Survey on Prominent RFID Authentication Protocols for Passive Tags
Abstract
:1. Introduction
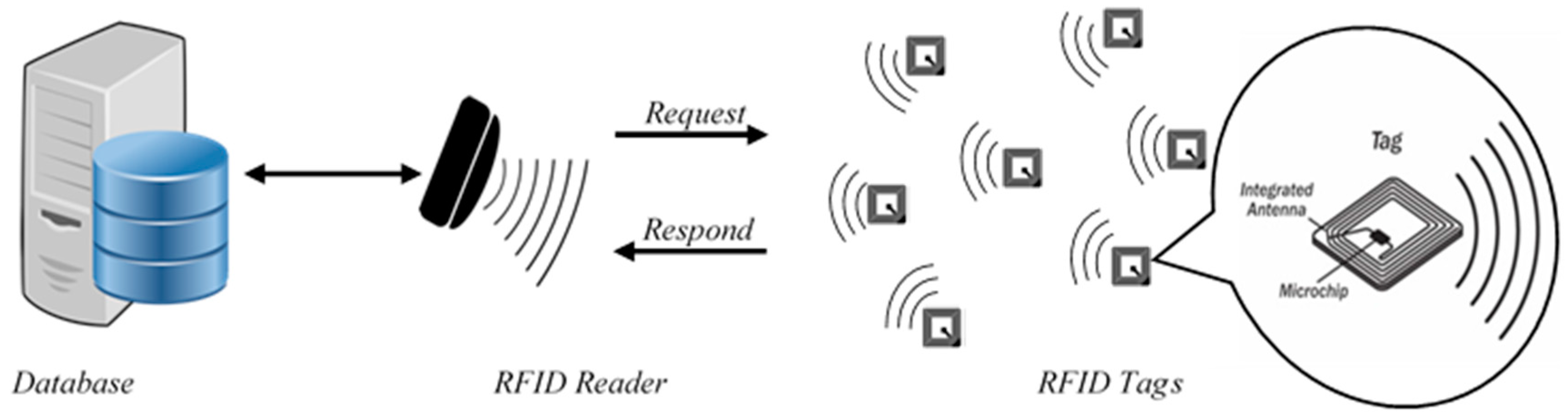
2. System Architecture and Communication Model
- A passive tag operates without battery, as the tag is energized when the reader interrogates it by sending a signal to request tag information. It has a short transmission range in communication, and has limited resources in term of storage. It is considered the lowest in cost and has a higher lifespan.
- A semi-passive tag has a battery for its internal chip circuit; however, it is also energized by the reader interrogation, as in the passive tag.
- An active tag runs with battery and can have two-way communication between tag and reader. It is larger due to the larger storage capacity and battery. The transmission range is also larger compared to passive tags. It is more expensive and has a limited life depending on the battery lifespan [2].
3. Security Requirements and Threats
3.1. Security Requirements
- Mutual Authentication: the main requirement in a simple scenario of RFID communication session is the authentication between the reader and tag before exchanging or transmitting any secret or valuable information. Both tag and reader have to prove their legitimacy to each other to start a secure communication.
- Confidentiality: all of the transmitted messages have to be secure in which secret information and values that are used to execute communication cannot be obtained by an unauthorized user.
- Integrity: the transmitted data has to maintain its accuracy and not to be altered or changed during communication.
- Availability: the communication should be successfully executed by maintaining a synchronous state between the RFID entities. Communication values have to be updated after every successful session to provide system availability.
- Privacy: all of the secret information such as tag identity has to be secured in order to provide anonymity and avoid tracing the tag or its location.
- Forward Security: the transmitted data during communication have to be independent and updated for every session, and cannot be used or related to another authentication session. If a tag or any information is compromised, it is impossible for an adversary to pass the authentication on or violate the system.
3.2. Security Threats
- Replay Attack: an adversary tries to capture the tag response and resend it to the reader to start a successful communication with the reader or obtain any secret information.
- Man-In-The-Middle: an adversary intercepts the message between two legitimate entities tag/reader to modify it and send it back.
- Impersonate Attack: an adversary obtains either the reader or tag identity information to create a forged entity. As a result, the adversary acts as a legitimate entity to pass the authentication and proceed with the communication.
- Traceability: an adversary traces the tag to find its location and revoke the tag’s privacy. This attack violates the private information of RFID users, which is an instance where the privacy is important.
- Desynchronization Attack: communication session between tag and reader starts using the synchronous values stored in both the tag and reader to authenticate each other. A desynchronization attack occurs when an adversary breaks the synchronous state between the tag and server by blocking the update messages, causing the communication values stored in both server and tag to be different.
- Denial of Service: an adversary sends multiple signals simultaneously to the server as responses to make the system unavailable for further communication, which could further lead to a desynchronization attack.
- Cloning: an adversary uses a malicious device to obtain the reader or tag secret information and create a fake entity that can be used to perform a successful communication.
- Disclosure: an adversary identifies the secret information of the tag and the secret keys used in the communication to fully compromise the security of the protocol.
4. Review of Recent RFID Authentication Protocols
4.1. Heavyweight Protocols
4.2. Simple-Weight Protocols
4.3. Lightweight Protocols
4.4. Ultra-Lightweight Protocols
5. Analysis and Security Evaluation
5.1. Comparison of Computation Cost
5.2. Comparison of Security Threats
5.3. Comparison of Security Requirements
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Zhao, Z. A Secure RFID Authentication Protocol for Healthcare Environments Using Elliptic Curve Cryptosystem. J. Med. Syst. 2014, 38, 46. [Google Scholar] [CrossRef] [PubMed]
- Roberts, C.M. Radio frequency identification (RFID). Comput. Secur. 2006, 25, 18–26. [Google Scholar] [CrossRef] [Green Version]
- Xie, L.; Yin, Y.; Vasilakos, A.V.; Lu, S. Managing RFID Data: Challenges, Opportunities and Solutions. IEEE Commun. Surv. Tutor. 2014, 16, 1294–1311. [Google Scholar] [CrossRef]
- Pagán Alexander, J.; Baashirah, R.; Abuzneid, A. Comparison and Feasibility of Various RFID Authentication Methods Using ECC. Sensors 2018, 18, 2902. [Google Scholar] [CrossRef] [PubMed]
- Syamsuddin, I.; Han, S.; Dillon, T. A survey on low-cost RFID authentication protocols. In Proceedings of the 2012 International Conference on Advanced Computer Science and Information Systems (ICACSIS), Depok, Indonesia, 1–2 December 2012. [Google Scholar]
- Chang, C.C.; Chen, W.Y.; Cheng, T.F. A Secure RFID Mutual Authentication Protocol Conforming to EPC Class 1 Generation 2 Standard. In Proceedings of the 2014 Tenth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Kitakyushu, Japan, 27–29 August 2014. [Google Scholar]
- Swedberg, C. Iotera Develops Active RFID Tag with 4-Mile Read Range. Available online: https://www.rfidjournal.com/articles/view?11374 (accessed on 22 October 2018).
- Roque, P. Performance Analysis of Effective Range and Orientation for UHF Passive RFID. In Department of Electrical and Computer Engieering; Air Force Institute of Technology: Dayton, OH, USA, 2008. [Google Scholar]
- Zheng, L.; Xue, Y.; Zhang, L.; Zhang, R. Mutual Authentication Protocol for RFID Based on ECC. In Proceedings of the 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), Guangzhou, China, 21–24 July 2017. [Google Scholar]
- Alagheband, M.R.; Aref, M.R. Simulation-Based Traceability Analysis of RFID Authentication Protocols. Wirel. Pers. Commun. 2014, 77, 1019–1038. [Google Scholar] [CrossRef]
- Wang, J.; Floerkemeier, C.; Sarma, S.E. Session-based security enhancement of RFID systems for emerging open-loop applications. Pers. Ubiquitous Comput. 2014, 18, 1881–1891. [Google Scholar] [CrossRef]
- ISO. ISO/IEC DIS 9798-2. In Information Technology-Security Techniques-Entity Authentication—Part 2: Mechanisms Using Authenticated Encryption; International Organization for Standardization: Geneva, Switzerland, 2017. [Google Scholar]
- Ryu, E.-K.; Kim, D.-S.; Yoo, K.-Y. On Elliptic Curve Based Untraceable RFID Authentication Protocols. In Proceedings of the 3rd ACM Workshop on Information Hiding and Multimedia Security, Portland, OR, USA, 17–19 June 2015. [Google Scholar]
- Songhela, R.; Das, M.L. Yet Another Strong Privacy-Preserving RFID Mutual Authentication Protocol; Springer International Publishing: Cham, Switzerland, 2014. [Google Scholar]
- Chou, J.-S. An efficient mutual authentication RFID scheme based on elliptic curve cryptography. J. Supercomput. 2014, 70, 75–94. [Google Scholar] [CrossRef]
- Chen, Y.; Chou, J.-S. ECC-based untraceable authentication for large-scale active-tag RFID systems. Electron. Commer. Res. 2015, 15, 97–120. [Google Scholar] [CrossRef]
- Yao, Q.; Ma, J.; Cong, S.; Li, X.; Li, J. Attack gives me power: DoS-defending constant-time privacy-preserving authentication of low-cost devices such as backscattering RFID tags. In Proceedings of the 3rd ACM Workshop on Mobile Sensing, Computing and Communication, Paderborn, Germany, 5–8 July 2016. [Google Scholar]
- EPCglobal, E.P.C. Radio-Frequency Identity Protocols Generation-2 UHF RFID. In Specification for RFID Air Interface Protocol for Communications at 860 MHz–960 MHz Version 2.0.1 Ratified; EPCglobal Inc.: Lawrenceville, NJ, USA, 2015. [Google Scholar]
- Farash, M.S. Cryptanalysis and improvement of an efficient mutual authentication RFID scheme based on elliptic curve cryptography. J. Supercomput. 2014, 70, 987–1001. [Google Scholar] [CrossRef]
- Zhang, Z.; Qi, Q. An Efficient RFID Authentication Protocol to Enhance Patient Medication Safety Using Elliptic Curve Cryptography. J. Med. Syst. 2014, 38, 47. [Google Scholar] [CrossRef] [PubMed]
- Chen, B.-C.; Yang, C.T.; Yeh, H.T.; Lin, C.C. Mutual Authentication Protocol for Role-Based Access Control Using Mobile RFID. Appl. Sci. 2016, 6, 215. [Google Scholar] [CrossRef]
- Fernando, H.; Abawajy, J. Mutual Authentication Protocol for Networked RFID Systems. In Proceedings of the 2011 IEEE 10th International Conference on Trust, Security and Privacy in Computing and Communications, Changsha, China, 16–18 November 2011. [Google Scholar]
- Chen, X.; Cao, T.; Zhai, J. Untraceability Analysis of Two RFID Authentication Protocols. Chin. J. Electron. 2016, 25, 912–920. [Google Scholar] [CrossRef]
- Chen, C.; Qian, Z.; You, I.; Hong, J.; Lu, S. ACSP: A Novel Security Protocol against Counting Attack for UHF RFID Systems. In Proceedings of the 2011 Fifth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Seoul, Korea, 30 June–2 July 2011. [Google Scholar]
- Safkhani, M.; Bagheri, N.; Mahani, A. On the security of RFID anti-counting security protocol (ACSP). J. Comput. Appl. Math. 2014, 259, 512–521. [Google Scholar] [CrossRef]
- Chien, H.-Y.; Huang, C.-W. A Lightweight Authentication Protocol for Low-Cost RFID. J. Signal Process. Syst. 2010, 59, 95–102. [Google Scholar] [CrossRef]
- Li, Y.Z.; Cho, Y.B.; Um, N.K.; Lee, S.H. Security and Privacy on Authentication Protocol for Low-cost RFID. In Proceedings of the 2006 International Conference on Computational Intelligence and Security, Guangzhou, China, 3–6 November 2006. [Google Scholar]
- ISO. ISO/IEC 15693-2:2006. In Identification Cards-Contactless Integrated Circuit Cards-Vicinity Cards—Part 2: Air Interface and Initialization; International Organization for Standardization: Geneva, Switzerland, 2006. [Google Scholar]
- Burmester, M.; Munilla, J. Lightweight RFID authentication with forward and backward security. ACM Trans. Inf. Syst. Secur. 2011, 14, 1–26. [Google Scholar] [CrossRef]
- Lee, S.; Asano, T.; Kim, K. RFID Mutual Authentication Scheme based on Synchronized Secret Information. In Proceedings of the 2006 Symposium on Cryptography and Information Security, Hiroshima, Japan, 17–20 January 2006. [Google Scholar]
- Zuo, Y. Survivability Experiment and Attack Characterization for RFID. IEEE Trans. Dependable Secur. Comput. 2012, 9, 289–302. [Google Scholar] [CrossRef]
- Lee, K.; Nieto, J.M.G.; Boyd, C. Improving the efficiency of RFID authentication with pre-computation. In Proceedings of the Tenth Australasian Information Security Conference, Melbourne, Australia, 31 January–3 February 2012. [Google Scholar]
- Rahman, F.; Ahamed, S.I. DRAP: A Robust Authentication protocol to ensure survivability of computational RFID networks. In Proceedings of the 27th Annual ACM Symposium on Applied Computing, Trento, Italy, 26–30 March 2012. [Google Scholar]
- Liu, H.; Liu, H.; Ning, H.; Zhang, Y.; He, D.; Xiong, Q.; Yang, L.T. Grouping-Proofs-Based Authentication Protocol for Distributed RFID Systems. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 1321–1330. [Google Scholar] [CrossRef]
- Rahman, F.; Ahamed, S.I. Efficient detection of counterfeit products in large-scale RFID systems using batch authentication protocols. Pers. Ubiquitous Comput. 2014, 18, 177–188. [Google Scholar] [CrossRef]
- Keqiang, Y.; Lingling, S.; Xing, Q.; Zhonghua, Z. Design of anti-collision integrated security mechanism based on chaotic sequence in UHF RFID system. China Commun. 2014, 11, 137–147. [Google Scholar] [CrossRef]
- Cho, J.-S.; Jeong, Y.-S.; Park, S.O. Consideration on the brute-force attack cost and retrieval cost: A hash-based radio-frequency identification (RFID) tag mutual authentication protocol. Comput. Math. Appl. 2015, 69, 58–65. [Google Scholar] [CrossRef]
- Liu, Z.; Liu, Z.; Liu, D.; Li, L.; Lin, H.; Yong, Z. Implementation of a New RFID Authentication Protocol for EPC Gen2 Standard. IEEE Sens. J. 2015, 15, 1003–1011. [Google Scholar]
- Niu, H.; Taqieddin, E.; Jagannathan, S. EPC Gen2v2 RFID Standard Authentication and Ownership Management Protocol. IEEE Trans. Mob. Comput. 2016, 15, 137–149. [Google Scholar] [CrossRef]
- Dass, P.; Om, H. A Secure Authentication Scheme for RFID Systems. Procedia Comput. Sci. 2016, 78, 100–106. [Google Scholar] [CrossRef]
- Mtita, C.; Laurent, M.; Delort, J. Efficient serverless radio-frequency identification mutual authentication and secure tag search protocols with untrusted readers. IET Inf. Secur. 2016, 10, 262–271. [Google Scholar] [CrossRef]
- Blanchet, B. CryptoVerif: Cryptographic Protocol Verifier in the Computational Model; IEEE: Oxford, UK, 2010; pp. 16–30. [Google Scholar]
- Sundaresan, S.; Doss, R.; Piramuthu, S.; Zhou, W. Secure Tag Search in RFID Systems Using Mobile Readers. IEEE Trans. Dependable Secur. Comput. 2015, 12, 230–242. [Google Scholar] [CrossRef]
- Aggarwal, R.; Das, M.L. RFID security in the context of “internet of things”. In Proceedings of the First International Conference on Security of Internet of Things, Kollam, India, 17–19 August 2012. [Google Scholar]
- Chen, Y.C.; Wang, W.L.; Hwang, M.S. RFID Authentication Protocol for Anti-Counterfeiting and Privacy Protection. In Proceedings of the 9th International Conference on Advanced Communication Technology, Kobe, Japan, 12–14 February 2007. [Google Scholar]
- Huang, Y.J.; Lin, W.C.; Li, H.L. Efficient Implementation of RFID Mutual Authentication Protocol. IEEE Trans. Ind. Electron. 2012, 59, 4784–4791. [Google Scholar] [CrossRef]
- ISO. ISO/IEC 18000-6:2013. In Information Technology-Radio Frequency Identification for Item Management—Part 6: Parameters for Air Interface Communications at 860 MHz to 960 MHz General; International Organization for Standardization: Geneva, Switzerland, 2013. [Google Scholar]
- Huang, Y.C.; Jiang, J.R. Ultralightweight RFID Reader-Tag Mutual Authentication. In Proceedings of the 2015 IEEE 39th Annual Computer Software and Applications Conference, Taichung, Taiwan, 1–5 July 2015. [Google Scholar]
- Chien, H.-Y.; Chen, C.-H. Mutual authentication protocol for RFID conforming to EPC Class 1 Generation 2 standards. Comput. Stand. Interfaces 2007, 29, 254–259. [Google Scholar] [CrossRef]
- Chen, C.-L.; Deng, Y.-Y. Conformation of EPC Class 1 Generation 2 standards RFID system with mutual authentication and privacy protection. Eng. Appl. Artif. Intell. 2009, 22, 1284–1291. [Google Scholar] [CrossRef]
- Hopper, N.J.; Blum, M. Secure Human Identification Protocols. In Proceedings of the 7th International Conference on the Theory and Application of Cryptology and Information Security: Advances in Cryptology, Gold Coast, Australia, 9–13 December 2001; Springer: Berlin/Heidelberg, Germany; pp. 52–66. [Google Scholar]
- Piramuthu, S. HB and Related Lightweight Authentication Protocols for Secure RFID Tag/Reader Authentication. CollECTeR Eur. 2006, 2006, 239. [Google Scholar]
- Lin, Z.; Song, J.S. An Improvement in HB-Family Lightweight Authentication Protocols for Practical Use of RFID System. J. Adv. Comput. Netw. 2013, 1, 61–65. [Google Scholar] [CrossRef]
- Juels, A.; Weis, S.A. Authenticating Pervasive Devices with Human Protocols. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2005; pp. 293–308. [Google Scholar]
- Gilbert, H.; Robshaw, M.; Sibert, H. Active attack against HB/sup +/: A provably secure lightweight authentication protocol. Electron. Lett. 2005, 41, 1169–1170. [Google Scholar] [CrossRef]
- Ouaskou, M.; Lahmer, M.; Belkasmi, M. A variant of HB protocols based on permutation for low-cost RFID. In Proceedings of the 2015 International Conference on Wireless Networks and Mobile Communications (WINCOM), Marrakech, Morocco, 20–23 October 2015. [Google Scholar]


























| Passive Tags | Semi-Passive Tags | Active Tags | |
|---|---|---|---|
| Power | Surrounding signal | Internal chip battery | Integrated battery |
| Storage | Read memory | Reade/write memory | Reade/write memory |
| Distance | 5 m | 100 m | 1000 m |
| Application | Identification | Real-time tracking | Environmental and logistic |
| Cost | Low | High | High |
| Size | Small | Large | Large |
| Lifespan | Unlimited | 10 years | 10 years |
| Tag Signal | Low | High | High |
| Required Signal | High | Low | Low |
| Protocol | Operations | Tag Passes | Reader Passes | Tag Overhead |
|---|---|---|---|---|
| SB-A [11] | 1 TENC + 2 TDEC + 2 TPRNG | 2 | 3 | High |
| SB-B [11] | 2 TENC + 2 TDEC + 2 TPRNG | 2 | 3 | High |
| EMA [15] | 2 TSMUL + 2 TCH | 2 | 1 | High |
| ECU [13] | 2 TSMUL + 2 TCH | 1 | 1 | High |
| SPA [14] | 4 TSMUL + 1 TCH | 1 | 1 | High |
| PII [16] | 4 TSMUL + 3 TCH | 1 | 1 | High |
| RUND [17] | 2 TH OR 1 TENC + 1 TPRNG | 1 | 2 | High |
| IECC [19] | 2 TSMUL + 2 TH | 1 | 2 | High |
| EECC [20] | 2 TSMUL + 2 TH | 1 | 2 | High |
| RBAC [21] | 2 TENC + 2 TDEC + 1 TPRNG | 2 | 2 | High |
| DRAP [33] | 1 TENC + 3 TXOR + 3 TH + 1 TRNG + 2 TPRNG | 1 | 2 | High |
| NRS [22] | 10 TXOR + 3 TH | 4 | 5 | Medium |
| NRS+ [10] | 10 TXOR + 6 TH | 4 | 5 | Medium |
| NRS++ [23] | 8 TXOR + 4 TH | 1 | 2 | Medium |
| ACSP [24] | 3 TXOR + 7 TH + 4 TCRC | 1 | 4 | Medium |
| ACSP+ [25] | 4 TXOR + 8 TH | 2 | 4 | Medium |
| ACSP++ [23] | 6 TXOR + 8 TH | 1 | 2 | Medium |
| MASS [31] | 4 TXOR + 2 TH + 1 TRNG | 1 | 2 | Medium |
| EP-UAP [32] | 2 TH + 1 TRNG | 1 | 2 | Medium |
| GUPA [34] | 2 TH + 3 TPRNG + 19 TBIT | 3 | 3 | Medium |
| HBA [37] | 6 TXOR + 2 TH + 1 TRNG + 4 TMOD | 1 | 2 | Medium |
| VLP [38] | 2 TXOR + 2 TRNG + 3 TBIT + 2 TVLFSR | 1 | 2 | Medium |
| SEAS [40] | 1 TXOR + 2 TH + 1 TRNG + 3 TPRNG + 1 TBIT | 1 | 2 | Medium |
| SAP [41] | 2 TH + 2 TRNG | 1 | 2 | Medium |
| LAP [26] | 2 TXOR + 1 TRNG + 2 TPRNG + 1 TROT + 1 TSHIFT | 2 | 2 | Low |
| Flyweight [29] | 5 TPRNG | 3 | 3 | Low |
| FTest [35] | 1 TXOR + 3 TCRC | 3 | 2 | Low |
| ACS [36] | 3 TXOR + 2 TITER + 1 TSPR | 1 | 2 | Low |
| HBA+ [6] | 7 TXOR + 1 TRNG + 5 TPRNG | 1 | 2 | Low |
| OMP [39] | 12 TXOR + 6 TPRNG + 2 TPER | 1 | 1 | Low |
| STS [43] | 7 TXOR + 3 TPRNG | 1 | 1 | Low |
| CWH+ [44] | 2 TXOR + 5 TROT + 1 TSHIFT + TBIT | 1 | 1 | Low |
| PGX [46] | 8 TXOR + 2 TRNG | 2 | 2 | Low |
| PGM [46] | 4 TXOR + 2 TRNG + 32 TMOD | 2 | 2 | Low |
| MACC [48] | 6 TXOR + 5 TPRNG | 1 | 2 | Low |
| MACD [48] | 5 TXOR + 3 TPRNG + 1 TCRC | 1 | 2 | Low |
| HBROT [53] | 1 TRNG + 2 TROT + 1 TXOR + 1 TBIT | 1 | 1 | Low |
| HBPER [56] | 1 TRNG + 2 TPER + 1 TXOR + 1 TBIT | 1 | 1 | Low |
| ST1 | ST2 | ST3 | ST4 | ST5 | ST6 | ST7 | ST8 | |
|---|---|---|---|---|---|---|---|---|
| SB-A [11] | Y | Y | Y | Y | Y | Y | * | Cloning |
| SB-B [11] | Y | Y | Y | Y | Y | Y | * | Cloning |
| ECU [13] | Y | Y | * | Y | Y | * | * | * |
| SPA [14] | N | * | * | N | Y | * | * | * |
| EMA [15] | Y | * | * | N | N | * | * | * |
| PII [16] | Y | * | * | Y | Y | * | * | * |
| RUND [17] | Y | * | * | Y | Y | Y | Y | * |
| IECC [19] | Y | Y | Y | Y | Y | Y | Y | Cloning |
| EECC [20] | Y | Y | Y | Y | Y | Y | Y | Spoofing |
| RBAC [21] | Y | * | * | Y | Y | * | Y | * |
| NRS [22] | N | Y | N | N | N | N | N | * |
| NRS+ [10] | N | Y | Y | N | N | N | N | * |
| NRS++ [23] | Y | Y | Y | Y | Y | Y | Y | * |
| ACSP [24] | N | N | N | N | N | N | N | Counting |
| ACSP+ [25] | N | * | * | N | Y | Y | N | Counting |
| ACSP++ [23] | Y | Y | Y | Y | Y | Y | Y | Counting |
| LAP [26] | Y | * | * | N | N | N | Y | * |
| Flyweight [29] | Y | Y | Y | Y | Y | Y | * | * |
| MASS [31] | N | N | N | N | Y | N | * | * |
| EP-UAP [32] | N | Y | Y | N | Y | * | * | * |
| DRAP [33] | Y | * | * | Y | Y | Y | Y | Y |
| GUPA [34] | Y | Y | Y | Y | Y | Y | Y | DoP |
| FTest [35] | Y | Y | Y | Y | Y | * | * | Counterfeit + Collision |
| ACS [36] | Y | Y | Y | Y | Y | * | * | Counterfeit + Collision |
| HBA [37] | N | Y | Y | Y | Y | Y | N | Brute + Counterfeit |
| HBA+ [6] | Y | Y | Y | Y | Y | Y | Y | Brute for |
| VLP [38] | Y | Y | Y | * | Y | Y | * | * |
| OMP [39] | N | * | * | Y | Y | Y | Y | * |
| SEAS [40] | Y | Y | * | Y | Y | Y | Y | * |
| SAP [41] | Y | * | Y | Y | Y | * | * | * |
| STS [43] | Y | * | * | Y | Y | Y | Y | * |
| CWH+ [44] | Y | * | Y | Y | * | Y | * | Disclosure |
| PGX [46] | Y | Y | Y | Y | N | Y | * | Cloning |
| PGM [46] | Y | Y | Y | Y | N | Y | * | Cloning |
| MACC [48] | Y | Y | * | Y | N | Y | Y | * |
| MACD [48] | Y | Y | * | Y | Y | Y | Y | * |
| HBROT [53] | Y | Y | Y | Y | Y | Y | Y | * |
| HBPER [56] | Y | Y | Y | Y | Y | Y | Y | * |
| SR1 | SR2 | SR3 | SR4 | SR5 | SR6 | SR7 | SR8 | |
|---|---|---|---|---|---|---|---|---|
| SB-A [11] | Y | Y | Y | Y | Y | * | Y | N |
| SB-B [11] | Y | Y | Y | Y | Y | * | Y | N |
| ECU [13] | N | Y | Y | Y | Y | * | Y | N |
| SPA [14] | * | * | * | * | N | * | * | * |
| EMA [15] | * | * | * | * | N | * | * | * |
| PII [16] | * | * | * | * | N | * | * | * |
| RUND [17] | Y | Y | Y | Y | Y | * | Y | N |
| IECC [19] | Y | Y | Y | Y | Y | Y | Y | N |
| EECC [20] | Y | Y | Y | Y | Y | Y | Y | N |
| RBAC [21] | Y | Y | Y | Y | * | * | Y | N |
| NRS [22] | N | Y | N | N | N | N | N | Y |
| NRS+ [10] | N | Y | Y | N | N | N | N | Y |
| NRS++ [23] | Y | Y | Y | Y | Y | Y | Y | Y |
| ACSP [24] | Y | N | N | N | N | N | N | Y |
| ACSP+ [25] | Y | Y | Y | * | N | Y | * | Y |
| ACSP++ [23] | Y | Y | Y | Y | Y | Y | * | Y |
| LAP [26] | Y | Y | Y | N | Y | * | N | Y |
| Flyweight [29] | Y | Y | Y | Y | Y | Y | Y | Y |
| MASS [31] | Y | Y | N | * | Y | * | * | Y |
| EP-UAP [32] | N | Y | Y | Y | * | * | Y | Y |
| DRAP [33] | Y | * | * | Y | * | * | Y | Y |
| GUPA [34] | Y | Y | Y | Y | Y | * | Y | Y |
| FTest [35] | N | Y | Y | Y | Y | * | Y | Y |
| ACS [36] | Y | * | * | Y | * | * | Y | Y |
| HBA [37] | Y | Y | Y | Y | Y | * | Y | Y |
| HBA+ [6] | Y | Y | Y | Y | Y | * | Y | Y |
| VLP [38] | Y | Y | Y | Y | Y | * | Y | Y |
| OMP [39] | Y | Y | Y | Y | Y | Y | Y | Y |
| SEAS [40] | Y | Y | Y | Y | Y | * | Y | Y |
| SAP [41] | Y | Y | Y | * | * | * | * | Y |
| STS [43] | Y | Y | Y | Y | Y | * | Y | Y |
| CWH+ [44] | Y | Y | Y | * | Y | * | * | Y |
| PGX [46] | Y | * | * | N | * | * | N | Y |
| PGM [46] | Y | * | * | N | * | * | N | Y |
| MACC [48] | Y | Y | Y | N | Y | * | N | Y |
| MACD [48] | Y | Y | Y | Y | Y | * | Y | Y |
| HBROT [53] | Y | Y | Y | Y | Y | * | * | Y |
| HBPER [56] | Y | Y | Y | Y | Y | * | * | Y |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Baashirah, R.; Abuzneid, A. Survey on Prominent RFID Authentication Protocols for Passive Tags. Sensors 2018, 18, 3584. https://doi.org/10.3390/s18103584
Baashirah R, Abuzneid A. Survey on Prominent RFID Authentication Protocols for Passive Tags. Sensors. 2018; 18(10):3584. https://doi.org/10.3390/s18103584
Chicago/Turabian StyleBaashirah, Rania, and Abdelshakour Abuzneid. 2018. "Survey on Prominent RFID Authentication Protocols for Passive Tags" Sensors 18, no. 10: 3584. https://doi.org/10.3390/s18103584
APA StyleBaashirah, R., & Abuzneid, A. (2018). Survey on Prominent RFID Authentication Protocols for Passive Tags. Sensors, 18(10), 3584. https://doi.org/10.3390/s18103584





