Intrinsic Physical Unclonable Function (PUF) Sensors in Commodity Devices
Abstract
:1. Introduction
- Some PUFs are very sensitive to environmental parameter changes. Therefore, one can use the PUF response to sense environmental changes. For example, a ring oscillator (RO) PUF can measure the temperature in the Field-Programmable Gate Array (FPGA) boards [8]. The digital PUF is easily embedded in the Application Specific Integrated Circuit (ASIC) or FPGA without analog circuits. Therefore, a PUF-based sensor is a good candidate to countermeasure a spoofing attack where the outputs from multiple traditional and PUF sensors can be compared to catch an anomaly [9].
- Some digital PUFs can be used as a fusion of low-cost key storage, authentication and sensor. It is easy to be implemented in digital devices because it does not require any analog-mixed process.
- Implementation of an intrinsic DRAM PUF-based temperature sensor in off-the-shelf commodity devices.
- Test the feasibility of the DRAM PUF-based sensor and configure it in a DRAM PUF-based key generation scheme.
2. Background
2.1. Physical Unclonable Functions
2.2. Secure Key Management Scheme for Sensor Networks
- Tamper-resistant. The key is extracted from the nano-scale manufacturing variations, not “burned” in the NVM like EEPROM. Therefore, even an invasive attack cannot compromise the secret key.
- Low-cost. For some intrinsic PUFs, the security system does not need to add any dedicated circuit in hardware. For example, the implementation of DRAM PUF [31] just requires the firmware modifications.
- Combing node identity. Integrating node identity in the process of key production will make a system more secure [32]. It is also helpful for the resistance of node replication attacks [33]. PUFs can be seen as the “fingerprints” of hardware, it can be used in identification and key generation. In the PUF-based key generation scheme, the key is extracted from the hardware feature. Obviously, this feature can be seen as the identity of nodes.
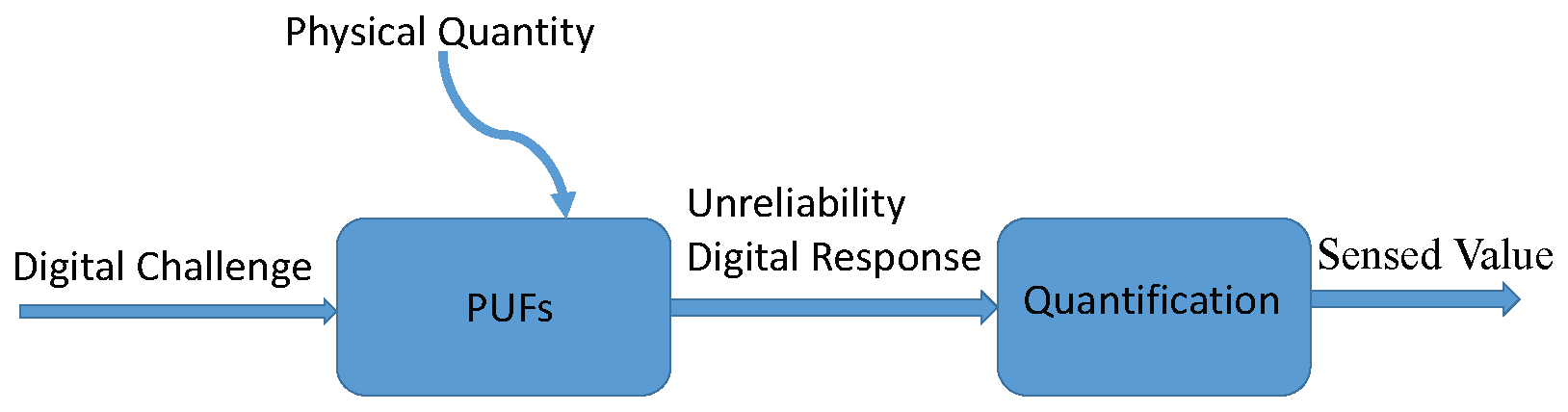
3. PUF Sensor
3.1. PUF-Protected Sensor
3.2. PUF-Based Sensor
4. Proposed Intrinsic PUF Sensor Based on DRAM PUF
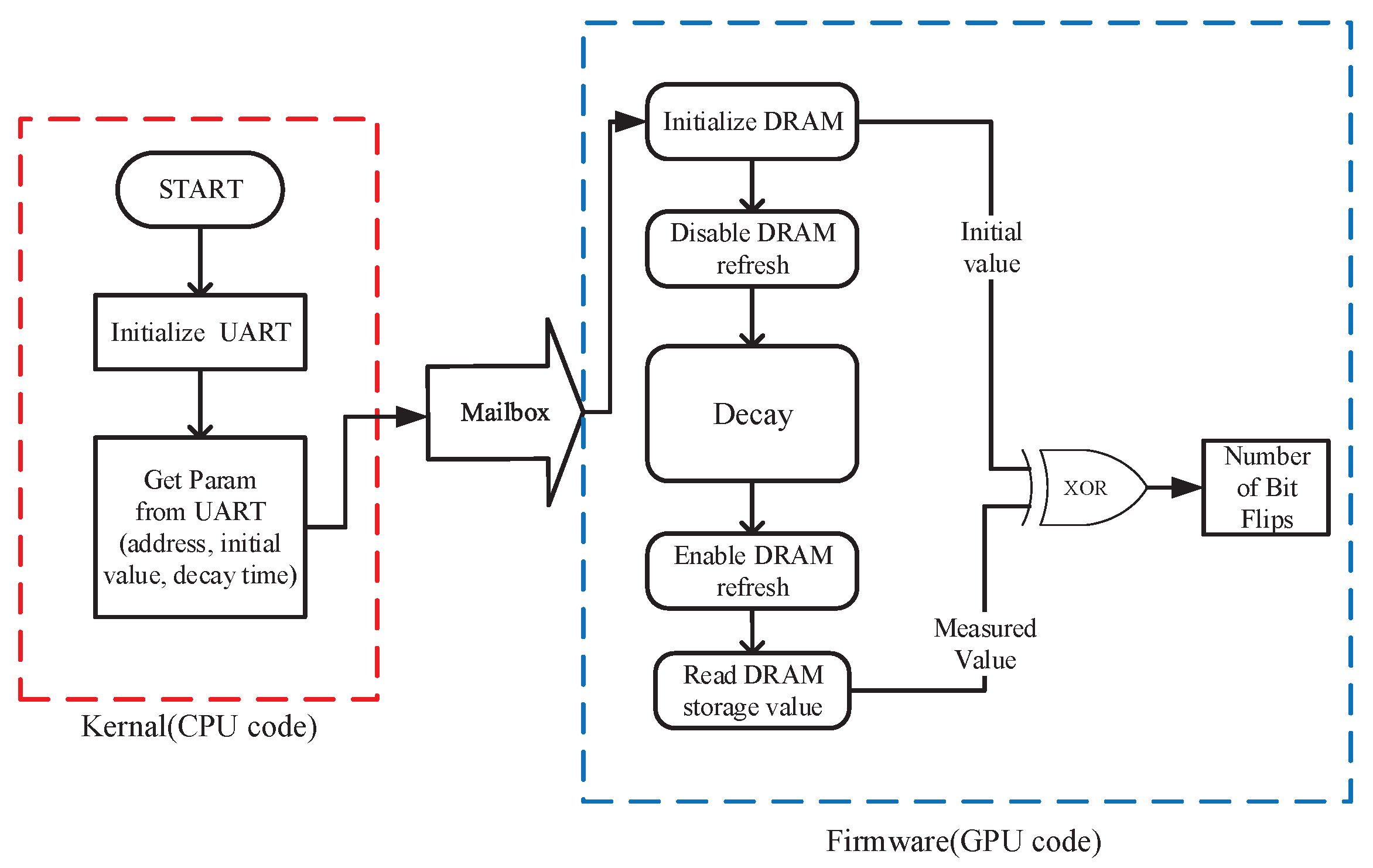
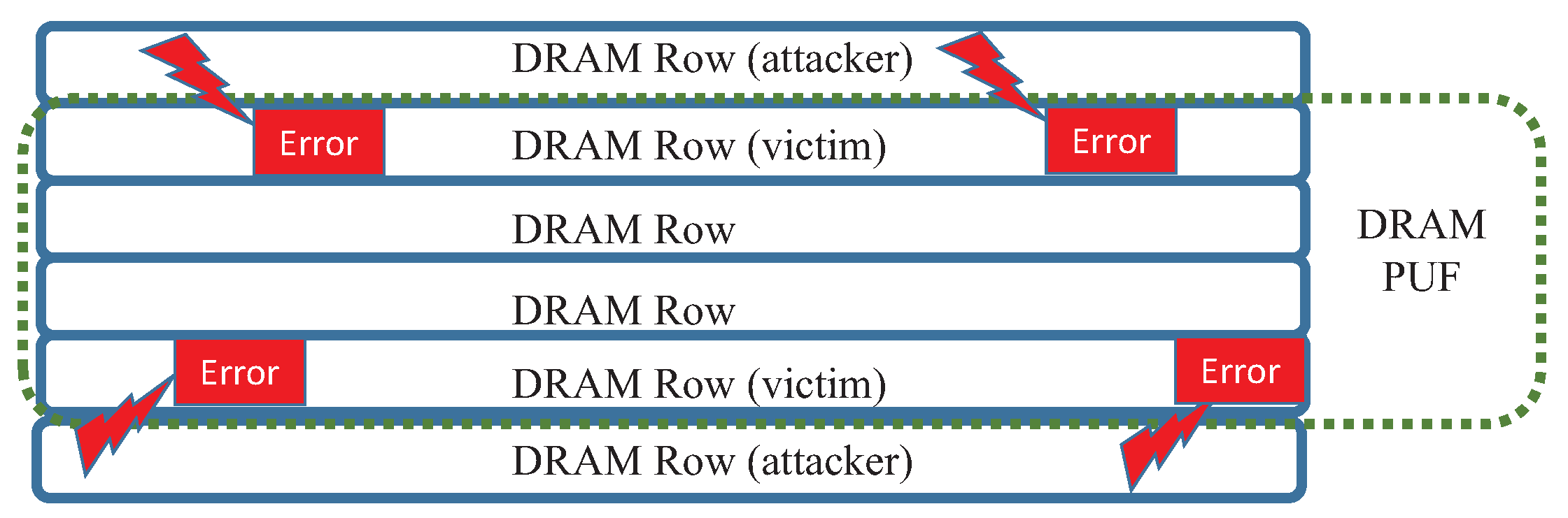
4.1. DRAM PUF
4.2. Implementation of DRAM PUF on Raspberry Pi B+
4.3. Embedded in the PUFs-Based Key Generation Scheme
5. Experimental Set Up and Evaluation
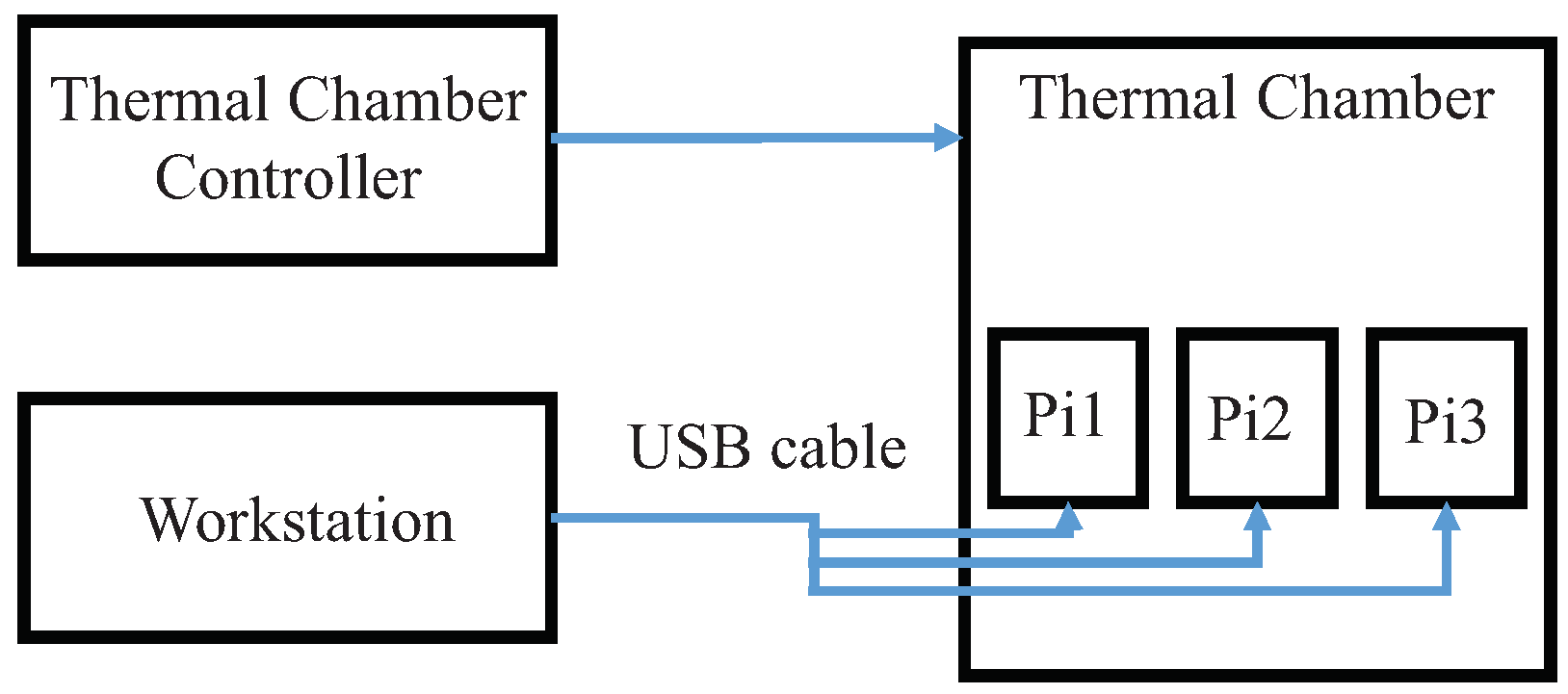
5.1. Experimental Set Up
- The workstation sets the temperature of thermal chamber by the thermal chamber controller and starts the loop to monitor the temperature.
- When the temperature requirements are reached, the workstation writes the parameters of the DRAM PUF to the CPU.
- Execute the DRAM PUF query process on GPU and count the number of bit flips.
- Restart from step 1 for next set of parameters.
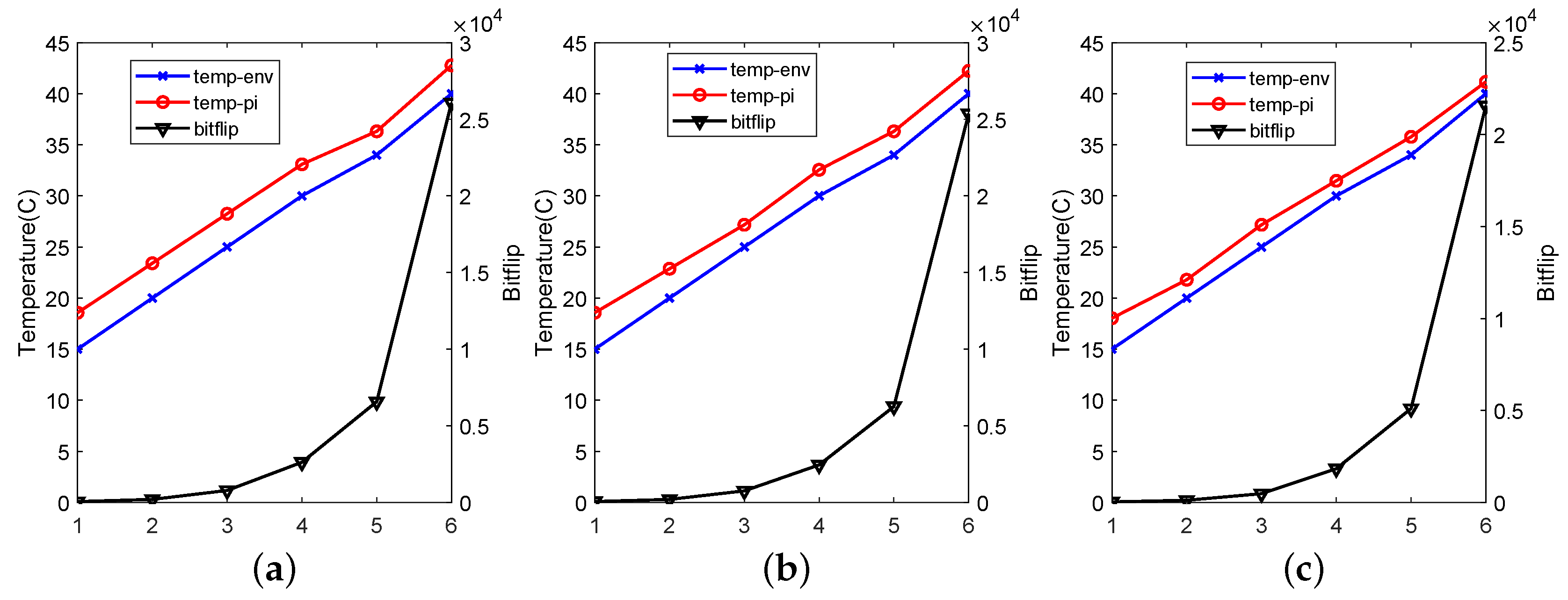
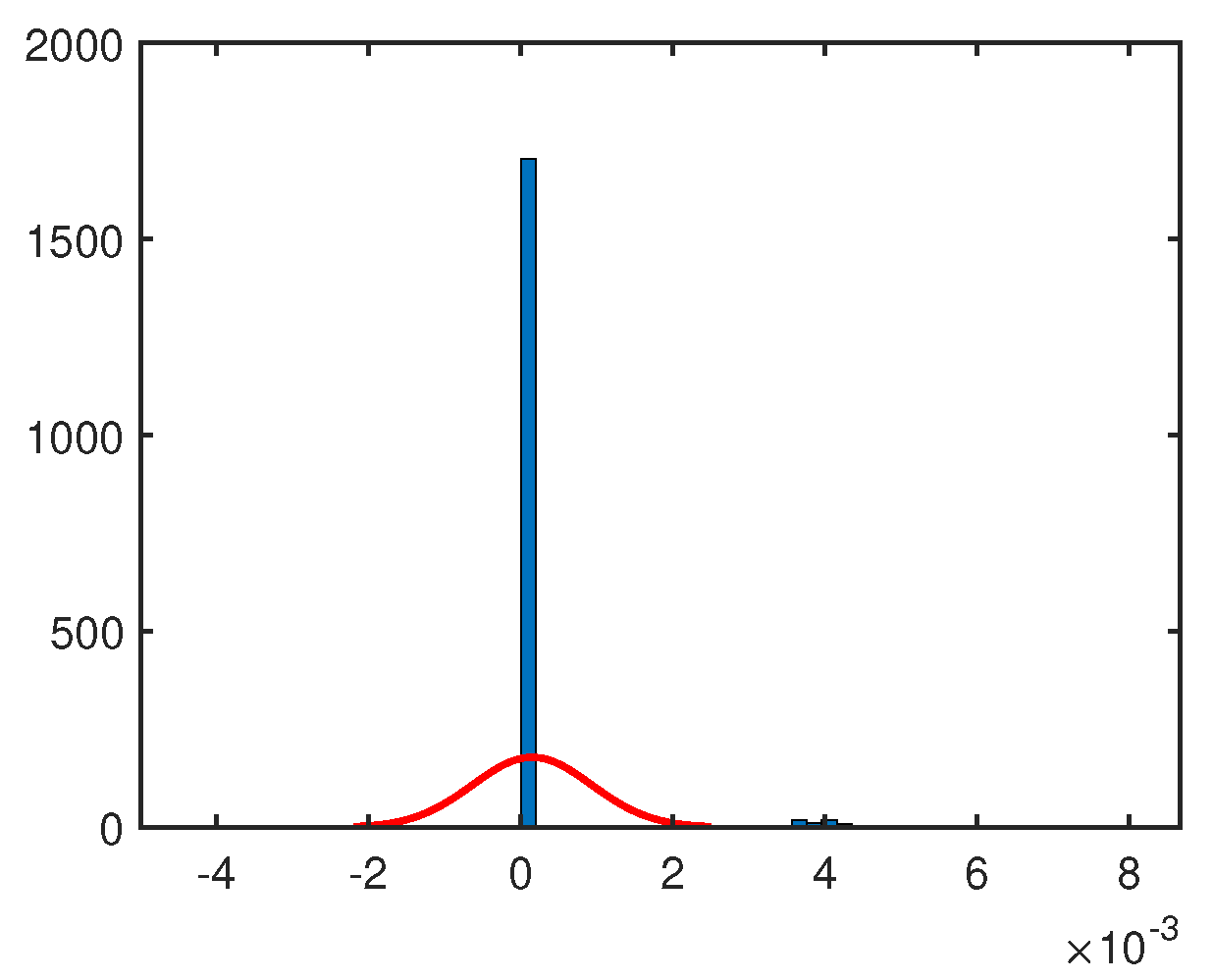
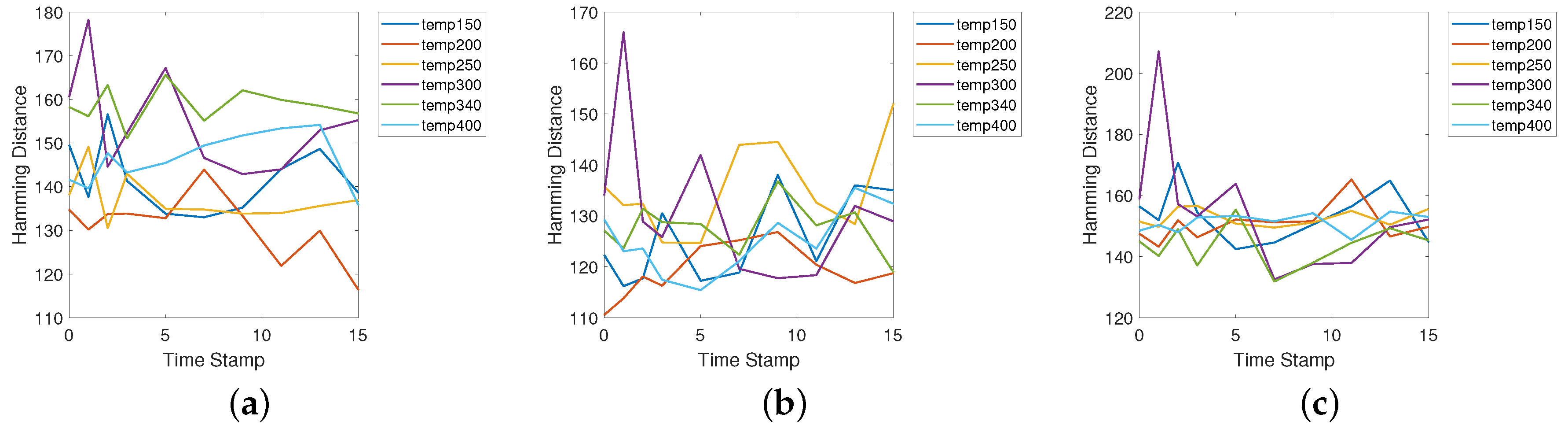
5.2. Test Results
6. Discussion
6.1. Security Discussion
6.2. Future Works
- We only verified the feasibility of the DRAM PUF-based sensor. Therefore, more comprehensive tests are necessary.
- The open source firmware [43] used in our implementation cannot boot up a whole operating system now. Therefore, we still are not clear about the influence of the operating code on the feature of the sensor.
- The query process of DRAM PUF needs several seconds of decay time. Therefore, it can not be used in certain real-time scenarios. Our future work will utilize more intrinsic PUF designs to address this issue.
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Schneier, B. The Internet of Things Is Wildly Insecure—and Often Unpatchable. Wired (Online). 6 January 2014. Available online: http://www.wired.com/2014/01/theres-no-good-way-to-patch-the-internet-of-things-and-thats-a-huge-problem/ (accessed on 8 July 2016).
- Skorobogatov, S.P. Data remanence in flash memory devices. In International Conference on Cryptographic Hardware Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2005; pp. 339–353. [Google Scholar]
- Torrance, R.; James, D.L. The State-of-the-Art in IC Reverse Engineering. In CHES 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 363–381. [Google Scholar] [Green Version]
- Shoukry, Y.; Martin, P.; Tabuada, P.; Srivastava, M. Non-invasive Spoofing Attacks for Anti-lock Braking Systems. In CHES 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 55–72. [Google Scholar]
- Gassend, B.; Clarke, D.; van Dijk, M.; Devadas, S. Silicon Physical Random Functions. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 148–160. [Google Scholar]
- Armknecht, F.; Maes, R.; Sadeghi, A.-R.; Sunar, B.; Tuyls, P. Memory leakage-resilient encryption based on physically unclonable functions. In Towards Hardware-Intrinsic Security; Springer: Berlin/Heidelberg, Germany, 2010; pp. 135–164. [Google Scholar]
- Kursawe, K.; Sadeghi, A.; Schellekens, D.; Skoric, B.; Tuyls, P. Reconfigurable Physical Unclonable Functions-Enabling technology for tamper-resistant storage. In Proceedings of the 2009 IEEE International Workshop on Hardware-Oriented Security and Trust, HOST, San Francisco, CA, USA, 27–27 July 2009; pp. 22–29. [Google Scholar]
- Franco, J.J.L.; Boemo, E.; Castillo, E.; Parrilla, L. Ring oscillators as thermal sensors in FPGAs: Experiments in low voltage. In Proceedings of the 2010 VI Southern Programmable Logic Conference, SPL, Ipojuca, Brazil, 24–26 March 2010; pp. 133–137. [Google Scholar]
- Shimizu, K.; Sugawara, T.; Suzuki, D.; Srivastava, M.T. PUF as a sensor. In Proceedings of the 2015 IEEE 4th Global Conference on Consumer Electronics GCCE, Osaka, Japan, 27–30 October 2015; pp. 88–92. [Google Scholar]
- Ma, H.; Gao, Y.; Kavehei, O.; Ranasinghe, D.C. A PUF sensor. Securing physical measurements. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops, PerCom Workshops, Kona, HI, USA, 13–17 March 2017; pp. 648–653. [Google Scholar]
- Pappu, R.; Recht, B.; Taylor, J.; Gershenfeld, N. Physical One-Way Functions. Sciences 2002, 297, 2026–2030. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Suh, G.E.; Devadas, S. MPhysical unclonable functions for device authentication and secret key generation. In Proceedings of the Design Automation Conference, San Diego, CA, USA, 4–8 June 2007; pp. 9–14. [Google Scholar]
- Ghaith, H.; Sunar, B. PUF-HB: A Tamper-Resilient HB Based Authentication Protocol. In Applied Cryptography Network Security, International Conference; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Van Herrewege, A.; Katzenbeisser, S.; Maes, R.; Peeters, R.; Sadeghi, A.R.; Verbauwhede, I.; Wachsmann, C. Reverse Fuzzy Extractors: Enabling Lightweight Mutual Authentication for PUF-Enabled RFIDs. In Proceedings of the Financial Cryptography Data Security-International Conference, Kralendijk, Bonaire, 27 Februray–2 March 2012. [Google Scholar]
- Majzoobi, M.; Koushanfar, F.; Devadas, S. FPGA PUF using programmable delay lines. In Proceedings of the IEEE International Workshop on Information Forensics Security, Seattle, WA, USA, 12–15 December 2011. [Google Scholar]
- Maiti, A.; Casarona, J.; McHale, L.; Schaumont, P. A large scale characterization of RO-PUF. In Proceedings of the 2010 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Anaheim, CA, USA, 13–14 June 2010; pp. 94–99. [Google Scholar]
- Selimis, G.; Konijnenburg, M.; Ashouei, M.; Huisken, J.; de Groot, H.; van der Leest, V.; Schrijen, G.-J.; van Hulst, M.; Tuyls, P. Evaluation of 90 nm 6T-SRAM as physical unclonable function for secure key generation in wireless sensor nodes. In Proceedings of the IEEE International Symposium on Circuits and Systems, Rio de Janeiro, Brazil, 15–18 May 2011; pp. 567–570. [Google Scholar]
- Rosenblatt, S.; Chellappa, S.; Cestero, A.; Robson, N.; Kirihata, T.; Iyer, S.S. A self-authenticating chip architecture using an intrinsic fingerprint of embedded DRAM. IEEE J. Solid-State Circuits 2013, 48, 2934–2943. [Google Scholar] [CrossRef]
- Serpanos, D.N.; Voyiatzis, A.G. Security challenges in embedded systems. Trans. Embedded Comput. Syst. TECS 2013, 12, 66. [Google Scholar] [CrossRef]
- Momani, M.; Challa, S.; Alhmouz, R. Can we trust trusted nodes in wireless sensor networks? In Proceedings of the 2008 International Conference on Computer and Communication Engineering, ICCCE, Kuala Lumpur, Malaysia, 13–15 May 2008; pp. 1227–1232. [Google Scholar]
- Momani, M.; Challa, S. Survey of Trust Models in Different Network Domains. Int. J. Ad Hoc Sens. Ubiq. Comput. 2010, 1, 1. [Google Scholar] [CrossRef]
- Zhang, J.; Varadharajan, V. Wireless sensor network key management survey and taxonomy. J. Netw. Comput. Appl. 2009, 33, 63–75. [Google Scholar] [CrossRef]
- He, X.; Niedermeier, M.; De Meer, H. Dynamic key management in wireless sensor networks: A survey. J. Netw. Comput. Appl. 2013, 36, 611–622. [Google Scholar] [CrossRef]
- Viega, J.; Thompson, H. The state of embedded-device secu-rity (Spoiler alert: It’s bad). IEEE Secur. Privacy 2012, 10, 68–70. [Google Scholar] [CrossRef]
- Arulraj, J.; Pavlo, A.; Dulloor, S.R. Let’s talk about storage recovery methods for non-volatile memory database systems. In Proceedings of the 2015 ACM SIGMOD International Conference on Management of Data, Melbourne, Australia, 31 May–4 June 2015; pp. 707–722. [Google Scholar]
- Naor, M.; Segev, G. Public-Key Cryptosystems Resilient to Key Leakage. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2009; pp. 18–35. [Google Scholar]
- Posch, R. Protecting devices by active coating. J. Univ. Comput. Sci. 1998, 4, 652–668. [Google Scholar]
- Gaubatz, G.; Sunar, B.; Karpovsky, M.G. Non-linear Residue Codes for Robust Public-Key Arithmetic. In Proceedings of the Fault Diagnosis Tolerance in Cryptography, Third International Workshop, FDTC, Yokohama, Japan, 10 October 2006. [Google Scholar]
- Anderson, R.; Kuhn, M. Tamper Resistance—A Cautionary Note. In Proceedings of the Conference on Second Usenix Workshop on Electronic Commerce USENIX Association, Oakland, CA, USA, 18–20 November 1996. [Google Scholar]
- Tuyls, P.; Škorić, B. Secret key generation from classical physics: Physical uncloneable functions. In AmIware Hardware Technology Drivers of Ambient Intelligence; Springer: Dordrecht, The Netherlands, 2006; pp. 421–447. [Google Scholar]
- Schaller, A.; Xiong, W.; Anagnostopoulos, N.A.; Saleem, M.U.; Gabmeyer, S.; Skoric, B.; Katzenbeisser, S.; Szefer, J. Decay-Based DRAM PUFs in Commodity Devices. IEEE Trans. Dependable Secure Comput. 2018, 16, 462–475. [Google Scholar] [CrossRef]
- Chen, X.; Makki, K.; Yen, K.; Pissinou, N. Sensor network security: A survey. IEEE Commun. Surv. Tutor. 2009, 11, 52–73. [Google Scholar] [CrossRef]
- Parno, B.; Perrig, A.; Gligor, V. Distributed detection of node replication attacks in sensor networks. In Proceedings of the 2005 IEEE Symposium on Security and Privacy, S P, Oakland, CA, USA, 8–11 May 2005; pp. 49–63. [Google Scholar]
- Rosenfeld, K.; Gavas, E.; Karri, R. Sensor physical unclonable functions. In Proceedings of the 2010 IEEE International Symposium on Hardware-Oriented Security and Trust, HOST, Anaheim, CA, USA, 13–14 June 2010; pp. 112–117. [Google Scholar]
- Cao, Y.; Zhang, L.; Chang, C. Using image sensor PUF as root of trust for birthmarking of perceptual image hash. In Proceedings of the 2016 IEEE Asian Hardware-Oriented Security and Trust, Asian HOST, Anaheim, CA, USA, 13–14 June 2016; pp. 1–6. [Google Scholar]
- Roel Maes, L. Physically Unclonable Functions: Constructions, Properties and Applications. In Properties and Applications, 1st ed.; Springer Publishing Company: Berlin, Germany, 2016; p. 193. [Google Scholar]
- Tang, J.; Karri, R.; Rajendran, J. Securing pressure measurements using SensorPUFs. In Proceedings of the 2016 IEEE International Symposium on Circuits and Systems, ISCAS, Montreal, QC, Canada, 22–25 May 2016; pp. 1330–1333. [Google Scholar]
- Sun, J.; Bittner, R.; Eguro, K. FPGA side-channel receivers. In Proceedings of the 19th ACM/SIGDA International Symposium on Field Programmable Gate Arrays, International Symposium on FPGA, Monterey, CA, USA, 27 February–1 March 2011; pp. 267–276. [Google Scholar]
- Iakymchuk, T.; Nikodem, M.; Kępa, K. Temperature-based covert channel in FPGA systems. In Proceedings of the 6th International Workshop on Reconfigurable Communication-Centric Systems-on-Chip, ReCoSoC, Montpellier, France, 20–22 June 2011; pp. 1–7. [Google Scholar]
- Tian, S.; Szefer, J. Temporal Thermal Covert Channels in Cloud FPGAs. In Proceedings of the 2019 ACM/SIGDA International Symposium on Field-Programmable Gate Arrays, Seaside, CA, USA, 24–26 February 2019. [Google Scholar]
- Tehranipoor, F.; Karimina, N.; Xiao, K.; Chandy, J. DRAM based intrinsic physical unclonable functions for system level security. In Proceedings of the Great Lakes Symposium on VLSI, Pittsburgh, PA, USA, 20–22 May 2015; pp. 15–20. [Google Scholar]
- Sutar, S.; Raha, A.; Raghunathan, V. D-PUF: An intrinsically reconfigurable DRAM PUF for device authentication in embedded systems. In Proceedings of the IEEE International Conference on Compilers, Architectures, and Sythesis of Embedded Systems, CASES, Pittsburgh, PA, USA, 2–7 October 2016; pp. 1–10. [Google Scholar]
- Badea, L.; Rosenzweig, A.; Brooks, K. rpi-open-firmware. Available online: https://github.com/christinaa/rpi-open-firmware (accessed on 5 February 2019).
- Chen, S.; Xiong, W.; Xu, Y.; Li, B.; Szefer, J. Thermal Covert Channels Leveraging Package-On-Package DRAM. In Proceedings of the International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Rotorua, New Zealand, 5–8 August 2019. [Google Scholar]
- Delvaux, J.; Gu, D.; Schellekens, D.; Verbauwhede, I. Helper Data Algorithms for PUF-Based Key Generation: Overview and Analysis. IEEE Trans. Comput.-Aided Des. Integr. Circ. Syst. 2015, 34, 889–902. [Google Scholar] [CrossRef]
- Liu, J.; Jaiyen, B.; Kim, Y.; Wilkerson, C.; Mutlu, O. An experimental study of data retention behavior in modern DRAM devices. In Proceedings of the ACM SIGARCH Computer Architecture News, Tel-Aviv, Israel, 23–27 June 2013; Volume 41. [Google Scholar]
- Tehranipoor, F.; Karimian, N.; Yan, W.; Chandy, J.A. Investigation of DRAM PUFs reliability under device accelerated aging effects. In Proceedings of the IEEE International Symposium on Circuits Systems, Baltimore, MD, USA, 28–31 May 2017. [Google Scholar]
- Hamamoto, T.; Sugiura, S.; Sawada, S. On the retention time distribution of dynamic random access memory (DRAM). IEEE Trans. Electron Devices 1998, 45, 1300–1309. [Google Scholar] [CrossRef]
- INTEL CORPORATION. Intel® Trusted Execution Technology Measured Launched Environment Programming Guide. Available online: https://www.intel.sg/content/www/xa/en/software-developers/intel-txt-software-development-guide.html (accessed on 13 August 2016).
- McKeen, F.; Alexandrovich, I.; Berenzon, A.; Rozas, C.V.; Shafi, H.; Shanbhogue, V.; Savagaonkar, U.R. Innovative Instructions and Software Model for Isolated Execution. Int. Workshop Hardw. Arch. Support Secur. Privacy 2013, 10, 10. [Google Scholar]
- ARM. Building a Secure System using TrustZone Technology. 2009. Available online: http://www.arm.com (accessed on 1 May 2009).
- Kim, Y.; Daly, R.; Kim, J.; Fallin, C.; Lee, J.H.; Lee, D.; Wilkerson, C.; Lai, K.; Mutlu, O. Flipping bits in memory without accessing them: An experimental study of DRAM disturbance errors. In Proceedings of the ACM SIGARCH Computer Architecture News, Minneapolis, MN, USA, 14–18 June 2014; pp. 361–372. [Google Scholar]





| Rpi | C | C | C | C | C | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| TR | ER | TR | ER | TR | ER | TR | ER | TR | ER | |
| Rpi1 | 198 | 188 | 781 | 647 | 2621 | 2219 | 6571 | 5948 | 26074 | 26103 |
| Rpi2 | 193 | 196 | 751 | 660 | 2448 | 2227 | 6256 | 5891 | 25359 | 25348 |
| Rpi3 | 117 | 106 | 476 | 400 | 1835 | 1511 | 5103 | 4378 | 21569 | 21584 |
| NIST Tests | Pi1 | Pi2 | Pd i3 | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| C | C | C | C | C | C | C | C | C | C | C | C | |
| Frequency | - | - | 100% | 100% | - | - | 97% | 97% | - | - | 99% | 99% |
| Blcok Frequency | - | - | 100% | 99% | - | - | 100% | 97% | - | - | 100% | 99% |
| Cumulative Sums | - | - | 100% | 100% | - | - | 99% | 96% | - | - | 98% | 99% |
| Runs | - | - | 100% | 99% | - | - | 99% | 97% | - | - | 98% | 99% |
| longest Run | - | - | 99% | 99% | - | - | 0% | 98% | - | - | 0% | 99% |
| FFT | - | - | 95% | 98% | - | - | 96% | 99% | - | - | 99% | 100% |
| N.O.T. | - | - | 47% | 100% | - | - | 59% | 91% | - | - | 98% | 98% |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, S.; Li, B.; Cao, Y. Intrinsic Physical Unclonable Function (PUF) Sensors in Commodity Devices. Sensors 2019, 19, 2428. https://doi.org/10.3390/s19112428
Chen S, Li B, Cao Y. Intrinsic Physical Unclonable Function (PUF) Sensors in Commodity Devices. Sensors. 2019; 19(11):2428. https://doi.org/10.3390/s19112428
Chicago/Turabian StyleChen, Shuai, Bing Li, and Yuan Cao. 2019. "Intrinsic Physical Unclonable Function (PUF) Sensors in Commodity Devices" Sensors 19, no. 11: 2428. https://doi.org/10.3390/s19112428
APA StyleChen, S., Li, B., & Cao, Y. (2019). Intrinsic Physical Unclonable Function (PUF) Sensors in Commodity Devices. Sensors, 19(11), 2428. https://doi.org/10.3390/s19112428






