Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review
Abstract
:1. Introduction
- Describe basic features about botnet techniques.
- Analyze existing studies relating to the deployment of machine learning in botnet detection and summarize their findings.
- Analyze existing studies relating to the deployment of machine learning in botnet detection in SDN and summarize their findings.
- Identify new challenges and issues that have arisen as a result of existing solutions and suggest directions for future research.
1.1. Botnet Elements
1.1.1. Bot
1.1.2. Botnet
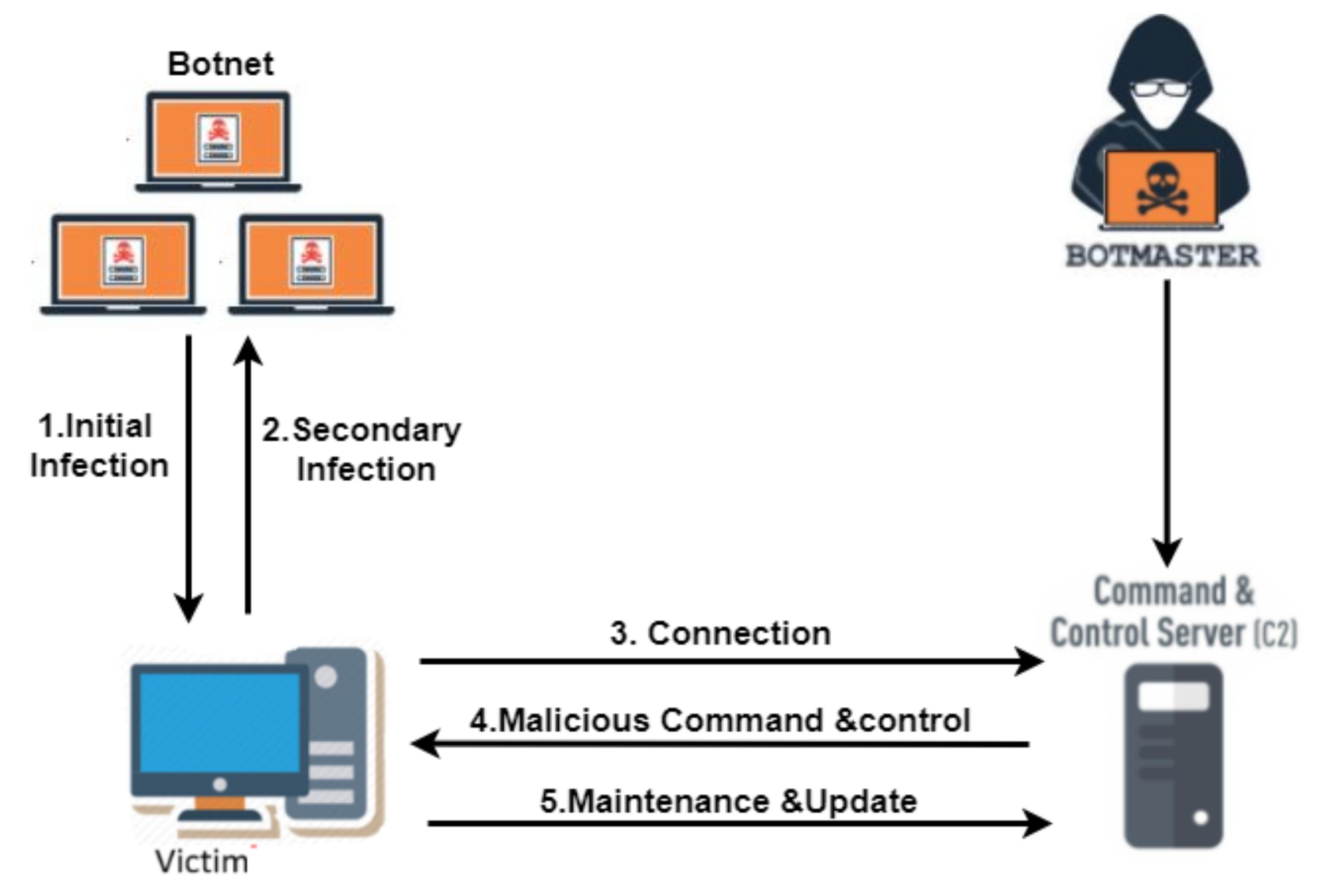
1.1.3. Botmaster
1.1.4. Command-and-Control
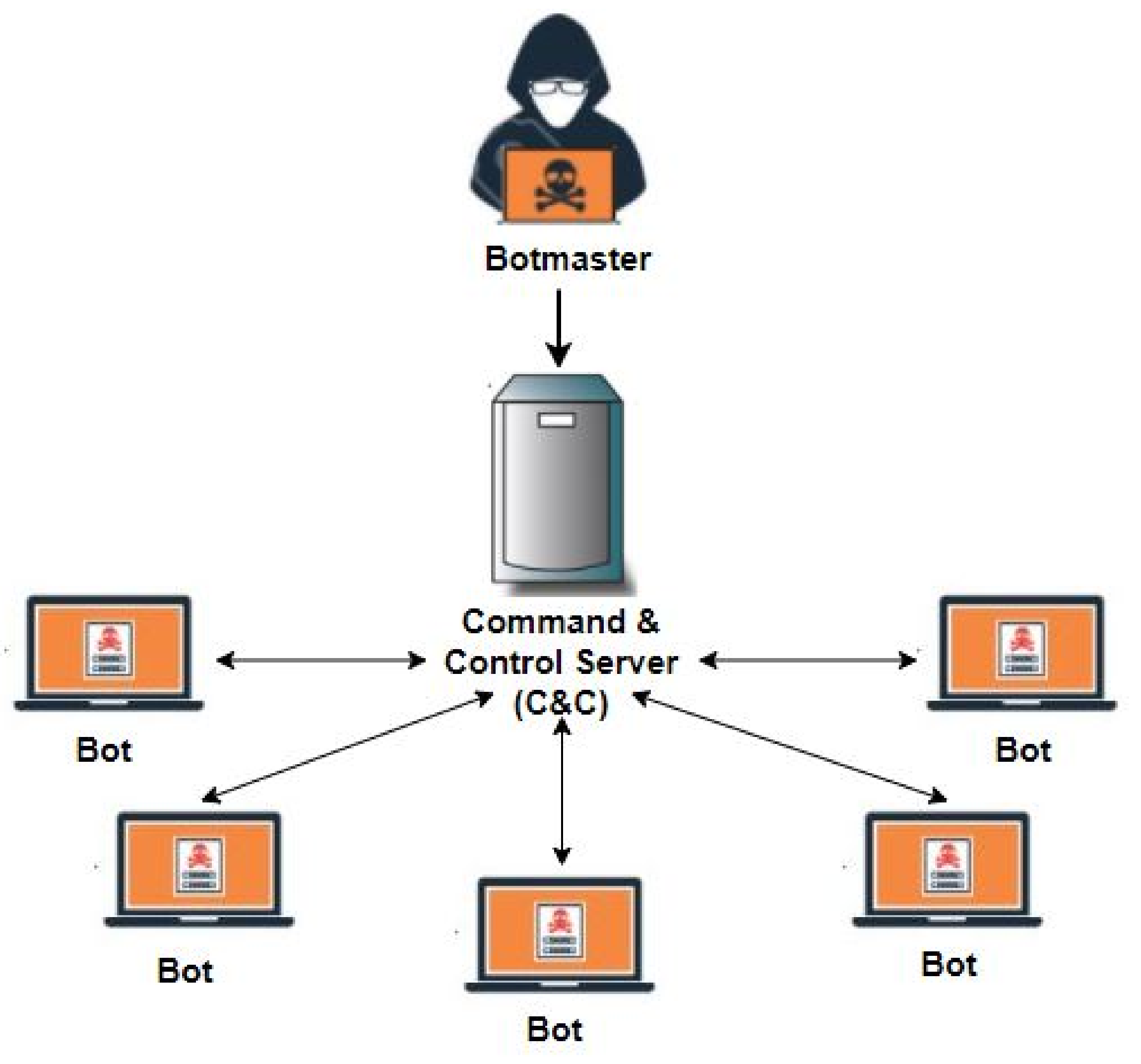
1.2. Botnet Architecture
1.2.1. Centralized Architecture
- Botnet based on IRC: The internet relay chat (IRC) is a protocol of real-time internet text messaging or synchronous conferencing. This protocol is the most popular botnet C&C channel. The reasons for this popularity are: the botmaster has real-time communication with the bots, it supports a large number of clients, it works with different network topologies, it is an open-source and it has expandable design. Spybot, Agobot, SDBot, and GT Bot are the most famous IRC-based botnets.
- Botnet based on HTTP: The hypertext transfer protocol (HTTP) is another common protocol used by C&C servers. HTTP communication is widely used in many web-based applications. These web-based C&C bots attempt to blend into regular HTTP traffic, making them hard to detect. They can easily evade intrusion detection systems (IDSs) and bypass firewalls with port-based filtering techniques. Bobax, ClickBot, Rustock, and the most popular, Blackenergy, are well-known bots that use the HTTP protocol.
1.2.2. Decentralized Architecture
- Botnet based on Peer to Peer (P2P): This communication protocol is mainly used in a decentralized architecture.The goal of P2P botnets is to remove the failure point, which is the main vulnerability of a centralized structure. Therefore, detecting this type of botnet is very difficult. To send commands to all bots over the entire network, the botmaster needs to connect to only one of the bots (peers) [1,14,15].
1.2.3. Hybrid Architecture
1.3. Botnet Life Cycle
1.4. Botnet Threats
1.4.1. Distributed Denial of Service
1.4.2. Spam
1.4.3. Stealing Information
1.4.4. Exploiting Resources
2. Methods
2.1. Search Strategy
2.2. Data Extraction
- a.
- Research contribution.
- b.
- Detection techniques.
- c.
- Botnet protocol.
- d.
- Method.
- e.
- Dataset.
- f.
- Accuracy and other metrics.
3. Research Findings and Discussion
3.1. RQ1: What Are the Latest Studies of Botnet Detection Approaches That Have Been Implemented?
3.1.1. Honeynet-Based Detection
3.1.2. DNS-Based Detection
3.1.3. Intrusion Detection System (IDS)
- 1.
- Signature-based IDS
- 2.
- Anomaly-based IDS
- Host-based anomaly detection In early botnet detection, host-based detection might be effective to identify known malware activities. This strategy both monitors and analyses the internal processes of a computer system and all network traffic received by a host computer. It has the advantage that it can discover if an attack is successful, and it also records what the attacker has performed on the host computer. By examining system traces such as event logs and system calls, this function is effectively accomplished [13,36,37]. The limitations of this system are high error rates and the need for extensive monitoring of all system activities, which consumes host system resources.
- Network-based anomaly detection This approach corresponds to the problem of discovering irregular patterns in network traffic that are not expected behavior. It analyzes and collects network traces, including flow statistics and network packets. Also, it allows a wide range of analysis, including botnet clustering, traffic classification, and network-wide anomaly detection while maintaining the performance of the monitored systems [13,38,39,40]. However, they focus primarily on offline learning, which is not suitable for botnet detection, and they require frequent retraining with new data. Furthermore, [41] has been focused on application detection as well as identifying significant techniques and issues in IP traffic analysis. Whereas [42] presented a review paper on network anomaly detection methods and [43] presented a review of intrusion detection system based on NetFlow. It also explained the principles of flow and classified attacks, and it reviewed detection strategies for botnets, scans, DDoS attacks, and worms in detail.
- Hybrid botnet detection Some authors have driven the development of botnet detection techniques further in conjunction with improving accuracy and precision. Some have used a hybrid intrusion detection system that incorporates the principles of both the network intrusion detection system(NIDS) and the host intrusion detection system (HIDS). Hybrid systems can detect new botnets in the early phase by collecting data and information for analysis from both the host side and the network side. This technique is more effective and efficient since it overcomes the limitations of both HIDS and NIDS [44].
3.2. RQ2: What Are the Latest Studies of Botnet Detection Based on Machine Learning?
3.3. RQ3: What Are the Latest Studies of Botnet Detection in Software-Defined Networks (SDNs)?
3.4. RQ4: What Are the Latest Studies of Botnet Detection Based on Machine Learning (ML) in SDNs?
4. Challenges and Directions for Future Research
4.1. Quantity and Quality of Datasets Used
4.2. Fast-Flux Evasion Techniques
4.3. Deep Packet Inspection (DPI)
4.4. Offline Mode Classification
4.5. High Intensive Resources Required
4.6. Host Acting as Normal
4.7. Overhead in Host-Based Bot Detection
4.8. Computational Power of ML
4.9. Unreliable Extraction of NetFlow Features
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Alothman, B. Similarity based instance transfer learning for botnet detection. Int. J. Intell. Comput. Res. (IJICR) 2018, 9, 880–889. [Google Scholar] [CrossRef]
- Morse, A. Investigation: WannaCry Cyber Attack and the NHS; Report by the National Audit Office. Accessed; National Audit Office: London, UK, 2018; Volume 1. [Google Scholar]
- Amini, P.; Araghizadeh, M.A.; Azmi, R. A survey on Botnet: Classification, detection and defense. In Proceedings of the 2015 International Electronics Symposium (IES), Surabaya, Indonesia, 29–30 September 2015; pp. 233–238. [Google Scholar]
- Alieyan, K.; ALmomani, A.; Manasrah, A.; Kadhum, M.M. A survey of botnet detection based on DNS. Neural Comput. Appl. 2017, 28, 1541–1558. [Google Scholar] [CrossRef]
- Li, X.; Wang, J.; Zhang, X. Botnet detection technology based on DNS. Future Internet 2017, 9, 55. [Google Scholar] [CrossRef] [Green Version]
- Singh, M.; Singh, M.; Kaur, S. Issues and challenges in DNS based botnet detection: A survey. Comput. Secur. 2019, 86, 28–52. [Google Scholar] [CrossRef]
- Gaonkar, S.; Dessai, N.F.; Costa, J.; Borkar, A.; Aswale, S.; Shetgaonkar, P. A survey on botnet detection techniques. In Proceedings of the2020 International Conference on Emerging Trends in Information Technology and Engineering (ic-ETITE), Vellore, India, 24–25 February 2020; pp. 1–6. [Google Scholar]
- Vishwakarma, R.; Jain, A.K. A survey of DDoS attacking techniques and defence mechanisms in the IoT network. Telecommun. Syst. 2020, 73, 3–25. [Google Scholar] [CrossRef]
- Hadianto, R.; Purboyo, T.W. A survey paper on botnet attacks and defenses in software defined networking. Int. J. Appl. Eng. Res. 2018, 13, 483–489. [Google Scholar]
- Ali, I.; Ahmed, A.I.A.; Almogren, A.; Raza, M.A.; Shah, S.A.; Khan, A.; Gani, A. Systematic Literature Review on IoT-Based Botnet Attack. IEEE Access 2020, 8, 212220–212232. [Google Scholar] [CrossRef]
- Silva, S.S.; Silva, R.M.; Pinto, R.C.; Salles, R.M. Botnets: A survey. Comput. Netw. 2013, 57, 378–403. [Google Scholar] [CrossRef]
- Limarunothai, R.; Munlin, M.A. Trends and challenges of botnet architectures and detection techniques. J. Inf. Sci. Technol. 2015, 5, 51–57. [Google Scholar]
- Ghafir, I.; Svoboda, J.; Prenosil, V. A survey on botnet command and control traffic detection. Int. J. Adv. Comput. Netw. Secur. 2015, 5, 7580. [Google Scholar]
- Haddadi, F.; Morgan, J.; Gomes Filho, E.; Zincir-Heywood, A.N. Botnet behaviour analysis using ip flows: With http filters using classifiers. In Proceedings of the 2014 28th International Conference on Advanced Information Networking and Applications Workshops, Victoria, BC, Canada, 13–16 May 2014; pp. 7–12. [Google Scholar]
- Miller, S.; Busby-Earle, C. The role of machine learning in botnet detection. In Proceedings of the 2016 11th International Conference for Internet Technology and Secured Transactions (ICITST), Barcelona, Spain, 5–7 December 2016; pp. 359–364. [Google Scholar]
- Vania, J.; Meniya, A.; Jethva, H. A review on botnet and detection technique. Int. J. Comput. Trends Technol. 2013, 4, 23–29. [Google Scholar]
- Panimalar, P.; Rameshkumar, K. A review on taxonomy of botnet detection. In Proceedings of the 2014 International Conference on Advances in Engineering and Technology (ICAET), Singapore, 29–30 March 2014; pp. 1–4. [Google Scholar]
- Asha, S.; Harsha, T.; Soniya, B. Analysis on botnet detection techniques. In Proceedings of the 2016 International Conference on Research Advances in Integrated Navigation Systems (RAINS), Karnataka, India, 6–7 May 2016; pp. 1–4. [Google Scholar]
- Alauthman, M. An Efficient Approach to Online Bot Detection Based on a Reinforcement Learning Technique. Ph.D. Thesis, Northumbria University, Newcastle upon Tyne, UK, 2016. [Google Scholar]
- Cisco Umbrella. Cisco Annual Internet Report (2018–2023) White Paper. 2020. Available online: https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.html (accessed on 25 April 2021).
- Zeidanloo, H.R.; Shooshtari, M.J.Z.; Amoli, P.V.; Safari, M.; Zamani, M. A taxonomy of botnet detection techniques. In Proceedings of the 2010 3rd International Conference on Computer Science and Information Technology, Chengdu, China, 9–11 July 2010; Volume 2, pp. 158–162. [Google Scholar]
- Karim, A.; Salleh, R.B.; Shiraz, M.; Shah, S.A.A.; Awan, I.; Anuar, N.B. Botnet detection techniques: Review, future trends, and issues. J. Zhejiang Univ. Sci. C 2014, 15, 943–983. [Google Scholar] [CrossRef]
- Samson, F.; Vaidehi, V. Hybrid botnet detection using ensemble approach. J. Theor. Appl. Inf. Technol 2017, 95, 1646–1654. [Google Scholar]
- Hyslip, T.S.; Pittman, J.M. A survey of botnet detection techniques by command and control infrastructure. J. Digit. Forensics Secur. Law 2015, 10, 2. [Google Scholar] [CrossRef] [Green Version]
- Krishnan, P.; Duttagupta, S.; Achuthan, K. VARMAN: Multi-plane security framework for software defined networks. Comput. Commun. 2019, 148, 215–239. [Google Scholar] [CrossRef]
- Amit, D.; Prashant, G. Botnet Detection through DNS based approach. Int. J. Appl. Innov. Eng. Manag. (IJAIEM) 2013, 2, 497–501. [Google Scholar]
- Dagon, D.; Zou, C.C.; Lee, W. Modeling Botnet Propagation Using Time Zones. In Proceedings of the Network and Distributed System Security Symposium, NDSS, San Diego, CA, USA, 23–26 February 2006; Volume 6, pp. 2–13. [Google Scholar]
- Hassan, M.M.M. Network Intrusion Detection System Using Genetic Algorithm and Fuzzy Logic. Ph.D. Thesis, Gauhati University, Guwahati, India, 2013. [Google Scholar]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J. Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity 2019, 2, 1–22. [Google Scholar] [CrossRef]
- Ieracitano, C.; Adeel, A.; Morabito, F.C.; Hussain, A. A novel statistical analysis and autoencoder driven intelligent intrusion detection approach. Neurocomputing 2020, 387, 51–62. [Google Scholar] [CrossRef]
- Nguyen, M.T.; Kim, K. Genetic convolutional neural network for intrusion detection systems. Future Gener. Comput. Syst. 2020, 113, 418–427. [Google Scholar] [CrossRef]
- Pawlicki, M.; Choraś, M.; Kozik, R. Defending network intrusion detection systems against adversarial evasion attacks. Future Gener. Comput. Syst. 2020, 110, 148–154. [Google Scholar] [CrossRef]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Beigi, E.B.; Jazi, H.H.; Stakhanova, N.; Ghorbani, A.A. Towards effective feature selection in machine learning-based botnet detection approaches. In Proceedings of the 2014 IEEE Conference on Communications and Network Security, San Francisco, CA, USA, 29–31 October 2014; pp. 247–255. [Google Scholar]
- Chowdhury, S.; Khanzadeh, M.; Akula, R.; Zhang, F.; Zhang, S.; Medal, H.; Marufuzzaman, M.; Bian, L. Botnet detection using graph-based feature clustering. J. Big Data 2017, 4, 1–23. [Google Scholar] [CrossRef] [Green Version]
- Creech, G.; Hu, J. A semantic approach to host-based intrusion detection systems using contiguousand discontiguous system call patterns. IEEE Trans. Comput. 2013, 63, 807–819. [Google Scholar] [CrossRef]
- Garfinkel, T.; Rosenblum, M. A virtual machine introspection based architecture for intrusion detection. In Proceedings of the Network and Distributed System Security Symposium, NDSS 2003, San Diego, CA, USA, 5–8 May 2003; Volume 3, pp. 191–206. [Google Scholar]
- Gu, G.; Perdisci, R.; Zhang, J.; Lee, W. Botminer: Clustering analysis of network traffic for protocol-and structure-independent botnet detection. In Proceedings of the 17th USENIX Security Symposium, San Jose, CA, USA, 28 July–1 August 2008. [Google Scholar]
- Saad, S.; Traore, I.; Ghorbani, A.; Sayed, B.; Zhao, D.; Lu, W.; Felix, J.; Hakimian, P. Detecting P2P botnets through network behavior analysis and machine learning. In Proceedings of the 2011 Ninth Annual International Conference on privacy, Security and Trust, Montreal, QC, Canada, 19–21 July 2011; pp. 174–180. [Google Scholar]
- Zhao, D.; Traore, I.; Sayed, B.; Lu, W.; Saad, S.; Ghorbani, A.; Garant, D. Botnet detection based on traffic behavior analysis and flow intervals. Comput. Secur. 2013, 39, 2–16. [Google Scholar] [CrossRef]
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Network anomaly detection: Methods, systems and tools. IEEE Commun. Surv. Tutor. 2013, 16, 303–336. [Google Scholar] [CrossRef]
- Zhang, W.; Yang, Q.; Geng, Y. A survey of anomaly detection methods in networks. In Proceedings of the 2009 International Symposium on Computer Network and Multimedia Technology, Wuhan, China, 18–20 December 2009; pp. 1–3. [Google Scholar]
- Sperotto, A.; Schaffrath, G.; Sadre, R.; Morariu, C.; Pras, A.; Stiller, B. An overview of IP flow-based intrusion detection. IEEE Commun. Surv. Tutor. 2010, 12, 343–356. [Google Scholar] [CrossRef] [Green Version]
- Bridges, R.A.; Glass-Vanderlan, T.R.; Iannacone, M.D.; Vincent, M.S.; Chen, Q. A survey of intrusion detection systems leveraging host data. ACM Comput. Surv. (CSUR) 2019, 52, 1–35. [Google Scholar] [CrossRef] [Green Version]
- Brezo, F.; de la Puerta, J.G.; Ugarte-Pedrero, X.; Santos, I.; Bringas, P.G. A supervised classification approach for detecting packets originated in a HTTP-based botnet. CLEI Electron. J. 2013, 16, 2. [Google Scholar] [CrossRef] [Green Version]
- Tariq, F.; Baig, S. Botnet classification using centralized collection of network flow counters in software defined networks. Int. J. Comput. Sci. Inf. Secur. 2016, 14, 1075. [Google Scholar]
- Barthakur, P.; Dahal, M.; Ghose, M.K. A framework for P2P botnet detection using SVM. In Proceedings of the 2012 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery, Sanya, China, 10–12 October 2012; pp. 195–200. [Google Scholar]
- Bilge, L.; Balzarotti, D.; Robertson, W.; Kirda, E.; Kruegel, C. Disclosure: Detecting botnet command and control servers through large-scale netflow analysis. In Proceedings of the 28th Annual Computer Security Applications Conference, Orlando, FL, USA, 3–7 December 2012; pp. 129–138. [Google Scholar]
- Wang, X.; Xu, Y.; Chen, C.; Yang, X.; Chen, J.; Ruan, L.; Xu, Y.; Chen, R. Machine Learning Empowered Spectrum Sharing in Intelligent Unmanned Swarm Communication Systems: Challenges, Requirements and Solutions. IEEE Access 2020, 8, 89839–89849. [Google Scholar] [CrossRef]
- Carl, L.; Walsh, R.; Lapsley, D.; Strayer, W.T. Using machine learning technliques to identify botnet traffic. In Proceedings of the 2006 31st IEEE Conference on Local Computer Networks, Tampa, FL, USA, 14–16 November 2006. [Google Scholar]
- Al-Jarrah, O.Y.; Alhussein, O.; Yoo, P.D.; Muhaidat, S.; Taha, K.; Kim, K. Data randomization and cluster-based partitioning for botnet intrusion detection. IEEE Trans. Cybern. 2015, 46, 1796–1806. [Google Scholar] [CrossRef]
- Stevanovic, M.; Pedersen, J.M. An analysis of network traffic classification for botnet detection. In Proceedings of the 2015 International Conference on Cyber Situational Awareness, Data Analytics and Assessment (CyberSA), London, UK, 8–9 June 2015; pp. 1–8. [Google Scholar]
- Chen, R.; Niu, W.; Zhang, X.; Zhuo, Z.; Lv, F. An effective conversation-based botnet detection method. Math. Probl. Eng. 2017, 2017. [Google Scholar] [CrossRef] [Green Version]
- Comaneci, D.; Dobre, C. Securing networks using SDN and machine learning. In Proceedings of the 2018 IEEE International Conference on Computational Science and Engineering (CSE), Bucharest, Romania, 29–31 October 2018; pp. 194–200. [Google Scholar]
- Gadelrab, M.S.; ElSheikh, M.; Ghoneim, M.A.; Rashwan, M. BotCap: Machine learning approach for botnet detection based on statistical features. Int. J. Commun. Netw. Inf. Secur 2018, 10, 563. [Google Scholar]
- Homayoun, S.; Ahmadzadeh, M.; Hashemi, S.; Dehghantanha, A.; Khayami, R. BoTShark: A deep learning approach for botnet traffic detection. In Cyber Threat Intelligence; Springer: Cham, Switzerland, 2018; pp. 137–153. [Google Scholar]
- Ryu, S.; Yang, B. A comparative study of machine learning algorithms and their ensembles for botnet detection. J. Comput. Commun. 2018, 6, 119. [Google Scholar] [CrossRef] [Green Version]
- Khan, R.U.; Kumar, R.; Alazab, M.; Zhang, X. A Hybrid Technique to Detect Botnets, Based on P2P Traffic Similarity. Technical Report. In Proceedings of the 2019 Cybersecurity and Cyberforensics Conference (CCC), Melbourne, VIC, Australia, 8–9 May 2019. [Google Scholar]
- Khan, R.U.; Zhang, X.; Kumar, R.; Sharif, A.; Golilarz, N.A.; Alazab, M. An adaptive multi-layer botnet detection technique using machine learning classifiers. Appl. Sci. 2019, 9, 2375. [Google Scholar] [CrossRef] [Green Version]
- Tuan, T.A.; Long, H.V.; Son, L.H.; Kumar, R.; Priyadarshini, I.; Son, N.T.K. Performance evaluation of Botnet DDoS attack detection using machine learning. Evol. Intell. 2019, 13, 283–294. [Google Scholar] [CrossRef]
- Vinayakumar, R.; Soman, K.; Poornachandran, P.; Alazab, M.; Jolfaei, A. DBD: Deep learning DGA-based botnet detection. In Deep Learning Applications for Cyber Security; Springer: Berlin/Heidelberg, Germany, 2019; pp. 127–149. [Google Scholar]
- Zhou, J.; Xu, Z.; Rush, A.M.; Yu, M. Automating Botnet Detection with Graph Neural Networks. arXiv 2020, arXiv:2003.06344. [Google Scholar]
- Gahelot, P.; Dayal, N. Flow based botnet traffic detection using machine learning. In Proceedings of ICETIT 2019; Springer: Cham, Switzerland, 2020; pp. 418–426. [Google Scholar]
- Asadi, M.; Jamali, M.A.J.; Parsa, S.; Majidnezhad, V. Detecting botnet by using particle swarm optimization algorithm based on voting system. Future Gener. Comput. Syst. 2020, 107, 95–111. [Google Scholar] [CrossRef]
- Shi, W.C.; Sun, H.M. DeepBot: A time-based botnet detection with deep learning. Soft Comput. 2020, 24, 16605–16616. [Google Scholar] [CrossRef]
- Soe, Y.N.; Feng, Y.; Santosa, P.I.; Hartanto, R.; Sakurai, K. Machine Learning-Based IoT-Botnet Attack Detection with Sequential Architecture. Sensors 2020, 20, 4372. [Google Scholar] [CrossRef]
- Lee, S.; Abdullah, A.; Jhanjhi, N.; Kok, S. Classification of botnet attacks in IoT smart factory using honeypot combined with machine learning. PeerJ Comput. Sci. 2021, 7, e350. [Google Scholar] [CrossRef] [PubMed]
- Almutairi, S.; Mahfoudh, S.; Almutairi, S.; Alowibdi, J.S. Hybrid Botnet Detection Based on Host and Network Analysis. J. Comput. Netw. Commun. 2020, 2020. [Google Scholar] [CrossRef]
- Alharbi, T. Deployment of blockchain technology in software defined networks: A survey. IEEE Access 2020, 8, 9146–9156. [Google Scholar] [CrossRef]
- Elsayed, M.S.; Le-Khac, N.A.; Jurcut, A.D. InSDN: A Novel SDN Intrusion Dataset. IEEE Access 2020, 8, 165263–165284. [Google Scholar] [CrossRef]
- Tank, G.P.; Dixit, A.; Vellanki, A.; Annapurna, D. Software-Defined Networking: The New Norm for Networks; Open Networking Foundation: Menlo Park, CA, USA, 2012. [Google Scholar]
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow: Enabling innovation in campus networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- Blial, O.; Ben Mamoun, M.; Benaini, R. An overview on SDN architectures with multiple controllers. J. Comput. Netw. Commun. 2016, 2016. [Google Scholar] [CrossRef] [Green Version]
- Adnan, M.; Iqbal, J.; Waheed, A.; Amin, N.U.; Zareei, M.; Goudarzi, S.; Umer, A. On the Design of Efficient Hierarchic Architecture for Software Defined Vehicular Networks. Sensors 2021, 21, 1400. [Google Scholar] [CrossRef]
- Gude, N.; Koponen, T.; Pettit, J.; Pfaff, B.; Casado, M.; McKeown, N.; Shenker, S. NOX: Towards an operating system for networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 105–110. [Google Scholar] [CrossRef]
- Ahmed, U.; Raza, I.; Hussain, S.A.; Ali, A.; Iqbal, M.; Wang, X. Modelling cyber security for software-defined networks those grow strong when exposed to threats. J. Reliab. Intell. Environ. 2015, 1, 123–146. [Google Scholar] [CrossRef] [Green Version]
- Shafi, Q.; Basit, A. DDoS Botnet prevention using blockchain in software defined Internet of Things. In Proceedings of the 2019 16th International Bhurban Conference on Applied Sciences and Technology (IBCAST), Islamabad, Pakistan, 8–12 January 2019; pp. 624–628. [Google Scholar]
- Shin, S.W.; Porras, P.; Yegneswara, V.; Fong, M.; Gu, G.; Tyson, M. Fresco: Modular composable security services for software-defined networks. In Proceedings of the 20th Annual Network & Distributed System Security Symposium, NDSS, San Diego, CA, USA, 24–27 February 2013. [Google Scholar]
- Wijesinghe, U.; Tupakula, U.; Varadharajan, V. Botnet detection using software defined networking. In Proceedings of the 2015 22nd International Conference on Telecommunications (ICT), Sydney, Australia, 27–29 April 2015; pp. 219–224. [Google Scholar]
- Nanda, S.; Zafari, F.; DeCusatis, C.; Wedaa, E.; Yang, B. Predicting network attack patterns in SDN using machine learning approach. In Proceedings of the 2016 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Palo Alto, CA, USA, 7–10 November 2016; pp. 167–172. [Google Scholar]
- Tariq, F.; Baig, S. Machine learning based botnet detection in software defined networks. Int. J. Secur. Its Appl. 2017, 11, 1–11. [Google Scholar] [CrossRef]
- Su, S.C.; Chen, Y.R.; Tsai, S.C.; Lin, Y.B. Detecting p2p botnet in software defined networks. Secur. Commun. Netw. 2018, 2018. [Google Scholar] [CrossRef] [Green Version]
- Yang, L.; Zhao, H. DDoS attack identification and defense using SDN based on machine learning method. In Proceedings of the 2018 15th International Symposium on Pervasive Systems, Algorithms and Networks (I-SPAN), Yichang, China, 16–18 October 2018; pp. 174–178. [Google Scholar]
- Park, Y.; Kengalahalli, N.V.; Chang, S.Y. Distributed security network functions against botnet attacks in software-defined networks. In Proceedings of the 2018 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Verona, Italy, 27–29 November 2018; pp. 1–7. [Google Scholar]
- Nugraha, B.; Murthy, R.N. Deep Learning-based Slow DDoS Attack Detection in SDN-based Networks. In Proceedings of the 2020 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), online, 9–12 November 2020; pp. 51–56. [Google Scholar]
- Dehkordi, A.B.; Soltanaghaei, M.; Boroujeni, F.Z. The DDoS attacks detection through machine learning and statistical methods in SDN. J. Supercomput. 2021, 77, 2383–2415. [Google Scholar] [CrossRef]
- Kumar, S.A.; Xu, B. A Machine Learning Based Approach to Detect Malicious Fast Flux Networks. In Proceedings of the 2018 IEEE Symposium Series on Computational Intelligence (SSCI), Bangalore, India, 18–21 November 2018; pp. 1676–1683. [Google Scholar]
- Daya, A.A.; Salahuddin, M.A.; Limam, N.; Boutaba, R. BotChase: Graph-Based Bot Detection Using Machine Learning. IEEE Trans. Netw. Serv. Manag. 2020, 17, 15–29. [Google Scholar] [CrossRef] [Green Version]
- Lagraa, S.; François, J.; Lahmadi, A.; Miner, M.; Hammerschmidt, C.; State, R. BotGM: Unsupervised graph mining to detect botnets in traffic flows. In Proceedings of the 2017 1st Cyber Security in Networking Conference (CSNet), Rio de Janeiro, Brazil, 18–20 October 2017; pp. 1–8. [Google Scholar]
- Blaise, A.; Bouet, M.; Conan, V.; Secci, S. BotFP: Fingerprints clustering for bot detection. In Proceedings of the NOMS 2020—2020 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 20–24 April 2020; pp. 1–7. [Google Scholar]






| Protocols | Def | Advantages | Examples |
|---|---|---|---|
| IRC | IRC is a protocol of real-time internet text messaging chat; Mainly used in centralized architecture. | 1. Low-latency communication. 2. Simple commands. 3. Private (one-to-one) communication. 4. Capable of group (many to-many) communication. 5. simple to set up. 6. Flexibility in communication. 7. Anonymous real-time communication | Agobot, SDBot, Spybot, and GT Bot |
| HTTP | HTTP protocols attempt to blend botnet traffic into regular HTTP traffic. Mainly used in centralized architecture. | Difficult to detect and easily bypasses firewalls. | Bobax, ClickBot, Rustock and Blackenergy. |
| P2P | P2P is a communication protocol which is mainly used in decentralized architecture | hard to detect, very high resilience. | Slapper, Sinit, Phatbot, Nugache, Storm. |
| Research Questions (RQs) | Discussion |
|---|---|
| RQ1: What are the latest studies of botnet detection approaches that have been implemented? | Discuss the approaches to detect botnets recently proposed in the literature and their limitations. |
| RQ2: What are the latest studies of botnet detection based on machine learning? | Present an overview of machine learning and summarize the studies in detecting botnets in network traffic that use machine learning techniques. |
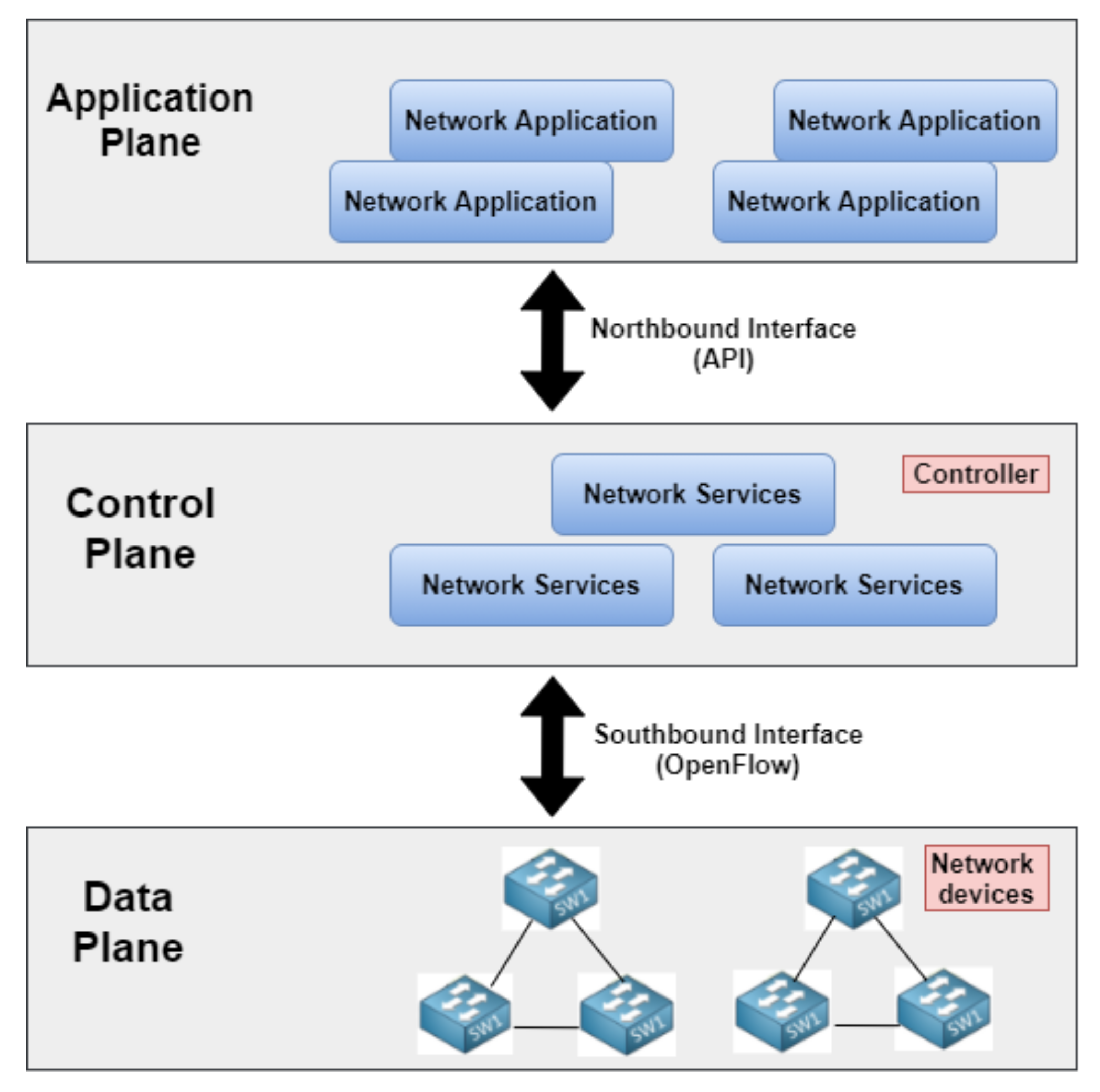
| RQ3: What are the latest studies of botnet detection in Software-defined Networks (SDNs)? | Present an overview of SDN characteristics and summarize studies of botnet detection that use it. |
| RQ4: What are the latest studies of botnet detection based on machine learning (ML) in SDNs? | Discuss recent studies that detected botnets based on machine learning in SDN and their results. |
| Ref/Year | Contribution | Protocol | Methods | Dataset | Result | Comments |
|---|---|---|---|---|---|---|
| [50]/2006 | First paper introduce botnet detection based on ML. | IRC | Bayesian networks | Dartmouth’s wireless campus network traffic traces | FPR: 15.04% | The system failed to capture botnet-specific network profiles effectively |
| [38]/2008 | Implement BotMiner prototype system to identify bot hosts. | IRC, HTTP, P2P | clustering algorithms | Real network traces | Accuracy: 99.6% | Achieves an extremely high detection rate with limited FPR in a real-world network trace |
| [39] 2011 | System considers both flow-based features and host-based features. | P2P | Gaussian-based, KNN, SVM, NB, NN | Ericsson Research in Hungary | Accuracy: 97% | Their dataset is public but there is only one infected machine for each type of botnet, therefore no synchronization analysis can be done |
| [48]/2012 | Proposed Disclosure, method for detecting botnets on a large scale. | IRC, HTTP, P2P | RF, J48 DT, SVM | university network dataset. | TPR: 65% FPR: 1% | There are no details of how many trees used on average in RF classifier |
| [34]/2014 | Indicate botnet detection based on flow based and ML. | IRC, HTTP, P2P | C4.5 DT | botnet (2014) (ISOT, ISCX 2012, and botnet traffic generating). | Accuracy: 75% FPR: 2.3% | Focuses on finding a mixture of packet-based, time-based, and behavior-based features that can be used to extract bot traffic |
| [51]/2016 | Built an RDPLM that based on feature selection. | P2P | C4.5, DT, RT, | ISOT | Accuracy: 99.984% Training time: 21.38 s | The computational complexity and power increase at an exponential rate with this large dataset. |
| [53]/2017 | Aimed to detect botnet under high-speed network environment. | IRC, HTTP, P2P | RF | CTU | Accuracy: 93.6% FAR: 0.3% | The researchers used only offline data; there was no online collection of other data. |
| [56]/2018 | proposed botnet traffic analyzer based on a deep learning approach called BoTShark. | IRC, P2P | CNN, SA | ISCX | TPR: 0.91 FPR: 0.13 | DL requires a huge amount of data and large amounts of processing power. |
| [55]/2018 | botnet detection based on statistics features of network traffic using ML. | IRC, HTTP | J48, SVM | Real Botware sample collect it in their laboratory | Accuracy: HTTP (80%), IRC (95%). FPR: HTTP (0.05%), IRC (0.025%) | Able to identify infected hosts without requiring to collect information about them. |
| [57]/2018 | ML ensembles flow-based for botnet detection | IRC, HTTP, P2P | GNB, NN, DT | CTU-13 | F1 score over 0.99 | DL needs a huge amount of data for progressive learning, as well as high computational power. |
| [59]/2019 | Multi-layer approach to classify P2P traffic as normal or botnet based on ML classifier on network features. | P2P | DT, KNN, LR and ANN | CTU, ISOT | Accuracy: 98.7% | DT achieved better results than other proposed models KNN, LR and ANN |
| [61]/2019 | Proposed DBD, a scalable deep learning DGA-based botnet detection system. | IRC, HTTP | CNN-LSTM | DGArchive, OSINT, internal network | Accuracy: 97.80% | Only DDoS attacks, one type of botnet attack, were included in this paper. |
| [58]/2019 | Novel approach based in two-stage traffic classification. | P2P | DT, NB and ANN | CTU-13 | Accuracy: 94.4% | NB was the lowest accuracy in this study, and they Prove that is used a two-stage technique is effective to detect P2P botnet traffic |
| [60]/2020 | Analysis of the machine learning methods for botnet DDoS attack detection. | IRC, HTTP | DT, ANN, SVM, NB, USML | KDD99, UNBS-NB 15 dataset | Accuracy: 98.08% | Only DDoS attacks, one type of botnet attack, were included in this paper. |
| [66]/2020 | botnet detection framework with sequential detection architecture based on ML in IoT network. | IRC, HTTP, P2P | ANN, J48 DT, NB | N-BaIoT dataset | Accuracy: 99% | Able to detect the known attacks and unknown attacks and their variances. |
| [62]/2020 | P2P botnet detection based on Deep Learning. | P2P | GNN | CAIDA | Accuracy: 99.5% | The method is restricted to detecting attack nodes, especially in the sense of botnets, and does not detect individual attack flows. |
| [63]/2020 | Indicate P2P botnet detection based on ML using three modules feature extraction, feature selection or reduction, and classification | P2P | J48 DT | PeerRush, botnet (2014) (ISOT, ISCX 2012, and botnet traffic generating). | Accuracy: 99.94% | The main restriction is the complexity of the model and a longer processing run-time |
| [65]/2020 | Aimed to detect botnets by inspecting the behaviors of network traffic from network packets using DL. | IRC, HTTP | LSTM-RNN, MCFP | real dataset collect it. | Accuracy: 99.36% | The proposed method able to detect different kinds of major botnets, as well as to adapt to the situation when those botnets alter how they interact or attack |
| [68]/2020 | Hybrid botnet detection correlation between network traffic analysis and host traffic analysis. | IRC, HTTP, P2P | NB, DT | ISCX, CTU-13 | Accuracy: 99.6% | The proposed technique implements the classification algorithm in an offline mode |
| Ref/Year | Contribution | Controller | Layer | Classifier | Dataset | Results | Comments |
|---|---|---|---|---|---|---|---|
| [79]/2015 | Using IPFIX template for botnet detection in SDN. | POX Controller | Controller plane | DT, SVM, Bayesian networks | Private dataset | DT high Accuracy (ACC) detect P2P | The approach does not share evaluation results. |
| [46]/2016 | Propose centralized collection of flow statistics for botnet detection using OpenFlow counters. | Opendaylight Controller. | Application plane | C4.5, DT | CTU-13, ISOT | ACC: 80% | This study aims to detect the attacks on the data plane to reduce the controller overhead |
| [80]/2016 | first paper that leverages ML approach for defining security rules on the SDN controller. | Not mention. | Controller plane | C4.5 DT, Bayesian Network, DT, NB | LongTail | ACC: 91.68% | The results show that BayesNet performs better than the other three algorithms. |
| [81]/2017 | flow-based approach to detect botnet by ML to SDN. | Opendaylight Controller | Application plane | C4.5 DT | CTU-13, ISOT | ACC: 97% known botnets, 90% unknown botnets. | the method of this study requires extensive computation |
| [82]/2018 | Propose framework integrated SDN and ML to P2P botnet. | Ryu Controller | Controller plane | KNN, SVM | PeerRush | ACC: 99.88% | the approach in this paper using binary classifiers for each P2P traffic in SDN. |
| [83]/ 2018 | Propose SDN framework to detect DDoS based on ML for the Campus network. | Ryu Controller | Controller plane | SVM | KDD99 | ACC: 99.8%. | The dataset used is old and did not include recent DDoS attacks types |
| [84]/2018 | Proposed a framework to mitigate botnet by SDN/NFV and ML. | Floodlight Controller | Controller plane | RF | CTU-13 | ACC: 100%TPR: 92% FPR: 10% | This work needs to cover more protocols to defend against botnet attacks |
| [85]/2020 | prposed hybrid CNN-LSTM model to detect slow DDoS attacks in SDN. | ONOS controller | Application Plane | CNN-LSTM | Synthetic Generation of Traffic flow | >99% | The detection framework is performed by using offline datasets |
| [86]/2021 | Proposed DDoS detection based on hybrid ML and the statistical method on SDN | Floodlight Controller | Controller plane | RT, LR, J48, BN and REPTree | UNB-ISCX, CTU-13, and ISOT datasets | In UNB-ISCX dataset: ACC: 99.85% FPR: 0.1%, In CTU-13 dataset: ACC: 99.12% | This method can be improved in networks by involving more than one controller |
| Dataset | Year | Host Data | Network Data | Labelled | Classes | Protocols | Avg. Sample | Sample Units | Scenario | Comments |
|---|---|---|---|---|---|---|---|---|---|---|
| KDD99 | 1999 | Yes | Yes | Yes | 4 | __ | 5.2 M | TCP packet | 1 | 41 features of samples that represent both legitimate and attack traffic. It is old and did not include recent attacks types. |
| ISOT | 2010 | No | Yes | Yes | 2 | HTTP and P2P | 1.7 M | Flows | 1 | It combines several existing malicious and non-malicious datasets. It includes lack normal data |
| Ctu-13 | 2011 | No | Yes | Yes | 7 | IRC, HTTP and P2P | 80 M | Flows | 13 | Well-known public benchmark includes both botnet and normal traffic. The first submitted in 2013, but dataset’s website states 2011. |
| ISCX IDS | 2012 | No | Yes | No | 4 | IRC | 2.5 M | Flows | 7 | It uses in several IDS studies |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shinan, K.; Alsubhi, K.; Alzahrani, A.; Ashraf, M.U. Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review. Symmetry 2021, 13, 866. https://doi.org/10.3390/sym13050866
Shinan K, Alsubhi K, Alzahrani A, Ashraf MU. Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review. Symmetry. 2021; 13(5):866. https://doi.org/10.3390/sym13050866
Chicago/Turabian StyleShinan, Khlood, Khalid Alsubhi, Ahmed Alzahrani, and Muhammad Usman Ashraf. 2021. "Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review" Symmetry 13, no. 5: 866. https://doi.org/10.3390/sym13050866
APA StyleShinan, K., Alsubhi, K., Alzahrani, A., & Ashraf, M. U. (2021). Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review. Symmetry, 13(5), 866. https://doi.org/10.3390/sym13050866






