: the public and private keys. The recipient, designated as the (forthcoming) guardian of the keys, ensures that potential senders access the public key. Upon this foundation, the sender adroitly employs the recipient’s key to encode the message, setting the stage for an intricate dance wherein the recipient wields their private key to decode this encrypted enigma.
4.2.2. Interoperability and Efficiency Challenges
4.2.3. Data Management and Analytics Challenges
4.2.4. Network Complexity and Bandwidth Challenges
4.2.5. Scalability
4.2.6. Power Consumption and Battery Life Challenges
4.3. Results Related to General IoT Applications
4.3.1. Smart Cities
- The smart economy endeavors to fortify the city’s commercial prowess, wherein parameters such as innovation, entrepreneurship, labor market adaptability, productivity, and global integration coalesce to determine competitiveness on the financial stage.
- Intelligent citizens embody the collective human and social capital, encompassing not only the educational attainment of residents but also their diversity, open-mindedness, creative faculties, quality of social interactions, and civic engagement.
- Intelligent governance orchestrates a transparent, all-encompassing administrative modality that nurtures robust civic participation.
- Intelligent mobility accentuates both local and international accessibility, facilitated by an interconnected ICT infrastructure and innovative, sustainable, secure transportation systems.
- An intelligent environment fosters ecological stewardship, advocating for a superior quality of life through the nurturing of green spaces, enhancement of air quality, sustainable resource management, and environmental safeguarding. Exemplars of such management are observable in localized eco-districts.
- An intelligent lifestyle encompasses the gamut of life-quality constituents, spanning cultural enrichment, healthcare provisioning, housing, education, tourism, safety enforcement, and social cohesiveness.
4.3.2. Smart Home
- Enhanced time management: The programming of mundane tasks such as shutter control, alarm activation, or gate manipulation via smartphones culminates in a significant temporal dividend.
- Augmented security: Through automation systems, homes are fortified against potential break-ins and intrusions.
- Prudent energy consumption: Automation empowers the modulation of thermostats based on temporal parameters, ushering in the benefits of sustained ambient temperatures.
4.3.3. Remote Learning
4.3.4. Transportation
- Automating tasks hitherto reliant on human intervention.
- Real-time monitoring and dynamic adjustment of road network performance.
- Acquisition of data previously garnered through costly infrastructural investments, now harnessed from more prolific sources.
- The transition from analyses rooted in historical data to those propelled by intelligent systems equipped with real-time data analytics.
- Empowerment of road users with choices influenced by a plethora of channels, encompassing mobile devices and in-vehicle systems, supplanting the erstwhile monopoly of road signs.
4.3.5. Wearables
- Empowerment through smart locks, wherein doors yield to the prompt of a smartphone, harmonizing convenience with security.
- Strategic modulation of lights and thermostats through intelligent control mechanisms, engendering energy conservation and operational cost containment.
- The advent of voice assistants—such as Alexa or Siri—enables seamless calendar management, note-taking, reminders, email dispatch, and messaging, underscoring an era of intuitive interactivity.
- The orchestration of connected printer sensors that discern ink levels, triggers the procurement of additional cartridges, thereby precluding disruptions to workflow.
- Surveillance cameras, rendered “smart” by connectivity, proffer the ability to transmit live content to the Internet, extending the purview of surveillance beyond physical confines.
4.3.6. Smart Retail
4.3.7. E-Health
- The burgeoning landscape of wearables, evolving at a rapid commercial clip, offers insights into the behavior of individuals and materials. From headgear to timepieces to footwear, the spectrum of IoT-enabled wearables is expanding, capturing metrics like heart rate, caloric intake and expenditure, food consumption patterns, and an intricate web of behavioral facets. While ethical and philosophical challenges remain salient, the potential applications of this deluge of information, whether predictive or therapeutic, are prodigious.
- The proliferation of real-time environmental awareness, propelled by the impending deluge of health-related data, beckons a plethora of ethical quandaries. Nevertheless, even when anonymized, this trove of information holds utility as a decision-making compass for public health initiatives and individual diagnoses. Expedited diagnoses during rapid disease outbreaks can tip the balance between life and death.
- Decision support systems are anchored in the analysis of data gleaned from sensor networks, offering the potential for predictive maintenance and real-time monitoring, thus nurturing the prospect of continuous enhancement.
- Streamlined manufacturing processes within healthcare institutions stand to gain traction. Elevated data management efficacy can empower hospitals to bolster productivity and optimize the utilization of critical equipment through enhanced scheduling. Expedited access to diagnostics like MRI scans can manifest as a pivotal determinant in patient outcomes, exemplifying the IoT’s capacity to chart optimal usage patterns for such assets.
- Resource consumption optimization bears transformative promise, potentially influencing physician remuneration paradigms. The profound reservoirs of patient-specific data, encompassing both individual profiles and broader demographics, hold the potential to accurately gauge care efficacy, treatment outcomes, and anomalies.
- Autonomous systems operating within open environments echo the ethos of preventive healthcare. Sensors and mobile applications, intertwined with smartphones, wield the potential to proactively detect diseases and instigate preemptive treatments. Moreover, the quantification of risks inherent in patient interactions emerges within the purview of IoT’s capabilities.
4.3.8. Industrial Internet
4.3.9. Smart Supply Chain
- Enter the domain of connected forklifts, a real-time locational awareness coupled with automatic cargo recording, liberating operators from halts for manual data entry.
- The aegis of connected silos ushers in the optimization of truck loading, fostering security by detecting instances such as uncleaned trucks before loading.
- The orchestration of real-time monitoring of transport conditions can precipitate pre-emptive quality inspections, nipping anomalies in the bud.
- Augmented reality unfurls its utility as a “hands-free kit” within the warehouse, charting new avenues for seamless exploration.
- Embark upon drone-assisted inventory mechanisms, coupled with the finesse of 3D modeling of loading flows.
- SAP solutions, standing as pillars of support, shine particularly bright within these innovative narratives, underpinned by their unique capability to holistically integrate disparate processes [36].
4.3.10. Smarts Water System
4.3.11. Smart Irrigation
4.3.12. Precision Agricultural
4.3.13. Real-Time Monitoring
4.3.14. Agriculture Warehouse Monitoring
4.4. Results Related to IoT Applications in Finance
- Accelerated Decision-Making: At the nucleus of manifold business determinations, including investment choices, lies the edifice of exhaustive data analytics, corporate pattern decipherment, and market research. IoT devices emerge as instrumental assets for amassing and dissecting customer data, endowing businesses with pivotal insights into their exigencies, thereby expediting the decision-making matrix. The integration of IoT with contemporary frontiers like AI amplifies its potential, particularly within the precincts of the banking sphere. By harnessing AI, ML, and RPA, financial luminaries are endowed with the capability to adroitly scrutinize voluminous data troves, thereby concretizing judicious strategic decisions concerning resource allocation.
- Optimized Finance and Accounting Dynamics: The rhythmic cadence of finance and accounting entwines effective inter-departmental communication, akin to a system’s harmonious overture. Through the complete automation of these intricate conduits, organizations can transcend reliance on manual synchronization. IoT devices, constituting conduits for real-time data assimilation and cloud-based updates, alleviate the labyrinthine labyrinth of workflow intricacies, thereby salvaging precious temporal and cognitive resources otherwise expended in consolidating and structuring data disseminated across multifarious teams.
- Elevated Operational Prowess: IoT’s imprint reverberates in real-time surveillance of personnel and operational performance, bequeathing an avenue to vigilantly monitor working hours through IoT entities like wearables, whilst promptly unearthing any deviations through alert mechanisms. Moreover, IoT devices impart invaluable metrics, propelling the assessment of critical machinery’s optimal functionality—A testament to the flawless operations of apparatus like ATMs and consumer kiosks, thus underpinning their seamless efficacy.
4.4.1. IoT Payments
4.4.2. Customer Service
4.4.3. Identity Management
4.4.4. Credit Risk Management
4.4.5. Fraud Detection
4.4.6. Auditing
5. Discussion and Open Issues
5.1. Importance of IoT in Finance
- Enhanced Perception and Computing Skills: The evolution of computing, sensing, and data analytics is not just benefiting businesses but also enriching consumer experiences. Consider the transformation of smart fridges from being considered impractical and expensive a decade ago to becoming indispensable within ten years. This rapid evolution underscores the dynamic potential of IoT technologies in reshaping the financial landscape.
- Rising Consumer Awareness: Modern consumers are increasingly immersed in technology, fostering higher expectations for innovative devices. The willingness to embrace groundbreaking technologies and share personal data has expanded. Manufacturers are now less concerned about market acceptance and more focused on rapid innovation, driving intense competition and stimulating financial growth.
- Automation and Efficiency Advancements: IoT solutions typically lead to reduced operational costs and ensure continuous device availability. Improved automation and connectivity empower machines to exert enhanced control, leading to diminished human errors. The adoption of IoT technologies encourages a cascading effect where successful automation of one process incentivizes further automation, ultimately culminating in end-to-end efficiency.
5.2. IoT Architecture
5.2.1. Significance of IoT Architectures
- Data-Driven Insights: IoT architecture allows financial institutions to collect and analyze vast amounts of real-time data from various sources, such as customer transactions, market trends, and financial indicators. This data-driven approach enables more informed decision-making, helping financial organizations identify new opportunities, optimize processes, and develop innovative products and services.
- Enhanced Customer Experience: By leveraging IoT architecture, financial institutions can personalize customer interactions and services. Through IoT-enabled devices and applications, customers can access their accounts, make transactions, and receive tailored financial advice seamlessly. This enhanced customer experience leads to increased customer satisfaction, loyalty, and retention, ultimately driving financial growth.
- Operational Efficiency: IoT architecture optimizes operational processes within the financial sector. Automated systems and smart devices can monitor and manage assets, detect anomalies, and predict maintenance needs. This results in reduced operational costs, improved resource utilization, and streamlined workflows, contributing to overall financial efficiency and profitability.
- Risk Management and Fraud Prevention: IoT architecture enhances risk management by providing real-time monitoring and early detection of potential risks. For instance, IoT sensors can track changes in market conditions, asset values, or transaction patterns, enabling proactive risk mitigation. Additionally, IoT-driven security measures, such as biometric authentication and surveillance, help prevent fraud and protect sensitive financial data.
- Innovative Products and Services: IoT architecture enables the creation of innovative financial products and services that cater to evolving customer needs. For example, IoT-powered insurance solutions can offer usage-based premiums, where premiums are adjusted based on actual driving behavior or health monitoring. These novel offerings attract new customers and revenue streams.
- Cross-Sector Collaboration: IoT architecture encourages collaboration between the financial sector and other industries, such as retail, healthcare, and transportation. Joint ventures and partnerships can lead to the development of integrated solutions, like point-of-sale financing for retail purchases or healthcare payment plans tied to IoT health monitoring devices.
- Market Expansion: IoT architecture facilitates market expansion by reaching underserved or unbanked populations. Through IoT-enabled mobile banking, financial services can be delivered to remote areas without traditional banking infrastructure, increasing financial inclusion and opening new markets.
- Data Monetization: Financial institutions can leverage IoT-generated data as an additional revenue stream. By anonymizing and aggregating data, they can offer valuable insights to businesses, policymakers, and researchers. This data monetization strategy contributes to financial growth beyond core banking activities.
- Regulatory Compliance: IoT architecture can aid in meeting regulatory requirements by providing accurate and auditable records of transactions, processes, and customer interactions. This ensures transparency, accountability, and compliance, reducing legal risks and potential penalties.
5.2.2. Reference Architectures
- Standardization and Best Practices: IoT reference architectures establish a set of best practices and standardized approaches for building IoT solutions. This consistency helps ensure that IoT deployments are reliable, scalable, and maintainable.
- Interoperability: IoT reference architectures often promote interoperability by defining common protocols, communication standards, and data formats. This ensures that devices and systems from different vendors can work together seamlessly, fostering a more diverse and open IoT ecosystem.
- Scalability: Reference architectures help IoT systems scale effectively by guiding how to add more devices, gateways, and components as the IoT deployment grows. This scalability is crucial as IoT deployments can rapidly expand in terms of the number of connected devices.
- Security: Security is a paramount concern in IoT. Reference architectures typically include security best practices for device authentication, data encryption, access control, and other aspects of IoT security. Following these guidelines helps mitigate security risks.
- Reduced Development Time and Costs: IoT reference architectures can significantly reduce development time and costs by providing a well-defined structure and reusable components. Developers can leverage existing architectural patterns and design principles rather than starting from scratch.
- Flexibility: While reference architectures provide a structured framework, they are often flexible enough to accommodate various use cases and industries. They can be adapted to specific requirements while maintaining a solid foundation.
- Ecosystem Growth: IoT reference architectures encourage the growth of the IoT ecosystem by making it easier for organizations and developers to enter the market. They can accelerate innovation and drive the development of new IoT solutions.
- Risk Mitigation: By following established reference architectures, organizations can reduce the risk of project failure or costly mistakes. These architectures are based on proven principles and real-world experiences, helping organizations make informed decisions.
- IoT-A: IoT-A (IoT Architecture) is an architecture developed by the European Union’s IoT research project. It focuses on the architectural aspects of IoT, including the modeling of IoT systems, resource management, and data processing.
- IBM IoT Reference Architecture: IBM has created a comprehensive IoT reference architecture that covers device management, connectivity, data processing, analytics, and application enablement. It emphasizes the importance of data-driven insights in IoT solutions.
- Industrial Internet Consortium (IIC) IoT Reference Architecture: IIC, a consortium focused on industrial IoT, has published an IoT reference architecture that addresses the specific needs of industrial applications, including manufacturing, energy, and healthcare.
- Microsoft Azure IoT Reference Architecture: Microsoft offers its reference architecture for building IoT solutions on its Azure cloud platform. It covers device connectivity, data processing, analytics, and integration with Azure services.
- AWS IoT Reference Architectures: Amazon Web Services (AWS) provides various reference architectures for IoT applications, including edge computing, data processing, and serverless IoT.
- Open Connectivity Foundation (OCF): OCF has defined IoT reference architecture for interoperable and secure connectivity among IoT devices. It focuses on standardizing communication protocols and data models.
- IETF IoT Reference Architectures: The Internet Engineering Task Force (IETF) has produced a series of RFCs (Request for Comments) related to IoT reference architectures and security considerations, emphasizing the importance of secure communication.
5.3. Current Advances to Simulate or Implement IoT
- Message queuing systems play a pivotal role in facilitating crucial interactions between producers and consumers. Notably, 16% of the scrutinized papers employed message queuing systems. Among these, Mosquitto (47%), Kafka (23%), Apache ActiveMQ (9%), RabbitMQ (8%), and Celery (8%) emerged as the most utilized systems.
- In addressing the critical need for efficient data storage in IoT implementations, our examination revealed the prevalent usage of databases such as MySQL, Redis, MongoDB, HBase, SQLite, PostgreSQL, CouchDB, and DynamoDB. MySQL stood out as the most prevalent choice, constituting 31% of the selections.
- Cloud services play a pivotal role in numerous IoT applications, providing reliable computational power and storage resources. Our analysis highlighted a diverse spectrum of cloud technologies and services adopted by the selected articles, including Apache Hadoop, Amazon EC2, Apache Spark, Amazon S3, Amazon IoT, and Amazon EMR.
- Containers and services hold paramount significance in constructing robust IoT solutions. Container platforms offer a comprehensive toolkit for IoT design and management, bolstering system resilience against failures. Prominent tools in this domain encompass Docker, OSGi, Docker Swarm, and Kubernetes.
5.4. IoT Open Issues
5.4.1. System Design
5.4.2. A Comprehensive Evaluation of IoT Requirements
5.4.3. Flexible and Broad-Purpose Methodologies
5.4.4. Regulatory and Legal Issues
5.4.5. Ethical Considerations
5.4.6. Environmental Effects
5.5. Financial Insights
- First, it is essential to consider the powerful dependence on the quantity of data, especially training data. Given the differences in activities, services, and management protocols in IoT systems around the world, how to guarantee the usefulness of the developed methods is a question to consider. Therefore, it is necessary to implement evaluation methods for performance tests.
- Secondly, for the commercial development of a system, there might be ethical and legal issues, concerning the use of the data from the training phase, as the performance depends on the quality of the training data.
5.6. Recommendations and Practical Implications
- Comprehensive Regulatory Frameworks: Establish comprehensive and adaptive regulatory frameworks that encompass technical standards, data privacy, security protocols, and environmental sustainability. Collaboration between policymakers, industry stakeholders, and research bodies is essential to ensure that regulations remain agile in the face of rapid technological advancements.
- Interdisciplinary Collaboration: Foster collaborative ecosystems that transcend traditional disciplinary boundaries. Engage experts from diverse domains such as technology, law, ethics, financials, and environmental science to devise holistic solutions that balance innovation with ethical, legal, and environmental considerations.
- Ethical Guidelines and Education: Develop clear ethical guidelines for IoT design, deployment, and use. Educate developers, users, and decision-makers about the ethical implications of IoT technologies to promote responsible innovation and ensure alignment with societal values.
- Resource-Efficient Design: Prioritize resource-efficient design principles in IoT devices and systems. Incorporate energy-efficient hardware, renewable energy sources, and sustainable manufacturing processes to minimize the environmental footprint while enhancing operational efficiency.
- Circular Economy Approach: Embrace a circular economy approach by designing IoT devices for durability, repairability, and recyclability. Implement strategies that extend product lifecycles and facilitate responsible disposal, reducing electronic waste and conserving valuable resources.
- Privacy-Preserving Technologies: Integrate privacy-preserving technologies, such as encryption, differential privacy, and decentralized architectures, to safeguard sensitive data in IoT ecosystems. Strive for a harmonious balance between data utility and individual privacy rights.
- Dynamic Risk Assessment: Implement dynamic risk assessment mechanisms that continuously monitor and adapt to emerging threats in IoT ecosystems. Utilize machine learning and artificial intelligence algorithms to detect anomalies, predict vulnerabilities, and facilitate timely mitigation.
- Stakeholder Engagement: Foster transparent communication and collaboration among IoT stakeholders, including manufacturers, consumers, regulators, and advocacy groups. Engage in open dialogues to address concerns, gather feedback, and collectively shape the evolution of IoT systems.
- Education and Skill Development: Invest in education and skill development programs that equip individuals with the knowledge and expertise required to navigate the complexities of IoT. Empower professionals to implement and manage IoT technologies while upholding ethical, legal, and environmental standards.
- Long-Term Impact Assessment: Conduct comprehensive, long-term impact assessments of IoT implementations to quantify their effects on financial, environmental, and societal dimensions. These assessments can inform decision-making and guide the evolution of IoT strategies.
- Innovation for Sustainability: Encourage research and innovation that explicitly targets the enhancement of IoT’s environmental sustainability. Support initiatives that explore novel energy harvesting techniques, eco-friendly materials, and innovative data processing methods.
- Global Collaboration: Foster international collaboration to establish universally accepted standards and practices for IoT deployments. Global cooperation can harmonize efforts, eliminate redundancies, and accelerate the adoption of sustainable IoT solutions.
- Business Strategy and Decision-Making: The study emphasizes the transformative impact of IoT on organizations and daily lives. Businesses can leverage IoT technologies to make more informed decisions, optimize processes, and enhance operational effectiveness. The insights gained from IoT data can guide strategic planning and resource allocation.
- Operational Efficiency: The study highlights the advantages of IoT in improving overall productivity. IoT devices and sensors can monitor and control various aspects of business operations, leading to streamlined processes, reduced inefficiencies, and cost savings.
- Data Handling and IT Infrastructure: With the increasing volume of data generated by IoT devices, the study underscores the importance of robust IT systems capable of handling and processing this data effectively. Businesses need to invest in scalable and secure IT architectures to manage and analyze the data generated by IoT devices.
- IoT Architecture Development: The study recognizes the challenge of developing appropriate IoT architectures to meet evolving requirements. Businesses must focus on designing flexible and adaptable architectures that can accommodate diverse use cases and circumstances while ensuring data integrity and security.
- Research and Innovation: The study’s systematic review of existing IoT research provides a comprehensive overview of the current state of the field. This can guide further research and innovation by identifying gaps, trends, and emerging areas of interest within the IoT domain.
- Problem Identification and Resolution: By highlighting unresolved difficulties in the IoT business landscape, the study encourages ongoing dialogue and investigation. Businesses can use these insights to address challenges, develop innovative solutions, and drive continuous improvement.
- Encouraging Further Inquiry: The study contributes to the broader conversation around IoT by recognizing and critically assessing issues. It catalyzes further inquiry and exploration, motivating researchers and practitioners to delve deeper into the complexities of IoT technologies and their applications.
- Adaptation to Change: The study underscores the dynamic nature of business settings in the face of technological breakthroughs. Businesses need to remain agile and adaptive to embrace IoT-driven changes, ensuring they stay competitive and relevant in a rapidly evolving landscape.
- Collaboration and Knowledge Sharing: The study’s comprehensive review and categorization of IoT research create opportunities for collaboration and knowledge sharing among researchers, practitioners, and stakeholders. This can lead to cross-disciplinary insights and innovative solutions.
- Awareness and Education: The study contributes to raising awareness about the significance of IoT technologies in contemporary business environments. It highlights the need for businesses to stay informed, educated, and proactive in adopting IoT strategies to stay ahead in the market.
5.7. Strength and Limitation
- Scope and Generalizability: The study’s focus on a specific set of 84 research papers may limit the generalizability of its findings. The selected papers might not fully represent the entire breadth of IoT research and applications, potentially overlooking important perspectives and advancements.
- Time Sensitivity: The rapidly evolving nature of IoT technologies means that the conclusions drawn from this study might become outdated relatively quickly. Breakthroughs, challenges, and trends may emerge that are not adequately addressed in the current research landscape.
- Methodological Limitations: While the study employs a systematic review strategy following PRISMA guidelines, the methodology itself might have limitations. For instance, the inclusion/exclusion criteria for research papers and the search terms used could influence the selection of papers and potentially omit relevant studies.
- Lack of Real-World Validation: While the study aims to encourage further dialogue and investigation, the actual impact of the study’s findings on real-world business practices and decision-making remains to be seen.
- Comprehensive Understanding: The study offers a thorough examination of the current ecosystem of IoT studies by systematically reviewing and categorizing 84 research papers. This comprehensive approach provides a holistic view of the field’s current state and trends.
- Methodological Rigor: The study follows the Preferred Reporting Items for Systematic Reviews and Meta-Analysis (PRISMA) guidelines, indicating a high level of methodological rigor and systematic selection of relevant research papers.
- Categorization Framework: The adoption of an empirical categorization strategy helps organize a wide range of IoT research topics and applications, making it easier for readers to grasp the diversity of the field.
- Practical Relevance: By focusing on the applications of IoT in business settings, the study addresses a practical and pertinent aspect of the technology’s impact. This emphasis on real-world implications enhances its relevance to corporate management and decision-making.
- Gap Identification: The study’s exploration of unresolved difficulties and challenges in the IoT business landscape highlights gaps in current knowledge and understanding. This can guide future research efforts and stimulate further inquiry.
- Encouragement of Dialogue: The study’s intention to foster additional discussion and investigation within the dynamic and evolving domain of IoT demonstrates its commitment to driving ongoing progress and innovation.
- Research Overview: The study’s systematic review and categorization offer a valuable resource for researchers seeking to gain a consolidated understanding of the diverse research topics and areas within the IoT domain.
- Foundational Insights: The study’s overview of IoT research provides foundational insights for individuals who are new to the field, helping them grasp key concepts, applications, and challenges.
- Reference for Decision-Makers: The study’s insights into the advantages of IoT for business purposes, operational effectiveness, and decision-making processes can guide corporate leaders in understanding the potential benefits of IoT adoption.
- Contribution to Knowledge: By identifying and critically assessing existing research, the study contributes to the ongoing conversation around IoT technologies, enriching the collective knowledge and informing future directions.
- Research Roadmap: The study’s categorization and analysis serve as a roadmap for potential areas of further investigation, offering guidance to researchers interested in advancing the understanding and application of IoT.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mazhar, T.; Irfan, H.M.; Haq, I.; Ullah, I.; Ashraf, M.; Shloul, T.A.; Ghadi, Y.Y.; Imran; Elkamchouchi, D.H. Analysis of Challenges and Solutions of IoT in Smart Grids Using AI and Machine Learning Techniques: A Review. Electronics 2023, 12, 242. [Google Scholar] [CrossRef]
- Aloi, G.; Caliciuri, G.; Fortino, G.; Gravina, R.; Pace, P.; Russo, W.; Savaglio, C. Enabling IoT interoperability through opportunistic smartphone-based mobile gateways. J. Netw. Comput. Appl. 2017, 81, 74–84. [Google Scholar] [CrossRef]
- Wanasinghe, T.R.; Gosine, R.G.; James, L.A.; Mann GK, I.; de Silva, O.; Warrian, P.J. The Internet of things in the oil and gas industry: A systematic review. IEEE Internet Things J. 2020, 7, 8654–8673. [Google Scholar] [CrossRef]
- Razzaque, M.A.; Milojevic-Jevric, M.; Palade, A.; Clarke, S. Middleware for Internet of Things: A survey. IEEE Internet Things J. 2015, 3, 70–95. [Google Scholar] [CrossRef]
- Yushi, L.; Fei, J.; Hui, Y. Study on application modes of military Internet of Things (miot). In Proceedings of the 2012 IEEE International Conference on Computer Science and Automation Engineering (CSAE), Zhangjiajie, China, 25–27 May 2012; Volume 3, pp. 630–634. [Google Scholar] [CrossRef]
- Meyer, J.; Boll, S. Smart health systems for personal health action plans. In Proceedings of the 2014 IEEE 16th International Conference on e-Health Networking, Applications and Services, Natal, Brazil, 15–18 October 2014; pp. 404–410. [Google Scholar] [CrossRef]
- Fan, Y.J.; Yin, Y.H.; Xu, L.D.; Zeng, Y.; Wu, F. Iot-based smart rehabilitation system. IEEE Trans. Ind. Inform. 2014, 10, 1568–1577. [Google Scholar] [CrossRef]
- Vippalapalli, V.; Ananthula, S. Internet of Things (IoT) based smart health care system. In Proceedings of the 2016 International Conference on Signal Processing, Communication, Power, and Embedded System (SCOPES), Paralakhemundi, India, 3–5 October 2016; pp. 1229–1233. [Google Scholar] [CrossRef]
- Haouel, J.; Ghorbel, H.; Bargaoui, H. Towards an IoT architecture for persons with disabilities and applications. In Proceedings of the International Conference on IoT Technologies for HealthCare, Västerås, Sweden, 18–19 October 2016; pp. 159–161. [Google Scholar] [CrossRef]
- Gaikwad, P.P.; Gabhane, J.P.; Golait, S.S. A survey based on smart homes system using internet-of-things. In Proceedings of the 2015 International Conference on Computation of Power, Energy, Information and Communication (ICCPEIC), Melmaruvathur, India, 22–23 April 2015; pp. 0330–0335. [Google Scholar] [CrossRef]
- Kasmi, M.; Bahloul, F.; Tkitek, H. Smart home based on Internet of Things and cloud computing. In Proceedings of the 2016 7th International Conference on Sciences of Electronics, Technologies of Information and Telecommunications (SETIT), Hammamet, Tunisia, 18–20 December 2016; pp. 82–86. [Google Scholar] [CrossRef]
- Gea, T.; Paradells, J.; Lamarca, M.; Roldán, D. Smart cities as an application of Internet of Things: Experiences and lessons learned in Barcelona. In Proceedings of the 2013 Seventh International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Taichung, Taiwan, 3–5 July 2013; pp. 552–557. [Google Scholar] [CrossRef]
- Cambra, C.; Sendra, S.; Lloret, J.; Garcia, L. An IoT service-oriented system for agriculture monitoring. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Zixuan, Y.; Zhifang, W.; Chang, L. Research on marine environmental monitoring system based on the Internet of Things technology. In Proceedings of the 2016 IEEE International Conference on Electronic Information and Communication Technology (ICEICT), Harbin, China, 20–22 August 2016; pp. 121–125. [Google Scholar] [CrossRef]
- Evans, D. Cisco. L’internet des Objets. 2011. Available online: http://www.cisco.com/web/CA/solutions/executive/assets/pdf/internetof-things-fr.pdf (accessed on 13 January 2023).
- Sahni, Y.; Cao, J.; Zhang, S.; Yang, L. Edge mesh: A new paradigm to enable distributed intelligence in Internet of things. IEEE Access 2017, 5, 16441–16458. [Google Scholar] [CrossRef]
- San Emeterio de la Parte, M.; Martínez-Ortega, J.F.; Hernández Díaz, V.; Martinez, N.L. Big Data and precision agriculture: A Novel spatio-temporal Semantic IoT Data Management Framework for Improved Interoperability. J Big Data 2023, 10, 52. [Google Scholar] [CrossRef]
- Ren, Y.; Huang, D.; Wang, W.; Yu, X. BSMD: A blockchain-based secure storage mechanism for big spatio-temporal data. Future Gener. Comput. Syst. 2023, 138, 328–338. [Google Scholar] [CrossRef]
- Safa, M.; Pandian, A.; Gururaj, H.L.; Ravi, V.; Krichen, M. Real-time health care big data analytics model for improved QoS in cardiac disease prediction with IoT devices. Health Technol. 2023, 13, 473–483. [Google Scholar] [CrossRef]
- Bi, Z.; Jin, Y.; Maropoulos, P.; Zhang, W.-J.; Wang, L. Internet of things (IoT) and big data analytics (BDA) for digital manufacturing (DM). Int. J. Prod. Res. 2023, 61, 4004–4021. [Google Scholar] [CrossRef]
- Kumar, M.; Mukherjee, P.; Verma, S.; Kavita; Shafi, S.; Wozniak, M. A smart privacy-preserving framework for industrial IoT using hybrid meta-heuristic algorithm. Sci. Rep. 2023, 13, 5372. [Google Scholar] [CrossRef] [PubMed]
- Zubaydi, H.D.; Varga, P.; Molnár, S. Leveraging Blockchain Technology for Ensuring Security and Privacy Aspects in Internet of Things: A Systematic Literature Review. Sensors 2023, 23, 788. [Google Scholar] [CrossRef] [PubMed]
- Najafi, S.E.; Nozari, H.; Edalatpanah, S.A. Investigating the Key Parameters Affecting Sustainable IoT-Based Marketing. In Computational Intelligence Methodologies Applied to Sustainable Development Goals; Verdegay, J.L., Brito, J., Cruz, C., Eds.; Studies in Computational Intelligence; Springer: Cham, Switzerland, 2022; Volume 1036. [Google Scholar] [CrossRef]
- Ediagbonya, V.; Tioluwani, C. The role of fintech in driving financial inclusion in developing and emerging markets: Issues, challenges, and prospects. Technol. Sustain. 2023, 2, 100–119. [Google Scholar] [CrossRef]
- Jarašūnienė, A.; Čižiūnienė, K.; Čereška, A. Research on Impact of IoT on Warehouse Management. Sensors 2023, 23, 2213. [Google Scholar] [CrossRef] [PubMed]
- Nagaty, K.A. IoT Commercial and Industrial Applications and AI-Powered IoT. InFrontiers of Quality Electronic Design (QED); Iranmanesh, A., Ed.; Springer: Cham, Switzerland, 2023. [Google Scholar] [CrossRef]
- Orfanos, V.A.; Kaminaris, S.D.; Papageorgas, P.; Piromalis, D.; Kandris, D. A Comprehensive Review of IoT Networking Technologies for Smart Home Automation Applications. J. Sens. Actuator Netw. 2023, 12, 30. [Google Scholar] [CrossRef]
- Pal, A.; Rath, H.K.; Shailendra, S.; Bhattacharyya, A. IoT standardization: The road ahead. In Internet of Things-Technology, Applications, and Standardization; IntechOpen: London, UK, 2018; pp. 53–74. [Google Scholar] [CrossRef]
- Bader, S.R.; Maleshkova, M.; Lohmann, S. Structuring reference architectures for the industrial Internet of things. Future Internet 2019, 11, 151. [Google Scholar] [CrossRef]
- Gaber, M.M.; Aneiba, A.; Basurra, S.; Batty, O.; Elmisery, A.M.; Kovalchuk, Y.; Rhanam, M.H.U. Internet of things and data mining: From applications to techniques and systems. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2019, 9, e1292. [Google Scholar] [CrossRef]
- Wei, Z.; Jia, Y.; Yao, Y.; Zhu, L.; Guan, L.; Mao, Y.; Liu, P.; Zhang, Y. Discovering and understanding the security hazards in the interactions between IoT devices, mobile apps, and clouds on smart home platforms. In Proceedings of the 28th Security Symposium, Santa Clara, CA, USA, 14–16 August 2019; pp. 1133–1150. [Google Scholar]
- Piccialli, F.; Cuomo, S.; Di Cola, V.S.; Casolla, G. A machine learning approach for IoT cultural data. J. Ambient. Intell. Humaniz. Comput. 2019, 1–12. [Google Scholar] [CrossRef]
- Fatima, H.; Hussain, R.; Hassan, S.A.; Hossain, E. Machine learning in IoT security: Current solutions and future challenges. IEEE Commun. Surv. Tutor. 2020, 22, 1686–1721. [Google Scholar] [CrossRef]
- Zeng, Q.; Lv, Z.; Li, C.; Shi, Y.; Lin, Z.; Liu, C.; Song, G. FedProLs: Federated learning for IoT perception data prediction. Appl. Intell. 2023, 53, 3563–3575. [Google Scholar] [CrossRef]
- Allioui, H.; Allioui, A. The Financial Sphere in the Era of COVID-19: Trends and Perspectives of Artificial Intelligence. In Finance, Law, and the Crisis of COVID-19; Contributions to Management Science, Mansour, N., Vadell, M.B., Eds.; Springer: Cham, Switzerland, 2022. [Google Scholar] [CrossRef]
- Allioui, H.; Allioui, A.; Mourdi, Y. AI-Based Logistics Solutions to Tackle COVID-19 Pandemic and Ensure a Sustainable Financial Growth. In Advanced AI and Internet of Health Things for Combating Pandemics; Lahby, M., Pilloni, V., Banerjee, J.S., Mahmud, M., Eds.; Internet of Things; Springer: Cham, Switzerland, 2023. [Google Scholar] [CrossRef]
- Yavari, A.; Korala, H.; Georgakopoulos, D.; Kua, J.; Bagha, H. Sazgar IoT: A Device-Centric IoT Framework and Approximation Technique for Efficient and Scalable IoT Data Processing. Sensors 2023, 23, 5211. [Google Scholar] [CrossRef] [PubMed]
- Pliatsios, A.; Kotis, K.; Goumopoulos, C. A systematic review on semantic interoperability in the IoE-enabled smart cities. Internet Things 2023, 22, 100754. [Google Scholar] [CrossRef]
- Lemus-Zúñiga, L.-G.; Félix, J.M.; Fides-Valero, A.; Benlloch-Dualde, J.-V.; Martinez-Millana, A. A Proof-of-Concept IoT System for Remote Healthcare Based on Interoperability Standards. Sensors 2022, 22, 1646. [Google Scholar] [CrossRef] [PubMed]
- Abounassar, E.M.; El-Kafrawy, P.; Abd El-Latif, A.A. Security and Interoperability Issues with Internet of Things (IoT) in Healthcare Industry: A Survey. In Security and Privacy Preserving for IoT and 5G Networks; Abd El-Latif, A.A., Abd-El-Atty, B., Venegas-Andraca, S.E., Mazurczyk, W., Gupta, B.B., Eds.; Studies in Big Data; Springer: Cham, Switzerland, 2022; Volume 95. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Khalaf, O.I.; Abdulsahib, G.M.; Al Humaimeedy, A.S.; Aldhyani, T.H.H.; Maashi, M.; Alkahtani, H. A Systematic Survey on Energy-Efficient Techniques in Sustainable Cloud Computing. Sustainability 2022, 14, 6256. [Google Scholar] [CrossRef]
- Cleber, M.; Sadok, D.; Kelner, J. An IoT sensor and scenario survey for data researchers. J. Br. Comput. Soc. 2019, 25, 4. [Google Scholar] [CrossRef]
- Albrecht, S.; Van Laerhoven, K. How to build smart appliances? IEEE Pers. Commun. 2001, 8, 66–71. [Google Scholar] [CrossRef]
- Khelif, F.; Bradai, A.; Benslimane, A.; Rawat, P.; Atri, M. A survey of localization systems in Internet of things. Mob. Netw. Appl. 2019, 24, 761–785. [Google Scholar] [CrossRef]
- Andrews, L.J.B.; Raja, L. Mobile android-based remote patient monitoring system through wearable sensors. J. Discret. Math. Sci. Cryptogr. 2019, 22, 557–568. [Google Scholar] [CrossRef]
- Vijaya, R.S.; Nalluri, S.; Ramasubbareddy, S.; Govinda, K.; Swetha, E. Brilliant corp yield prediction utilizing Internet of Things. In Data Engineering and Communication Technology; Springer: Singapore, 2020; pp. 893–902. [Google Scholar] [CrossRef]
- Salah, M. IoT physical layer: Sensors, actuators, controllers, and programming. In The Era of Internet of Things; Springer: Cham, Switzerland, 2019; pp. 21–47. [Google Scholar] [CrossRef]
- Tournier, J.; Lesueur, F.; Mouel, F.; Guyon, L.; Hassine, H.B. A survey of IoT protocols and their security issues through the lens of a generic IoT stack. Internet Things 2021, 16, 100264. [Google Scholar] [CrossRef]
- Lee, J.S.; Dong, M.F.; Sun, Y.H. A preliminary study of low power wireless technologies: ZigBee and Bluetooth low energy. In Proceedings of the 2015 IEEE 10th Conference on Industrial Electronics and Applications (ICIEA), Auckland, New Zealand, 15–17 June 2015; pp. 135–139. [Google Scholar] [CrossRef]
- Jabraeil Jamali, M.A.; Bahrami, B.; Heidari, A.; Allahverdizadeh, P.; Norouzi, F. IoT Architecture. In Towards the Internet of Things. EAI/Springer Innovations in Communication and Computing; Springer: Cham, Switzerland, 2020. [Google Scholar] [CrossRef]
- Gupta, B.B.; Quamara, M. An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurr. Comput. Pract. Exp. 2020, 32, e4946. [Google Scholar] [CrossRef]
- Alfonso, I.; Garcés, K.; Castro, H.; Cabot, J. A model-based infrastructure for the specification and runtime execution of self-adaptive IoT architectures. Computing 2023, 105, 1883–1906. [Google Scholar] [CrossRef]
- Moreta, N.; Aragon, D.; Oña, S.; Jaramillo, A.; Ibarra, J.; Jahankhani, H. Comparison of Cybersecurity Methodologies for the Implementing of a Secure IoT Architecture. In Cybersecurity in the Age of Smart Societies; Jahankhani, H., Ed.; Advanced Sciences and Technologies for Security Applications; Springer: Cham, Switzerland, 2023. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Elijah, O.; Rahman, T.A.; Orikumhi, I.; Leow, C.Y.; Hindia, M.N. An overview of Internet of Things (IoT) and data analytics in agriculture: Benefits and challenges. IEEE Internet Things J. 2018, 5, 3758–3773. [Google Scholar] [CrossRef]
- Pons, M.; Valenzuela, E.; Rodríguez, B.; Nolazco-Flores, J.A.; Del-Valle-Soto, C. Utilization of 5G Technologies in IoT Applications: Current Limitations by Interference and Network Optimization Difficulties—A Review. Sensors 2023, 23, 3876. [Google Scholar] [CrossRef] [PubMed]
- PRISMA. 2023. Available online: http://www.prisma-statement.org/?AspxAutoDetectCookieSupport=1 (accessed on 13 January 2023).
- Mengist, W.; Soromessa, T.; Legese, G. Method for Conducting Systematic Literature Review and Meta-Analysis for Environmental Science Research. MethodsX 2020, 7, 100777. [Google Scholar] [CrossRef]
- Arshad, R.; Zahoor, S.; Shah, M.A.; Wahid, A.; Yu, H. Green IoT: An Investigation on Energy Saving Practices for 2020 and beyond. IEEE Access 2017, 5, 15667–15681. [Google Scholar] [CrossRef]
- Albreem, M.A.; Sheikh, A.M.; Alsharif, M.H.; Jusoh, M.; Yasin, M.N. Green Internet of Things (GIoT): Applications, practices, awareness, and challenges. IEEE Access 2021, 9, 38833–38858. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad. Hoc. Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef]
- Baliga, J.; Ayre, R.W.; Hinton, K.; Tucker, R.S. Green cloud computing: Balancing energy in processing, storage, and transport. Proc. IEEE 2011, 99, 149–167. [Google Scholar] [CrossRef]
- Shaikh, F.K.; Zeadally, S. Energy harvesting in wireless sensor networks: A comprehensive review. Renew. Sustain. Energy Rev. 2016, 55, 1041–1054. [Google Scholar] [CrossRef]
- Akkaya, K.; Guvenc, I.; Aygun, R.; Pala, N.; Kadri, A. IoT-based occupancy monitoring techniques for energy-efficient smart buildings. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference Workshops (WCNCW 2015), New Orleans, LA, USA, 9–12 March 2015; pp. 58–63. [Google Scholar]
- Amendola, S.; Lodato, R.; Manzari, S.; Occhiuzzi, C.; Marrocco, G. RFID technology for IoT-based personal healthcare in smart spaces. IEEE Internet Things J. 2014, 1, 144–152. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A survey on Internet of things: Architecture, enabling technologies, security, privacy, and applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Goudos, S.K.; Dallas, P.I.; Chatziefthymiou, S.; Kyriazakos, S. A survey of IoT key enabling and future technologies: 5G, mobile IoT, semantic web, and applications. Wirel. Pers. Commun. 2017, 97, 1645–1675. [Google Scholar] [CrossRef]
- Alam, M.M.; Malik, H.; Khan, M.I.; Pardy, T.; Kuusik, A.; Le Moullec, Y. A survey on the roles of communication technologies in IoT-based personalized healthcare applications. IEEE Access 2018, 6, 36611–36631. [Google Scholar] [CrossRef]
- Taivalsaari, A.; Mikkonen, T. A taxonomy of IoT client architectures. IEEE Softw. 2018, 35, 83–88. [Google Scholar] [CrossRef]
- Yaqoob, I.; Ahmed, E.; Hashem, I.A.T.; Ahmed, A.I.A.; Gani, A.; Imran, M.; Guizani, M. Internet of Things architecture: Recent advances, taxonomy, requirements, and open challenges. IEEE Wirel. Commun. 2017, 24, 10–16. [Google Scholar] [CrossRef]
- Ray, P. A survey on Internet of Things architectures. J. King Saud Univ.-Comput. Inf. Sci. 2018, 30, 291–319. [Google Scholar] [CrossRef]
- Sheng, Z.; Yang, S.; Yu, Y.; Vasilakos, A.V.; Mccann, J.A.; Leung, K.k. A survey on the ietf protocol suite for the Internet of Things: Standards, challenges, and opportunities. IEEE Wirel. Commun. 2013, 20, 91–98. [Google Scholar] [CrossRef]
- Weyrich, M.; Ebert, C. Reference architectures for the Internet of Things. IEEE Softw. 2016, 1, 112–116. [Google Scholar] [CrossRef]
- Minoli, D.; Sohraby, K.; Occhiogrosso, B. IoT considerations, requirements, and architectures for smart buildings—Energy optimization and next-generation building management systems. IEEE Internet Things J. 2017, 4, 269–283. [Google Scholar] [CrossRef]
- Guillaume, B.; Benjamin, D.; Vincent, C. Review of the Impact of IT on the Environment and Solution with a Detailed Assessment of the Associated Gray Literature. Sustainability 2022, 14, 2457. [Google Scholar] [CrossRef]
- Naghib, A.; Jafari Navimipour, N.; Hosseinzadeh, M.; Sharifi, A. A comprehensive and systematic literature review on the big data management techniques in the Internet of things. Wirel. Netw. 2023, 29, 1085–1144. [Google Scholar] [CrossRef]
- IoT Analytics. 2023. Available online: https://iot-analytics.com (accessed on 3 June 2023).
- MQ. 2023. Available online: https://www.emqx.com/en (accessed on 10 June 2023).
- IBM. Real-Time Analytics on IoT Data. 2023. Available online: https://www.ibm.com/blog/real-time-analytics-on-iot-data/ (accessed on 10 June 2023).
- MMAT. 2018. Available online: http://mixedmethodsappraisaltoolpublic.pbworks.com/w/file/fetch/127916259/MMAT_2018_criteria-manual_2018-08-01_ENG.pdf (accessed on 13 January 2023).
- Kiljander, J.; D’elia, A.; Morandi, F.; Hyttinen, P.; Mattila, J.T.; Oja, A.Y.; Soininen, J.P.; Cinotti, T.S. Semantic interoperability architecture for pervasive computing and Internet of Things. IEEE Access 2014, 2, 856–873. [Google Scholar] [CrossRef]
- Cirani, S.; Davoli, L.; Ferrari, G.; Leone, R.; Medagliani, P.; Picone, M.; Veltri, L. A scalable and self-configuring architecture for service discovery on the Internet of Things. IEEE Internet Things J. 2014, 1, 508–521. [Google Scholar] [CrossRef]
- Tracey, D.; Sreenan, C. A holistic architecture for the Internet of Things, sensing services, and big data. In Proceedings of the 2013 13th IEEE/ACM International Symposium on Cluster, Cloud, and Grid Computing, Delft, The Netherlands, 13–16 May 2013; pp. 546–553. [Google Scholar] [CrossRef]
- Catarinucci, L.; Donno, D.; Mainetti, L.; Palano, L.; Patrono, L.; Steranizzi, M.L.; Tarricone, L. An IoT-aware architecture for smart healthcare systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Sarkar, C.; Nambi, A.U.S.N.; Prasad, R.V.; Rahim, A.; Neisse, R.; Baldini, G. Diat: A scalable distributed architecture for IoT. IEEE Internet Things J. 2014, 2, 230–239. [Google Scholar] [CrossRef]
- Vucinic, M.; Tourancheau, B.; Rousseau, F.; Duda, A.; Damon, L.; Guizzetti, R. Object security architecture for the Internet of Things. Ad. Hoc. Netw. 2015, 32, 3–16. [Google Scholar] [CrossRef]
- Guo, Y.; Zhu, H.; Yang, L. Service-oriented network virtualization architecture for the Internet of Things. China Commun. 2016, 13, 163–172. [Google Scholar] [CrossRef]
- Hou, L.; Zhao, S.; Xiong, X.; Zheng, K.; Chatzimisios, P.; Hossain, M.S.; Xiang, W. Internet of Things cloud: Architecture and implementation. IEEE Commun. Mag. 2016, 54, 32–39. [Google Scholar] [CrossRef]
- Balampanis, S.; Sotiriadis, S.; Petrakis, E.G.M. Internet of Things architecture for enhanced living environments. IEEE Cloud Comput. 2016, 3, 28–34. [Google Scholar] [CrossRef]
- Da Cunha, M.S.; Almeira, M.C.; Fernandes, R.F.; Carrijo, R.S. Proposal for an IoT architecture in industrial processes. In Proceedings of the 2016 12th IEEE International Conference on Industry Applications (INDUSCON), Curitiba, PR, Brazil, 20–23 November 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Roffia, L.; Morandi, F.; Kiljander, J.; Elia, A.D.; Vergari, F.; Viola, F.; Bononi, L.; Cinotti, T.S. A semantic publish-subscribe architecture for the Internet of Things. IEEE Internet Things J. 2016, 3, 1274–1296. [Google Scholar] [CrossRef]
- Beligianni, F.; Alamaniotis, M.; Fevgas, A.; Tsompanopoulou, P.; Bozanis, P.; Tsoukalas, L.H. An Internet of Things Architecture for Preserving the Privacy of Energy Consumption. In Proceedings of the Mediterranean Conference on Power Generation, Transmission, Distribution and Energy Conversion (MedPower), Belgrade, Serbia, 6–9 November 2016. [Google Scholar] [CrossRef]
- Lloret, J.; Tomas, J.; Canovas, A.; Parra, L. An integrated IoT architecture for smart metering. IEEE Commun. Mag. 2016, 54, 50–57. [Google Scholar] [CrossRef]
- Kaur, N.; Sood, S.K. An energy-efficient architecture for the Internet of Things (IoT). IEEE Syst. J. 2015, 11, 796–805. [Google Scholar] [CrossRef]
- Zhu, T.; Dhelim, S.; Zhou, Z.; Yang, S.; Ning, H. An architecture for aggregating information from distributed data nodes for industrial Internet of Things. Comput. Electr. Eng. 2017, 58, 337–349. [Google Scholar] [CrossRef]
- Perles, A.; Pérez-Marín, E.; Mercado, R.; Segrelles, J.D.; Blanquer, I.; Zarzo, M.; Diego, F.j.G. An energy-efficient Internet of Things (IoT) architecture for preventive conservation of cultural heritage. Future Gener. Comput. Syst. 2018, 81, 566–581. [Google Scholar] [CrossRef]
- Mendoza, J.; Ordóñez, H.; Ordonez, A.; Jurado, J.L. Architecture for embedded software in microcontrollers for Internet of Things (IoT) in fog water collection. Procedia Comput. Sci. 2017, 109, 1092–1097. [Google Scholar] [CrossRef]
- Manogaran, G.; Varatharajan, R.; Lopez, D.; Kumar, P.M.; Sundarasekar, R.; Thota, C. A new architecture of Internet of Things and big data ecosystem for secured smart healthcare monitoring and alerting system. Future Gener. Comput. Syst. 2018, 82, 375–387. [Google Scholar] [CrossRef]
- Pape, S.; Rannenberg, K. Applying privacy patterns to the Internet of Things (IoT) architecture. Mob. Networks Appl. 2019, 24, 925–933. [Google Scholar] [CrossRef]
- Liu, C.; Chen, F.; Zhao, C.; Wang, T.; Zhang, C.; Zhang, Z. Ipv6-based architecture of community medical Internet of Things. IEEE Access 2018, 6, 7897–7910. [Google Scholar] [CrossRef]
- Kumar, P.M.; Gandhi, U.D. A novel three-tier Internet of Things architecture with machine learning algorithm for early detection of heart diseases. Comput. Electr. Eng. 2018, 65, 222–235. [Google Scholar] [CrossRef]
- Usamentiaga, R.; Fernandez, M.A.; Villan, F.Z.; Carus, L. Temperature monitoring for electrical substations using infrared thermography: Architecture for industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 5667–5677. [Google Scholar] [CrossRef]
- Moosavi, S.R.; Gia, T.N.; Rahmani, A.M.; Nigussie, E.; Virtanem, S.; Isoaho, J.; Isoaho, J.; Tenhunen, H. Sea: A secure and efficient authentication and authorization architecture for IoT-based healthcare using smart gateways. Procedia Comput. Sci. 2015, 52, 452–459. [Google Scholar] [CrossRef]
- Guo, H.; Ren, J.; Zhang, D.; Zhang, Y.; Hu, J. A scalable and manageable IoT architecture based on transparent computing. J. Parallel Distrib. Comput. 2018, 118, 5–13. [Google Scholar] [CrossRef]
- Suarez, J.; Quevedo, J.; Vidal, I.; Corujo, D.; Reinoso, J.G.; Aguiar, R.L. A secure IoT management architecture based on information-centric networking. J. Netw. Comput. Appl. 2016, 63, 190–204. [Google Scholar] [CrossRef]
- De Morais, B.; de Aquino Junior, G.S. A software reference architecture for IoT-based healthcare applications. In Proceedings of the International Conference on Computational Science and Its Applications, Melbourne, VIC, Australia, 2–5 July 2018; pp. 173–188. [Google Scholar] [CrossRef]
- Lopes, N.; Pinto, P.; Furtado, P.; Silva, J. Iot architecture proposal for disabled people. In Proceedings of the 2014 IEEE 10th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Larnaca, Cyprus, 8–10 October 2014; pp. 152–158. [Google Scholar] [CrossRef]
- Kitagami, S.; Ogino, T.; Suganuma, T.; Shiratori, N. Proposal of a multiagent-based flexible IoT edge computing architecture harmonizing its control with cloud computing. In Proceedings of the 2017 Fifth International Symposium on Computing and Networking (CANDAR), Aomori, Japan, 19–22 November 2017; p. 22. [Google Scholar] [CrossRef]
- Loria, M.; Toja, M.; Carchiolo, V.; Malgeri, M. An efficient real-time architecture for collecting IoT data. In Proceedings of the 2017 Federated Conference on Computer Science and Information Systems (FedCSIS), Prague, Czech Republic, 3–6 September 2017; pp. 1157–1166. [Google Scholar] [CrossRef]
- Xu, D.G.; Qin, L.H.; Park, J.H.; Zhou, J.L. Odsa: Chord-based object discovery service architecture for the Internet of Things. Wirel. Pers. Commun. 2013, 73, 1455–1476. [Google Scholar] [CrossRef]
- Kim, H.; Wasicek, A.; Mehne, B.; Lee, E. A secure network architecture for the Internet of Things based on local authorization entities. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria, 22–24 August 2016; pp. 114–122. [Google Scholar] [CrossRef]
- Sicari, S.; Cappiello, C.; De Pellegrini, F.; Miorandi, D.; Porisini, A.C. A security-and quality-aware system architecture for Internet of Things. Inf. Syst. Front. 2016, 18, 665–677. [Google Scholar] [CrossRef]
- Tao, M.; Zuo, J.; Liu, Z.; Castiglione, A.; Palmieri, F. Multilayer cloud architectural model and ontology-based security service framework for IoT-based smart homes. Future Gener. Comput. Syst. 2018, 78, 1040–1051. [Google Scholar] [CrossRef]
- Hu, P.; Ning, H.; Chen, L.; Daneshmand, M. An Open Internet of Things System Architecture Based on Software-Defined Device. IEEE Internet Things J. 2018, 6, 2583–2592. [Google Scholar] [CrossRef]
- Mecibah, R.; Djamaa, B.; Yachir, A.; Aissani, M. A scalable semantic resource discovery architecture for the Internet of Things. In Proceedings of the International Conference on Computer Science and Its Applications, Algiers, Algeria, 24–25 April 2018; pp. 37–47. [Google Scholar] [CrossRef]
- Mainetti, L.; Mighali, V.; Patrono, L.; Rametta, P. A novel rule-based semantic architecture for IoT building automation systems. In Proceedings of the 2015 23rd International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 16–18 September 2015; pp. 124–131. [Google Scholar] [CrossRef]
- Tomovic, S.; Yoshigoe, K.; Maljevic, I.; Radusinovic, I. Software-defined fog network architecture for IoT. Wirel. Pers. Commun. 2017, 92, 181–196. [Google Scholar] [CrossRef]
- Lunardi, R.; Michelin, R.; Neu, C.V.; Zorzo, A.F. Distributed access control on IoT ledger-based architecture. In Proceedings of the NOMS 2018-2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Miorandi, D.; Cappiello, C.; Porsini, A.C. A secure and quality-aware prototypical architecture for the Internet of Things. Inf. Syst. 2016, 58, 43–55. [Google Scholar] [CrossRef]
- Shanbhag, R.; Shankarmani, R. Architecture for Internet of Things to minimize human intervention. In Proceedings of the 2015 International Conference on Advances in Computing, Communications, and Informatics (ICACCI), Kochi, India, 10–13 August 2015; pp. 2348–2353. [Google Scholar] [CrossRef]
- Din, S.; Ghayvat, H.; Paul, A.; Ahmad, A.; Rathore, M.; Shafi, I. An architecture to analyze big data on the Internet of Things. In Proceedings of the 2015 9th International Conference on Sensing Technology (ICST), Auckland, New Zealand, 8–10 December 2015; pp. 677–682. [Google Scholar] [CrossRef]
- Khan, W.Z.; Aalsalem, M.Y.; Khan, M.K.; Hossain, M.S.; Atiuzzaman, M. A reliable Internet of Things-based architecture for oil and gas industry. In Proceedings of the 2017 19th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Republic of Korea, 19–22 February 2017; pp. 705–710. [Google Scholar] [CrossRef]
- Javed, A.; Heljanko, K.; Buda, A.; Framling, K. Cefiot: A fault-tolerant IoT architecture for edge and cloud. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 813–818. [Google Scholar] [CrossRef]
- Xu, Y.; Helal, A. Scalable cloud-sensor architecture for the Internet of Things. IEEE Internet Things J. 2015, 3, 285–298. [Google Scholar] [CrossRef]
- Wang, K.; Wang, Y.; Sun, Y.; Guo, S.; Wu, J. Green industrial Internet of Things architecture: An energy-efficient perspective. IEEE Commun. Mag. 2016, 54, 48–54. [Google Scholar] [CrossRef]
- Iqbal, J.; Khan, M.; Talha, M.; Farman, H.; Jan, B.; Muhammad, A.; Khattak, H.A. A generic Internet of Things architecture for controlling electrical energy consumption in smart homes. Sustain. Cities Soc. 2018, 43, 443–450. [Google Scholar] [CrossRef]
- Ma, M.; Shi, G.; Li, F. Privacy-oriented blockchain-based distributed key management architecture for hierarchical access control in the IoT scenario. IEEE Access 2019, 7, 34045–34059. [Google Scholar] [CrossRef]
- Luo, J.; Yin, L.; Hu, J.; Wang, C.; Liu, X.; Fan, X.; Luo, H. Container-based fog computing architecture and energy-balancing scheduling algorithm for energy IoT. Future Gener. Comput. Syst. 2019, 97, 50–60. [Google Scholar] [CrossRef]
- Marques, P.; Manfroi, D.; Deitos, E.; Cegoni, J.; Castilhos, R.; Rochol, J.; Pignaton, E.; Kunst, R. An IoT-based smart cities infrastructure architecture applied to a waste management scenario. Ad. Hoc. Netw. 2019, 87, 200–208. [Google Scholar] [CrossRef]
- Tiburski, R.T.; Moratelli, C.R.; Johann, S.F.; Neves, M.V.; De Matos, E.; Amaral, L.A.; Hessel, F. Lightweight security architecture based on embedded virtualization and trust mechanisms for IoT edge devices. IEEE Commun. Mag. 2019, 57, 67–73. [Google Scholar] [CrossRef]
- Zarca, A.M.; Bernabe, J.B.; Trapero, R.; Rivera, D.; Villalabos, J.; Skarmeta, A.; Bianchi, S.; Zafeiropoulos, A.; Gouvas, P. Security Management Architecture for NFV/SDN-Aware IoT Systems. IEEE Internet Things J. 2019, 6, 8005–8020. [Google Scholar] [CrossRef]
- Urbina, M.; Acosta, T.; Lázaro, J.; Astarloa, A.; Bidarte, U. Smart Sensor: SoC Architecture for the Industrial Internet of Things. IEEE Internet Things J. 2019, 6, 6567–6577. [Google Scholar] [CrossRef]
- Chekired, D.A.; Khoukhi, L. Multi-tier fog architecture: A new delay-tolerant network for IoT data processing. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Sun, Y.; Qiao, X.; Cheng, B.; Chen, J. A low-delay, lightweight publish/subscribe architecture for delay-sensitive IoT services. In Proceedings of the 2013 IEEE 20th International Conference on Web Services, Santa Clara, CA, USA, 28 June–3 July 2013; pp. 179–186. [Google Scholar] [CrossRef]
- Pérez, S.; Garcia-Carrillo, D.; Marín-López, R.; Ramos, J.L.H.; Perez, R.M.; Skarmeta, A.F. Architecture of security association establishment based on boot-strapping technologies for enabling secure IoT infrastructures. Future Gener. Comput. Syst. 2019, 95, 570–585. [Google Scholar] [CrossRef]
- Tekeste, T.; Saleh, H.; Mohammad, B.; Ismail, M. Ultra-low power qrs detection and ECG compression architecture for IoT healthcare devices. IEEE Trans. Circuits Syst. I Regul. Pap. 2018, 66, 669–679. [Google Scholar] [CrossRef]
- Malche, T.; Maheshwary, P.; Kumar, R. Environmental monitoring system for smart city based on secure Internet of Things (IoT) architecture. Wirel. Pers. Commun. 2019, 107, 2143–2172. [Google Scholar] [CrossRef]
- Dang-Ha, T.H.; Roverso, D.; Olsson, R. Graph of virtual actors (gova): A big data analytics architecture for IoT. In Proceedings of the 2017 IEEE International Conference on Big Data and Smart Computing (BigComp), Jeju, Republic of Korea, 13–16 February 2017; pp. 162–169. [Google Scholar]
- Ahad, M.A.; Biswas, R. Request-based, secured, and energy-efficient (rbsee) architecture for handling IoT big data. J. Inf. Sci. 2019, 45, 227–238. [Google Scholar] [CrossRef]
- Wang, X. The architecture design of the wearable health monitoring system based on Internet of Things technology. Int. J. Grid Util. Comput. 2015, 6, 207–212. [Google Scholar] [CrossRef]
- Darabseh, A.; Freris, N.M. A software-defined architecture for control of IoT cyber-physical systems. arXiv 2018, arXiv:1810.03822. [Google Scholar]
- Almajali, S.; Abou-Tair, D.D.I.; Salameh, H.B.; Ayyash, M.; Elgala, H. A distributed multi-layer mec-cloud architecture for processing large-scale IoT-based multimedia applications. Multimed. Tools Appl. 2019, 78, 24617–24638. [Google Scholar] [CrossRef]
- Rocha, V.; Brandão, A.F. A scalable multiagent architecture for monitoring IoT devices. J. Netw. Comput. Appl. 2019, 139, 1–14. [Google Scholar] [CrossRef]
- Pillai, A.S.; Chandraprasad, G.S.; Khwaja, A.S.; Anpalagan, A. A service-oriented IoT architecture for disaster preparedness and forecasting system. Internet Things 2019, 14, 100076. [Google Scholar] [CrossRef]
- Gopikrishnan, S.; Priakanth, P.; Awangga, R.M. Hsir: Hybrid architecture for sensor identification and registration for IoT applications. J. Supercomput. 2019, 75, 5000–5018. [Google Scholar] [CrossRef]
- Naranjo, P.G.V.; Pooranian, Z.; Shojafar, M.; Conti, M.; Buyya, R. FOCAN: A Fog-supported smart city network architecture for the management of applications on the Internet of Everything environments. J. Parallel Distrib. Comput. 2019, 132, 274–283. [Google Scholar] [CrossRef]
- Maktoubian, J.; Ansari, K. An IoT architecture for preventive maintenance of medical devices in healthcare organizations. Health Technol. 2019, 9, 233–243. [Google Scholar] [CrossRef]
- Naranjo, P.; Baccarelli, E.; Scarpiniti, M. Design and energy-efficient resource management of virtualized networked fog architectures for the real-time support of IoT applications. J. Supercomput. 2018, 74, 2470–2507. [Google Scholar] [CrossRef]
- Aravind, M.; Wiklander, G.; Palmheden, J.; Dobrin, R. An event-based messaging architecture for vehicular Internet of Things (IoT) platforms. In Proceedings of the International Conference on ICT Innovations, Skopje, Macedonia, 18–23 September 2017; pp. 37–46. [Google Scholar]
- Ibrahim, H.; Mostafa, N.; Halawa, H.; Elsalamouny, M.; Daoud, R.; Amer, H.; Adel, Y.; Shaarawi, A.; Khattab, A.; ElSayed, H. A layered IoT architecture for greenhouse monitoring and remote control. SN Appl. Sci. 2019, 1, 223. [Google Scholar] [CrossRef]
- Lomotey, R.K.; Pry, J.C.; Chai, C. Traceability and visual analytics for the Internet-of-Things (IoT) architecture. World Wide Web 2018, 21, 7–32. [Google Scholar] [CrossRef]
- Mesmoudi, Y.; Lamnaour, M.; El Khamlichi, Y.; Tahiri, A.; Touhafi, A.; Braeken, A. A Middleware based on Service Oriented Architecture for Heterogeneity Issues within the Internet of Things (MSOAH-IoT). J. King Saud Univ.-Comput. Inf. Sci. 2018, 32, 1108–1116. [Google Scholar] [CrossRef]
- Almeida, R.B.; Junes, V.R.C.; Machado, R.S.; da Rosa, D.Y.L.; Donato, L.M.; Yamin, A.C.; Pernas, A.M. A distributed event-driven architectural model based on situational awareness applied on Internet of Things. Inf. Soft. Technol. 2019, 111, 144–158. [Google Scholar] [CrossRef]
- Valecce, G.; Strazzella, S.; Radesca, A.; Grieco, L.A. Solarfertigation: Internet of Things architecture for smart agriculture. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Lee, S.H.; Huang, K.W.; Yang, C.S. TBAS: Token-based authorization service architecture in Internet of Things scenarios. Int. J. Distrib. Sens. Netw. 2017, 13, 1–14. [Google Scholar] [CrossRef]
- Mourdı, Y.; Sadgal, M.; Berrada Fathı, W.; El Kabtane, H. A Machine Learning Based Approach to Enhance MOOC Users’ Classification. Turk. Online J. Distance Educ. 2020, 21, 47–68. [Google Scholar] [CrossRef]
- Indrakumari, R.; Poongodi, T.; Suresh, P.; Balamurugan, B. The growing role of the Internet of Things in healthcare wearables. In Emergence of Pharmaceutical Industry Growth with Industrial IoT Approach; Academic Press: Cambridge, MA, USA, 2020; pp. 163–194. [Google Scholar] [CrossRef]
- Athul, J. Smart retail 4.0 IoT consumer retailer model for retail intelligence and strategic marketing of in-store products. In Proceedings of the 17th International Business Horizon-INBUSH ERA-2017, Noida, India, 8–10 February 2017. [Google Scholar]
- Liao, S.-H.; Yang, L.L. Mobile payment and online to offline retail business models. J. Retail. Consum. Serv. 2020, 57, 102230. [Google Scholar] [CrossRef]
- Benomar, Z.; Longo, F.; Merlino, G.; Puliafito, A. Cloud-based Network Virtualization in IoT with OpenStack. ACM Trans. Internet Technol. 2021, 22, 1–26. [Google Scholar] [CrossRef]
- Benomar, Z.; Longo, F.; Merlino, G.; Puliafito, A.A. Cloud-Based and Dynamic DNS Approach to Enable the Web of Things. IEEE Trans. Netw. Sci. Eng. 2021, 9, 3968–3978. [Google Scholar] [CrossRef]


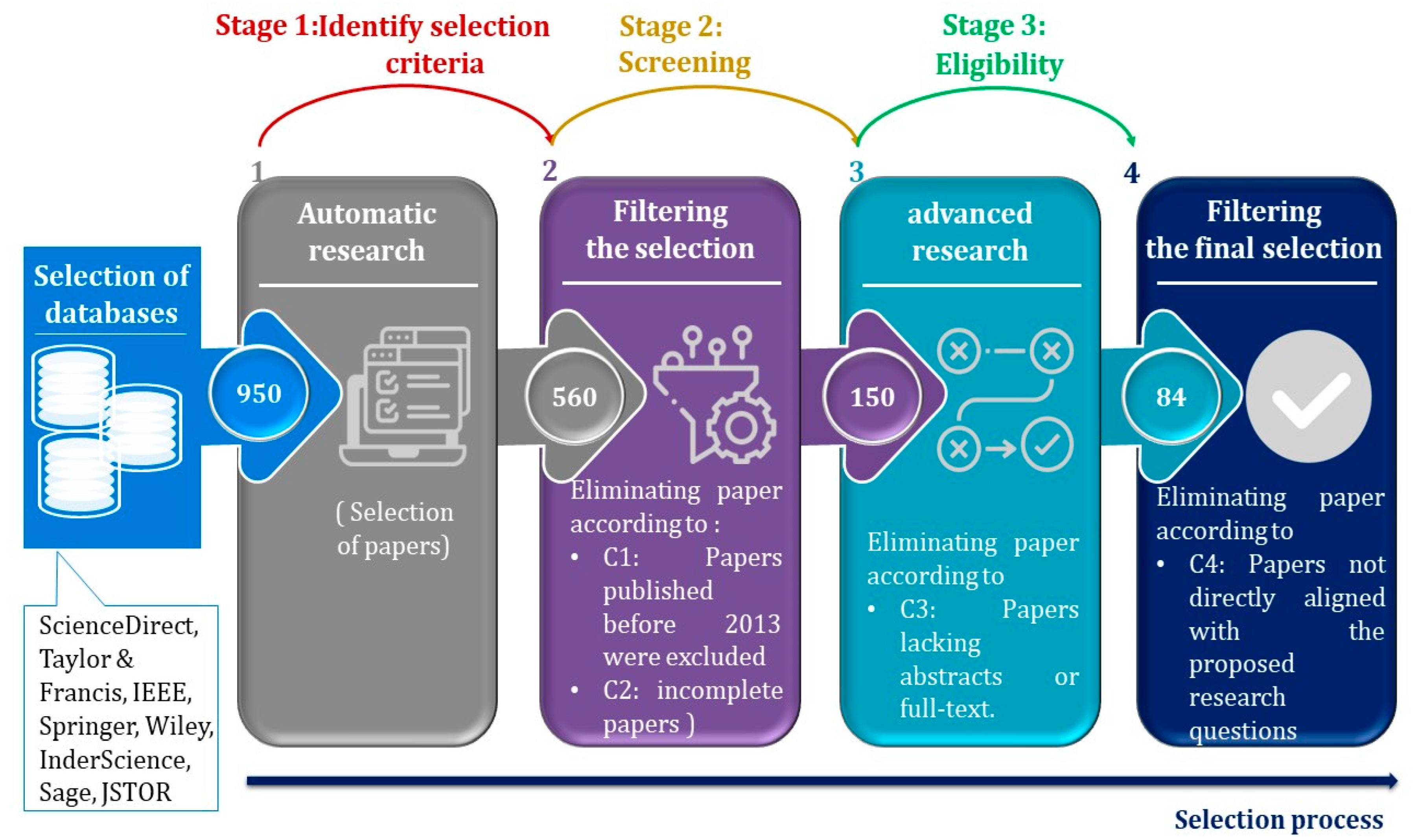

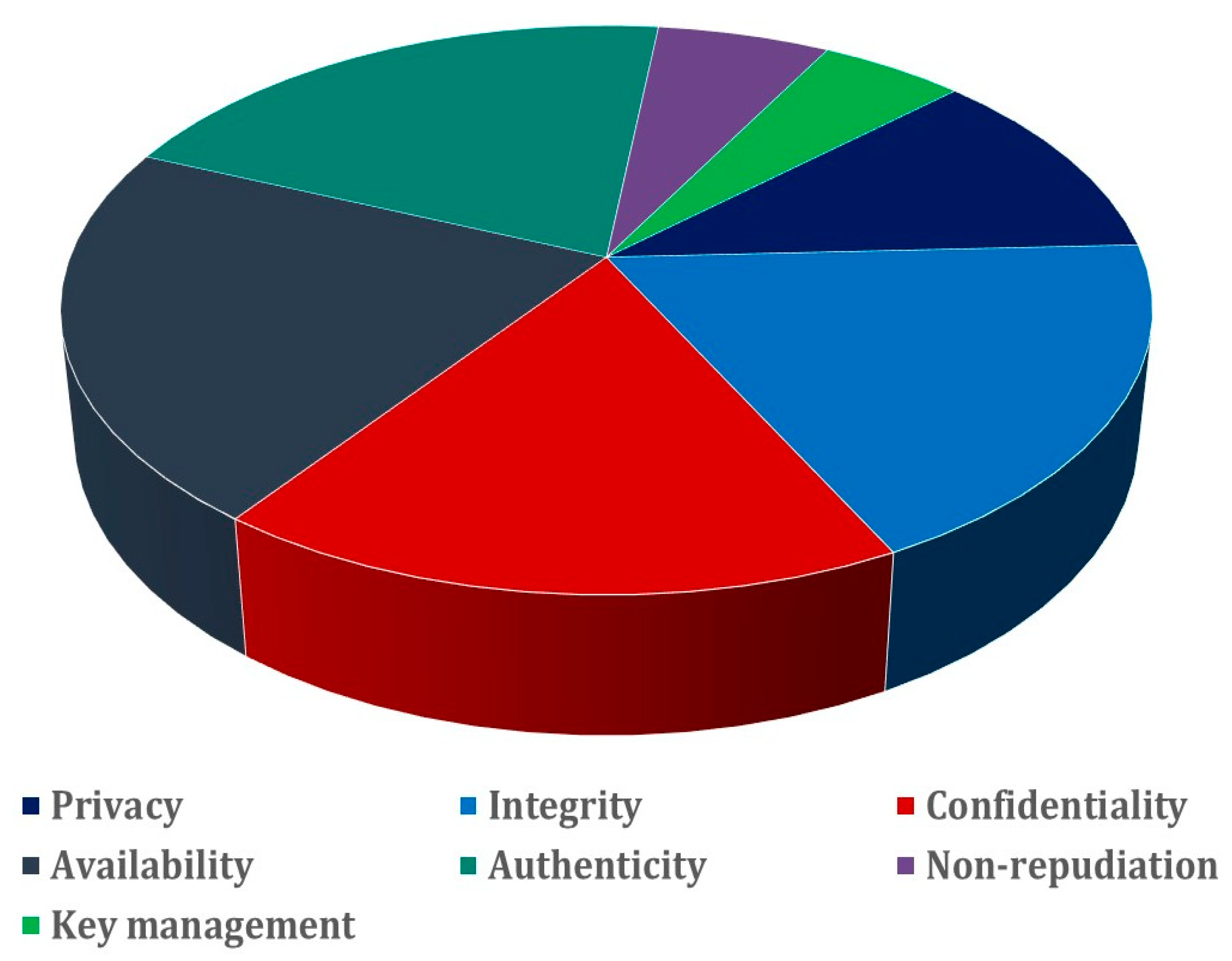


| Database | URL Address |
|---|---|
| ScienceDirect | http://www.sciencedirect.com/ |
| Taylor & Francis | http://www.tandfonline.com/ |
| IEEE Xplore | http://www.ieeexplore.ieee.org/ |
| Springer | http://www.link.springer.com/ |
| Wiley | http://www.onlinelibrary.wiley.com/ |
| InderScience | http://www.inderscienceonline.com/ |
| Sage | http://www.journals.sagepub.com/ |
| JSTOR | http://www.jstor.org/ |
| Search Statement |
|---|
| Internet of Things |
| IoT |
| “Internet of Things” or “IoT” |
| (“Internet of Things” or “IoT”) and not an “inductive output tube” |
| (“Internet of Things” or “IoT”) and “challenges” |
| (“Internet of Things” or “IoT”) and “trends” |
| (“Internet of Things” or “IoT”) and “technologies” |
| (“Internet of Things” or “IoT”) and “applications” |
| (“Internet of Things” or “IoT”) and “Security and Privacy” |
| Publications | Thematic | Technologies and Paradigms | Advantages and Drawbacks |
|---|---|---|---|
| MQ [23] | White papers platform | Literature and tutorials | A guide to concise information on IoT advances |
| Kiljander et al. [81] | Implementation | Programming language: Python Operating system: Linux (Ubuntu) Technologies: OSGi, Apache Jena, VirtualBox | An interoperable and incorporated system for pervasive computing, without scalability. |
| Cirani et al. [82] | Simulation | Programming language: Java Operating system: Contiki, Linux (Ubuntu) Simulation tools: Cooja | Self-configuration and service discovery, without traffic efficiency statistics. |
| Tracey et al. [83] | Implementation | Programming language: C and Java Operating system: Linux and Contiki Technologies: Hadoop HBase | The proposition considered mixed resource devices, but without presenting fault tolerance or self-management strategies. |
| Catarinucci et al. [84] | Case study: Smart health | Programming language: Java Operating system: Contiki Technologies: MySQL. | Improvement of traffic overhead and interoperability, without addressing the data issues in smart health. |
| Sarkar et al. [85] | Case study | Simulation tools: SecKit | Interoperability without efficiency statistics. |
| Vucinic et al. [86] | Simulation | Operating system: Contiki Simulation tools: Cooja, MSPsim | Improvement of security, latency, and optimization of energy consumption |
| Guo et al. [87] | Case study: Smart campus (Nanjing University) | _ | Services semantic description without any evaluation results. |
| Hou et al. [88] | Implementation | Technologies: Redis, Node.js | Improvement of system performance, without addressing security and privacy issues |
| Balampanis et al. [89] | Case study: Health monitoring | Technologies: Firmware, OpenStack cloud system | Improvement of the flexibility Without considering network performance as well as the accuracy of collected data. |
| Da Cunha et al. [90] | Case study: Industrial environments | Technologies: Mosquito | An architecture for IIoT to reduce development time. |
| Roffia et al. [91] | Case study: Public lighting system | language: SPARQL Operating system: Linux (Ubuntu) Technologies: Smart-M3 Query | Event detection algorithm without considering eminent protocols (i.e., HTTP, MQTT, 6LoWPAN, and CoAP). |
| Beligianni et al. [92] | Case study: Smart metering | ___ | Study of smart metering considering privacy concerns. |
| Lloret et al. [93] | study: Smart metering | Technologies: Spark, MLib Case | The study considered big data and knowledge extraction. |
| Kaur et al. [94] | Case study: University campus | Programming language: JavaScript Technologies: EC2, EMR, Hadoop clusters | Privacy concerns are considered. |
| Zhu et al. [95] | Case study: Product tracing system | Semantic language: Semantic Web Rule Language | The study considered the availability and heterogeneity of information. |
| Perles et al. [96] | Case study: Cultural heritage monitoring | Technologies: Docker, Docker Swarm, MongoDB, SPARK cluster. | Specific architecture for monitoring. |
| Mendoza et al. [97] | Case study: Fog water collection | Programming language: C++ Development platform: MediaTek LinkIt ONE | Ensuring the quality attributes during the design phase. |
| Manogaran et al. [98] | Case study: Health monitoring system | Dataset: Cleveland heart disease DB Technologies: Amazon KMS, Apache HBase, Amazon CloudTrail, EBS, EMR, Pig, S3 | Addressing data management issues in healthcare applications. |
| Pape et al. [99] | Case study: Smart vehicles | ___ | Addressing privacy concerns. |
| Liu et al. [100] | Case study: healthcare system | Technologies: MySQL Modeling environment: Ptolemy II | Addressing the interconnection in a heterogeneous network. |
| Kumar et al. [101] | Case study: Health monitoring system | Programming language: Java Technologies: Hbase, HDFS, EMR, mahout, Pig, S3 Dataset: Heart Disease | Management issues in Big data are addressed without considering the energy efficiency, security, and privacy issues. |
| Usamentiaga et al. [102] | Case study: Temperature monitoring | Programming language: Python and C++ Technologies: Kafka, Docker | The approach addressed data management issues. |
| Moosavi et al. [103] | Case study: Health monitoring system | Operating system: Ubuntu Technologies: MySQL | Management of authentication and authorizations for resource-controlled devices. |
| Guo et al. [104] | Implementation | Operating system: MetaOS, OpenWrt, CentO | Addressing scalability, heterogeneity, and resource management. |
| Suarez et al. [105] | Simulation and implementation | Programming language: Java Simulation tools: NS-3 | Studying interoperation, energy efficiency, and security. |
| De Morais et al. [106] | Case study: Health monitoring system | __ | Addressing security and privacy issues. |
| Lopes et al. [107] | Case study: Healthcare monitoring for disabled people | __ | Addressing data volume as well as heterogeneity. |
| Kitagami et al. [108] | Case study: Energy management system | __ | Decreasing the communication and improving the load between edge servers and the cloud. |
| Loria et al. [109] | Use case: Back-end of “SeeYourBox” services | Programming language: Python Technologies: Radis, AWS IoT | Studying the scalability without evaluation results. |
| Xu et al. [110] | Theoretical analysis and simulation | Programming language: C++ Simulation tools: P2PSim | Addressing load balancing and scalability concerns. |
| Kim et al. [111] | Implementation | Programming language: JavaScript Technologies: Node.JS, Mosquitto | A lightweight and security approach. |
| Sicari et al. [112] | Implementation | Technologies: MongoDB2, Mosquitto, Node.js | Tackling security and heterogeneity issues. |
| Tao et al. [113] | Case study: Smart home | Semantic language: Semantic Web Rule Language Operating system: Ubuntu Technologies: EC2, KVM, OpenStack, VMware vCenter, VMware vSphere | Ensuring interoperability, and security. |
| Hu et al. [114] | Case study: Smart health care | __ | Enhancing device discovery services. |
| Mecibah et al. [115] | Simulation | Programming language: Matlab | Ensuring effective resource exploration in the IoT ecosystem. |
| Mainetti et al. [116] | Simulation | Programming language: Java Technologies: OSGi Semantic language: Semantic Web Rule Language | Dealing with the heterogeneity of data. |
| Tomovic et al. [117] | Case study | __ | Increasing resource management in a mixed IoT ecosystem (video surveillance, transportation, precision agriculture) |
| Lunardi et al. [118] | Case study: Smart buildings | Operating system: Linux (Ubuntu) | Ensuring access management. |
| Sicari et al. [119] | Case study: Smart retailing experience | __ | Enhancing reliability, data quality, security, and privacy. |
| Shanbhag et al. [120] | Case study: Smart office | Technologies: MySQL, PHP, RESTful API | Minimizing human intervention. |
| Din et al. [121] | Health monitoring system (case study) | Technologies: Hadoop Dataset: mHealth dataset | Developing the processing time, but with questionable flexibility. |
| Khan et al. [122] | Case study: IIoT | __ | Reducing human intervention |
| Javed et al. [123] | Case study: Surveillance camera system | Operating system: Linux Technologies: Docker, Kubernetes, Kafka | Supplying fault-tolerant architectures. Not considering the scalability. |
| Xu et al. [124] | Case study: Smart home | Dataset: PLCouple1 Technologies: Amazon CloudWatch, EC2, OSGi | Addressing heterogeneity without much interest in scalability and energy efficiency. |
| Wang et al. [125] | Case study: IIoT | Technologies: RESTful service | Enhancement of resource use. |
| Iqbal et al. [126] | Case study: Smart home | Operating system: Linux, Windows server 2008 Technologies: Hadoop, SPARK | Enhancement of resource use. |
| Ma et al. [127] | Simulation | Evaluation: Simulation Simulation tools: OMNeT++ | Ensuring lightweight security considering malicious node blocking mechanism. |
| Luo et al. [128] | Implementation | Technologies: Docker, KVM, Libvirt, MySQL, Redis | Ensuring an energy-aware algorithm. |
| Marques et al. [129] | Case study: Intelligent waste management | Technologies: Mosquitto | Application protocols regarding latency, power consumption, throughput, and concurrent users. |
| Tiburski et al. [130] | Implementation | Programming language: C Technologies: Hellfire Hypervisor | Ensuring integrity, confidentiality, and availability, without addressing privacy issues. |
| Zarca et al. [131] | Case study: Building management system | Programming language: Python Technologies: MySQL, RabbitMQ, Storm, Kafka Simulation tools: Cooja | Ensuring higher scalability as well as minimizing human intervention. |
| Urbina et al. [132] | Implementation | Programming language: Python and JAVA Operating system: Linaro | Establishing real-time event processing with high availability. |
| Chekired et al. [133] | Simulation | Programming language: MATLAB Simulation tools: NS-2 | Tackling the workload offloading. |
| Sun et al. [134] | Case study: Production system | Programming language: C++ Technologies: RESTful web services Simulation tools: OverSim and OMNeT++ | Ensuring low latency, but without the possibility of use for precise tasks in extensive systems. |
| Pérez et al. [135] | Case study: Building automation | Technologies: ProVerif Simulation tools: Cooja | Addressing end-to-end security with credential institutions for constrained devices. |
| Tekeste et al. [136] | Case Study: Health monitoring system | Dataset: Physio net Programming language: Verilog-RTL | Ensuring scalability based on lossless data compression technique. |
| Malche et al. [137] | Case study: Environmental monitoring | Programming language: Python Technologies: Mosquito, MongoDB | Forbidding unauthorized access to sensors. |
| Dang-Ha et al. [138] | Implementation | __ | Using graph database |
| Ahad MA et al. [139] | Implementation | __ | Optimizing energy consumption without any efficiency statistics. |
| Wang et al. [140] | Case study: Health monitoring system | __ | Introducing requirement assessment for communication technologies. |
| Darabseh et al. [141] | Simulation | Programming languages: Python Technologies: virtual box | Addressing extendibility issues and security analysis for cyber-physical systems. |
| Almajali et al. [142] | Case study: Car tracking application | Programming languages: Java, C#, ASP.Net Technologies: Microsoft IIS Simulation tools: CloudSim | Addressing efficiency as well as heterogeneity. |
| Rocha et al. [143] | Simulation | Programming languages: Java Simulation tools: PeerSim | Addressing scalability without energy consumption evaluation. |
| Pillai et al. [144] | Implementation | Programming languages: Java and Javascript Technologies: Amazon ML, AWS Data Pipeline, AWS IoT, DynamoDB | Ensuring data management combined with data availability. |
| Gopikrishnan et al. [145] | implementation | Programming languages: Java Technologies: Mosquitto Simulation tools: Cooja | Addressing confidentiality, registration, traffic, and energy consumption issues. |
| Naranjo et al. [146] | Case study: Smart city | Programming languages: Java Simulation tools: iFogSim | Enhancing efficiency regarding data heterogeneity for better communication technologies. |
| Maktoubian et al. [147] | Case study: Health monitoring | __ | Considering the monitoring and maintenance. |
| Naranjo et al. [148] | Simulation | Programming languages: Java Technologies: Docker Simulation tools: iFogSim | Addressing energy consumption and latency. |
| Aravind et al. [149] | Case study: Smart vehicles | Simulation tools: self-developed | Decreasing data transmission and increasing the effectiveness regarding the processing time and network bandwidth. |
| Ibrahim et al. [150] | Case study: Greenhouse monitoring | Simulation tools: Riverbed Modeler | Addressing real-time feedback, self-organized networks, data management, and latency. |
| Lomotey et al. [151] | Implementation | Technologies: CouchDB, EC2 | Addressing data traceability and integrity. |
| Mesmoudi et al. [152] | Case study: Smart home | Programming language: Java Technologies: TomCat, SQLite | Tackling heterogeneity issues and introducing an SOA-based middleware. |
| Almeida et al. [153] | Implementation | Programming language: Python, JavaScript Operating system: Linux (Debian) Technologies: Hadoop, Docker, Redis, MySQL | Considering flexibility and heterogeneity. |
| Valecce et al. [154] | Case study: Smart agriculture | Programming language: Typescript Technologies: ActiveMQ, MongoDB, SQLite, Heroku Platform, AWS IoT | Introducing an automation and monitoring architecture for smart agriculture. |
| Lee et al. [155] | Case study: Health monitoring | Operating system: Linux Technologies: Apache HTTP Server, Postgresql | Introducing a token-based approach. |
| Mourdi et al. [156] | Remote learning system | Programming language: Python | Introducing a novel remote leaning platform |
| Indrakumari et al. [157] | Academic study | ___ | Study the growing need for heath wearables |
| Athul et al. [158] | Case study retails | Programming language: Python | Introducing retailer and customer models |
| Shu-Hsien [158] | Case study Mobile payment | __ | State of art of existing business models |
| Classes | Technologies |
|---|---|
| Message queuing systems | RabbitMQ, Apache Kafka, Mosquitto, Celery, ActiveMQ, MongoDB, Apache HBase, Redis, DynamoDB, CouchDB, SQLite, PostgreSQL, Amazon web services, Amazon EMR, Amazon EC2, Amazon S3, Amazon EBS, Amazon CloudWatch, Amazon CloudTrail, Amazon KMS, Amazon SNS, AWS IoT, AWS data pipeline, AWS ML, Apache Hadoop, Apache Mahout, Apache Pig, Apache Spark, Apache Storm, Apache Jena, Apache HTTP server, Apache Tomcat, Microsoft IIS, OpenStack, FIWARE, KeyRock, Google Cloud Messaging, Heroku Platform, Open Service Gateway Initiative, Docker, Docker Swarm, Kubernetes, etc. |
| Database | PostgreSQL, SQLite, CouchDB, DynamoDB, MySQL, HBase, MongoDB, Redis, etc. |
| Cloud frameworks, platforms, and services | Apache Spark, Apache Hadoop, Apache Pig, Apache Mahout, Apache Storm, Apache TomCat, Apache HTTP server, Apache Jena, AWS KMS, AWS cloud trail, Amazon EBS, Amazon EC2, Amazon S3, Amazon ML, AWS Data Pipeline, Amazon EMR, Amazon CloudWatch, Amazon SNS, Microsoft ITS web platforms, Fiware, OpenStack, Google Cloud Message, Heroku Platform, etc. |
| Containers and service platform | Docker swarm, Kubemetes, Docker, OSGi, etc. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Allioui, H.; Mourdi, Y. Exploring the Full Potentials of IoT for Better Financial Growth and Stability: A Comprehensive Survey. Sensors 2023, 23, 8015. https://doi.org/10.3390/s23198015
Allioui H, Mourdi Y. Exploring the Full Potentials of IoT for Better Financial Growth and Stability: A Comprehensive Survey. Sensors. 2023; 23(19):8015. https://doi.org/10.3390/s23198015
Chicago/Turabian StyleAllioui, Hanane, and Youssef Mourdi. 2023. "Exploring the Full Potentials of IoT for Better Financial Growth and Stability: A Comprehensive Survey" Sensors 23, no. 19: 8015. https://doi.org/10.3390/s23198015





