Unix Domain Sockets Applied in Android Malware Should Not Be Ignored
Abstract
:1. Introduction
2. Background
2.1. Android App Overview
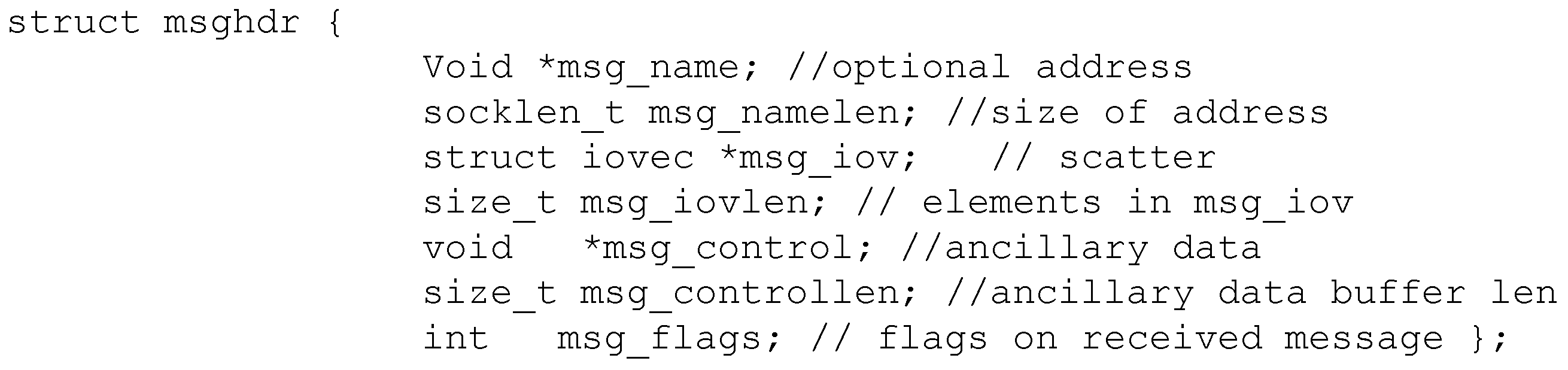
2.2. Unix Domain Sockets
2.3. Related Work
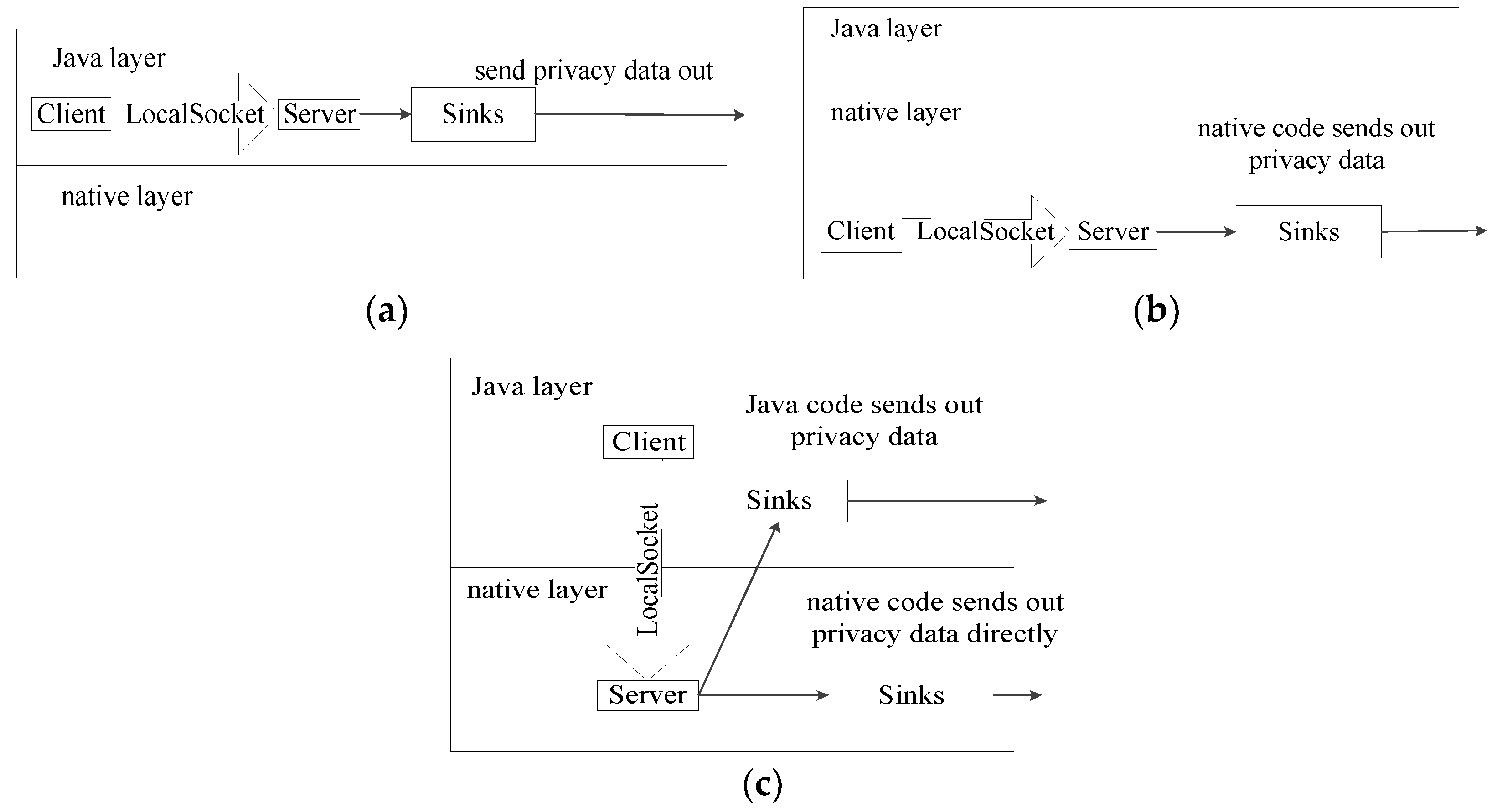
2.4. Threat Model and Assumptions
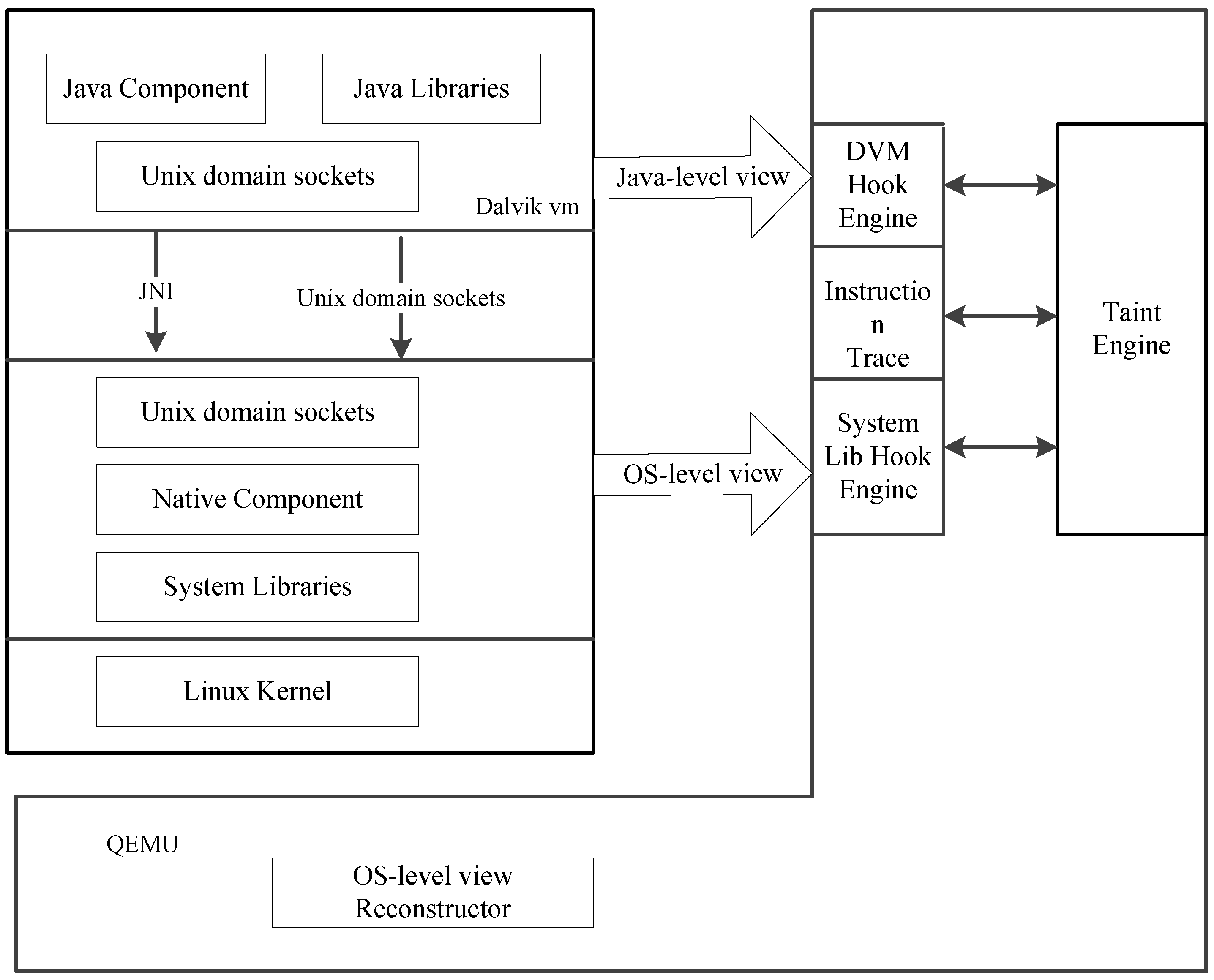
3. Design and Implement
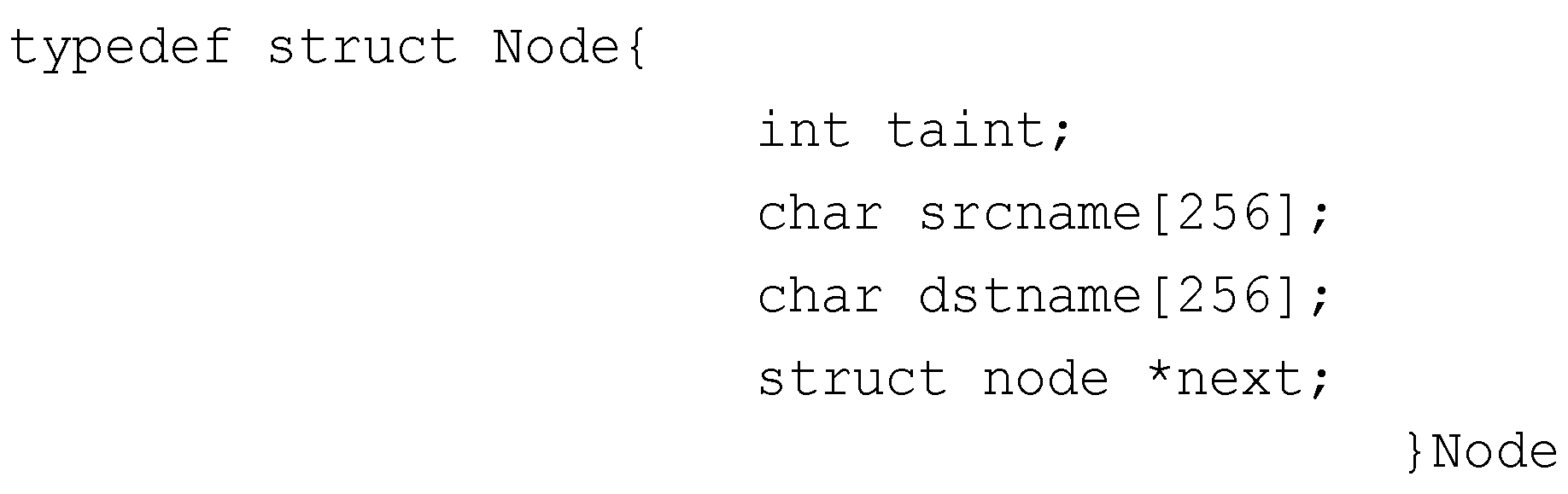
3.1. Taint Propagation
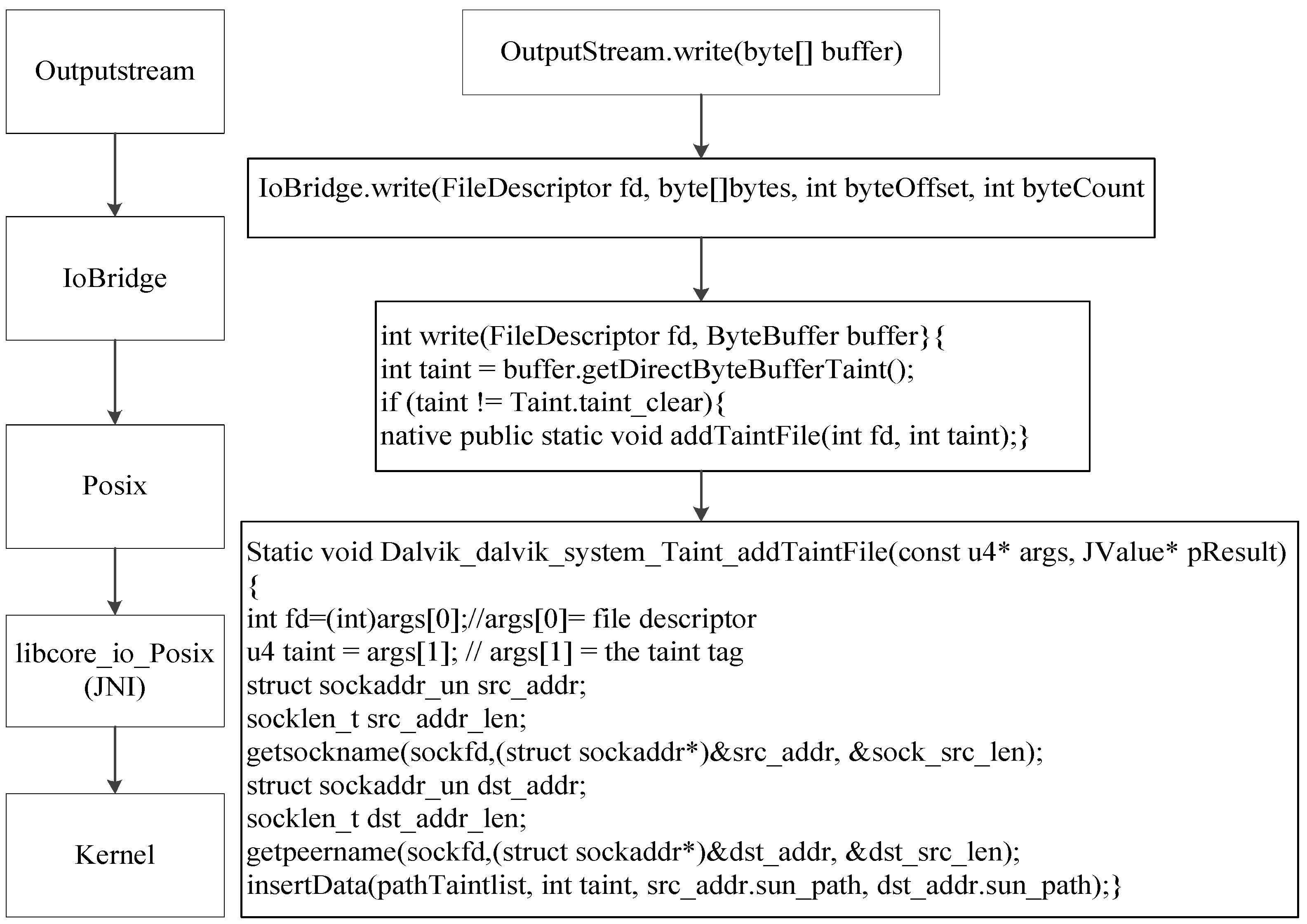
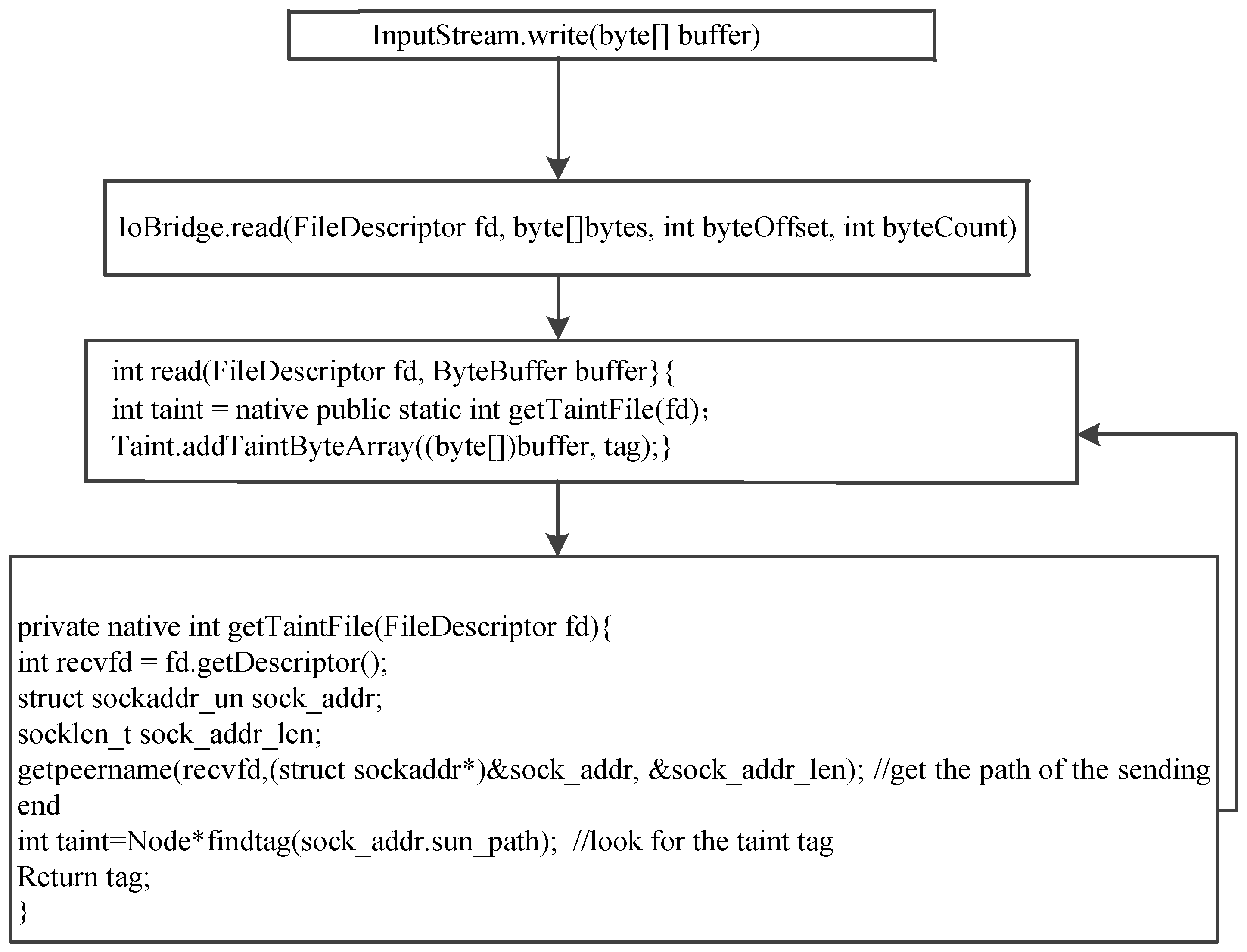
3.2. The Handle in the Sending End
3.3. The Handle in the Receiving End
4. Experiments
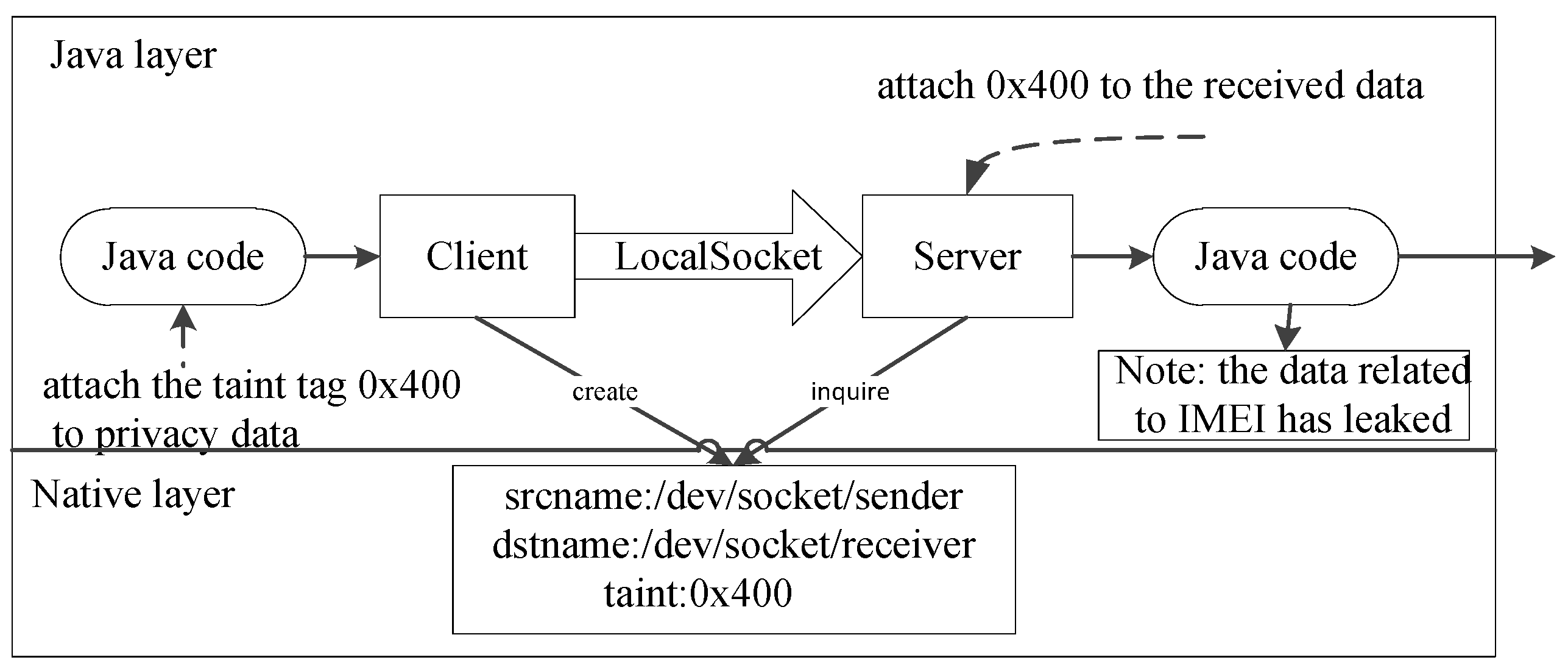
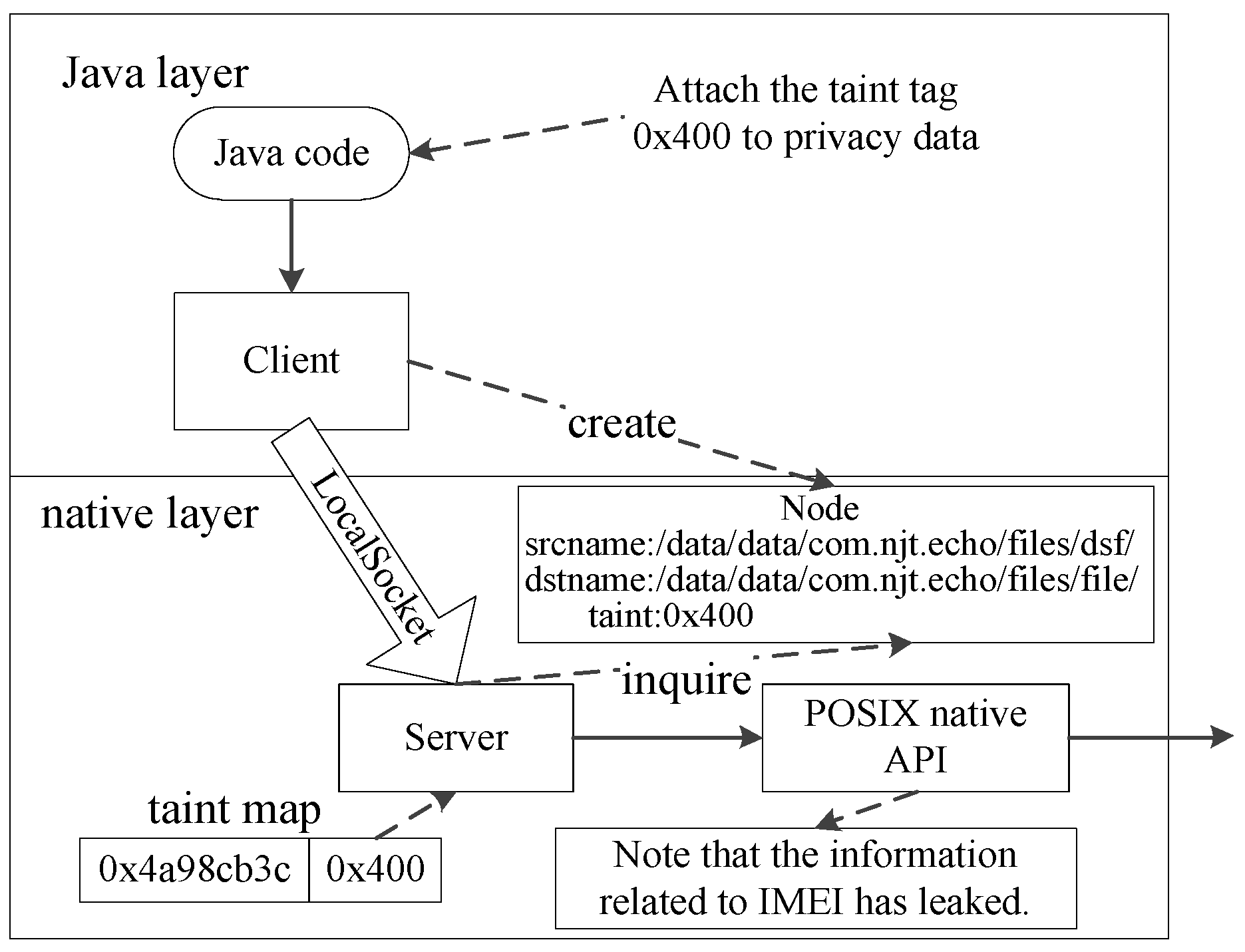
4.1. PoC of Case 1 in Information Leakage
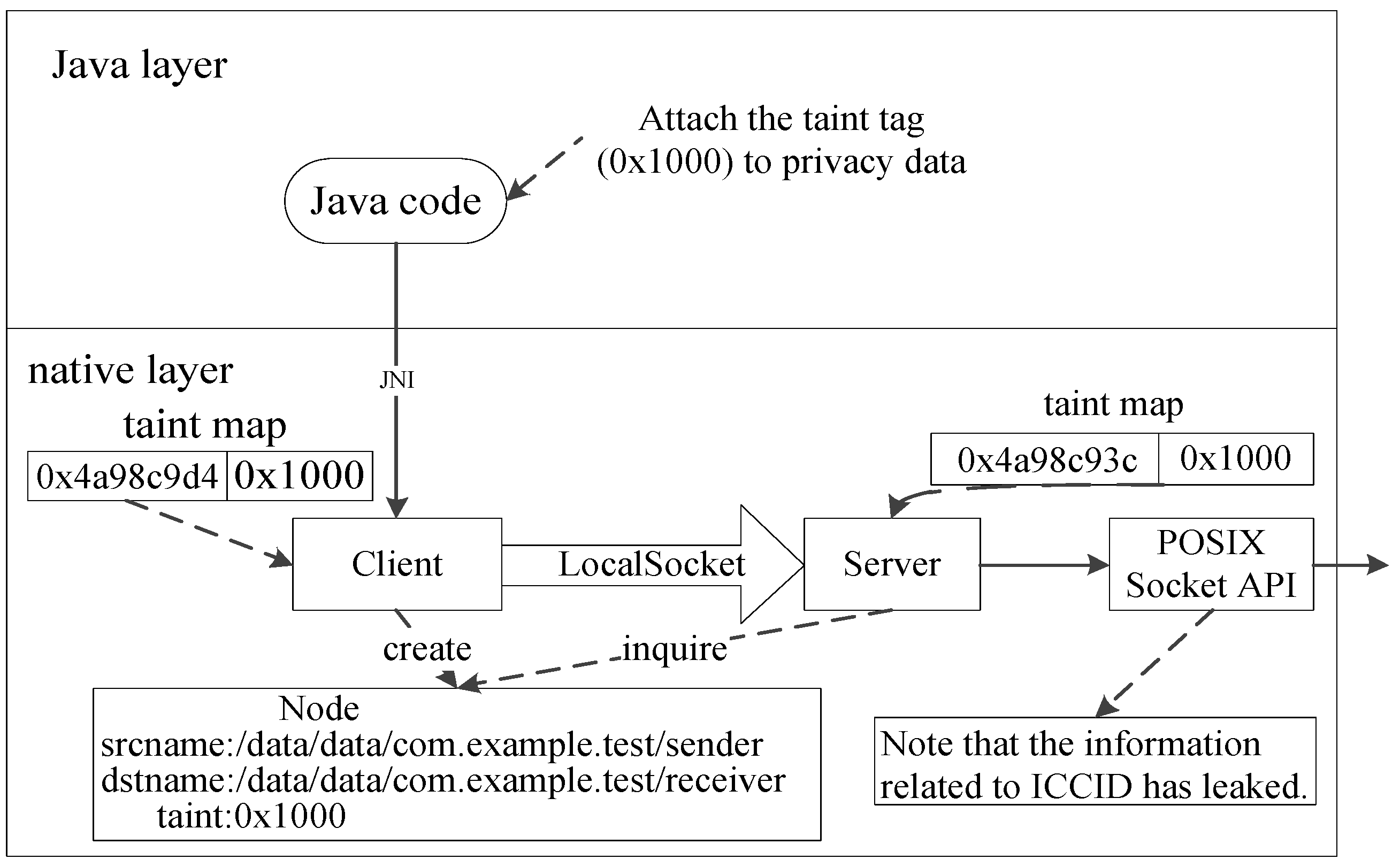
4.2. PoC of Case 2 in Information Leakage
4.3. Echo
4.4. Compare with Other Analysis Systems
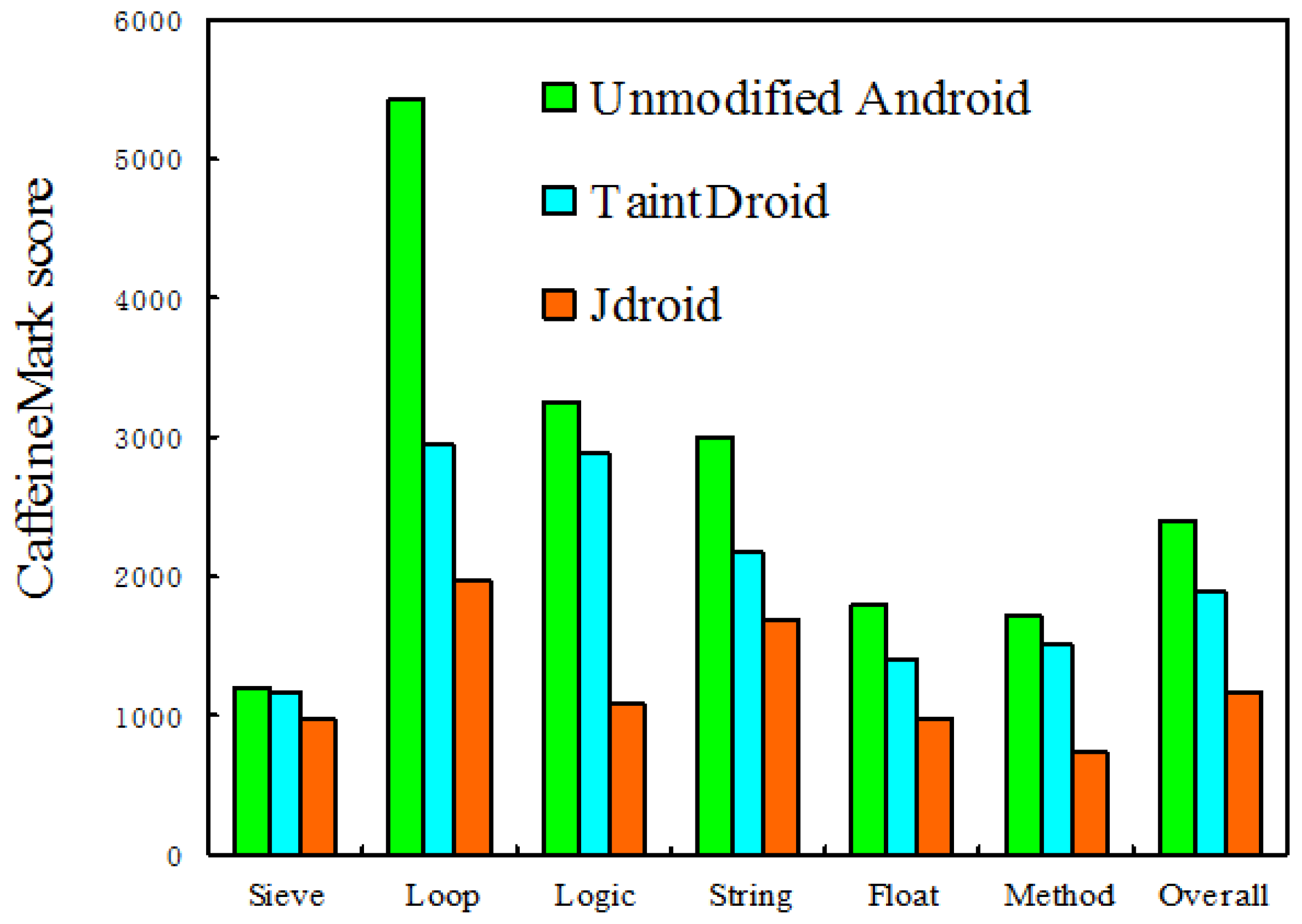
5. Performance
6. Discussion and Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Zhou, Y.; Wang, Z.; Zhou, W.; Jiang, X. Hey, you, get off of my market: Detecting malicious apps in official and alternative android markets. In Proceedings of the 19th Annual Network and Distributed System Security Symposium, San Diego, CA, USA, 7 February 2012; pp. 50–52. [Google Scholar]
- Tam, K.; Feizollah, A.; Anuar, N.B.; Salleh, R.; Cavallaro, L. The Evolution of Android Malware and Android Analysis Techniques. ACM Comput. Surv. 2017, 49, 76. [Google Scholar] [CrossRef]
- Mariconti, E.; Onwuzurike, L.; Andriotis, P.; De Cristofaro, E.; Ross, G.; Stringhini, G. MamaDroid: Detecting Android Malware by Building Markov Chains of Behavioral Models. In Proceedings of the NDSS ‘17: Network and Distributed Systems Security Symposium, San Diego, CA, USA, 26 February–1 March 2017. [Google Scholar]
- Tan, J.; Drolia, U.; Martins, R.; Gandhi, R.; Narasimhan, P. Chips: Content-Based heuristics for improving photo privacy for smartphones. In Proceedings of the 7th ACM Conference on Security and Privacy in Wireless & Mobile Networks, London, UK, 23–25 July 2014; pp. 213–218. [Google Scholar]
- Gordon, M.I.; Kim, D.; Perkins, J.; Rinard, M. Information-Flow Analysis of Android Applications in DroidSafe. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 8 February 2015. [Google Scholar]
- Bugiel, S.; Davi, L.; Dmitrienko, A.; Fischer, T.; Sadeghi, A.R. Xmandroid: A New Android Evolution to Mitigate Privilege Escalation Attacks; Technical Report; Technische Universität Darmstadt: Darmstadt, Germany, 2011; p. 4. [Google Scholar]
- Bugiel, S.; Davi, L.; Dmitrienko, A.; Fischer, T.; Sadeghi, A.-R.; Shastry, B. Towards taming privilege-escalation attacks on android. In Proceedings of the 19th Network and Distributed System Security Symposium, San Diego, CA, USA, 7 February 2012; p. 19. [Google Scholar]
- Dietz, M.; Shekhar, S.; Pisetsky, Y.; Shu, A.; Wallach, D.S. Quire: Lightweight provenance for smart phone operating systems. In Proceedings of the 20th USENIX Conference on Security, San Francisco, CA, USA, 8–12 August 2011; p. 23. [Google Scholar]
- Felt, A.P.; Wang, H.J.; Moshchuk, A.; Hanna, S.; Chin, E. Permission re-delegation: Attacks and defenses. In Proceedings of the USENIX Security Symposium, San Francisco, CA, USA, 8–12 August 2011. [Google Scholar]
- Fragkaki, E.; Bauer, L.; Jia, L.; Swasey, D. Modeling and enhancing androids permission system. In Proceedings of the 17th European Symposium on Research in Computer Security, Pisa, Italy, 10–12 September 2012; pp. 1–18. [Google Scholar]
- Seo, J.; Kim, D.; Cho, D.; Shin, I.; Kim, T. FLEXDROID: Enforcing in-app privilege separation in Android. In Proceedings of the 23rd Network and Distributed System Security Symposium, San Diego, CA, USA, 21–24 February 2016; pp. 21–24. [Google Scholar]
- Chin, E.; Felt, A.P.; Greenwood, K.; Wagner, D. Analyzing inter-application communication in Android. In Proceedings of the 9th International Conference on Mobile Systems, Applications, and Services, Bethesda, MD, USA, 28 June–1 July 2011; pp. 239–252. [Google Scholar]
- Davi, L.; Dmitrienko, A.; Sadeghi, A.R.; Winandy, M. Privilege escalation attacks on android. In Proceedings of the 2010 IEEE International Conference on Information Security, Boca Raton, FL, USA, 25–28 October 2010; pp. 346–360. [Google Scholar]
- Grace, M.C.; Zhou, Y.; Wang, Z.; Jiang, X. Systematic detection of capability leaks in stock android smartphones. In Proceedings of the 19th Network and Distributed System Security Symposium, San Diego, CA, USA, 7 February 2012; p. 19. [Google Scholar]
- Cinar, O.; Grant, A. Pro Android C++ with the NDK; Apress: New York, NY, USA, 2012. [Google Scholar]
- Ghafari, M.; Gadient, P.; Nierstrasz, O. Security Smells in Android. In Proceedings of the IEEE International Working Conference on Source Code Analysis and Manipulation, Shanghai, China, 17–18 September 2017; pp. 121–130. [Google Scholar]
- Li, Y.; Hao, Q.; Ma, X.; Zhang, P.; Fan, Y.; Jiang, J. Design and implementation of Android-based speech storage system. In Proceedings of the Information Technology. Networking, Electronic and Automation Control Conference, Chongqing, China, 20–22 May 2016; pp. 178–181. [Google Scholar]
- Shao, Y.; Ott, J.; Jia, Y.J.; Qian, Z.; Mao, Z.M. The Misuse of Android Unix Domain Sockets and Security Implications. In Proceedings of the 23rd ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 80–91. [Google Scholar]
- Enck, W.; Gilbert, P.; Han, S.; Tendulkar, V.; Chun, B.G.; Cox, L.P.; Sheth, A.N. TaintDroid: An information-flow tracking system for realtime privacy monitoring on smartphones. In Proceedings of the ACM Transactions on Computer Systems, Vancouver, BC, Canada, 4–6 October 2010; Volume 22. [Google Scholar]
- Qian, C.; Luo, X.; Shao, Y.; Chan, A.T. On tracking information flows through JNI in android applications. In Proceedings of the 44th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Atlanta, GA, USA, 23–26 June 2014; pp. 180–191. [Google Scholar]
- Backes, M.; Bugiel, S.; Gerling, S.; von Styp-Rekowsky, P. Android security framework: Extensible multi-layered access control on Android. In Proceedings of the Computer Security Applications Conference, New Orleans, LA, USA, 8–12 December 2014; ACM: New York, NY, USA, 2014; pp. 46–55. [Google Scholar]
- Allix, K.; Bissyandé, T.F.; Klein, J.; Le Traon, Y. AndroZoo: Collecting Millions of Android Apps for the Research Community. In Proceedings of the 2016 IEEE/ACM 13th Working Conference on Mining Software Repositories, Austin, TX, USA, 14–15 May 2016; pp. 468–471. [Google Scholar]
- Gu, Y.; Sun, K.; Su, P.; Li, Q.; Lu, Y.; Ying, L.; Feng, D. JGRE: An Analysis of JNI Global Reference Exhaustion Vulnerabilities in Android. In Proceedings of the IEEE/IFIP International Conference on Dependable Systems and Networks, Denver, CO, USA, 26–29 June 2017; pp. 427–438. [Google Scholar]
- Sawada, Y.; Arai, Y.; Ootsu, K.; Yokota, T.; Ohkawa, T. Performance of Android Cluster System Allowing Dynamic Node Reconfiguration. Wirel. Pers. Commun. Int. J. 2017, 93, 1067–1087. [Google Scholar] [CrossRef]
- Demertzis, K.; Iliadis, L. Computational intelligence anti-malware framework for android OS. Vietnam J. Comput. Sci. 2017, 4, 1–15. [Google Scholar] [CrossRef]
- Hofmann, M.; Rünger, G. Sustainability through flexibility: Building complex simulation programs for distributed computing systems. Simul. Model. Pract. Theory 2015, 58, 65–78. [Google Scholar] [CrossRef]
- Fox, R.; Kasten, E.; Orji, K.; Bolen, C.; Maurice, C.; Venema, J. Real-time results without real-time systems. IEEE Trans.Nucl. Sci. 2015, 51, 571–575. [Google Scholar] [CrossRef]
- Grace, M.; Zhou, Y.; Zhang, Q.; Zou, S.; Jiang, X. Riskranker: Scalable and accurate zero-day android malware detection. In Proceedings of the 10th International Conference on Mobile Systems, Applications and Services, Low Wood Bay, Lake District, UK, 25–29 June 2012; pp. 281–294. [Google Scholar]
- Byun, S.S. TCP over scarce transmission opportunity in cognitive radio networks. Comput. Netw. 2016, 103, 101–114. [Google Scholar] [CrossRef]
- Lin, C.C.; Li, H.; Zhou, X.; Wang, F. Screenmilker: How to Milk Your Android Screen for Secrets. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 24 February 2014. [Google Scholar]
- Rafnsson, W. Tracking Information Flows in Interactive and Object-Oriented Programs; Chalmers University of Technology: Göteborg, Sweden, 2012. [Google Scholar]
- Gries, S.; Hesenius, M.; Gruhn, V. Tracking Information Flow in Cyber-Physical Systems. In Proceedings of the IEEE International Conference on Distributed Computing Systems, Atlanta, GA, USA, 5–8 June 2017; pp. 2589–2590. [Google Scholar]
- Lantz, P.; Desnos, A.; Yang, K. DroidBox: An Android Application Sandbox for Dynamic Analysis. Available online: https://code. google.com/p/droidbox (accessed on 3 March 2018).
- Hornyack, P.; Han, S.; Jung, J.; Schechter, S.; Wetherall, D. These aren’t the Droids you’re looking for: Retrofitting android to protect data from imperious applications. In Proceedings of the 18th ACM Conference on Computer and Communication Security, Chicago, IL, USA, 17–21 October 2011; pp. 639–652. [Google Scholar]
- Egele, M.; Scholte, T.; Kirda, E.; Kruegel, C. A survey on automated dynamic malware-analysis techniques and tools. ACM Comput. Surv. 2012, 44. [Google Scholar] [CrossRef]
- Fratantonio, Y.; Bianchi, A.; Robertson, W.; Kirda, E.; Kruegel, C.; Vigna, G. Triggerscope: Towards detecting logic bombs in android applications. In Proceedings of the Security and Privacy Symposium, San Jose, CA, USA, 22–26 May 2016; pp. 377–396. [Google Scholar]
- Zhou, Y.; Jiang, X. Dissecting android malware: Characterization and evolution. In Proceedings of the 33rd IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–23 May 2012; pp. 95–109. [Google Scholar]
- Portokalidis, G.; Homburg, P.; Anagnostakis, K.; Bos, H. Paranoid android: Versatile protection for smartphones. In Proceedings of the 2010 Annual Computer Security Applications Conference, Austin, TX, USA, 6–10 December 2010; pp. 347–356. [Google Scholar]
- Burguera, I.; Zurutuza, U.; Nadjm-Tehrani, S. Crowdroid: Behavior-Based malware detection system for android. In Proceedings of the 1st ACM Workshop on Security and Privacy in Smartphones and Mobile Devices, New York, NY, USA, 17 October 2011; pp. 15–26. [Google Scholar]
- Spreitzenbarth, M.; Echtler, F.; Hoffmann, J. Mobilesandbox: Having a deeper look into android applications. In Proceedings of the 28th Annual ACM Symposium on Applied Computing, New York, NY, USA, 18–22 March 2013; pp. 1808–1815. [Google Scholar]
- Tam, K.; Khan, S.J.; Fattori, A.; Cavallaro, L. CopperDroid: Automatic Reconstruction of Android Malware Behaviors. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 8–11 February 2015. [Google Scholar]
- Yan, L.K.; Yin, H. Droidscope: Seamlessly reconstructing OS and Dalvik semantic views for dynamic Android malware analysis. In Proceedings of the 21st USENIX Security Symposium, Bellevue, WA, USA, 8–10 August 2012; pp. 569–584. [Google Scholar]
- Johnson, R.; Wang, Z.; Gagnon, C.; Stavrou, A. Analysis of Android Applications’ Permissions. In Proceedings of the IEEE Sixth International Conference on Software Security and Reliability Companion, Gaithersburg, MD, USA, 20–22 June 2012; pp. 45–46. [Google Scholar]
- Ghandour, W.J.; Akkary, H.; Masri, W. The potential of using dynamic information flow analysis in data value prediction. In Proceedings of the International Conference on Parallel Architectures and Compilation Techniques, Vienna, Austria, 11–15 September 2010; pp. 431–442. [Google Scholar]
- Sarwar, G.; Mehani, O.; Boreli, R.; Kaafar, M.A. On the effectiveness of dynamic taint analysis for protecting against private information leaks on android-based devices. In Proceedings of the 10th International Conference on Security and Cryptography, Reykjavík, Iceland, 29–31 July 2013; pp. 461–468. [Google Scholar]
- Shao, Y.; Luo, X.; Qian, C. RootGuard: Protecting Rooted Android Phones. Computer 2014, 47, 32–40. [Google Scholar] [CrossRef]





| Client | |||
|---|---|---|---|
| Java | Native | ||
| Server | Java | Case 1 | Case 3 |
| Native | Case 3 | Case 2 | |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, X.; Mu, D.; Zhang, H. Unix Domain Sockets Applied in Android Malware Should Not Be Ignored. Information 2018, 9, 54. https://doi.org/10.3390/info9030054
Jiang X, Mu D, Zhang H. Unix Domain Sockets Applied in Android Malware Should Not Be Ignored. Information. 2018; 9(3):54. https://doi.org/10.3390/info9030054
Chicago/Turabian StyleJiang, Xu, Dejun Mu, and Huixiang Zhang. 2018. "Unix Domain Sockets Applied in Android Malware Should Not Be Ignored" Information 9, no. 3: 54. https://doi.org/10.3390/info9030054





