Robust and Agile System against Fault and Anomaly Traffic in Software Defined Networks
Abstract
:1. Introduction
- We design the RAD system having fast detection and defense against faults and attacks as well as generating reactive flow rules for elephant flows by considering network status.
- We evaluate the RAD system with respect to robustness, agility, and efficiency through experiments with various scenarios by employing each module.
2. Related Work
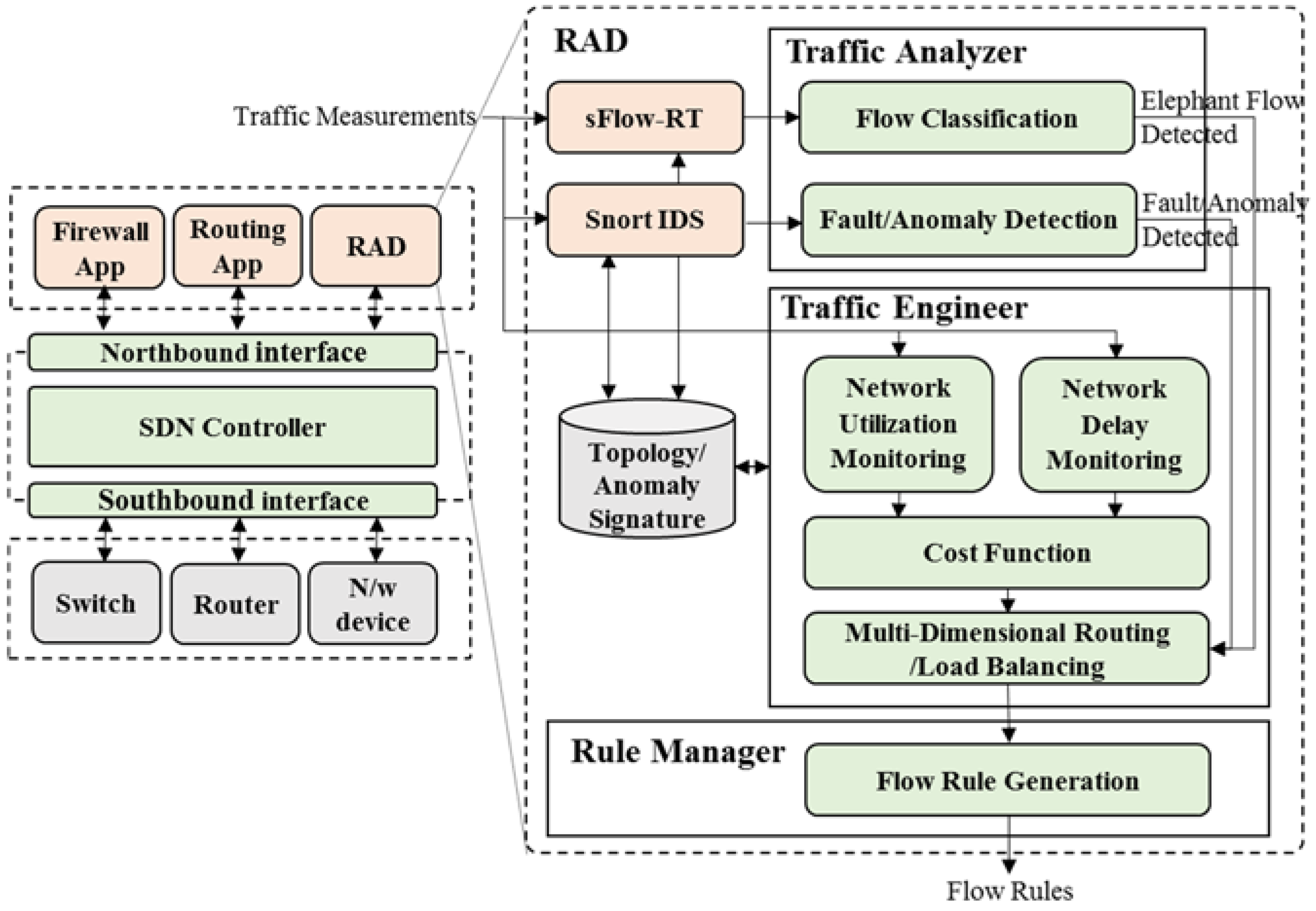
3. RAD System
3.1. Overview of RAD System Architecture
3.2. Main Modules of RAD System
3.2.1. Traffic Analyzer
- (1)
- Snort Rule:// ICMP flooding attack with any IP/port to any IP/port exceeding 10 ICMP messages in 1 salert icmp any any -> any any (msg:“ICMP FLOODING ATTACK DETECTED”; GID:1; sid:10000011; rev:001; itype:8; threshold: type threshold, track by dst, count 10, seconds 1; classtype:icmp-event;)Snort Input:// Mounting ICMP flooding attack by hping3 attack tool (SrcIP 10.0.0.1, DstIP 10.0.0.22)hping3 -1 --flood -a 10.0.0.1 10.0.0.22Snort Output:10/07-13:54:37.429751 [**] [1:10000013:1] ICMP FLOODING ATTACK DETECTED [**] [Classification]: Generic ICMP event] [Priority: 3]{ICMP} 10.0.0.1 -> 10.0.0.22:66530
- (2)
- Snort Rule:// TCP SYN flooding attack with any IP/port to any IP/port exceeding 100 SYN messages in 1 salert tcp any any -> any any (msg:“DDOS ATTACK Detected (TCP SYN Flooding)”; flags:S; threshold: type threshold, track by_dst, count 100, seconds 1; sid: 10000003; rev:1;)Snort Input:// Mounting TCP SYN flooding attack by hping3 attack tool (SrcIP 10.0.0.1, DstIP 10.0.0.22, interval 100 µs)Source 10.0.0.1 >> hping3 -i u100 -S 10.0.0.22Snort Output:10/07-14:15:37.839869 [**] [1:50000008:0] DDOS ATTACK Detected (TCP SYN Flooding) [**] [Priority: 0] {TCP} 10.0.0.1 -> 10.0.0.22:3334
3.2.2. Traffic Engineer
3.2.3. Rule Manager
- (1)
- Switch Rule:// This is a general routing rule on switch S5 for host H1(10.0.0.1), which sends traffic to H5(10.0.0.5). The ‘actions’: output:1 represents H1 uses port 1 to send traffic to H5. The similar rules are pushed on other switches in the generated paths (Refer to network topology in Figure 2).{‘ipv4_src’: ’10.0.0.1’, ‘cookie’: ’0’, ‘actions’: output: 1, ‘active’: ‘true’, ‘eth_src’: ‘3a:e4:de:ed:02:ac’, ‘ipv4_dst’: ’10.0.0.5’, ‘eth_dst’: ’72:f1:22:9a:95:91’, ‘name’: ‘flow1’, ‘priority’: ‘0’, ‘switch’:’00:00:00:00:00:00:00:05’, ‘eth_type’: ‘0X0800’, ‘in_port’: ‘3’}
- (2)
- Switch Rule:// If a host H1(10.0.0.1) connected to switch S5 is identified as an agent to attack a host H22(10.0.0.22), the following rule is pushed into switch S5 for dropping the attack traffic.{‘ipv4_src’: ’10.0.0.1’, ‘cookie’: ’0’, ‘actions’: ’drop’, ‘active’: ‘true’, ‘eth_src’: ‘3a:e4:de:ed:02:ac’, ‘ipv4_dst’: ’10.0.0.22’, ‘eth_dst’: ’72:f1:22:9a:95:91’, ‘name’: ‘flow1’, ‘priority’: ‘0’, ‘switch’: ’00:00:00:00:00:00:00:05’, ‘eth_type’: ‘0X0800’, ‘in_port’: ‘3’}
4. Performance Evaluation
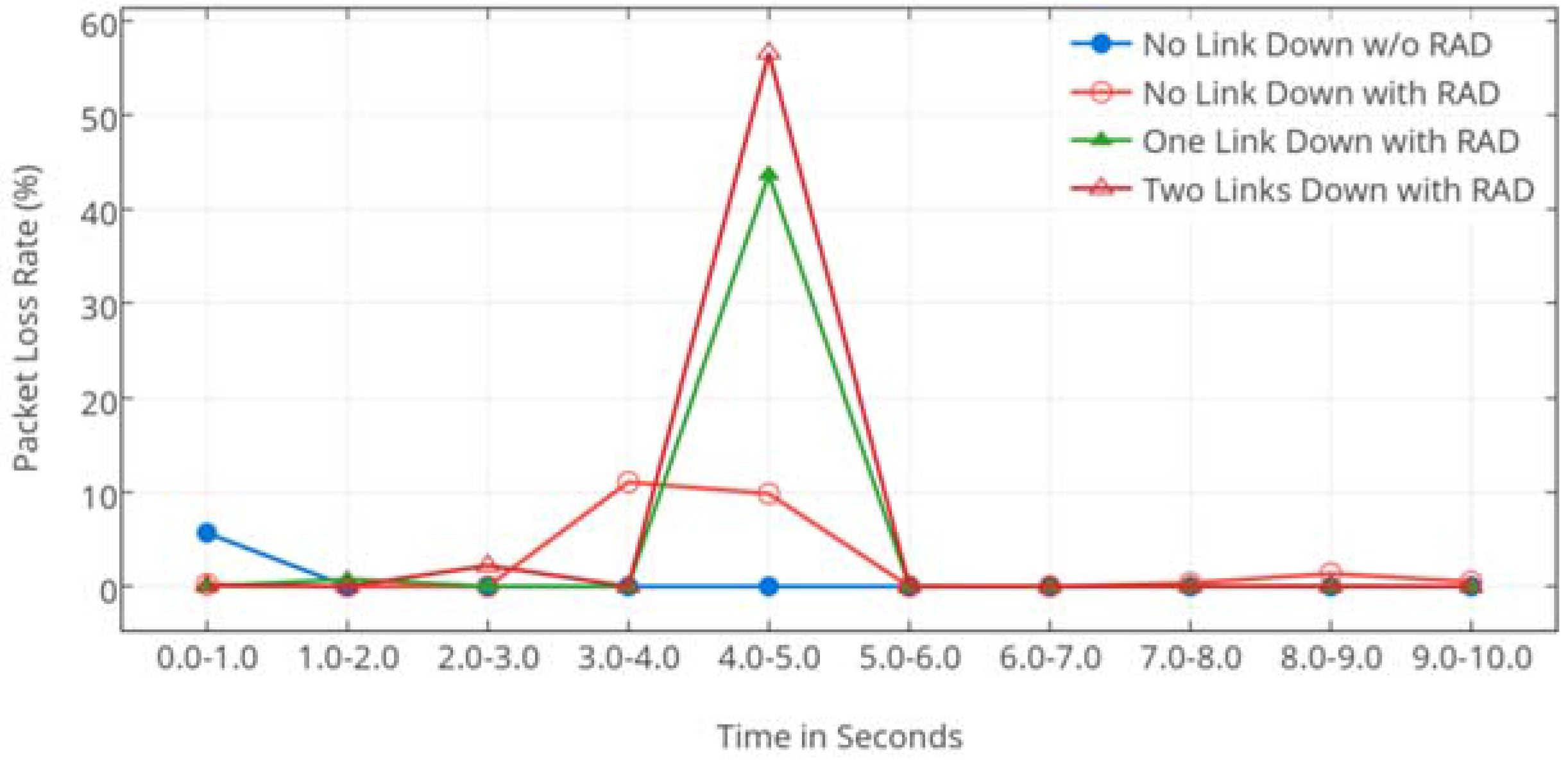
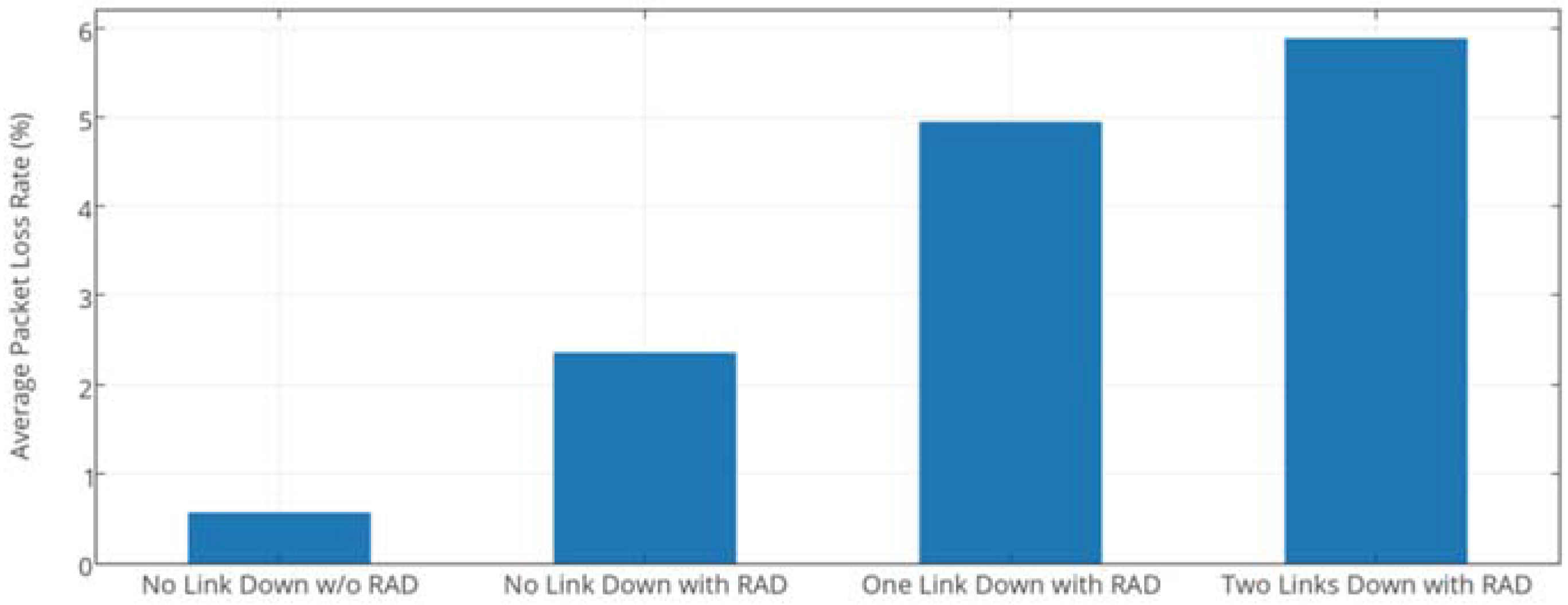
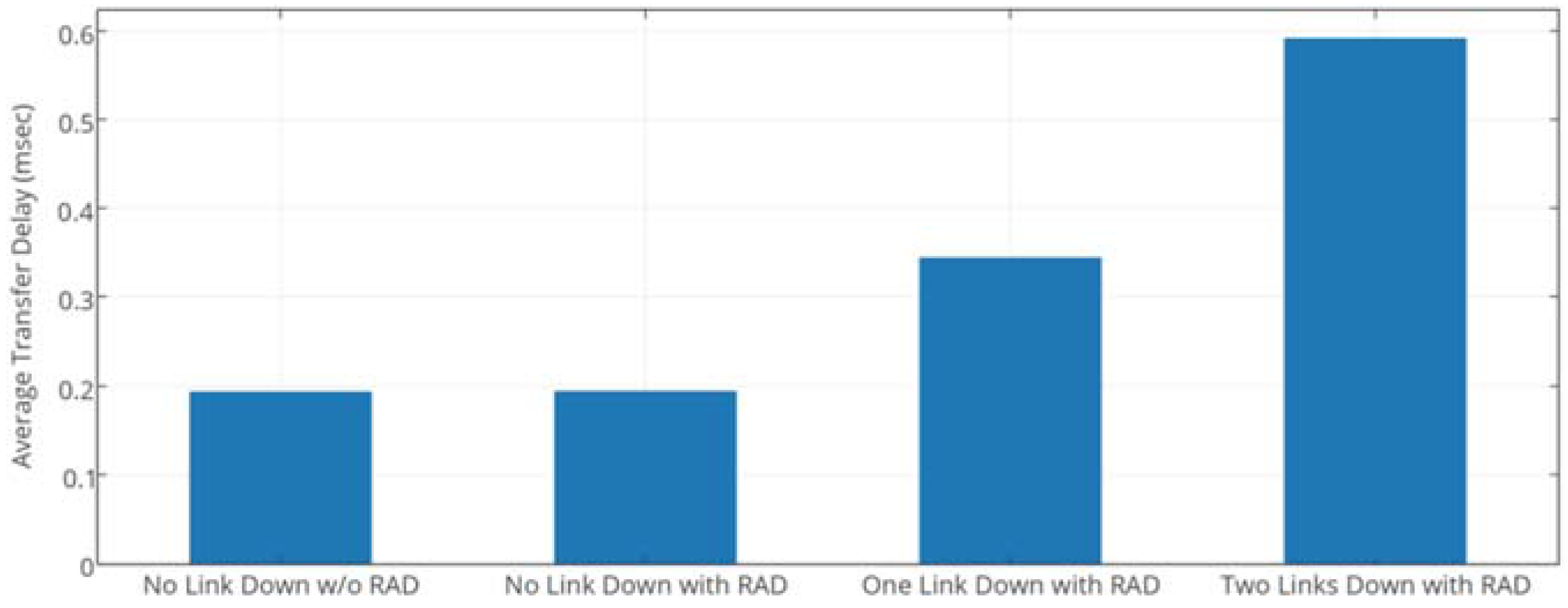
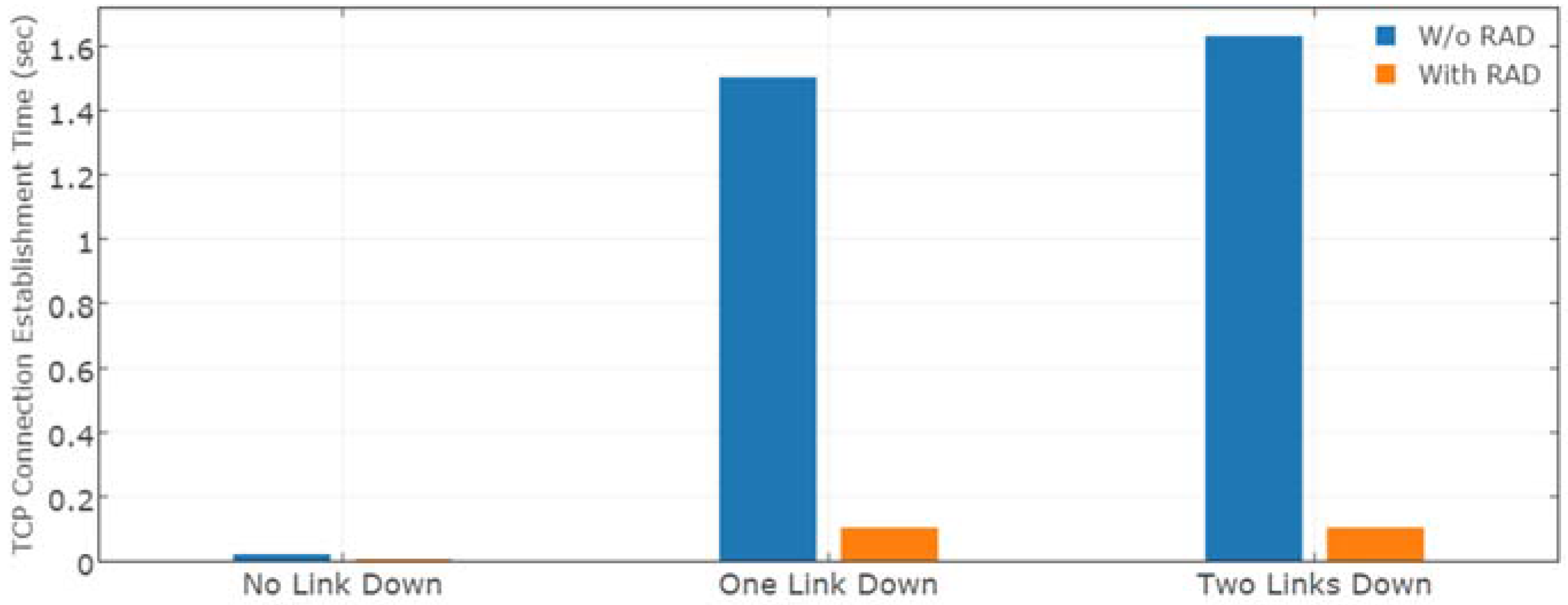
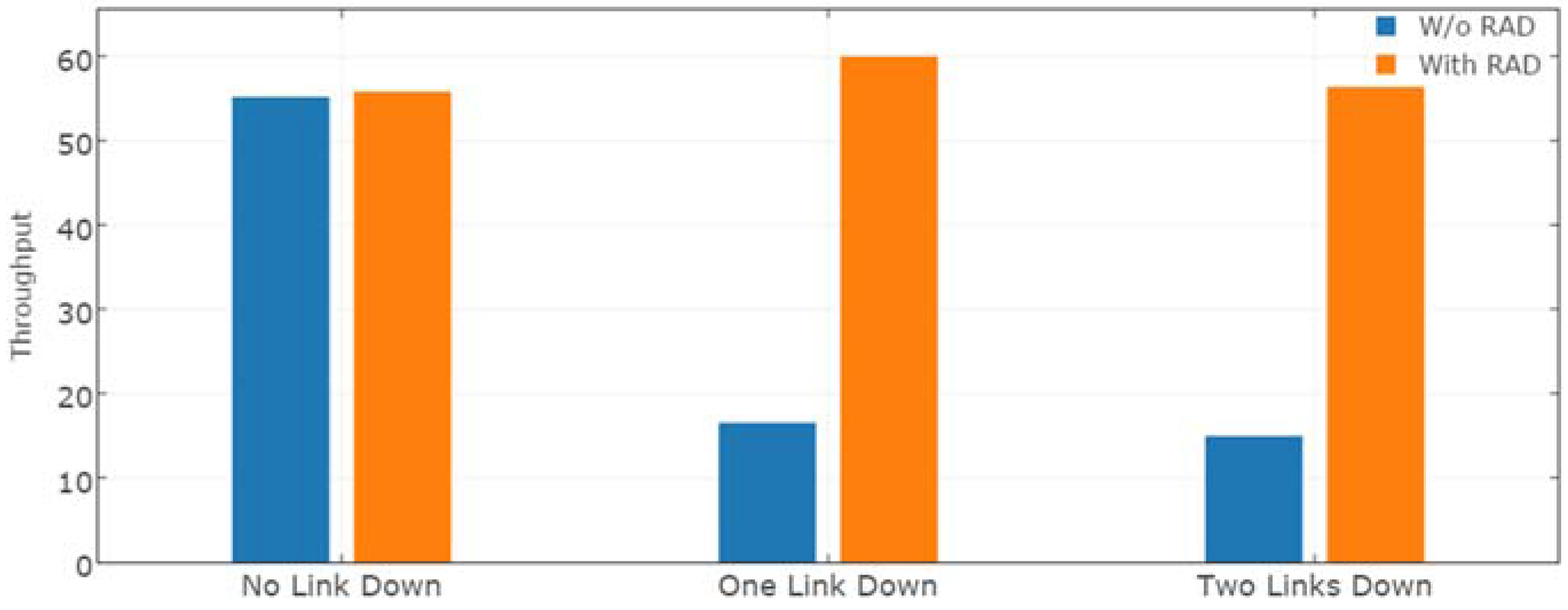
4.1. Effect on Faults
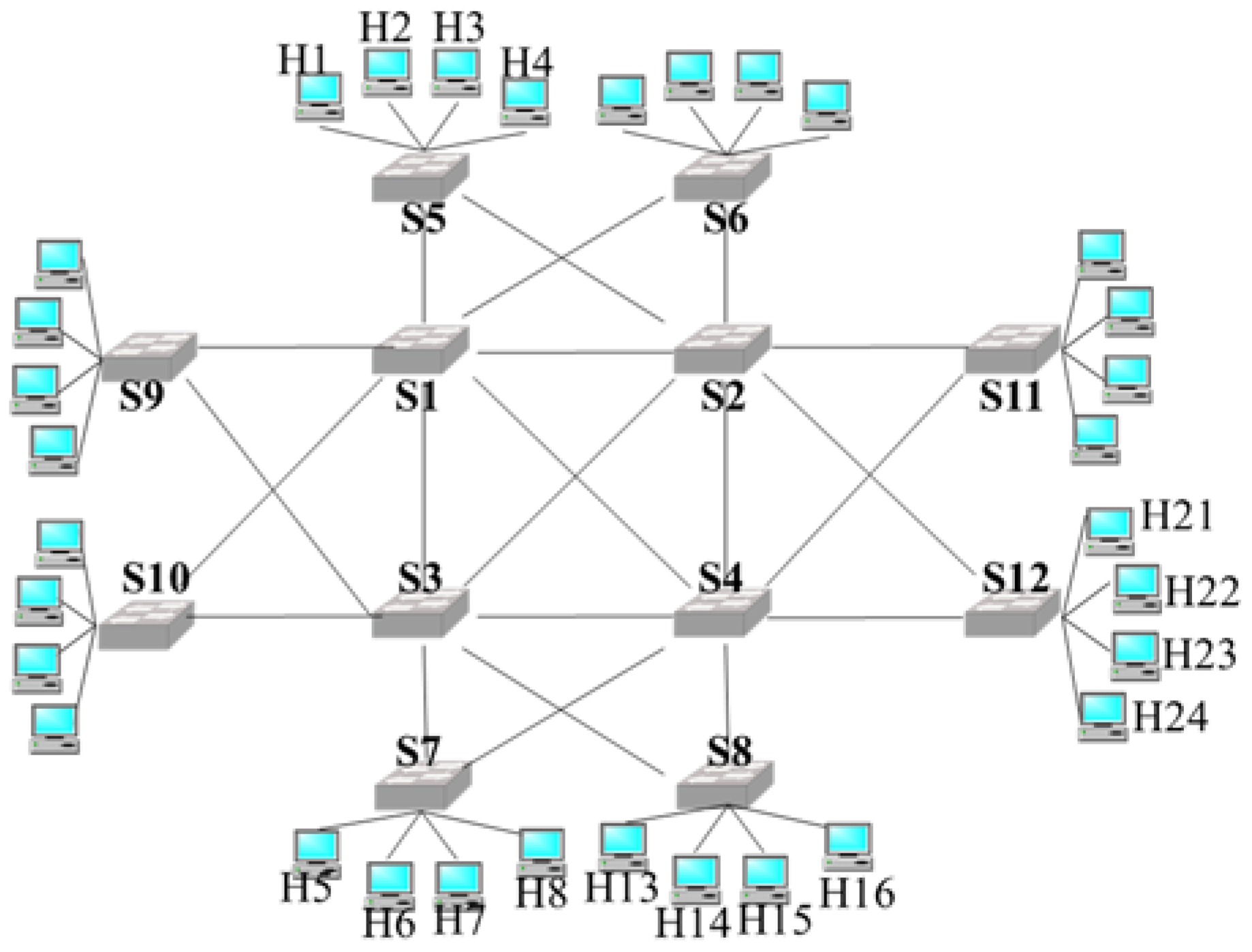
4.1.1. Experimental Setup
- Robustness: Packet Loss Rate (%)
- Agility: Transfer Delay (UDP), Connection Establishment Time (TCP)
- Efficiency: Throughput
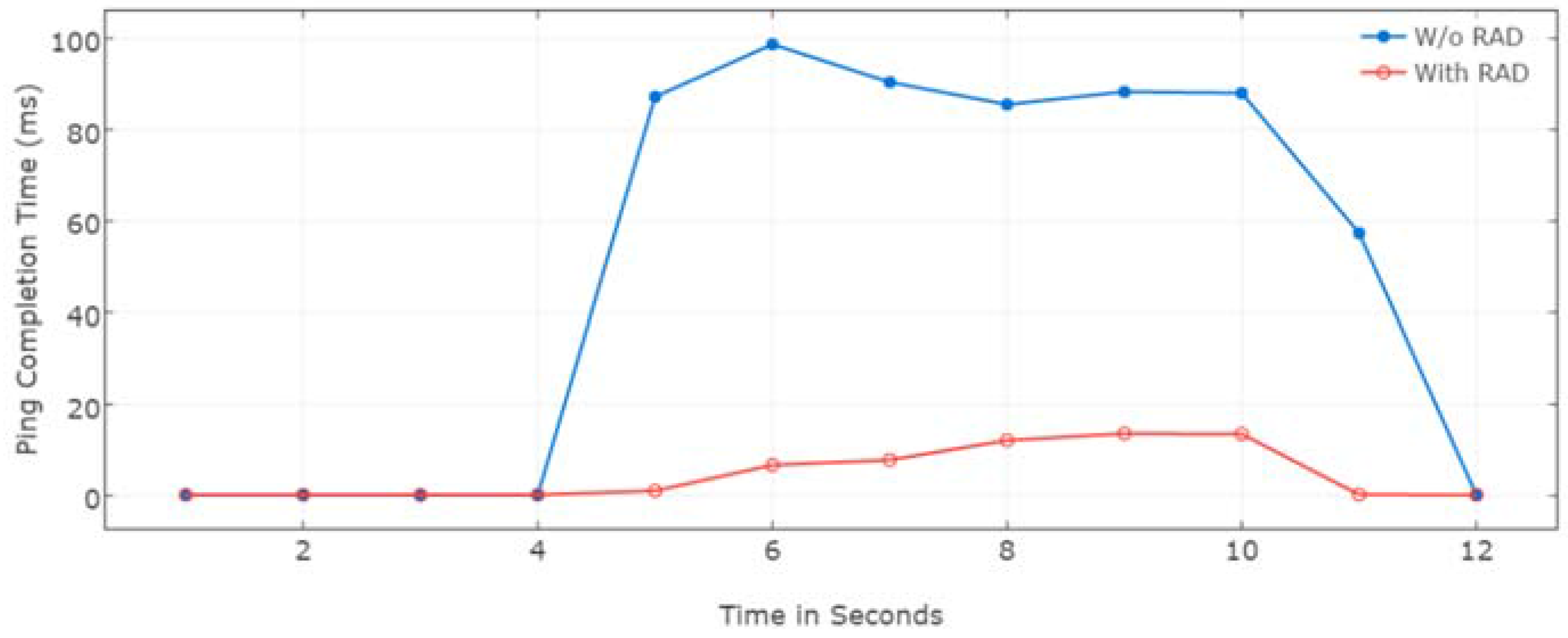
4.1.2. Results Analysis
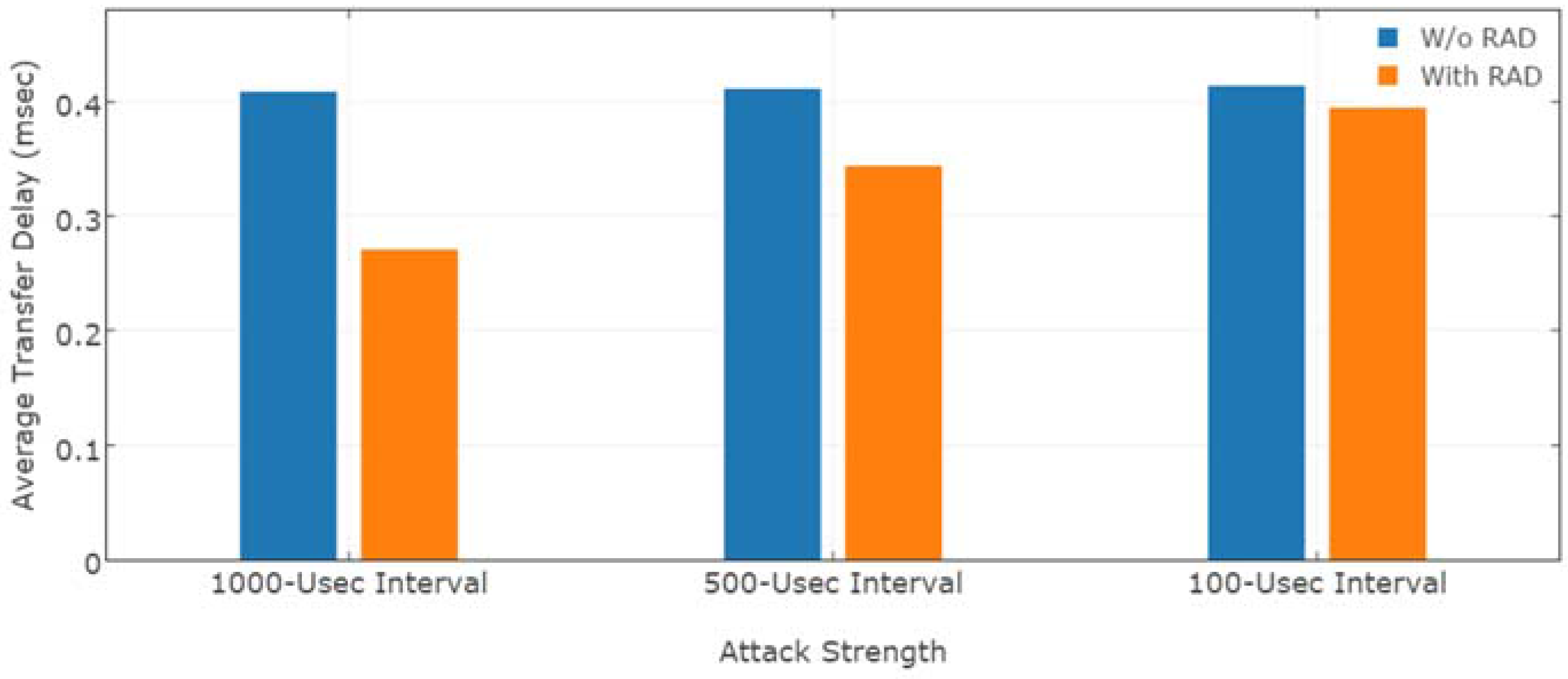
4.2. Effect on Attacks
4.2.1. Experimental Setup
4.2.2. Results Analysis
4.3. Effect on Elephant Flow
4.3.1. Experimental Setup
4.3.2. Results Analysis
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Ahmad, I.; Namal, S.; Ylianttila, M.; Gurtov, A. Security in Software Defined Networks: A Survey. Commun. Surv. Tutor. 2015, 17, 2317–2346. [Google Scholar] [CrossRef]
- Delivering High Availability in Carrier Grade NFV Infrastructures. In VMware Technical White Paper; VMware, Inc.: Palo Alto, CA, USA, 2016.
- Wang, R.; Butnariu, D.; Rexford, J. OpenFlow-based server load balancing gone wild. In Proceedings of the USENIX Conference on Hot Topics in Management of Internet, Cloud, and Enterprise Networks and Services (Hot-ICE), Boston, MA, USA, 29 March 2011; p. 12.
- Carlos, A.B.M.; Rothenberg, C.E.; Maurício, F.M. In-packet Bloom filter based data center networking with distributed OpenFlow controllers. In Proceedings of the 2010 IEEE GLOBECOM Workshops (GC Wkshps), Miami, FL, USA, 6–10 December 2010; pp. 584–588.
- Handigol, N.; Seetharaman, S.; Flajslik, M.; McKeown, N.; Johari, R. Plug-n-Serve: Load-balancing web traffic using OpenFlow. In Proceedings of the ACM Sigcomm Demo, Barcelona, Spain, 17–21 August 2009.
- Wang, Y.; Zhang, Y.; Chen, J. SDNPS: A Load-Balanced Topic-Based Publish/Subscribe System in Software-Defined Networking. Appl. Sci. 2016, 6, 91. [Google Scholar] [CrossRef]
- Nguyen, X.-N.; Saucez, D.; Barakat, C.; Turletti, T. Optimizing rules placement in OpenFlow networks: trading routing for better efficiency. In Proceedings of the 3rd Workshop on Hot Topics in Software Defined Networking (HotSDN), Chicago, IL, USA, 22 August 2014; pp. 127–132.
- Nguyen, X.-N.; Saucez, D.; Barakat, C.; Turletti, T. Rules Placement Problem in OpenFlow Networks: A Survey. IEEE Commun. Surv. Tutor. 2016, 18, 1273–1286. [Google Scholar] [CrossRef]
- Zarek, A.; Ganjali, Y.; Lie, D. OpenFlow Timeouts Demystified. Master’s Thesis, Department of Computer Science, University of Toronto, Toronto, ON, Canada, 2014. [Google Scholar]
- Kim, E.-D.; Lee, S.-I.; Choi, Y.; Shin, M.-K.; Kim, H.-J. A flow entry management scheme for reducing controller overhead. In Proceedings of the 2014 16th International Conference on Advanced Communication Technology (ICACT), Pyeong Chang, Korea, 16–19 February 2014; pp. 754–757.
- Curtis, A.R.; Mogul, J.C.; Tourrilhes, J.; Yalagandula, P.; Sharma, P.; Banerjee, S. DevoFlow: Scaling flow management for high-performance networks. SIGCOMM Comput. Commun. Rev. 2011, 41, 254–265. [Google Scholar] [CrossRef]
- Chiba, Y.; Shinohara, Y.; Shimonishi, H. Source flow: Handling millions of flows on flow-based nodes. In Proceedings of the ACM SIGCOMM Conference, New Delhi, India, 30 August–3 September 2010; pp. 465–466.
- Nguyen, X.N.; Saucez, D.; Barakat, C.; Turletti, T. OFFICER: A general optimization framework for OpenFlow rule allocation and endpoint policy enforcement. In Proceedings of the IEEE INFOCOM, Hong Kong, China, 26 April–1 May 2015; pp. 478–486.
- Li, H.; Li, P.; Guo, S. Morule. Optimized rule placement for mobile users in SDN-enabled access networks. In Proceedings of the IEEE GLOBECOM, Austin, TX, USA, 8–12 December 2014; pp. 4953–4958.
- Benson, T.; Anand, A.; Akella, A.; Zhang, M. MicroTE: Fine grained traffic engineering for data centers. In Proceedings of the 7th Conference Emerging Network Experiments and Technologies (CoNEXT), Tokyo, Japan, 6–9 December 2011; pp. 1–12.
- Ishimori, A.; Farias, F.; Cerqueira, E.; Abelem, A. Control of multiple packet schedulers for improving QoS on OpenFlow/SDN networking. In Proceedings of the 2nd European Workshop on Software Defined Networks, The Hague, The Netherlands, 10–11 October 2013; pp. 81–86.
- Zeng, H.; Zhang, S.; Ye, F.; Jeyakumar, V.; Ju, M.; Liu, J.; McKeown, N.; Vahdat, A. Libra: Divide and conquer to verify forwarding tables in huge networks. In Proceedings of the 11th USENIX Symposium on Networked Systems Design and Implementation (NSDI), Seattle, WA, USA, 2–4 April 2014; pp. 87–99.
- Mehdi, S.A.; Khalid, J.; Khayam, S.A. Revisiting traffic anomaly detection using software defined networking. In Proceedings of the 14th International Conference on Recent Advances in Intrusion Detection (RAID), Menlo Park, CA, USA, 20–21 September 2011; pp. 161–180.
- Yu, Y.; Qian, C.; Li, X. Distributed and collaborative traffic monitoring in software defined networks. In Proceedings of the 3rd Workshop on Hot Topics in Software Defined Networking (HotSDN), Chicago, IL, USA, 22 August 2014; pp. 85–90.
- Suh, J.; Kwon, T.; Dixon, C.; Felter, W.; Carter, J. OpenSample: A low-latency, sampling-based measurement platform for commodity SDN. In Proceedings of the IEEE 34th International Conference on Distributed Computing Systems (ICDCS), Madrid, Spain, 30 June–3 July 2014; pp. 228–237.
- Yu, M.; Jose, L.; Miao, R. Software defined traffic measurement with OpenSketch. In Proceedings of the 10th USENIX Conference on Networked Systems Design and Implementation (NSDI), Lombard, IL, USA, 2–5 April 2013; pp. 29–42.
- Chowdhury, S.R.; Bari, M.F.; Ahmed, R.; Boutaba, R. PayLess: A Low Cost Netowrk Monitoring Framework for Software Defined Networks. In Proceedings of the 14th IEEE/IFIP Network Operations and Management Symposium (NOMS), Krakow, Poland, 5–9 May 2014; pp. 1–9.
- Shin, S.; Song, Y.; Lee, T.; Lee, S.; Chung, J.; Porras, P.; Yegneswaran, V.; Noh, J.; Kang, B.B. Rosemary: A robust, secure, and high-performance network operating system. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security (CCS), Scottsdale, AZ, USA, 3–7 November 2014; pp. 78–89.
- Hong, S.; Xu, L.; Wang, H.; Gu, G. Poisoning network visibility in software-defined networks: New attacks and countermeasures. In Proceedings of the 22nd Annual Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 7 February 2015; pp. 78–89.
- Shin, S.; Yegneswaran, V.; Porras, P.; Gu, G. Avant-guard: Scalable and vigilant switch flow management in software-defined networks. In Proceedings of the 2013 ACM SIGSAC Conference on Computer and Communications Security, Berlin, Germany, 4–8 November 2013; pp. 413–424.
- sFlow-RT. Available online: http://www.inmon.com/products/sFlow-RT.php (accessed on 1 December 2016).
- Snort. Available online: https://en.wikipedia.org/wiki/Snort (accessed on 1 December 2016).
- Kreutz, D.; Ramos, F.M.V.; Veríssimo, P.E.C.; Rothenberg, E.; Azodolmolky, S.; Uhlig, S. Software-Defined Networking: A Comprehensive Survey. Proc. IEEE 2015, 103, 14–76. [Google Scholar] [CrossRef]
- OpenFlow Switch Consortium. Available online: http://archive.openflow.org/ (accessed on 1 December 2016).
- Sundaresan, S.; Donato, W.; Feamster, N.; Teixeira, R.; Crawford, S.; Pescapè, A. Broadband internet performance: A view from the gateway. SIGCOMM Comput. Commun. Rev. 2011, 41, 134–145. [Google Scholar] [CrossRef]
- Kim, H.; Feamster, N. Improving network management with software defined networking. IEEE Commun. Mag. 2013, 51, 114–119. [Google Scholar] [CrossRef]
- Kim, J.; Filali, F.; Ko, Y.-B. Trends and Potentials of the Smart Grid Infrastructure: From ICT Sub-System to SDN-Enabled Smart Grid Architecture. Appl. Sci. 2015, 5, 706–727. [Google Scholar] [CrossRef]
- Casado, M.; Garfinkel, T.; Akella, A.; Freedman, M.J.; Boneh, D.; McKeown, N.; Shenker, S. SANE: A protection architecture for enterprise networks. In Proceedings of the 15th conference on USENIX Security Symposium (USENIX-SS), Vancouver, BC, Canada, 31 July–4 August 2006.
- Hand, R.; Ton, M.; Keller, E. Active Security. In Proceedings of the 12th ACM Workshop on Hot Topics in Networks (HotNets-XII), College Park, MD, USA, 21–22 November 2013.
- Porras, P.; Shin, S.; Yegneswaran, V.; Fong, M.; Tyson, M.; Gu, G. A security enforcement kernel for OpenFlow networks. In Proceedings of the First Workshop on Hot Topics in Software Defined Networks (HotSDN), Chicago, IL, USA, 22 August 2014; pp. 121–126.
- Shin, S.; Porras, P.; Yegneswaran, V.; Fong, M.; Gu, G.; Tyson, M. FRESCO: Modular composable security services for software-defined networks. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 24–27 February 2013.
- Porras, P.; Cheung, S.; Fong, M.; Skinner, K.; Yegneswaran, V. Securing the software-defined network control layer. In Proceedings of the 2015 Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 8–11 February 2015.
- Hayward, S.S.; Kane, C.; Sezer, S. Operationcheckpoint: Sdn application control. In Proceedings of the IEEE 22nd International Conference on Network Protocols (ICNP), Research Triangle Park, NC, USA, 21–24 October 2014; pp. 618–623.
- Wen, X.; Chen, Y.; Hu, C.; Shi, C.; Wang, Y. Towards a secure controller platform for openflow applications. In Proceedings of the 2nd ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, Hong Kong, China, 16 August 2013; pp. 171–172.
- InMon. Available online: http://www.inmon.com/ (accessed on 1 December 2016).
- Cheng, W.; Ren, F.; Jiang, W.; Qian, K.; Zhang, T.; Shu, R. Isolating Mice and Elephant in Data Centers. arXiv, 2016; arXiv:1605.07732. [Google Scholar]
- RestFlow. Available online: https://github.com/restflow-org/restflow/wiki (accessed on 1 December 2016).
- Lohier, S.; Rachedi, A.; Doudane, Y.G. A cost function for QoS-aware routing in Multi-tier Wireless Multimedia Sensor Networks. Lect. Notes Comput. Sci. 2009, 5842, 81–93. [Google Scholar]
- Badia, L.; Lindström, M.; Zander, J.; Zorzi, M. An economic model for the radio resource management in multimedia wireless systems. Comput. Commun. 2004, 27, 1056–1064. [Google Scholar] [CrossRef]
- Shaikh, A.; Rexford, J.; Shin, K.G. Evaluating the impact of stale link state on quality-of-service routing. IEEE/ACM Trans. Netw. 2001, 9, 162–176. [Google Scholar] [CrossRef]
- Mininet. Available online: http://mininet.org/ (accessed on 1 December 2016).
- Floodlight. Available online: http://www.projectfloodlight.org/floodlight/ (accessed on 1 December 2016).
- Iperf. Available online: https://iperf.fr/ (accessed on 1 December 2016).
- Hping. Available online: http://www.hping.org/ (accessed on 1 December 2016).
- TCP SYN Flooding and IP Spoofing Attacks. Advisory, Software Engineering Institute, Carnegie-Mellon University, 1996. Available online: https://www.cert.org/historical/advisories/CA-1996–21.cfm (accessed on 1 December 2016).
- Suricata. Available online: https://suricata-ids.org/ (accessed on 18 Febrary 2017).
- NetFlow. Available online: https://en.wikipedia.org/wiki/NetFlow (accessed on 18 Febrary 2017).
- Groš, S. Anomaly Detection in Snort. Available online: http://sgros.blogspot.com/2015/02/anomaly-detection-in-snort.html (accessed on 18 Febrary 2017).
- SNORT.AD. Available online: http://www.anomalydetection.info/?home,1 (accessed on 18 Febrary 2017).
- Ding, Y.X.; Xiao, M.; Liu, A.-W. Research and implementation on snort-based hybrid intrusion detection system. In Proceedings of the International Conference on Machine Learning and Cybernetics, Baoding, China, 12–15 July 2009; pp. 1414–1418.



| Type | Work | Goal |
|---|---|---|
| Traffic Engineering | Load balancing [3,4,5,6] | Network efficiency |
| Rules/traffic optimization [7,8,9,10,11,12,13,14,15] | Efficiency of SDN controller or networks | |
| Application-aware networking [16,17] | QoS guarantee | |
| Measurement and Monitoring | New functionality provided to existing networks [30,31,32] | Efficient management with new features |
| Efficient measurement and monitoring [18,19,20,21,22] | High measurement accuracy and overhead reduction | |
| Security and Dependability | Reinforcement security of other networks [33,34] | Improvement of security with programmability of SDN |
| SDN-specific security [23,24,25,35,36] | Securing against SDN network-specific vulnerabilities | |
| Policy-based approaches [37,38,39] | Access control at SDN controller | |
| Comprehensive Monitoring and Reactive System | Our proposed system, RAD | Agile and robust response against abnormalities (i.e., faults, elephant flows, and attacks) with efficient network performance |
| Tools and Technologies | Name | Version | Description |
|---|---|---|---|
| Simulator | Mininet [46] | 2.2.1 | Create a realistic virtual network, running real kernel, switch, and application code on a single machine (VM, cloud, or native). |
| SDN Controller | FloodLight [47] | 1.2 | An Open SDN Controller offered by Big Switch Networks that works with the OpenFlow protocol to orchestrate traffic flows in an SDN environment. |
| IDS | Snort [27] | 2.9.8 | The most popular network intrusion detection system. |
| Traffic Generator | Iperf [48] | 2.0 | A popular network tool that was developed to measure TCP and UDP bandwidth performance. By tuning various parameters and characteristics of the TCP/ UDP protocol, the user can perform several tests that provide an insight on the network’s bandwidth availability, delay, jitter, and data loss. |
| Attack Tool | Hping [49] | 3.0 | A network tool that can send custom TCP/IP packets and display target replies as a ping program does with ICMP replies. Hping3 handles fragmentation as well as, arbitrary packets body and size, and can be used to transfer files encapsulated under supported protocols. It can thus be used as an attack tool. |
| Development tools | Python | 2.0/3.0 | Python scripting language is used to develop the script for load balancing, routing, and preventing an attack. |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, M.; Park, Y.; Kotalwar, R. Robust and Agile System against Fault and Anomaly Traffic in Software Defined Networks. Appl. Sci. 2017, 7, 266. https://doi.org/10.3390/app7030266
Kim M, Park Y, Kotalwar R. Robust and Agile System against Fault and Anomaly Traffic in Software Defined Networks. Applied Sciences. 2017; 7(3):266. https://doi.org/10.3390/app7030266
Chicago/Turabian StyleKim, Mihui, Younghee Park, and Rohit Kotalwar. 2017. "Robust and Agile System against Fault and Anomaly Traffic in Software Defined Networks" Applied Sciences 7, no. 3: 266. https://doi.org/10.3390/app7030266






