An SVM-Based Method for Classification of External Interference in Industrial Wireless Sensor and Actuator Networks
Abstract
:1. Introduction
- This is the first study that employs an SVM classifier to process signal features extracted from received signal strength indicator (RSSI) traces to identify the source of external interference. The proposed method employs four lightweight signal features, designed considering hardware constraints of commercial off-the-shelf (COTS) WSN devices.
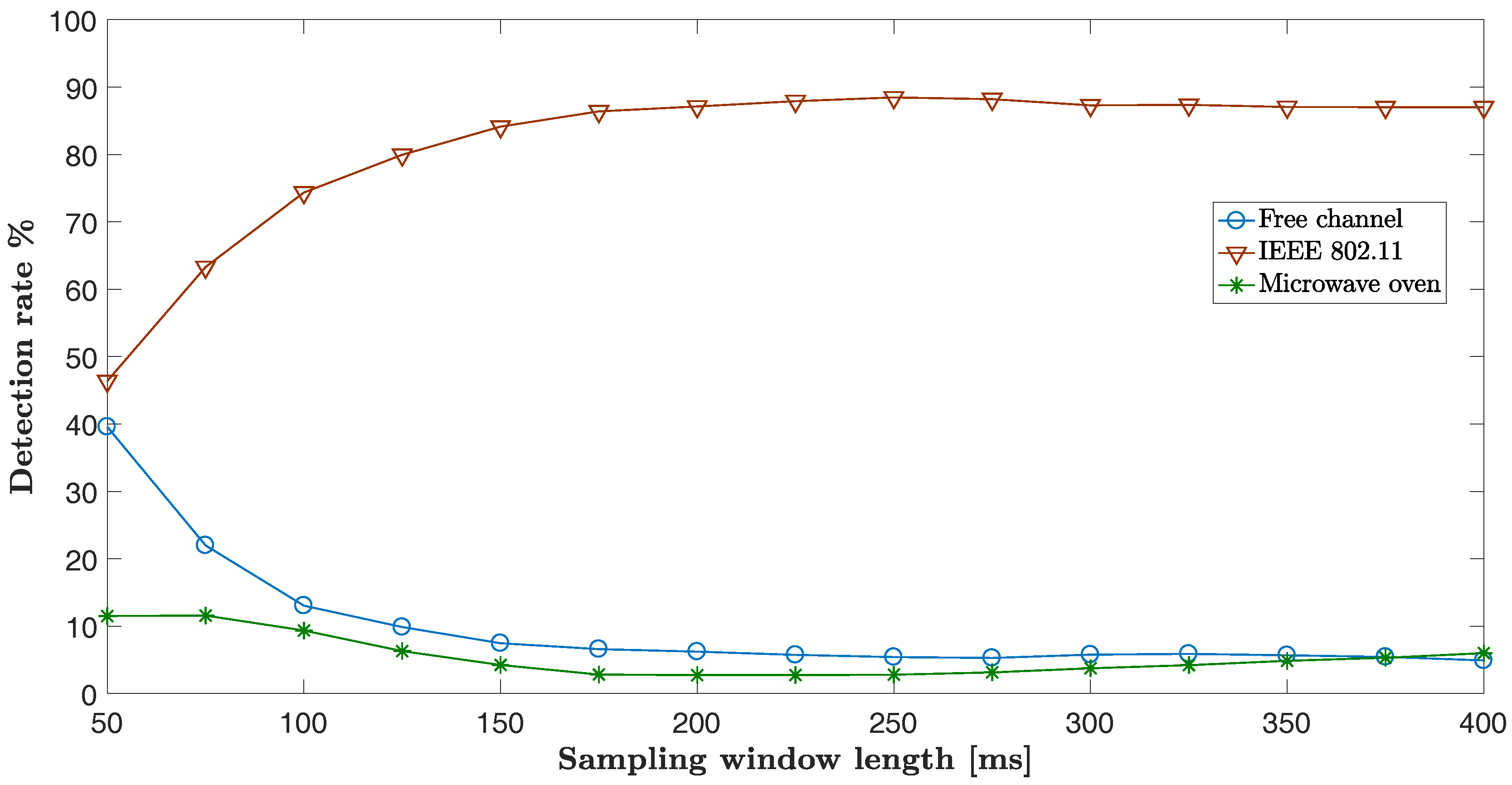
- It is shown that, in order to ensure good detection performance, the proposed classifier requires a time window for spectrum sensing consistently below 300 ms, which, to the best knowledge of the authors, places the proposed solution amongst the quickest and most reliable methods reported in the literature.
- The performance of the proposed solution is validated by using an RSSI dataset collected in different industrial environments. Both the controlled and uncontrolled interferences from IEEE 802.11 networks are taken into account.
- The often overlooked influence of device calibration on spectrum sensing-based interference classification is analyzed, showing that the classifier accuracy is subject to the intrinsic hardware variations of the employed devices. However, we show that this factor can be easily corrected by means of a straightforward calibration process.
2. Related Works
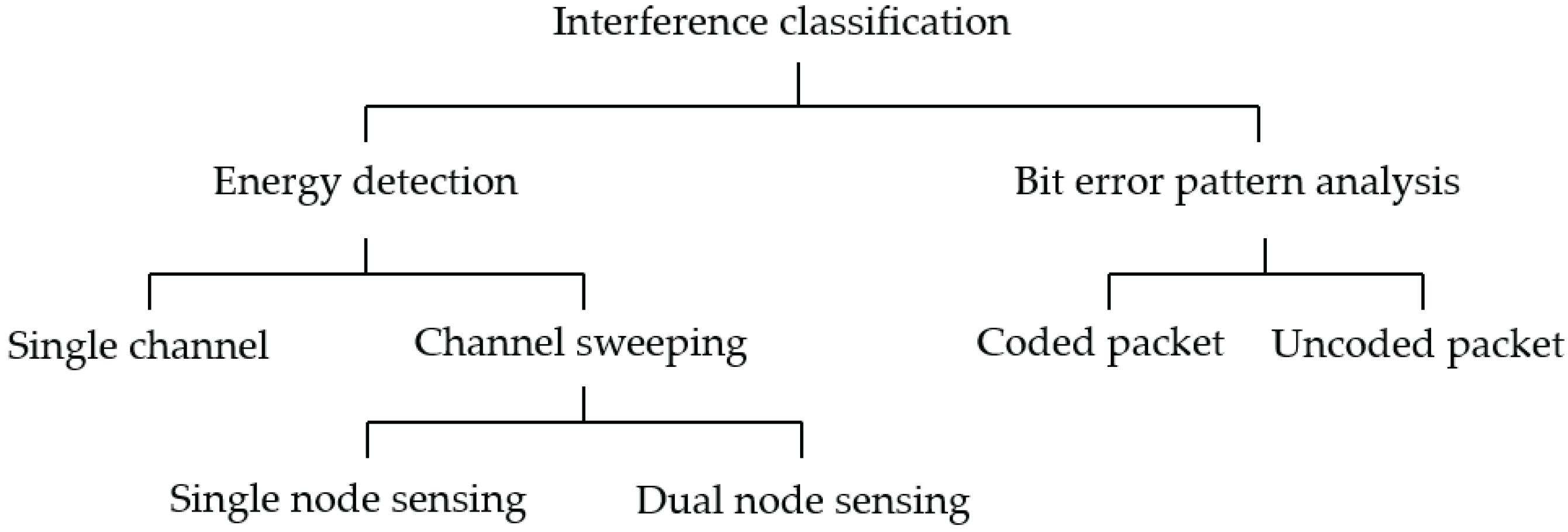
2.1. Energy Detection-Based Interference Classification
2.2. Bit Error Pattern-Based Interference Classification
3. Background
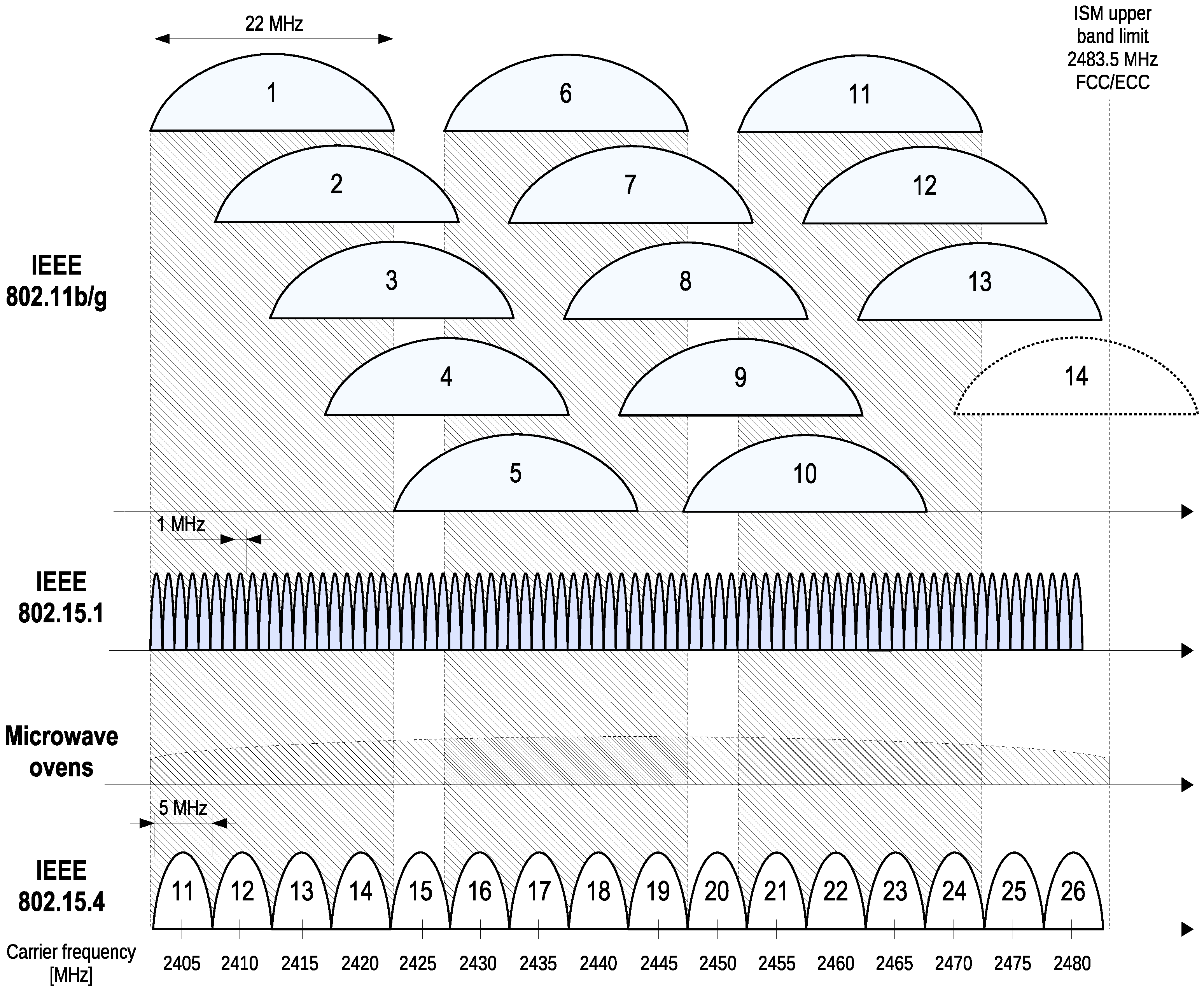
3.1. Cross-Technology Interference Sources
3.1.1. IEEE 802.11
3.1.2. Microwave Ovens
4. Support Vector Machines
4.1. The Standard Model for SVM
4.2. SVM: Training and Classification
5. The Proposed Solution
5.1. Classifier Setup
- SVM-free channel: this SVM is trained to detect the presence of an IFC.
- SVM-active network: targets the presence of an active IEEE 802.11 network occupying the related IEEE 802.15.4 PHY channel (i.e., an IEEE 802.11 access point with at least one associated terminal, generating uplink/downlink traffic).
- SVM-silent network: targets a silent IEEE 802.11 network overlapping the specific channel. This is the case of an IEEE 802.11 access point with no associated terminal or an access point with associated terminals that are not generating data traffic in the observation time window.
- SVM-microwave oven: detects the presence of RF leakage from a microwave-oven operating in close proximity to the radio node.
5.2. Signal Features
5.2.1. Number and Length of Signal Bursts
5.2.2. Mean, Variance and Cardinality of Over-Threshold Samples
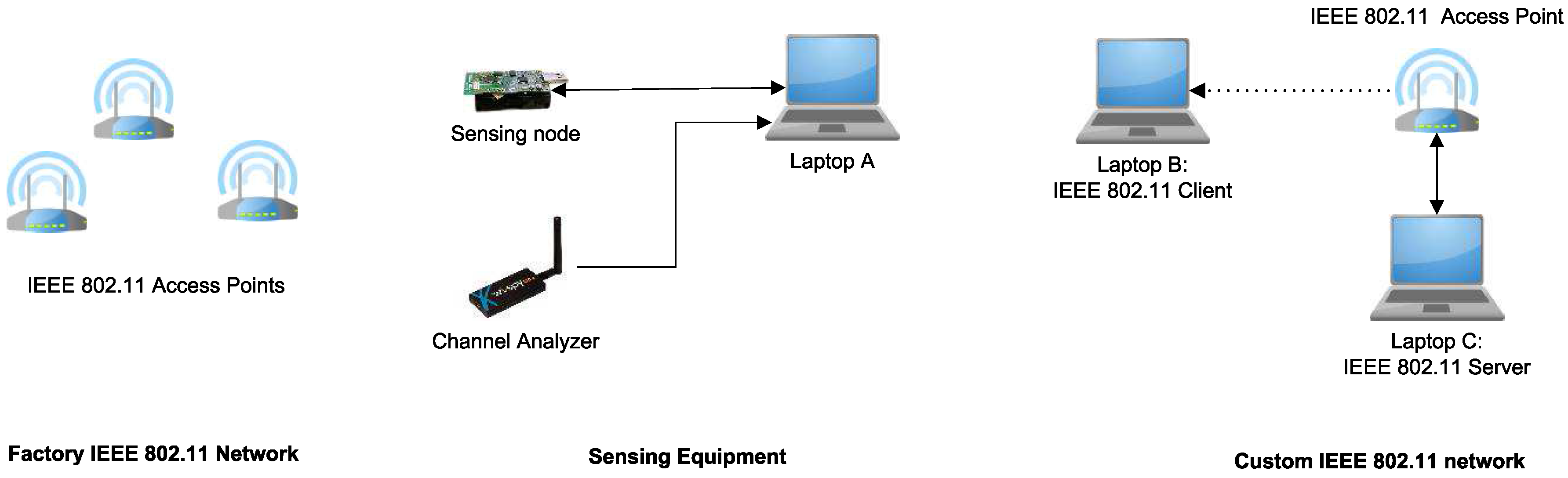
6. Experimental Setup
6.1. Hardware Setup
6.2. Test Environments
6.3. The Collection of Training Data for SVM
6.3.1. Training Data from Uncontrolled IEEE 802.11 Networks
6.3.2. Training Data from Controlled Sources
6.3.3. Training Data from Microwave Oven
6.3.4. Test Data
7. Results
7.1. Global Classification Accuracy
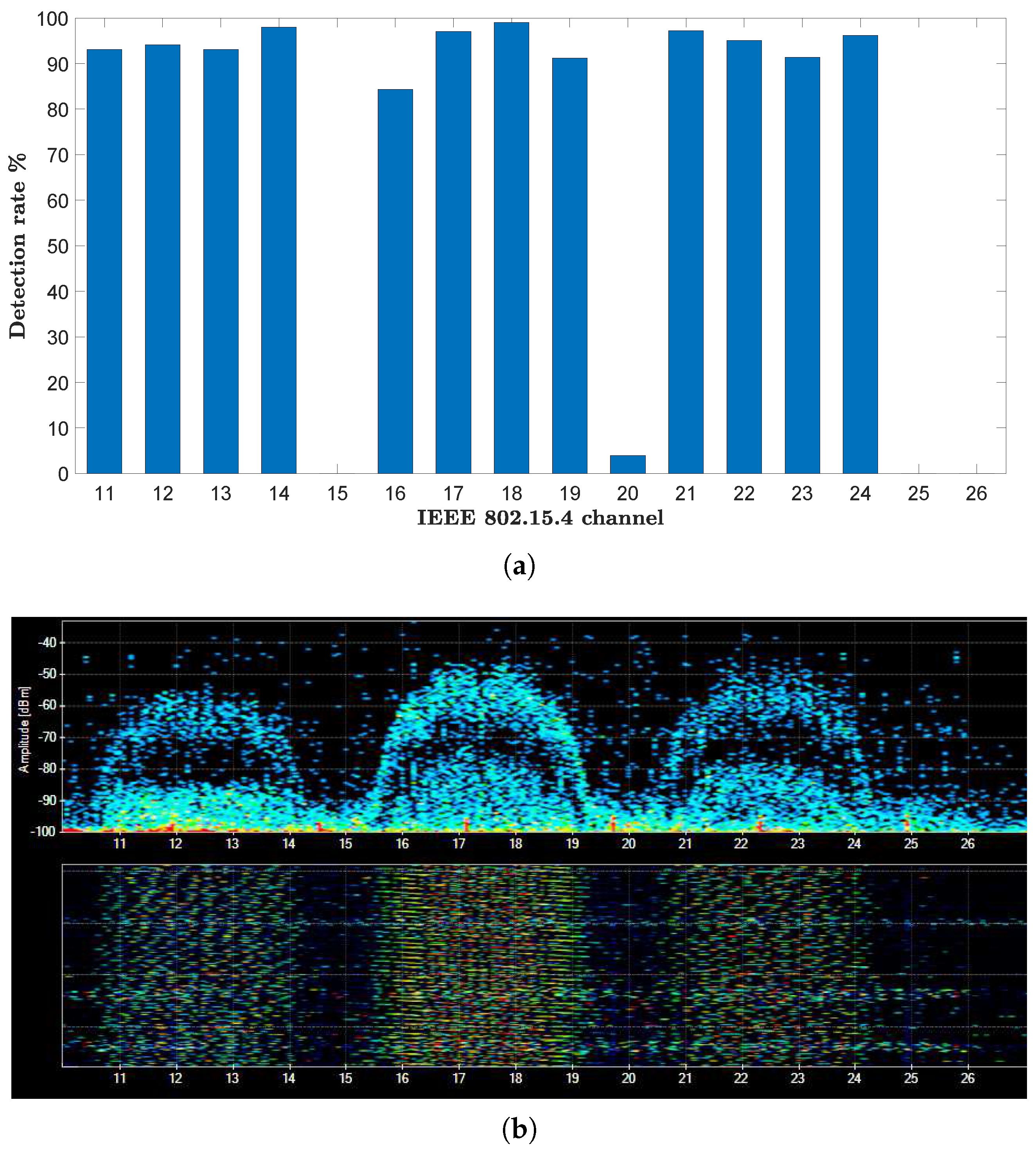
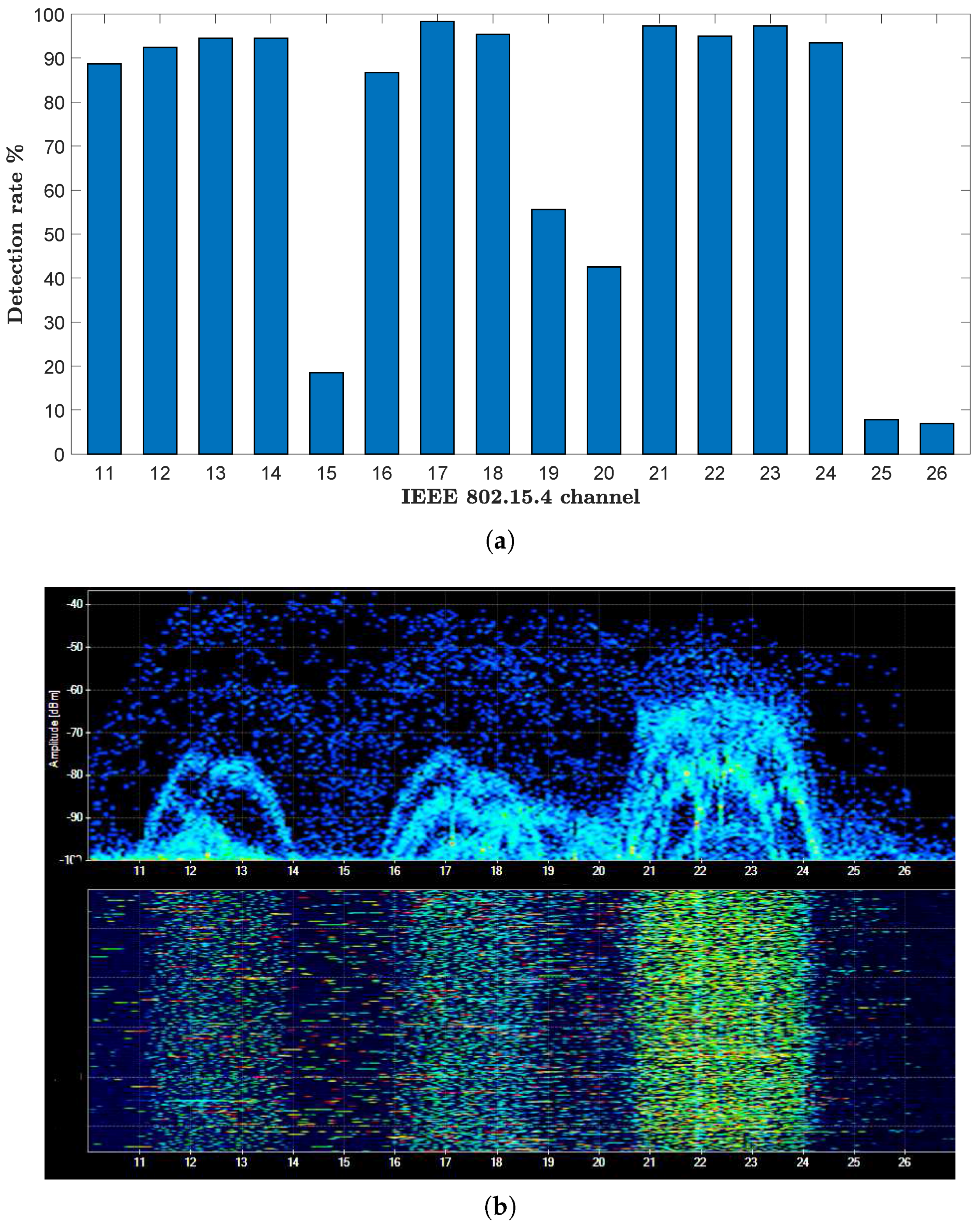
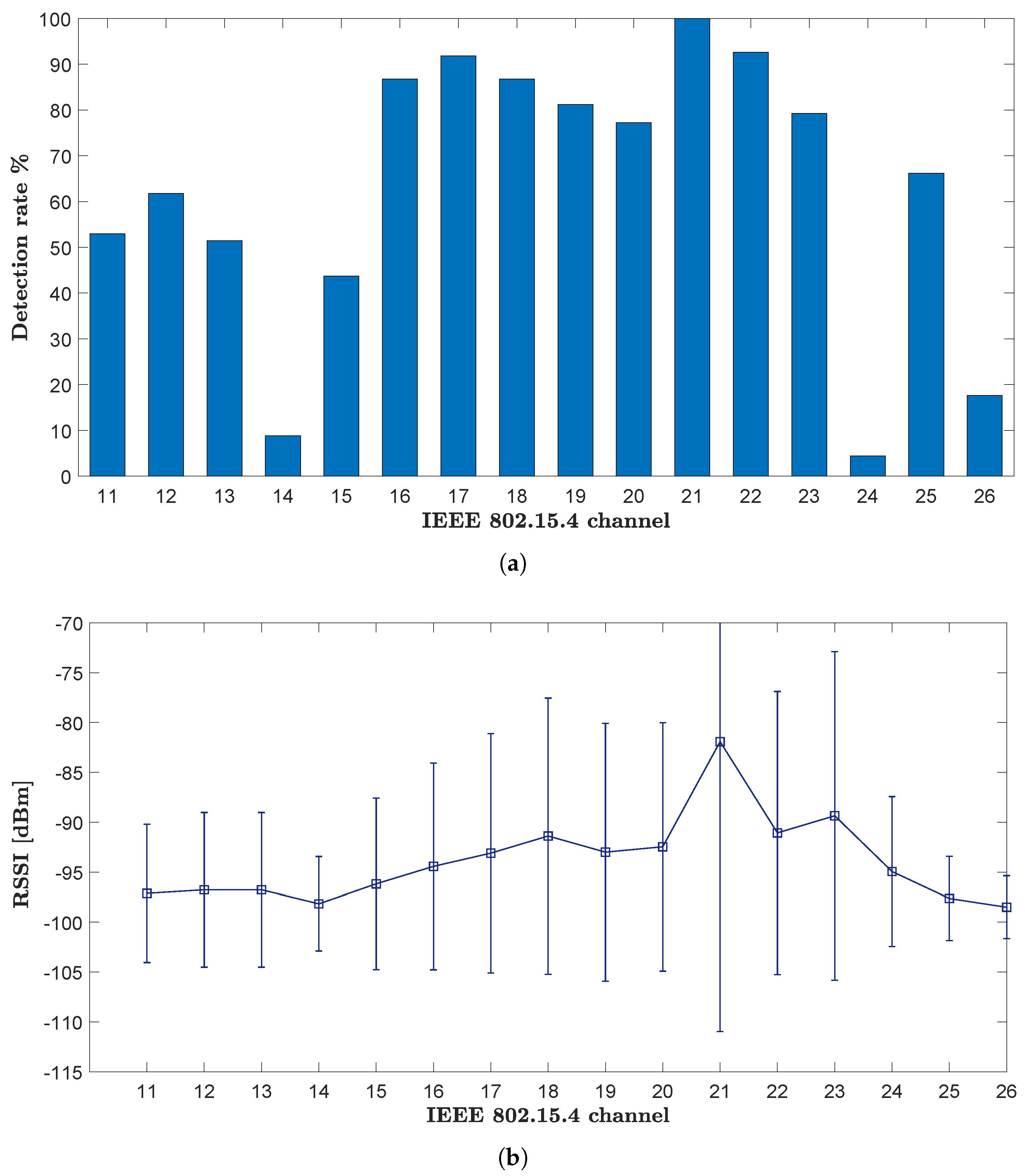
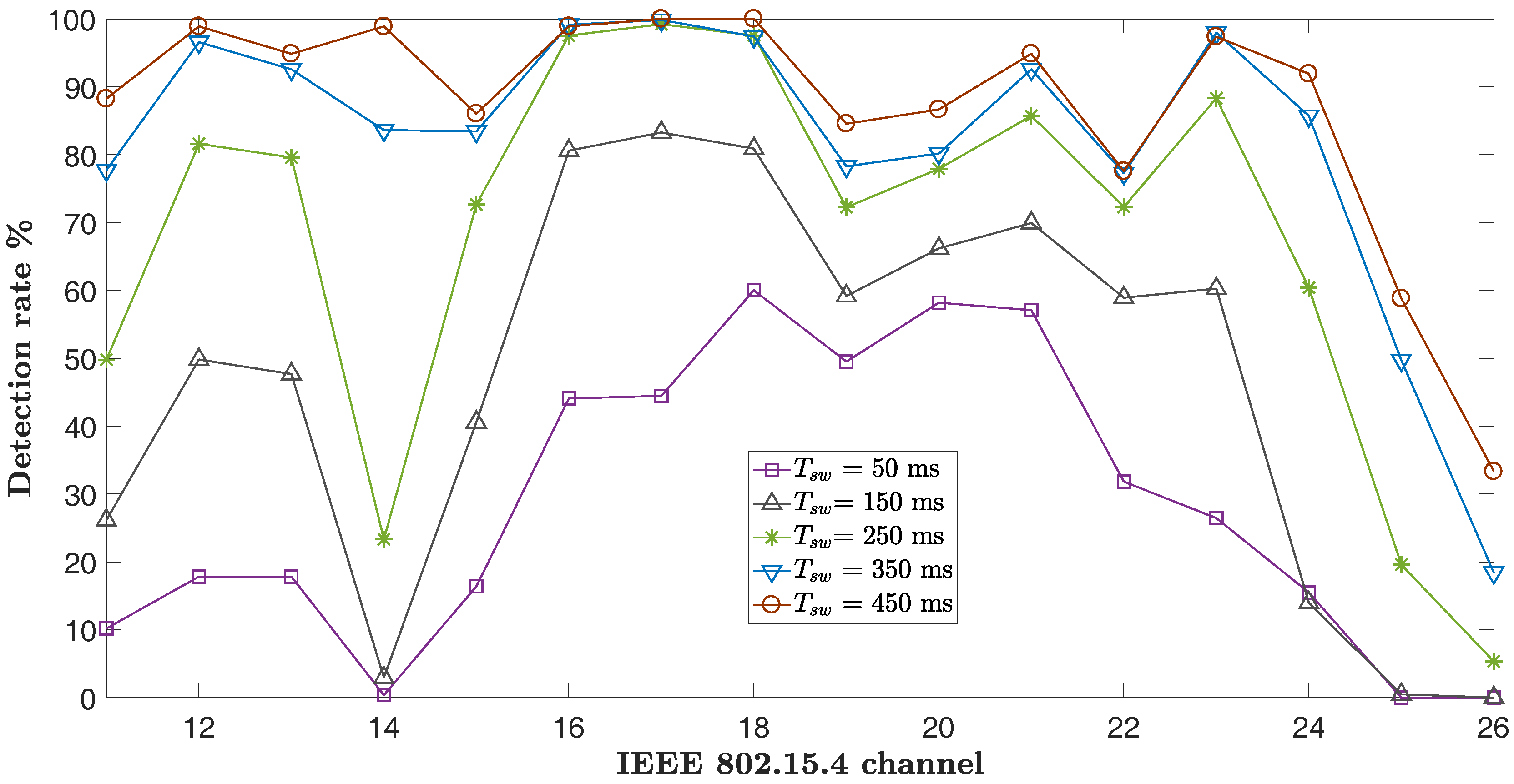
7.2. Channel-Specific Accuracy
8. Discussion
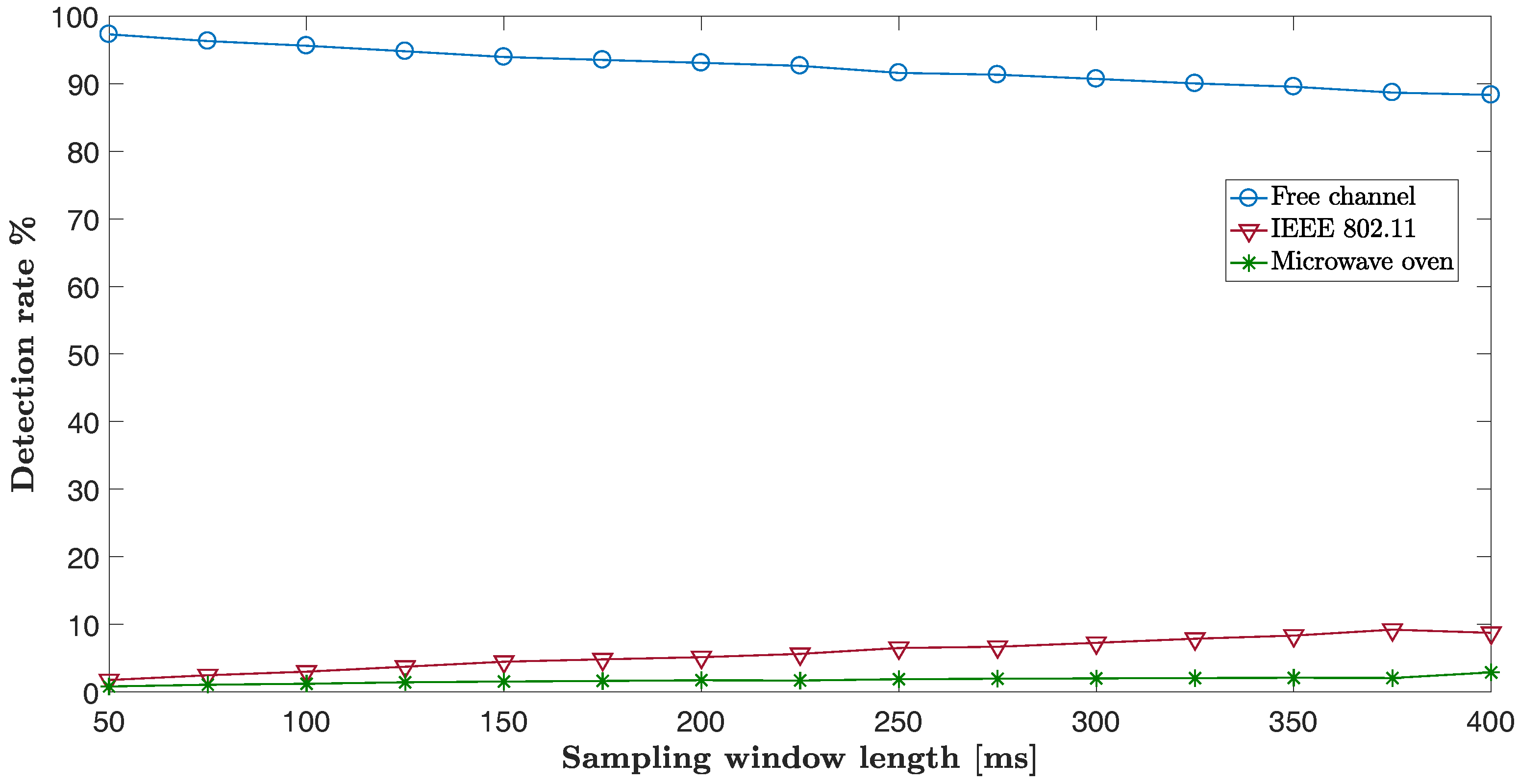
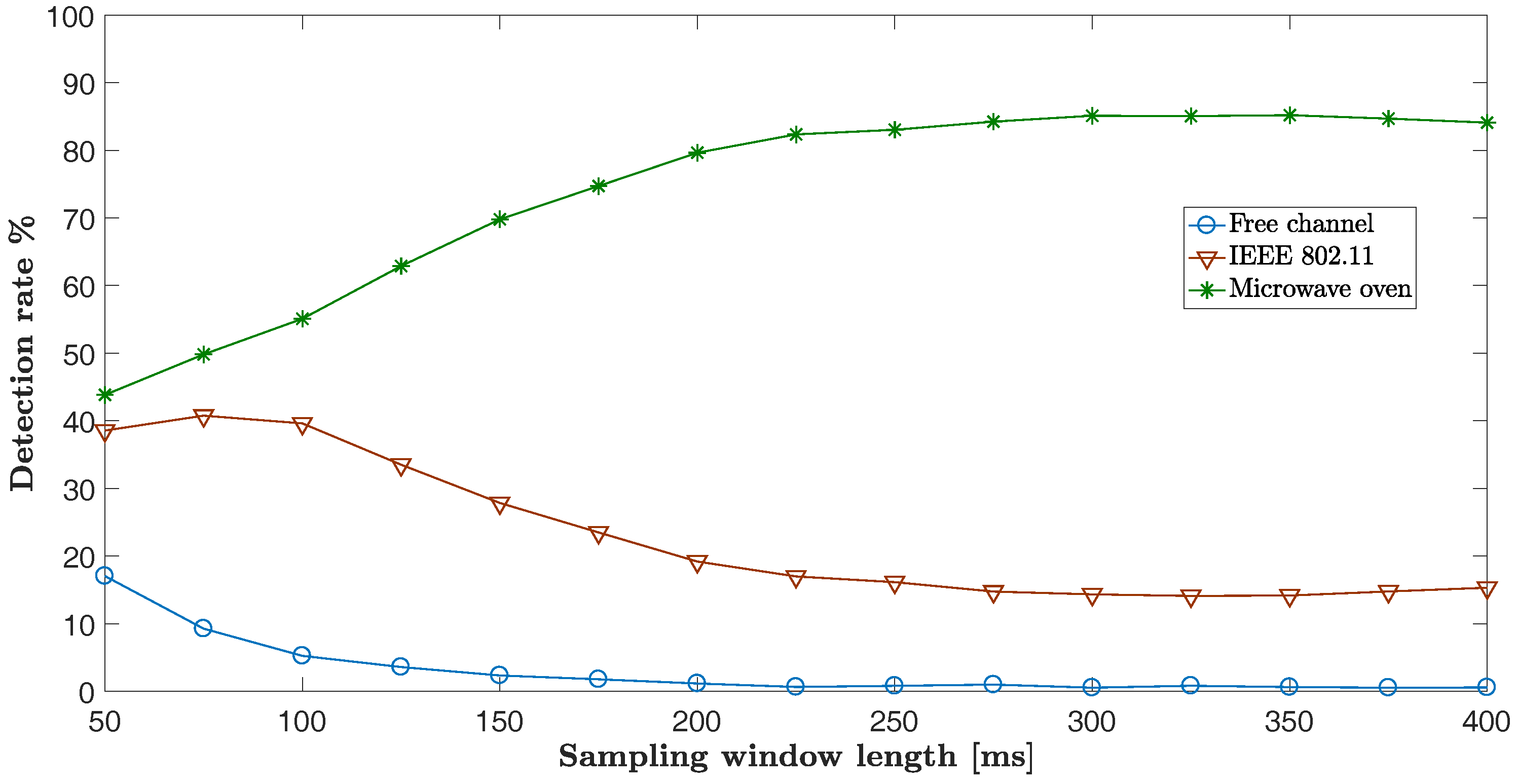
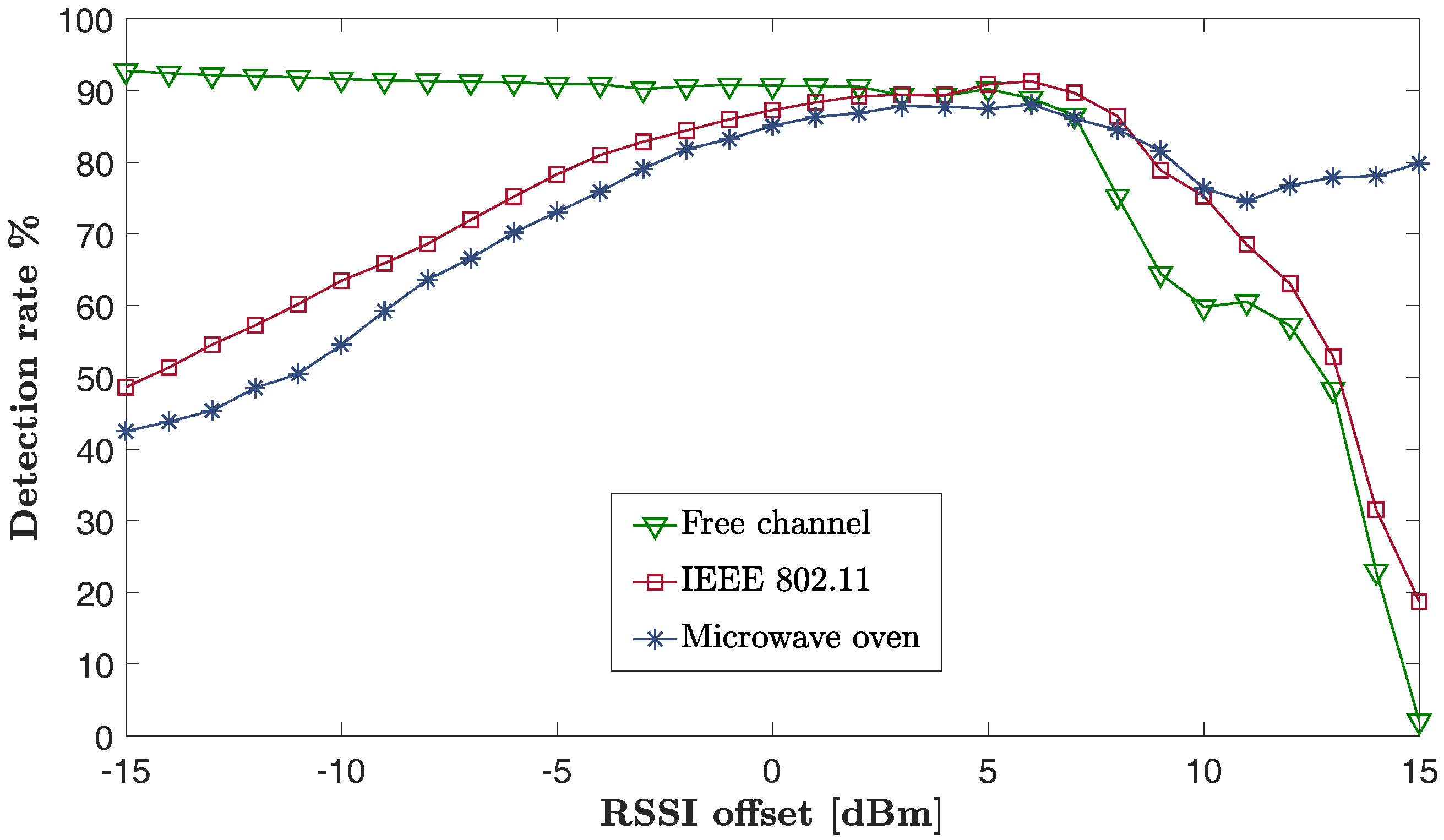
8.1. The Influence of Sampling Window Length
8.2. Hardware-Related Considerations
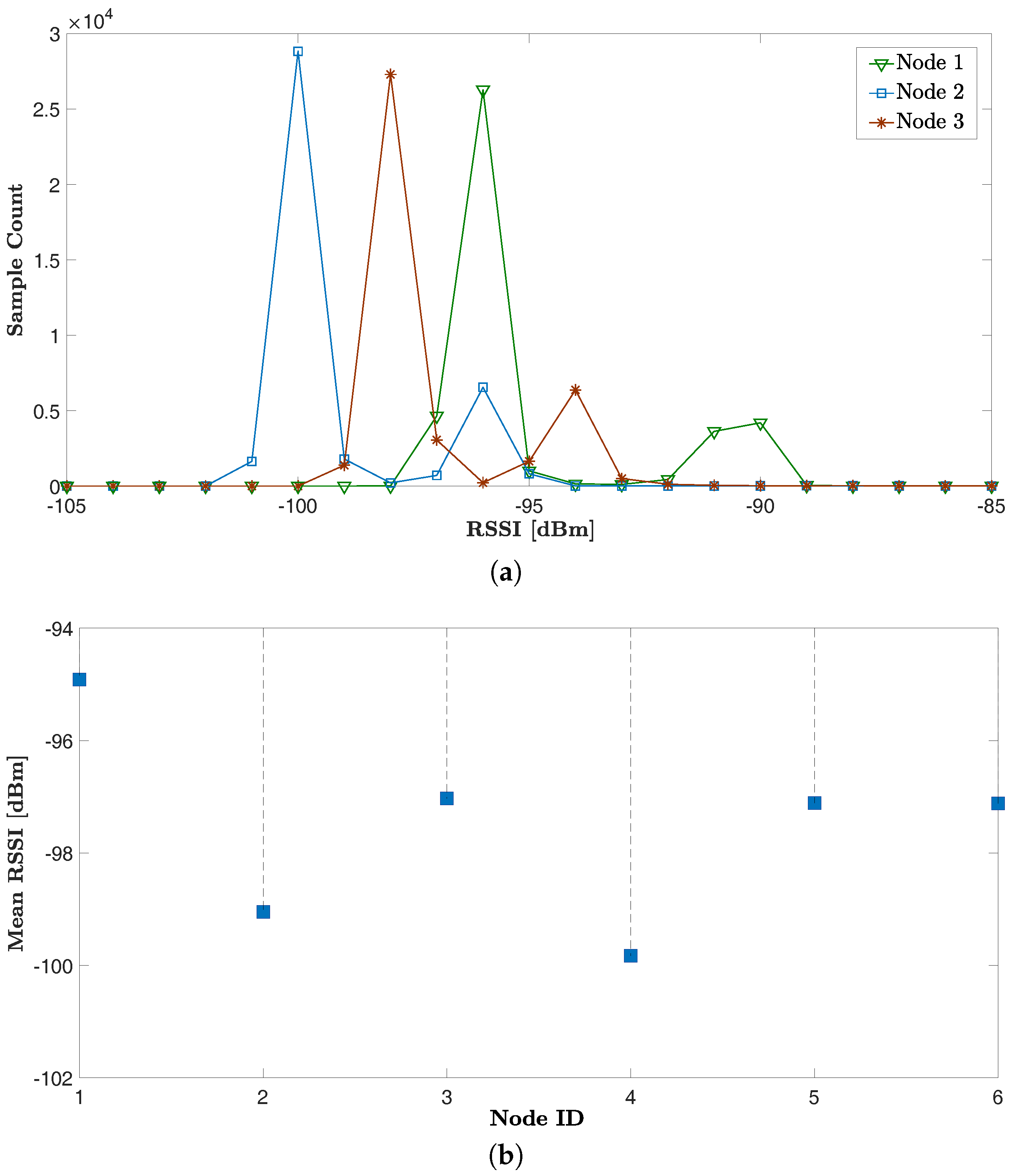
8.2.1. The Role of Node Calibration
8.2.2. Assessing the Timeliness of the Sampling Process
9. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Prathap, U.; Shenoy, P.D.; Venugopal, K.R.; Patnaik, L.M. Wireless Sensor Networks Applications and Routing Protocols: Survey and Research Challenges. In Proceedings of the 2012 International Symposium on Cloud and Services Computing, Mangalore, India, 17–18 December 2012; pp. 49–56. [Google Scholar]
- Đurišić, M.P.; Tafa, Z.; Dimić, G.; Milutinović, V. A survey of military applications of wireless sensor networks. In Proceedings of the 2012 Mediterranean Conference on Embedded Computing (MECO), Bar, Montenegro, 19–21 June 2012; pp. 196–199. [Google Scholar]
- Mangali, N.K.; Kota, V.K. Health monitoring systems: An energy efficient data collection technique in wireless sensor networks. In Proceedings of the 2015 International Conference on Microwave, Optical and Communication Engineering (ICMOCE), Bhubaneswar, India, 18–20 December 2015; pp. 130–133. [Google Scholar]
- Benkhelifa, I.; Nouali-Taboudjemat, N.; Moussaoui, S. Disaster Management Projects Using Wireless Sensor Networks: An Overview. In Proceedings of the 2014 28th International Conference on Advanced Information Networking and Applications Workshops, Victoria, BC, Canada, 13–16 May 2014; pp. 605–610. [Google Scholar]
- IEEE Standard for Information technology—Local and metropolitan area networks—Specific requirements—Part 15.4: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Low Rate Wireless Personal Area Networks (WPANs); IEEE Std 802.15.4-2006; IEEE: New York, NY, USA, 2006.
- Åkerberg, J.; Gidlund, M.; Björkman, M. Future research challenges in wireless sensor and actuator networks targeting industrial automation. In Proceedings of the 2011 9th IEEE International Conference on Industrial Informatics, Lisbon, Portugal, 26–29 July 2011; pp. 410–415. [Google Scholar]
- Galloway, B.; Hancke, G. Introduction to Industrial Control Networks. IEEE Commun. Surv. Tutor. 2013, 15, 860–880. [Google Scholar] [CrossRef]
- Rappaport, T.S. Indoor radio communications for factories of the future. IEEE Commun. Mag. 1989, 27, 15–24. [Google Scholar] [CrossRef]
- Gwarek, W.K.; Celuch-Marcysiak, M. A review of microwave power applications in industry and research. In Proceedings of the 15th International Conference on Microwaves, Radar and Wireless Communications (IEEE Cat. No.04EX824), Warsaw, Poland, 17–19 May 2004; Volume 3, pp. 843–848. [Google Scholar]
- Sikora, A. Wireless Personal and Local Area Networks; Wiley: Chichester, UK; Hoboken, NJ, USA, 2003. [Google Scholar]
- Liang, C.J.M.; Priyantha, N.B.; Liu, J.; Terzis, A. Surviving Wi-Fi Interference in Low Power ZigBee Networks. In Proceedings of the 8th ACM Conference on Embedded Networked Sensor Systems, Zürich, Switzerland, 3–5 November 2010; ACM: New York, NY, USA, 2010; pp. 309–322. [Google Scholar]
- Yang, D.; Xu, Y.; Gidlund, M. Wireless Coexistence between IEEE 802.11- and IEEE 802.15.4-Based Networks: A Survey. Int. J. Distrib. Sens. Netw. 2011, 7, 912152. [Google Scholar] [CrossRef]
- Hermans, F.; Rensfelt, O.; Voigt, T.; Ngai, E.; Norden, L.A.; Gunningberg, P. SoNIC: Classifying Interference in 802.15.4 Sensor Networks. In Proceedings of the 12th International Conference on Information Processing in Sensor Networks (IPSN ’13), Philadelphia, PA, USA, 8–11 April 2013; ACM: New York, NY, USA, 2013; pp. 55–66. [Google Scholar]
- HART Communication Protocol Specification, Revision 7.4; Technical Report; HART Communication Foundation: Austin, TX, USA, 2012.
- Wireless Systems for Industrial Automation: Process Control and Related Applications; ISA 100.11a-2011; International Society of Automation: Research Triangle Park, NC, USA, 2011.
- Industrial Communication Networks—Fieldbus Specifications—WIA-PA Communication Network and Communication Profile; IEC 62601; International Electrotechnical Commission: Geneva, Switzerland, 2011.
- Yucek, T.; Arslan, H. A survey of spectrum sensing algorithms for cognitive radio applications. IEEE Commun. Surv. Tutor. 2009, 11, 116–130. [Google Scholar] [CrossRef]
- Brown, J.; Roedig, U.; Boano, C.A.; Römer, K. Estimating packet reception rate in noisy environments. In Proceedings of the 39th Annual IEEE Conference on Local Computer Networks Workshops, Edmonton, AB, Canada, 8–11 September 2014; pp. 583–591. [Google Scholar]
- Zacharias, S.; Newe, T.; O’Keeffe, S.; Lewis, E. A Lightweight Classification Algorithm for External Sources of Interference in IEEE 802.15.4-Based Wireless Sensor Networks Operating at the 2.4 GHz. Int. J. Distrib. Sens. Netw. 2014, 10, 265286. [Google Scholar] [CrossRef]
- Zhou, R.; Xiong, Y.; Xing, G.; Sun, L.; Ma, J. ZiFi: wireless LAN discovery via ZigBee interference signatures. In Proceedings of the sixteenth annual international conference on Mobile computing and networking, Chicago, IL, USA, 20–24 September 2010; ACM: New York, NY, USA, 2010; pp. 49–60. [Google Scholar]
- Gao, Y.; Niu, J.; Zhou, R.; Xing, G. ZiFind: Exploiting cross-technology interference signatures for energy-efficient indoor localization. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 2940–2948. [Google Scholar]
- Choi, J. WidthSense: Wi-Fi Discovery via Distance-based Correlation Analysis. IEEE Commun. Lett. 2016, 21, 422–425. [Google Scholar] [CrossRef]
- Petrova, M.; Wu, L.; Mahonen, P.; Riihijarvi, J. Interference Measurements on Performance Degradation between Colocated IEEE 802.11 g/n and IEEE 802.15.4 Networks. In Proceedings of the Sixth International Conference on Networking (2007. ICN ’07), Sainte-Luce, France, 22–28 April 2007; p. 93. [Google Scholar]
- Hossian, M.M.A.; Mahmood, A.; Jäntti, R. Channel ranking algorithms for cognitive coexistence of IEEE 802.15.4. In Proceedings of the 2009 IEEE 20th International Symposium on Personal, Indoor and Mobile Radio Communications, Tokyo, Japan, 13–16 September 2009; pp. 112–116. [Google Scholar]
- ZigBee Standards Organization. ZigBee Specifications; ZigBee Standards Organization: San Ramon, CA, USA, 2012; pp. 1–622. [Google Scholar]
- Zacharias, S.; Newe, T.; O’Keeffe, S.; Lewis, E. 2.4 GHz IEEE 802.15.4 channel interference classification algorithm running live on a sensor node. In Proceedings of the 2012 IEEE Sensors, Taipei, Taiwan, 28–31 Octorber 2012; pp. 1–4. [Google Scholar]
- Iyer, V.; Hermans, F.; Voigt, T. Detecting and Avoiding Multiple Sources of Interference in the 2.4 GHz Spectrum. In Proceedings of the12th European Conference on Wireless Sensor Networks (EWSN), Porto, Portugal, 9–11 February 2015; Abdelzaher, T., Pereira, N., Tovar, E., Eds.; Springer International Publishing: Cham, Switzerland, 2015; pp. 35–51. [Google Scholar]
- Ansari, J.; Ang, T.; Mähönen, P. WiSpot: fast and reliable detection of Wi-Fi networks using IEEE 802.15.4 radios. In Proceedings of the 9th ACM International Symposium on Mobility Management and Wireless Access, Miami, FL, USA, 31 October–4 November 2011; ACM: New York, NY, USA, 2011; pp. 35–44. [Google Scholar]
- Chowdhury, K.R.; Akyildiz, I.F. Interferer Classification, Channel Selection and Transmission Adaptation for Wireless Sensor Networks. In Proceedings of the 9th IEEE International Conference on Communications (ICC ’09), Dresden, Germany, 14–18 June 2009; pp. 1–5. [Google Scholar]
- Rayanchu, S.; Patro, A.; Banerjee, S. Airshark: Detecting non-WiFi RF Devices Using Commodity WiFi Hardware. In Proceedings of the 2011 ACM SIGCOMM Conference on Internet Measurement Conference (IMC ’11), Berlin, Germany, 2–4 November 2011; ACM: New York, NY, USA, 2011; pp. 137–154. [Google Scholar]
- Weng, Z.; Orlik, P.; Kim, K.J. Classification of wireless interference on 2.4 GHz spectrum. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 786–791. [Google Scholar]
- Hermans, F.; Larzon, L.A.; Rensfelt, O.; Gunningberg, P. A Lightweight Approach to Online Detection and Classification of Interference in 802.15.4-based Sensor Networks. SIGBED Rev. 2012, 9, 11–20. [Google Scholar] [CrossRef]
- Nicolas, C.; Marot, M. Dynamic link adaptation based on coexistence-fingerprint detection for WSN. In Proceedings of the 2012 11th Annual Mediterranean Ad Hoc Networking Workshop (Med-Hoc-Net), Ayia Napa, Cyprus, 19–22 June 2012; pp. 90–97. [Google Scholar]
- Barać, F.; Gidlund, M.; Zhang, T. Ubiquitous, Yet Deceptive: Hardware-Based Channel Metrics on Interfered WSN Links. IEEE Trans. Veh. Technol. 2015, 64, 1766–1778. [Google Scholar] [CrossRef]
- Zheng, X.; Cao, Z.; Wang, J.; He, Y.; Liu, Y. ZiSense: Towards Interference Resilient Duty Cycling in Wireless Sensor Networks. In Proceedings of the 12th ACM Conference on Embedded Network Sensor Systems, (SenSys ’14), Memphis, TN, USA, 3–6 November 2014; ACM: New York, NY, USA, 2014; pp. 119–133. [Google Scholar]
- Rondeau, T.W.; D’Souza, M.F.; Sweeney, D.G. Residential microwave oven interference on Bluetooth data performance. IEEE Trans. Consum. Electron. 2004, 50, 856–863. [Google Scholar] [CrossRef]
- Bishop, C.M. Pattern Recognition and Machine Learning (Information Science and Statistics); Springer: Secaucus, NJ, USA, 2006. [Google Scholar]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: New York, NY, USA, 2004. [Google Scholar]
- Crossbow TelosB Mote Plattform, Datasheet. Available online: http://www.willow.co.uk/TelosB_Datasheet.pdf (accessed on 16 June 2017).
- Texas Instruments CC2420 - 2.4 GHz IEEE 802.15.4/ZigBee-ready RF Transceiver. Available online: http://www.ti.com/lit/ds/symlink/cc2420.pdf (accessed on 16 June 2017).
- Chen, Y.; Terzis, A. On the mechanisms and effects of calibrating RSSI measurements for 802.15.4 radios. In Proceedings of the 7th European conference on Wireless Sensor Networks, Coimbra, Portugal, 17–19 February 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 256–271. [Google Scholar]
- Metageek Wi-Spy Chanalizer. Available online: http://files.metageek.net/marketing/data-sheets/MetaGeek_Wi-Spy-Chanalyzer_DataSheet.pdf (accessed on 16 June 2017).
- Boano, C.A.; Voigt, T.; Noda, C.; Römer, K.; Zúñiga, M. JamLab: Augmenting sensornet testbeds with realistic and controlled interference generation. In Proceedings of the 10th ACM/IEEE International Conference on Information Processing in Sensor Networks, Chicago, IL, USA, 12–14 April 2011; pp. 175–186. [Google Scholar]

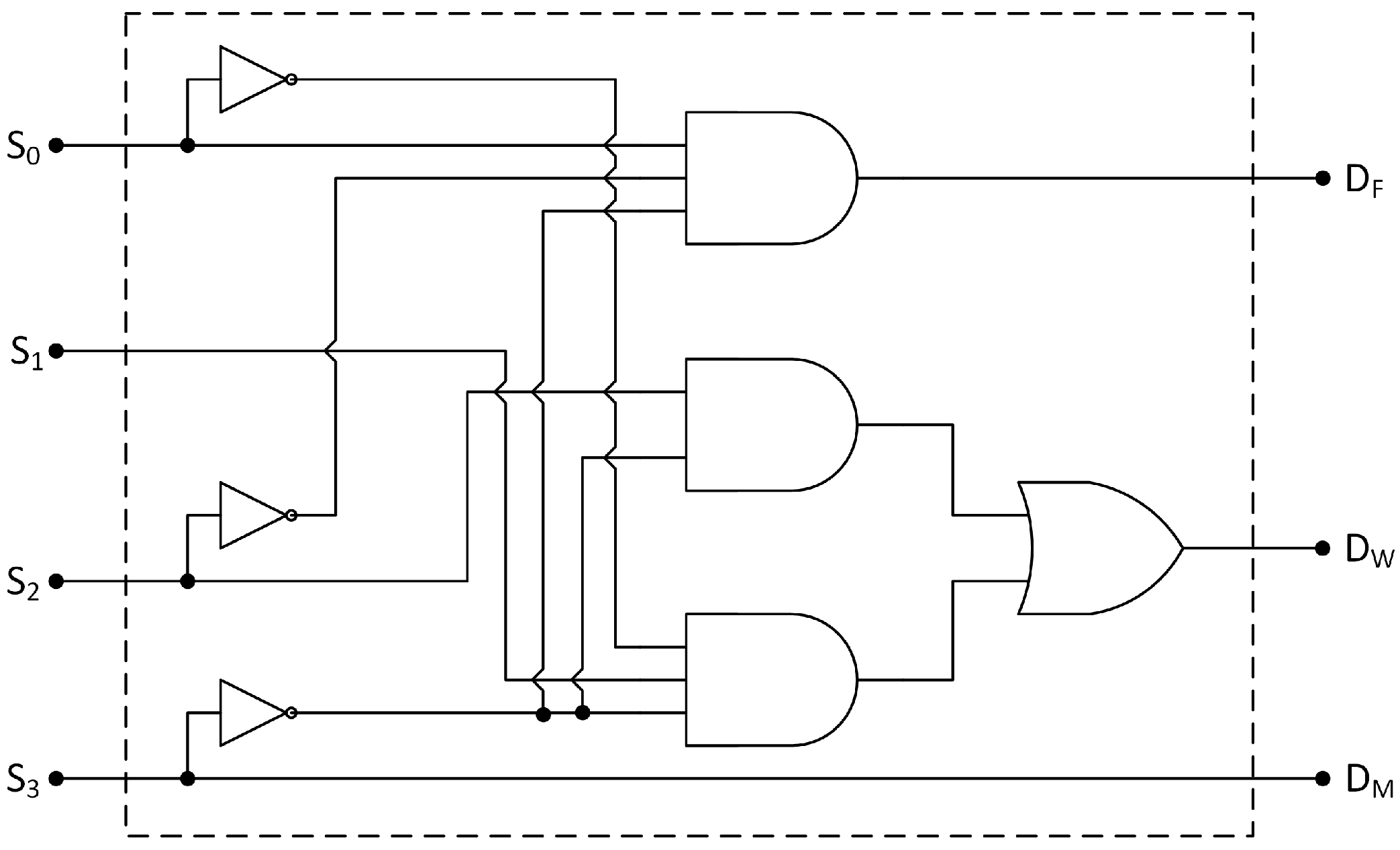


| Classification Outcome | |||
|---|---|---|---|
| 1 | 0 | 0 | The channel is free from the interference sources in the analysis. |
| 0 | 0 | 1 | A MWO was active during the sensing period. |
| 0 | 1 | 0 | An IEEE 802.11 network was overlapping the channel in the analysis. |
| 0 | 0 | 0 | The source of interference is unknown. |
| Channel Status | Detected Interference Source | |||
|---|---|---|---|---|
| IFC | IEEE 802.11 | Microwave Oven | Unknown | |
| IFC | 91.2% | 6.6% | 2.1% | 0.1% |
| IEEE 802.11 | 12.4% | 83.9% | 1.4% | 2.3% |
| Microwave Oven | 0.8% | 16.3% | 82.8% | 0.1% |
| Channel Status | Detected Interference Source | |||
|---|---|---|---|---|
| IFC | IEEE 802.11 | Microwave Oven | Unknown | |
| IFC | 98.2% | 1.7% | 0.1% | 0.0% |
| IEEE 802.11 | 0.1% | 98.9% | 0.3% | 0.7% |
| Channel Status | Detected Interference Source | |||
|---|---|---|---|---|
| IFC | IEEE 802.11 | Microwave Oven | Unknown | |
| IFC | 84.9% | 11.2% | 3.8% | 0.1% |
| IEEE 802.11 | 10.7% | 77.9% | 5.2% | 6.1% |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Grimaldi, S.; Mahmood, A.; Gidlund, M. An SVM-Based Method for Classification of External Interference in Industrial Wireless Sensor and Actuator Networks. J. Sens. Actuator Netw. 2017, 6, 9. https://doi.org/10.3390/jsan6020009
Grimaldi S, Mahmood A, Gidlund M. An SVM-Based Method for Classification of External Interference in Industrial Wireless Sensor and Actuator Networks. Journal of Sensor and Actuator Networks. 2017; 6(2):9. https://doi.org/10.3390/jsan6020009
Chicago/Turabian StyleGrimaldi, Simone, Aamir Mahmood, and Mikael Gidlund. 2017. "An SVM-Based Method for Classification of External Interference in Industrial Wireless Sensor and Actuator Networks" Journal of Sensor and Actuator Networks 6, no. 2: 9. https://doi.org/10.3390/jsan6020009






