Digital Threat and Vulnerability Management: The SVIDT Method
Abstract
:1. Vulnerability Management as a Means of Successfully Using and Adapting to Digital Environments
1.1. Objectives
1.2. The Specifics of Digital Threats
1.3. Methodological Background
1.4. What Will Be Found in the Following Sections?
2. Theoretical and Conceptual Foundations of Vulnerability Management
2.1. Vulnerability and Resilience in the Frame of Sustainability
- (I)
- an ongoing inquiry for
- (II)
- system-limit management (i.e., avoiding system collapse)
- (III)
- in the frame of intra-generational and
- (IV)
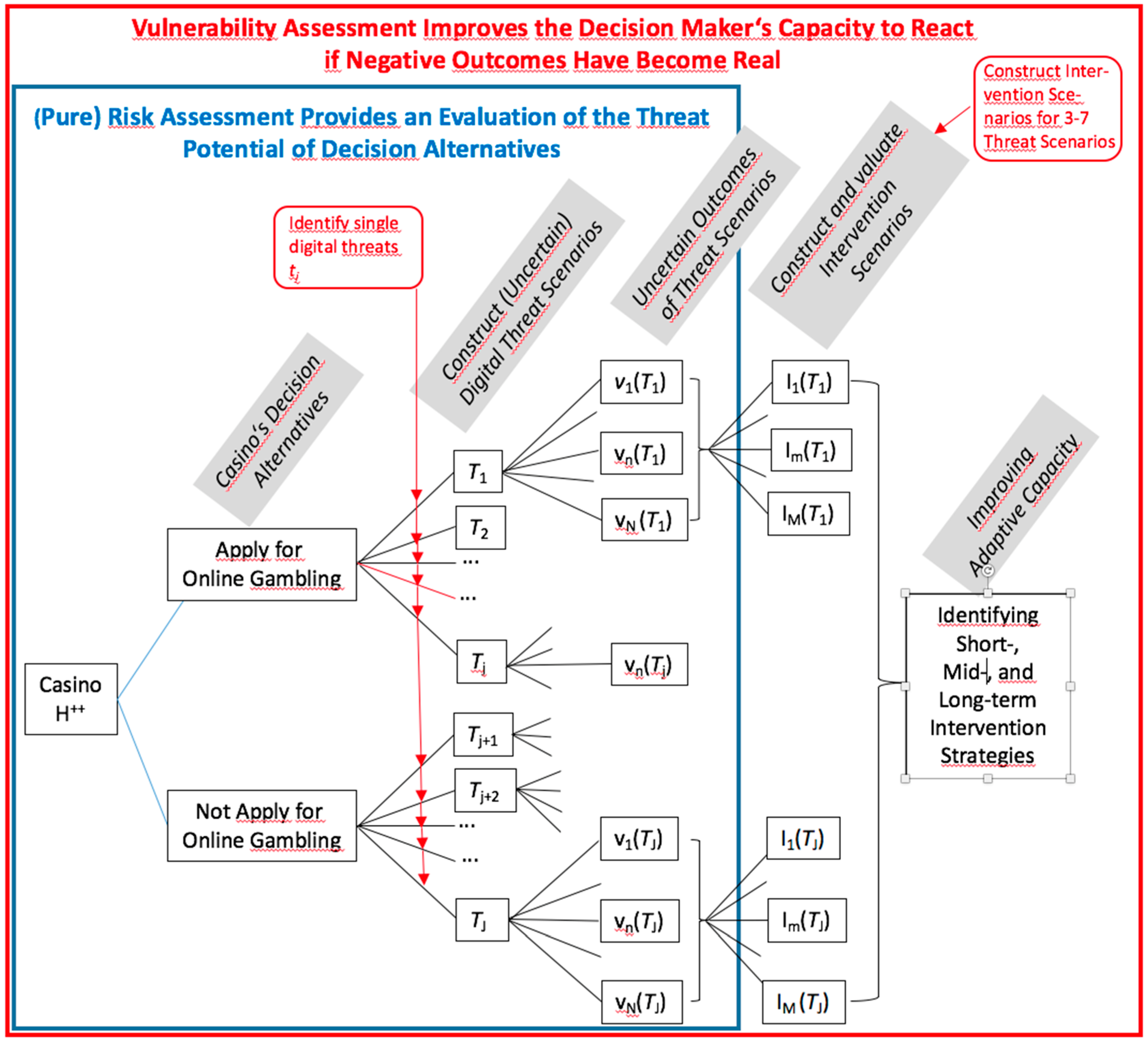
2.2. The Relationship between Risk and Vulnerability
- (1)
- To diagnose, anticipate, and evaluate critical negative impacts; and
- (2)
- To have the sufficient resources (e.g., financial means) to change the behavioral setting in order to
- (2a)
- Reduce exposure,
- (2b)
- Reduce sensitivity (and increase robustness), and
- (2c)
- Cope with any negative impacts that have taken place.
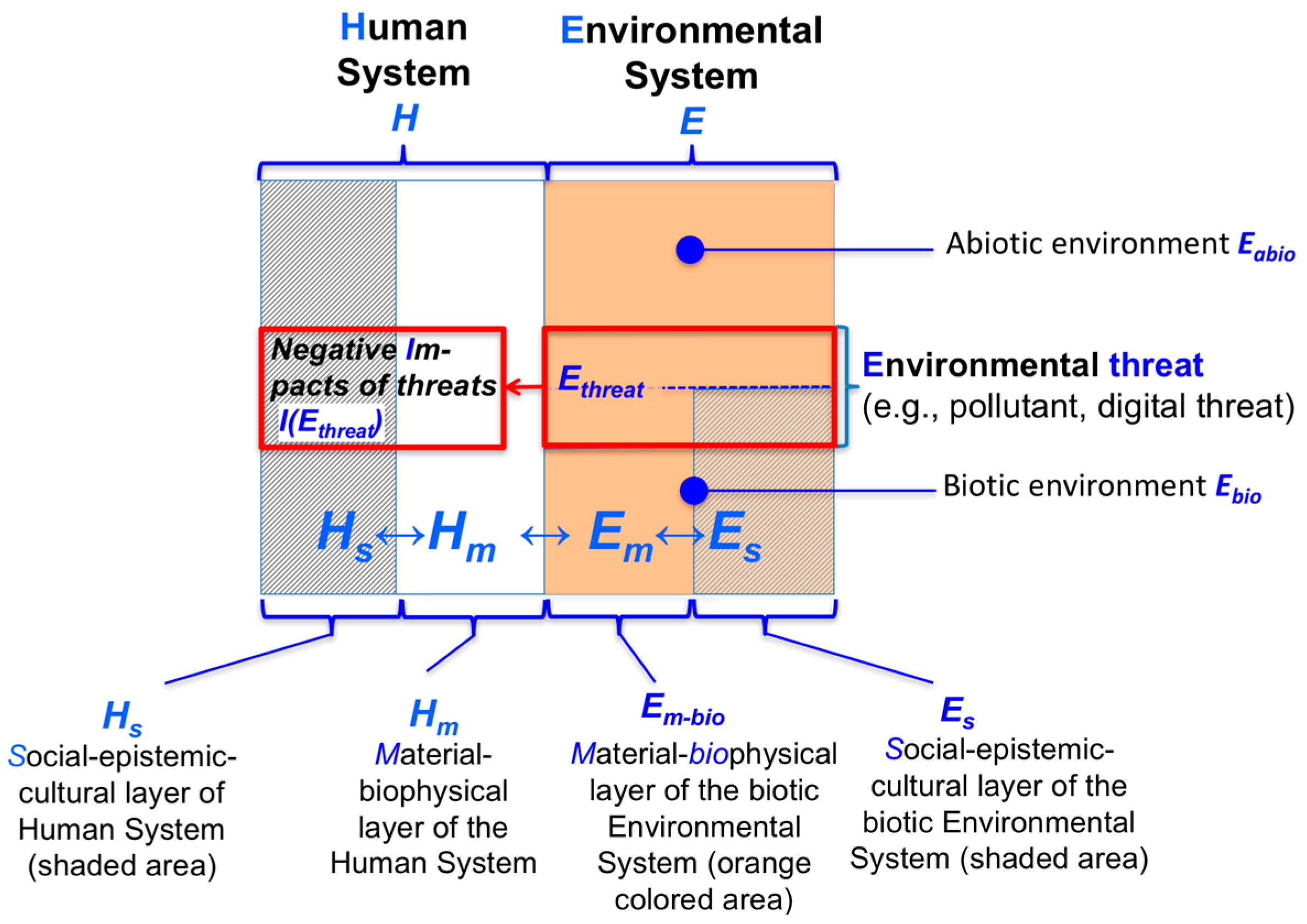
2.3. Vulnerability from a Multilevel Coupled Human–Environment Systems Perspective
2.4. Assimilation and Accommodation as Two Levels of Adaptation
2.5. Vulnerability as a Component of Sustainability Evaluation
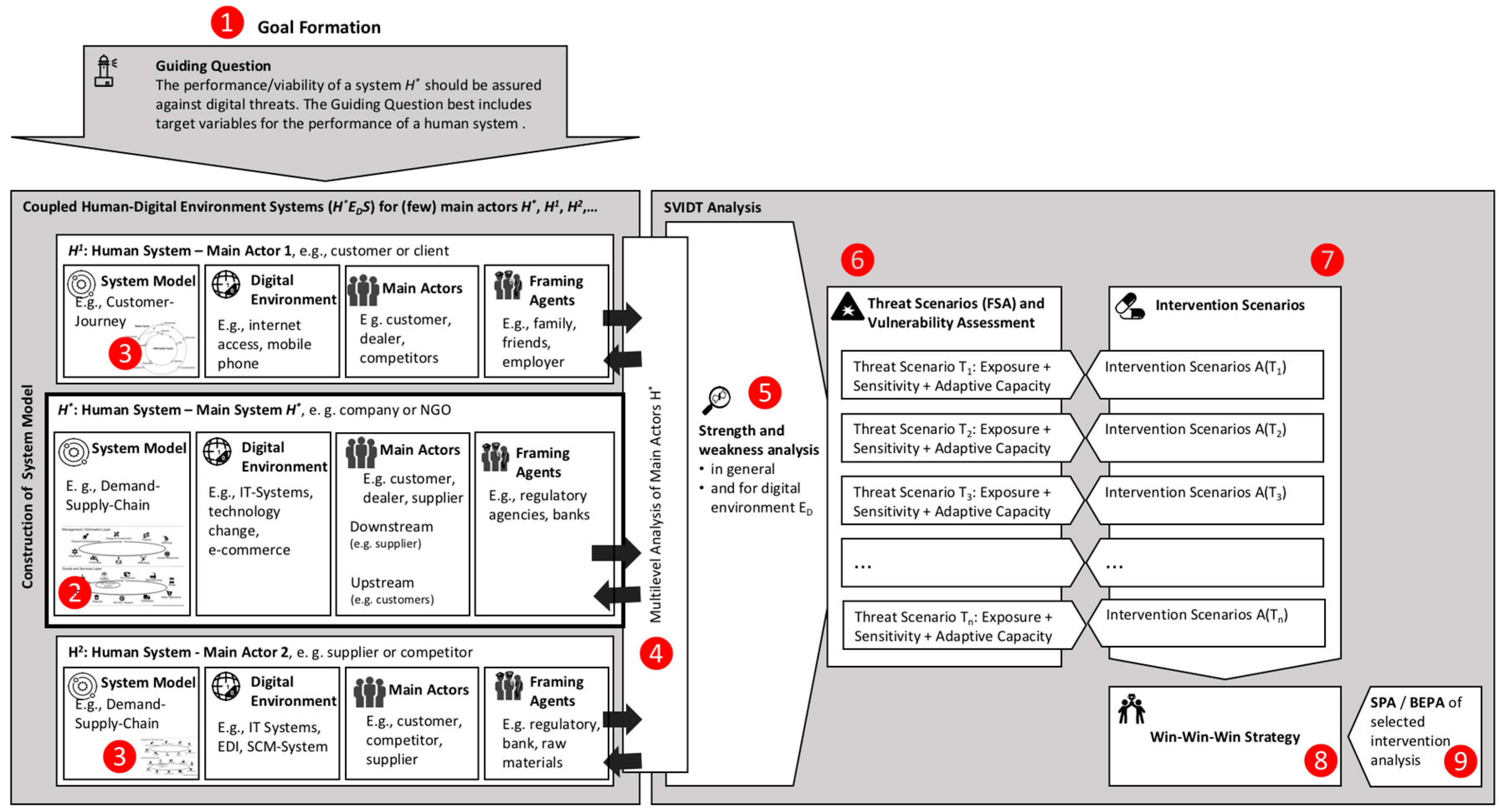
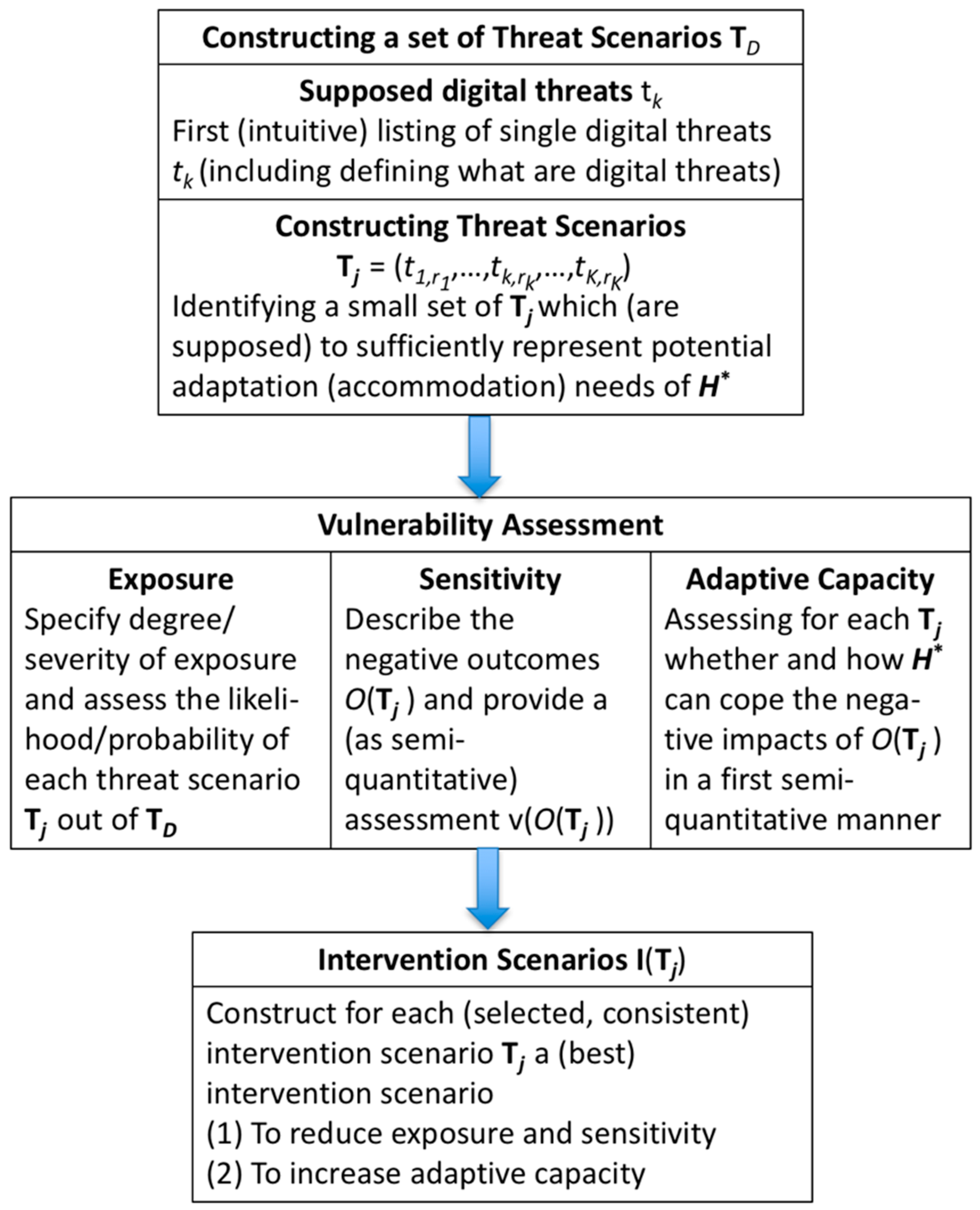
3. The SVIDT Method
- (6.1)
- the identification of digital threats,
- (6.2)
- the construction of threat scenarios, and
- (6.3)
- the assessment of the deliberation of vulnerability (among a research team or in a dialogue between scientists/method experts and representatives of ) with the three main components: exposure, sensitivity, and adaptive capacity.
- the degree of exposure;
- the likelihood of negative effects given a certain exposure, i.e., sensitivity; and
- adaptive capacity that evaluates what countermeasures can be taken against threat scenarios to avoid a “hard landing” of .
4. Applying the SVIDT Method
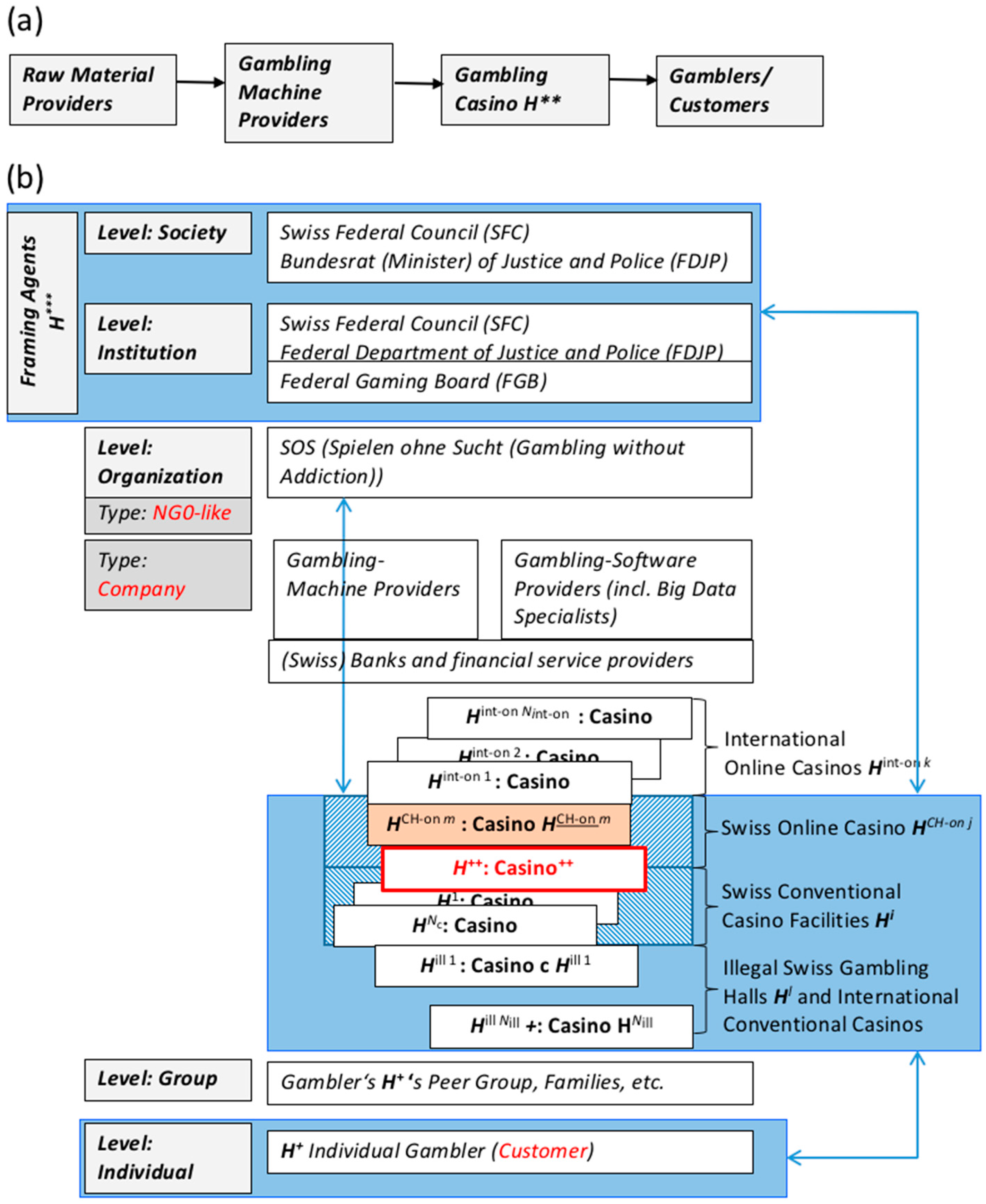
4.1. System Analysis for a Swiss Casino Facing a Transition to Online Gambling
4.2. Goal Formation
4.3. Multilevel SVIDT Analysis Applied to Online Transitioning of the SWISS CASINO H++
4.4. From Strengths and Weaknesses to Threat and Intervention Scenarios
- How is the organizational structure to be changed?
- Do staff possess sufficient knowledge to be prepared to run an online business, including management of Big Data?
- What (international) online-gaming software providers may economically implement a Swiss, social-concept-tailored Internet platform for managing and monitoring gaming?
- What human resources are needed to design procedures for a social concept? Should NGOs or organizations such as SOS or other experts/researchers be included?
- Do we have the right connections with competitors or stakeholders to balance precompetitive joint lobbying (e.g., for collaborating with banks) and competition for getting an online license?
5. Discussion: Vulnerability Assessment as Part of Sustainability Assessment
5.1. The Problem/Challenge
5.2. The Conceptual Framework
5.3. Strengths and Limits of the Proposed SVIDT Method
6. Conclusions
Supplementary Materials
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix A

References
- Helbing, D. Thinking Ahead-Essays on Big Data, Digital Revolution, and Participatory Market Society; Springer: Cham, Switzerland, 2015. [Google Scholar]
- Scholz, R.W.; Blumer, Y.B.; Brand, F.S. Risk, vulnerability, robustness, and resilience from a decision-theoretic perspective. J. Risk Res. 2012, 15, 313–330. [Google Scholar] [CrossRef]
- Klibi, W.; Martel, A.; Guitouni, A. The design of robust value-creating supply chain networks: A critical review. Eur. J. Oper. Res. 2010, 203, 283–293. [Google Scholar] [CrossRef]
- Bauch, C.T.; Sigdel, R.; Pharaon, J.; Anand, M. Early warning signals of regime shifts in coupled human-environment systems. Proc. Natl. Acad. Sci. USA 2016, 113, 14560–14567. [Google Scholar] [CrossRef] [PubMed]
- Galvani, A.P.; Bauch, C.T.; Anand, M.; Singer, B.H.; Levin, S.A. Human–Environment Interactions in Population and Ecosystem Health; National Academy of Sciences: Washington, DC, USA, 2016. [Google Scholar]
- Scholz, R.W.; Binder, C.R. Principles of human-environment systems (HES) research. In Complexity and Integrated Resources Management Transactions of the 2nd Biennial Meeting of the International Environmental Modelling and Software Society; Pahl-Wostl, C., Schmidt, S., Rizzoli, A.E., Jakeman, A.J., Eds.; Zentrum für Umweltkommunikation (ZUK): Osnabrück, Germany, 2004; pp. 791–796. [Google Scholar]
- Hilbert, M.; López, P. The world’s technological capacity to store, communicate, and compute information. Science 2011, 332, 60–65. [Google Scholar] [CrossRef] [PubMed]
- Scholz, R.W. Sustainable Digital Environments: What Major Challenges Is Humankind Facing? Sustainability 2016, 8, 726. [Google Scholar] [CrossRef]
- Block, J.J. Issues for DSM-V: Internet addiction. Am. J. Psychiatry 2008, 165, 306–307. [Google Scholar] [CrossRef] [PubMed]
- Petry, N.M.; Rehbein, F.; Gentile, D.A.; Lemmens, J.S.; Rumpf, H.J.; Mößle, T.; Bischof, G.; Tao, R.; Fung, D.S.; Borges, G.; et al. An international consensus for assessing internet gaming disorder using the new DSM-5 approach. Addiction 2014, 109, 1399–1406. [Google Scholar] [CrossRef] [PubMed]
- Helbing, D. Big Data, privacy, and trusted web: What need to be done. In Thinking Ahead-Essays on Big Data, Digital Revolution, and Participatory Market Society; Helbing, D., Ed.; Springer: Cham, Switzerland, 2015. [Google Scholar]
- Shum, S.B.; Aberer, K.; Schmidt, A.; Bishop, S.; Lukowicz, P.; Anderson, S.; Charalabidis, Y.; Domingue, J.; de Freitas, S.; et al. Towards a global participatory platform Democratising open data, complexity science and collective intelligence. Eur. Phys. J. Spec. Top. 2012, 214, 109–152. [Google Scholar] [CrossRef]
- Frey, C.B.; Osborne, M. The Future of Employment. How Susceptible Are Jobs to Computerisation; University of Oxford: Oxford, UK, 2013. [Google Scholar]
- Frey, C.B. How Susceptible Are Countries Worldwide? Jobs at Risk of Automatation; Oxford University, Oxford Martin School: Oxford, UK, 2016; pp. 11–19. [Google Scholar]
- Helbing, D. The Automatization of Society Is Next; Amazon: Berkshire, UK, 2015. [Google Scholar]
- Bertelsmann Stiftung. “To the Man with a Hammer...”. Augmenting the Policymaker’s Toolbox for a Complex World; Verlag Bertelsmann Stiftung: Gütersloh, Germany, 2016. [Google Scholar]
- Piaget, J. The Development of Thought; Viking: New York, NY, USA, 1977. [Google Scholar]
- Christensen, C. The Innovator’s Dilemma: When New Technologies Cause Great Firms to Fail; Harvard Business Review Press: Cambridge MA, USA, 2013. [Google Scholar]
- Tushman, M.L.; Anderson, P. Technological discontinuities and organizational environments. Adm. Sci. Q. 1986, 31, 439–465. [Google Scholar] [CrossRef]
- Carlo, J.L.; Lyytinen, K.; Rose, G.M. Internet computing as a disruptive information technology innovation: The role of strong order effects. Inf. Syst. J. 2011, 21, 91–122. [Google Scholar] [CrossRef]
- Ackermann, F. Problem structuring methods ‘in the Dock’: Arguing the case for Soft OR. Eur. J. Oper. Res. 2012, 219, 652–658. [Google Scholar] [CrossRef]
- Friend, J.; Hickling, J. Planning under Pressure. The Strategic Choice Approach; Elsevier: Amsterdam, The Netherlands, 2005. [Google Scholar]
- Checkland, P.; Poulter, J. Soft systems methodology. In Systems Approaches to Managing Change: A Practical Guide; Reynolds, M., Holwell, S., Eds.; Springer: London, UK, 2010; pp. 191–242. [Google Scholar]
- Beer, S. The Viable System Model: Its provenance, development, methodology and pathology. J. Oper. Res. Soc. 1984, 35, 7–25. [Google Scholar] [CrossRef]
- Eden, C.; Ackermann, F. SODA—The principles. In Rational Analysis for a Problematic World Revisited; Rosenhead, J., Mingers, J., Eds.; Wiley: Chichester, UK, 2001; pp. 21–41. [Google Scholar]
- Klein, J.T.; Grossenbacher-Mansuy, W.; Häberli, R.; Bill, A.; Scholz, R.W.; Welti, M. (Eds.) Transdisciplinarity: Joint Problem Solving among Science, Technology, and Society. An Effective Way for Managing Complexity; Birkhäuser: Basel, Switzerland, 2001. [Google Scholar]
- Scholz, R.W.; Steiner, G. Transdisciplinarity at the crossroads. Sustain. Sci. 2015, 10, 521–526. [Google Scholar] [CrossRef]
- Jantsch, E. Inter- and transdisciplinary university: A systems approach to education and innovation. Policy Sci. 1970, 1, 403–428. [Google Scholar] [CrossRef]
- Scholz, R.W.; Marks, D. Learning about transdisciplinarity: Where are we? Where have we been? Where should we go? In Transdisciplinarity: Joint Problem Solving among Science, Technology, and Society; Klein, J.T., Grossenbacher-Mansuy, W., Häberli, R., Bill, A., Scholz, R.W., Welti, M., Eds.; Birkhäuser Verlag AG: Basel, Switzerland, 2001; pp. 236–252. [Google Scholar]
- Scholz, R.W.; Tietje, O. Embedded Case Study Methods: Integrating Quantitative and Qualitative Knowledge; Sage: Thousand Oaks, CA, USA, 2002. [Google Scholar]
- Scholz, R.W.; Steiner, G. The real type and the ideal type of transdisciplinary processes. Part II—What constraints and obstacles do we meet in practice? Sustain. Sci. 2015, 10, 653–671. [Google Scholar]
- Harsanyi, J.C. Cardinal utility in welfare economics and in the theory of risk-taking. J. Political Econ. 1953, 61, 434–435. [Google Scholar] [CrossRef]
- Slovic, P. Assessment of risk-taking behavior. Psychol. Bull. 1964, 61, 220–233. [Google Scholar] [CrossRef] [PubMed]
- Paustenbach, D.J. (Ed.) The Risk Assessment of Environmental and Human Health Hazards: A Textbook of Case Studies; Wiley & Sons, Inc.: New York, NY, USA, 1989. [Google Scholar]
- Moser, C.; Stauffacher, M.; Blumer, Y.B.; Scholz, R.W. From risk to vulnerability: The role of perceived adaptive capacity for the acceptance of contested infrastructure. J. Risk Res. 2015, 18, 622–636. [Google Scholar] [CrossRef]
- Keeney, R.L.; Raiffa, H. Decisions with Multiple Objectives: Preferences and Value Trade-Offs; Wiley: New York, NY, USA, 1976. [Google Scholar]
- Saaty, T.L. The Analytic Hierarchy Process, 2nd ed.; RWS Publications: Pittburgh, PA, USA, 1990; Volume 287. [Google Scholar]
- Mintzberg, H. The fall and rise of strategic planning. Harv. Bus. Rev. 1994, 72, 107–114. [Google Scholar]
- Helms, M.M.; Nixon, J. Exploring SWOT analysis—Where are we now? A review of academic research from the last decade. J. Strategy Manag. 2010, 3, 215–251. [Google Scholar] [CrossRef]
- Checkland, P.; Scholes, J. Soft Systems Methodology in Action; Wiley: Chichester, UK, 1990. [Google Scholar]
- Midgley, G.; Cavana, R.Y.; Brocklesby, J.; Foote, J.L.; Wood, D.R.R.; Ahuriri-Driscoll, A. Towards a new framework for evaluating systemic problem structuring methods. Eur. J. Oper. Res. 2013, 229, 143–154. [Google Scholar] [CrossRef]
- Rosenhead, J.; Mingers, L. (Eds.) Rational Analysis for a Problematic World Revisited; Wiley: Chichester, UK, 2001. [Google Scholar]
- Midgley, G. Systems Thinking; Sage: London, UK, 2003; Volumes I–IV. [Google Scholar]
- Gibbons, M.; Limoges, C.; Nowotny, H.; Schwartzman, S.; Scott, P.; Trow, M. The New Production of Knowledge; Sage: London, UK, 1994. [Google Scholar]
- Scholz, R.W.; Lang, D.J.; Wiek, A.; Walter, A.L.; Stauffacher, M. Transdisciplinary case studies as a means of sustainability learning: Historical framework and theory. Int. J. Sustain. Higher Educ. 2006, 7, 226–251. [Google Scholar] [CrossRef]
- Scholz, R.W.; Steiner, G. The real type and the ideal type of transdisciplinary processes. Part I—Theoretical foundations. Sustain. Sci. 2015, 10, 527–544. [Google Scholar] [CrossRef]
- McCarthy, J.; Canziani, O.F.; Leary, N.A.; Dokken, D.J.; White, K.S. Climate Change 2001: Impacts, Adaptation and Vulnerability; Contribution of Working Group II to the Third Assessment Report of the IPPC; Cambridge University Press: Cambridge, UK, 2001. [Google Scholar]
- Holling, C.S.; Gunderson, L.H. Resilience and adaptive cycles. In Panarchy: Understanding Transformation in Human and Natural Systems; Gunderson, L.H., Holling, C.S., Eds.; Island Press: Washington, DC, USA, 2002; pp. 25–63. [Google Scholar]
- Folke, C.; Carpenter, S.; Walker, B.; Scheffer, M.; Elmqvist, T.; Gunderson, L.; Holling, C.S. Regime shifts, resilience, and biodiversity in ecosystem management. Annu. Rev. Ecol. Evol. Syst. 2004, 35, 557–581. [Google Scholar] [CrossRef]
- Adger, W.N. Vulnerability. Glob. Environ. Chang. 2006, 16, 268–281. [Google Scholar] [CrossRef]
- Turner, B.L.; Kasperson, R.E.; Matson, P.A.; McCarthy, J.J.; Corell, R.W.; Christensen, L.; Eckley, N.; Kasperson, J.X.; Luers, A.; Martello, M.L.; et al. A framework for vulnerability analysis in sustainability science. Proc. Natl. Acad. Sci. USA 2003, 100, 8074–8079. [Google Scholar] [CrossRef] [PubMed]
- Turner, B.L.; Matson, P.A.; McCarthy, J.J.; Corell, R.W.; Christensen, L.; Eckley, N.; Hovelsrud-Broda, G.K.; Kasperson, J.X.; Kasperson, R.E.; Luers, A.; et al. Illustrating the coupled human-environment system for vulnerability analysis: Three case studies. Proc. Natl. Acad. Sci. USA 2003, 100, 8080–8085. [Google Scholar] [CrossRef] [PubMed]
- Laws, D.; Scholz, R.W.; Shiroyama, H.; Susskind, L.; Suzuki, T.; Weber, O. Expert views on sustainability and technology implementation. Int. J. Sustain. Dev. World Ecol. 2004, 11, 247–261. [Google Scholar] [CrossRef]
- World Commission on Environment and Development. Our common future. In UN Documents; United Nations: New York, NY, USA, 1987. [Google Scholar]
- Paustenbach, D.J. (Ed.) Human and Ecological Risk Assessment. Theory and Practice; Wiley: New York, NY, USA, 2002. [Google Scholar]
- Vlek, C.A.J.; Stallen, P.-J. Judging risks and benefits in the small and in the large. Organ. Behav. Hum. Perform. 1981, 28, 235–271. [Google Scholar] [CrossRef]
- Oh, J.H.; Yang, S.J.; Do, Y.R. Healthy, natural, efficient and tunable lighting: Four-package white LEDs for optimizing the circadian effect, color quality and vision performance. Light Sci. Appl. 2014, 3, e141. [Google Scholar] [CrossRef]
- Figueiro, M.G.; Wood, B.; Plitnick, B.; Rea, M.S. The impact of light from computer monitors on melatonin levels in college students. Neuroendocrinol. Lett. 2011, 32, 158–163. [Google Scholar] [PubMed]
- Brachinger, H.W.; Weber, M. Risk as a primitive: A survey of measures of perceived risk. Oper. Res. Spectr. 1997, 19, 235–294. [Google Scholar] [CrossRef]
- Aven, T. Risk assessment and risk management: Review of recent advances on their foundation. Eur. J. Oper. Res. 2016, 253, 1–13. [Google Scholar] [CrossRef]
- Holling, C.S. Resilience and stability of ecological systems. Annu. Rev. Ecol. Syst. 1973, 4, 1–23. [Google Scholar] [CrossRef]
- Gunderson, L.H.; Holling, C.S. (Eds.) Panarchy: Understanding Transformation in Human and Natural Systems; Island Press: Washington, DC, USA, 2002. [Google Scholar]
- Cohen, M.A.; Lee, H.L. Strategic analysis of integrated production-distribution systems—Models and methods. Oper. Res. 1988, 36, 216–228. [Google Scholar] [CrossRef]
- Tax, S.S.; McCutcheon, D.; Wilkinson, I.F. The Service Delivery Network (SDN): A Customer-Centric Perspective of the Customer Journey. J. Serv. Res. 2013, 16, 454–470. [Google Scholar] [CrossRef]
- Scholz, R.W. Environmental Literacy in Science and Society: From Knowledge to Decisions; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Soloveichik, D.; Winfree, E. The computational power of Benenson automata. Theor. Comput. Sci. 2005, 344, 279–297. [Google Scholar] [CrossRef]
- Ryan, M.; Goldman, A. Officials: San Bernardino Shooters Pledged Allegiance to the Islamic State, in Chicago Tribune. Available online: http://www.chicagotribune.com/news/nationworld/ct-san-bernardino-shooting-20151208-story.html (accessed on 1 April 2017).
- Schwartz, P.M. Privacy and democracy in cyberspace. Vanderbilt Law Rev. 1999, 52, 1607. [Google Scholar] [CrossRef]
- Sklansky, D.A. Too much information: How not to think about privacy and the Fourth Amendment. Calif. Law Rev. 2014, 102, 1069–1121. [Google Scholar]
- Hedstrom, M. Digital preservation: A time bomb for digital libraries. Comput. Humanit. 1997, 31, 189–202. [Google Scholar] [CrossRef]
- Morency, K. Cybersecurity finally takes centers stage in the US. J. High Technol. Law 2014, 15, 192–229. [Google Scholar]
- Yar, M. Cybercrime and Society; Sage: Thousand Oaks, CA, USA, 2013. [Google Scholar]
- Piaget, J. Genetic Epistemology; Columbia University Press: New York, NY, USA, 1968. [Google Scholar]
- Scholz, R.W. Begriffslernen als Regelerwerb: Die Entwicklung des Proportionsbegriffs aus der Sicht des Informationsverarbeitungsansatzes. [The acquisition of the concept of proportions from a rule assessment approach]. Math. Didact. 1989, 12, 63–87. [Google Scholar]
- Commission Expert Group on Taxation of the Digital Economy, Report; European Commision: Brussels, Bulgium, 2014.
- Justitia US Law. 2014 Kentucky Revised Statutes, Chapter 139—Sales and Use Taxes; Justitia: Mountain View, CA, USA, 2014. [Google Scholar]
- Bell, S.; Morse, S. Sustainability Indicators: Measuring the Immeasurable? Earthscan: London, UK, 2008. [Google Scholar]
- Bell, S.; Morse, S. Measuring Sustainability: Learning from Doing; Routledge: London, UK, 2013. [Google Scholar]
- Parris, T.M.; Kates, R.W. Characterizing and measuring sustainable development. Annu. Rev. Environ. Resour. 2003, 28, 559–586. [Google Scholar] [CrossRef]
- Evans, A.; Strezov, V.; Evans, T.J. Assessment of sustainability indicators for renewable energy technologies. Renew. Sustain. Energy Rev. 2009, 13, 1082–1088. [Google Scholar] [CrossRef]
- Singh, R.K.; Muty, H.R.; Gupta, S.K.; Dikshit, A.K. An overview of sustainability assessment methodologies. Ecol. Indic. 2009, 9, 189–212. [Google Scholar] [CrossRef]
- Binder, C.R.; Feola, G.; Steinberger, J.K. Considering the normative, systemic and procedural dimensions in indicator-based sustainability assessments in agriculture. Environ. Impact Assess. Rev. 2010, 30, 71–81. [Google Scholar] [CrossRef]
- Lang, D.J.; Binder, C.R.; Scholz, R.W.; Wiek, A.; Stäublib, B.; Sieber, C. Sustainability Potential Analysis (SPA) of landfills—A systemic approach: Initial application towards a legal landfill assessment. J. Clean. Prod. 2007, 15, 1654–1661. [Google Scholar] [CrossRef]
- Lang, D.J.; Scholz, R.W.; Binder, C.R.; Wiek, A.; Stäublib, B. Sustainability Potential Analysis (SPA) of landfills—A systemic approach: Theoretical considerations a systemic. J. Clean. Prod. 2007, 15, 1628–1638. [Google Scholar] [CrossRef]
- Hermans, L.M.; Thissen, W.A.H. Actor analysis methods and their use for public policy analysts. Eur. J. Oper. Res. 2009, 196, 808–818. [Google Scholar] [CrossRef]
- Bryson, J.M. What to do when stakeholders matter. Stakeholder identification and analysis techniques. Public Manag. Rev. 2004, 6, 21–53. [Google Scholar] [CrossRef]
- Steiner, G. Supporting sustainable innovation through stakeholder management: A systems view. Int. J. Innov. Learn. 2008, 5, 595–616. [Google Scholar] [CrossRef]
- Kelly, G.A. The Psychology of Personal Constructs; Norton: New York, NY, USA, 1955. [Google Scholar]
- Fransella, F.; Bell, R.; Bannister, D. A Manual for Repertory Grid Technique; John Wiley: New York, NY, USA, 2004. [Google Scholar]
- Eden, C. Analyzing cognitive maps to help structure issues or problems. Eur. J. Oper. Res. 2004, 159, 673–686. [Google Scholar] [CrossRef]
- Tietje, O. Identification of a small reliable and efficient set of consistent scenarios. Eur. J. Oper. Res. 2005, 162, 418–432. [Google Scholar] [CrossRef]
- Von Wirth, T.; Hayek, U.K.; Kunze, A.; Neuenschwander, N.; Stauffacher, M.; Scholz, R.Z. Identifying urban transformation dynamics: Functional use of scenario techniques to integrate knowledge from science and practice. Technol. Forecast. Soc. Chang. 2014, 89, 115–130. [Google Scholar] [CrossRef]
- Tietje, O.; Scholz, R.W.; Hesske, S.; Grasmück, D.; Sell, J.; Weber, O. Integrale Bewertung von Sanierungsalternativen: Potentiale, Komponenten und Grenzen eines transdisziplinären Prozesses. TerraTech 2002, 2, 44–48. [Google Scholar]
- FDJP. Bundesgesetz über Geldspiele (Geldspielgesetz, BGS) [935.51] (Entwurf)—Federal Law on Real Money Gabling [935.51] (Proposal). 2016. Available online: https://www.admin.ch/opc/de/classified-compilation/20151500/index.html (accessed on 7 April 2016).
- Renz, F.; de Carli, L. Schweiz bricht Tabu und sperrt Website. TagesAnzeiger, 2 March 2017; 1. [Google Scholar]
- Grusser, S.M.; Thalemann, R.; Griffiths, M.D. Excessive computer game playing: Evidence for addiction and aggression? Cyberpsychol. Behav. 2007, 10, 290–292. [Google Scholar] [CrossRef] [PubMed]
- SCV. Jahresbericht SCV; Schweizer Casino Verband: Bern, Switzerland, 2014. [Google Scholar]
- Glarner, A.; Valloni, N. The Principal Objections to the Swiss Draft Gambling Law. Available online: http://www.cecileparkmedia.com/online-gambling-lawyer/article_template.asp?Contents=Yes&from=woglr&ID=2098 (accessed on 1 April 2017).
- FDJP. Neues Gesetz für alle Geldspiele: Bundesrat Verabschiedet Botschaft. 2015. Available online: http://www.ejpd.admin.ch/ejpd/de/home/aktuell/news/2015/2015-10-21.html (accessed on 21 October 2015).
- Swiss Supreme Court. Swiss Supreme Court, BGer 2C_776/2013 vom 27.05.2014; University of Bern: Bern, Switzerland, 2014; Available online: http://www.servat.unibe.ch/dfr/bger/140527_2C_776-2013.html (accessed on 1 April 2017).
- Eichenberger, Y.; Rihs-Middel, M. Glücksspiel: Verhalten und Problematik in der Schweiz. Schlussbericht, 7 August 2016; Ferarihs: Villars-sur-Glâne, Switzerland, 2014. [Google Scholar]
- Bondolfi, G.; Jermann, F.; Ferrero, F.; Zullino, D.; Osiek, C. Prevalence of pathological gambling in Switzerland after the opening of casinos and the introduction of new preventive legislation. Acta Psychiatr. Scand. 2008, 117, 236–239. [Google Scholar] [CrossRef] [PubMed]
- Abderhalden, I. Schweizer Suchtpanorama 2016, Mediendossier, 8 February 2016; Sucht Schweiz: Lausanne, Switzerland, 2016. [Google Scholar]
- Jeanrenaud, C.; Gay, M.; Kohler, D.; Besson, J.; Simon, O. Le Coût Social du jeu Excessif en Suisse; Institut de Recherches Économiques de l’Université de Neuchâtel et Centre du jeu Excessif: Neuchatel, Switzerland, 2012. [Google Scholar]
- Sucht Schweiz. Stellungnahme von Sucht Schweiz zum neuen Geldspielgesetz (BGS) vom 18.8.2014; Sucht Schweiz: Lausanne, Switzerland, 2014. [Google Scholar]
- Chopra, S.; Meindl, P. Supply Chain Management. Strategy, Planning & Operation; Prentice Hall: New York, NY, USA, 2012. [Google Scholar]
- Bojanova, I. The Digital Revolution: What’s on the Horizon? IEEE: Piscataway, NJ, USA, 2014; pp. 8–12. [Google Scholar]
- Schumpeter, J.A. The process of creative destruction. In Capitalism, Socialism and Democracy; Schumpeter, J.A., Ed.; Allen and Unwin: London, UK, 1950. [Google Scholar]
- Simon, H.A. A behavioral model of rational choice. Q. J. Econ. 1955, 69, 99–118. [Google Scholar] [CrossRef]
- Brunswik, E. The Conceptual Framework of Psychology; University of Chicago Press: Chicago, IL, USA, 1952. [Google Scholar]
- Ragnedda, M.; Muschert, G.W. (Eds.) The Digital Divide. The Internet and Social Inequality in International Perspective; Routledge: London, UK, 2013. [Google Scholar]
- Van Dijk, J.; Hacker, K. The digital divide as a complex and dynamic phenomenon. Inf. Soc. 2003, 19, 315–326. [Google Scholar] [CrossRef]
- Wessels, B. The Reproduction and Reconfiguration of Inequality: Differentiation and Class, Status and Power in the Dynamics of Digital Divides in The Digital Divide. The Internet and Social Inequality in International Perspective; Ragnedda, M., Muschert, G.W., Eds.; Routledge: London, UK, 2013; pp. 17–29. [Google Scholar]
- Seagriff, T.; Lord, S. Soft operational research techniques : Current and future uses. YoungOR 2009, 17, 40–53. [Google Scholar]
- Mingers, J.; Rosenhead, J. Introduction to the special issue: Teaching soft OR, problem structuring methods, and multimethodology. INFORMS Trans. Educ. 2011, 12, 1–3. [Google Scholar] [CrossRef]
- Gregory, R.; Failing, L.; Harstone, M.; Long, G.; McDaniels, T.; Ohlson, D. Structured Decision Making. A Practical Guide to Environmental Management Choices; Wiley: Chicester, UK, 2012. [Google Scholar]
- Wang, W.; Liu, S.W.; Mingers, J. A systemic method for organisational stakeholder identification and analysis using Soft Systems Methodology (SSM). Eur. J. Oper. Res. 2015, 264, 562–574. [Google Scholar] [CrossRef]
| No. | Labels from BEPA and SPA | Essential Properties | ||
|---|---|---|---|---|
| (1) | Function/system productivity and performance | The functions a human system may provide | ||
| (2) | Vulnerability (ability to accommodate) | Components of vulnerability | ||
| (2a) | Exposure to threats (probability) | |||
| (2b) | Sensitivity to threats (magnitude of harm), also considered a complement of robustness (which includes buffer capacity) | |||
| (2c) | Adaptive capacities | |||
| Properties affecting vulnerability | ||||
| (2.1) | Change rates | Sensitivity increases in times of overly fast decline or growth of a system. | ||
| (2.2) | Well-structuredness | Does the system show an inefficient connectivity, edginess, network structure, or other patterns? | ||
| (2.3) | (In-)Dependence on other systems | Can the system survive if other systems are in a critical state? | ||
| (3) | Societal justice, normative aspects, intra- and intergenerational justice | Does the distribution of wealth enter a stage that the poor will resist? Will future generations (or the system at later points in time) suffer because of the consumption/environmental impacts of today’s generation? | ||
| Label | Threat for a Swiss Casino | Levels (r = 1, 2) | Key Questions for Identifying Interventions |
|---|---|---|---|
| Critical decline of pre-tax profit after legalizing Swiss online gambling. | : <x% : ≥x% | How does a business plan look with reduced demand for terrestrial gambling if no online concession is received (a, b1) or if a concession is received (b2)? | |
| How does the banning of foreign Internet access function? | r: well-functioning r not functioning | What levels of reduction can be met with what means? By what promotion might we get what share of gamblers and what gaming sum? | |
| Investment for successfully introducing online gambling is beyond the possibility/capacity of the casino. | : yes : no | If one’s own capacity is too small, who might become a business partner? | |
| Costs and conceptualizing an application for an online license (including a social license), given (*) a decline of the proposal by FGB, are too high. | : too high to survive; : feasible | If 1, who is a potential partner for a joint application? | |
| Costs for practicing/running a social concept for online monitoring. | : feasible; : too high to survive | Can you build an alliance with other casinos? | |
| … | |||
| … | |||
| (Swiss) Banks do not cooperate in the monitoring of endangered gamblers. | +/− | What alliances/laws/decrees are needed? | |
| … | |||
| … | … |
© 2017 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Scholz, R.W. Digital Threat and Vulnerability Management: The SVIDT Method. Sustainability 2017, 9, 554. https://doi.org/10.3390/su9040554
Scholz RW. Digital Threat and Vulnerability Management: The SVIDT Method. Sustainability. 2017; 9(4):554. https://doi.org/10.3390/su9040554
Chicago/Turabian StyleScholz, Roland W. 2017. "Digital Threat and Vulnerability Management: The SVIDT Method" Sustainability 9, no. 4: 554. https://doi.org/10.3390/su9040554





