A Framework for Systematic Refinement of Trustworthiness Requirements
Abstract
:1. Introduction
2. Background and Fundamentals
2.1. Trust and Trustworthiness
2.2. Business Process Modeling Using BPMN
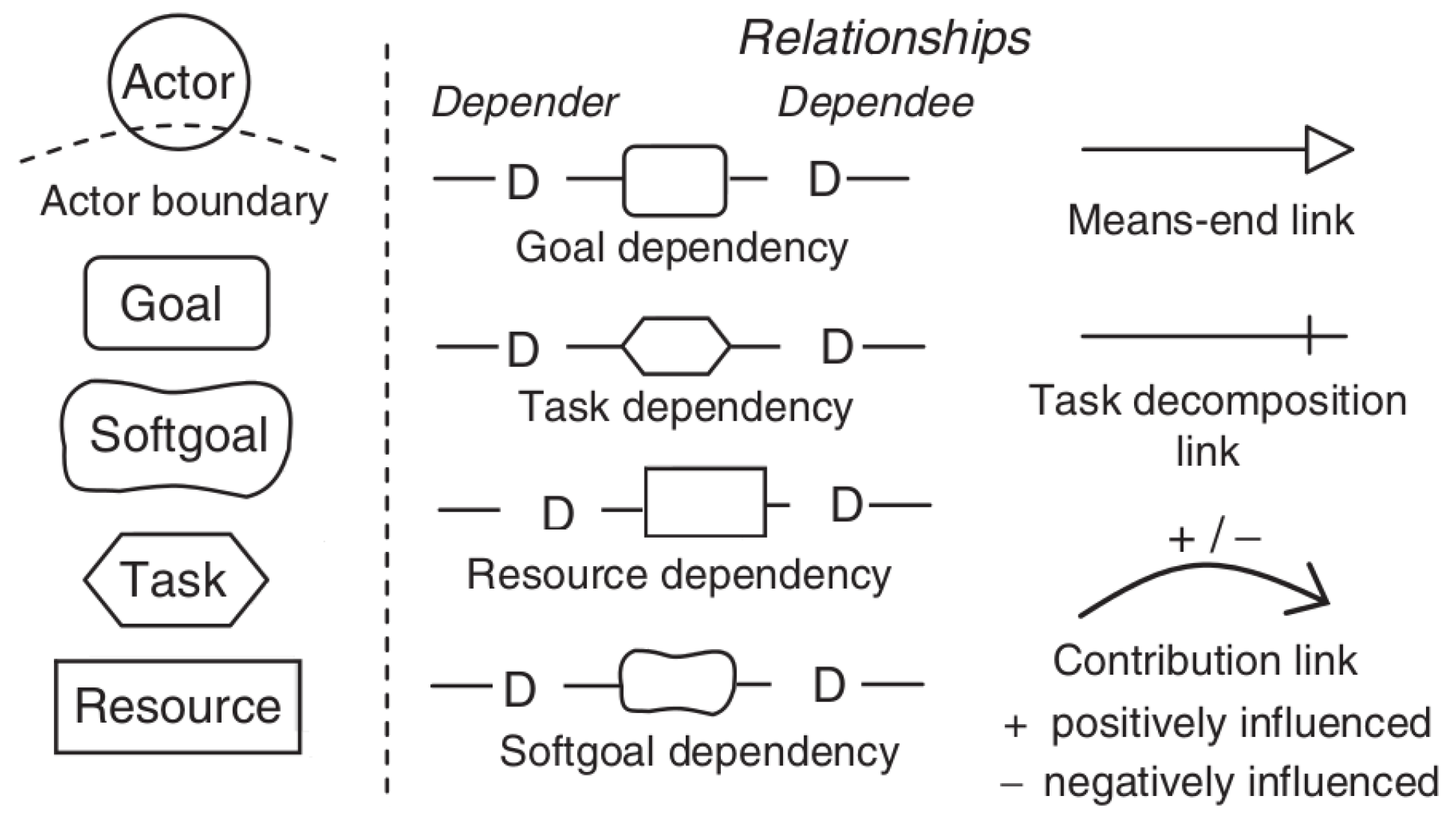
2.3. Goal Modeling Using i*
2.4. Choice of i* and BPMN as Modeling Languages in Our Approach
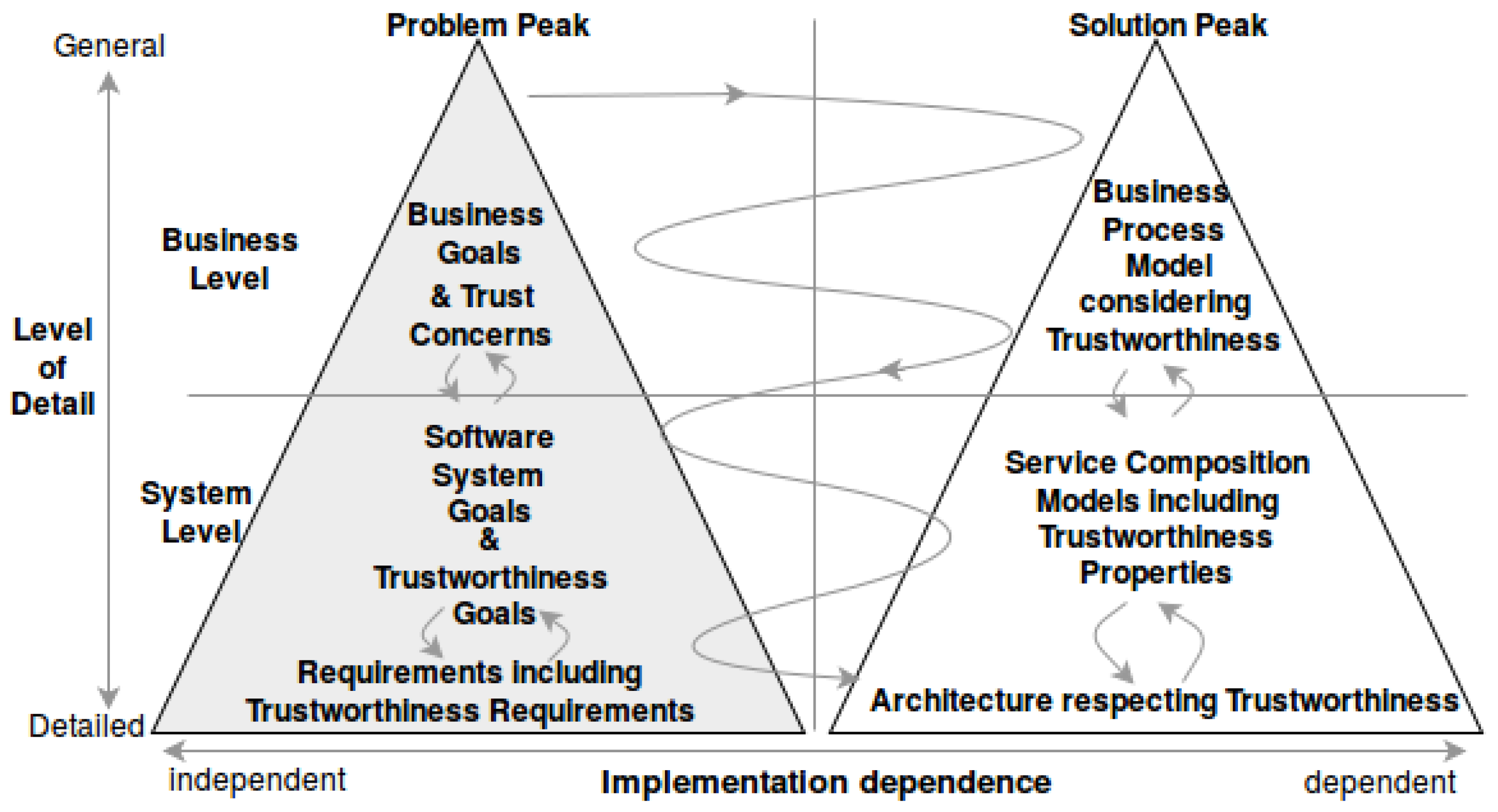
3. Framework for Systematic Analysis and Modeling of Trustworthiness Requirements
4. The Method for Systematic Analysis of Trustworthiness Requirements
- Step 1.
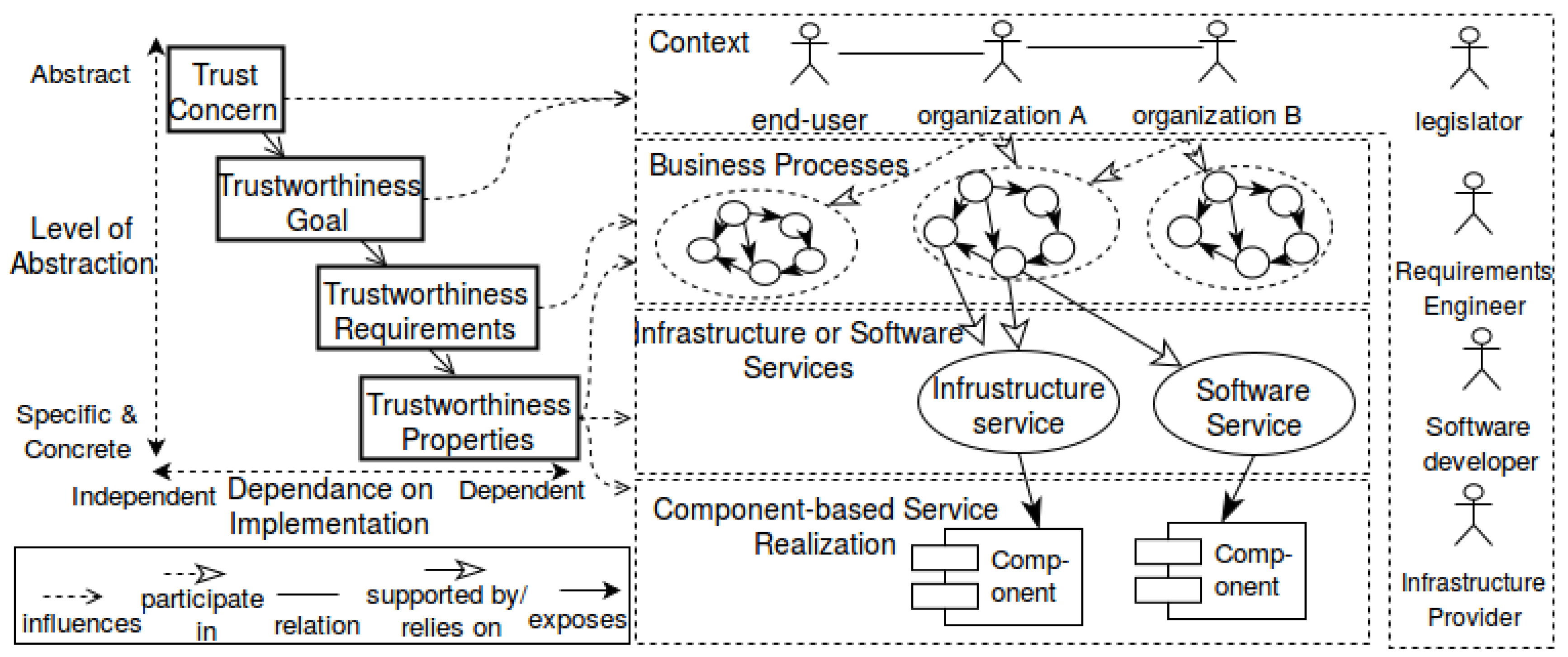
- Context analysis: The first step is concerned with identifying the participants and initial context information. The latter can be captured in a context model. The context information provides an overview of the process, as well.
- Step 2.
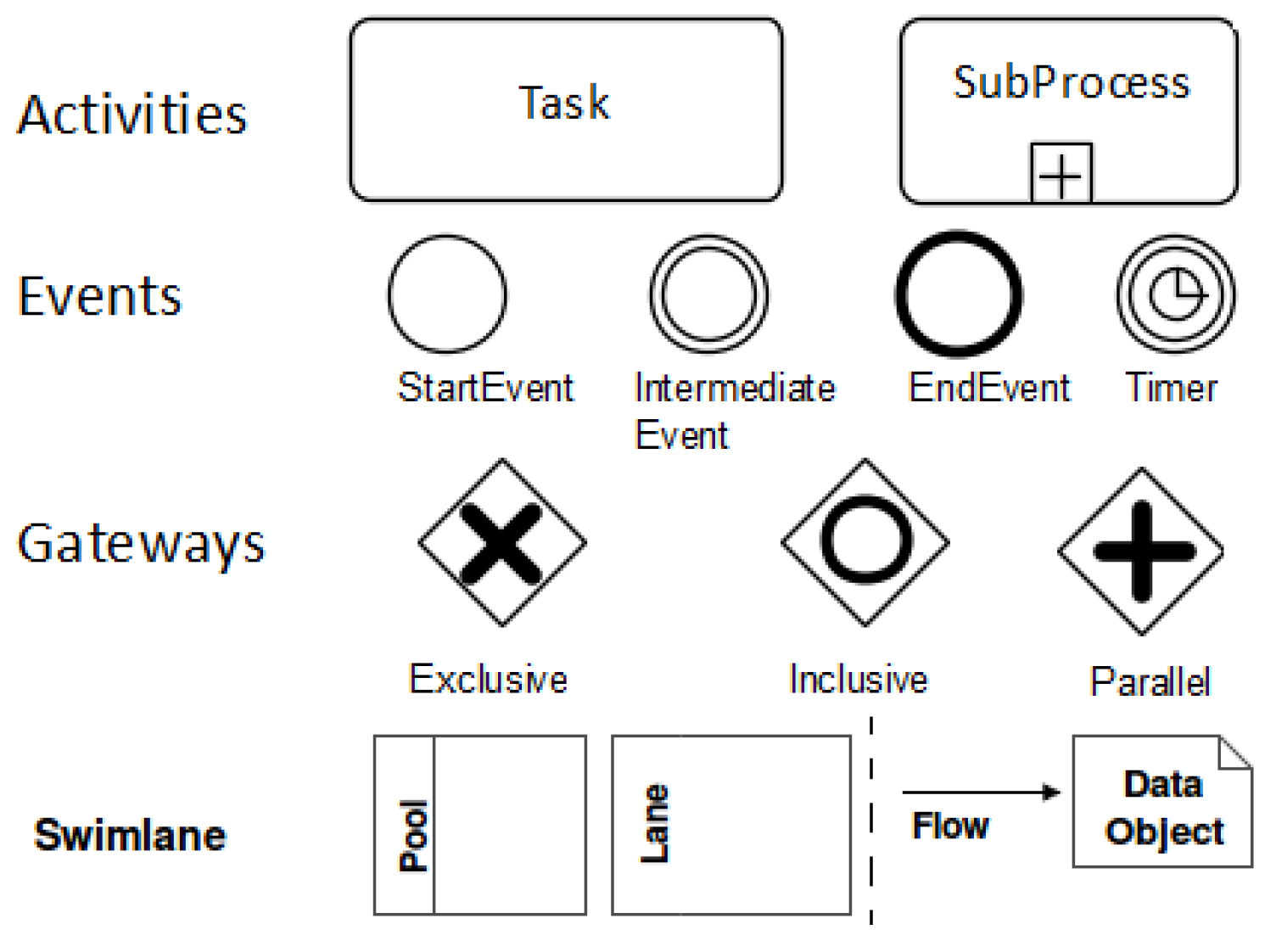
- Set up the goal model: This step is concerned with setting up the goal model by capturing the major intentions of the involved participants/stakeholders. The goals are captured either by interviewing involved stakeholders or are based on the expertise of a requirements engineer or business engineer at the business level. We start with high-level goals and then refine them within the problem peak. The basic elements of the i* modeling notation are shown in Figure 4.We model and document the goals in the SDM (cf. Figure 7) and SRM (cf. Figure 9) models. Please note that from the SRM in Figure 9, only the white-colored elements exist at this point of time.
- Step 3.
- Set up the business process models: As input, the SDM and SRM models are used. We select a specific goal from the SDM. For satisfying the selected goal, we set up a business process model. As notation, we use BPMN. The basic elements of the BPMN notation for business process modeling are shown in Figure 5. To create the business process model, we use information shown in the SDM and SRM. Based on the SDM, the dependency between roles and other goals can be analyzed. SRM models give insight into the resources and activities. The business process model (cf. Figure 8) for a specific goal visualizes the control and data flow between identified tasks, used resources and involved actors.
- Step 4.
- Identify trust concerns: Trust concerns of end-users and their dependencies on other participants in the business are identified. Trust concerns can be collected either by interviewing involved end-users or are based on the expertise of a requirements engineer. Prior to this step, the participants of a business and stakeholders are captured. We assume that this information about the context is provided in a context model. Trust concerns are subjective. To support this step (especially considering subjectiveness of trust), a questionnaire is provided in our previous work [17].
- Step 5.
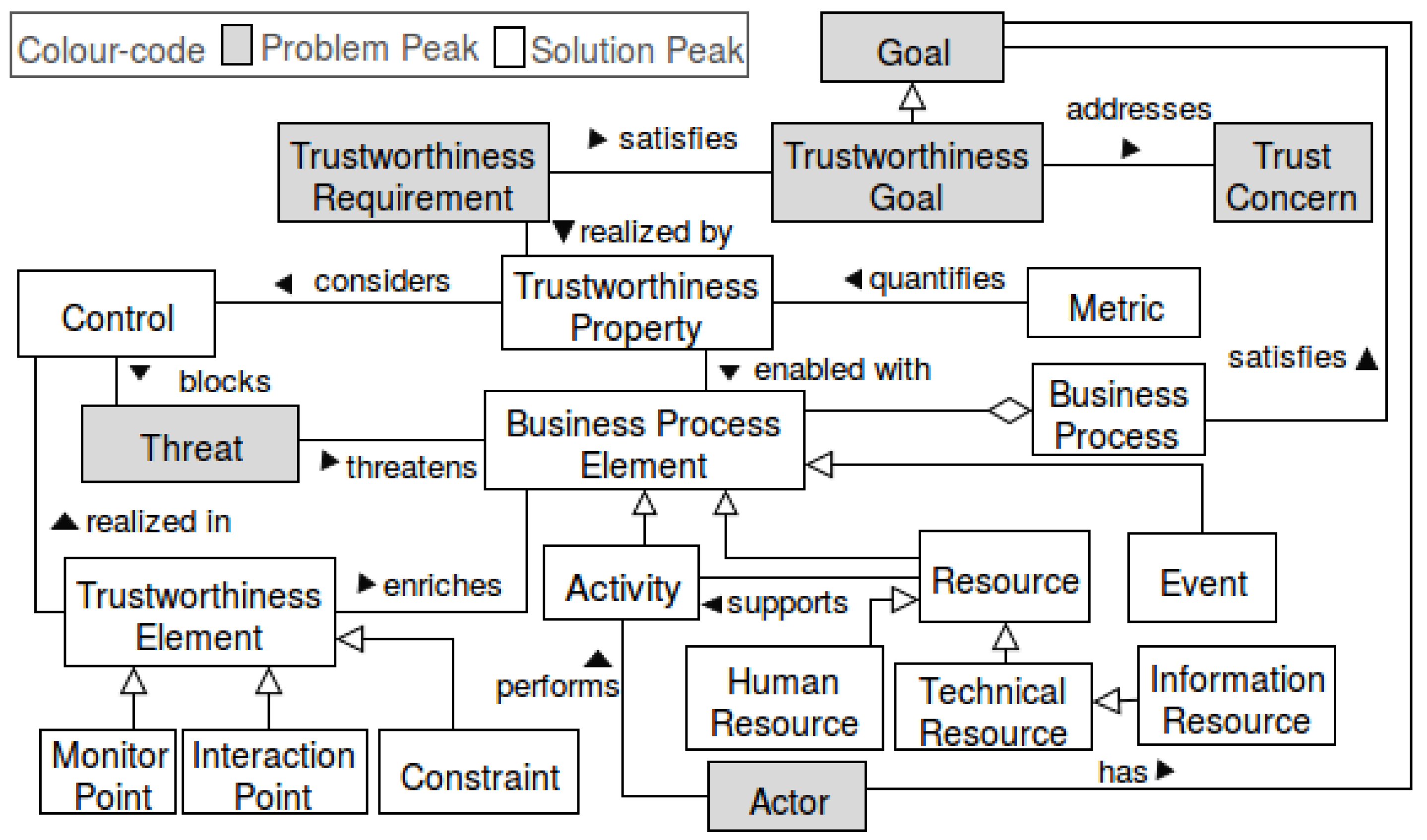
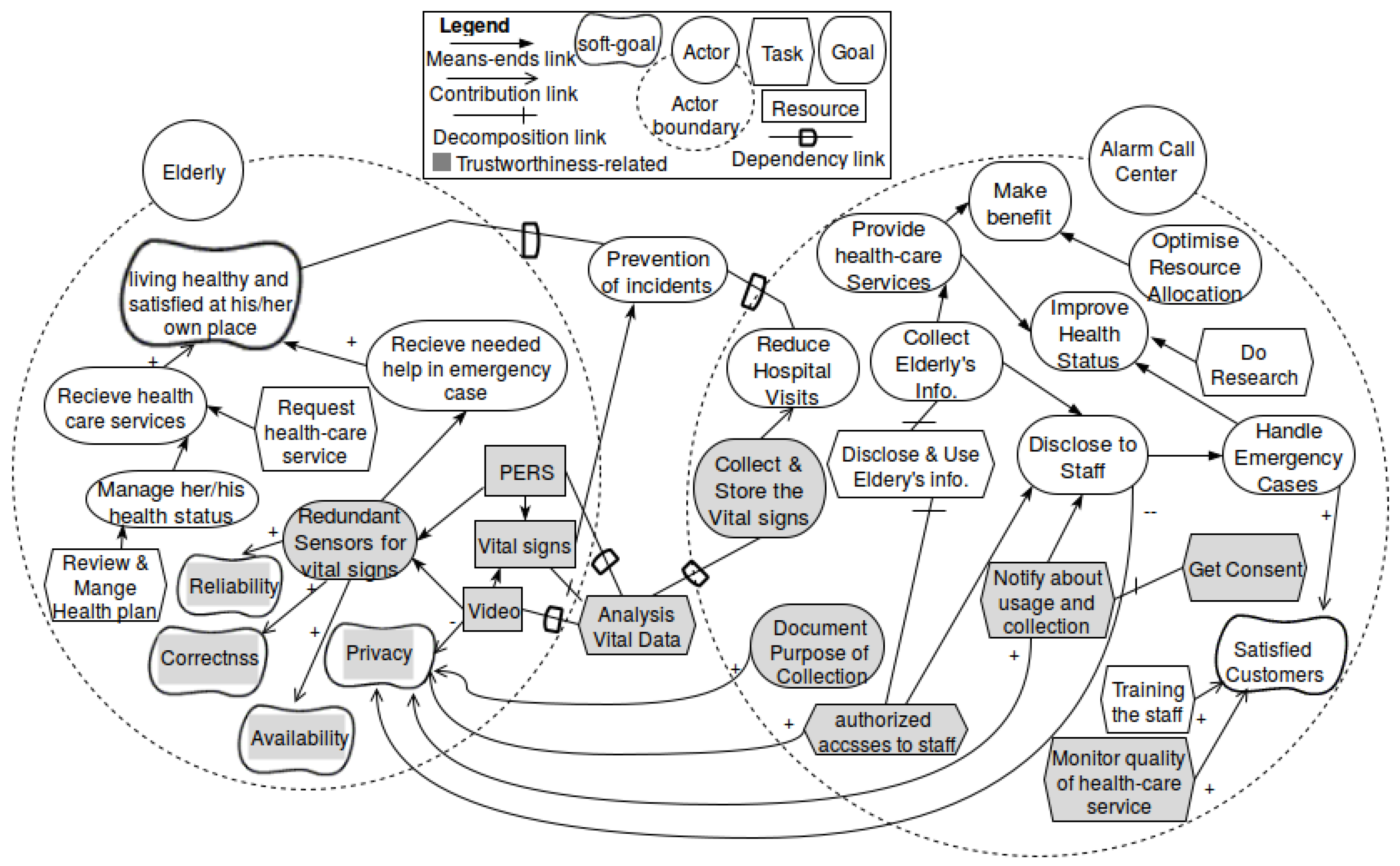
- Goal model including trustworthiness goals: Based on trust concerns, we refine the goal model with the trustworthiness goals and their relation to the other goals (negative or positive influences). The trustworthiness goals include the purpose for incorporating trustworthiness properties into the system under development. To support this step, a catalog of trustworthiness attributes that contribute to mitigate trust concerns is provided in our previous work [18]. Figure 9 shows such a goal model. Please note that the gray-colored elements were added to the goal model for addressing trustworthiness.
- Step 6.
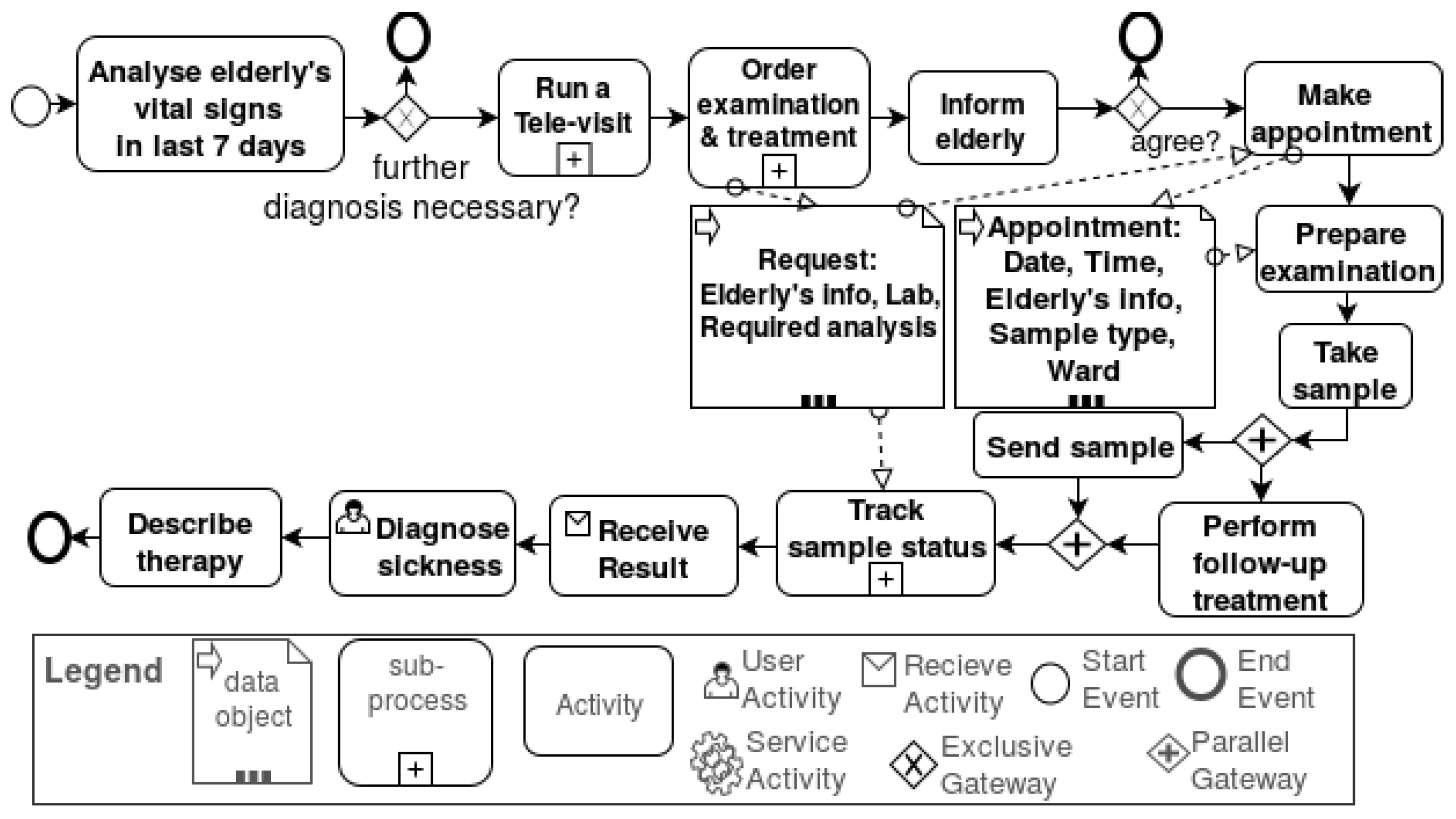
- Business process model including trustworthiness properties: Enhance the business process model from Step 3 by adding trustworthiness properties, which fulfill the trustworthiness goals. For supporting this step, we provide the new trustworthiness elements (cf. Figure 3). The new elements and the notation we suggest are shown in Table 1.We propose a BPMN extension that allows the integration of trustworthiness requirements into a business process. We introduce trustworthiness elements for business process modeling, which allows modeling and documenting trustworthiness requirements, as well as placing a control or putting constraints on the resources used in the business process to address the trust the concerns of the end-users. We list our new elements (cf. Table 1) that enrich business process elements in documenting the trustworthiness requirements as follows:
- Monitor points: We introduce the monitoring points with start and end points in the process model for monitoring and the trustworthiness properties that must be considered in the defined monitored points, as well as the desired/target values for them. Furthermore, the metrics can also be provided for quantifying trustworthiness properties that will be under observation at run-time. Monitor points can be used in combination with constraints to express the desired values and metrics for measuring trustworthiness properties at run-time.
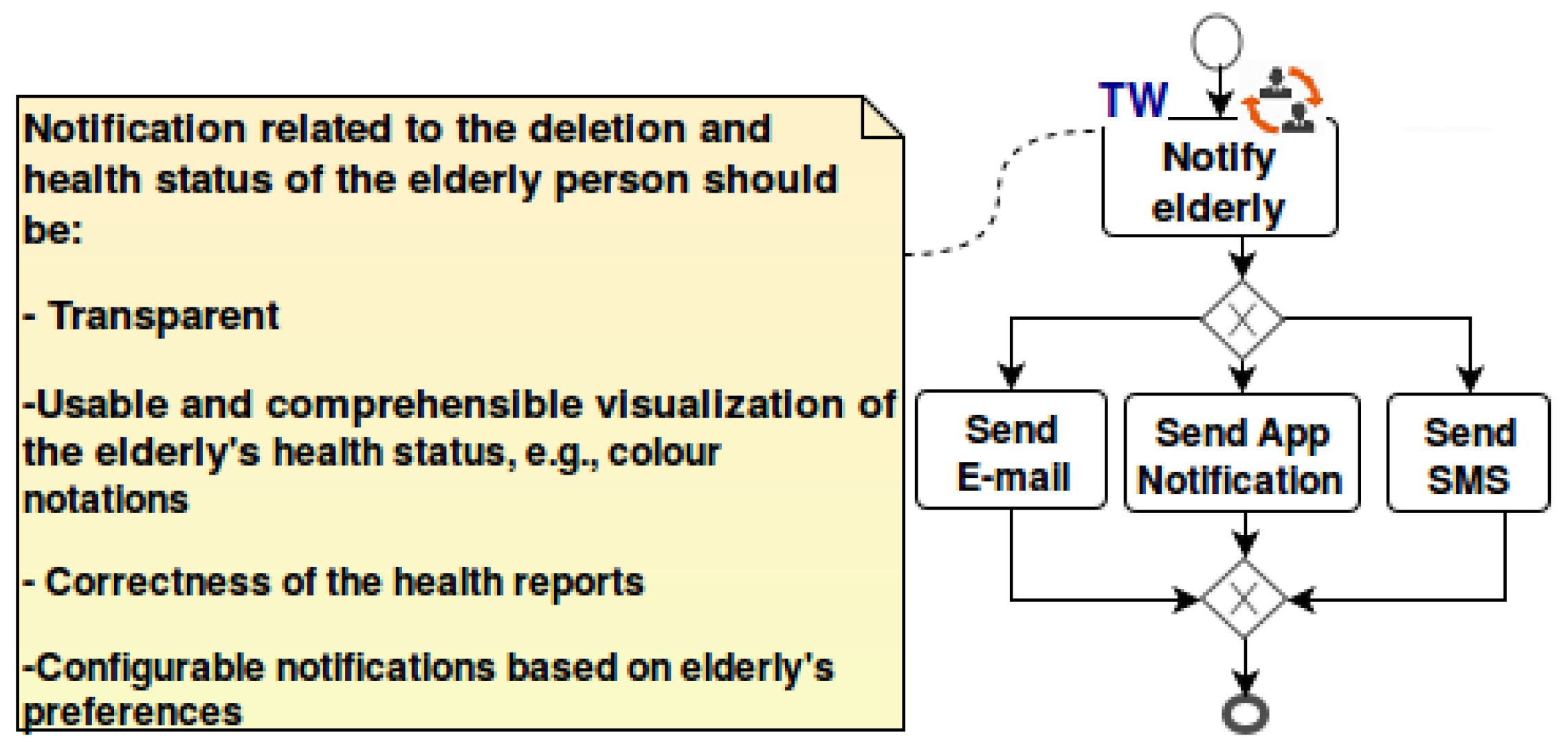
- Interaction points: These points specify the interfaces where the end-user is involved in the business process, e.g., she/he may interact with the technical resources (e.g., apps, software services) that support her/him in performing her/his tasks. In these interfaces, there are factors that could signal the trustworthiness of the system to the end-user, e.g., reliability, quality of visualization, usability, understandability of represented information, quality of service like availability or response time. For example, if an elderly person uses an app for reviewing his/her medical plan and medication, the visualization of his/her health status and medical plan influences her/his trust about the correctness of those health reports, medications or medical plans. Therefore, the trustworthiness requirements in these points need to be investigated further, and the resources involved in these points should include related trustworthiness properties that satisfy the trustworthiness requirements.
- Trustworthiness constraints: In addition to new elements like monitor and interaction points, each BPMN element can be enriched/annotated with the constraints that it should keep for satisfying trustworthiness requirements. The action with trustworthiness requirements and constraints is tagged with “TW” in the business process model, e.g., time constraints on activities or constraints on the resources that are used in performing a specific activity.
The business process model from Step 3 is analyzed by identifying which business process elements are related to the identified trustworthiness goals from Step 5. We select one of the business process models for including trustworthiness requirements satisfying trustworthiness goals. This selection is based on the relation of the trustworthiness goal to the other goals. This step goes through business process elements and control flow and questions whether the element in the business process is trustworthiness related. The relation of trustworthiness goals in the goal model to the other goals from Step 5 assists this step. - Step 7.
- Refinement of goal model (problem peak): Refine the goals and trustworthiness goals further in order to obtain user-centered trustworthiness requirements on resources and tasks. This refinement is performed within the problem peak. However, based on the output of this step, revisions of business process models can be necessary.
- Step 8.
- Refinement of business process model (solution peak): Detail the business processes by including trustworthiness properties on resources, activities, etc., for satisfying trustworthiness requirements. This refinement is performed within the solution peak. However, based on the output of this step, revisions of goal models can be necessary. Refinement of the business process model details business processes by including more concrete trustworthiness properties on business process elements. This step can be performed concurrently to the goal and trustworthiness goal refinements, and both models can develop iteratively.
5. Application Example
Motivating Scenario
- Step 1.
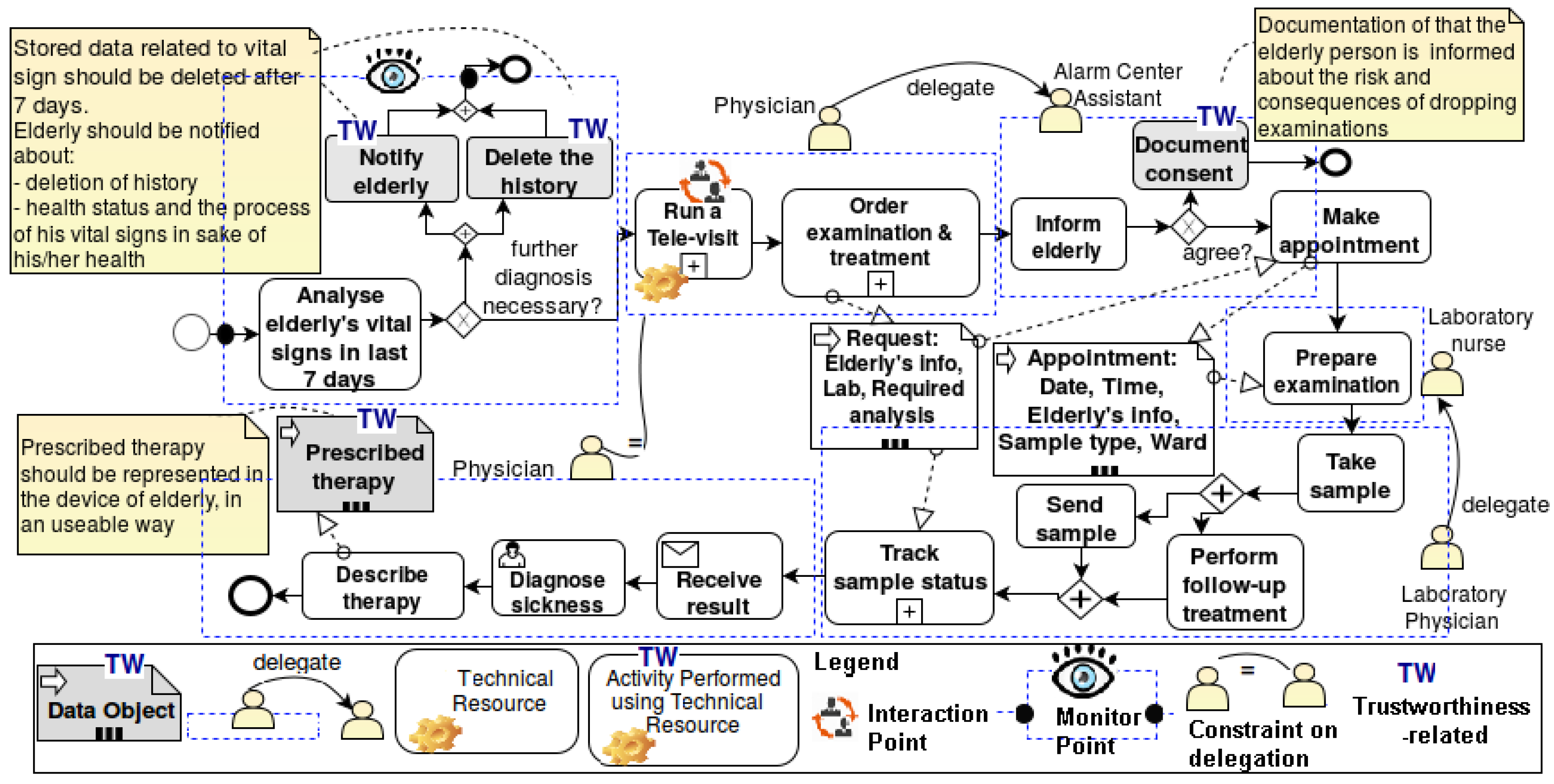
- Context analysis: We will focus on a Home Monitoring System (HMS) for incident detection and detection of abnormal situations to prevent emergency incidents. The home monitoring system allows elderly people in their homes to call for help in case of emergency situations. Furthermore, HMS analyzes the elderly person’s health status for preventing incidents in the first place. The incidents are reported to an alarm call center that, in turn, reacts by, e.g., sending out ambulances or other medical caregivers and notifying the elderly person’s relatives. For preventing emergency situations, the vital signs of the elderly person are diagnosed at regular intervals to reduce hospital visits and falls. Figure 6 shows an exemplary design-time system model including physical, logical and human resources/assets.
- Step 2.
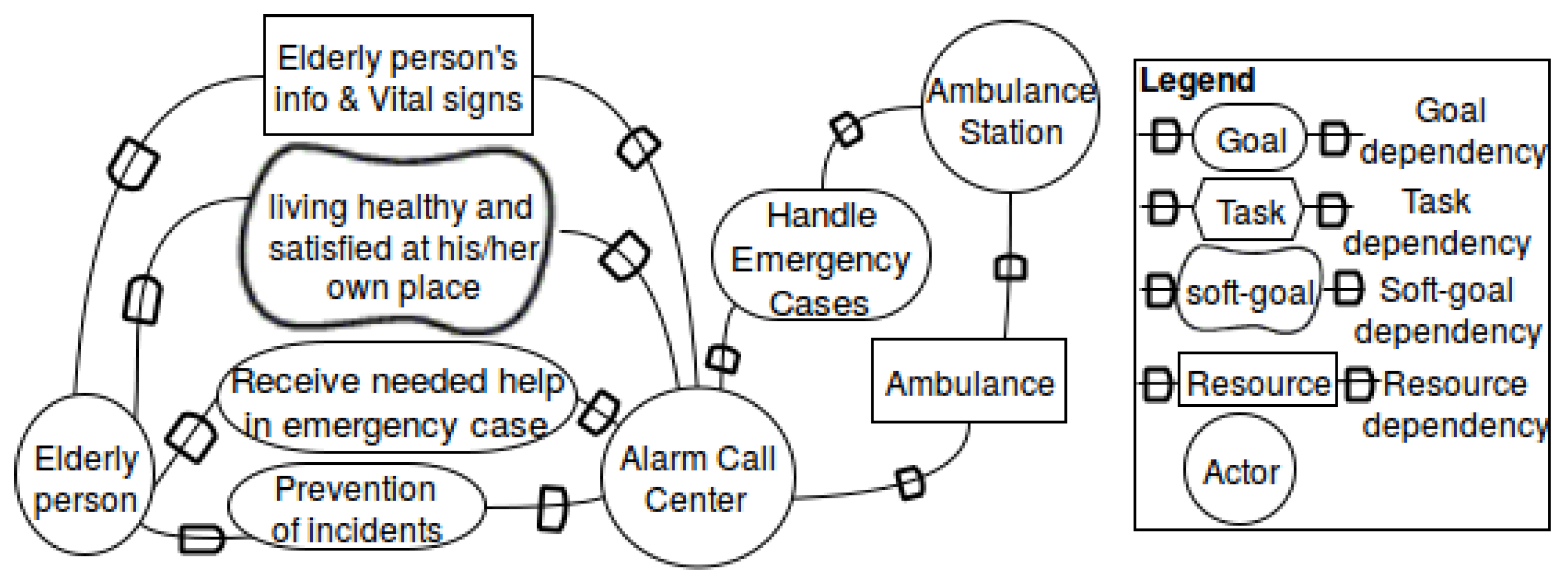
- Set up the goal model: Figure 7 captures the goals of different participants and their dependencies on each other or the realization of the goals. This is done based on the expertise of a requirements engineer and the knowledge gained during the context analysis, for example, by means of interviews. Here, we only focus on the elderly person and the alarm call center. The ambulance station is also involved, because for handling the emergency cases, the alarm call center is dependent on the ambulance as a resource.
- Step 3.
- Set up the business process model: Figure 8 illustrates and exemplifies the typical steps that, for example, caregivers in an alarm center have to take once they notice that the health record of an elderly person deviates from the normal situation and further examination is needed. This business process model targets the satisfaction of the goals reducing hospital visits and prevention of incidents (cf. Figure 7).
- Step 4.
- Identify trust concerns: Alice is concerned about whether she will really receive the emergency help if a similar situation happens again (heart attack experience). Alice is informed that by using the HMS, she can have regular diagnoses, which can prevent frequent hospital visits. However, Alice is concerned whether she will be able to use the service in a proper way. She is also concerned about who can get access to the data about her diseases or life habits. She indicates that she would only prefer her regular nurse and doctor to be able to see her history and health status.
- Step 5.
- Goal model including trustworthiness goals: Based on the trust concerns, a requirement engineer adds trustworthiness goals to the goal model. The existing goal-based refinement techniques are applied to refine these trustworthiness goals into trustworthiness requirements. Considering the healthcare domain, reliability, availability, usability, raising awareness and privacy (providing guidance and users’ data protection) are crucial issues related to trustworthiness [19]. For instance, electronic medical transactions require the transmission of personal and medical information over insecure channels, e.g., the Internet. Patients’ profiles document the medical behavior of patients or even include sensitive information, e.g., their medical history.
- Step 6.
6. Benefits of Our Method
- Elicitation of trustworthiness requirements with a direct link to the originating trust concern and using them to make informed design decisions is a key success factor for developing a trustworthy system.
- Bridging the two peaks (problem and solution) helps to elaborate the synergies between requirements and design artifacts. The benefits of interleaving the tasks of eliciting and refining requirements with the tasks of designing a software solution has long been recognized [20]. Trustworthiness requirements together with other requirements are evolutionarily developed and will not be ignored. In a development process that incorporates just an up-front requirements engineering method, there is the risk of ignoring trust concerns. Developers might deliver solutions that fail to treat trust concerns of end-users. It is therefore important to proactively elicit trustworthiness requirements from different participating actors during early phases and then to consider design solutions that balance and satisfy those concerns.
- Combining goal models and business process models has the benefit that we avoid gold plating. Gold plating [21] is known as the implementation of irrelevant requirements, i.e., requirements that were never requested by stakeholders and are thus not backward traceable to any goals of stakeholders. Yet, our trustworthiness requirements can always be traced back to trust concerns of stakeholders. Therefore, there is always a justification for the trustworthiness requirements that are realized. This becomes even more critical, when the users pay it with the cost of their privacy or sometimes harming trust. For instance, in the home monitoring system, when the elderly person does not desire any assistance outside her/his home, the provided app (e.g., health manager) should not be permitted on location information.
- The explicit consideration of conflicts on the goal level is another benefit of our approach. Sometimes some of the end-users’ trust concerns are in conflict with the goals of other involved actors. For instance, the privacy goal of an elderly person in terms of transparency might be in conflict with the business goals of the hospital or insurance company. To resolve this conflict, the extent of transparency can be negotiated between the parties. In our approach, such kinds of contradictions are dealt with before the developers go into technical realizations of the goals.
- Dependencies between actors together with positive and negative links in i* [6] describe the trustworthiness-related dependencies. However, dependencies and contribution links do not capture business relationships. These relationships are described in the business process models in our approach. One may understand the business process models also as an architectural description of the application.
- The resulting business process models with specified trustworthiness requirements can be used as a basis for designing and developing trustworthy software systems, applications and even for the evaluation of the trustworthiness properties [1] (e.g., privacy, reliability, confidentiality or integrity) on an abstract level.
- Business process modeling offers an appropriate abstraction level to describe trustworthiness requirements and to later evaluate trustworthiness-related risks.
7. Related Work
8. Evaluation Plan
9. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| Tr | Trust |
| TW | TrustWorthines |
| BPMN | Business Process Model and Notation |
| SecBPMN | Secure Business Process Model and Notation |
| KAOS | Knowledge Acquisition in autOmated Specification |
| UML | Unified Modeling Language |
| AAL | Ambient Assisted Living |
| HMS | Home Monitoring System |
| PERS | Personal Emergency Response System |
| EMHT | Emergency Monitoring and Handling Tool |
| HM | Health Manager |
| CASE | Computer-Aided Software Engineering |
| RALPH | Resource Assignment Language graPH |
| GRL | Goal-oriented Requirement Language |
| PriS | Privacy Safeguard |
References
- Gol Mohammadi, N.; Bandyszak, T.; Kalogiros, C.; Kanakakis, M.; Weyer, T. A Framework for Evaluating the End-to-End Trustworthiness. In Proceedings of the 14th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (IEEE TrustCom), Helsinki, Finland, 20–22 August 2015; pp. 638–645. [Google Scholar]
- Gol Mohammadi, N.; Bandyszak, T.; Paulus, S.; Meland, P.H.; Weyer, T.; Pohl, K. Extending Software Development Methodologies to Support Trustworthiness-by-Design. In Proceedings of the CAiSE Forum, Stockholm, Sweden, 8–12 June 2015; pp. 213–220. [Google Scholar]
- Haley, C.B.; Laney, R.C.; Moffett, J.D.; Nuseibeh, B. The Effect of Trust Assumptions on the Elaboration of Security Requirements. In Proceedings of the 12th IEEE International Requirements Engineering Conference, Kyoto, Japan, 6–10 September 2004; pp. 102–111. [Google Scholar]
- Giorgini, P.; Massacci, F.; Mylopoulos, J.; Zannone, N. Requirements Engineering for Trust Management: Model, Methodology, and Reasoning. Int. J. Inf. Secur. 2006, 5, 257–274. [Google Scholar] [CrossRef]
- Cabanillas, C.; Knuplesch, D.; Resinas, M.; Reichert, M.; Mendling, J.; Ruiz-Cortés, A. RALph: A Graphical Notation for Resource Assignments in Business Processes. In Advanced Information Systems Engineering, CAiSE 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 53–68. [Google Scholar]
- Yu, E.S.K. Towards Modelling and Reasoning Support for Early-Phase Requirements Engineering. In Proceedings of the 3rd IEEE International Symposium on Requirements Engineering, Annapolis, MD, USA, 5–8 January 1997; pp. 226–235. [Google Scholar]
- Object Management Group (OMG). Business Process Model and Notation (BPMN) Version 2.0. Technical Report. Available online: http://www.omg.org/spec/BPMN/2.0/ (accessed on 17 April 2017).
- Gol Mohammadi, N.; Heisel, M. A Framework for Systematic Analysis and Modeling of Trustworthiness Requirements Using i* and BPMN. In Proceedings of the International Conference on Trust and Privacy in Digital Business (TrustBUS 2016), Porto, Portugal, 5–8 September 2016; pp. 3–18. [Google Scholar]
- Sztompka, P. Trust: A Sociological Theory; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar]
- Mei, H.; Huang, G.; Xie, T. Internetware: A Software Paradigm for Internet Computing. Computer 2012, 45, 26–31. [Google Scholar] [CrossRef]
- Stroppi, L.J.R.; Chiotti, O.; Villarreal, P.D. Extending BPMN 2.0: Method and Tool Support. In Proceedings of the 3rd International Workshop Proceedings of Business Process Model and Notation (BPMN); Springer: Berlin/Heidelberg, Germany, 2011; pp. 59–73. [Google Scholar]
- Van Lamsweerde, A.; Letier, E. Handling Obstacles in Goal-Oriented Requirements Engineering. In Proceedings of the 3rd IEEE International Symposium on Requirements Engineering, Annapolis, MD, USA, 5–8 January 1997; pp. 226–235. [Google Scholar]
- Letier, E.; van Lamsweerde, A. Agent-based tactics for goal-oriented requirements elaboration. IEEE Trans. Softw. Eng. 2000, 26, 978–1005. [Google Scholar]
- Nuseibeh, B. Weaving together Requirements and Architectures. Computer 2001, 34, 115–119. [Google Scholar] [CrossRef]
- Papazoglou, M.P. Service-Oriented Computing: Concepts, Characteristics and Directions. In Proceedings of the Fourth International Conference on Web Information Systems Engineering, (WISE 2003), Rome, Italy, 10–12 December 2003; pp. 3–12. [Google Scholar]
- Papazoglou, M.P.; Traverso, P.; Dustdar, S.; Leymann, F. Service-Oriented Computing: State of the Art and Research Challenges. Computer 2007, 40, 38–45. [Google Scholar] [CrossRef]
- Gol Mohammadi, N.; Heisel, M. Patterns for Identification of Trust Concerns and Specification of Trustworthiness Requirements. In Proceedings of the 21st European Conference on Pattern Languages of Programs (EuroPlop ’16); ACM: New York, NY, USA, 2016. [Google Scholar]
- Gol Mohammadi, N.; Paulus, S.; Bishr, M.; Metzger, A.; Könnecke, H.; Hartenstein, S.; Weyer, T.; Pohl, K. Trustworthiness Attributes and Metrics for Engineering Trusted Internet-Based Software Systems. In Cloud Computing and Services Science—3rd International Conference, CLOSER; Revised Selected Papers; Springer: Berlin/Heidelberg, Germany, 2013; pp. 19–35. [Google Scholar]
- Avancha, S.; Baxi, A.; Kotz, D. Privacy in Mobile Technology for Personal Healthcare. ACM Comput. Surv. (CSUR) 2012, 45, 1–54. [Google Scholar] [CrossRef]
- Chung, L.; do Prado Leite, J. On Non-Functional Requirements in Software Engineering. In Conceptual Modeling: Foundations and Applications; Springer: Berlin/Heidelberg, Germany, 2009; pp. 363–379. [Google Scholar]
- Pohl, K. Requirements Engineering: Fundamentals, Principles, and Techniques; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Horkoff, J.; Başak Aydemir, F.; Cardoso, E. Goal-Oriented Requirements Engineering: A Systematic Literature Map. In Proceedings of the 2016 IEEE 24th International Requirements Engineering Conference (RE), Beijing, China, 12–16 September 2016; pp. 106–115. [Google Scholar]
- Van Lamsweerde, A. Elaborating Security Requirements by Construction of Intentional Anti-Models. Proceeding of the 26th International Conference on Software Engineering (ICSE’04), Edinburgh, UK, 23–28 May 2004; pp. 148–157. [Google Scholar]
- Liu, L.; Yu, E.; Mylopoulos, J. Security and Privacy Requirements Analysis within a Social Setting. In Proceedings of the 11th IEEE International Conference on Requirements Engineering (RE’03), Monterey, CA, USA, 8–12 September 2003; pp. 151–161. [Google Scholar]
- Giorgini, P.; Massacci, F.; Mylopoulous, J.; Zannone, N. Requirements Engineering meets Trust Management: Model, Methodology, and Reasoning. In Proceedings of iTrust’04, LNCS 2995; Springer: Berlin/Heidelberg, Germany, 2004; pp. 176–190. [Google Scholar]
- Bresciani, P.; Giorgini, P.; Giunchiglia, F.; Mylopoulos, J.; Perini, A. TROPOS: An Agent- Oriented Software Development Methodology. JAAMAS 2004, 8, 203–236. [Google Scholar] [CrossRef]
- Mellado, D.; Sánchez, L.E.; Fernández-Medina, E. A Systematic Review of Security Requirements Engineering. Comput. Stand. Interfaces 2010, 32, 153–165. [Google Scholar] [CrossRef]
- Jackson, M. Problem Frames: Analyzing and Structuring Software Development Problems; Addison-Wesley: Boston, MA, USA, 2001. [Google Scholar]
- De la Vara, J.L.; Sánchez, J. Improving Requirements Analysis through Business Process Modelling: A Participative Approach. In Business Information Systems; Springer: Berlin/Heidelberg, Germany, 2008; pp. 165–176. [Google Scholar]
- Short, S.; Kaluvuri, S.P. A Data-Centric Approach for Privacy-Aware Business Process Enablement. In Proceedings of the 3rd International IFIP Working Conference Enterprise Interoperability (IWEI), Stockholm, Sweden, 23–24 March 2011; pp. 191–203. [Google Scholar]
- Wang, M.; Bandara, K.; Pahl, C. Process as a Service Distributed Multi-tenant Policy-Based Process Runtime Governance. In Proceedings of the IEEE International Conference on Services Computing (SCC), Miami, FL, USA, 5–10 July 2010; pp. 578–585. [Google Scholar]
- Koschmider, A.; Yingbo, L.; Schuster, T. Role Assignment in Business Process Models. In Business Process Management Workshops; Springer: Berlin/Heidelberg, Germany, 2012; Volume 99, pp. 37–49. [Google Scholar]
- Van der Aalst, W.M.P.; Kumar, A. A Reference Model for Team-enabled Workflow Management Systems. Data Knowl. Eng. 2001, 38, 335–363. [Google Scholar] [CrossRef]
- Stroppi, L.J.R.; Chiotti, O.; Villarreal, P.D. A BPMN 2.0 Extension to Define the Resource Perspective of Business Process Models. In Proceedings of the XIV Congreso Iberoamericano en Software Engineering (CIbSE), Rio de Janeiro, Brasil, 27–29 April 2011. [Google Scholar]
- Stepien, B.; Felty, A.; Matwin, S.A. A Non-technical User-Oriented Display Notation for XACML Conditions. In E-Technologies: Innovation in an Open World; Lecture Notes in Business Information Processing; Springer: Berlin/Heidelberg, Germany, 2009; Volume 26, pp. 53–64. [Google Scholar]
- Russell, N.; van der Aalst, W.; ter Hofstede, A.; Edmond, D. Workflow Resource Patterns: Identification, Representation and Tool Support. In Advanced Information Systems Engineering; Springer: Berlin/Heidelberg, Germany, 2005; pp. 216–232. [Google Scholar]
- Strembeck, M.; Mendling, J. Modeling Process-related RBAC Models with Extended UML Activity Models. Inf. Softw. Technol. 2011, 53, 456–483. [Google Scholar] [CrossRef]
- Wolter, C.; Menzel, M.; Schaad, A.; Miseldine, P.; Meinel, C. Model-driven Business Process Security Requirement Specification. J. Syst. Archit. Spec. Issue Secure SOA 2009, 55, 211–223. [Google Scholar] [CrossRef]
- Rodríguez, A.; Fernández-Medina, E.; Piattini, M. A BPMN Extension for the Modeling of Security Requirements in Business Processes. IEICE Trans. Inf. Syst. 2007, E90-D, 745–752. [Google Scholar] [CrossRef]
- Sang, K.S.; Zhou, B. BPMN Security Extensions for Healthcare Process. In Proceedings of the IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, (CIT/IUCC/DASC/PICOM), Liverpool, UK, 26–28 October 2015; pp. 2340–2345. [Google Scholar]
- Maines, C.L.; Llewellyn-Jones, D.; Tang, S.; Zhou, B. A Cyber Security Ontology for BPMN-Security Extensions. In Proceedings of the IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, Liverpool, UK, 26–28 October 2015; pp. 1756–1763. [Google Scholar]
- Salnitri, M.; Dalpiaz, F.; Giorgini, P. Designing Secure Business Processes with secBPMN. Softw. Syst. Model. 2017, 16, 1–21. [Google Scholar] [CrossRef]
- Horkoff, J.; Li, T.; Li, F. Taking Goal Models Downstream: A Systematic Roadmap. In Proceedings of the IEEE 8th International Conference on Research Challenges in Information Science (RCIS), Marrakech, Morocco, 28–30 May 2014; pp. 1–12. [Google Scholar]
- Bleistein, S.J.; Aurum, A.; Cox, K.; Ray, P.K. Linking Requirements Goal Modeling Techniques to Strategic e-Business Patterns and Best Practice. In Proceedings of the I8th Australian Workshop on Requirements Engineering (AWRE’03), Sydney, Australia, 4–5 December 2003; pp. 13–22. [Google Scholar]
- Salnitri, M.; Paja, E.; Giorgini, P. From Socio-Technical Requirements to Technical Security Design: An STS-Based Framework. Ph.D. Thesis, University of Trento, Trento, Italy, 2015. [Google Scholar]
- Kalloniatis, C.; Kavakli, E.; Gritzalis, S. Addressing Privacy Requirements in System Design: The PriS Method. Requir. Eng. 2008, 13, 241–255. [Google Scholar] [CrossRef]
- Argyropoulos, N.; Shei, S.; Kalloniatis, C.; Mouratidis, H. A Semi-Automatic Approach for Eliciting Cloud Security and Privacy Requirements. In Proceedings of the 50th Hawaii International Conference on System Sciences (HICSS), Waikoloa Village, HI, USA, 4–7 January 2017. [Google Scholar]

| Defined TrustworthinessElement (Extension) | Definition | Symbols | |
|---|---|---|---|
| Monitor Point | Inserting monitor points into the business process defines the start and end point of monitoring at run-time. Monitor points can be used in combination with constraints to express the desired values and metrics for measuring trustworthiness properties at run-time. |  | |
| Interaction Point | Interaction points are the places where the end-user interacts with the system. The interaction is normally supported by the apps or softwareservices. Qualities of these apps and software services have an impact on the trust perceptionof users. Therefore, it should be studied well how to signal their trustworthiness to the end-user. Interaction points can be further detailed in combination with constraints on technical resources (in interaction points), e.g., specifying which quality, to what extent (e.g., 99% availability). |  | |
| Constraint | Constraints on Activity | Trustworthiness requirements on a specific activity, e.g., expected duration of an activity. |  |
| Constraints on Resources | Trustworthiness requirements on a specific resource (either human or non-human), e.g., expertise of the involved human resource. |  | |
| Constraints on Delegations | Trustworthiness requirements on delegation, e.g., if a delegation (e.g., activity delegation) is allowed or delegation to whom or which roles are allowed. |  | |
| Trust Concerns | Trustworthiness Requirements | Activities | Affected Resources |
|---|---|---|---|
| Privacy | Transparency, intervenability | Storage, deletion within 7 days, update | Private inventory system from the alarm call center, external cloud storage |
| Awareness | Usability, transparency, reliability, availability | Notifications, place appointments | App on the elderly person’s smart device (HM) |
| Safety, reliability | Reliability, availability | Raise alarm | Redundant sensors in addition to PERS |
| Privacy | Correctness, usability, availability | Make appointment, prescribe examination | Elderly person’s details |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mohammadi, N.G.; Heisel, M. A Framework for Systematic Refinement of Trustworthiness Requirements. Information 2017, 8, 46. https://doi.org/10.3390/info8020046
Mohammadi NG, Heisel M. A Framework for Systematic Refinement of Trustworthiness Requirements. Information. 2017; 8(2):46. https://doi.org/10.3390/info8020046
Chicago/Turabian StyleMohammadi, Nazila Gol, and Maritta Heisel. 2017. "A Framework for Systematic Refinement of Trustworthiness Requirements" Information 8, no. 2: 46. https://doi.org/10.3390/info8020046






