Fuzzy Extractor and Elliptic Curve Based Efficient User Authentication Protocol for Wireless Sensor Networks and Internet of Things
Abstract
:1. Introduction
- The sensor nodes of WSNs sufferer with energy constraints, memory limitations, unreliable communications, higher latency in communication and unattended operation of networks.
- The topology of WSNs can vary very often.
- The sensor node can be deployed densely in WSNs area.
- In this paper, we first discuss various security issues involved in authenticating the users of WSNs and IoT.
- We perform the security analysis of various existing protocols of user authentication for WSNs. Through security analysis, we show that the existing protocols are vulnerable to various attacks like user impersonation attack, sensor node impersonation attack, attacks based on legitimate users.
- We propose a secure and efficient protocol for authenticating the users of WSNs and IoT considering mutual authentication, session key establishment, data freshness, and confidentiality.
- Through informal security analysis, we show that our proposed protocol resists the stolen smart card, sensor node compromise, gateway node compromise, man-in-the-middle and replay attacks.
- We execute “proof of security” using random oracle model to ensure the correctness of various security features involved in our proposed protocol.
- Subsequently, we verify the proposed protocol on popular and robust security verification tool such as AVISPA and Scyther.
- We use BAN logic to determine whether exchanged messages of the proposed protocol are trustworthy and secure against eavesdropping.
- Finally, we present the comparative analysis of our proposed protocol with other existing protocols based on security and computational overhead.
2. Related Work
3. Notations, Assumptions and Cryptography Concepts Used
3.1. Notations
3.2. Assumptions
- Sensor node may not fix up with tamper-resistant hardware and if a node is captured by an adversary, all the prominent and confidential information stored in its memory can be accessed by the adversary. If the sensor nodes are tamper-resistant the adversary can know the information stored in the memory by measuring the power consumption of the captured sensor nodes.
- The base station or the gateway node is the trusted entity, and it works both as an authentication as well as a key distribution center.
- The adversary can intercept the public communication channel, inject packets and replay the previously transmitted packets.
- The adversary can capture the smart card of user and it can extract the sensitive information stored in the card through simple and differential power analysis techniques [24].
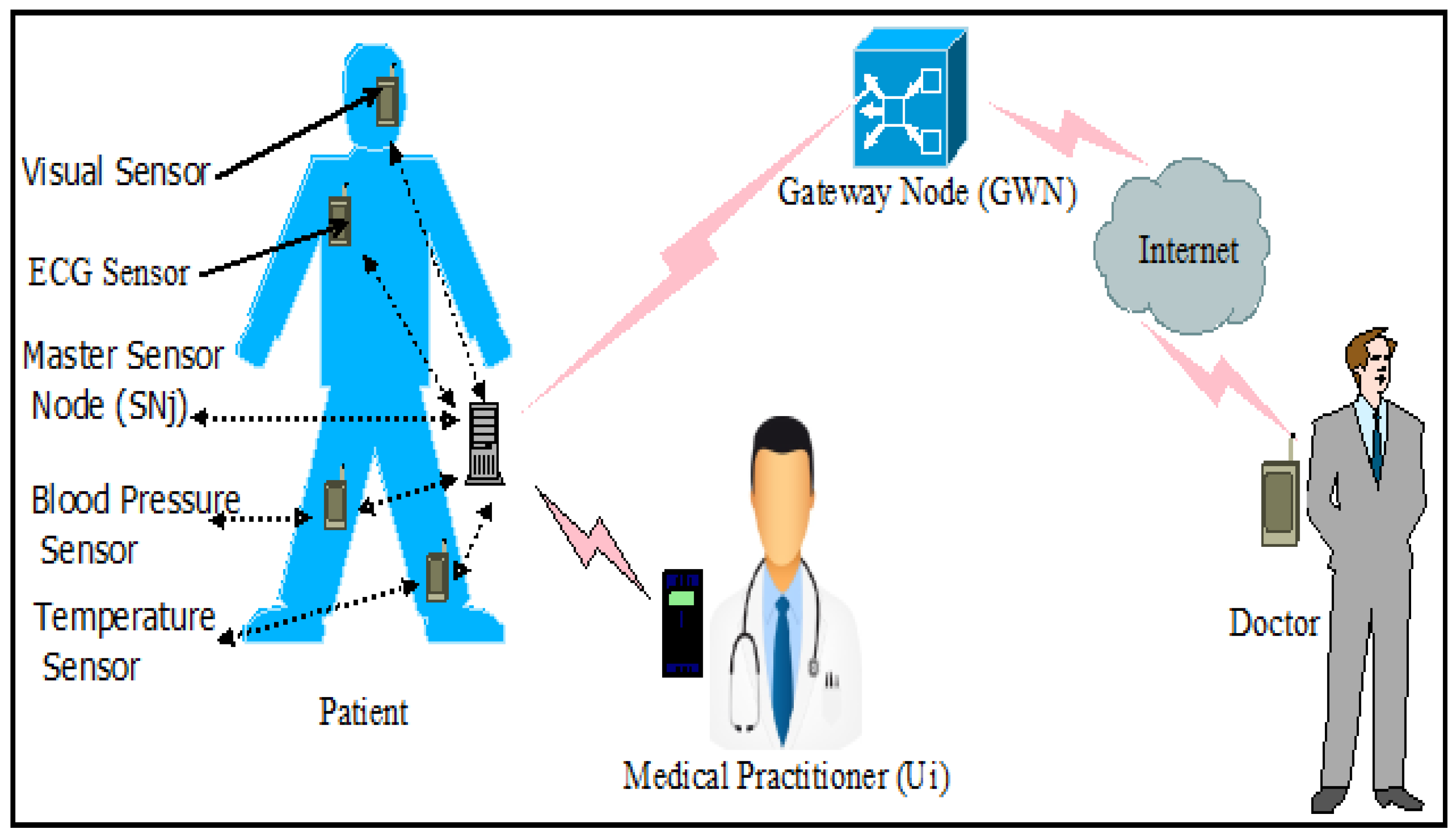
- We assume that the WSNs and IoT consist of few users (with smart card which can be captured or stolen by the adversary ), hundreds of sensor nodes (it can be captured by ) and the trusted gateway node.
- The processed data from the sensor nodes are gathered periodically at the gateway node . The gathered data may not always be real-time and fresh at . Therefore, the authentic user should be allowed to access the data directly from the sensor node to make quick decision for secure and real-time applications of WSNs and IoT.
3.3. Cryptography Concepts Used
- ’s advantage to find the collision and
- , for any sufficiently small .
- .
- iff
- , where
- The operation takes a bio-metric credential of user as an input and produces outputs—a secret string and a public accessory string , i.e.,
- The operation takes a noisy bio-metric credential of user and the public accessory string as an input and reproduces the secret string as an output i.e., if and only if
4. Review and Cryptanalysis of Various Recent Schemes of User Authentication for WSNs
4.1. Review of A.K.Das’s Scheme
- Step DR1:
- The user inputs and and generates 1024 bit random number K. Subsequently, calculates and selects a key Then, transmits to using secure communication channel.
- Step DR2:
- After receiving the message , the gateway node generates 1024 bit key , evaluates and stores into . Then, sends to using secure communication channel.
- Step DR3:
- After receiving , the user evaluates and Finally, replaces with in and stores into
- Step DA1:
- The registered user inserts his/her smart card into the card reader device and provides the secret bio-metric information . Then, evaluates . If , transmits to via public communication channel. Otherwise, aborts this phase.
- Step DA2:
- After receiving the message , verifies the message. If is valid, sends a Random challenge R to via public communication channel. Otherwise, aborts this phase.
- Step DA3:
- After receiving the Random challenge R, evaluates Finds the current time-stamp . Then, transmits to via public communication channel.
- Step DA4:
- evaluates using decryption operation based on key . If is fresh and R is valid, computes , finds the current time-stamp and computes Finally, transmits to via public communication channel. Otherwise, aborts this phase immediately.
- Step DA5:
- retrieves as using decryption operation on based on key . If is fresh and is valid, finds the current time-stamp and evaluates the session key . Then, sends to via public communication channel and stores in its memory. Otherwise, aborts this phase immediately. Finally, stores in its memory.
- Step DA6:
- If is fresh, the user computes , If establishes the session key with the sensor node Otherwise, aborts this phase immediately.
4.2. Cryptanalysis of A.K.Das’s Scheme
4.2.1. Stolen Smart Card Attacks
- Derives the value of K and using the frequency analysis of stream cipher and .
- Eavesdrops R and and implements the known plain text attack to find out the value of . Thereafter, find out the value of .
- Steals the bio-metric information of (where ) and find out the value of . Eavesdrops the value of from public communication channel and then evaluates the value of , . It is possible, because is not password protected.
- insert and inputs and imprints .
- computes , and . Then, it verifies if . It would be true i.e., both the password and bio-metric verification would be correct.
- Afterwards, sends the login message to via a public channel. However, the adversary intercepts the message and replaces with .
- Since is valid, therefore generates a random challenge R and send it to .
- select the login sensor node and sends to .
- After receiving , decrypt it using and verifies the validity of and R. Subsequently, computes and finally sends to the sensor node
- After receiving , computes and sends to
- Then, computes using , stolen bio-metric and evaluated K. It is possible because has no password protection.
- Finally, computes and the session key shared with .
4.3. Review of Choi et al.’s Scheme
- Step CR1:
- The user inputs his/her identity , biometric information and computes: . Then, transmits to via secure communication channel.
- Step CR1:
- After receiving the message , the gateway node generates 1024 bit secret key x and computes , Then, stores into smart card . Finally, sends the smart card to the user
- Step CR2:
- After receiving the smart card , the user stores into .
4.4. Cryptanalysis of Choi et al.’s Scheme
4.4.1. Attack Based on Legitimate User
- inputs , imprints , computes , , and finally verifies
- If verification succeeds, generate random number and computes
- intercepts the message of and find out:
- Therefore, we find that Choi et al. scheme does not provide user anonymity i.e., an adversary can compute user ’s identification . However, Choi et al. claimed that their protocol provides user anonymity.
- Furthermore intercepts the cipher text and derives the plain-text , therefore Choi et al. scheme is vulnerable to known plain-text attack.
4.4.2. User Impersonation Attack
- extracts from the smart card of the user and computes and verify the computed with the stored .
- generates a random number , calculates ,. Find out the current timestamps , computes , , , .
- sends the message to . Subsequently, establishes the session key with using Steps 2–4 of authentication and session key establishment phase of Choi et al. protocol.
4.5. Review of Park et al.’s Scheme
4.6. Cryptanalysis of Park et al.’s Scheme
4.6.1. Sensor Node Impersonation Attack
- The adversary intercepts the message and
- Then, generates a random number , finds current times-stamp and computes: Query response and .
- Afterwards, sends to .
- After receiving , computes: If , computes
4.6.2. User Impersonation Attack
- First, the adversary extract the information from the smart card.
- Then, imprints its biometric information and computes and , .
- Afterwards, generates random number , selects an identity and computes: and . Finally, sends to
- After receiving , if , computes
- If , the finds the current time stamp and computes:
- Finally, sends to
- After receiving , if and , computes: and
- If , generates a random number and computes: Query Response,
- Then, sends to the adversary
- After receiving , if the adversary computes: If , computes and establishes the session key with sensor node Therefore, Park et al.’s scheme is vulnerable to user impersonation attack. Similar attack is possible in Moon et al.’s scheme [23] also, since the value of in Moon et al.’s scheme can be evaluated using and .
5. Proposed Protocol
5.1. Set-Up before the Deployment of WSNs/IoT
5.2. Registration of by the Using Secure Communication Channel
- Step R1:
- A legitimate user selects her identity , password and inputs his/her biometric information into the generator function which generates a secret information and a public reproduction parameter . Then, calculates using secure hash function and sends to the gateway node
- Step R2:
- generates a secret key x, selects a generator point P of G with order q and computes:(where “×” is the scalar multiplication operator of elliptic curve),Finally, the gateway node stores the value of into the smart card and sends to the user .
- Step R3:
- After receiving the from , the user stores function and the values of into .
5.3. User Authentication and Session Key Establishment Phase
- Step A1:
- inputs , imprints her noisy biometric information and computes using reproduction function of fuzzy extractor as described in Definition 4. Then, calculates , , .If the equivalent condition does not fulfill; abort the protocol. Otherwise, evaluates generates a random number . and find out her current time stamp . Then, the user calculates , (where “×” is the scalar multiplication operator of elliptic curve) and encrypts the message considering as a symmetric key to find: . Finally, Construct a message and sends to the gateway node .
- Step A2:
- After receiving the message , the gateway node compute and decrypts the cipher text considering as a symmetric key to find: And if the condition does not fulfill; the aborts the protocol. Otherwise, the gateway node generates a random number and calculates the session key (where “×” is the scalar multiplication operator of elliptic curve). Then, the gateway node finds its current time-stamp and calculates: , Finally, construct the message and sends to the sensor node .
- Step A3:
- After receiving the message , decrypts the cipher text using symmetric key to find out: If the condition fulfills, stores the session key and finally transmits to
- Step A4:
- After receiving the message , the user decrypts the message considering as a symmetric key and find out: Once the condition fulfills, the user establishes the session key with . Where based on problem.
5.4. User’s Credential Update Phase
6. Security Analysis:
6.1. Informal Analysis
6.2. Formal Security Analysis
6.2.1. Formal Security Verification Using Random Oracle Model
| Algorithm 1: |
 |
6.2.2. Verification Using Scyther tool
- Guaranteed termination, after which the result is either unbounded correctness, falsification, or bounded correctness.
- Efficient generation of a finite representation of an infinite set of traces concerning patterns, also known as a complete characterization.
- State-of-the-art performance, which has made new types of protocol analysis feasible, such as multi-protocol analysis.
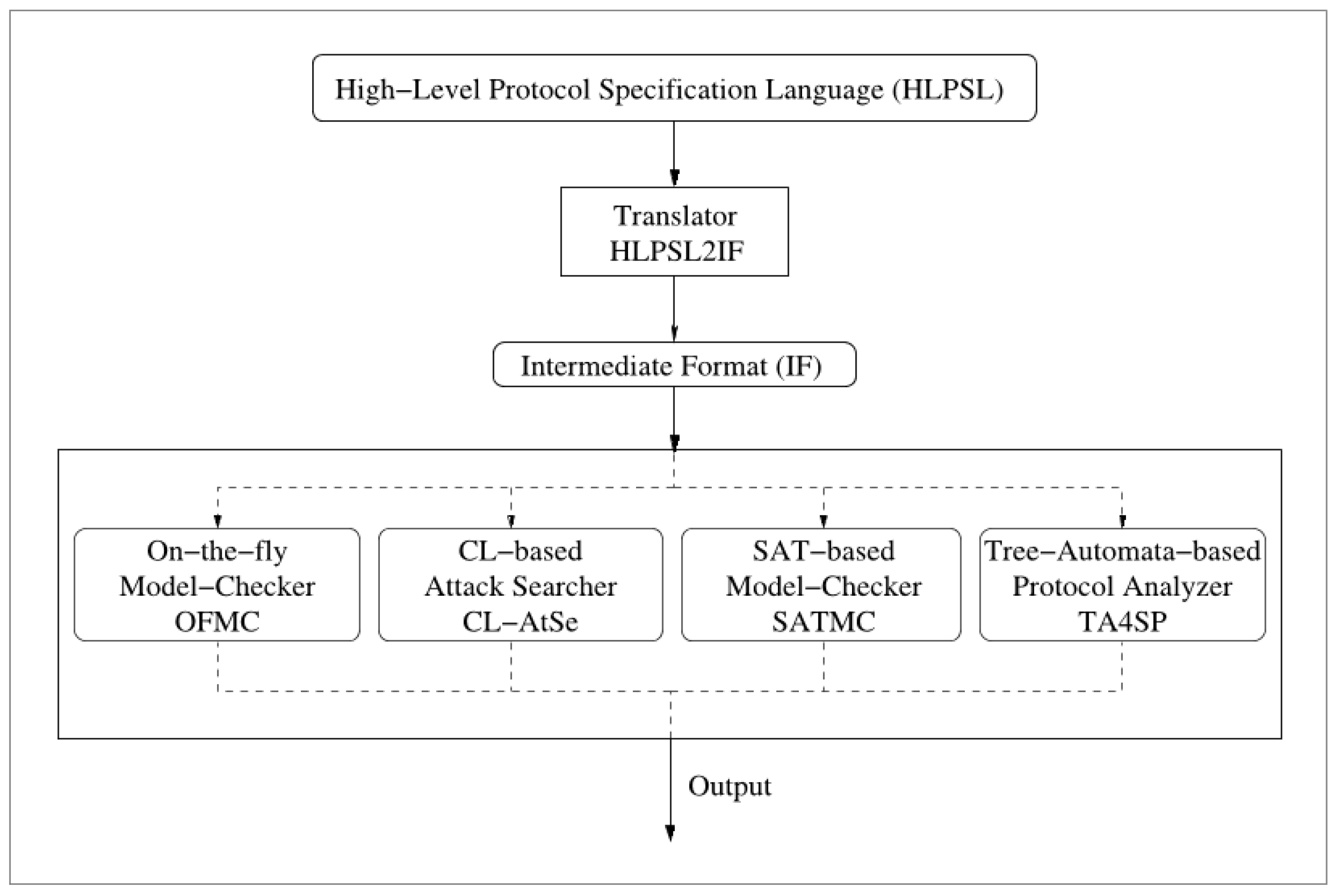
6.3. Verification Using AVISPA Tool
6.3.1. Experimental Setup and the Size of the Entities Involved in WSNs/IoT for the Simulation of Proposed Protocol Using AVISPA Tool
6.3.2. Basic Features of AVISPA Tool
- On-the-fly model-checker (OFMC)
- Constraint-logic based attack searcher (CL-AtSe)
- SAT-based model-checker (SATMC)
- Tree automata based on automatic approximation for the analysis of security protocols (TA4SP).
6.4. Implementation of the Proposed Protocol Using HLPSL
- Basic Role: Basic role explains the activity of the entities (e.g., User , Gateway and Sensor node ) involve in the protocol.
- Each role may have some parameter like , , of type agent and Kui1, Kgsnj of type symmetric_key.
- The parameter RCV and SND denotes the agent’s communication channels for receiving and sending the information.
- The parameter (dy) represents the Dolev-Yao intruder model for the channel.
- The function H, Gen, Rep, EccMul, Enc, Dec and XOR corresponding to the hash function, fuzzy extractor’s generator, fuzzy extractor’s reproduction, elliptic curve scalar multiplication, encryption, decryption and logical XOR operations respectively.
- The term hash_func represents all the functions which are not easily invertible because the random non-invertible arithmetic operators are not supportable in HLPSL.
- The term “played_by ” denotes that the role User is played by .
- Transitions: The transitions are declared in steps. It consist of trigger which fires when an event occurs. For any States in a transition if a message received on channel RCV, then transition fires and allocates a new value to the State.
- Composed Roles: It makes one or more basic roles to execute together and represent the sessions involve in the protocol. The operator ∧ represents the parallel execution of the roles.The HLPSL specification of proposed protocol’s session is shown in Table 17.
- Environment: It consist of global constant and session composition, where the adversary may execute some role as a authorized user.The HLPSL specification of proposed protocol’s environment is shown in Table 18.
- Security Goal: This module specifies the security Goal of the protocol. Some important predicates used in this module are as follows:
- secret({PWi,Bi,SIGi’}, sub1, Ui): It indicates that the information {PWi,Bi,SIGi’} is secretly shared to and it can be recognize with a constant identity in goal section.
- witness(Ui, GWN, gateway_user_gu, Tui,Alpha’): It represents the weak authenticity of by and is the witness for the data {Tui’, Alpha’}. The identity of this goal is represented as in goal section.
- request(Ui,SNj, user_sensor_us, Skey’): It represents the strong authenticity of by on Skey with an identity user_sensor_us.
- Symbols: Concatenation (.) is used for message composition (e.g., SND (IDi.PBi’)) and Commas (,) is used in case of multiple arguments of events or functions (e.g., secret(PWi,Bi,SIGi’, sub1, Ui)).
6.5. Description of the Output Format Generated by AVISPA Tool
- Summary: This section specifies the security reliability of the protocol regarding safe, unsafe or inconclusive.
- Details: In this portion, the output specifies the environment and the context under which the protocol is claimed to be safe, unsafe or inconclusive.
- Protocol: It indicates the name of the protocol given as an input for security verification.
- Goal: This section represents the specified security goal of the protocol.
- Backend: This section represents one of the four back-ends used for the analysis of the protocol.
6.5.1. Logical Verification Using BAN Logic
- Rule 1
- Message meaning rule: . That is, if believes that she shared the key K with , and sees the message encrypted with key K, believes that once said S.
- Rule 2
- Nonce verification rule: . That is, if believes S is fresh and once said S, believes believes S.
- Rule 3
- Jurisdiction rule: . That is, if believes that had jurisdiction right to S and believes believes S, believes S.
- Message 1
- Message 2
- Message 3
- Derivation of user ’s trusts on the truth of secret information .That is, if believes that has jurisdiction over then trusts on the truth of Therefore, we achieve Goal 1.
- Derivation of sensor node ’s trusts on the truth of secret informationThat is, if sensor node believes that the gateway node has jurisdiction over then trusts on the truth of Therefore, we achieve Goal 2.
- Verification of freshness of user’s time-stamp on the gateway node (using message-meaning and nonce verification rule):
- (Based on message-meaning rule)
That is, if believes the secret is shared with and sees , then believes once said- (Based on nonce verification rule)
That is, if believes that the time-stamp is fresh and once said , then believes believes Therefore, we achieve Goal 3. - Verification of freshness of gateway node’s time-stamp on the sensor node (using message-meaning and nonce verification rule):
- (Based on message-meaning rule)
That is, if believes the secret is shared with and sees , then believes once said- (Based on nonce-verification rule)
That is, if believes that the time-stamp is fresh and once said , then believes believes Therefore, we achieve Goal 4. - Verification of freshness of gateway node’s time-stamp on user (using message-meaning and nonce verification rule):
- (Based on message-meaning rule)
That is, if believes the secret is shared with and sees , then believes once said- (Based on nonce-verification rule)
That is, if believes that the time-stamp is fresh and once said , then believes believes Therefore, we achieve Goal 5. - Verification of sensor node’s identity on the gateway node :
- (Based on message-meaning rule)
That is, if believes the secret is shared with and sees , then believes once said Therefore, we achieve Goal 6. - Verification of user’s identity on the sensor node :
- (Based on message-meaning rule)
That is, if believes the secret is shared with and sees , then believes once said Therefore, we achieve Goal 7. - Verification of the public key by user :
- (Based on message-meaning rule)
That is, if believes the secret is shared with and sees , then believes once said Therefore, we achieve Goal 8.
7. Comparative Study Based on Security Features and Computational Overhead
7.1. Relative Security Analysis
7.2. Relative Performance Based on Computational Cost
8. Comprehensive Analysis and Lessons Learnt
9. Conclusions and Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: A Survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Ashton, K. That ‘Internet of Things’ Thing. In the real world, things matter more than ideas. RFID J. 2009. Available online: http://www.rfidjournal.com/articles/view?4986 (accessed on 27 October 2017).
- Benenson, Z.; Gartner, F.; Kesdogan, D. User authentication in sensor networks. In Proceedings of the Workshop Sensor Networks, Lecture Notes Informatics Proceedings Informatik, Ulm, Germany, 2004; pp. 385–389. [Google Scholar]
- Watro, R.; Kong, D.; Cuti, S.F.; Gardiner, C.; Lynn, C.; Kruus, P. TinyPK: Securing Sensor Networks with Public Key Technology. In ACM Workshop on Security of Ad Hoc and Sensor Networks; ACM Press: Washington, DC, USA, 2004; pp. 59–64. [Google Scholar]
- Benenson, Z.; Gedicke, N.; Raivio, O. Realizing robust user authentication in sensor networks. In Proceedings of the Workshop on Real-World Wireless Sensor Network (REALWSN’05), Stockholm, Sweden, 20–21 June 2005. [Google Scholar]
- Wong, K.H.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the 2006 IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, Taichung, Taiwan, 5–7 June 2006; pp. 1–9. [Google Scholar]
- Tseng, H.R.; Jan, R.H.; Yang, W. An improved dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM’07), Washington, DC, USA, 26–30 November 2007; pp. 9869–9890. [Google Scholar]
- Lee, T.H. Simple Dynamic User Authentication Protocols for Wireless Sensor Networks. In Proceedings of the Second International Conference on Sensor Technologies and Applications, Cap Esterel, France, 25–31 August 2008; pp. 657–660. [Google Scholar]
- Ko, L.C. A Novel Dynamic User Authentication Scheme for Wireless Sensor Networks. In Proceedings of the IEEE International Symposium on Wireless Communication Systems (ISWCS ’08), Reykjavik, Iceland, 21–24 October 2008; pp. T608–T612. [Google Scholar]
- Vaidya, B.; Silva, J.S.; Rodrigues, J.J. Robust Dynamic User Authentication Scheme for Wireless Sensor Networks. In Proceedings of the 5th ACM Symposium on QoS and Security for Wireless and Mobile Networks (Q2SWinet 2009), Tenerife, Spain, 26–30 October 2009; pp. 88–91. [Google Scholar]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and Security Improvements of “Two-factor User Authentication in Wireless Sensor Networks”. Sensors 2010, 10, 2450–2459. [Google Scholar] [CrossRef] [PubMed]
- Yuan, J.; Jiang, C.; Jiang, Z. A biometric-based user authentication for wireless sensor networks. Wuhan Univ. J. Nat. Sci. 2010, 15, 272–276. [Google Scholar] [CrossRef]
- Yoo, S.G.; Park, K.Y.; Kim, J. A Security-performance-balanced User Authentication Scheme for Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2012, 8, 1–11. [Google Scholar] [CrossRef]
- Xue, K.; Ma, C.; Hong, P.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Lu, X.; Tian, Y. An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-Peer Netw. Appl. 2014. [Google Scholar] [CrossRef]
- Das, A.K. A secure and effective biometric-based user authentication scheme for wireless sensor networks using smart card and fuzzy extractor. Int. J. Commun. Syst. 2015. [Google Scholar] [CrossRef]
- Althobaiti, O.; Al-Rodhaan, M.; Al-Dhelaan, A. An efficient biometric authentication protocol for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2013, 8, 1–13. [Google Scholar] [CrossRef]
- Sharaf-Dabbagh, Y.; Saad, W. On the Authentication of Devices in the Internet of Things. In Proceedings of the 17th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Coimbra, Portugal, 21–24 June 2016. [Google Scholar]
- Alizadeh, M.; Abolfazli, S.; Zamani, M.; Baharun, S.; Sakurai, K. Authentication in mobile cloud computing: A survey. J. Netw. Comput. Appl. 2016, 61, 59–80. [Google Scholar] [CrossRef]
- Choi, Y.; Lee, Y.; Won, D. Security improvement on biometric based authentication scheme for wireless sensor networks using fuzzy extraction. Int. J. Distrib. Sens. Netw. 2016, 12, 1–16. [Google Scholar] [CrossRef]
- Park, Y.; Park, Y. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
- Moon, J.; Lee, D.; Lee, Y.; Won, D. Improving Biometric-Based Authentication Schemes with Smart Card Revocation/Reissue for Wireless Sensor Networks. Sensors 2017, 17, 940. [Google Scholar] [CrossRef] [PubMed]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology-CRYPTO 99, LNCS, Santa Barbara, California, USA, 15–19 August 1999; Springer: Berlin, Germany, 1999; Volume 1666, pp. 388–397. [Google Scholar]
- Stinson, D.R. Some observations on the theory of cryptographic hash functions. Des. Codes Cryptogr. 2006, 38, 259–277. [Google Scholar] [CrossRef]
- Miller, V.S. Use of elliptic curves in cryptography. In Advances in Cryptology-CRYPTO 85; Lecture Notes in Computer Sciences; Springer-Verlag New York, Inc.: New York, NY, USA, 1986; pp. 417–426. [Google Scholar]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Advances in Cryptology (Eurocrypt 04), Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin, Germany, 2004; pp. 523–540. [Google Scholar]
- Yoon, E.J.; Kim, C. Advanced biometric-based user authentication scheme for wireless sensor networks. Sens. Lett. 2013, 11, 1836–1843. [Google Scholar] [CrossRef]
- Chang, I.P.; Lee, T.F.; Lin, T.H.; Liu, C.M. Enhanced two-factor authentication and key agreement using dynamic identities in wireless sensor networks. Sensors 2015, 15, 29841–29854. [Google Scholar] [CrossRef] [PubMed]
- Cremers, C. Scyther-Semantics and Verification of Security Protocols. Ph.D. Thesis, Eindhoven University of Technology, Eindhoven, The Netherlands, 2006. [Google Scholar]
- AVISPA Tool. Available online: http://www.avispa-project.org/ (accessed on 11 July 2017).
- Bellare, M.; Rogaway, P. Random oracles are practical: A paradigm for designing efficient protocols. In Proceedings of the First Annual Conference Computer and Communications Security, Fairfax, VA, USA, 3–5 November 1993; pp. 62–73. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. Proc. R. Soc. Lond. 1989, 426, 233–271. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Karati, A.; Biswas, G.; Khan, M.K. A standard mutual authentication protocol for cloud computing based health care system. J. Med. Syst. 2017, 41, 50. [Google Scholar] [CrossRef] [PubMed]
- Chiou, S.Y.; Ying, Z.; Liu, J. Improvement of a privacy authentication scheme based on cloud for medical environment. J. Med. Syst. 2016, 40, 1–15. [Google Scholar] [CrossRef] [PubMed]
- TinyOS: An Open-Source OS for the Networked Sensor Regime. Available online: http://www.tinyos.net/ (accessed on 13 July 2017).
- Gay, D.; Levis, P.; Von Behren, R.; Welsh, M.; Brewer, E.; Culler, D. The nesc language: A holistic approach to networked embedded systems. ACM SIGPLAN Not. 2003, 38, 1–11. [Google Scholar] [CrossRef]
- Lee, J.; Kapitanova, K.; Son, S. The price of security in wireless sensor networks. Comput. Netw. 2010, 54, 2967–2978. [Google Scholar] [CrossRef]
- Eastlake, D., 3rd; Jones, P. US Secure Hash Algorithm 1 (SHA 1). Available online: https://www.rfc-editor.org/rfc/rfc3174.txt (accessed on 25 October 2017).
- Liu, Z.; Wenger, E.; Johann, G. MoTE-ECC: Energy-scalable elliptic curve cryptography for wireless sensor networks. In Applied Cryptography and Network Security—ACNS 2014, LNCS, Proceedings of the 12th International Conference, ACNS 2014, Lausanne, Switzerland, 10–13 June 2014; Springer: Cham, Switzerland, 2014; Volume 8479, pp. 361–379. [Google Scholar]

| Notations | Explanation |
|---|---|
| Two large prime numbers | |
| A finite field of characteristic p | |
| E | Elliptic curve over |
| G | Group of points on E |
| P | Generator point on E with order q |
| ith User of WSNs/IoT | |
| The identity of | |
| nth sensor node | |
| Password of | |
| The identity of | |
| ’s Smart card | |
| The gateway node | |
| x | Random number |
| Secure hash function | |
| Fuzzy generator function | |
| Fuzzy reproduction function | |
| Set of positive integers | |
| Bio-metric information of | |
| The error tolerance limit | |
| Maximum transmission delay | |
| Current time at and | |
| Symmetric encryption of message s using key k | |
| Symmetric decryption of using key k | |
| Concatenation operator | |
| ⊕ | Bitwise XOR operator |
| × | Point multiplication operator of E |
| Adversary |
| Step 1: For User | Step 2: For Gateway |
| The user inputs and and generates 1024 bit random number K. Subsequently, calculates and selects a key Then, | After receiving the message , the gateway node generates 1024 bit key , evaluates and stores into Then, stores related to |
| Step 3: For User | |
| evaluates , and Then, replaces with in . Finally, stores into . |
| Step 1: For User | Step 2: For Gateway |
 | |
| Step 3: For User | Step 4: For Gateway |
 | |
| Step 5: For Sensor Node | Step 6: For User |
 | |
| Step 1: For User | Step 2: For Gateway |
 | |
| Step 3: For Sensor Node | Step 4: For User |
 | |
| Step 1: For User | Step 2: For Gateway |
| selects the identity , imprints bio-metric information and computes: | computes 1024 bit secret key x and Computes: , Store into smart card . |
| Step 3: For User | |
| Inputs into the smart card |
| Step 1: For User | Step 2: For Gateway |
 | |
| Step 3: For Sensor Node | Step 4: For User |
 | |
| Step 1: For User | Step 2: For Gateway |
| inputs and Computes: | computes 1024 bit secret key x and Computes: , BUi = h(IDUi || PBi ||h(IDUi ⊕ x)), WUi = h(IDUi || PBi) ⊕ KUi stores the value of into |
| Step 3: For User () | |
| stores and the value of into . |
| Step 1: For User | Step 2: For Gateway |
 | |
| Step 3: For Sensor Node | Step 4: For User |
 | |
 |
| hashfunction h; /*Secure hash function */ const XOR: Function; /*XOR operation */ const Concat: Function; /*Concatenation Function */ const EccMul: Function; /*Scalar Point Multiplication Operation of ECC */ const Gen: Function; /*Generator function of Fuzzy Extractor*/ const Rep: Function; /*Reproduction function of Fuzzy Extractor*/ const Enc: Function; /*Encryption Function*/ const Dec: Function; /*Decryption Function*/ /*IDui, PWui, Bi represents the identity, password and bio-metric information of the user Ui respectively.Kgsnj denotes the secret key shared between sensor and gateway node. Tui, Tgwn denotes the current time-stamp of user, gateway respectively. Rui and Rsnj represents the random number generated at user Ui and sensor node SNj respectively. */ protocol Protocol(Ui, GWN, SNj) { macro SIGi = Gen(Bi); /*macro defines abbreviations for particular term */ macro PBi = h(Concat (PWui, SIGi)); macro SIGi’ = Rep(Bi’, TAUi); macro PBi’ = h(Concat(PWui, SIGi’)); macro Kui = EccMul(h(Concat(IDui,x)),P); macro Aui = XOR(PBi, h(XOR(IDui,x))); macro Bui = h(Concat(IDui,PBi,h(XOR(IDui,x)))); macro Wui = XOR(h(Concat(IDui,PBi)), Kui); macro Xui = EccMul(Rui, P); macro Xui’= EccMul(Rui, Kui); macro Ysnj = EccMul(Rsnj,P); macro sk = EccMul(Rui, Ysnj); macro Alpha = Enc(Xui’, Concat(IDsnj,Tui)); macro Alpha’ = Dec(Xui’, Enc(Xui’, Concat(IDsnj,Tui))); macro Beta = Enc(Xui’, Concat(IDsnj,Ysnj,Tgwn)); macro Beta’ = Dec(Enc(Xui’, Concat(IDsnj,Ysnj,Tgwn))); macro Gamma = Enc(Kgsnj, Concat(IDui,sk,Beta,Tgwn)); macro Gamma’ = Dec(Enc(Kgsnj, Concat(IDui,sk,Beta,Tgwn))); |
| role Ui { var Tsnj,Tgwn: Nonce; fresh Tui: Nonce; /*Time-stamp Tui is freshly generated */ const IDui, PWui, Bi, Bi’, PBi, IDsnj, Rui, Rsnj, Kgsnj, Xui, Xui’, x, Tui,Tgwn,P,TAUi: Ticket; send_1(Ui, GWN, IDui, PBi); /*Ui sends IDui, PBi to GWN */ recv_2(GWN, Ui,P,Aui,Bui,Wui); /*Ui received P,Aui,Bui,Wui from GWN */ send_3(Ui, GWN, Xui, Alpha); recv_5(SNj, Ui, Beta); match(Beta’, Beta); /*Test the equality of Beta’ and Beta */ claim_Ui1(Ui,Secret,Bi); /*Bi should be secret for Ui */ claim_Ui2(Ui,Secret,PWui); claim_Ui3(Ui,Secret,x); claim_Ui4(Ui,Secret,Xui’); claim_Ui5(Ui,Secret,Tui); claim_Ui6(Ui,SKR,sk); /*Session key sk should be secret */ claim_Ui7(Ui,Niagree); /*Non-injective agreement */ claim_Ui78(Ui,Nisynch); /*Non-injective synchronization */ } |
| role GWN |
| { |
| fresh Tgwn: Nonce; |
| var Tui: Nonce; |
| const IDui, PWui, IDsnj, Bi, P, x, Rui, Tui, Bi, PWui: Ticket; |
| recv_1(Ui, GWN, IDui, IPBi); |
| send_2(GWN, Ui, P,Aui, Bui, Wui); |
| recv_3(Ui, GWN, IDui, IDsnj, Xui, TSui, Alpha); |
| match (Alpha, Alpha’); |
| send_4(GWN, SNj, Beta, Gamma, Xui, TGgwn, TUgwn); |
| claim_GWN1(GWN,Secret,Tgwn); |
| claim_GWN2(GWN,Secret,x); |
| claim_GWN3(GWN,Secret,k(GWN,SNj)); |
| claim_GWN4(GWN,Secret,Kui); |
| claim_GWN5(GWN,Secret,Xui’); |
| } |
| role SNj |
| { |
| var Tgwn: Nonce; |
| fresh Tsnj: Nonce; |
| const IDui, IDsnj, x,Rui, Tui, P, Bi, PWui, Rsnj: Ticket; |
| recv_4(GWN, SNj, Beta, Gamma, Xui, TGgwn, TUgwn); |
| match(Beta, Beta’); |
| send_5(SNj, Ui, Delta, Gamma, Ysnj, Tsnj, TUgwn); |
| claim_SNj1(SNj,Secret,Tgwn); |
| claim_SNj2(SNj, Secret, Rsnj); |
| claim_SNj3(SNj, Secret, Tsnj); |
| claim_SNj4(SNj,Secret,k(GWN,SNj)); |
| claim_SNj5(SNj,SKR,h(EccMul(Rsnj,Xui))); |
| } } |
| role user(Ui, GWN, SNj: agent, |
| Xui1, Kgsnj: symmetric_key, |
| H,Gen, Rep, EccMul, Enc, Dec, XOR: hash_func, |
| SND, RCV: channel(dy)) |
| played_by Ui def= |
| local |
| State: nat, |
| IDui, IDsnj, PWui, Bi, Bi1, SIGi, SIGi1, TAUi, PBi, PBi1, P, Kui1, Rui, Aui, Bui, Wui, Alpha, Beta, Gamma, Ysnj, Ysnj1, Tui, Tgwn, Xui, X, Beta1, Kui, Rsnj, Gamma1, Skey, Skey1: text |
| const sub1, sub2, sub3, sub4, sub5, sub6, sub7, sub8, |
| gateway_sensor_gs, gateway_user_gu, user_sensor_us: protocol_id |
| init |
| State: = 0 |
| transition |
| 0. State = 0 ∧ RCV (start) |
| State’: = 2 ∧ SIGi’: = Gen(Bi) |
| ∧ PBi’: = H(PWui.SIGi’) |
| ∧ secret(PWui,Bi,SIGi’, sub1, Ui) |
| ∧ SND (IDui.PBi’) |
| 2. State = 2 ∧ RCV (P.Aui’.Bui’.Wui’) |
| State’: = 5 ∧ Rui’: = new() |
| ∧ Tui’: = new() |
| ∧ secret(Rui’, sub2, Ui) |
| ∧ SIGi1’: = Rep(Bi1.TAUi) |
| ∧ PBi1’: = H(PWui.SIGi1’) |
| ∧ Kui1’: = XOR(Wui, H(IDui.PBi1’)) |
| ∧ Xui’: = EccMul(Rui’.P) |
| ∧ Xui1’: = EccMul(Rui’.Kui1’) |
| ∧ secret(Xui1’, sub3, Ui, GWN) |
| ∧ Alpha’: = Enc(IDsnj.Tui) |
| ∧ SND(IDui.Xui’.Alpha’) |
| ∧ witness(Ui, GWN, gateway_user_gu, Tui,Alpha’) |
| 6. State = 5 ∧ RCV(Beta1’) |
| State’: = 6 ∧ Ysnj1’: = Dec(Beta1’) |
| ∧ Skey’: = EccMul(Rui’.Ysnj1’) |
| ∧ request(Ui,SNj, user_sensor_us, Skey’) |
| end role |
| role gateway(Ui, GWN, SNj: agent, |
| Xui1, Kgsnj: symmetric_key, |
| H,Gen, Rep, EccMul, Enc, Dec, XOR: hash_func, |
| SND, RCV: channel(dy)) |
| played_by GWN def= |
| local |
| State: nat, |
| IDui, IDsnj, PWui, Bi, Bi1, SIGi, SIGi1, TAUi, PBi, PBi1, P, Kui1, Rui, Aui, Bui, Wui, Alpha, Beta, Gamma, Ysnj, Tui, Tgwn, Xui, X, Beta1, Kui, Rsnj, Gamma1, Skey, Skey1: text |
| const sub1, sub2, sub3, sub4, sub5, sub6, sub7, sub8, |
| gateway_sensor_gs, gateway_user_gu, user_sensor_us: protocol_id |
| init |
| State: = 1 |
| transition |
| 1. State = 1 ∧RCV (IDui.PBi’) |
| State’: = 3 ∧ X’: = new() |
| ∧ Kui’: = EccMul(H(IDui.X’).P) |
| ∧ Aui’: = XOR(PBi’.H(XOR(IDui.X’))) |
| ∧ Bui’: = H(IDui.PBi’.XOR(IDui.X’)) |
| ∧ secret(X’,sub4, GWN) |
| ∧ Wui’: = XOR(H(IDui.PBi).Kui’) |
| ∧ secret(Kui’, sub5, GWN,Ui) |
| ∧ SND(P.Aui’.Bui’.Wui’) |
| 3. State = 3 ∧ RCV(IDui.Xui’.Alpha’) |
| State’: = 4 ∧ Tgwn’: =new() |
| ∧request(GWN, Ui, gateway_user_gu, Alpha’) |
| ∧ IDsnj’: = Dec(Alpha’) |
| ∧ Rsnj’: = new() |
| ∧ Ysnj’: = EccMul(Rsnj’.P) |
| ∧ Beta’: = Enc(IDsnj’.Ysnj’.Tgwn) |
| ∧secret(Kgsnj, sub6, GWN,SNj) |
| ∧Gamma’: = Enc(IDui.Skey’.Beta’.Tgwn’) |
| ∧ SND(Gamma’) |
| ∧ witness(GWN, Ui, gateway_user_gu, Tgwn’) |
| end role |
| role sensor(Ui, GWN, SNj: agent, |
| Xui1, Kgsnj: symmetric_key, |
| H,Gen, Rep, EccMul, Enc, Dec, XOR: hash_func, |
| SND, RCV: channel(dy)) |
| played_by SNj def= |
| local |
| State: nat, |
| IDui, IDsnj, PWui, Bi, Bi1, SIGi, SIGi1, TAUi, PBi, PBi1, P, Kui1, Rui, Aui, Bui, Wui, Alpha, Beta, Gamma, Ysnj, Tui, Tgwn, Xui, X, Beta1, Kui, Rsnj, Gamma1, Skey, Skey1: text |
| const sub1, sub2, sub3, sub4, sub5, sub6, sub7, sub8, |
| gateway_sensor_gs, gateway_user_gu, user_sensor_us: protocol_id |
| init |
| State: = 4 |
| transition |
| 4. State = 4 ∧RCV (Gamma’) |
| State’: = 5∧ Skey1’: = Dec(Gamma’.Kgsnj) |
| ∧ secret(Skey1’, sub7, SNj) |
| ∧ Beta1’: = Dec(Gamma’) |
| ∧ secret(Skey1’, sub8, SNj) |
| ∧ SND(Beta1’) |
| end role |
| role session(Ui,GWN,SNj:agent, |
| Xui1, Kgsnj:symmetric_key, |
| H,Gen, Rep, EccMul, Enc, Dec, XOR: hash_func) |
| def= |
| local GWNUi,RUi,GWNSNj,RSNj,GWNGWN,RGWN:channel(dy) |
| composition |
| user(Ui, GWN, SNj, Xui1,Kgsnj,H,Gen, Rep, EccMul, Enc, Dec,XOR,GWNUi, RUi) |
| ∧ sensor(Ui, GWN, SNj,Xui1, Kgsnj, H,Gen, Rep, EccMul, Enc, Dec, XOR,GWNSNj, RSNj) |
| ∧ gateway(Ui, GWN, SNj, Xui1, Kgsnj,H,Gen, Rep, EccMul, Enc, Dec, XOR, GWNGWN,RGWN) |
| end role |
| role environment() |
| def= |
| const ui, gwn, snj: agent, |
| xui1,kgsnj,kig: symmetric_key, |
| h,gen, rep, eccMul, enc, dec, xOR: hash_func, |
| sub1, sub2, sub3, sub4, sub5, sub6, sub7, sub8, |
| gateway_sensor_gs, gateway_user_gu, user_sensor_us: protocol_id |
| intruder_knowledge = ui,gwn,snj,kig |
| composition |
| session(ui,snj,gwn,xui1,kig,h,gen, rep, eccMul, enc, dec, xOR) |
| ∧ session(ui,snj,gwn,kgsnj,kig,h,gen, rep, eccMul, enc, dec, xOR) |
| ∧ session(ui,snj,gwn,kig,kgsnj,h,gen, rep, eccMul, enc, dec, xOR) |
| end role |
| goal |
| secrecy_of sub1, sub2, sub3, sub4, sub5, sub6, sub7, sub8 |
| authentication_on gateway_sensor_gs, gateway_user_gu, user_sensor_us |
| end goal |
| environment() |
| Using OFMC BACKEND | Using CL-AtSe BACKEND |
|---|---|
 | |
| Notations | Description |
|---|---|
| Principals like and | |
| S | Statements like etc. |
| K | Secret key or secret informations like |
| believes S, or believes S is true. | |
| has received a information containing S and it can read or repeat S | |
| once said S. sent a data containing S and it could be a fresh or old data. | |
| has jurisdiction over S. That is ’s beliefs about S should be trusted | |
| The information S is fresh and it has not been sent before. | |
| S is a secret data and it is only known to or and perhaps to the trusted principals | |
| is a secret and its presence gives the identity of whoever generates |
|
|
|
|
| Security Feature | A.K.Das [17] | Choi et al. [21] | Park et al. [22] | Moon et al. [23] | Proposed Protocol |
|---|---|---|---|---|---|
| Resist stolen smart card attack | No | No | No | No | Yes |
| Resists Replay attack | Yes | Yes | No | Yes | Yes |
| Resists Man-in-the-middle attack | No | No | No | Yes | Yes |
| Resists user impersonation attack | No | No | No | Yes | Yes |
| Resists sensor impersonation attack | No | No | No | Yes | Yes |
| Resists insider attack | Yes | Yes | Yes | Yes | Yes |
| Offers mutual authentication | Yes | Yes | Yes | Yes | Yes |
| Offers biometric data updating | Yes | Yes | Yes | Yes | Yes |
| Offers secure password updating | No | No | No | Yes | Yes |
| Offers formal security analysis | Yes | Yes | Yes | Yes | Yes |
| Notation | Operation | Time Taken (in ) |
|---|---|---|
| One-way cryptographic hash function | 0.5 | |
| Elliptic curve point multiplication | 50.3 | |
| Fuzzy extractor used in biometric verification | 0.5 | |
| Symmetric key encryption/decryption | 8.7 |
| Function | Time (in ) | Energy (in ) |
|---|---|---|
| Symmetric Encryption and Decryption (AES-128) [39] | 5.05 | 121.2 |
| Hashing (SHA-1) [40] | 3.63 | 87.12 |
| Elliptic curve Fixed Point Multiplication (MoTE ECC-160) [41] | 370 | 8880 |
| Scheme | Registration Phase Time (in ) | Authentication and Session Key Establishment Phase Time (in ) | |||
|---|---|---|---|---|---|
| A.K.Das [17] | |||||
| Choi et al. [21] | |||||
| Park et al. [22] | |||||
| Moon et al. [23] | |||||
| Proposed Protocol | |||||
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Maurya, A.K.; Sastry, V.N. Fuzzy Extractor and Elliptic Curve Based Efficient User Authentication Protocol for Wireless Sensor Networks and Internet of Things. Information 2017, 8, 136. https://doi.org/10.3390/info8040136
Maurya AK, Sastry VN. Fuzzy Extractor and Elliptic Curve Based Efficient User Authentication Protocol for Wireless Sensor Networks and Internet of Things. Information. 2017; 8(4):136. https://doi.org/10.3390/info8040136
Chicago/Turabian StyleMaurya, Anup Kumar, and V. N. Sastry. 2017. "Fuzzy Extractor and Elliptic Curve Based Efficient User Authentication Protocol for Wireless Sensor Networks and Internet of Things" Information 8, no. 4: 136. https://doi.org/10.3390/info8040136




