Security Concepts in Emerging 6G Communication: Threats, Countermeasures, Authentication Techniques and Research Directions
Abstract
:1. Introduction
1.1. Existing Previous Work in Literature
1.2. Scope and Contributions
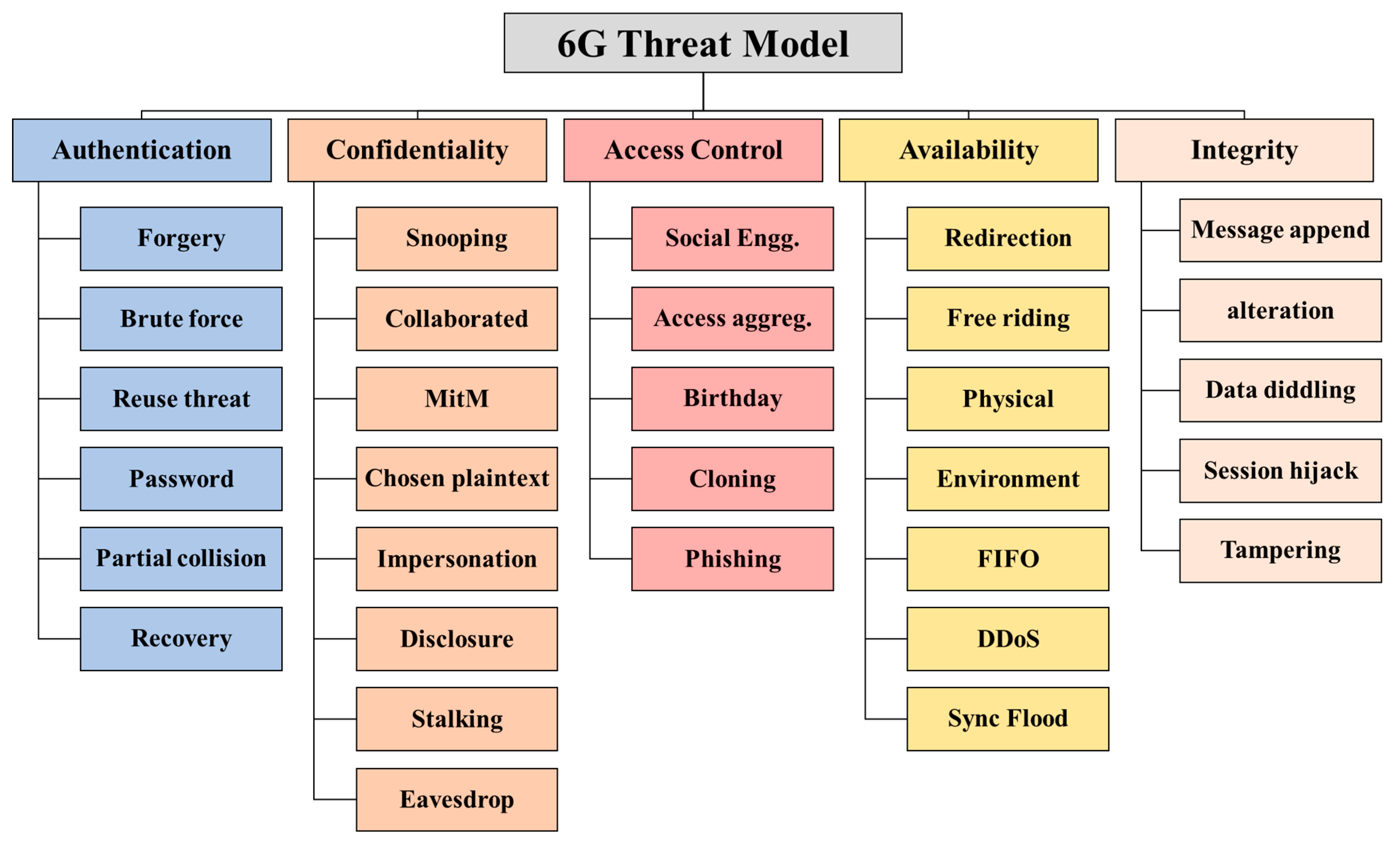
- We presented a threat model for the vulnerabilities in 6G cellular networks in five classifications: threats against Confidentiality, Integrity, Authentication, Availability and Access control (CIA3).
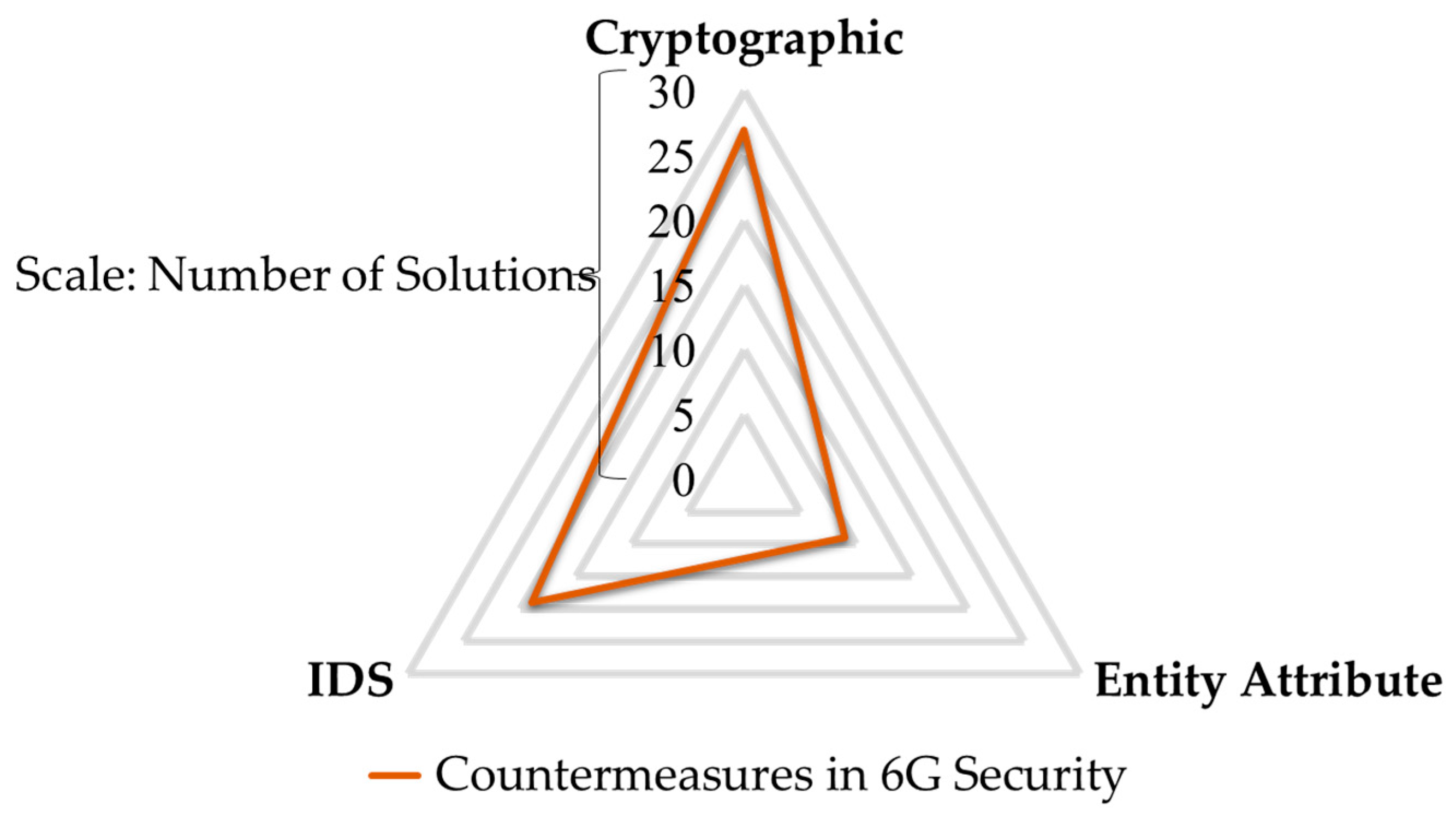
- We presented a categorization for countermeasures used in 6G networks into three types based on asymmetries: (1) Cryptographic Methods (CM), (2) Entity Attributes (EA) and (3) Intrusion Detection Systems (IDS).
- We suggested a taxonomy of authentication techniques for 6G networks in eight types: handover authentication, mutual authentication, physical layer authentication, deniable authentication, Token-based authentication, Certificate-based authentication, key agreement-based authentication and multi-factor authentication.
- We specifically highlighted future research directions on the basis of overall discussion on the topic, including, (1) Privacy Preservation in 6G network-based 3D Fog Computing, (2) 6G-enabled secure smart Infrastructures and Augmented Reality, (3) SDN-based privacy-protected architecture in 6G networks, (4) Optimized secure routing in 6G networks, (5) 6G Physical Layer security and (Tera-Hertz) THz spectrum, (6) 6G security in Quantum computing and (7) Blockchain-based distributed security in 6G.
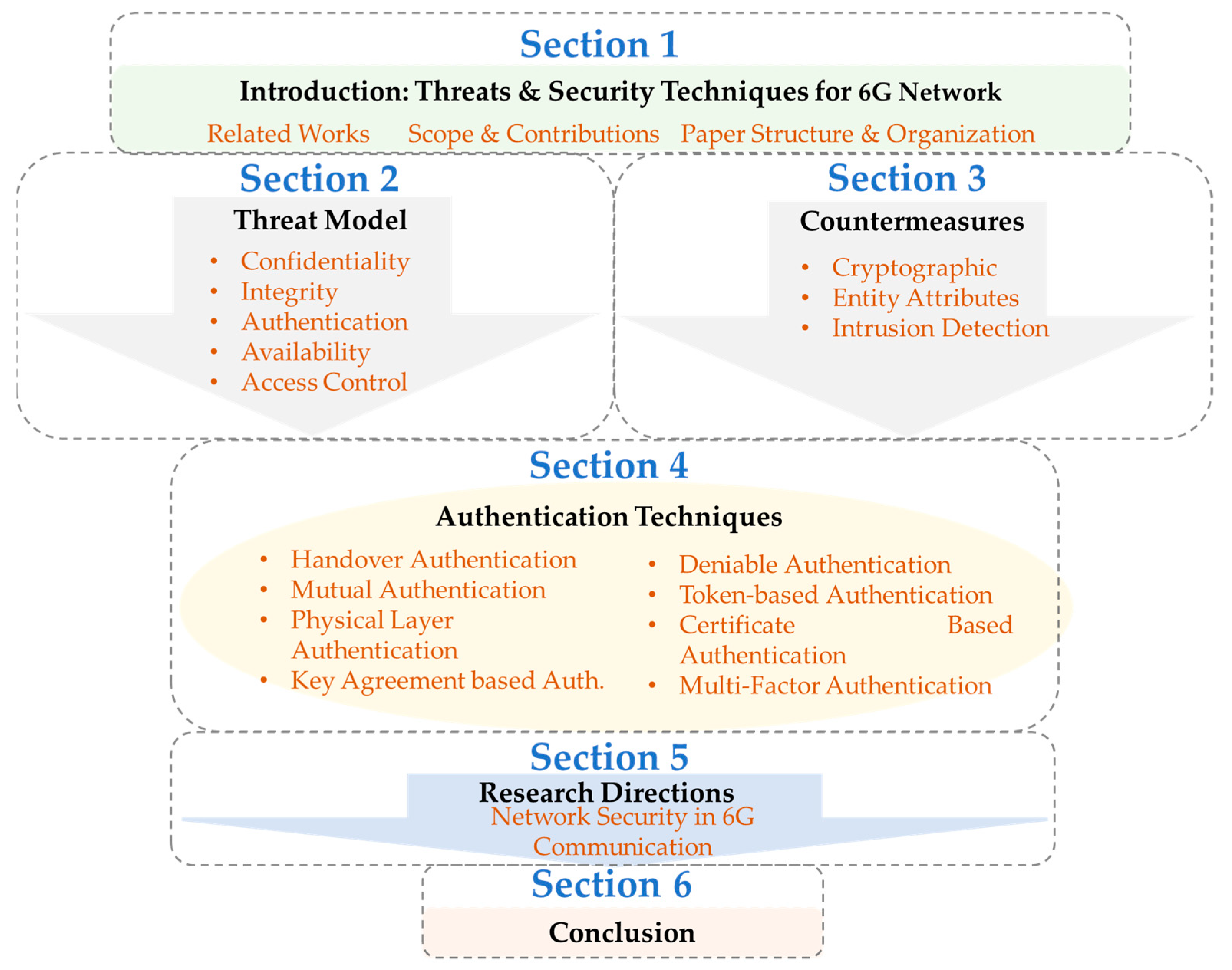
1.3. Paper Structure and Organization
2. Taxonomy for the Threat Model
2.1. Threats against Confidentiality
2.2. Threats against Integrity
2.3. Threats against Availability
2.4. Threats against Authentication
2.5. Threat against Access Control
3. Countermeasures
3.1. Cryptographic-Based Countermeasures
3.2. Entity Attributes-Based Countermeasures
3.3. Intrusion Detection-Based Countermeasures
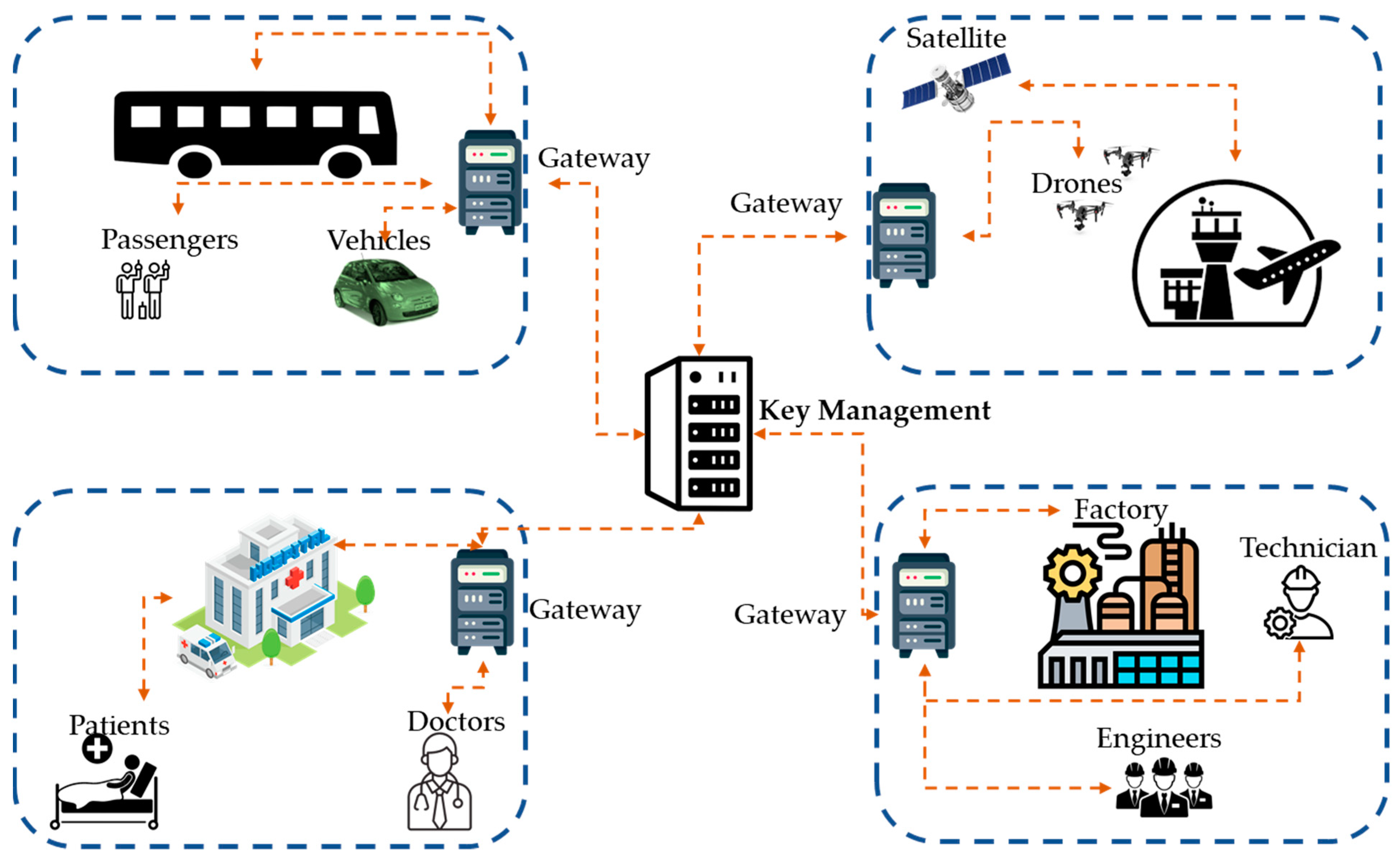
4. Authentication Techniques in 6G Communication
4.1. Handover Authentication
4.2. Mutual Authentication
4.3. Physical Layer Authentication
4.4. Deniable Authentication
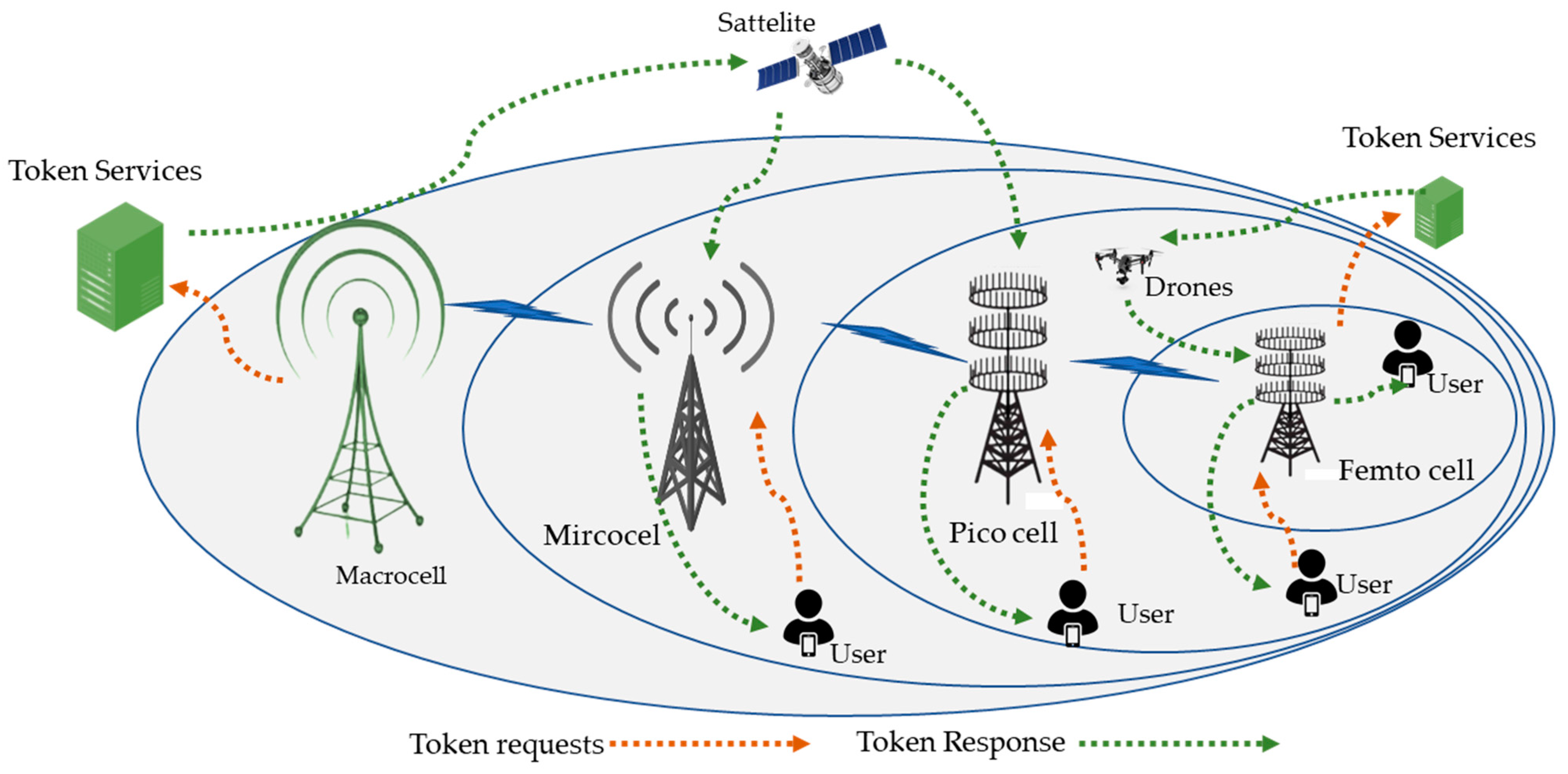
4.5. Token-Based Authentication
4.6. Certificate-Based Authentication
4.7. Key Agreement with Privacy
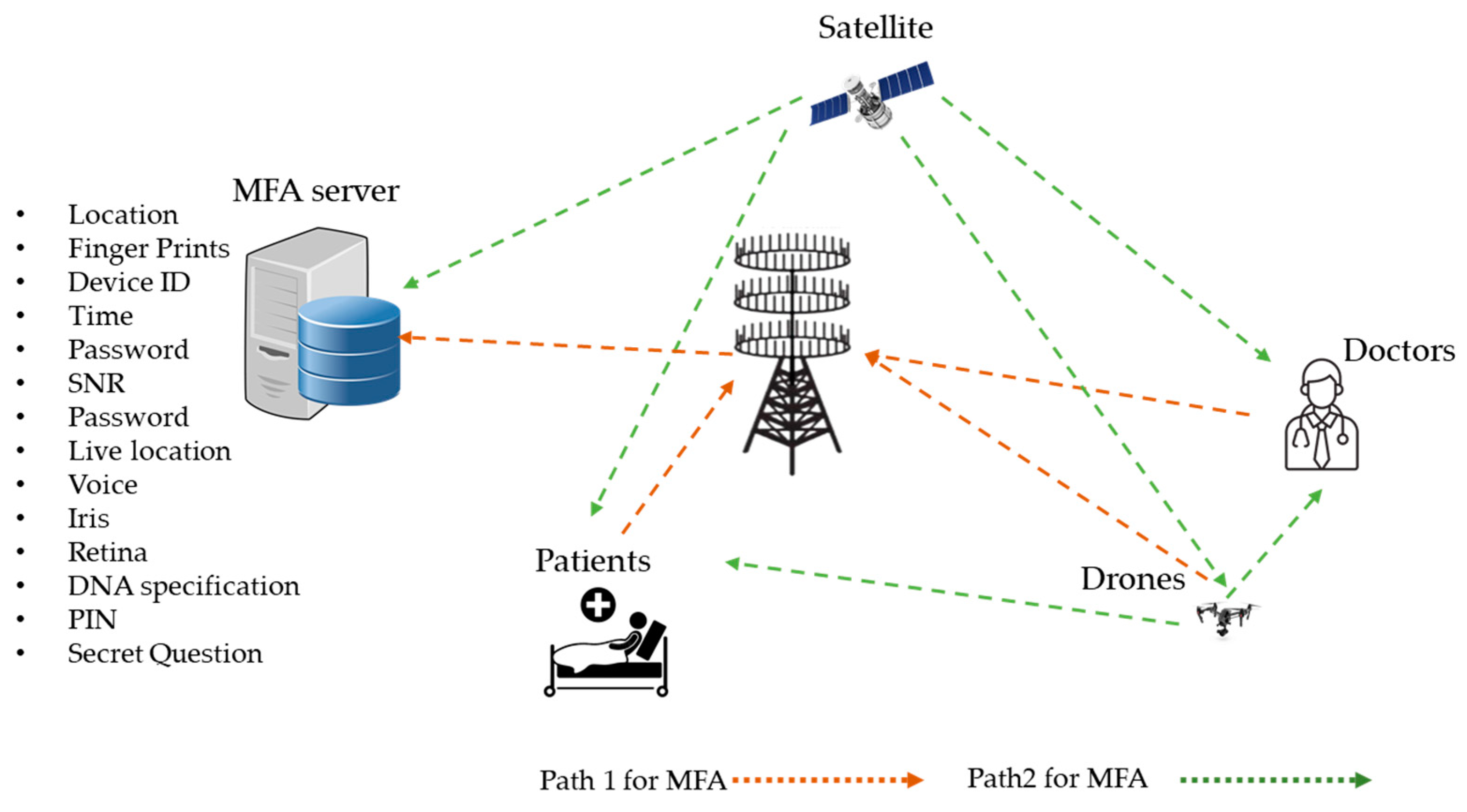
4.8. Multi-Factor Authentication
5. Research Directions
5.1. Privacy Preservation in 6G Network-Based 3D Fog Computing
5.2. 6G-Enabled Privacy-Protected Smart Infrastructures and Augmented Reality
5.3. SDN-Based Secure Architecture in 6G Network
5.4. Optimized Secure Routing in 6G Networks
5.5. 6G Physical Layer Security and THz Spectrum
5.6. 6G Security in Quantum Computing
5.7. Blockchain-Based Distributed Security in 6G
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Hassan, R.; Qamar, F.; Hasan, M.K.; Aman, A.H.M.; Ahmed, A.S. Internet of Things and its applications: A comprehensive survey. Symmetry 2020, 12, 1674. [Google Scholar] [CrossRef]
- Snehi, J.; Snehi, M.; Prasad, D.; Simaiya, S.; Kansal, I.; Baggan, V. SDN-Based Cloud Combining Edge Computing for IoT Infrastructure. In Software Defined Networks: Architecture and Applications; Wiley-Scrivener Publishing: Beverly, MA, USA, 2022; pp. 497–540. [Google Scholar]
- Katz, M.; Matinmikko-Blue, M.; Latva-Aho, M. 6Genesis flagship program: Building the bridges towards 6G-enabled wireless smart society and ecosystem. In Proceedings of the 2018 IEEE 10th Latin-American Conference on Communications (LATINCOM), Guadalajara, Mexico, 14–16 November 2018; pp. 1–9. [Google Scholar]
- Uusitalo, M.A.; Ericson, M.; Richerzhagen, B.; Soykan, E.U.; Rugeland, P.; Fettweis, G.; Sabella, D.; Wikström, G.; Boldi, M.; Hamon, M.-H. Hexa-X the European 6G flagship project. In Proceedings of the 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Porto, Portugal, 8–11 June 2021; pp. 580–585. [Google Scholar]
- Strinati, E.C.; Alexandropoulos, G.C.; Sciancalepore, V.; Di Renzo, M.; Wymeersch, H.; Phan-huy, D.-T.; Crozzoli, M.; D’Errico, R.; De Carvalho, E.; Popovski, P. Wireless environment as a service enabled by reconfigurable intelligent surfaces: The RISE-6G perspective. arXiv 2021, arXiv:2104.06265. [Google Scholar]
- Corici, M.; Troudt, E.; Chakraborty, P.; Magedanz, T. An Ultra-Flexible Software Architecture Concept for 6G Core Networks. In Proceedings of the 2021 IEEE 4th 5G World Forum (5GWF), Montreal, QC, Canada, 13–15 October 2021; pp. 400–405. [Google Scholar]
- McBurnett, M.M. Regulatory Audit Summary of South Texas Project, Units 3 and 4 Combined License Application Revision 4—American Society Of Mechanical Engineers Design Specifications and Component Classification; Nuclear Innovation North America (NINA): Bay City, TX, USA, 2011. [Google Scholar]
- Brito, J.M.C.; Mendes, L.L.; Gontijo, J.G.S. Brazil 6G project-an approach to build a national-wise framework for 6G networks. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar]
- Dang, S.; Amin, O.; Shihada, B.; Alouini, M.-S. What should 6G be? Nat. Electron. 2020, 3, 20–29. [Google Scholar] [CrossRef]
- Qamar, F.; Hindia, M.N.; Abbas, T.; Dimyati, K.B.; Amiri, I.S. Investigation of QoS performance evaluation over 5G network for indoor environment at millimeter wave bands. Int. J. Electron. Telecommun. 2019, 65, 95–101. [Google Scholar]
- Nor, A.M.; Fratu, O.; Halunga, S. Quality of Service Based Radio Resources Scheduling for 5G eMBB Use Case. Symmetry 2022, 14, 2193. [Google Scholar] [CrossRef]
- Kazmi, S.H.A.; Masood, A.; Nisar, K. Design and Analysis of Multi Efficiency Motors Based High Endurance Multi Rotor with Central Thrust. In Proceedings of the 2021 IEEE 15th International Conference on Application of Information and Communication Technologies (AICT), Virtual, 13–15 October 2021; pp. 1–4. [Google Scholar]
- Khan, L.U.; Yaqoob, I.; Imran, M.; Han, Z.; Hong, C.S. 6G wireless systems: A vision, architectural elements, and future directions. IEEE Access 2020, 8, 147029–147044. [Google Scholar] [CrossRef]
- Nayak, S.; Patgiri, R. 6g communication: Envisioning the key issues and challenges. arXiv 2020, arXiv:2004.04024. [Google Scholar] [CrossRef]
- Wang, J.; Wang, C.-X.; Huang, J.; Chen, Y. 6G THz Propagation Channel Characteristics and Modeling: Recent Developments and Future Challenges. IEEE Commun. Mag. 2022; in press. [Google Scholar]
- Qamar, F.; Siddiqui, M.U.A.; Hindia, M.N.; Hassan, R.; Nguyen, Q.N. Issues, challenges, and research trends in spectrum management: A comprehensive overview and new vision for designing 6G networks. Electronics 2020, 9, 1416. [Google Scholar] [CrossRef]
- Sheikholeslami, S.M.; Fazel, F.; Abouei, J.; Plataniotis, K.N. Sub-Decimeter VLC 3D Indoor Localization With Handover Probability Analysis. IEEE Access 2021, 9, 122236–122253. [Google Scholar] [CrossRef]
- Je, D.; Jung, J.; Choi, S. Toward 6G Security: Technology Trends, Threats, and Solutions. IEEE Commun. Stand. Mag. 2021, 5, 64–71. [Google Scholar] [CrossRef]
- Shayea, I.; Dushi, P.; Banafaa, M.; Rashid, R.A.; Ali, S.; Sarijari, M.A.; Daradkeh, Y.I.; Mohamad, H. Handover Management for Drones in Future Mobile Networks—A Survey. Sensors 2022, 22, 6424. [Google Scholar] [CrossRef]
- Nguyen, V.-L.; Lin, P.-C.; Cheng, B.-C.; Hwang, R.-H.; Lin, Y.-D. Security and Privacy for 6G: A Survey on Prospective Technologies and Challenges. IEEE Commun. Surv. Tutor. 2021, 23, 2384–2428. [Google Scholar] [CrossRef]
- Wang, M.; Zhu, T.; Zhang, T.; Zhang, J.; Yu, S.; Zhou, W. Security and privacy in 6G networks: New areas and new challenges. Digit. Commun. Netw. 2020, 6, 281–291. [Google Scholar] [CrossRef]
- Sun, Y.; Liu, J.; Wang, J.; Cao, Y.; Kato, N. When machine learning meets privacy in 6G: A survey. IEEE Commun. Surv. Tutor. 2020, 22, 2694–2724. [Google Scholar] [CrossRef]
- Porambage, P.; Gur, G.; Osorio, D.P.M.; Liyanage, M.; Gurtov, A.; Ylianttila, M. The Roadmap to 6G Security and Privacy. IEEE Open J. Commun. Soc. 2021, 2, 1094–1122. [Google Scholar] [CrossRef]
- Porambage, P.; Gür, G.; Osorio, D.P.M.; Liyanage, M.; Ylianttila, M. 6G security challenges and potential solutions. In Proceedings of the European Conference on Networks and Communications (EuCNC), Porto, Portugal, 8–11 June 2021; pp. 1–6. [Google Scholar]
- Sheth, K.; Patel, K.; Shah, H.; Tanwar, S.; Gupta, R.; Kumar, N. A taxonomy of AI techniques for 6G communication networks. Comput. Commun. 2020, 161, 279–303. [Google Scholar] [CrossRef]
- Zhao, Y.; Zhai, W.; Zhao, J.; Zhang, T.; Sun, S.; Niyato, D.; Lam, K.-Y. A comprehensive survey of 6g wireless communications. arXiv 2020, arXiv:2101.03889. [Google Scholar]
- Vaigandla, K.K.; Bolla, S.; Karne, R. A Survey on Future Generation Wireless Communications-6G: Requirements, Technologies, Challenges and Applications. Int. J. Adv. Trends Comput. Sci. Eng. 2021, 10, 3067–3076. [Google Scholar]
- Steingartner, W.; Galinec, D.; Kozina, A. Threat defense: Cyber deception approach and education for resilience in hybrid threats model. Symmetry 2021, 13, 597. [Google Scholar] [CrossRef]
- Farooqui, M.N.I.; Arshad, J.; Khan, M.M. A Layered Approach to Threat Modeling for 5G-Based Systems. Electronics 2022, 11, 1819. [Google Scholar] [CrossRef]
- Novokhrestov, A.; Konev, A.; Shelupanov, A.; Buymov, A. Computer network threat modelling. In Proceedings of the International Scientific Conference on Electronic Devices and Control Systems (EDCS 2019), Tomsk, Russia, 20–22 November 2019; p. 012002. [Google Scholar]
- Rizvi, S.; Pipetti, R.; McIntyre, N.; Todd, J.; Williams, I. Threat model for securing internet of things (IoT) network at device-level. Internet Things 2020, 11, 100240. [Google Scholar] [CrossRef]
- Chorti, A.; Barreto, A.N.; Kopsell, S.; Zoli, M.; Chafii, M.; Sehier, P.; Fettweis, G.; Poor, H.V. Context-aware security for 6G wireless the role of physical layer security. arXiv 2021, arXiv:2101.01536. [Google Scholar] [CrossRef]
- Lin, D.; Peng, T.; Zuo, P.; Wang, W. Deep-Reinforcement-Learning-Based Intelligent Routing Strategy for FANETs. Symmetry 2022, 14, 1787. [Google Scholar] [CrossRef]
- Abdel Hakeem, S.A.; Hussein, H.H.; Kim, H. Security Requirements and Challenges of 6G Technologies and Applications. Sensors 2022, 22, 1969. [Google Scholar] [CrossRef] [PubMed]
- Ahmed, S.; Hossain, M.; Kaiser, M.S.; Noor, M.B.T.; Mahmud, M.; Chakraborty, C. Artificial Intelligence and Machine Learning for Ensuring Security in Smart Cities. In Data-Driven Mining, Learning and Analytics for Secured Smart Cities; Springer: Berlin/Heidelberg, Germany, 2021; pp. 23–47. [Google Scholar]
- Sun, W.; Li, S.; Zhang, Y. Edge caching in blockchain empowered 6G. China Commun. 2021, 18, 1–17. [Google Scholar] [CrossRef]
- Li, G.; Lai, C.; Lu, R.; Zheng, D. SecCDV: A Security Reference Architecture for Cybertwin-driven 6G V2X. IEEE Trans. Veh. Technol. 2021, 71, 4535–4550. [Google Scholar] [CrossRef]
- Elkandoz, M.T.; Alexan, W. Image encryption based on a combination of multiple chaotic maps. Multimed. Tools Appl. 2022, 81, 25497–25518. [Google Scholar] [CrossRef]
- Vinodha, D.; Anita, E.M.; Geetha, D.M. A novel multi functional multi parameter concealed cluster based data aggregation scheme for wireless sensor networks (NMFMP-CDA). Wirel. Netw. 2021, 27, 1111–1128. [Google Scholar] [CrossRef]
- Azari, M.M.; Solanki, S.; Chatzinotas, S.; Bennis, M. THz-Empowered UAVs in 6G: Opportunities, Challenges, and Trade-offs. IEEE Commun. Mag. 2022, 60, 24–30. [Google Scholar] [CrossRef]
- Shen, X.S.; Liu, D.; Huang, C.; Xue, L.; Yin, H.; Zhuang, W.; Sun, R.; Ying, B. Blockchain for Transparent Data Management Toward 6G. Engineering 2021, 8, 74–85. [Google Scholar] [CrossRef]
- Zakaria, M.S.; Ghani, A.T.A.; Yahya, M.S.; Jamali, S.N. Information Technology Risk Management for Water Quality Monitoring IoT Infrastructure: A Case Study at Tasik Chini Unesco Biosphere Reserve. Asia-Pac. J. Inf. Technol. Multimed. 2020, 9, 94–102. [Google Scholar] [CrossRef]
- Ayaz, F.; Sheng, Z.; Tian, D.; Nekovee, M.; Saeed, N. Blockchain-empowered AI for 6G-enabled Internet of Vehicles. Electronics 2022, 11, 3339. [Google Scholar] [CrossRef]
- Hiller, J.; Henze, M.; Serror, M.; Wagner, E.; Richter, J.N.; Wehrle, K. Secure low latency communication for constrained industrial IoT scenarios. In Proceedings of the 2018 IEEE 43rd Conference on Local Computer Networks (LCN), Chicago, IL, USA, 1–4 October 2018; pp. 614–622. [Google Scholar]
- Kumar, K.S.; Radhamani, A.; Sundaresan, S. Proficient approaches for scalability and security in IoT through edge/fog/cloud computing: A survey. Int. J. Data Sci. 2021, 6, 33–44. [Google Scholar] [CrossRef]
- Xiong, L.; Zhong, X.; Xiong, N.N.; Liu, W. QR-3S: A High Payload QR code Secret Sharing System for Industrial Internet of Things in 6G Networks. IEEE Trans. Ind. Inform. 2020, 17, 7213–7222. [Google Scholar] [CrossRef]
- Chen, Y.-H.; Lai, Y.-C.; Zhou, K.-Z. Identifying Hybrid DDoS Attacks in Deterministic Machine-to-Machine Networks on a Per-Deterministic-Flow Basis. Micromachines 2021, 12, 1019. [Google Scholar] [CrossRef]
- Soussi, W.; Christopoulou, M.; Xilouris, G.; Gür, G. Moving Target Defense as a Proactive Defense Element for Beyond 5G. IEEE Commun. Stand. Mag. 2021, 5, 72–79. [Google Scholar] [CrossRef]
- Hasan, M.K.; Habib, A.A.; Shukur, Z.; Ibrahim, F.; Islam, S.; Razzaque, M.A. Review on cyber-physical and cyber-security system in smart grid: Standards, protocols, constraints, and recommendations. J. Netw. Comput. Appl. 2022, 209, 103540. [Google Scholar] [CrossRef]
- Long, Q.; Chen, Y.; Zhang, H.; Lei, X. Software defined 5G and 6G networks: A survey. Mob. Netw. Appl. 2022, 27, 1792–1812. [Google Scholar] [CrossRef]
- Shrestha, R.; Omidkar, A.; Roudi, S.A.; Abbas, R.; Kim, S. Machine-learning-enabled intrusion detection system for cellular connected UAV networks. Electronics 2021, 10, 1549. [Google Scholar] [CrossRef]
- Ma, X.; Zhou, Y.; Wang, L.; Miao, M. Privacy-preserving Byzantine-robust federated learning. Comput. Stand. Interfaces 2022, 80, 103561. [Google Scholar] [CrossRef]
- Lin, J.; Du, M.; Liu, J. Free-riders in federated learning: Attacks and defenses. arXiv 2019, arXiv:1911.12560. [Google Scholar]
- Kantola, R. 6g network needs to support embedded trust. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26–29 August 2019; pp. 1–5. [Google Scholar]
- Hewa, T.; Gür, G.; Kalla, A.; Ylianttila, M.; Bracken, A.; Liyanage, M. The role of blockchain in 6G: Challenges, opportunities and research directions. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar]
- Kumari, A.; Gupta, R.; Tanwar, S. Amalgamation of blockchain and IoT for smart cities underlying 6G communication: A comprehensive review. Comput. Commun. 2021, 172, 102–118. [Google Scholar] [CrossRef]
- Partala, J. Post-quantum Cryptography in 6G. In 6G Mobile Wireless Networks; Springer: Berlin/Heidelberg, Germany, 2021; pp. 431–448. [Google Scholar]
- Gui, G.; Liu, M.; Tang, F.; Kato, N.; Adachi, F. 6G: Opening new horizons for integration of comfort, security, and intelligence. IEEE Wirel. Commun. 2020, 27, 126–132. [Google Scholar] [CrossRef]
- Catak, F.O.; Catak, E.; Kuzlu, M.; Cali, U.; Unal, D. Security Concerns on Machine Learning Solutions for 6G Networks in mmWave Beam Prediction. arXiv 2021, arXiv:2105.03905. [Google Scholar] [CrossRef]
- Jiang, H.; Zhu, X.; Han, J. Instruction-Fetching Attack and Practice in Collision Fault Attack on AES. Symmetry 2022, 14, 2201. [Google Scholar] [CrossRef]
- Al Mousa, A.; Al Qomri, M.; Al Hajri, S.; Zagrouba, R. Utilizing the eSIM for Public Key Cryptography: A Network Security Solution for 6G. In Proceedings of the 2020 2nd International Conference on Computer and Information Sciences (ICCIS), Sakaka, Saudi Arabia, 13–15 October 2020; pp. 1–6. [Google Scholar]
- Yu, Q.; Ren, J.; Zhou, H.; Zhang, W. A cybertwin based network architecture for 6G. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar]
- Yu, Q.; Wang, M.; Zhou, H.; Ni, J.; Chen, J.; Céspedes, S. Guest Editorial Special Issue on Cybertwin-Driven 6G: Architectures, Methods, and Applications. IEEE Internet Things J. 2021, 8, 16191–16194. [Google Scholar] [CrossRef]
- Liu, J.; Yu, Y.; Li, K.; Gao, L. Post-Quantum Secure Ring Signatures for Security and Privacy in the Cybertwin-Driven 6G. IEEE Internet Things J. 2021, 8, 16290–16300. [Google Scholar] [CrossRef]
- Liu, J.K. Ring signature. In Advances in Cyber Security: Principles, Techniques, and Applications; Springer: Berlin/Heidelberg, Germany, 2019; pp. 93–114. [Google Scholar]
- Somsuk, K. The Improvement of Elliptic Curve Factorization Method to Recover RSA’s Prime Factors. Symmetry 2021, 13, 1314. [Google Scholar] [CrossRef]
- Soleymani, S.A.; Goudarzi, S.; Anisi, M.H.; Movahedi, Z.; Jindal, A.; Kama, N. PACMAN: Privacy-Preserving Authentication Scheme for Managing Cybertwin-based 6G Networking. IEEE Trans. Ind. Inform. 2021, 18, 4902–4911. [Google Scholar] [CrossRef]
- Shankar, K.; Taniar, D.; Yang, E.; Yi, O. Secure and Optimal Secret Sharing Scheme for Color Images. Mathematics 2021, 9, 2360. [Google Scholar] [CrossRef]
- Liao, S.; Sun, Y.; Cao, S.; Yang, L. A 23.8Tbps Random Number Generator on a Single GPU. In Proceedings of the 2020 International Conference on Space-Air-Ground Computing (SAGC), Beijing, China, 4–6 December 2020; pp. 33–37. [Google Scholar]
- Suraci, C.; Pizzi, S.; Molinaro, A.; Araniti, G. MEC and D2D as Enabling Technologies for a Secure and Lightweight 6G eHealth System. IEEE Internet Things J. 2021, 9, 11524–11532. [Google Scholar] [CrossRef]
- Tsavos, M.; Sklavos, N.; Alexiou, G.P. Lightweight Security Data Streaming, Based on Reconfigurable Logic, for FPGA Platform. In Proceedings of the 2020 23rd Euromicro Conference on Digital System Design (DSD), Kranj, Slovenia, 26–28 August 2020; pp. 277–280. [Google Scholar]
- Al-Eryani, Y.; Hossain, E. The D-OMA method for massive multiple access in 6G: Performance, security, and challenges. IEEE Veh. Technol. Mag. 2019, 14, 92–99. [Google Scholar] [CrossRef]
- Lee, Y.U. Secure visible light communication technique based on asymmetric data encryption for 6G communication service. Electronics 2020, 9, 1847. [Google Scholar] [CrossRef]
- Mao, B.; Kawamoto, Y.; Kato, N. AI-based joint optimization of QoS and security for 6G energy harvesting Internet of Things. IEEE Internet Things J. 2020, 7, 7032–7042. [Google Scholar] [CrossRef]
- Ulitzsch, V.Q.; Park, S.; Marzougui, S.; Seifert, J.-P. A Post-Quantum Secure Subscription Concealed Identifier for 6G. In Proceedings of the 15th ACM Conference on Security and Privacy in Wireless and Mobile Networks, San Antonio, TX, USA, 16–19 May 2022; pp. 157–168. [Google Scholar]
- Zhang, Z.; Duan, A. An Adaptive Data Traffic Control Scheme with Load Balancing in a Wireless Network. Symmetry 2022, 14, 2164. [Google Scholar] [CrossRef]
- Ong, A.V.; Peradilla, M. An IoT Framework Based on SDN and NFV for Context-Aware Security. In Proceedings of the 2021 Twelfth International Conference on Ubiquitous and Future Networks (ICUFN), Jeju Island, Korea, 17–20 August 2021; pp. 167–172. [Google Scholar]
- Kazmi, S.H.A.; Qamar, F.; Hassan, R.; Nisar, K. Routing-based Interference Mitigation in SDN enabled Beyond 5G Communication Networks: A Comprehensive Survey. IEEE Access 2023, 11, 4023–4041. [Google Scholar] [CrossRef]
- Zhang, X.; Zhao, J.; Xu, C.; Wang, H.; Zhang, Y. Dopiv: Post-quantum secure identity-based data outsourcing with public integrity verification in cloud storage. IEEE Trans. Serv. Comput. 2022, 15, 334–345. [Google Scholar] [CrossRef]
- Al-Mohammed, H.A.; Yaacoub, E. On the use of quantum communications for securing IoT devices in the 6G era. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Virtual, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Qin, P.; Zhu, Y.; Zhao, X.; Feng, X.; Liu, J.; Zhou, Z. Joint 3D-location planning and resource allocation for XAPS-enabled C-NOMA in 6G heterogeneous Internet of Things. IEEE Trans. Veh. Technol. 2021, 70, 10594–10609. [Google Scholar] [CrossRef]
- Muniyandi, R.C.; Qamar, F.; Jasim, A.N. Genetic optimized location aided routing protocol for VANET based on rectangular estimation of position. Appl. Sci. 2020, 10, 5759. [Google Scholar] [CrossRef]
- Zhang, L.; Zhong, W.; Zhang, J.; Lin, Z.; Yang, Z.; Wang, J. mmWave Beam Tracking for V2I Communication Systems Based on Spectrum Environment Awareness. Symmetry 2022, 14, 677. [Google Scholar] [CrossRef]
- Ibrahim, M.; Badrudduza, A.; Hossen, M.; Kundu, M.K.; Ansari, I.S. Enhancing security of TAS/MRC based mixed RF-UOWC system with induced underwater turbulence effect. arXiv 2021, arXiv:2105.09088. [Google Scholar] [CrossRef]
- Siddiqui, M.U.A.; Qamar, F.; Kazmi, S.H.A.; Hassan, R.; Arfeen, A.; Nguyen, Q.N. A Study on Multi-Antenna and Pertinent Technologies with AI/ML Approaches for B5G/6G Networks. Electronics 2023, 12, 189. [Google Scholar] [CrossRef]
- Liu, Z.; Huang, F.; Weng, J.; Cao, K.; Miao, Y.; Guo, J.; Wu, Y. BTMPP: Balancing trust management and privacy preservation for emergency message dissemination in vehicular networks. IEEE Internet Things J. 2020, 8, 5386–5407. [Google Scholar] [CrossRef]
- Khalid, W.; Yu, H.; Do, D.-T.; Kaleem, Z.; Noh, S. RIS-aided physical layer security with full-duplex jamming in underlay D2D networks. IEEE Access 2021, 9, 99667–99679. [Google Scholar] [CrossRef]
- Lanoue, M.; Bollmann, C.A.; Michael, J.B.; Roth, J.; Wijesekera, D. An Attack Vector Taxonomy for Mobile Telephony Security Vulnerabilities. Computer 2021, 54, 76–84. [Google Scholar] [CrossRef]
- Lu, K.; Yang, H. Design of NOMA Sparse Signature Matrix for 6G Integrating Sensing and Communications Networks. In Proceedings of the 2021 IEEE 94th Vehicular Technology Conference (VTC2021-Fall), Norman, OK, USA, 27–30 September 2021; pp. 1–5. [Google Scholar]
- Soni, G.; Chandravanshi, K. Security Scheme to Identify Malicious Maneuver of Flooding Attack for WSN in 6G. In Proceedings of the 2021 8th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 26–27 August 2021; pp. 124–129. [Google Scholar]
- Srinivasan, M.; Skaperas, S.; Chorti, A. On the Use of CSI for the Generation of RF Fingerprints and Secret Keys. arXiv 2021, arXiv:2110.15415. [Google Scholar]
- Tang, F.; Kawamoto, Y.; Kato, N.; Liu, J. Future intelligent and secure vehicular network toward 6G: Machine-learning approaches. Proc. IEEE 2019, 108, 292–307. [Google Scholar] [CrossRef]
- Sagu, A.; Gill, N.S.; Gulia, P.; Chatterjee, J.M.; Priyadarshini, I. A Hybrid Deep Learning Model with Self-Improved Optimization Algorithm for Detection of Security Attacks in IoT Environment. Future Internet 2022, 14, 301. [Google Scholar] [CrossRef]
- Ankita, A.; Rani, S. Machine Learning and Deep Learning for Malware and Ransomware Attacks in 6G Network. In Proceedings of the 2021 Fourth International Conference on Computational Intelligence and Communication Technologies (CCICT), Sonepat, India, 3 July 2021; pp. 39–44. [Google Scholar]
- Rekkas, V.P.; Sotiroudis, S.; Sarigiannidis, P.; Karagiannidis, G.K.; Goudos, S.K. Unsupervised Machine Learning in 6G Networks-State-of-the-art and Future Trends. In Proceedings of the 2021 10th International Conference on Modern Circuits and Systems Technologies (MOCAST), Thessaloniki, Greece, 5–7 July 2021; pp. 1–4. [Google Scholar]
- Abbas, L.; Shoaib, U.; Bashir, A.K. Priority based dynamic spectrum management using Virtual Utility Functions in Cognitive Radio enabled Internet of Things. Comput. Commun. 2022, 196, 239–248. [Google Scholar] [CrossRef]
- Aslam, M.M.; Du, L.; Zhang, X.; Chen, Y.; Ahmed, Z.; Qureshi, B. Sixth Generation (6G) Cognitive Radio Network (CRN) Application, Requirements, Security Issues, and Key Challenges. Wirel. Commun. Mob. Comput. 2021, 2021, 1331428. [Google Scholar] [CrossRef]
- Xu, L.; Zhou, X.; Tao, Y.; Yu, X.; Yu, M.; Khan, F. AF Relaying Secrecy Performance Prediction for 6G Mobile Communication Networks in Industry 5.0. IEEE Trans. Ind. Inform. 2021, 18, 5485–5493. [Google Scholar] [CrossRef]
- Kazmi, S.H.A.; Qamar, F.; Hassan, R.; Nisar, K.; Chowdhry, B.S. Survey on Joint Paradigm of 5G and SDN Emerging Mobile Technologies: Architecture, Security, Challenges and Research Directions. Wirel. Pers. Commun. 2022, in press.
- Shukla, A.; Gupta, R.; Tanwar, S.; Kumar, N.; Rodrigues, J.J. Block-RAS: A P2P resource allocation scheme in 6G environment with public blockchains. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 8–10 December 2020; pp. 1–6. [Google Scholar]
- Lin, H.; Garg, S.; Hu, J.; Kaddoum, G.; Peng, M.; Hossain, M.S. A blockchain-based secure data aggregation strategy using 6g-enabled nib for industrial applications. IEEE Trans. Ind. Inform. 2020, 17, 7204–7212. [Google Scholar] [CrossRef]
- Manogaran, G.; Rawal, B.S.; Saravanan, V.; Kumar, P.M.; Martínez, O.S.; Crespo, R.G.; Montenegro-Marin, C.E.; Krishnamoorthy, S. Blockchain based integrated security measure for reliable service delegation in 6G communication environment. Comput. Commun. 2020, 161, 248–256. [Google Scholar] [CrossRef]
- Wu, J. Security and Intelligent Management for Fog/Edge Computing Resources. In Fog/Edge Computing for Security, Privacy, and Applications; Springer: Berlin/Heidelberg, Germany, 2021; pp. 213–234. [Google Scholar]
- Khan, L.U.; Saad, W.; Niyato, D.; Han, Z.; Hong, C.S. Digital-Twin-Enabled 6G: Vision, Architectural Trends, and Future Directions. arXiv 2021, arXiv:2102.12169. [Google Scholar] [CrossRef]
- Hindia, M.; Qamar, F.; Majed, M.B.; Abd Rahman, T.; Amiri, I.S. Enabling remote-control for the power sub-stations over LTE-A networks. Telecommun. Syst. 2019, 70, 37–53. [Google Scholar] [CrossRef]
- Yap, K.Y.; Chin, H.H.; Klemeš, J.J. Future outlook on 6G technology for renewable energy sources (RES). Renew. Sustain. Energy Rev. 2022, 167, 112722. [Google Scholar] [CrossRef]
- Ji, S.; Sheng, M.; Zhou, D.; Bai, W.; Cao, Q.; Li, J. Flexible and Distributed Mobility Management for Integrated Terrestrial-Satellite Networks: Challenges, Architectures, and Approaches. IEEE Netw. 2021, 35, 73–81. [Google Scholar] [CrossRef]
- Guo, Y.; Guo, Y. FogHA: An efficient handover authentication for mobile devices in fog computing. Comput. Secur. 2021, 108, 102358. [Google Scholar] [CrossRef]
- Siddiqui, M.U.A.; Qamar, F.; Tayyab, M.; Hindia, M.N.; Nguyen, Q.N.; Hassan, R. Mobility Management Issues and Solutions in 5G-and-Beyond Networks: A Comprehensive Review. Electronics 2022, 11, 1366. [Google Scholar] [CrossRef]
- Abdullah, F.; Kimovski, D.; Prodan, R.; Munir, K. Handover authentication latency reduction using mobile edge computing and mobility patterns. Computing 2021, 103, 2667–2686. [Google Scholar] [CrossRef]
- Khan, M.A.; Kumar, N.; Mohsan, S.A.H.; Khan, W.U.; Nasralla, M.M.; Alsharif, M.H.; Żywiołek, J.; Ullah, I. Swarm of UAVs for network management in 6G: A technical review. arXiv 2022, arXiv:2210.03234. [Google Scholar] [CrossRef]
- Angjo, J.; Shayea, I.; Ergen, M.; Mohamad, H.; Alhammadi, A.; Daradkeh, Y.I. Handover Management of Drones in Future Mobile Networks: 6G Technologies. IEEE Access 2021, 9, 12803–12823. [Google Scholar] [CrossRef]
- Qamar, F.; Siddiqui, M.H.S.; Hindia, M.N.; Dimyati, K.; Abd Rahman, T.; Talip, M.S.A. Propagation Channel Measurement at 38 GHz for 5G mm-wave communication Network. In Proceedings of the 2018 IEEE student conference on research and development (SCOReD), Bangi, Malaysia, 26–28 November 2018; pp. 1–6. [Google Scholar]
- Özkoç, M.F.; Koutsaftis, A.; Kumar, R.; Liu, P.; Panwar, S.S. The Impact of Multi-Connectivity and Handover Constraints on Millimeter Wave and Terahertz Cellular Networks. IEEE J. Sel. Areas Commun. 2021, 39, 1833–1853. [Google Scholar] [CrossRef]
- Chow, M.C.; Ma, M. A lightweight traceable D2D authentication and key agreement scheme in 5G cellular networks. Comput. Electr. Eng. 2021, 95, 107375. [Google Scholar] [CrossRef]
- Bairwa, A.K.; Joshi, S. Mutual authentication of nodes using session token with fingerprint and MAC address validation. Egypt. Inform. J. 2021, 22, 479–491. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Irshad, A.; Khan, M.A.; Khan, S.A.; Nosheen, S.; AlZubi, A.A.; Zikria, Y.B. A Lightweight Authentication Scheme for 6G-IoT Enabled Maritime Transport System. IEEE Trans. Intell. Transp. Syst. 2021, in press.
- Vijayakumar, P.; Azees, M.; Kozlov, S.A.; Rodrigues, J.J. An Anonymous Batch Authentication and Key Exchange Protocols for 6G Enabled VANETs. IEEE Trans. Intell. Transp. Syst. 2021, 23, 1630–1638. [Google Scholar] [CrossRef]
- Yang, L.; Chen, Y.-C.; Wu, T.-Y. Provably Secure Client-Server Key Management Scheme in 5G Networks. Wirel. Commun. Mob. Comput. 2021, 2021, 4083199. [Google Scholar] [CrossRef]
- Hindia, M.N.; Qamar, F.; Abbas, T.; Dimyati, K.; Abu Talip, M.S.; Amiri, I.S. Interference cancelation for high-density fifth-generation relaying network using stochastic geometrical approach. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719855879. [Google Scholar] [CrossRef]
- Paul, L.Y.; Baras, J.S.; Sadler, B.M. Physical-layer authentication. IEEE Trans. Inf. Forensics Secur. 2008, 3, 38–51. [Google Scholar]
- Bahache, A.N.; Chikouche, N.; Mezrag, F. Authentication Schemes for Healthcare Applications Using Wireless Medical Sensor Networks: A Survey. SN Comput. Sci. 2022, 3, 382. [Google Scholar] [CrossRef]
- Fang, H.; Wang, X.; Hanzo, L. Learning-aided physical layer authentication as an intelligent process. IEEE Trans. Commun. 2018, 67, 2260–2273. [Google Scholar] [CrossRef]
- Chen, Y.; Wen, H.; Wu, J.; Song, H.; Xu, A.; Jiang, Y.; Zhang, T.; Wang, Z. Clustering based physical-layer authentication in edge computing systems with asymmetric resources. Sensors 2019, 19, 1926. [Google Scholar] [CrossRef] [PubMed]
- Mucchi, L.; Jayousi, S.; Caputo, S.; Panayirci, E.; Shahabuddin, S.; Bechtold, J.; Morales, I.; Stoica, R.-A.; Abreu, G.; Haas, H. Physical-layer security in 6G networks. IEEE Open J. Commun. Soc. 2021, 2, 1901–1914. [Google Scholar] [CrossRef]
- Shakiba-Herfeh, M.; Chorti, A.; Poor, H.V. Physical layer security: Authentication, integrity, and confidentiality. In Physical Layer Security; Springer: Berlin/Heidelberg, Germany, 2021; pp. 129–150. [Google Scholar]
- Alzubaidi, O.T.H.; Hindia, M.N.; Dimyati, K.; Noordin, K.A.; Wahab, A.N.A.; Qamar, F.; Hassan, R. Interference Challenges and Management in B5G Network Design: A Comprehensive Review. Electronics 2022, 11, 2842. [Google Scholar] [CrossRef]
- Singh, S.P. Physical Layer Design Challenges for 6G Wireless. In 6G Mobile Wireless Networks; Springer: Berlin/Heidelberg, Germany, 2021; pp. 43–52. [Google Scholar]
- Hao, Y.; Miao, Y.; Chen, M.; Gharavi, H.; Leung, V. 6G cognitive information theory: A mailbox perspective. Big Data Cogn. Comput. 2021, 5, 56. [Google Scholar] [CrossRef]
- Lee, D.; Sasaki, H.; Fukumoto, H.; Yagi, Y.; Shimizu, T. An evaluation of orbital angular momentum multiplexing technology. Appl. Sci. 2019, 9, 1729. [Google Scholar] [CrossRef]
- Djordjevic, I.B. OAM-based hybrid free-space optical-terahertz multidimensional coded modulation and physical-layer security. IEEE Photonics J. 2017, 9, 7905812. [Google Scholar] [CrossRef]
- Hu, T.; Zhang, B.; Zhao, K.; Wang, Y.; Zhang, J. Data BER analysis of OAM-assisted physical layer authentication system. IEICE Electron. Express 2022, 19, 20220434. [Google Scholar] [CrossRef]
- Cagliero, A.; Gaffoglio, R. On the spectral efficiency limits of an OAM-based multiplexing scheme. IEEE Antennas Wirel. Propag. Lett. 2016, 16, 900–903. [Google Scholar] [CrossRef]
- Hale, B.; Komlo, C. On End-to-End Encryption. Cryptol. Eprint Arch. 2022, in press.
- Zeng, S.; Mu, Y.; Zhang, H.; He, M. A practical and communication-efficient deniable authentication with source-hiding and its application on Wi-Fi privacy. Inf. Sci. 2020, 516, 331–345. [Google Scholar] [CrossRef]
- Al-Mekhlafi, Z.G.; Hassan, R. Evaluation study on routing information protocol and dynamic source routing in Ad-Hoc network. In Proceedings of the 2011 7th International Conference on Information Technology in Asia, Sarawak, Malaysia, 12–13 July 2011; pp. 1–4. [Google Scholar]
- Abdelhaq, M.; Serhan, S.; Alsaqour, R.; Hassan, R. A local intrusion detection routing security over MANET network. In Proceedings of the 2011 International Conference on Electrical Engineering and Informatics, Bandung, Indonesia, 17–19 July 2011; pp. 1–6. [Google Scholar]
- Gupta, D.S.; Islam, S.H.; Obaidat, M.S.; Hsiao, K.-F. A Novel Identity-based Deniable Authentication Protocol Using Bilinear Pairings for Mobile Ad Hoc Networks. Adhoc Sens. Wirel. Netw. 2020, 47, 227–247. [Google Scholar]
- Li, F.; Hong, J.; Omala, A.A. Practical deniable authentication for pervasive computing environments. Wirel. Netw. 2018, 24, 139–149. [Google Scholar] [CrossRef]
- Huang, W.; Liao, Y.; Zhou, S.; Chen, H. An efficient deniable authenticated encryption scheme for privacy protection. IEEE Access 2019, 7, 43453–43461. [Google Scholar] [CrossRef]
- Niewolski, W.; Nowak, T.W.; Sepczuk, M.; Kotulski, Z. Token-Based Authentication Framework for 5G MEC Mobile Networks. Electronics 2021, 10, 1724. [Google Scholar] [CrossRef]
- Ibrahim, M.Z.; Hassan, R. The implementation of internet of things using test bed in the UKMnet environment. Asia-Pac. J. Inf. Technol. Multimed. 2019, 8, 1–17. [Google Scholar] [CrossRef]
- Aman, M.N.; Taneja, S.; Sikdar, B.; Chua, K.C.; Alioto, M. Token-based security for the Internet of Things with dynamic energy-quality tradeoff. IEEE Internet Things J. 2018, 6, 2843–2859. [Google Scholar] [CrossRef]
- Soldani, D. 6G Fundamentals: Vision and Enabling Technologies. J. Telecommun. Digit. Econ. 2021, 9, 58–86. [Google Scholar] [CrossRef]
- Kamruzzaman, M. 6G-Enabled Smart City Networking Model Using Lightweight Security Module. Res. Sq. 2021, in press.
- Sadeq, A.S.; Hassan, R.; Al-rawi, S.S.; Jubair, A.M.; Aman, A.H.M. A qos approach for Internet of Things (Iot) environment using mqtt protocol. In Proceedings of the 2019 International Conference on Cybersecurity (ICoCSec), Negeri Sembilan, Malaysia, 25–26 September 2019; pp. 59–63. [Google Scholar]
- Mukherjee, A.; Mukherjee, P.; De, D.; Dey, N. QoS-aware 6G-enabled ultra low latency edge-assisted Internet of Drone Things for real-time stride analysis. Comput. Electr. Eng. 2021, 95, 107438. [Google Scholar] [CrossRef]
- Balachandran, C.; Ramachandran, G.; Krishnamachari, B. EDISON: A Blockchain-based Secure and Auditable Orchestration Framework for Multi-domain Software Defined Networks. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Rhode Island, Greece, 2–6 November 2020; pp. 144–153. [Google Scholar]
- Munasinghe, G.K.; Murtaza, M. Analyzing Vehicle-to-Everything Communication for Intelligent Transportation System: Journey from IEEE 802.11p to 5G and Finally Towards 6G. In Proceedings of the 2020 5th International Conference on Innovative Technologies in Intelligent Systems and Industrial Applications (CITISIA), Sydney, Australia, 25–27 November 2020; pp. 1–7. [Google Scholar]
- Pothumarti, R.; Jain, K.; Krishnan, P. A lightweight authentication scheme for 5G mobile communications: A dynamic key approach. J. Ambient Intell. Humaniz. Comput. 2021, 12, 1–19. [Google Scholar] [CrossRef]
- Singh, P.; Masud, M.; Hossain, M.S.; Kaur, A. Cross-Domain Secure Data Sharing using Blockchain for Industrial IoT. J. Parallel Distrib. Comput. 2021, 156, 176–184. [Google Scholar] [CrossRef]
- Nyangaresi, V.O.; Ogundoyin, S.O. Certificate Based Authentication Scheme for Smart Homes. In Proceedings of the 2021 3rd Global Power, Energy and Communication Conference (GPECOM), Virtual, 5–8 October 2021; pp. 202–207. [Google Scholar]
- Farooq, S.M.; Hussain, S.; Kiran, S.; Ustun, T.S. Certificate based authentication mechanism for PMU communication networks based on IEC 61850-90-5. Electronics 2018, 7, 370. [Google Scholar] [CrossRef]
- Garzon, S.R.; Yildiz, H.; Küpper, A. Decentralized Identifiers and Self-sovereign Identity in 6G. arXiv 2021, arXiv:2112.09450. [Google Scholar] [CrossRef]
- Chai, H.; Leng, S.; He, J.; Zhang, K.; Cheng, B. CyberChain: Cybertwin Empowered Blockchain for Lightweight and Privacy-preserving Authentication in Internet of Vehicles. IEEE Trans. Veh. Technol. 2021, 71, 4620–4631. [Google Scholar] [CrossRef]
- Wang, W.; Hu, N.; Liu, X. BlockCAM: A blockchain-based cross-domain authentication model. In Proceedings of the 2018 IEEE Third International Conference on Data Science in Cyberspace (DSC), Guangzhou, China, 18–21 June 2018; pp. 896–901. [Google Scholar]
- Zhang, L.; Zhang, Y.; Tang, S.; Luo, H. Privacy protection for e-health systems by means of dynamic authentication and three-factor key agreement. IEEE Trans. Ind. Electron. 2017, 65, 2795–2805. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. Privacy-aware authenticated key agreement scheme for secure smart grid communication. IEEE Trans. Smart Grid 2018, 10, 3953–3962. [Google Scholar] [CrossRef]
- Günlü, O.; Schaefer, R.F. An optimality summary: Secret key agreement with physical unclonable functions. Entropy 2021, 23, 16. [Google Scholar] [CrossRef]
- Hojjati, M.; Shafieinejad, A.; Yanikomeroglu, H. A Blockchain-Based Authentication and Key Agreement (AKA) Protocol for 5G Networks. IEEE Access 2020, 8, 216461–216476. [Google Scholar] [CrossRef]
- Zhang, J.; Wang, Z.; Wang, D.; Zhang, X.; Gupta, B.; Liu, X.; Ma, J. A Secure Decentralized Spatial Crowdsourcing Scheme for 6G-Enabled Network in Box. IEEE Trans. Ind. Inform. 2021, 18, 6160–6170. [Google Scholar] [CrossRef]
- Asim, J.; Khan, A.S.; Saqib, R.M.; Abdullah, J.; Ahmad, Z.; Honey, S.; Afzal, S.; Alqahtani, M.S.; Abbas, M. Blockchain-based Multifactor Authentication for Future 6G Cellular Networks: A Systematic Review. Appl. Sci. 2022, 12, 3551. [Google Scholar] [CrossRef]
- Joshi, S.; Stalin, S.; Shukla, P.K.; Shukla, P.K.; Bhatt, R.; Bhadoria, R.S.; Tiwari, B. Unified Authentication and Access Control for Future Mobile Communication-Based Lightweight IoT Systems Using Blockchain. Wirel. Commun. Mob. Comput. 2021, 2021, 8621230. [Google Scholar] [CrossRef]
- Євcєєв, C.; Пoгaciй, C.; Xвocтeнкo, B. Development of a protocol for a closed mobile internet channel based on post-quantum algorithms. Cucmeмu oбpoбкu iнфopмaцiї 2021, 35–40. [Google Scholar] [CrossRef]
- Gonzalez, A.J.; Grønsund, P.; Dimitriadis, A.; Reshytnik, D. Information Security in a 5G Facility: An Implementation Experience. In Proceedings of the 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Porto, Portugal, 8–11 June 2021; pp. 425–430. [Google Scholar]
- Rahman, M.A.; Hossain, M.S.; Showail, A.J.; Alrajeh, N.A.; Ghoneim, A. AI-Enabled IIoT for Live Smart City Event Monitoring. IEEE Internet Things J. 2021, in press.
- Shin, S.; Kwon, T. A privacy-preserving authentication, authorization, and key agreement scheme for wireless sensor networks in 5G-integrated Internet of Things. IEEE Access 2020, 8, 67555–67571. [Google Scholar] [CrossRef]
- Sen, J.; Haas, Z. Vulnerability assessment of AODV and SAODV routing protocols against network routing attacks and performance comparison. In Proceedings of the 2011 Wireless Advanced, London, UK, 20–22 June 2011. [Google Scholar]
- Zhang, X.; Zhao, J.; Xu, C.; Li, H.; Wang, H.; Zhang, Y. CIPPPA: Conditional identity privacy-preserving public auditing for cloud-based WBANs against malicious auditors. IEEE Trans. Cloud Comput. 2019, 9, 1362–1375. [Google Scholar] [CrossRef]
- Sevilla, J.; Riedel, C.J. Forecasting timelines of quantum computing. arXiv 2020, arXiv:2009.05045. [Google Scholar]
- Shah, K.; Chadotra, S.; Tanwar, S.; Gupta, R.; Kumar, N. Blockchain for IoV in 6G environment: Review solutions and challenges. Clust. Comput. 2022, 25, 1927–1955. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.-N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]



| Year | Project | Scope |
|---|---|---|
| 2019 | 6G Flagship | Formed and finished an academic and industrial consortium aiming at developing key enabling technologies for 6G [3] |
| 2021 | Hexa-X | 6G European flagship initiative of future [4] |
| 2021 | RISE-6G | RISE-6G project aims at investigating innovative solutions [5] |
| 2021 | 6G Sentinel Lighthouse | Targeting improvements to device antennas and front-end modules [6] |
| 2021 | 6G UT (University of Texas) | New sensing methods, wireless-specific machine learning algorithms and networking innovations [7] |
| 2020 | 6G Brazil project | Allowing the construction of a nation-wise view for the future mobile network [8] |
| Ref. | 6G | Auth. | Observations | |
|---|---|---|---|---|
| [20] | √ | 0 | Only specific authentication and privacy-preserving schemes are reviewed. It lacks a review concerning the threat spectrum. | None of the previous surveys cover the CIA3 triad-based Threat Model to analyze authentication and privacy in 6G Security. |
| [21] | √ | 0 | ||
| [22] | √ | 0 | Focus only on ML-based techniques. Moreover, it lacks threat model-based analysis. | |
| [23] | √ | X | Only privacy is covered with a general overview. Aspects related to various attacks and techniques require further review. | |
| [24] | √ | X | ||
| [25] | √ | X | ||
| [26] | √ | X | Limited coverage to the security perspective. | |
| [27] | √ | X | ||
| Ref. | Threat Area | Countermeasure | Attributes | Limitations |
|---|---|---|---|---|
| [41] | Confidentiality | Paillier cryptosystem |
|
|
| [57] | Authentication | RSA |
|
|
| [64] | Authentication | Quantum secure ring signature |
|
|
| [37] | Authentication | Proxy ring signature |
|
|
| [67] | Authentication | Key exchange |
|
|
| [68] | Confidentiality | Lightweight cryptography |
|
|
| [69] | Confidentiality | Random number generation |
|
|
| [70] | Authentication | Lightweight cryptography |
|
|
| [71] | Confidentiality | Stream cipher |
|
|
| [72] | Confidentiality | Distributed encryption |
|
|
| [73] | Confidentiality | Asymmetric encryption |
|
|
| [74] | Confidentiality | AES encryption |
|
|
| [75] | Confidentiality | Post quantum KEM |
|
|
| Ref. | Threat Area | Countermeasure | Attributes | Limitations |
|---|---|---|---|---|
| [32] | Integrity | Context-aware security |
|
|
| [46] | Authentication | QR code |
|
|
| [80] | Authentication | Quantum key distribution |
|
|
| [81] | Authentication | 3D location |
|
|
| [86] | Confidentiality | Conditional Attributes |
|
|
| [87] | Availability | Physical layer attributes |
|
|
| [84] | Confidentiality | Antenna selection |
|
|
| Ref. | Threat Area | Countermeasure | Attributes | Limitations |
|---|---|---|---|---|
| [88] | CIA3 | Simplified threat matrix |
|
|
| [89] | Authentication | Sparse Signatures matrix |
|
|
| [90] | Availability | Routing scheme |
|
|
| [91] | Authentication | CSI |
|
|
| [48] | Confidentiality | Moving target defense |
|
|
| [51] | CIA3 | Machine Learning |
|
|
| [98] | Confidentiality | Neural network-based prediction |
|
|
| [102] | Integrity | Blockchain |
|
|
| [103] | Availability | SDN-enabled fog computing |
|
|
| [104] | Authentication | Digital twin |
|
|
| Ref. | Network Model | Technique | Features | Limitations |
|---|---|---|---|---|
| [107] | Mobility in terrestrial satellites and 6G terrestrial broadband | Clustering and game-based handover decision-based lightweight authentication framework |
|
|
| [37] | Cybertwin edge nodes in vehicles to everything | Proxy ring signature |
|
|
| [108] | Handover in fog computing | Cooperative fog nodes |
|
|
| [110] | Mobile edge computing | Nodes categorization on mobility patterns |
|
|
| [114] | Handover in fading signals | Multi-connectivity architecture |
|
|
| Ref. | Network Model | Technique | Features | Limitations |
|---|---|---|---|---|
| [115] | D2D communication | Randomly HMAC and ECC |
|
|
| [116] | Mobile nodes communication | Fingerprint and MAC address-based mutual authentication |
|
|
| [117] | Maritime transport systems | Lightweight mutual authentication in multi-server architecture |
|
|
| [118] | Batch authentication in 6G vehicular networks | Bilinear pairing technique |
|
|
| [119] | Client–Server Key Management | Bilinear pairings and ECC |
|
|
| Ref. | Network Model | Technique | Features | Limitations |
|---|---|---|---|---|
| [121] | Spread spectrum | Secret modulation |
|
|
| [123] | Channel estimation | ML with kernel least mean square |
|
|
| [124] | CSI | Clustering and lightweight symmetric cipher with channel state information |
|
|
| [129] | 6G transmission with PLS | Mailbox theory, distributed learning and blockchain |
|
|
| Ref. | Network Model | Technique | Features | Limitations |
|---|---|---|---|---|
| [135] | Wi-Fi authentication | Source hiding with projective hash functions |
|
|
| [138] | Mobile Ad Hoc Networks | Bilinear Pairings |
|
|
| [139] | Pervasive computing | Bilinear pairings |
|
|
| [140] | Social Networks | Random oracle model |
|
|
| Ref. | Network Model | Technique | Features | Limitations |
|---|---|---|---|---|
| [141] | MEC | JSON Web Token |
|
|
| [143] | Conventional client-server | On-chip physically unclonable functions |
|
|
| [145] | Geographically distributed networking | Lightweight security module |
|
|
| [147] | Edge level | Gait information aggregation |
|
|
| [148] | SDN | Blockchain |
|
|
| [150] | Narrow-band internet of things | SHA-256 cyclic keys |
|
|
| [151] | Cross-domain secure data sharing | Blockchain with ECC |
|
|
| Ref. | Network Model | Technique | Features | Limitations |
|---|---|---|---|---|
| [152] | Smart Homes | ECC |
|
|
| [153] | Phasor measurement unit | Explicit certificate |
|
|
| [154] | Cross-domain identity management | Self-sovereign Identity |
|
|
| [155] | CyberTwin | Diffused Practical Byzantine Fault Tolerance |
|
|
| [156] | Cross-domain authentication model | Blockchain |
|
|
| Ref. | Network Model | Technique | Features | Limitations |
|---|---|---|---|---|
| [157] | Electronic healthcareLuo MiaoBiometric parameters | Biometric authentication |
|
|
| [158] | Smart Grid | Physically unclonable functions |
|
|
| [160] | Subscriber authentication | Blockchain |
|
|
| [161] | Network In Box | Spatial crowdsourcing |
|
|
| Ref. | Network Model | Technique | Features | Limitations |
|---|---|---|---|---|
| [167] | Wireless Sensors | Elliptic curve cryptography with user anonymity |
|
|
| [163] | Heterogeneous device | Blockchain |
|
|
| [164] | Closed Mobile Internet Channel | McEliece and Niederreiter crypto-code on elliptic codes |
|
|
| [166] | Distributed edge and cloud nodes | AI-processed events |
|
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kazmi, S.H.A.; Hassan, R.; Qamar, F.; Nisar, K.; Ibrahim, A.A.A. Security Concepts in Emerging 6G Communication: Threats, Countermeasures, Authentication Techniques and Research Directions. Symmetry 2023, 15, 1147. https://doi.org/10.3390/sym15061147
Kazmi SHA, Hassan R, Qamar F, Nisar K, Ibrahim AAA. Security Concepts in Emerging 6G Communication: Threats, Countermeasures, Authentication Techniques and Research Directions. Symmetry. 2023; 15(6):1147. https://doi.org/10.3390/sym15061147
Chicago/Turabian StyleKazmi, Syed Hussain Ali, Rosilah Hassan, Faizan Qamar, Kashif Nisar, and Ag Asri Ag Ibrahim. 2023. "Security Concepts in Emerging 6G Communication: Threats, Countermeasures, Authentication Techniques and Research Directions" Symmetry 15, no. 6: 1147. https://doi.org/10.3390/sym15061147








