BSEA: A Blind Sealed-Bid E-Auction Scheme for E-Commerce Applications
Abstract
:1. Introduction
2. Related Work
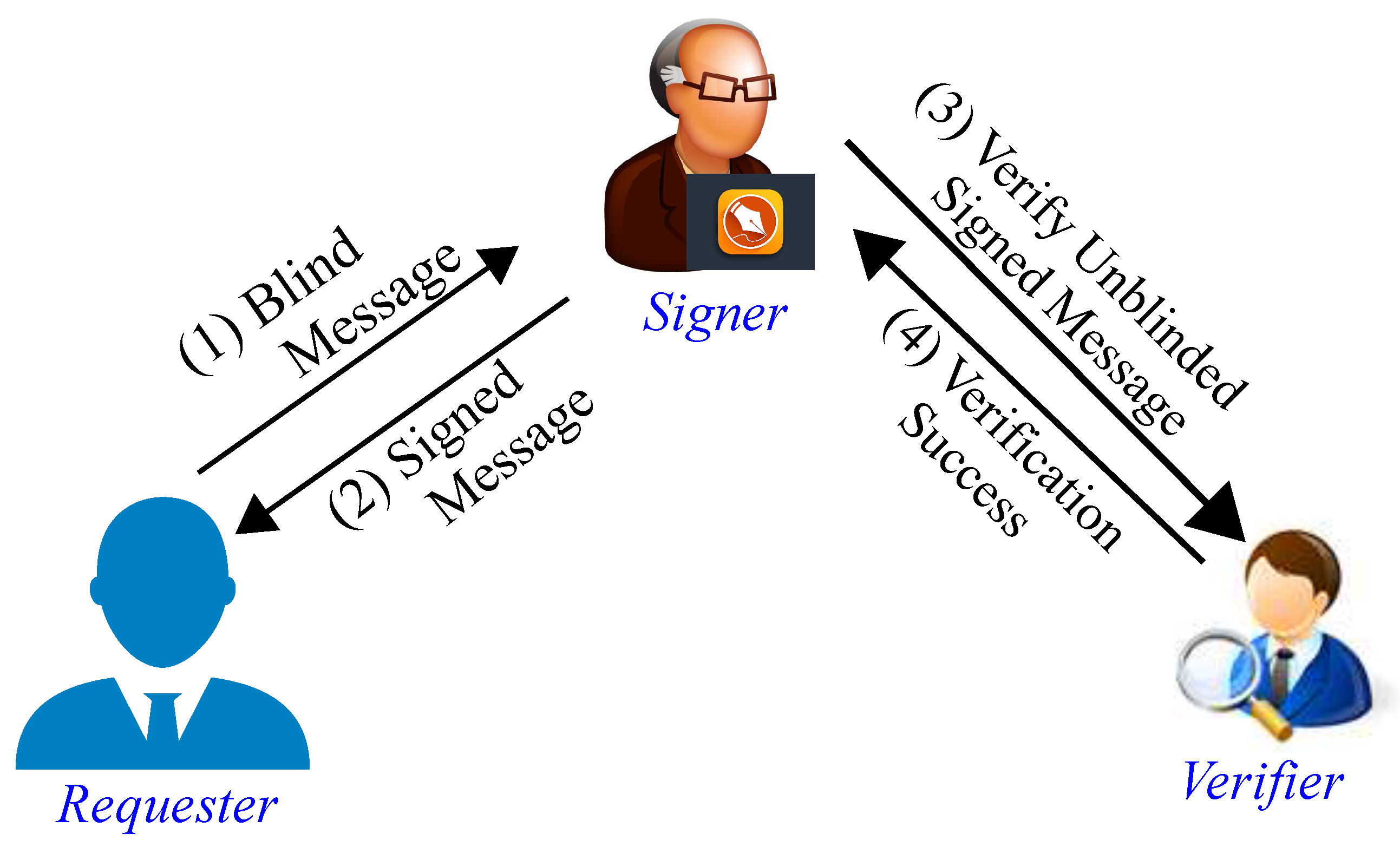
3. Proposed Controlled Traceable Blind Signature Scheme
| Algorithm 1 Key Generation Phase |
|
| Algorithm 2 Blinding Phase |
|
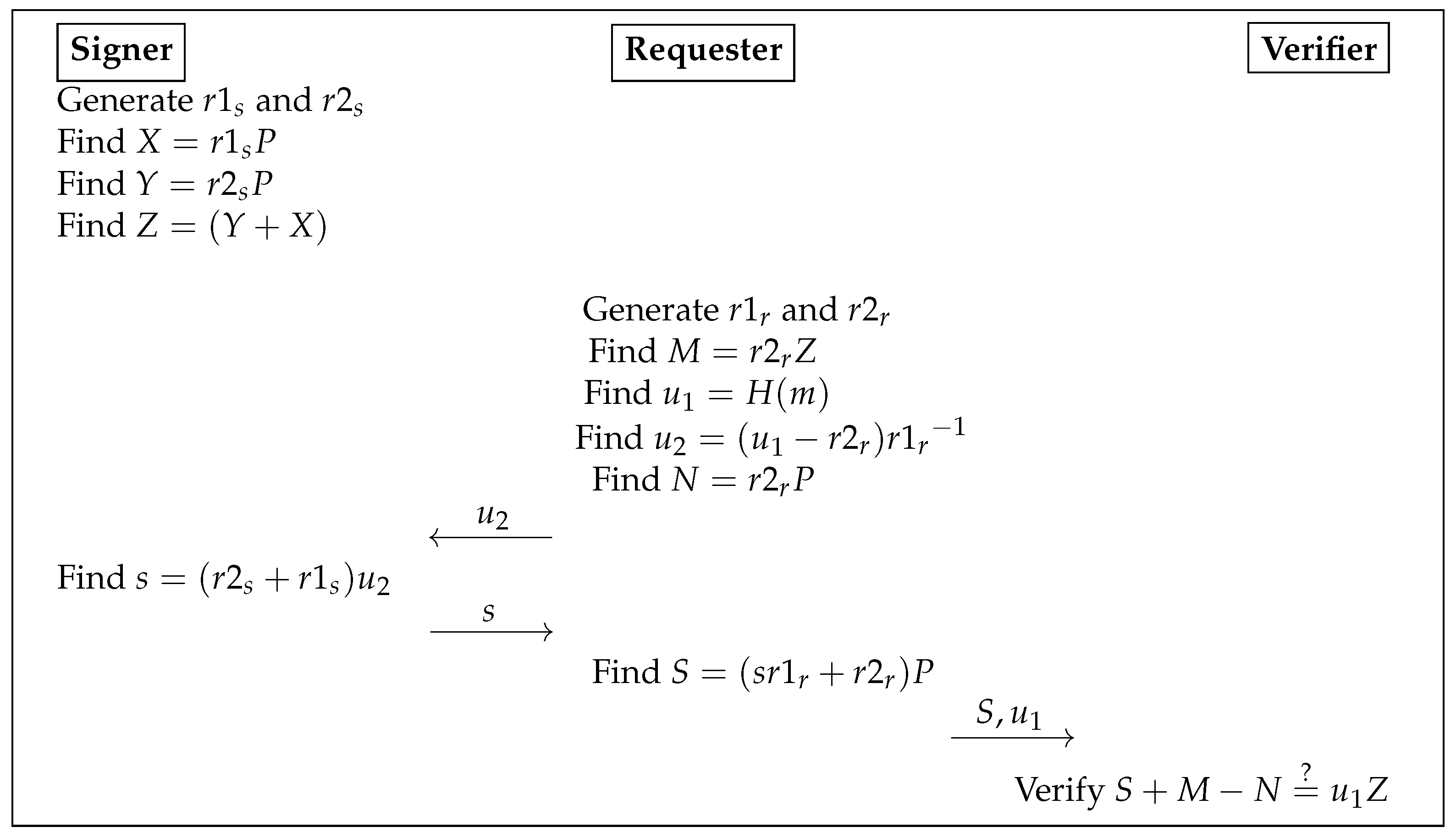
| Algorithm 3 Signing Phase |
|
| ▹ s is the Signer’s signature on the blind message. |
|
| Algorithm 4 Unblinding with Verification Phase |
|
4. Security Analysis of CTBSS
4.1. Correctness Proof
4.2. Blindness
4.3. Traceability
4.4. Universally Verifiable
5. Proposed Blind Sealed-Bid Electronic-Auction Scheme
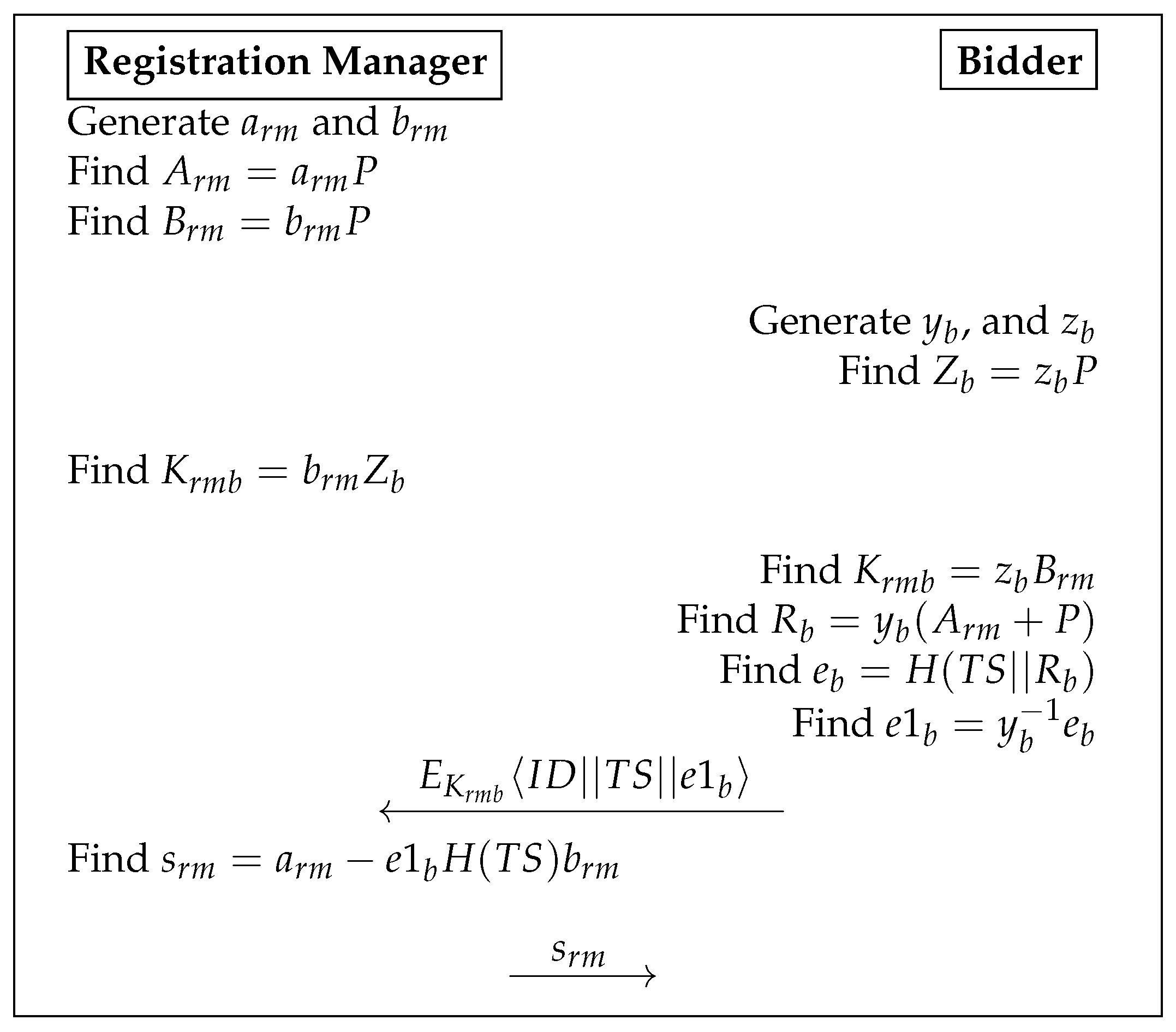
| Algorithm 5 Registration Setup Phase |
|
| Algorithm 6 Registration Confirmation Phase |
|
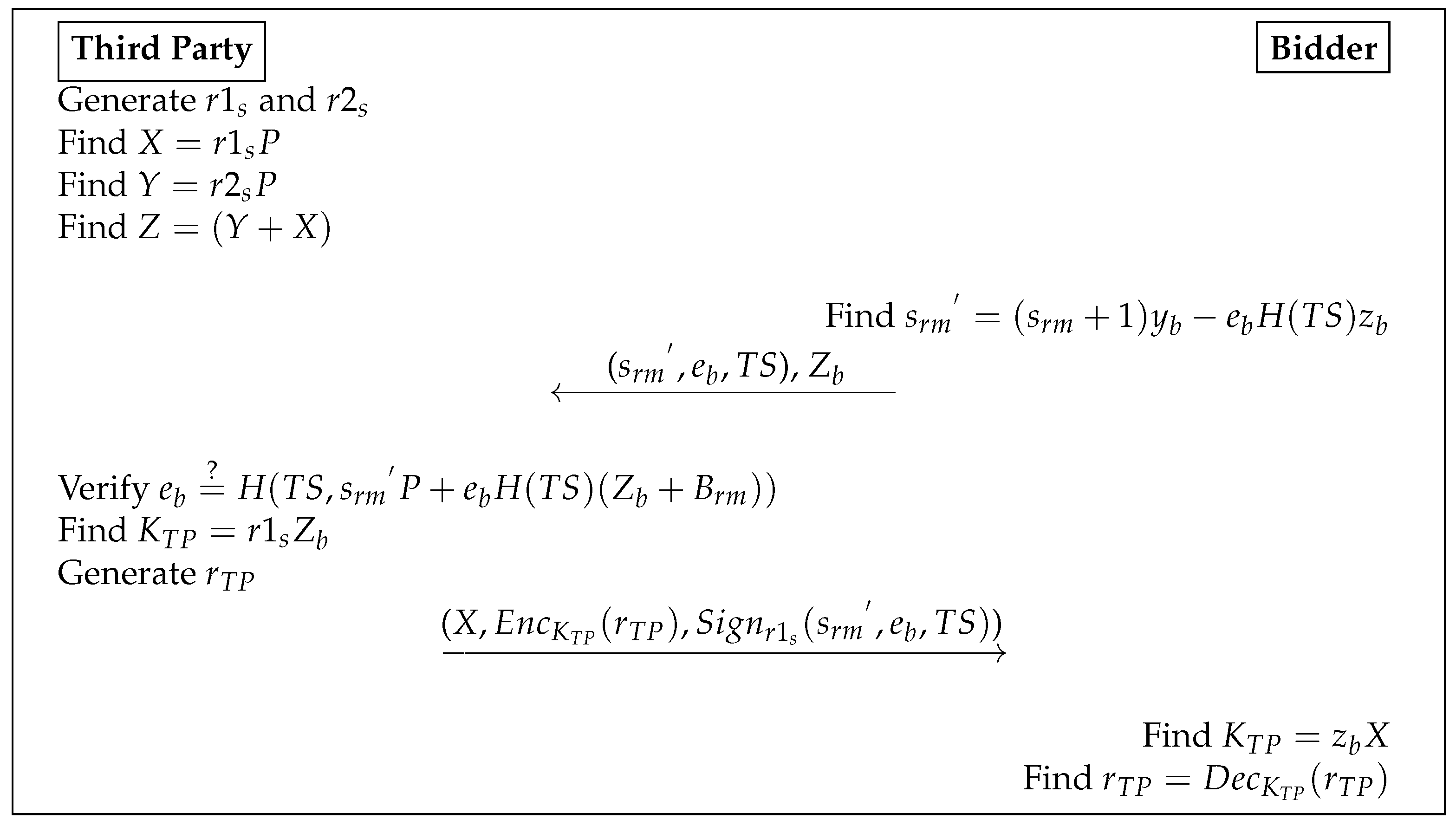
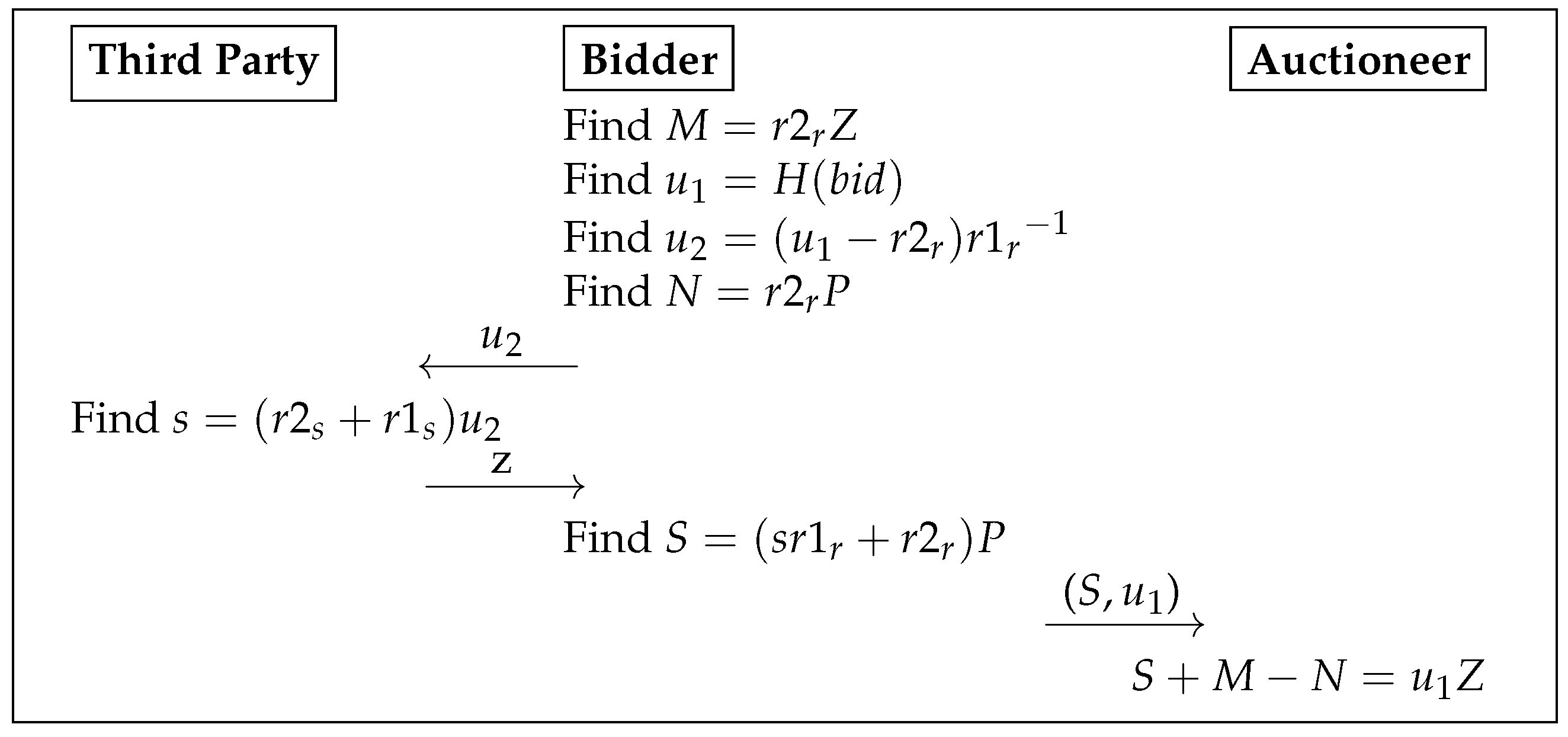
| Algorithm 7 Bidding Phase |
|
| ▹ Here, the TP can not find anything about the value. |
|
| ▹ The signed value by the TP is S. |
|
| ▹ Here, without revealing the value, it can be verified. |
| Algorithm 8 Winner Determination Phase |
|
6. Security and Requirement Analysis of BSEA
6.1. Correctness Proof
6.2. Security Analysis
- Key only attack: In order to successfully launch a key only attack, the attacker needs to get a valid signature. Even if she gets a valid signature, then she is also unable to unblind the signature, as she does not know the blinding factor and the private key of the Bidder (i.e., and ). The difficulty of finding depends on the difficulty of ECDLP and finding the value of depends on the difficulty of solving IFP.
- Known message attack: In the known message attack, the attacker generates a valid signature for his own message . Here, she has access to two or more message-signature pairs like and . Here, the attacker can generate another signature for message , if she can find . This is very difficult if the hash function is preimage resistant. Moreover, she also needs to find the value of for which she has to find and .
- Chosen message attack: In case of chosen message attack, the attacker can make the TP to sign for two messages, and . Then, she can calculate a new signature . If the attacker can find and the blind message for his/her message , then she can do a chosen message attack on BSEA. However, it is very difficult to find the hash value of a message that is the same as the hash value of the given messages and .
- Forgery attack: Given X and P, finding is difficult due to the difficulty in solving the ECDLP problem. Hence, the private key of the TP can never be guessed correctly. It will be difficult for the attacker to unblind the message because and are the private components of the Bidder.
- Replay attack: An attacker cannot retrieve the of the Bidder as the message sent to the RM is encrypted with the session key . She would not be able to find either or . Similarly, due to the session key that is only with the Bidder and the TP, the attacker would not be able to find the random number .
- Eavesdropping attack: Even if the attacker wants to eavesdrop on the communication between any Bidder and the RM or the TP, she will not get enough advantage. The reason for this is that the data that flows are encrypted with the session keys and and are also being signed by the respective entities.
- Identity theft attack: In the proposed BSEA, the Bidder’s is not used for authentication. Instead, timestamp () is being used for authentication, which prevents the Bidder from the risk of identity theft. In addition to this, the random number provided by the TP is only known to them. However, in case the TP is corrupted, she may reveal the random number , but the real identity of the Bidder is still concealed.
- Impersonate attack: It is impossible to impersonate either the Bidder or the RM or the TP because all have used either their session key to encrypt the messages or the private keys to sign the messages.
6.3. Requirement Analysis
- Anonymity: The information about every Bidder must be hidden from other Bidders. The TP will authenticate the Bidders and will assign a random number to each of them. Every Bidder blinds their value and sends to the TP to get his/her signature. Thus, all the information about the Bidder, including his/her value, is hidden from everyone until the auction process is closed. In the winner determination phase, the Bidder sends his/her value only to the TP to determine the . Thus, anonymity is preserved for all the Bidders even if the TP is corrupted.
- Un-forgeability: Any attempt by the attacker to forge bid value will fail as she can not find . For this, she has to find and , and, for this, she has to solve ECDLP. Moreover, all the necessary information is encrypted with the session key and/or signed by the Sender. Hence, forgery attack is not possible.
- Non-Repudiation: The Bidder as well as the TP must not be able to deny the act that they have done during the execution of the phases of BSEA. The Bidder cannot deny casting the because the signed value S can be verified using Equation (13), where M is the public key of the Bidder. Similarly, the TP can not deny receiving the , as the same signature is also verified by using his public key Z.
- Public Verifiability: The signature S can be verified by everyone after publishing the signature parameter . Moreover, the final winner’s can also be verified by everyone once the TP publishes the tuple . As anyone can now find and verify the signature S. The authenticity of every Bidder can also be verified by everyone.
- Traceability: The winning Bidder or any other Bidder who does not follow the auction rule can be identifiable because the proposed BSEA is traceable (the explanation is given in Section 4.3).
- Fairness and Robustness: BSEA satisfies the fairness property because even if the malicious Bidder or Auctioneer colludes with the TP, they will not gain any information about the honest Bidder, which can harm him/her in the running auction process or any future auction process.
- Privacy: BSEA maintains the privacy of every Bidder during the auction process. It also preserves the privacy of the losing Bidder even after the winner determination phase is over.
- Integrity and Confidentiality: The integrity and confidentiality of BSEA are achieved through blind signature and the session key. No one can find the value before the winner determination phase is over due to the blindness property of the proposed BSEA. No one can change the value once signed by the TP because, even if it is modified, it cannot be verified by Equation (13).
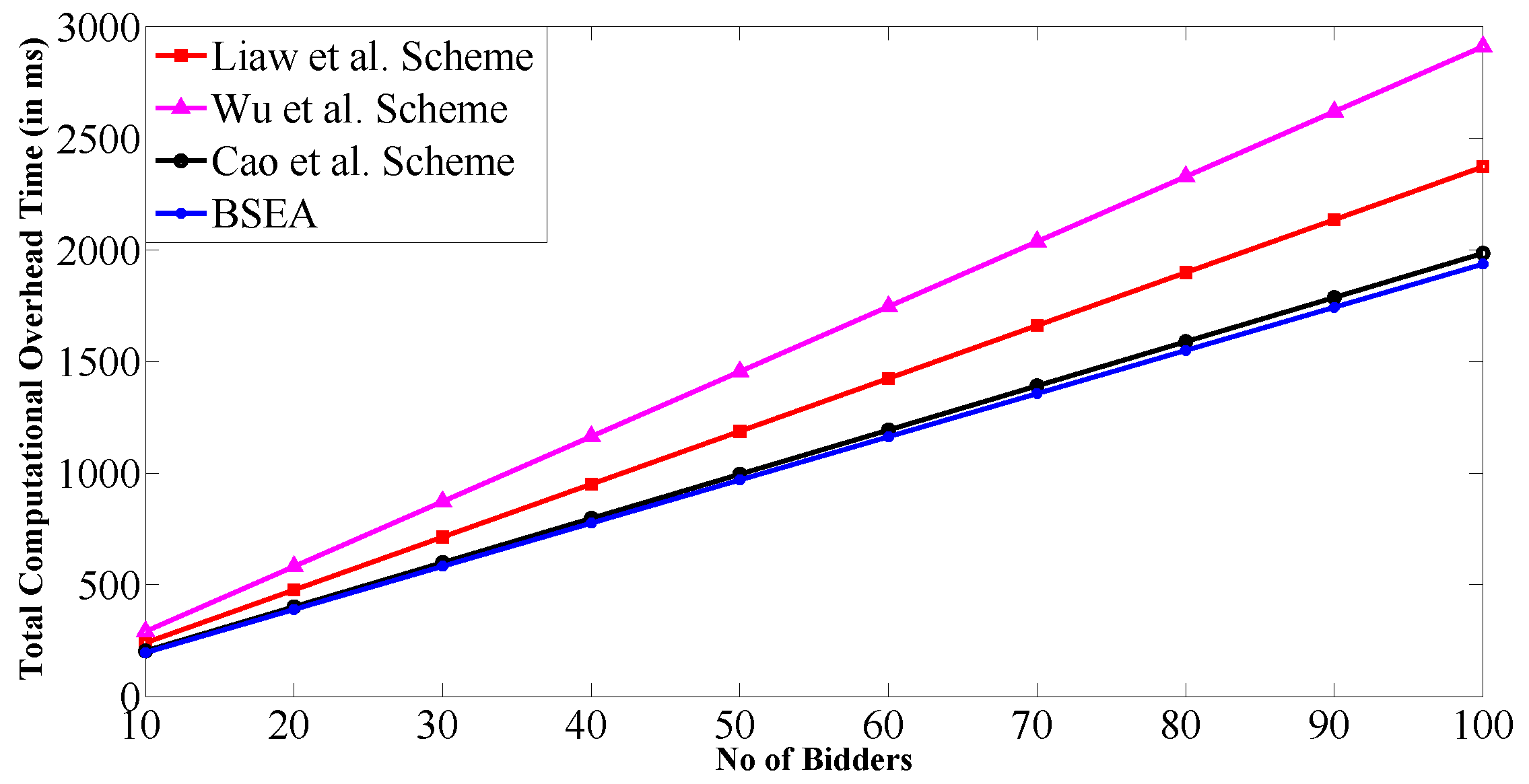
7. Performance Analysis of BSEA
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| BSEA | blind sealed-bid electronic auction |
| CTBSS | controlled traceable blind signature scheme |
| DLP | discrete logarithm problem |
| ECC | elliptic curve cryptography |
| ECDLP | elliptic curve discrete logarithm problem |
References
- Omote, K. A Study on Electronic Auctions. Ph.D. Thesis, Japan Advanced Institute of Science and Technology, Nomi, Japan, 2002. [Google Scholar]
- Kleusberg, P. E-Collaboration und E-Reverse Auctions: Sicherung von Wettbewerbsvorteilen im Verarbeitenden Gewerbe; VDM Publishing: Saarbrucken, Germany, 2009. (In German) [Google Scholar]
- Engelbrecht-Wiggans, R.; Katok, E. E-sourcing in Procurement: Theory and Behavior in Reverse Auctions with Noncompetitive Contracts. Manag. Sci. 2006, 52, 581–596. [Google Scholar] [CrossRef]
- Chang, Y.F.; Chang, C.C. Enhanced anonymous auction protocols with freewheeling bids. In Proceedings of the 20th International Conference on Advanced Information Networking and Applications, Vienna, Austria, 18–20 April 2006; Volume 1, pp. 6–11.
- Vickrey, W. Counterspeculation, auctions, and competitive sealed tenders. J. Financ. 1961, 16, 8–37. [Google Scholar] [CrossRef]
- Liu, Y. A new secure and efficient M+1st price auction scheme based on ECC system. In Proceedings of the 3rd International Conference on Anti-counterfeiting, Security, and Identification in Communication, Hong Kong, China, 20–22 August 2009; pp. 489–492.
- Lee, B.; Kim, K.; Ma, J. Efficient Public Auction with One-Time Registration and Public Verifiability. In Progress in Cryptology—INDOCRYPT 2001; Rangan, C., Ding, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2247, pp. 162–174. [Google Scholar]
- Chaum, D. Blind Signatures for Untraceable Payments. In Proceedings of the CRYPTO ’82 Advances in Cryptology, Santa Barbara, CA, USA, 23–25 August 1982; pp. 199–203.
- Castiglione, A.; Palmieri, F.; Chen, C.L.; Chang, Y.C. A Blind Signature-Based Approach for Cross-Domain Authentication in the Cloud Environment. Int. J. Data Warehous. Min. 2016, 12, 34–48. [Google Scholar] [CrossRef]
- Tian, H.; Zhang, F.; Wei, B. A lattice-based partially blind signature. Secur. Commun. Netw. 2016, 9, 1820–1828. [Google Scholar] [CrossRef]
- Zou, X.; Qiu, D. Attack and improvements of fair quantum blind signature schemes. Quantum Inf. Process. 2013, 12, 2071–2085. [Google Scholar] [CrossRef]
- Nayak, S.K. Blind Signature Schemes using Elliptic Curve Cryptography. Ph.D. Thesis, National Institute of Technology, Rourkela, India, 2013. [Google Scholar]
- Shao, Z. Improved User Efficient Blind Signatures. Electron. Lett. 2000, 36, 1372–1374. [Google Scholar] [CrossRef]
- Yum, D.H.; Lee, P.J. Generic Construction of Certificateless Signature. In Information Security and Privacy; Wang, H., Pieprzyk, J., Varadharajan, V., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3108, pp. 200–211. [Google Scholar]
- Nayak, S.K.; Mohanty, S.; Majhi, B. CLB-ECC: Certificateless Blind Signature Using ECC. J. Inf. Process. Syst. 2014. [Google Scholar] [CrossRef]
- Islam, S.; Obaidat, M.S. Design of provably secure and efficient certificateless blind signature scheme using bilinear pairing. Secur. Commun. Netw. 2015, 8, 4319–4332. [Google Scholar] [CrossRef]
- Jiang, S.; Zhu, X.; Guo, L.; Liu, J.; Hao, R.; Yang, B. Efficient private matching based on blind signature for proximity-based mobile social networks. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 3246–3251.
- Shi, J.; Shi, R.; Guo, Y.; Peng, X.; Tang, Y. Batch proxy quantum blind signature scheme. Sci. China Inf. Sci. 2013, 56, 1–9. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, Z.; Sun, R.; Kwak, K.S. Certificateless partially blind signature. In Proceedings of the 26th International Conference on Advanced Information Networking and Applications Workshops (WAINA), Fukuoka, Japan, 26–29 March 2012; pp. 128–133.
- Nayak, S.K.; Majhi, B.; Mohanty, S. An ECDLP based untraceable blind signature scheme. In Proceedings of the 2nd IEEE International Conference on Circuits, Power and Computing Technologies (ICCPCT), Nagercoil, India, 20–21 March 2013; pp. 829–834.
- Tahat, N.; Abdallah, E.E. A proxy partially blind signature approach using elliptic curve cryptosystem. Int. J. Math. Oper. Res. 2016, 8, 87–95. [Google Scholar] [CrossRef]
- Alam, K.; Alam, K.R.; Faruq, O.; Morimoto, Y. A comparison between RSA and ElGamal based untraceable blind signature schemes. In Proceedings of the 2016 International Conference on Networking Systems and Security (NSysS), Dhaka, Bangladesh, 7–9 January 2016; pp. 1–4.
- Dahshan, H.; Kamal, A.; Rohiem, A. A Threshold Blind Digital Signature Scheme Using Elliptic Curve Dlog-Based Cryptosystem. In Proceedings of the 2015 IEEE 81st Vehicular Technology Conference (VTC Spring), Glasgow, UK, 11–14 May 2015; pp. 1–5.
- Miller, V.S. Use of Elliptic Curves in Cryptography. In Advances in Cryptology— CRYPTO ’85; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1986; Volume 218, pp. 417–426. [Google Scholar]
- Chaudhry, S.A.; Farash, M.S.; Naqvi, H.; Sher, M. A secure and efficient authenticated encryption for electronic payment systems using elliptic curve cryptography. Electron. Commer.Res. 2015, 16, 113–139. [Google Scholar] [CrossRef]
- Chen, Y.; Chou, J.S. ECC-based untraceable authentication for large-scale active-tag RFID systems. Electron. Commer. Res. 2015, 15, 97–120. [Google Scholar] [CrossRef]
- Lopez, J.; Dahab, R. An Overview of Elliptic Curve Cryptography. Available online: http:// citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.37.2771&rep=rep1&type=pdf (accessed on 13 December 2016).
- Wang, T.Y.; Wei, Z.L. Analysis of Forgery Attack on One-Time Proxy Signature and the Improvement. Int. J. Theor. Phys. 2016, 55, 743–745. [Google Scholar] [CrossRef]
- Cheng, L.; Wen, Q. Cryptanalysis and improvement of a certificateless partially blind signature. Inf. Secur. IET 2015, 9, 380–386. [Google Scholar] [CrossRef]
- Zhang, K.J.; Jia, H.Y. Cryptanalysis of a quantum proxy weak blind signature scheme. Int. J. Theor. Phys. 2015, 54, 582–588. [Google Scholar] [CrossRef]
- Das, R.K. Development of an ECDLP based Traceable Blind Signature Scheme and its Application to E-Auction. Ph.D. Thesis, National Institute of Technology, Rourkela, India, 2014. [Google Scholar]
- Franklin, M.K.; Reiter, M.K. The design and implementation of a secure auction service. IEEE Trans. Softw. Eng. 1996, 22, 302–312. [Google Scholar] [CrossRef]
- Kudo, M. Secure electronic sealed-bid auction protocol with public key cryptography. IEICE Trans. Fundam. 1998, 81, 20–27. [Google Scholar]
- Kikuchi, H.; Hakavy, M.; Tygar, D. Multi-round anonymous auction protocols. IEICE Trans. Inf. Syst. 1999, 82, 769–777. [Google Scholar]
- Chang, C.C.; Chang, Y.F. Efficient anonymous auction protocols with freewheeling bids. Comput. Secur. 2003, 22, 728–734. [Google Scholar] [CrossRef]
- Jiang, R.; Pan, L.; Li, J.H. An improvement on efficient anonymous auction protocols. Comput. Secur. 2005, 24, 169–174. [Google Scholar] [CrossRef]
- Liaw, H.T.; Juang, W.S.; Lin, C.K. An electronic online bidding auction protocol with both security and efficiency. Appl. Math. Comput. 2006, 174, 1487–1497. [Google Scholar] [CrossRef]
- Wu, C.C.; Chang, C.C.; Lin, I.C. New Sealed-Bid Electronic Auction with Fairness, Security and Efficiency. J. Comput. Sci. Technol. 2008, 23, 253–264. [Google Scholar] [CrossRef]
- Cao, G.; Chen, J. Practical Electronic Auction Scheme Based on Untrusted Third-Party. In Proceedings of the 2013 Fifth International Conference on Computational and Information Sciences (ICCIS), Shiyan, China, 21–23 June 2013; pp. 493–496.
- Cao, G. Secure and efficient electronic auction scheme with strong anonymity. J. Netw. 2014, 9, 2189–2194. [Google Scholar] [CrossRef]
- Ksikezopolski, B.; Kotulski, Z. Cryptographic protocol for electronic auctions with extended requirements. Ann. UMCS Sect. AI Inf. 2015, 2, 391–400. [Google Scholar]
- Lynn, B. The Pairing-Based Cryptography Library. Available online: https://crypto.stanford.edu/pbc/ (accessed on 27 March 2013).

| Symbols | Meaning |
|---|---|
| P | base point of large order, such that |
| n | number of points on |
| O | point at infinity |
| random numbers chosen by the Signer | |
| random numbers chosen by the Requester | |
| m | message |
| secure hash function |
| Liaw et al. [37] | √ | √ | × | √ | √ | × | × | √ |
| Wu et al. [38] | √ | √ | √ | √ | √ | √ | × | √ |
| Cao et al. [39] | √ | √ | √ | √ | × | √ | × | √ |
| Ksiezopolski et al. [41] | √ | √ | √ | √ | √ | × | × | √ |
| Cao [40] | √ | √ | √ | √ | × | √ | √ | √ |
| BSEA | √ | √ | √ | √ | √ | √ | √ | √ |
| Schemes/Phases | Advertisement | Registration | Bidding | Winner Determination |
|---|---|---|---|---|
| Liaw et al. [37] | ||||
| Wu et al. [38] | ||||
| Cao et al. [39] | ||||
| BSEA |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Das, R.K.; Nayak, S.K.; Bhoi, S.K.; Choudhury, S.K.; Majhi, B.; Mohanty, S. BSEA: A Blind Sealed-Bid E-Auction Scheme for E-Commerce Applications. Computers 2016, 5, 32. https://doi.org/10.3390/computers5040032
Das RK, Nayak SK, Bhoi SK, Choudhury SK, Majhi B, Mohanty S. BSEA: A Blind Sealed-Bid E-Auction Scheme for E-Commerce Applications. Computers. 2016; 5(4):32. https://doi.org/10.3390/computers5040032
Chicago/Turabian StyleDas, Rohit Kumar, Sanjeet Kumar Nayak, Sourav Kumar Bhoi, Suman Kumar Choudhury, Banshidhar Majhi, and Sujata Mohanty. 2016. "BSEA: A Blind Sealed-Bid E-Auction Scheme for E-Commerce Applications" Computers 5, no. 4: 32. https://doi.org/10.3390/computers5040032





