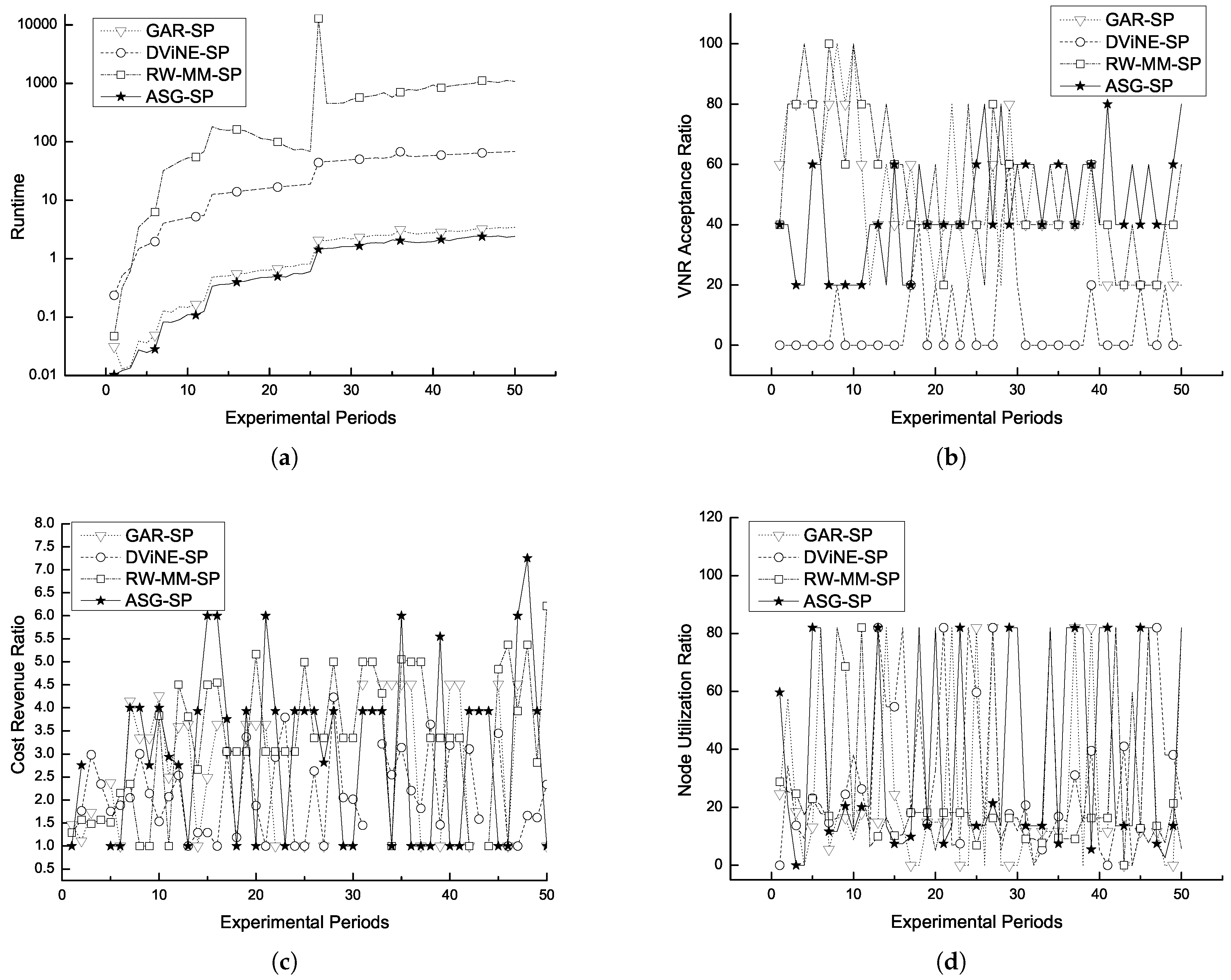
1.1. Research Advances in Virtual Network Embedding
Network virtualization (NV) technology [
1] represents a promising way of overcoming the network ossification problem, via providing an efficient solution to the mismatch between various Internet applications and rigid substrate physical network (SPN) architecture. Success in applying NV to allocation of computational resources in cloud data centers [
1] encourages researchers to explore more efficient solutions and reliable schemes for realizing NV.
The main objects in NV are called virtual networks, which will be provided by Internet Service Provider (ISP) in next-generation network architecture. One virtual network consists of virtual nodes connected by virtual links. In essence, the virtual nodes are logical function entries that are constructed by allocating computational or communication resources from ISPs to provide user-expected services. This function of resource allocation is known as virtual network embedding (VNE). The term embedding is sometimes equivalent to mapping, provisioning or assignment. The process of virtual network embedding maps virtual nodes in VN to the resource nodes in SPN, and virtual links to the physical paths in SPN.
As key parts of NV technology, VN embedding and scheduling have received a great deal of attention from researchers since 2008. At first, static VNE algorithms, running in an offline mode, were considered [
2]. In this approach, after the user VN is embedded into SPN by a mapping
, the mapping
need not be reconstructed when the property and status of SPN are changed.
Generally, the virtual network request (VNR) always arrives and leaves dynamically (almost randomly), and it is not known a priori. Thus, the VNE algorithm must process the continuously arriving VNRs in real time, along with the current status of the SPN, and needs to implement VNE in an online scheme. Even though the static VNE has a relatively simple algorithmic design, it is still difficult to apply practically, since its model relies on assumptions that do not hold in practice. Thus, online VNE has been pursued by Marquezan et al. [
3], who begin by presenting a distributed way of solving dynamic type VNE. They then reorganize SPN to renew the embedding of VN when the original VNR changes, but the connection between VN nodes and links is not coordinated. Houidi [
4] has proposed a fault-tolerant VNE scheme to tackle the node and link failures in SPN.
Currently, the main research focus is still on mathematical optimization and heuristics. Optimization approaches still derive
by linear or integer programming, but with added objects reflecting varied user demands, changed SPN structure and performance, and relaxed optimization limitation to mitigate the computational complexity of solving VNE. Heuristic algorithms usually try to achieve a near-optimal solution, and contributions focus on improving the quality of VNE solution, i.e., closing the gap between approximate and optimal solutions. The various works in two approaches can be characterized as survivable/dependable VNE; multiple InPs [
5], and topology-aware VNE [
6,
7]. Furthermore, VNE for special SPN has also garnered some attention, as in the case of datacenters, optical networks, and wireless networks. For example, Beck et al. [
8] proposes a distributed and parallel framework called DPVNE to implement VNE, in which several VNE algorithms are run to map VNR into SPN so that the single point pressure in SPN is reduced and overall efficiency is improved. Zhang et al. [
9] provide opportunistic resource sharing VNE scheme called ORS to deal with time-dependent VNRs, with time-slot allocation expressed as an optimization problem.
The online VNE with multiple InPs has also been discussed by Shen et al. [
5], who employ a broker-like entity to make centralized decisions, with an information-sharing scheme providing part of InP’s information, while keeping its privacy. Their scheme uses integer programming to settle VNE in polynomial time. Their VNE scheme achieves 80–90% efficacy over other methods under the assumption of all SPN information being known.
Distributed and parallel algorithms are preferred for realizing VNE among multiple InPs. Houidi et al. [
10] proposed a distributed method to solve the cross-domain (multiple InPs) VNE, regardless of network scale. Generally, parallel and distributed algorithms become desirable, if not necessary, when dealing with large-scale input objects, which requires the work to be extended to more SPN locations. Beck et al. [
8] introduced an algorithmic framework named DPVNE to implement VNE in a parallel and distributed fashion. In their scheme, the SPN is clustered as levels, via a multi-level recursive bisection algorithm. Next, they determine the delegate nodes in each cluster to receive VNR and select the most appropriate to process it, setting the deadlock tree for each cluster to deal with parallel embedding of many VNRs to avoid conflicts in utilizing the resources of the SPN. Although experiments show that DPVNE can simultaneously process many VNRs with a low communication overhead and comparable embedding cost compared to centralized algorithms, the computational complexity of dynamic real-time embedding is unknown. Moreover, selecting the delegate nodes and embedding VNE in all clusters, usually with irregular topologies, also present difficult challenges. Houidi et al. [
4] reconfigured the VNE in a distributed real-time scheme. However, the influence of existing VNE on the reconfiguration necessitates a formal approach, and the scheme usually entails a large overhead in message communication.
The main drawback of optimization type VNE methods is that they have a high computational complexity. Actually, when connecting the VNE to the multi-way separator problem, solving it is NP-hard [
1]. Accordingly, Xue et al. [
11] has aimed to implement VNE with a partition, using concurrency. The method called NC-DSBA utilizes a dynamically balanced service to improve the efficiency of VNE.
There are also other innovative approaches in the VNE field. Zhang et al. [
9] postulate the application of an opportunistic mechanism to resource sharing in VNE. Cheng and Su [
7] focus on the topology of SPN, coordinating the mapping of nodes and links. In the node-mapping stage, the topological properties of nodes in the physical network are considered as the most significant parameter of the VNE. They then emulate PageRank, Google’s method of ranking web pages, to rank the nodes for associating VN nodes with SPN nodes. Ultimately, the relations of node association are merged into the VNE algorithm to improve efficiency and acceptance ratio. Ref. [
5] formulates VNE across-domain physical networks. Zhang and Gao [
6] rank the nodes of SPN by topological properties to embed the users’ VN.
1.2. The Role of Network Symmetry
Readers of this journal hardly need to be reminded of the theoretical and practical importance of symmetry in nature and various technical domains. We thus focus in this section on the benefits of network symmetry in the design, analysis, management, and applications of computer and communications networks [
12], factors that motivated us to pursue the line of research described in this paper. Sometimes, complete symmetry can be troublesome, and we must resort to symmetry-breaking methods to make progress by preventing or removing deadlocks and other points of indecision [
13]. In a vast majority of instances, however, symmetry is an ally of network designer, evaluator, manager, and user because it leads to simplifications and efficiencies, advantages that we demonstrate for solving the VNE problem in this paper.
Symmetric networks lack a weakest point that might lead to service disruptions as a result of random malfunctions or deliberate attacks, and they lend themselves better to the use of distributed diagnostic methods [
14]. They lead to simpler routing and load-balancing algorithms [
15,
16] because all nodes have the same view of the system and thus execute identical component tasks as part of the overall algorithm. The interchangeable parts of a symmetric network allow the system to more easily recover from the effects of node and link failures [
17]. It has been proven that the ratio of network diameter to the average internode distance is upper-bounded by 2 in symmetric networks [
18], thus making the diameter, which is an easily derived quantity, a good predictor of network performance. The average internode distance, which is a better predictor of actual network performance, is, by comparion, much harder to compute and much more sensitive to assumptions about link and node capacities, especially under failure scenarios.
Wide-area and local-area computer networks grow in an ad hoc manner, based on communications needs and geographic considerations. They are thus often irregular. However, given that such networks tend to contain a large number of nodes and links, lack of symmetry isn’t a major drawback. Such networks are often characterized as small-world or scale-free networks [
19] that exhibit strong advantages in the face of failures, congestions, and other routing difficulties. Distributed decision-making reduces the complexity burden for many applications. However, for global resource management and mapping of user computations to such a network, topological irregularity creates immense computational burdens. Interconnection networks for parallel processing are more controllable in terms of topology, be they implemented by cables within equipment racks or by etched/printed paths on microchips or printed circuit-boards. It would be nice if the benefits of symmetry could be extended to all domains, including those in which topological symmetry is non-existent. Our work reported here represents a step in this direction.
1.3. Application of Symmetry to Our Scheme
Mainly, our VNE scheme employs the graph symmetry for two purposes: raising efficiency of VNE via symmetric graph auxiliary, and stabilizing VNE process via symmetric graph inducement.
To reduce the complexity of embedding a virtual network
H into an irregular substrate network
G, one can select a static topology model
K to assist the embedding. The main advance of using an auxiliary
K is that some good algorithm properties can be induced from
K to
H and
G such that the related algorithms are probably simplified and enhanced after VNE is implemented, like routing and load balancing. As shown in
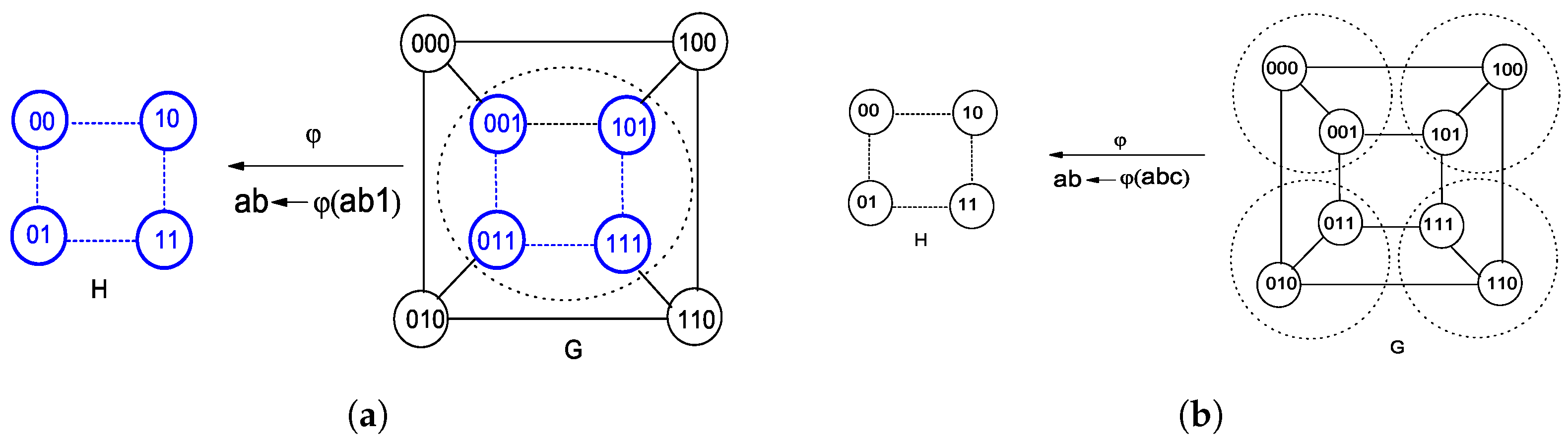
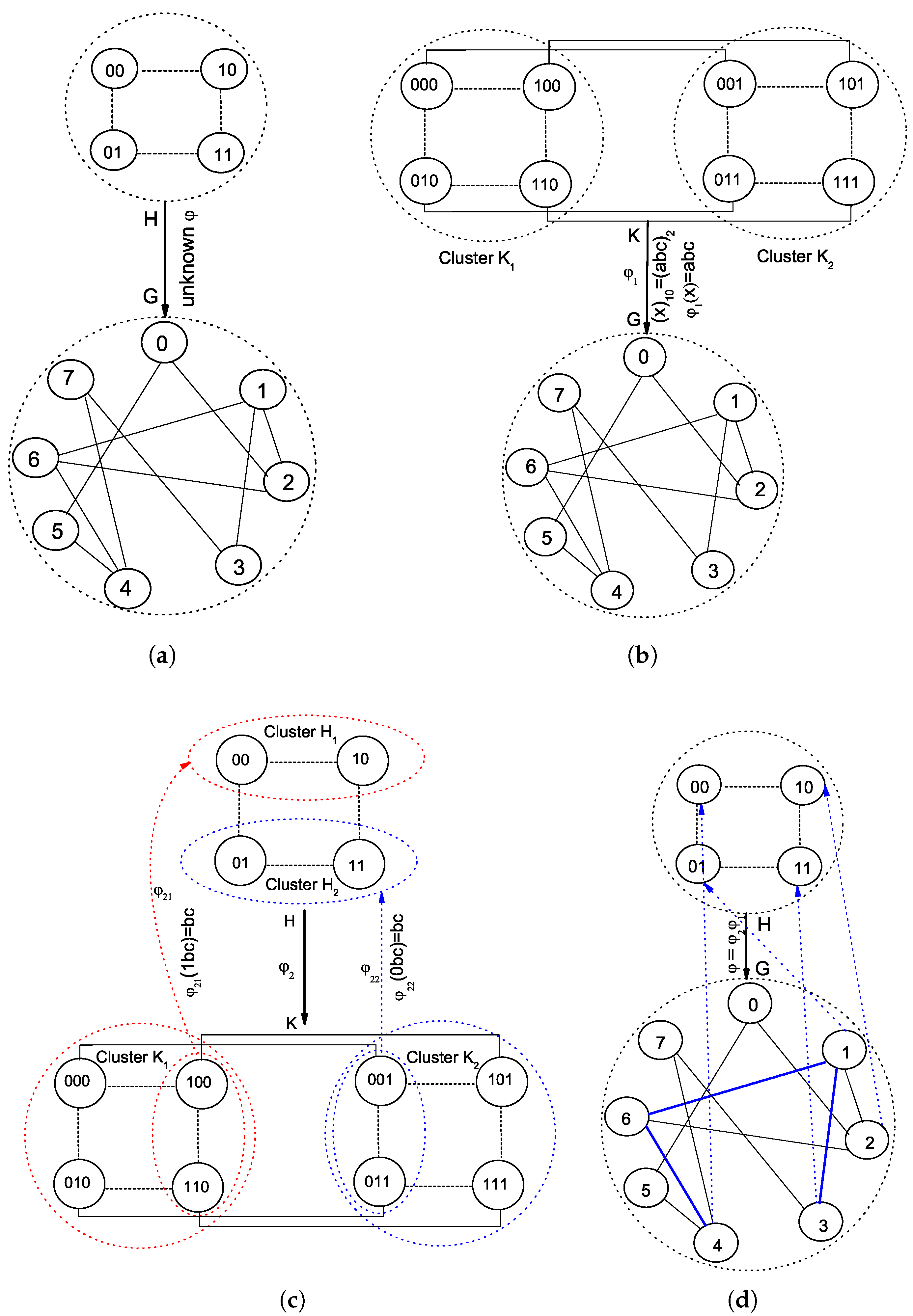
Figure 1, we obtain a generalized subgraph homomorphism in (a) and isomorphism in (b) to model the abstract embedding
H into
G relying on a regular hypercube topology Cube(3). As aforementioned, a static model
K with symmetry properties may reduce the complexity of embedding
H to
G. From the viewpoints of mathematics, one can solve
to map
K to
G, and
to map
H to
K so as to obtain the final
to embed
H to
G. It should be noticed that the two structures related to
are relatively static, and of the other two ones related to
, the larger one generally keeps static. The total time complexity to solve
and
is reduced apparently than to solve
independently.