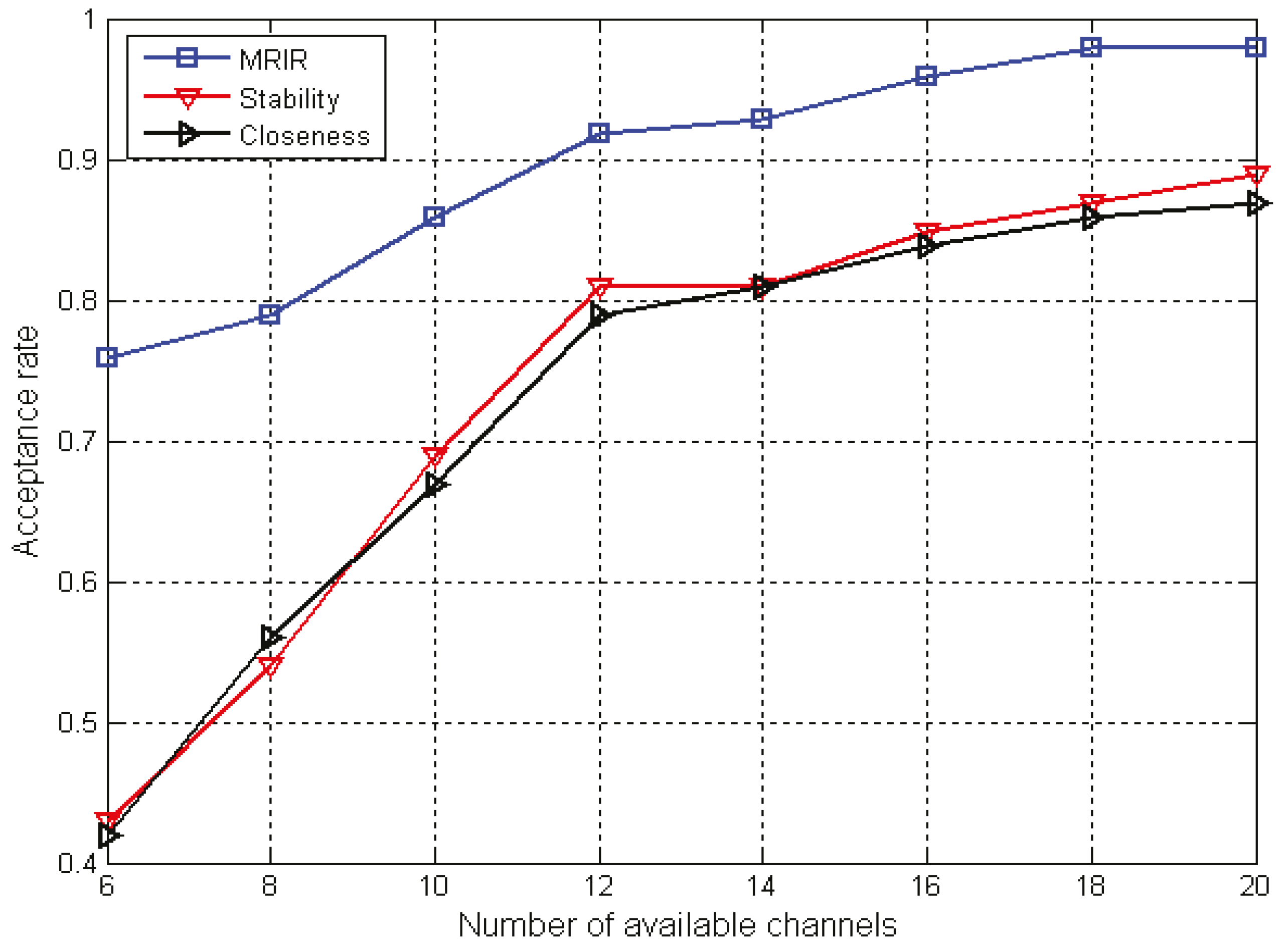
2.1. Network Model
The SU obtains the unused spectrum of the PU by the spectrum sensing algorithm in CWMNs. This paper did not address the specific spectrum sensing algorithm, but focused on how to construct a routing path to satisfy the QoS constraints, and to allocate the unused spectrum resources after the available spectrum is sensed.
It was assumed that there is a common control channel (CCC) for transmitting the available spectrum information and control information between the SUs [
19]. The communication distance of each node is
TR, and the interference distance is
IR, and
IR = 2 ×
TR.
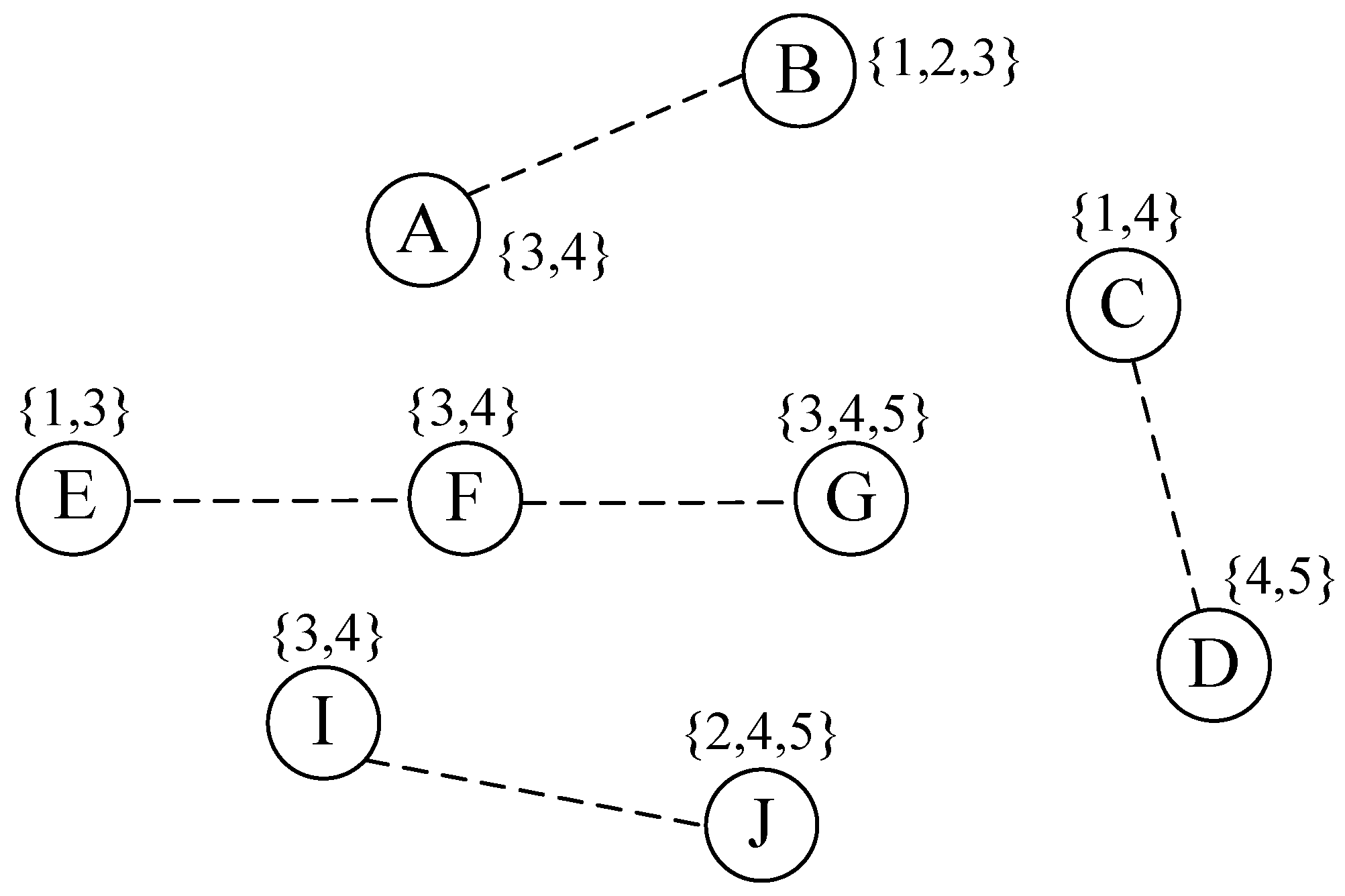
We adopted a simple undirected graph G = (V,E) model of a CWMN, where V represents the set of the CR-Mesh node, and E represents the set of wireless links. The physical distance between node vi and node vj is represented by d(vi,vj). As each node is in a different location and the PU uses a spectrum with a different pattern, the sensed available spectrum of each node was not the same. Each node vi ∈ V had an available channel set Ki, which had been sensed.
Two CR-Mesh nodes that can communicate with each other must satisfy the following conditions: (1) there are common available channels, Ki ∩ Kj ≠ ; and, (2) the nodes must satisfy the restriction of distance, d(vi,vj) < TR.
The set of available channels K was {1,2,3,4,5} in the current network, and the bandwidth of the channel k was Mbps. Different channels had different bandwidths, i.e., different channels i and j, leads to Bi ≠ Bj. x(u,v) = k represents the wireless link (u,v) allocated to channel k. x(u,v) = 0 represents the wireless link (u,v) not allocated to any channel. Every wireless link was either allocated only one channel, or was not allocated a channel.
2.2. Problem Description
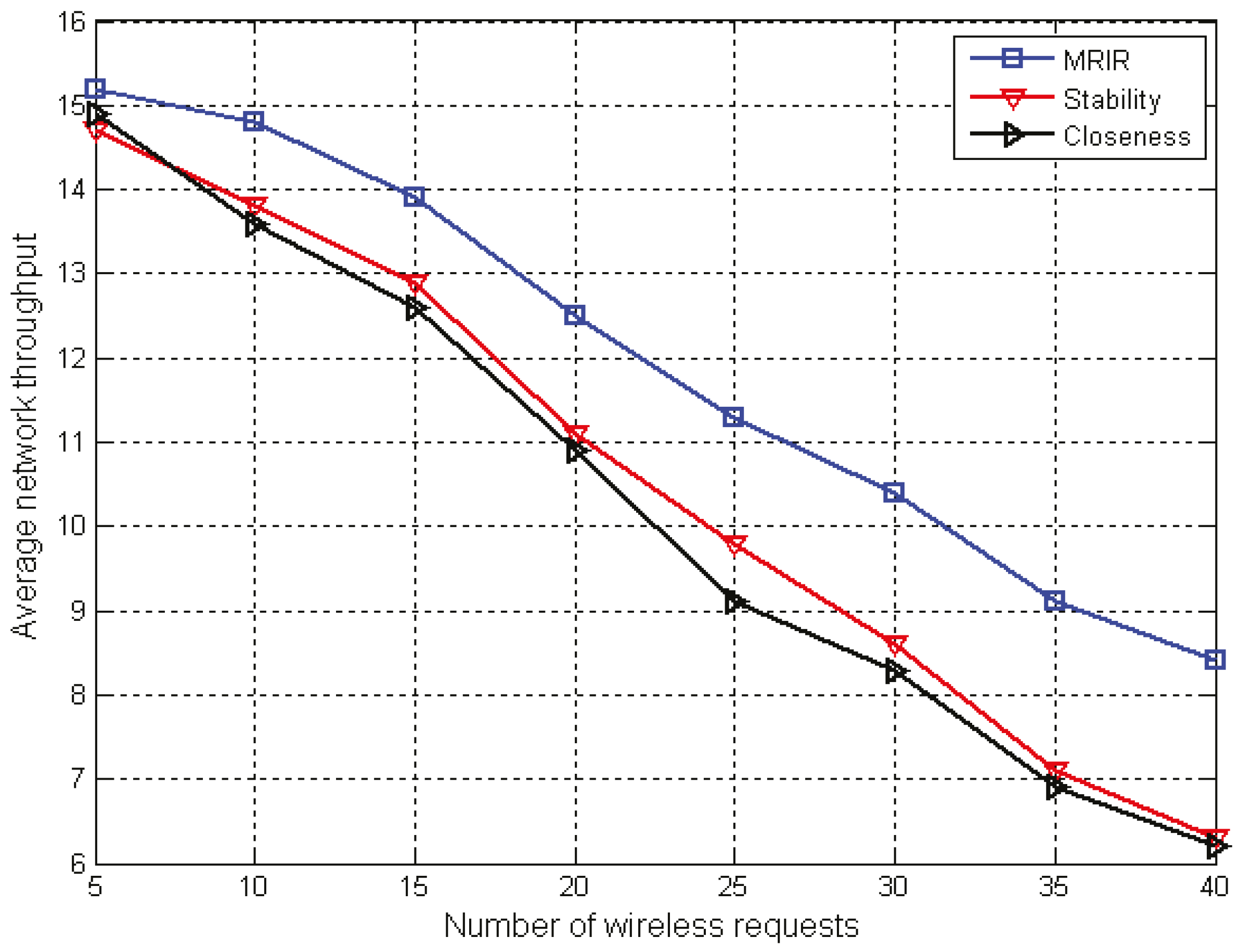
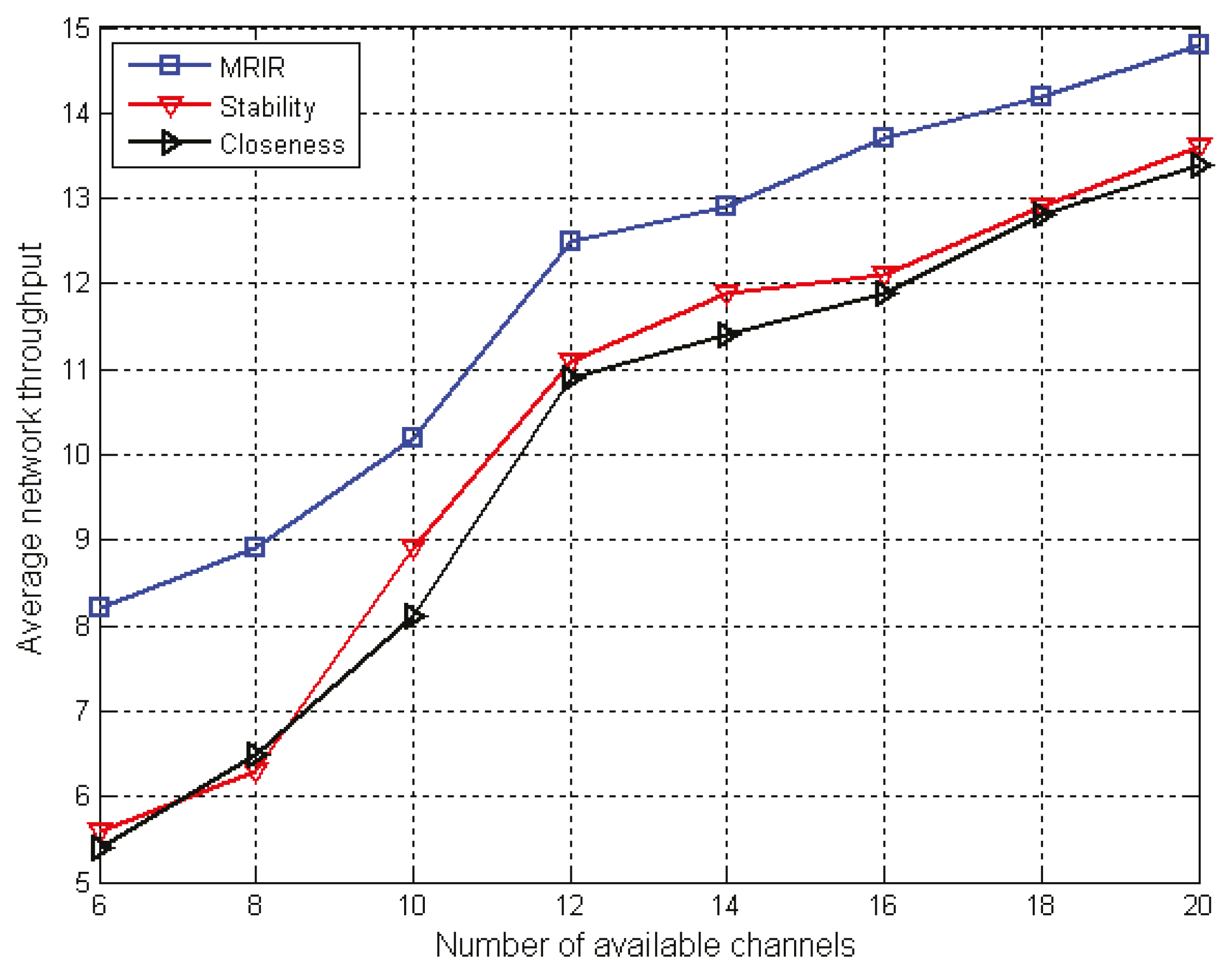
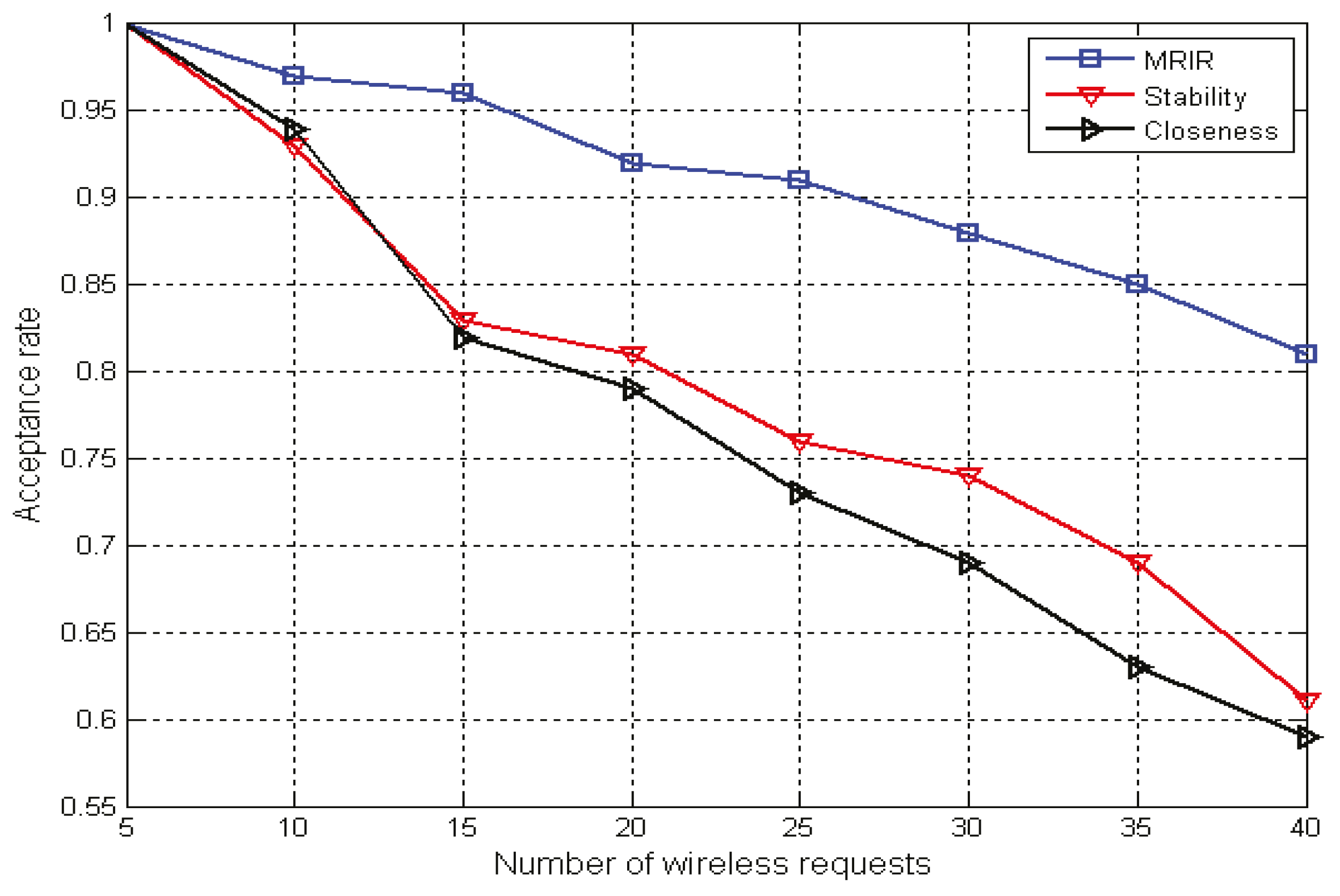
The problem of multi-path routing and spectrum allocation based on channel interference and reusability with the QoS constraints was investigated. For each new arriving wireless request, a primary path and a backup path were constructed simultaneously.
In the backup path construction, a strategy based on channel interference and reusability was proposed to meet the following objectives: (1) when link failure occurs on the primary path, the backup path continues to transmit data to reduce the impact on the accepted wireless request, and improve the network throughput; and, (2) in the construction of the backup path, it is desirable to include a link with the interference to the primary path, and with interference, to a plurality of wireless request primary paths to save resources and to improve the acceptance rate of wireless requests and network throughput.
Let Δ = {γi = (si,di,bi)} be the set of wireless requests, where si and di represent the source and destination node of the wireless request γi; and bi represents the bandwidth constraint of the wireless request γi.
The primary path and backup path from the source node si to the destination node di constructed for the wireless request γi is denoted as and , respectively.
Definition 1. Primary link, which means that for any one of the links (u,v), if (u,v) ∈ , then (u,v) is called the primary link.
Definition 2. Backup link, which means that for any one of the links (u,v), if (u,v) ∈
, then (u,v) is called the backup link.
Definition 3. Idle link, which means that for any one of the links (u,v), if (u,v) , then (u,v) is called the idle link.
Any link (u,v) ∈ E can only be either the primary link, backup link, or idle link. Wireless links (,) and (,) that meet the following conditions will interfere with each other. (1) , or , or , or ; (2) The two links are allocated the same channel, i.e., .
The allocated channel set of links (
u,
v) is denoted as
K(
u,
v), which is given by
I(
u,
v) represents the set of all the links that interfere with the link (
u,
v). If the link (
u,
v) is allocated a different channel, the
I(
u,
v) is different.
Ik(
u,
v) denotes the link set that interferes with the link (
u,
v) allocated the channel
k, which is given by
Definition 4. Interference degree, which means the number of links in the Ik(u,v).
denotes the primary link set that interferes with the link (
u,
v) allocated the channel
k, which is given by
Definition 5. Primary link interference degree, which is the number of links in the set .
denotes the backup link set that interferes with the link (
u,
v) allocated the channel
k, which is given by
Definition 6. Backup link interference degree, which is the number of links in the set .
denotes the idle link set that interferes with the link (
u,
v) allocated the channel
k, which is given by
Definition 7. Idle link interference degree, which is the number of links in the set .
The set of link loads is denoted as
, and the load of the link (
u,
v) on channel
k is denoted as
Mbps. The available bandwidth of the link (
u,
v) on channel
k is denoted as
, which is given by
where
is the proportion of the bandwidth of the link (
,
) used to transmit load
.