DTN Trustworthiness for Permafrost Telemetry IoT Network
Abstract
:1. Introduction
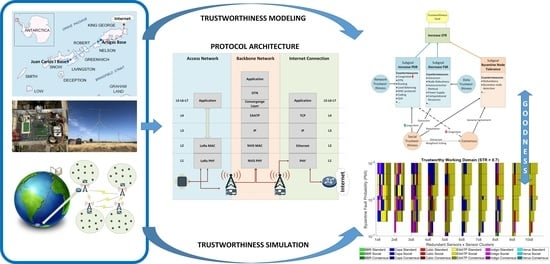
- The definition and concretion of the remote sensor network architecture that will be deployed in Antarctica, detailing the type of nodes, protocol stack, and communication techniques that will be used.
- The modeling of the Antarctic scenario in the simulator. To perform the simulation tests, we modeled the communication media (LoRa and NVIS), the telemetry application, the faulty behavior of Byzantine nodes, the social trust management and the consensus algorithms, the DTN technique, and the tested transport protocols.
- The assessment and analysis of the results using our proposed trustworthiness model. From this analysis, we conclude which transport protocol best suits our use case and propose a modification of the scenario to be deployed in Antarctica.
2. Related Work
2.1. Delay Tolerant Networks
2.2. Transport Protocols
2.3. Trustworthiness in Cyber Physical Systems
- Data trustworthiness: It is defined as the possibility to ascertain the correctness of the data provided by the source [50]. Many methods use different approaches that try to detect faulty nodes, false alarms, and sensor misreading using. For instance, authors in [51] use a fog computing architecture to detect, filter, and correct abnormal sensed data. In addition, authors in [52] present a data intrusion detection system to trigger false data from malicious attacks.
- Network trustworthiness: Defined as the likelihood of a packet to reach its destination unaltered despite the adversities (e.g., link failure, link saturation, or malicious attacks, among others), it is a relevant aspect to consider in challenging networks [53], such as the use case we propose. The network’s performance and trustworthiness have been addressed from several perspectives, such as channel coding [54], transport protocols [11], dynamic routing and topology control protocols [55,56], and DTN architectures and protocols [8].
- Social trustworthiness: This field has become more popular since the appearance of the Social Internet of Things (SIoT) [57,58]. In SIoT trustworthiness, objects or network nodes interact and establish social relationships, which are used to define trust and reputation models that take into account several input parameters. Authors in [59] present a model that considers factors as the computational capabilities of the nodes, the type of relationship between them, the total number of transactions, the credibility of a node, and the feedback provided by other nodes, among others. Authors in [60] present an evolution of the aforementioned trust management model, which applies a machine learning algorithm to calculate novel parameters such as the goodness, usefulness, and perseverance of a node. Thanks to these parameters, this upgraded trust model is resilient to more types of malicious node attacks. Authors in [61] propose another model that defines the input parameters as the expected gain on success, the expected damage on a failure, the expected cost, the expected result, and the goal. Authors in [62] define a decentralized self-enforcing trust management system which is based on a feedback system and reputational secure multiparty calculations to ensure the privacy of each party’s provided data.
- Consensus: It represents a state where all the participants of the same distributed system agree on the same data values [63]. Consensus protocols can be classified into two major groups: proof-based consensus and Byzantine consensus. The first group is related to blockchain technology, where all participants compete against each other to mine a block, and the most commonly used protocols are proof-of-work, proof-of-stake, and their variants [63]. The main drawback of these protocols for the IoT is that devices usually have lesser hardware resources and low processing power, which make the mining tasks of blockchain extremely difficult [63]. On the other hand, Byzantine-based protocols implement voting-based mechanisms to reach an agreement rather than competing among them, generating less resource consumption in general. Their main drawback is the number of messages that need to be delivered through the network to reach an agreement. Some well-known protocols from this category are Practical Byzantine Fault Tolerance (PBFT), RAFT, PaXoS, and Ripple, among others [63].
3. Remote Sensor Network Architecture
4. Trustworthiness Model Specification
4.1. Data Trustworthiness Layer
4.2. Network Trustworthiness Layer
4.3. Social Trustworthiness Layer
4.4. Consensus Layer
4.5. Trustworthiness Layers Relationships
5. Simulation Tests
6. Results
7. Discussion
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AATP | Adaptive and Aggressive Transport Protocol |
| BDP | Bandwidth Delay Product |
| BIC-TCP | Binary Increase Control TCP |
| BNT | Byzantine Node Tolerance |
| BP | Bundle Protocol |
| bps | Bits per second |
| BW | Bandwidth |
| CPS | Cyber Physical System |
| DTN | Delay Tolerant Network |
| DUACK | Duplicated Acknowledgment |
| EAATP | Enhanced AATP |
| FSR | Faulty Sensing Ratio |
| FSV | False Sensed Values |
| GA | General Agreement |
| GTN-P | Ground Terrestrial Network-Permafrost |
| HF | High Frequency |
| H-TCP | High-Speed TCP |
| ICN | Information-Centric Networking |
| IoT | Internet of Things |
| ISAC | Integrated Sensing and Communication System |
| JSCTP | Jitter Stream Control Transmission Protocol |
| LFN | Long Fat Network |
| M2M | Machine to Machine |
| NVIS | Near Vertical Incidence Skywave |
| OSI | Open Systems Interconnection |
| PBFT | Practical Byzantine Fault Tolerance |
| PCC | Performance-oriented Congestion Control |
| PDR | Packet Delivery Ratio |
| QoS | Quality of Service |
| RFC | Request For Comments |
| RTT | Round-Trip Time |
| SACK | Selective Acknowledgment |
| SIoT | Social Internet of Things |
| S-TCP | Scalable TCP |
| ST | Successful Transactions |
| STR | Successful Transaction Rate |
| TCP | Transmission Control Protocol |
| TSV | Total Sensed Values |
| TT | Total Transactions |
| WSN | Wireless Sensor Network |
References
- Kennicutt, M.C.; Kim, Y.D.; Rogan-Finnemore, M.; Anandakrishnan, S.; Chown, S.L.; Colwell, S.; Cowan, D.; Escutia, C.; Frenot, Y.; Hall, J.; et al. Delivering 21st century Antarctic and Southern Ocean science. Antarct. Sci. 2016, 28, 407–423. [Google Scholar] [CrossRef] [Green Version]
- Alsina-Pagès, R.M.; Hervás, M.; Orga, F.; Pijoan, J.L.; Badia, D.; Altadill, D. Physical layer definition for a long-haul HF antarctica to Spain radio link. Remote Sens. 2016, 8, 380. [Google Scholar] [CrossRef] [Green Version]
- Porte, J.; Maso, J.M.; Pijoan, J.L.; Badia, D. Sensing System for Remote Areas in Antarctica. Radio Sci. 2020, 55, 1–12. [Google Scholar] [CrossRef]
- Male, J.; Porte, J.; Gonzalez, T.; Maso, J.M.; Pijoan, J.L.; Badia, D. Analysis of the Ordinary and Extraordinary Ionospheric Modes for NVIS Digital Communications Channels. Sensors 2021, 21, 2210. [Google Scholar] [CrossRef] [PubMed]
- Briones, A.; Mallorquí, A.; Zaballos, A.; de Pozuelo, R.M. Adaptive and aggressive transport protocol to provide QoS in cloud data exchange over Long Fat Networks. Futur. Gener. Comput. Syst. 2021, 115, 34–44. [Google Scholar] [CrossRef]
- Gonzalez, T.; Porte, J.; Pijoan, J.L.; Badia, D.; Male, J.; Navarro, J.; Maso, J.M. SC-FDE Layer for Sensor Networks in Remote Areas Using NVIS Communications. Electronics 2021, 10, 1636. [Google Scholar] [CrossRef]
- Mallorquí, A.; Zaballos, A. A heterogeneous layer-based trustworthiness model for long backhaul nvis challenging networks and an iot telemetry service for antarctica. Sensors 2021, 21, 3446. [Google Scholar] [CrossRef]
- Bounsiar, S.; Benhamida, F.Z.; Henni, A.; de Ipiña, D.L.; Mansilla, D.C. How to Enable Delay Tolerant Network Solutions for Internet of Things: From Taxonomy to Open Challenges. Proceedings 2019, 31, 24. [Google Scholar] [CrossRef] [Green Version]
- de Pablo Hernández, M.Á.; Jiménez, J.J.; Ramos, M.; Prieto, M.; Molina, A.; Vieira, G.; Hidalgo, M.A.; Fernández, S.; Recondo, C.; Calleja, J.F.; et al. Frozen ground and snow cover monitoring in livingston and deception islands, antarctica: Preliminary results of the 2015–2019 PERMASNOW project. Geogr. Res. Lett. 2020, 46, 187–222. [Google Scholar] [CrossRef] [Green Version]
- Location Map of Low Island in the South Shetland Islands. Available online: https://en.wikipedia.org/wiki/Low_Island_(South_Shetland_Islands)#/media/File:Low-Island-location-map.png (accessed on 2 September 2021).
- Briones, A.; Mallorquí, A.; Zaballos, A.; de Pozuelo, R.M. Wireless loss detection over fairly shared heterogeneous long fat networks. Electronics 2021, 10, 987. [Google Scholar] [CrossRef]
- Rodrigues, J.J.P.C. (Ed.) Advances in Delay-Tolerant Networks (DTNs): Architecture and Enhanced Performance, 2nd ed.; Woodhead Publishing: Sawston, UK, 2020. [Google Scholar]
- Burleigh, S.; Hooke, A.; Torgerson, L.; Fall, K.; Cerf, V.; Durst, B.; Scott, K.; Weiss, H. Delay-tolerant networking: An approach to interplanetary internet. IEEE Commun. Mag. 2003, 41, 128–136. [Google Scholar] [CrossRef] [Green Version]
- Partan, J.; Kurose, J.; Levine, B.N. A Survey of Practical Issues in Underwater Networks. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2007, 11, 23–33. [Google Scholar] [CrossRef] [Green Version]
- Tovar, A.; Friesen, T.; Ferens, K.; McLeod, B. A DTN wireless sensor network for wildlife habitat monitoring. In Proceedings of the Canadian Conference on Electrical and Computer Engineering, Calgary, AB, Canada, 2–5 May 2010; pp. 1–5. [Google Scholar] [CrossRef]
- Matsuzaki, R.; Ebara, H.; Muranaka, N. Rescue support system with DTN for earthquake disasters. IEICE Trans. Commun. 2015, E98B, 1832–1847. [Google Scholar] [CrossRef] [Green Version]
- Soares, V.N.G.J.; Farahmand, F.; Rodrigues, J.J.P.C. A layered architecture for Vehicular Delay-Tolerant Networks. In Proceedings of the 2009 IEEE Symposium on Computers and Communications, Sousse, Tunísia, 5–8 July 2009; pp. 122–127. [Google Scholar] [CrossRef] [Green Version]
- Scott, K.L.; Burleigh, S. Bundle Protocol Specification. Available online: https://tools.ietf.org/html/rfc5050 (accessed on 20 September 2021).
- Penning, A.; Baumgärtner, L.; Höchst, J.; Sterz, A.; Mezini, M.; Freisleben, B. DTN7: An Open-Source Disruption-Tolerant Networking Implementation of Bundle Protocol 7. In Proceedings of the International Conference on Ad-Hoc Networks and Wireless, LNCS, Luxembourg, 1–3 October 2019; Springer: Basel, Switzerland; Volume 11803, pp. 196–209. [Google Scholar]
- Schildt, S.; Morgenroth, J.; Pöttner, W.B.; Wolf, L. IBR-DTN: A lightweight, modular and highly portable Bundle Protocol implementation. Electron. Commun. EASST 2011, 37. [Google Scholar] [CrossRef]
- Von Zengen, G.; Büsching, F.; Pöttner, W.-B.; Wolf, L. An Overview of µDTN: Unifying DTNs and WSNs. In Proceedings of the 11th GI/ITG KuVS Fachgespräch Drahtlose Sensornetze (FGSN), Darmstadt, Germany, 13 September 2012; pp. 1–4. [Google Scholar]
- Al-Turjman, F.M.; Al-Fagih, A.E.; Alsalih, W.M.; Hassanein, H.S. A delay-tolerant framework for integrated RSNs in IoT. Comput. Commun. 2013, 36, 998–1010. [Google Scholar] [CrossRef]
- Guo, Z.; Wang, B.; Cui, J.H. Generic prediction assisted single-copy routing in underwater delay tolerant sensor networks. Ad Hoc Netw. 2013, 11, 1136–1149. [Google Scholar] [CrossRef]
- Wong, K.S.; Wan, T.C. Reliable Multicast Disruption Tolerant Networking: Conceptual Implementation Using Message Ferry. In Proceedings of the IEEE Region 10 Annual International Conference, Proceedings/TENCON, Penang, Malaysia, 5–8 November 2017; pp. 1817–1822. [Google Scholar]
- Mao, Y.; Zhou, C.; Ling, Y.; Lloret, J. An optimized probabilistic delay tolerant network (DTN) routing protocol based on scheduling mechanism for internet of things (IoT). Sensors 2019, 19, 243. [Google Scholar] [CrossRef] [Green Version]
- Guo, B.; Zhang, D.; Wang, Z.; Yu, Z.; Zhou, X. Opportunistic IoT: Exploring the harmonious interaction between human and the internet of things. J. Netw. Comput. Appl. 2013, 36, 1531–1539. [Google Scholar] [CrossRef]
- Xu, Y.; Mahendran, V.; Radhakrishnan, S. Internet of Hybrid Opportunistic Things: A Novel Framework for Interconnecting IoTs and DTNs. In Proceedings of the 2016 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), San Francisco, CA, USA, 10–14 April 2016; pp. 1067–1068. [Google Scholar] [CrossRef]
- Elmangoush, A.; Corici, A.; Catalan, M.; Steinke, R.; Magedanz, T.; Oller, J. Interconnecting Standard M2M Platforms to Delay Tolerant Networks. In Proceedings of the Proceedings-2014 International Conference on Future Internet of Things and Cloud, FiCloud 2014, Barcelona, Spain, 27–29 August 2014; pp. 258–263. [Google Scholar]
- Sathiaseelan, A.; Trossen, D.; Komnios, I.; Ott, J.; Crowcroft, J. Information Centric Delay Tolerant Networking: An Internet Architecture for the Challenged; University of Cambridge: Cambridge, UK, 2013. [Google Scholar]
- Manzoni, P.; Hernández-Orallo, E.; Calafate, C.T.; Cano, J.C. A Proposal for a Publish/Subscribe, Disruption Tolerant Content Island for Fog Computing. In Proceedings of the SMARTOBJECTS 2017-Proceedings of the 3rd Workshop on Experiences with the Design and Implementation of Smart Objects, Co-Located with MobiCom 2017, Snowbird, UT, USA, 16 October 2017; pp. 47–52. [Google Scholar]
- Kazmi, M.; Shamim, A.; Wahab, N.; Anwar, F. Comparison of TCP Tahoe, Reno, New Reno, Sack and Vegas in IP and MPLS Networks under Constant Bit Rate Traffic. In Proceedings of the International Conference on Advanced Computational Technology and Creative Media (ICACTCM), Pattaya, Thailand, 14–15 August 2014; pp. 33–38. [Google Scholar]
- Kelly, T. Scalable TCP: Improving performance in highspeed wide area networks. ACM SIGCOMM Comput. Commun. Rev. 2003, 33, 83–91. [Google Scholar] [CrossRef]
- Jin, C.; Wei, D.X.; Low, S.H. FAST TCP: Motivation, Architecture, Algorithms, Performance. IEEE/ACM Trans. Netw. 2006, 14, 1246–1259. [Google Scholar] [CrossRef] [Green Version]
- Leith, D.; Shorten, R. H-TCP Protocol for High-Speed Long-Distance Networks. In Proceedings of the PFLDnet, Argonne, IL, USA, 16–17 February 2004. [Google Scholar]
- Xu, L.; Harfoush, K.; Rhee, I. Binary Increase Congestion Control (BIC) for Fast Long-Distance Networks. In Proceedings of the IEEE INFOCOM 2004, Hong Kong, China, 7–11 March 2004; Volume 4, pp. 2514–2524. [Google Scholar]
- Ha, S.; Rhee, I.; Xu, L. Cubic: A new TCP-friendly high-speed TCP variant. ACM SIGOPS Oper. Syst. Rev. 2008, 42, 64–74. [Google Scholar] [CrossRef]
- Dong, M.; Li, Q.; Zarchy, D.; Godfrey, P.B.; Schapira, M. PCC: Re-Architecting Congestion Control for Consistent High Performance. In Proceedings of the 12th USENIX Symposium on Networked Systems Design and Implementation (NSDI’15), Oakland, CA, USA, 4–6 May 2015; pp. 395–408. [Google Scholar]
- Fu, C.P.; Liew, S.C. TCP Veno: TCP Enhancement for Transmission Over Wireless Access Networks. IEEE J. Sel. Areas Commun. 2003, 21, 216–228. [Google Scholar]
- Grieco, L.A.; Mascolo, S. Performance evaluation and comparison of Westwood+, New Reno, and Vegas TCP congestion control. ACM SIGCOMM Comput. Commun. Rev. 2004, 34, 25–38. [Google Scholar] [CrossRef]
- Kanagarathinam, M.R.; Singh, S.; Sandeep, I.; Roy, A.; Saxena, N. D-TCP: Dynamic TCP Congestion Control Algorithm for next Generation Mobile Networks. In Proceedings of the 15th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Wu, E.H.K.; Huang, Y.U.C.; Chang, G.K. EJTCP: Enhanced Jitter-based TCP for Wireless Broadband Networks. J. Inf. Sci. Eng. 2007, 23, 1663–1679. [Google Scholar]
- Chen, J.M.; Chu, C.H.; Wu, E.H.K.; Tsai, M.F.; Wang, J.R. Improving SCTP performance by jitter-based congestion control over wired-wireless networks. Eurasip J. Wirel. Commun. Netw. 2011, 2011, 103027. [Google Scholar] [CrossRef] [Green Version]
- Cardwell, N.; Cheng, Y.; Gunn, C.S.; Yeganeh, S.H.; Jacobson, V. BBR: Congestion-Based Congestion Control. Queue 2016, 14, 20–53. [Google Scholar] [CrossRef]
- Arun, V.; Balakrishnan, H.; Csail, M.I.T.; Design, S.; Nsdi, I. Copa: Practical Delay-Based Congestion Control for the Internet. In Proceedings of the 15th USENIX Symposium on Networked Systems Design and Implementation (NSDI’18), Renton, WA, USA, 9–11 April 2018; pp. 329–342. [Google Scholar]
- Yan, F.Y.; Ma, J.; Hill, G.D.; Raghavan, D.; Wahby, R.S.; Levis, P.; Winstein, K. Pantheon: The Training Ground for Internet Congestion-Control Research. In Proceedings of the 2018 USENIX Annual Technical Conference, USENIX ATC 2018, Boston, MA, USA, 11–13 July 2020; pp. 731–743. [Google Scholar]
- Zaki, Y.; Pötsch, T.; Chen, J.; Subramanian, L.; Görg, C. Adaptive Congestion Control for Unpredictable Cellular Networks. Comput. Commun. Rev. 2015, 45, 509–522. [Google Scholar] [CrossRef]
- Crawford, M.; Liongosary, E. The Industrial Internet of Things Consortium. IIC J. Innov. 2018, 9, 1–141. [Google Scholar]
- Junior, F.M.R.; Kamienski, C.A. A Survey on Trustworthiness for the Internet of Things. IEEE Access 2021, 9, 42493–42514. [Google Scholar] [CrossRef]
- Labib, N.S.; Brust, M.R.; Danoy, G.; Bouvry, P. Trustworthiness in IoT-A Standards Gap Analysis on Security, Data Protection and Privacy. In Proceedings of the 2019 IEEE Conference on Standards for Communications and Networking (CSCN), Granada, Spain, 28–30 October 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Haron, N.; Jaafar, J.; Aziz, I.A.; Hassan, M.H.; Shapiai, M.I. Data Trustworthiness in Internet of Things: A Taxonomy and Future Directions. In Proceedings of the 2017 IEEE Conference on Big Data and Analytics (ICBDA), Kuching, Malaysia, 16–17 November 2017; pp. 25–30. [Google Scholar]
- Zhang, G.; Li, R. Fog computing architecture-based data acquisition for WSN applications. China Commun. 2017, 14, 69–81. [Google Scholar] [CrossRef]
- Fantacci, R.; Nizzi, F.; Pecorella, T.; Pierucci, L.; Roveri, M. False Data Detection for Fog and Internet of Things Networks. Sensors 2019, 19, 4235. [Google Scholar] [CrossRef] [Green Version]
- Hassan, M.M.; Gumaei, A.; Huda, S.; Almogren, A. Increasing the Trustworthiness in the Industrial IoT Networks through a Reliable Cyberattack Detection Model. IEEE Trans. Ind. Inform. 2020, 16, 6154–6162. [Google Scholar] [CrossRef]
- Bioglio, V.; Condo, C.; Land, I. Design of Polar Codes in 5G New Radio. IEEE Commun. Surv. Tutor. 2021, 23, 29–40. [Google Scholar] [CrossRef] [Green Version]
- Alahari, H.P.; Yalavarthi, S.B. A Survey on Network Routing Protocols in Internet of Things (IOT). Int. J. Comput. Appl. 2017, 160, 18–22. [Google Scholar] [CrossRef]
- Li, J.; Li, X.; Cheng, X.; Yuan, J.; Zhang, R. A trustworthiness-enhanced reliable forwarding scheme in mobile Internet of Things. J. Netw. Comput. Appl. 2019, 140, 40–53. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. SIoT: Giving a Social Structure to the Internet of Things. IEEE Commun. Lett. 2011, 15, 1193–1195. [Google Scholar] [CrossRef]
- Caballero, V.; Vernet, D.; Zaballos, A. Social Internet of Energy-A New Paradigm for Demand Side Management. IEEE Internet Things J. 2019, 6, 9853–9867. [Google Scholar] [CrossRef]
- Nitti, M.; Girau, R.; Atzori, L. Trustworthiness Management in the Social Internet of Things. IEEE Trans. Knowl. Data Eng. 2013, 26, 1253–1266. [Google Scholar] [CrossRef]
- Marche, C.; Nitti, M. Trust-Related Attacks and Their Detection: A Trust Management Model for the Social IoT. IEEE Trans. Netw. Serv. Manag. 2021, 18, 3297–3308. [Google Scholar] [CrossRef]
- Lin, Z.; Dong, L. Clarifying Trust in Social Internet of Things. IEEE Trans. Knowl. Data Eng. 2018, 30, 234–248. [Google Scholar] [CrossRef] [Green Version]
- Azad, M.A.; Bag, S.; Hao, F.; Shalaginov, A. Decentralized Self-Enforcing Trust Management System for Social Internet of Things. IEEE Internet Things J. 2020, 7, 2690–2703. [Google Scholar] [CrossRef]
- Bodkhe, U.; Mehta, D.; Tanwar, S.; Bhattacharya, P.; Singh, P.K.; Hong, W.C. A survey on decentralized consensus mechanisms for cyber physical systems. IEEE Access 2020, 8, 54371–54401. [Google Scholar] [CrossRef]
- All about Moteino | LowPowerLab. Available online: https://lowpowerlab.com/guide/moteino/ (accessed on 21 September 2021).
- Gaelens, J.; Van Torre, P.; Verhaevert, J.; Rogier, H. Lora mobile-to-base-station channel characterization in the Antarctic. Sensors 2017, 17, 1903. [Google Scholar] [CrossRef] [Green Version]
- Fang, Y.; Chen, P.; Cai, G.; Lau, F.C.M.; Liew, S.C.; Han, G. Outage-limit-approaching channel coding for future wireless communications: Root-protograph low-density parity-check codes. IEEE Veh. Technol. Mag. 2019, 14, 85–93. [Google Scholar] [CrossRef]
- Pan, X.; Di Maio, F.; Zio, E. A Benchmark of Dynamic Reliability Methods for Probabilistic Safety Assessment. In Proceedings of the 2017 2nd International Conference on System Reliability and Safety (ICSRS), Milan, Italy, 20–22 December 2017; pp. 82–90. [Google Scholar]
- Castro, M.; Liskov, B. Practical Byzantine Fault Tolerance and Proactive Recovery. ACM Trans. Comput. Syst. 2002, 20, 398–461. [Google Scholar] [CrossRef]













| Parameter | NVIS | LoRa |
|---|---|---|
| Transmission Band | 4.3 MHz | 868 MHz |
| Channel Bandwidth | 2.3 kHz | 125 kHz |
| Channel Bitrate | 4.6 kbps | 5.47 kbps |
| Coverage Range | Up to 250 km | Up to 30 km |
| Daytime Availability (6 a.m.–5 p.m.) | 70–100% | 100% (LoS), 2–100% (No LoS) |
| Night Availability (5 p.m.–6 a.m.) | 0% | 100% (LoS), 2–100% (No LoS) |
| Maximum Payload Size | 242 bytes | 140 bytes |
| Parameter | Value |
|---|---|
| Number of runs per test | 30 |
| Simulation duration | 120 h (5 days) |
| [1 × 10−3, 2 × 10−3, 4 × 10−3, 8 × 10−3, 1 × 10−2, 2 × 10−2, 4 × 10−2, 8 × 10−2, 1 × 10−1] | |
| k | 5.7 × 10−5 |
| Transport protocol | [BBR, Copa, CUBIC, EAATP, Indigo, Verus] |
| Redundancy Mode | [None, Social, Consensus (PBFT)] |
| Number of NVIS gateways | 5 |
| GTN-P clusters per gateway | [8,16,32,64,128,256,512,1024,2048,4096] |
| GTN-P redundant stations per cluster | [1,2,3,4,5,6,7,8,9,10] |
| BBR | Copa | CUBIC | EAATP | Indigo | Verus | |
|---|---|---|---|---|---|---|
| 1 × 10−3 | 0.767 | 0.818 | 0.817 | 0.818 | 0.814 | 0.801 |
| 2 × 10−3 | 0.767 | 0.814 | 0.814 | 0.819 | 0.817 | 0.802 |
| 4 × 10−3 | 0.772 | 0.819 | 0.819 | 0.819 | 0.811 | 0.795 |
| 8 × 10−3 | 0.768 | 0.816 | 0.814 | 0.817 | 0.807 | 0.797 |
| 1 × 10−2 | 0.767 | 0.818 | 0.817 | 0.820 | 0.805 | 0.794 |
| 2 × 10−2 | 0.767 | 0.814 | 0.813 | 0.815 | 0.799 | 0.782 |
| 4 × 10−2 | 0.762 | 0.811 | 0.809 | 0.813 | 0.777 | 0.765 |
| 8 × 10−2 | 0.750 | 0.796 | 0.795 | 0.794 | 0.741 | 0.727 |
| 1 × 10−1 | 0.731 | 0.785 | 0.781 | 0.779 | 0.724 | 0.710 |
| BBR | Copa | CUBIC | EAATP | Indigo | Verus | |
|---|---|---|---|---|---|---|
| 1 × 10−3 | 0.757 | 0.797 | 0.798 | 0.797 | 0.795 | 0.783 |
| 2 × 10−3 | 0.752 | 0.799 | 0.799 | 0.798 | 0.796 | 0.783 |
| 4 × 10−3 | 0.748 | 0.796 | 0.798 | 0.797 | 0.792 | 0.777 |
| 8 × 10−3 | 0.75 | 0.794 | 0.795 | 0.801 | 0.792 | 0.775 |
| 1 × 10−2 | 0.749 | 0.793 | 0.795 | 0.796 | 0.786 | 0.775 |
| 2 × 10−2 | 0.74 | 0.79 | 0.787 | 0.792 | 0.779 | 0.764 |
| 4 × 10−2 | 0.73 | 0.776 | 0.781 | 0.781 | 0.757 | 0.747 |
| 8 × 10−2 | 0.698 | 0.74 | 0.736 | 0.737 | 0.727 | 0.706 |
| 1 × 10−1 | 0.672 | 0.717 | 0.714 | 0.718 | 0.704 | 0.692 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mallorquí, A.; Zaballos, A.; Briones, A. DTN Trustworthiness for Permafrost Telemetry IoT Network. Remote Sens. 2021, 13, 4493. https://doi.org/10.3390/rs13224493
Mallorquí A, Zaballos A, Briones A. DTN Trustworthiness for Permafrost Telemetry IoT Network. Remote Sensing. 2021; 13(22):4493. https://doi.org/10.3390/rs13224493
Chicago/Turabian StyleMallorquí, Adrià, Agustín Zaballos, and Alan Briones. 2021. "DTN Trustworthiness for Permafrost Telemetry IoT Network" Remote Sensing 13, no. 22: 4493. https://doi.org/10.3390/rs13224493