A Study on a JWT-Based User Authentication and API Assessment Scheme Using IMEI in a Smart Home Environment
Abstract
:1. Introduction
2. Related Works
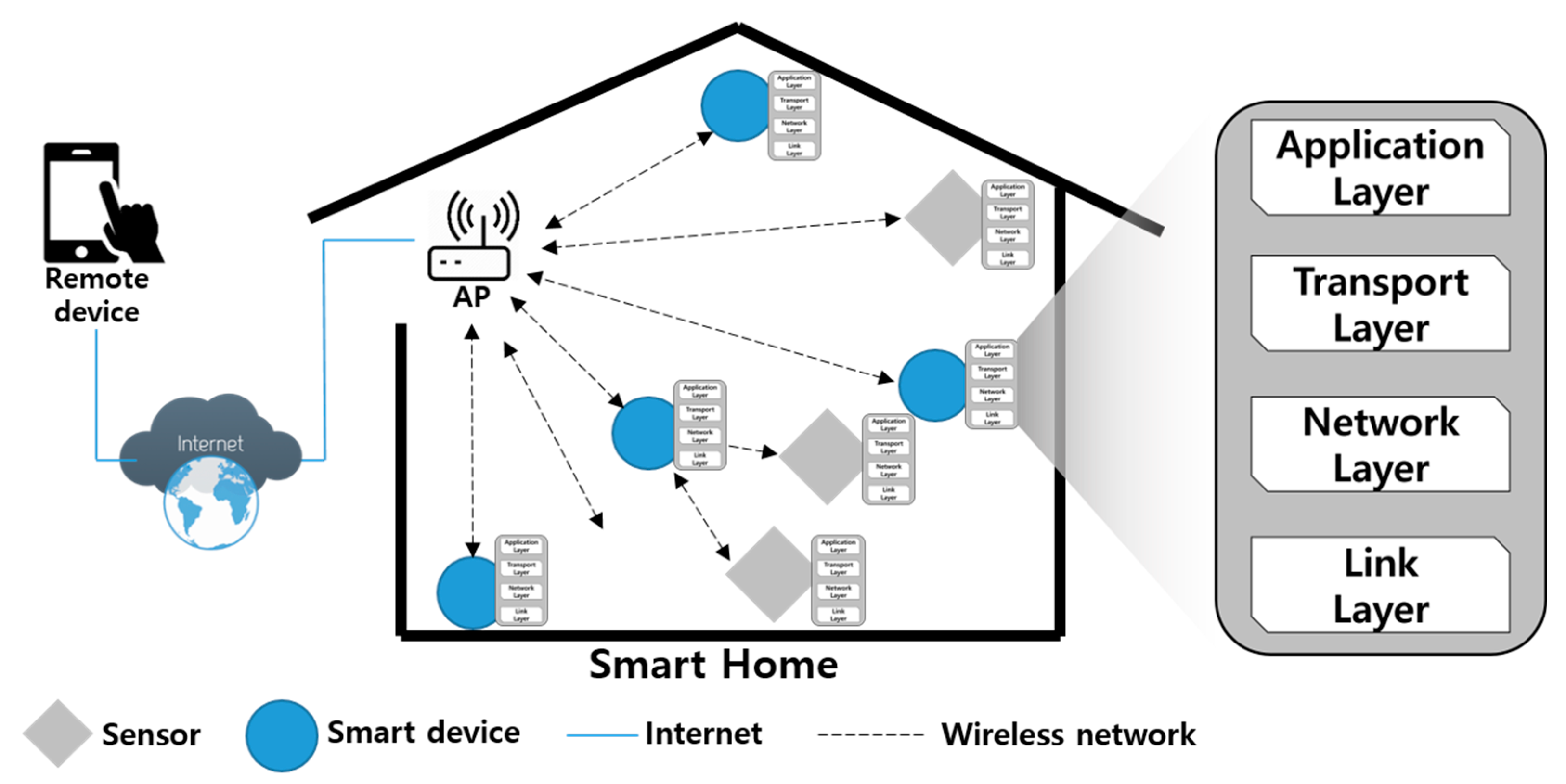
2.1. Smart Home
2.2. Security Requirements for a Smart Home
2.2.1. Privacy
2.2.2. Registration of Certified Smart Home Device
2.2.3. User Authentication in Smart Home
2.2.4. Security Threats
2.2.5. Heterogeneous Communication
2.2.6. Low Resources
2.3. Previous Research on Smart Home
3. Proposed Method
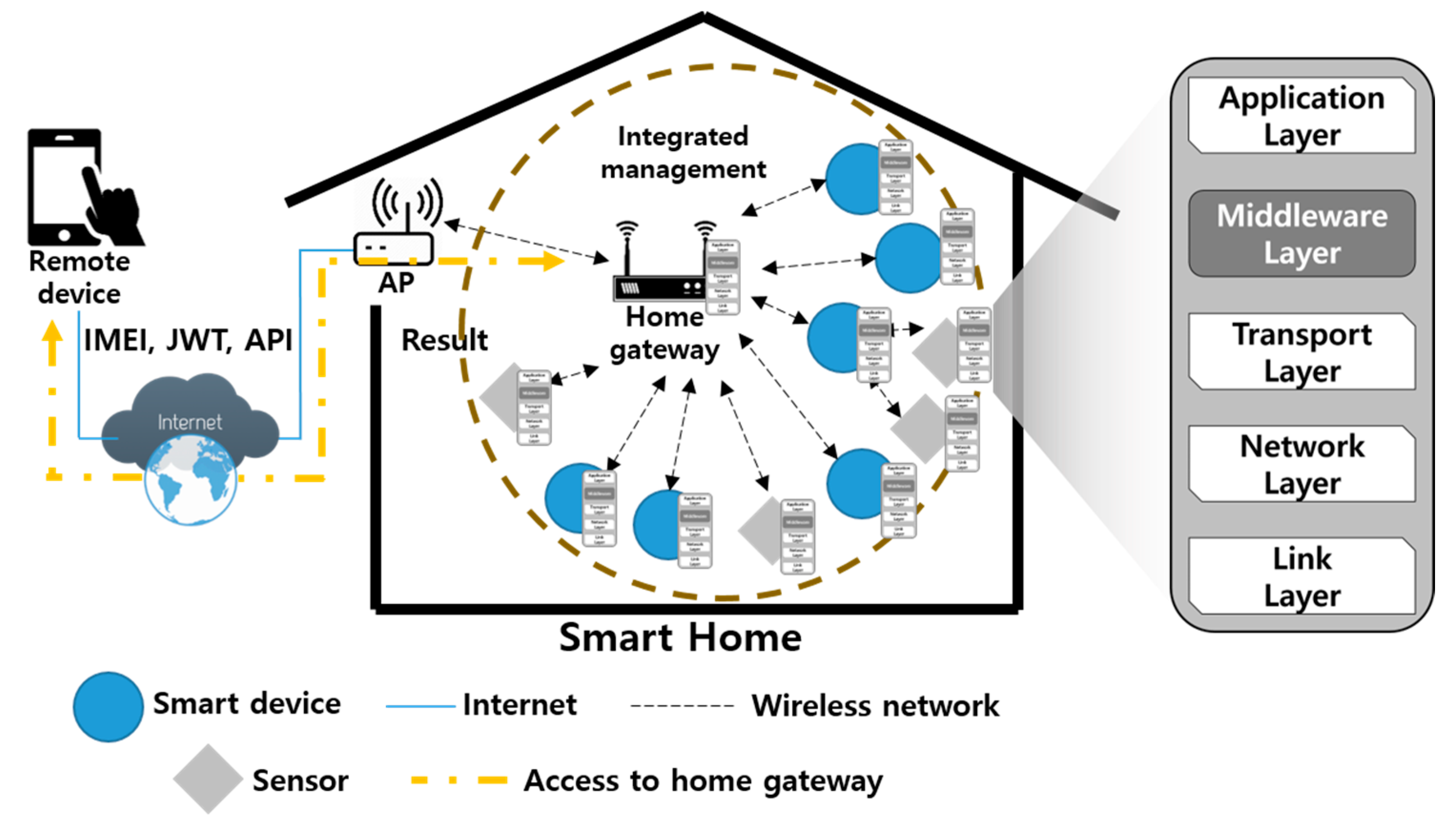
3.1. Proposed Smarthome Infrastructure
3.2. Proposed Scheme
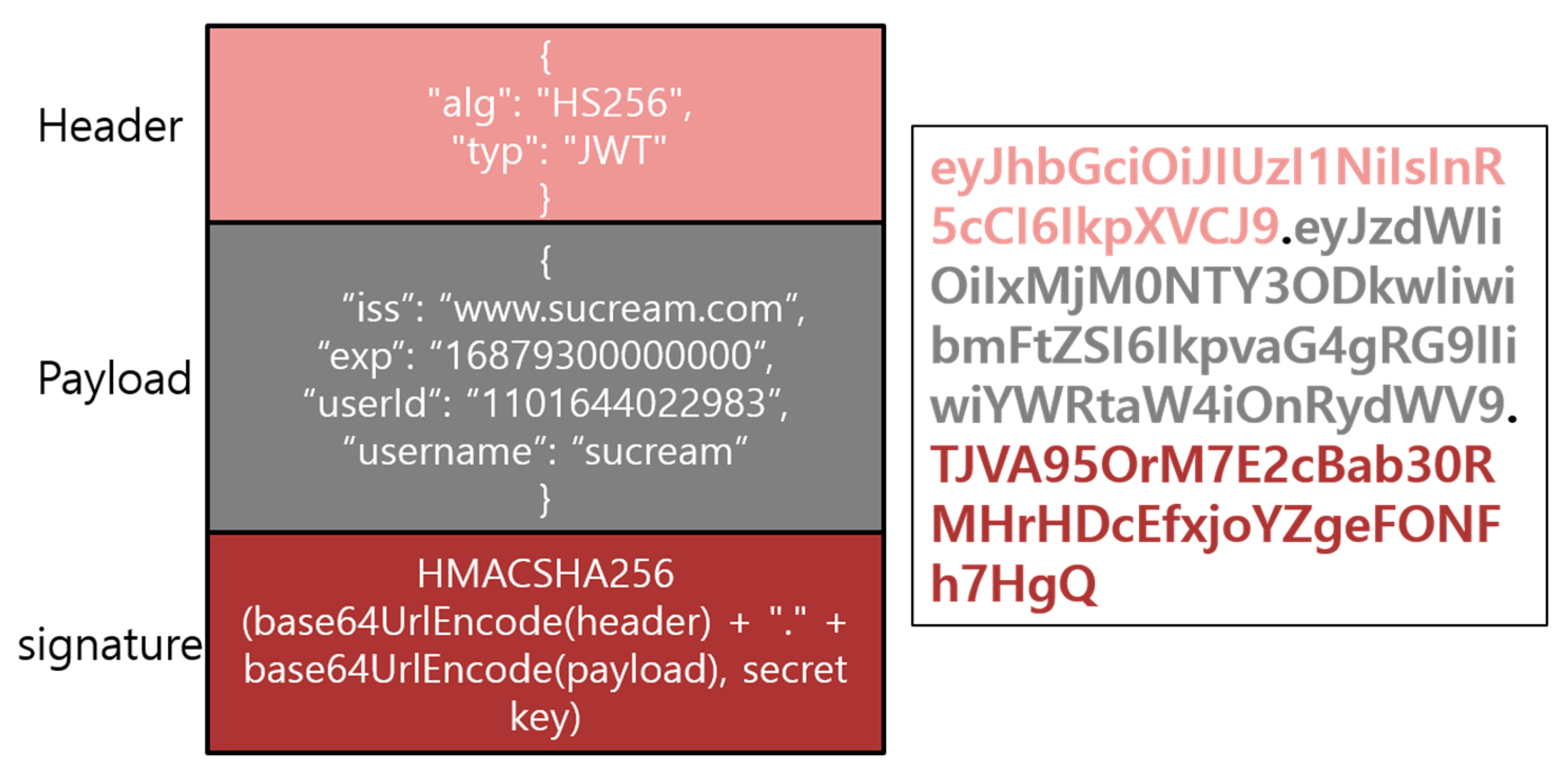
3.2.1. JSON Web Token
3.2.2. Proposed Scheme
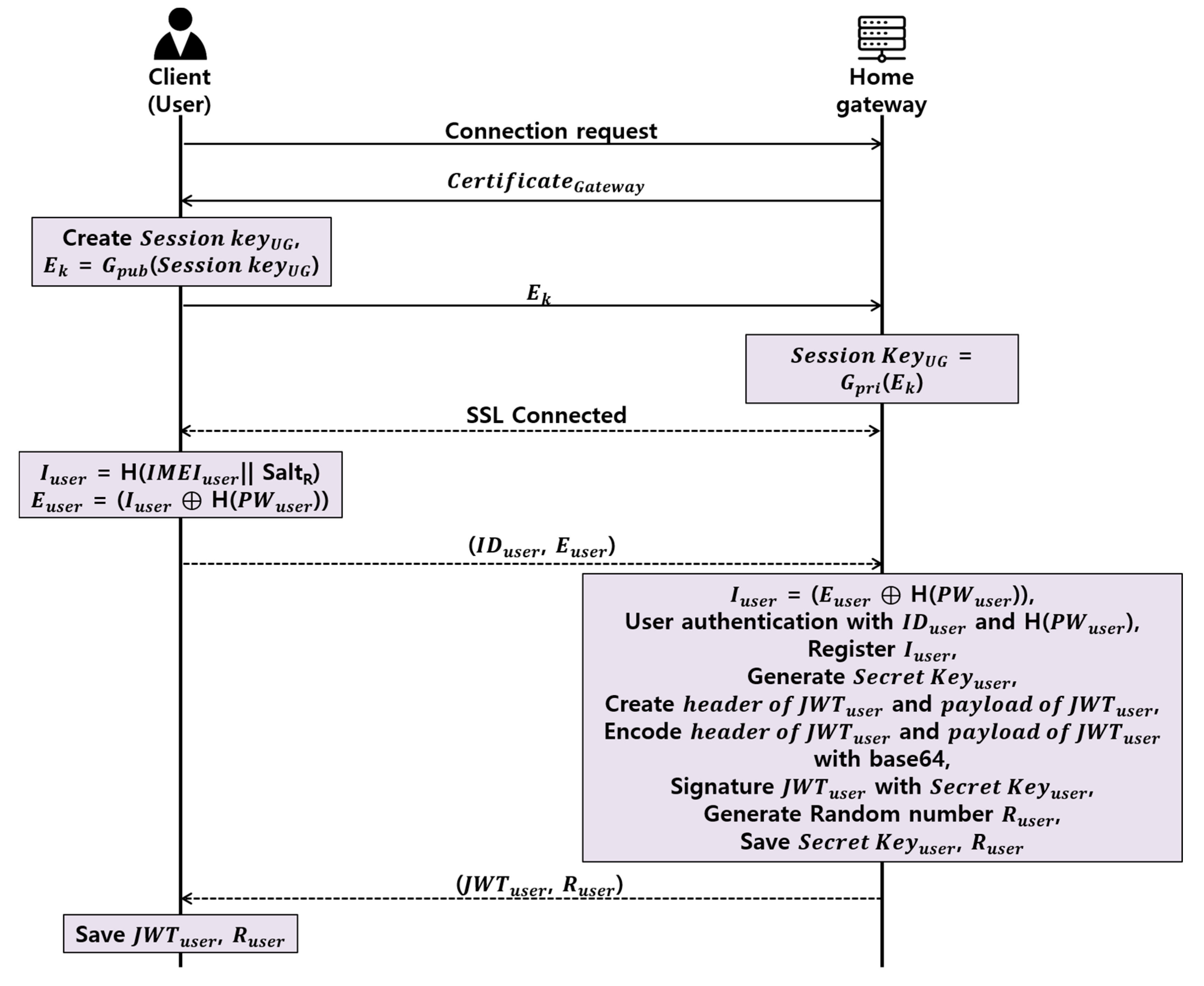
Proposed User Authentication Phase
- Step 1.
- Client and home gateway establishs TLS session through TLS handshake.
- Step 2.
- Client obtains Iuser by concatenating and hashing randomly generated SaltR with IMEIuser, which is the device’s original value, and subsequently, generates Euser through the XOR with the password’s hash value, H(PWuser), and transmits IDuser and Euser to the home gateway.
- Step 3.
- The home gateway obtains the Iuser by XORing the H(PWuser) of the previously-registered client and the Euser received from the client.
- Step 4.
- The home gateway authenticates the client via IDuser and H (PWuser), and registers the IMEIuser as the IMEI of the client.
- Step 5.
- The home gateway randomly generates a JWT secret key to be issued to the client, and then generates the header field and a payload field of the JWT. At this time, the header field is used to determine whether to use JWT and the signature technique to be used in the signature field. In the payload field, the issuer, the expiration period of the token, the user identification ID, the user name, and the access right of the user are inputted.
- Step 6.
- The home gateway signs the JWT with the secret key using the HMAC method, randomly generates a random number Ruser, and sends JWTuser and Ruser to the client.
- Step 7.
- The client stores JWTuser and Ruser, which are delivered from the home gateway.
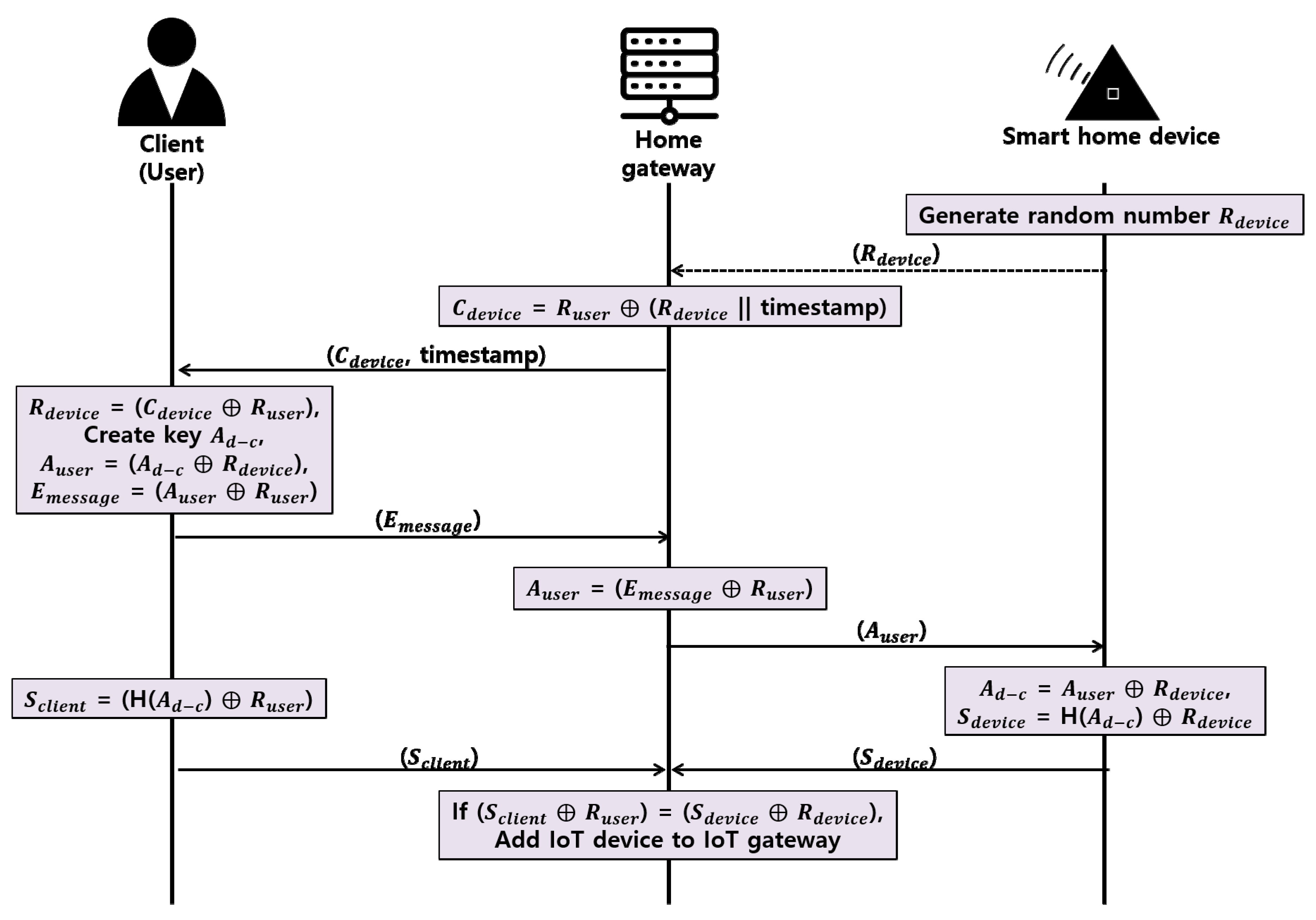
Proposed Register New Smart Home Device Phase
- Step 1.
- The smart home device generates a random number Rdevice and sends it to the home gateway through a secure channel.
- Step 2.
- The home gateway concatenates the timestamp and the Rdevice to prevent a replay attack, then the home gateway creates a Cdevice that XORs the Ruser shared with the client in the user authentication phase and delivers it to the client.
- Step 3.
- The client XORs the received Cdevice and Ruser to obtain the Rdevice and generates the random number Ad-c. Client XORs Ad-c and Rdevice to create Auser, then XORs Auser and Ruser to deliver Emessage to the home gateway.
- Step 4.
- The home gateway XORs Emessage and Ruser to obtain the Auser and delivers the Auser to the smart home device.
- Step 5.
- The smart home device XORs Auser and Rdevice to obtain Ad-c, XORs H (Ad-c), which is a hash of Ad-c and Rdevice, generates Sdevice, and delivers Sdevice to the home gateway.
- Step 6.
- The client also XORs the Ad-c hash H(Ad-c), and Ruser to obtain Sclient and deliver Sclient to the home gateway.
- Step 7.
- The home gateway compares the acquired H(Ad-c) obtained by XORing the Sclient and Sdevice received from the client and smart home device with Ruser and Rdevice, respectively, and if the smart home device has the same value, the smart home device is registered in the home gateway, and refused if different.
Proposed Access API Phase
- Step 1.
- The client generates Iuser by concatenating and hashing IMEIuser and SaltR and, subsequently, delivers Kuser to the home gateway, which is generated through the XOR of Ruser with this value.
- Step 2.
- The home gateway identifies the authorized client by obtaining Iuser through the XOR of Kuser and Ruser and, subsequently, compares the existing registered client’s Iuser. At this time, the home gateway judges that it is abnormal if it receives different IMEI values from one client to another JWT within a short time.
- Step 3.
- For the JWT received from the client, the home gateway verifies the validity of the token through the HMAC using the secret key that only it knows.
- Step 4.
- The home gateway concatenates the client’s API with the timestamp, XORs this value with the Rdevice, creates S1, and delivers it to the smart home device.
- Step 5.
- The smart home device XORs S1 and Rdevice to obtain the client’s API, and then generates the result after processing the client’s request. Then, the S2 created by XORing result and Rdevice is sent to the home gateway.
- Step 6.
- The home gateway obtains the result by XORing S2 and Rdevice. The home gateway concatenates the IMEI value and the timestamp of the registered client, XORs the result, and sends the Mresult value to the client by XORing the value with the Ruser value again.
- Step 7.
- The client XORs the Mresult and Ruser values and XORs the IMEI with the timestamp to obtain the result.
4. Implementation of the Proposed Protocol
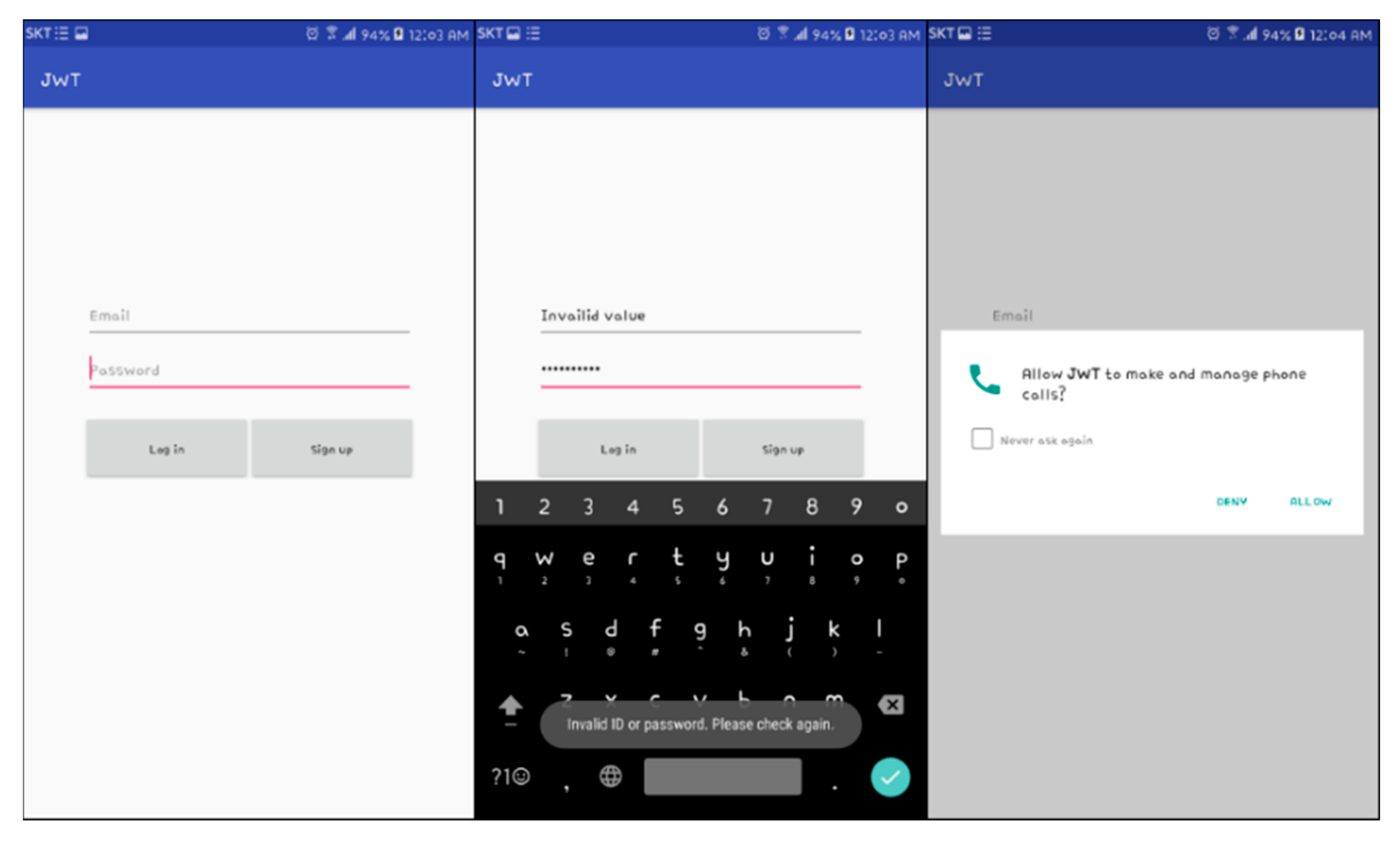
4.1. Login Function
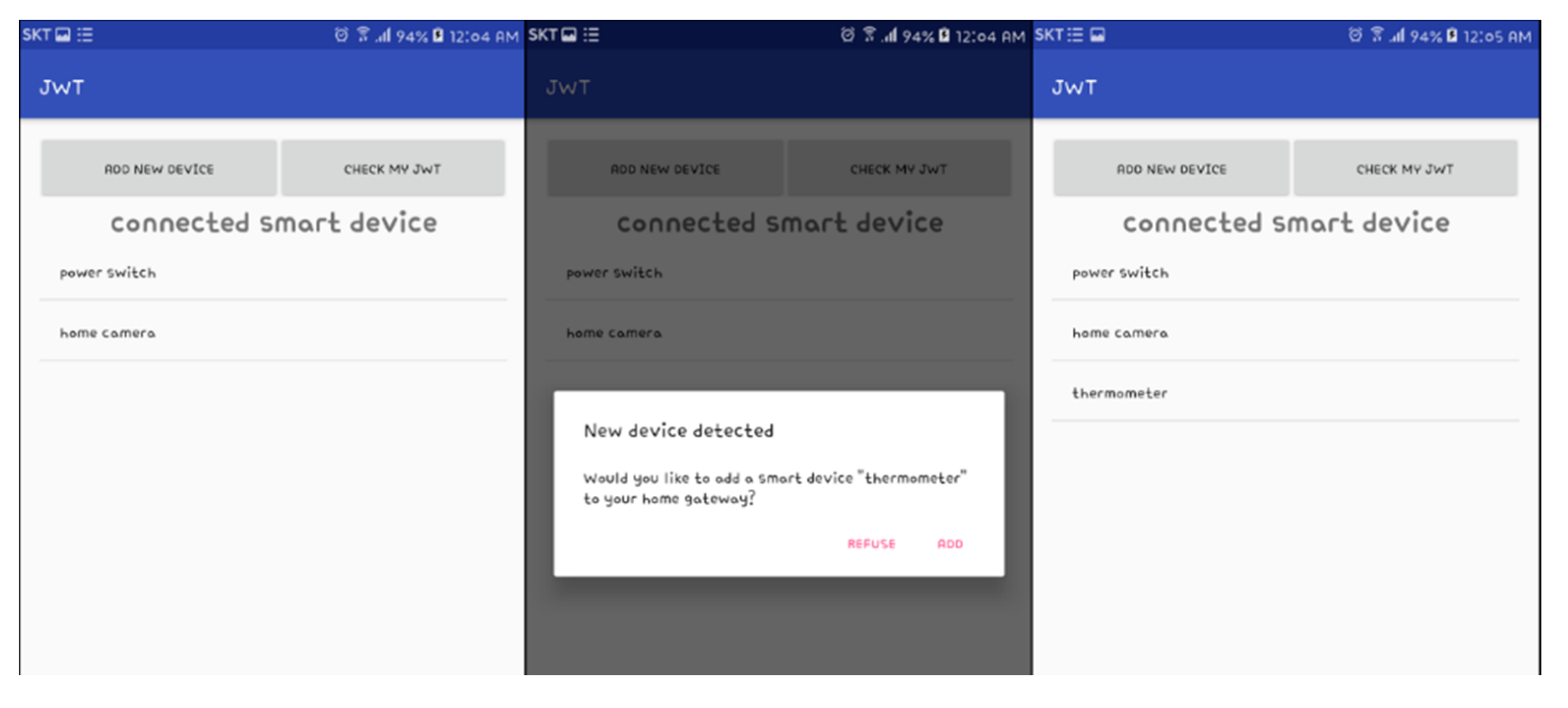
4.2. Identification and Registration of Smart Home Devices
4.3. JWT Validation and Smart Home Device Access
5. Security and Performance Analysis
5.1. Secuity Requirement Analysis
5.1.1. Privacy
5.1.2. Registration of a Certified Smart Home Device
5.1.3. User Authentication in the Smart Home
5.1.4. Security Threats
5.1.5. Heterogeneous Communication
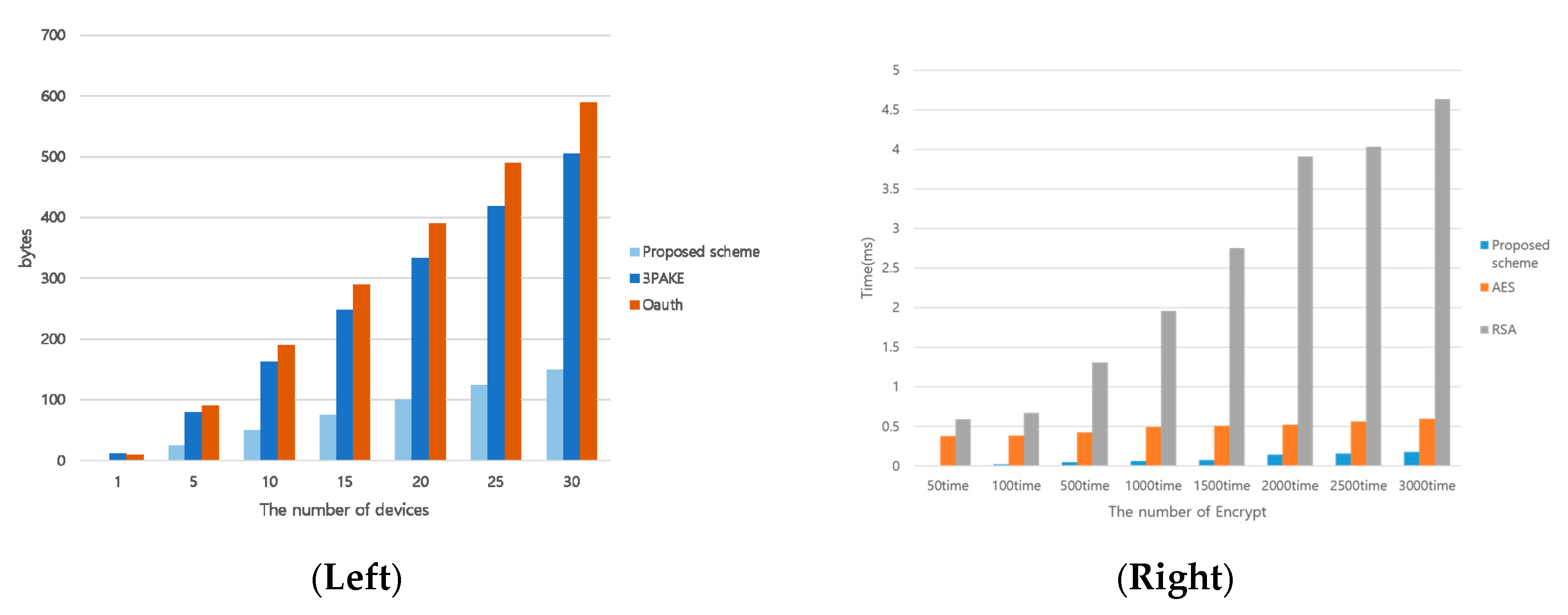
5.1.6. Computing Resource Analysis
6. Discussion
7. Conclusions
Author Contributions
Conflicts of Interest
References
- Lin, H.; Bergmann, N.W. IoT Privacy and Security Challenges for Smart Home Environments. Information 2016, 7, 44. [Google Scholar] [CrossRef]
- Marianthi, T.; Tsalis, N.; Gritzalis, D. Smart Home Solutions: Privacy Issues. In Handbook of Smart Homes, Health Care and Well-Being; Springer International Publishing: Cham, Switzerland, 2017; pp. 67–81. [Google Scholar]
- Kumar, P.; Gurtov, A.; Iinatti, J.; Ylianttila, M.; Sain, M. Lightweight and secure session-key establishment scheme in smart home environments. IEEE Sens. J. 2016, 16, 254–264. [Google Scholar] [CrossRef]
- Andreas, J.; Boldt, M.; Carlsson, B. A risk analysis of a smart home automation system. Future Gener. Comput. Syst. 2016, 56, 719–733. [Google Scholar]
- Choi, B.-M. A Study on Setting up the Concept of Smart City through Analysis on the Term ‘Smart’. J. Korea Contents Assoc. 2011, 11, 943–949. [Google Scholar] [CrossRef]
- Lee, M.; Park, J. Analysis and Study on Invasion Threat and Security Measures for Smart Home Services in IoT Environment. J. Inst. Int. Broadcast. Commun. 2016, 16, 27–32. [Google Scholar] [CrossRef]
- Verhoef, P.C.; Kannan, P.K.; Luo, X.; Zhang, Y. Consumer Connectivity in a Complex, Technology-Enabled, and Mobile-Oriented World with Smart Products. Northeastern U. D’Amore-McKim School of Business Research Paper, No. 2912321. Available online: https://ssrn.com/abstract=2912321 (accessed on 23 June 2017).
- Suryadevara, N.K. Wireless Sensor Sequence Data Model for Smart Home and IoT Data Analytics. In Proceedings of the First International Conference on Computational Intelligence and Informatics; Springer: Singapore, 2017. [Google Scholar]
- Bandara, A.M.K.C. Secure Smart Home System. Master of Science in Information Security. 2016. Available online: documents.ucsc.lk/jspui/handle/123456789/3711 (accessed on 23 June 2017).
- Tan, J.Y.; Ker, P.J.; Abdullah, A. Smart Home Design with XBee Wi-Fi and Android-Based Graphical User Interface. In Proceedings of the 2016 IEEE Student Conference on Research and Development (SCOReD), Kuala Lumpur, Malaysia, 13–14 December 2016. [Google Scholar]
- Wang, G.; Song, D. Smart Home Services Using the Internet of Things. In Internet of Things and Data Analytics Handbook; Wiley: Hoboken, NJ, USA, 2017; pp. 613–630. [Google Scholar]
- Sharma, P.K.; Moon, S.Y.; Park, J.H. Block-VN: A Distributed Blockchain Based Vehicular Network Architecture in Smart City. J. Inf. Proc. Syst. 2017, 13, 184–195. [Google Scholar] [CrossRef]
- Lee, D.-H.; Lee, I.-Y. A Study on Enhanced 3PAKE Scheme against Password Guessing Attack in Smart Home Environment. J. Korea Inst. Inf. Secur. Cryptol. 2016, 26, 1471–1481. [Google Scholar] [CrossRef]
- Fremantle, P. Privacy-enhancing Federated Middleware for the Internet of Things. In Proceedings of the Doctoral Symposium of the 17th International Middleware Conference, New York, NY, USA, 12–16 December 2016. [Google Scholar]
- Prakash, N.S.; Venkatram, N. Establishing efficient security scheme in home IOT devices through biometric finger print technique. Indian J. Sci. Technol. 2016, 9. [Google Scholar] [CrossRef]
- Fernandes, E.; Jung, J.; Prakash, A. Security Analysis of Emerging Smart Home Applications. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016. [Google Scholar]
- Min, K.W.; Moon, S.Y.; Park, J.H. An enhanced security framework for home appliances in smart home. Hum.-Centric Comput. Inf. Sci. 2017, 7, 6. [Google Scholar]
- Kim, M.-S.; Lee, J.-K.; Park, J.H.; Kang, J.-H. Security Challenges in Recent Internet Threats and Enhanced Security Service Model for Future IT Environments. J. Int. Technol. 2016, 17, 947–955. [Google Scholar]
- Zhu, W.; Lee, C. A Security Protection Framework for Cloud Computing. J. Inf. Proc. Syst. 2016, 12, 538–547. [Google Scholar] [CrossRef]
- Moazzami, M.-M.; Xing, G.; Mashima, D.; Chen, W.-P.; Herberg, U. SPOT: A Smartphone-Based Platform to Tackle Heterogeneity in Smart-Home IoT Systems. In Proceedings of the 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 12–14 December 2016. [Google Scholar]
- Jungho, K.; Park, G.; Park, J.H. Design of secure authentication scheme between devices based on zero-knowledge proofs in home automation service environments. J. Supercomput. 2016, 72, 4319–4336. [Google Scholar]
- Kwon, T.; Lee, J.; Choi, H.; Yi, O.; Ju, S. Efficiency of LEA compared with AES. J. Converg. 2015, 6, 16–25. [Google Scholar]
- Deschambault, O.; Gherbi, A.; Légaré, C. Efficient Implementation of the MQTT Protocol for Embedded Systems. J. Inf. Proc. Syst. 2017, 13, 26–39. [Google Scholar] [CrossRef]
- Lee, S.-W.; Yu, J.-H.; Sim, K.-B. Real-time Streaming and Remote Control for the Smart Door-Lock System based on Internet of Things. J. Korean Inst. Intell. Syst. 2015, 25, 565–570. [Google Scholar] [CrossRef]
- Wu, X.; Hu, X.; Moura, S.; Yin, X.; Pickert, V. Stochastic control of smart home energy management with plug-in electric vehicle battery energy storage and photovoltaic array. J. Power Sources 2016, 333, 203–212. [Google Scholar] [CrossRef]
- Kang, J.; Kim, M.; Park, J.H. A reliable TTP-based infrastructure with low sensor resource consumption for the smart home multi-platform. Sensors 2016, 16, 1036. [Google Scholar] [CrossRef] [PubMed]
- Jones, M.; Bradley, J.; Sakimura, N. JSON Web Token (JWT), RFC 7519, 2015. Available online: http://www.rfc-editor.org/info/rfc7519 (accessed on 23 June 2017).



| Notation | Meaning |
|---|---|
| Client | Client |
| Home gateway | Home gateway |
| Smart home device | Smart home device |
| Session keyUG | Session key between client and home gateway |
| Gpub | Home gateway’s public key |
| Gpri | Home gateway’s private key |
| H(x) | Hash function |
| IDx | x’s ID |
| PWx | x’s password |
| Exclusive or operator | |
| IMEIx | x’s IMEI value |
| Secret keyx | x’s secret key |
| JWTx | x’s JWT |
| Base64 | Base64 encoding/decoding |
 | Secure communication |
| Rx | Generated random number for x |
| Ad-c | Generated random key between client and smart home device |
| API | API requested from client |
| Result | Result processed by smart home device |
| SaltR | Random number to cover user’s IMEI |
| Client | Home Gateway | Smart Home Device | ||||||
|---|---|---|---|---|---|---|---|---|
| Name | Samsung Galaxy Note5 | Raspberry pi3 | Apache2 | MySQL | PHP | ESP8266 | LED | DHT11 |
| Feature | Android 6.0.1 | Raspbian OS JESSIE | Apache/2.4.10 (Raspbian) | 15.1 Distrib 10.0.25-MariaDB | PHP 5.6.22-0+deb8u1 | WiFi module | Yellow LED | Temperature-humidity sensor |
| Dae-Hwi Lee et al. [13] | Fremantle et al. [14] | Prakash et al. [15] | Kang, Jungho et al. [26] | Proposed Scheme | |
|---|---|---|---|---|---|
| Privacy | O | O | O | O | O |
| Secure Smart home device Registration | O | X | X | X | O |
| User authentication in smart home | O | O | O | O | O |
| Security threats | O | Δ | Δ | O | O |
| Heterogeneous communication | X | X | X | O | O |
| Low resource | X | X | O | O | O |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hong, N.; Kim, M.; Jun, M.-S.; Kang, J. A Study on a JWT-Based User Authentication and API Assessment Scheme Using IMEI in a Smart Home Environment. Sustainability 2017, 9, 1099. https://doi.org/10.3390/su9071099
Hong N, Kim M, Jun M-S, Kang J. A Study on a JWT-Based User Authentication and API Assessment Scheme Using IMEI in a Smart Home Environment. Sustainability. 2017; 9(7):1099. https://doi.org/10.3390/su9071099
Chicago/Turabian StyleHong, Namsu, Mansik Kim, Moon-Seog Jun, and Jungho Kang. 2017. "A Study on a JWT-Based User Authentication and API Assessment Scheme Using IMEI in a Smart Home Environment" Sustainability 9, no. 7: 1099. https://doi.org/10.3390/su9071099





