Abstract
The Energy hole problem, a common phenomenon in wireless sensor networks, significantly decreases the lifetime of any deployed network. Some of the popular techniques to minimize such problems are using mobile sinks instead of static sinks, extending the transmission range dynamically, and deploying redundant sensor nodes near the base station/sink. The major drawback to these techniques are that energy holes may still be created at some point due to their static nature of deployment, despite having the overall residual energy very high. In this research work, we adopt a new approach by dividing the whole network into equiangular wedges and merging a wedge with its neighboring wedge dynamically whenever individual residual energy of all member nodes of a wedge fall below a threshold value. We also propose an efficient Head Node (HN) selection scheme to reduce the transmission energy needed for forwarding data packets among Head Nodes. Simulation results show that WEMER, our proposed WEdge MERging based scheme, provides significantly higher lifetime and better energy efficiency compared to state-of-the-art Power-Efficient Gathering in Sensor Information Systems (PEGASIS) and contemporary Concentric Clustering Scheme (CCS), and Multilayer Cluster Designing Algorithm (MCDA).
1. Introduction
Wireless Sensor Networks (WSNs), a collection of a large number of resource constraint sensor nodes [1], are widely used in applications like environment monitoring, military surveillance, disaster forecasting, agriculture, remote patient monitoring, factory automation [2,3,4], etc. In such applications, the main task of the sensor nodes is to collect the relevant data from the environment and send this gathered data to the Base Station (BS) or sink through multi-hop communication. Nodes closer to the sink or BS in multi-hop WSNs need to transmit or forward more traffic than other distant nodes of the network. This topological disadvantage makes the closer nodes drain out their energy at a significantly higher rate, which may create energy holes in the network [5].
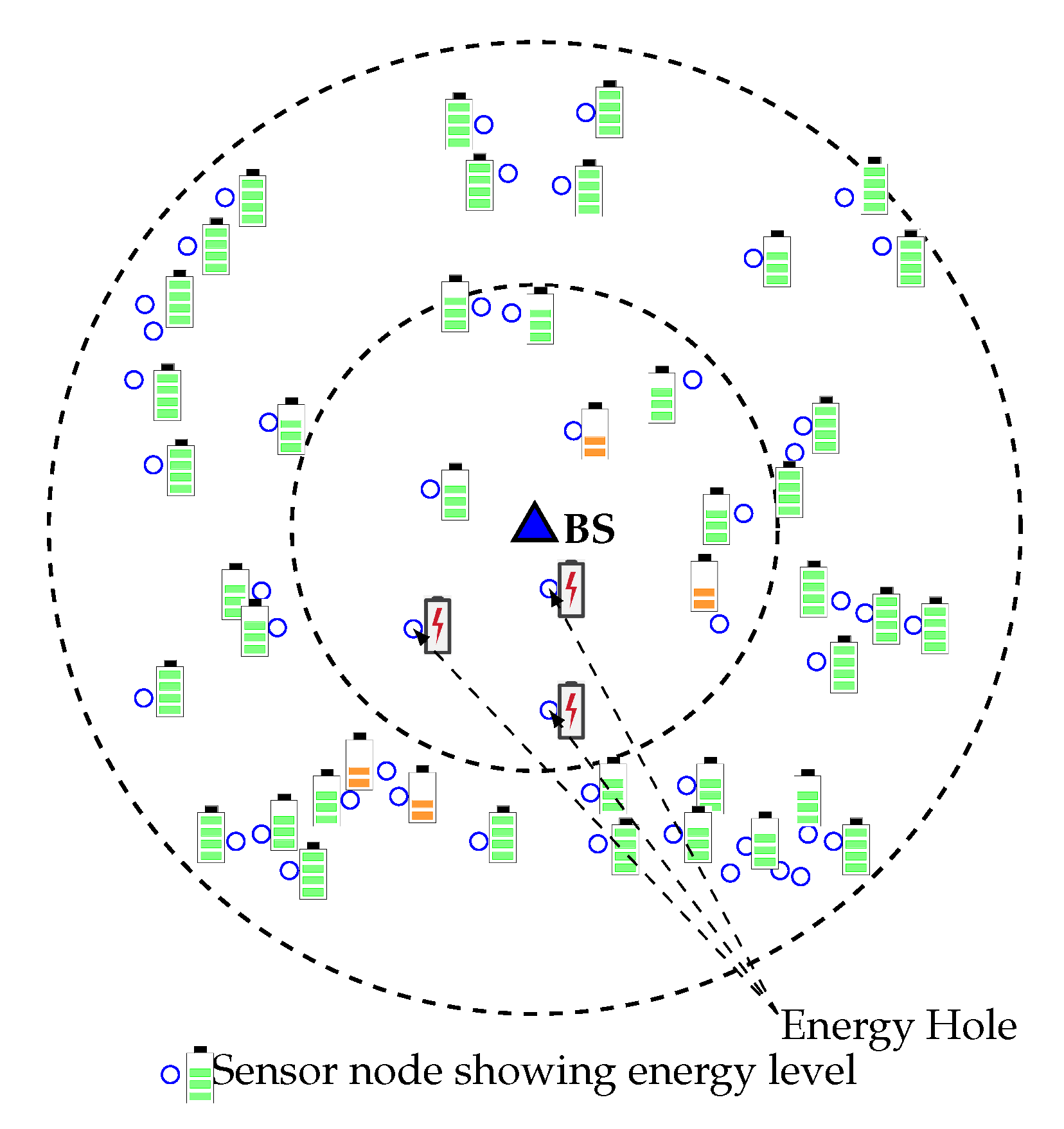
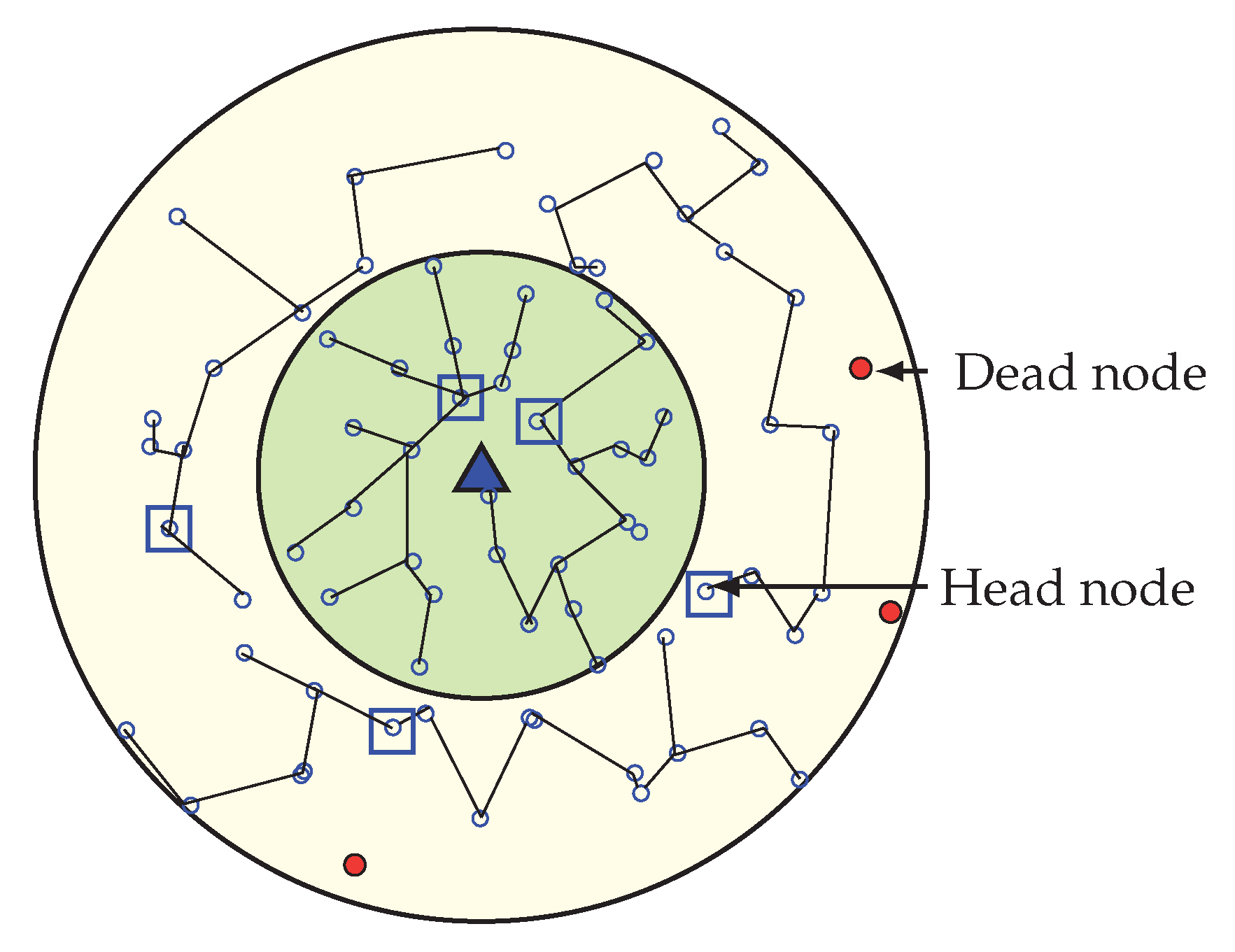
As a result, outer layer sensor nodes cannot forward data to the sink, which eventually decreases the network lifetime, even in case of high overall residual energy. Figure 1 gives an overview of the energy hole situation in which nodes closer to the Base Station have low remaining battery power, and nodes that are far away from BS have high remaining battery power. The energy hole problem can also happen if any nodes in the network receive and/or transmit more packets than the other nodes [6]. In a multi-hop network scenario, the overall network can collapse due to this energy hole problem. So, balancing the energy consumption among the deployed nodes is therefore of great importance, and grouping the nodes dynamically and more efficiently is an up-and-coming technique to achieve such a goal. A lot of medium access protocols are introduced in the last decade for improving the energy efficiency of sensor networks, but few of them consider the adverse effect of energy hole [7]. In this paper, we propose a new WEMER mechanism based on WEdge MERging to improve the energy efficiency of the network considering the negative impact of the energy hole. The major contributions of this paper are listed below:
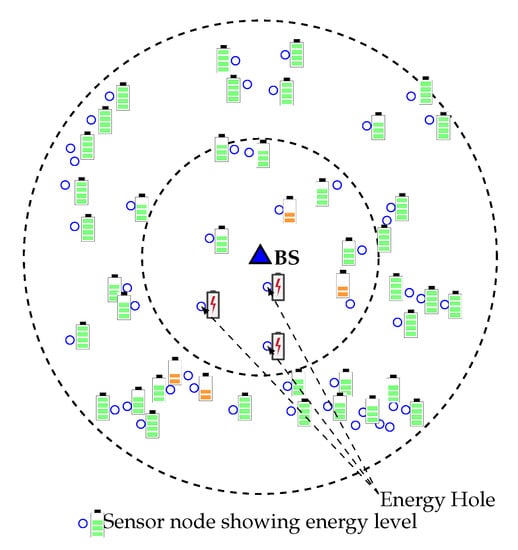
Figure 1.
Energy hole problem in Wireless Sensor Networks (WSNs).
- Unlike other existing protocols, the proposed WEMER protocol considers the distance between the HN of the immediate inner corona and the prospective HNs of the current corona while selecting an HN. Since HN of each corona forwards messages that it accumulates from its member nodes to the HN of the inner corona, a prospective HN may not be the optimal one unless its distance to the HN of the inner corona is considered, especially in case of multi-hop communication. WEMER, therefore, starts HN selection from the innermost corona so that the nodes from the successor corona can calculate their distance from the predecessor HN. While most of the other HN selection algorithms consider the distance between a prospective HN and its member nodes as the main selection factor, this paper also considers the distance between a prospective HN and its predecessor. By utilizing this distance as well as residual energy information, a distributed advertisement mechanism selects the most efficient HN for a sector.
- We also improve the reconstruction procedure of the network by introducing a dynamic wedge merging approach whenever an energy hole situation occurs. This distributed approach checks Residual Energy (RE) of each sector in every round, and if the RE of a sector is less than a predefined threshold, it merges with one of its neighbor sectors that has higher RE.
- Finally, we also improve the chain construction of a sector to avoid long link problem. Whenever a distance threshold is reached while forming a chain within a sector, it selects more than one HN to reduce the delay associated with long-distance communication.
A very preliminary version of this research work has been presented in [8]. The remainder of this paper is organized as follows. In Section 2, we describe the preliminaries related to all concepts and provide a summary of state of the art. Our proposed work is described in detail in Section 3. Section 4 is dedicated to results and performance analysis. Finally, we conclude the paper in Section 5.
2. Related Work
Nodes deployment is the first step in establishing a sensor network. Sensor nodes are battery powered and randomly deployed in the target area. The significant challenges of the sensor nodes are battery power limitations, processing power constraints, duplicate data gathering, and the limited memory of the network. Optimizing energy consumption is one of the significant tasks in WSNs, in order to prolong the network lifetime. For addressing the issue, researchers focused more on this area during the last few years. If the sensor nodes are deployed uniformly, nodes near the sink send their own data, as well as the data collected by other nodes, away from the sink, in a multi-hop scenario. In this case, the sensor nodes that are nearest to the sink consume more energy and die out quickly [9,10,11]. On the other hand, if multi-hop is not used and all nodes transmit their data directly to the BS, the nodes farthest from the BS die much more quickly than the nodes that are closer to the BS, this is because they need more transmission power to transmit their data to the BS [12]. As a result, the sensor network is disconnected, having sufficient energy left unused [13], which causes a significant decrease in the network lifetime. Energy holes create a partition in the network in such a way that it cannot make full connectivity in the network. Various techniques have been proposed to address the Energy Hole Problem (EHP) [14]. Some techniques that alleviate the energy hole problem include: adjustable transmission range [15], compressed sensing [16], sink or node mobility, and non-uniform sensor distribution, which mainly deploys redundant nodes near the sink [17]. The aim of an energy hole avoidance is to delay or bypass the formation of the energy hole to maximize the network lifetime.
Based on the network structure Pantazis et al. [18] categorized the routing protocol of WSN into flat and hierarchical routing. In large scale network, hierarchical protocol improves energy efficiency than flat routing. The hierarchical protocol is further divided into clusters, chain, tree, grid, etc. Clustering is an efficient way to both save energy and prolong the network lifetime [19,20,21,22,23]. For large scale networks, clustering is a popular approach. In this approach, every member of the cluster sends their data to the cluster head, in order to transmit it to the base station. Based on the residual energy of the node and the average energy of the cluster, the Adaptive Decentralized Re-clustering Protocol (ADRP) chooses the set of the next cluster heads for upcoming rounds [24]. But until the next initial phase, no new node can be added, and if any next head node dies, the cluster will not be formed. In [25] the authors restrict the number of CH advertisement to the optimal number of the CH count during CH selection time, in order to save energy. A lot of clustering protocol has been proposed in various literature but they doesnot consider the energy hole situation [26,27,28,29,30,31].
Several mobile sensor-based protocols are proposed for achieving the energy efficiency of WSNs [32] Yarinezhad et al. [33] proposed a cluster-based protocol based on virtual grid infrastructure and mobile sink to fairly utilizing the energy consumption of sensor nodes by reducing traffic load in the network. They partitioned the sensing area into several same dimensioned region. Some nodes that are near the intersecting region of the virtual grid are responsible for tracking the recent position of the mobile sink. The sensing node sends its data to the mobile sync by using a geographic routing algorithm through the location information gathered from the intersecting region node. The key feature of this protocol is to minimize the communication cost between the mobile sink and sensing nodes. But, it increases the traffic load of the responsible node. Toor et al. [34] proposed Multi-hop Energy Efficient Routing Protocol using Multiple Mobile Nodes (MEACBM) protocol for WSN. They propose a new probabilistic CH selection algorithm and form several clusters and sub-clusters. Then, the sensing region is divided into several sectors and each sector contains multiple clusters and sub-clusters. A mobile data collector (MDC) is placed in each sector to collect data from the CH. It reduces the transmission cost of CH. However, it requires proper synchronization among the CHs and MDC. Besides, MDC consumes more energy due to the high traffic load.
On the other hand, PEGASIS [35] used greedy algorithm to construct a chain. Chain construction procedure is started from the farthest node from the base station. However PEGASIS has some limitations, firstly, One chain is form for whole network which creates long chain and long chain makes delay of communication. Secondly, only leader node can transmit data to the base station. So leader node is heavily loaded. Thirdly, when PEGASIS protocol selects leader node, energy or distance is not considered. Fourthly, it is essential to have a complete view of the topology at each and every node for chain construction. Finally, greedy algorithm create long link problem in large network, that makes energy consumption of node is high. Another Chain Based Cluster Cooperative Protocol (C BCCP) [36] partitions the network into some subareas (clusters). Each subarea contains CH and Cluster Coordinator (CCO) to distribute the load defined number of the relay node. The number of CCO depends on the position of the cluster, since there is one CCO for every below lying cluster of it. CBCCP randomly select CH, CCO, and do not consider the RE or distance so, there is a probability that a node with low RE can be selected as CH or CCO instead of a high RE node.
CCS [37] is an enhanced of PEGASIS protocol. The main improvement of CCS is that it consider base station position when divide the network into concentric circles. The term concentric clustering means that the shape of a cluster is concentric circles when cluster is formed. CCS improves the delay problem of PEGASIS but there is unbalanced node distribution at each level, which will cause the levels with a small number of nodes to deplete their energy first. Furthermore, during head node selection of each level, energy and distance are not considered which creates unbalanced energy consumption.
Multilayer cluster designing algorithm (MCDA) [38] for improving energy efficiency is a combination of Distributed Cluster Designing (DCD) and Centralized Cluster Designing Approach (CCD). This protocol comprises of three steps: self organizing, flat layer design and clustered layer design. However, nodal density is the only metric to select a cluster head, so it makes the same node to select as cluster head again and again. Furthermore, number of cluster member for a cluster is not defined. That’s why cluster is not equally loaded. L. Prabha et al. [39] proposed an energy hole repelling algorithm by which sensor nodes closer to the BS creates smaller cluster and nodes far away from BS creates big cluster. Baniata et al. [40] proposed an Energy Efficient Unequal Chain Length Clustering (EEUCLC) protocol to overcome the energy hole problem, by creating an unequal chain within a cluster. However, there is no mechanism in the network face energy hole situation because cluster members near the BS still handle huge traffic loads from the successor clusters. Elkamel et al. [41] proposed unequal clustering in order to avoid the energy hole problem, by creating a smaller cluster near the BS and a large cluster far from the BS. This protocol distributes the energy load in the network, but does not ensure the mechanism if the energy hole problem exists. Wang et al. [42] proposed a layer based unequal clustering mechanism, using multi hop communication to avoid the energy hole problem. Zhao et al. [43] proposed an Immune Clone Selection-based Power Control (ICSPC) algorithm for solving the energy hole problem by using a cluster based coronal model. The dynamic CH selection, non-uniform node distribution, imbalance energy consumption in each corona and the transmission range adjustment is introduced to solve the energy hole problem. Reem et al. [44] has proposed On-hole children reconnection (OHCR) by considering local nature and on-hole alert (OHA) by considering global nature protocols to reconnect the network after the premature death of a node. In the case of a cluster or chain based protocol, the OHCR protocol increases the number of cluster head or chain head. The reason is whenever a parent node dies; its child nodes search for a new parent node within their ranges. If no other node (same level or upper level) within its range exist, it joins the BS directly. In chain based network, it forms another chain head. However, the number of chain head is closely related to the performance metrics. Too many chain head creates extra energy consumption in the network. Moreover, a significant number of control packets are also needed to exchange that increases energy consumption.
Naranjo et al. [45] proposed Prolong Stable Election Protocol (P-SEP) to prolong the network lifetime and to enhance energy efficiency by selecting optimal cluster heads in fog supported WSNs. In this protocol, some fog nodes, responsible for sending the gathered data to the internet gateway, must be placed in the sensing area. The protocol considers two-level heterogeneity based on energy and classifies the sensor nodes (which are pre-placed or randomly deployed) into two categories: advanced node and normal node. However, in most scenarios, sensor nodes are placed in a remote area, which limits its deployment in a practical scenario due to its pre-placement requirement. Table 1 gives an overall comparison of existing hierarchical protocols that consider energy hole situation in their literature.

Table 1.
Comparison of existing protocols mitigating energy hole problem.
3. Proposed WEMER Scheme
Due to the multi-hop communication nature in WSNs, nodes that are closer to the Base Station (BS) need to forward many more data packets than other nodes, and they tend to die much faster because of this many-to-one communication characteristics. As a result, energy holes are created in the inner circles of the BS, and critical data from the relevant regions are not forwarded to the BS, despite having high overall residual energy. As a result, network lifetime decreases very drastically and a significant amount of energy is wasted. An efficient scheme to balance the energy consumption among nodes is therefore inevitable. A layered-based routing technique with a dynamic wedge merging mechanism is proposed here to distribute the energy consumption uniformly across the network. At first, the whole network is divided into unequal width coronas with equiangular wedges, that creates many sectors. A sector is an area between the corona and the wedge. The sensor nodes at each sector then form a chain to transmit data packets toward the sink via Head Node (HN), and HN forwards the data of its sector and are selected based on their remaining energy and distance with its relevant successor HN.
In this paper, we assume that nodes and BS are static in nature, and no mobile sensor node or mobile BS does exist at any time. Furthermore, link asymmetry [46,47] is not considered in this research work. The communication links are assumed to be symmetric in such that two neighbor nodes can always communicate with each other by using the same transmission power. Nodes are required to send their sensed data constantly at a certain rate. For simplicity, we assume that each sensor node generates and sends one packet per round.
3.1. Energy Model
The three basic units of sensor nodes are: the sensing unit, the processing unit, and the transceivers. The first order radio model is adopted for the proposed scheme [48]. In this radio model, the electronics energy is used, in order to operate the transmitter or receiver circuit. The transmitter amplifier utilizes both channel models of the free space with power loss, and multi-path fading with power loss. The radios have power control capabilities and, to reach the intended recipients, can expend the minimum required energy. In order to avoid receiving an unintended transmission, the radios can be turned off. Thus, to transmit a K-bit message a distance d using this radio model, the radio expends:
If than will be
If than will be
And to receive this message, the radio expends:
where is the unit energy dissipation for transmitter electronics or receiver electronics. is the amplifier energy in the free space model, while is the one in the multi-path model, and is the threshold and defined as:
3.2. Proposed Wedge Merging Scheme
The lifetime of a sensor node mainly depends on the number of alive nodes and connectivity of the network. Once a sensor node is out of energy, it dies prematurely, which affects the performance of the network. The proposed scheme aims to eliminate the energy hole problem in WSN, as well as to maximize the network lifetime. In this section, the WEMER technique is presented in detail. WEMER is divided into the following four phases:
- Initial setup phase
- Data transmission phase
- Merging procedure of a wedge
- Avoid long link communication
All of the above mentioned phases are discussed in the subsequent sub-sections.
3.2.1. Initial Setup Phase
At the initial setup, the BS divides the whole network into some sector. A sector is the small portion of the network, between the corona and the wedge. We adapt two algorithms described in [49] in order to create coronas and wedges in our proposed scheme.
Corona Creation Procedure
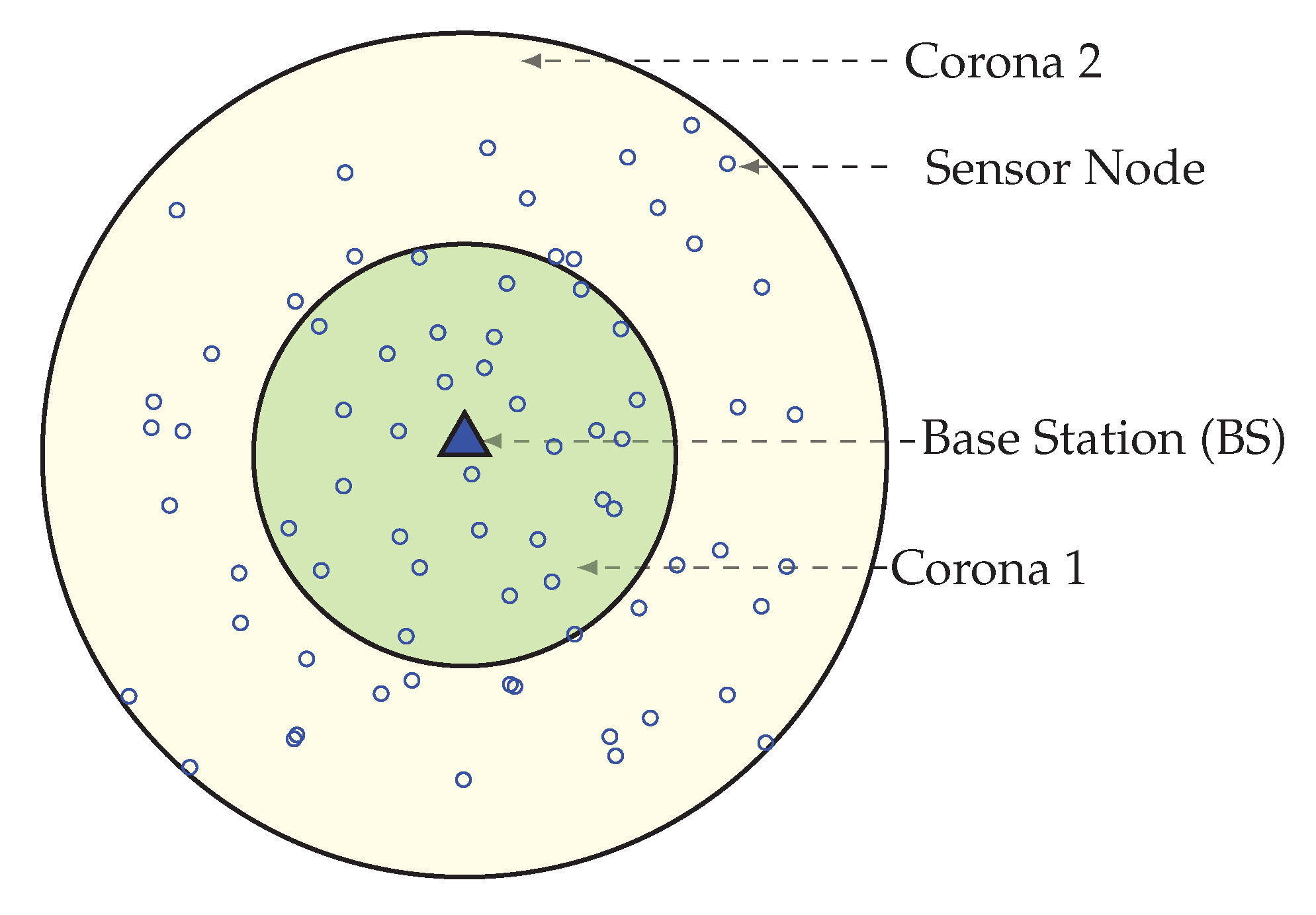
This section describes how the network area is divided into unequal width, concentric coronas. Before the data transmission starts, each node needs to find its corona. In the network initialization phase, by adjusting transmission power, the BS divides the network into some circularly shaped coronas. The range of transmission for corona creation mainly set by the BS depends on both the requirement of the number of coronas and the node density in the network. The BS sets itself as corona number zero (CN = 0) and adjusts its transmission power equivalent to half of its range. In order to assign a node to coronas BS broadcast, a corona_creation packet must increase its corona number by 1. When a node receives a corona message with CN = i, it sets its corona number to i, if it already not joined to a lower or equal corona. Until all nodes get their corona number from the BS, this corona creation method continues by increasing both the transmission range and the corona number by 1. After these processes, the entire network is alienated into several coronas, that look like concentric circles with center Sink. Figure 2 is showing a network with 2 concentric coronas. The innermost circular region is corona 1 and outermost is corona 2, this is because with the help of the BS, the whole network is divided into two coronas.
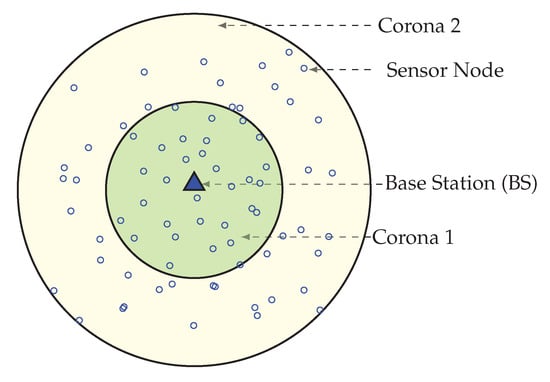
Figure 2.
Network divided in 2 coronas.
Wedge Creation Procedure
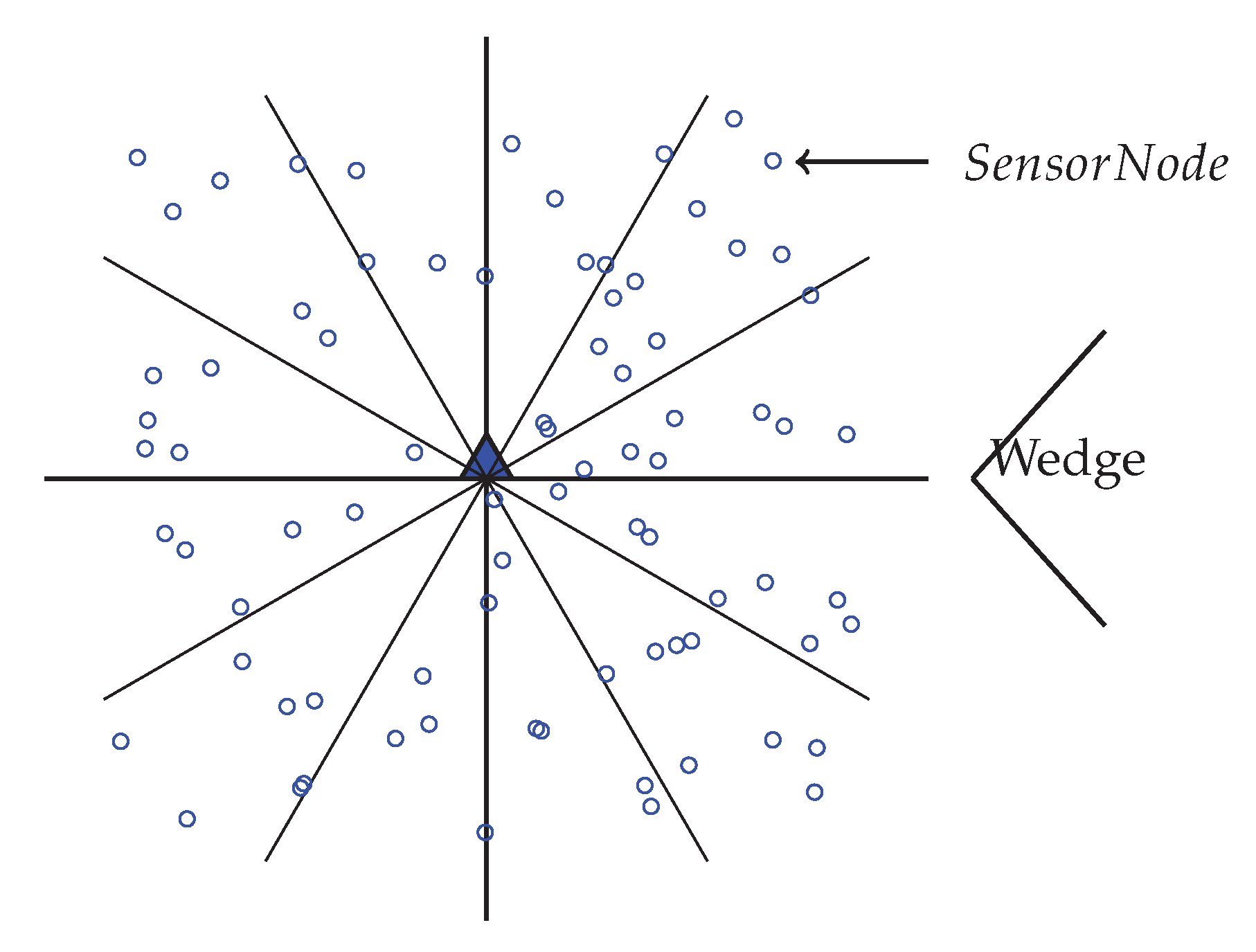
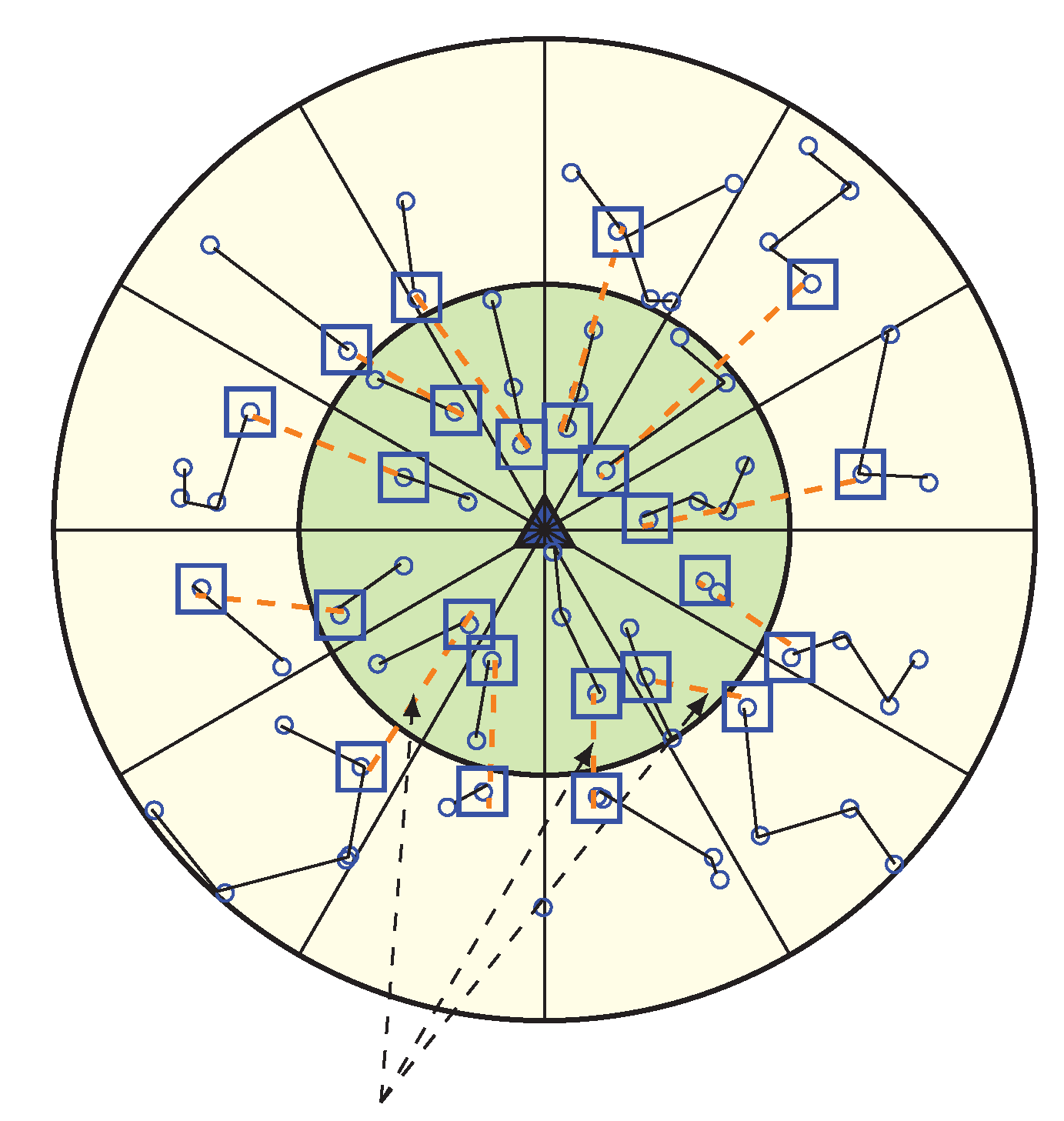
In order to partition the network into equiangular wedges, the BS directs its antenna to one portion of the network and transmits a wedge_creation packet that contains sink ID and a wedge number. This packet is send out with its maximum transmission power level, to ensure coverage of every node in that direction. When a node receives a wedge_creation packet with a wedge number, then it assigns its wedge to that wedge number, unless it has already joined an equal or lower wedge. Until all nodes get its wedge number from the BS, this wedge creation method continues by both changing the angle of directionality and wedge number by 1. Figure 3 is showing a network with wedges. Here, the entire network gets divided into 12 wedges.
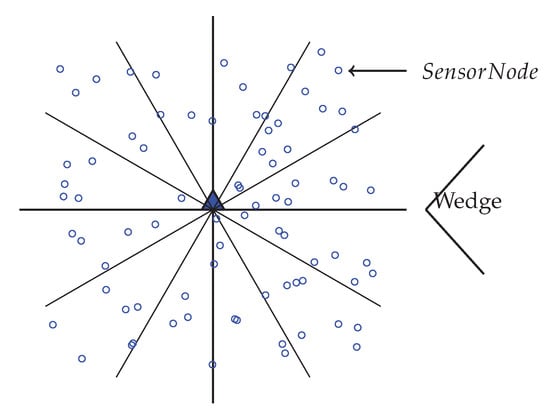
Figure 3.
Network with 12 equiangular Wedges.
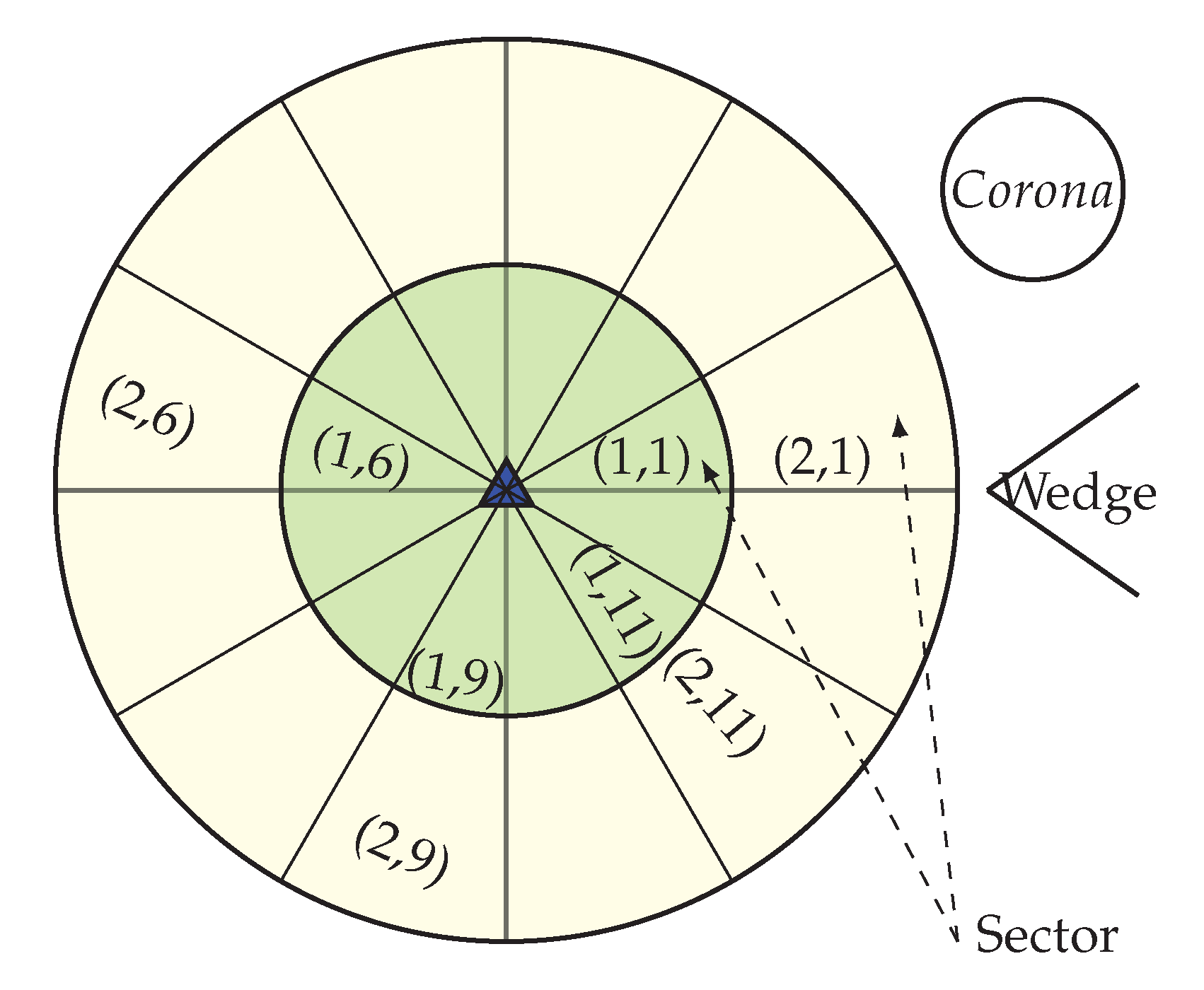
After the configuration of the whole network into coronas and wedges, each sensor node gets its corona and wedge number. The corona and wedge creation procedure makes sure that each node belongs to only one sector in the coordinate system. The positions of all the sensor nodes that have the same coordinates form a sector, like a hard disk. A unique sector is defined by the intersection of a wedge and a corona; every sector is identifiable by the combination of a unique corona and wedge identifier. Figure 4 is showing a network with a corona, wedge and sector. In the figure, the corona and wedge number of a node is showing in brackets. Position of corona 1 and wedge 1 for a node is indicated by (1, 1), at the same way corona 2 and wedge 1 are indicated by (2, 1). After the formation every sector, there must be more than one node; if not, the BS then merge that sector’s wedge with its neighbor wedge. According to the distance from the BS, sector size varies. A sector which is closer to the BS is smaller in size, which means there is less intra sector traffic and energy cost. So, the smaller sector consumes less energy and time for the intra sector communication, as they need to use small transmission energy and can concentrate it onto the inter sector communication.
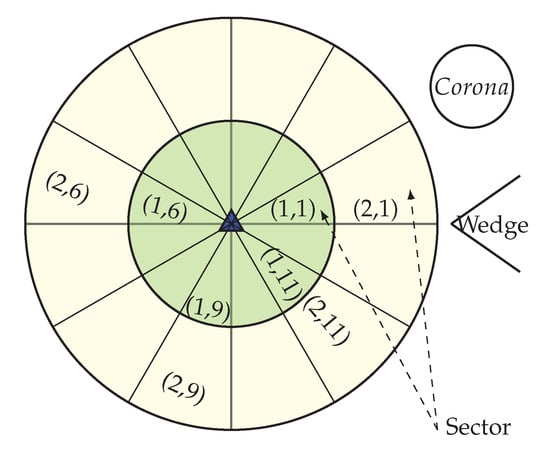
Figure 4.
Network with corona, wedge and sector.
3.2.2. Data Transmission
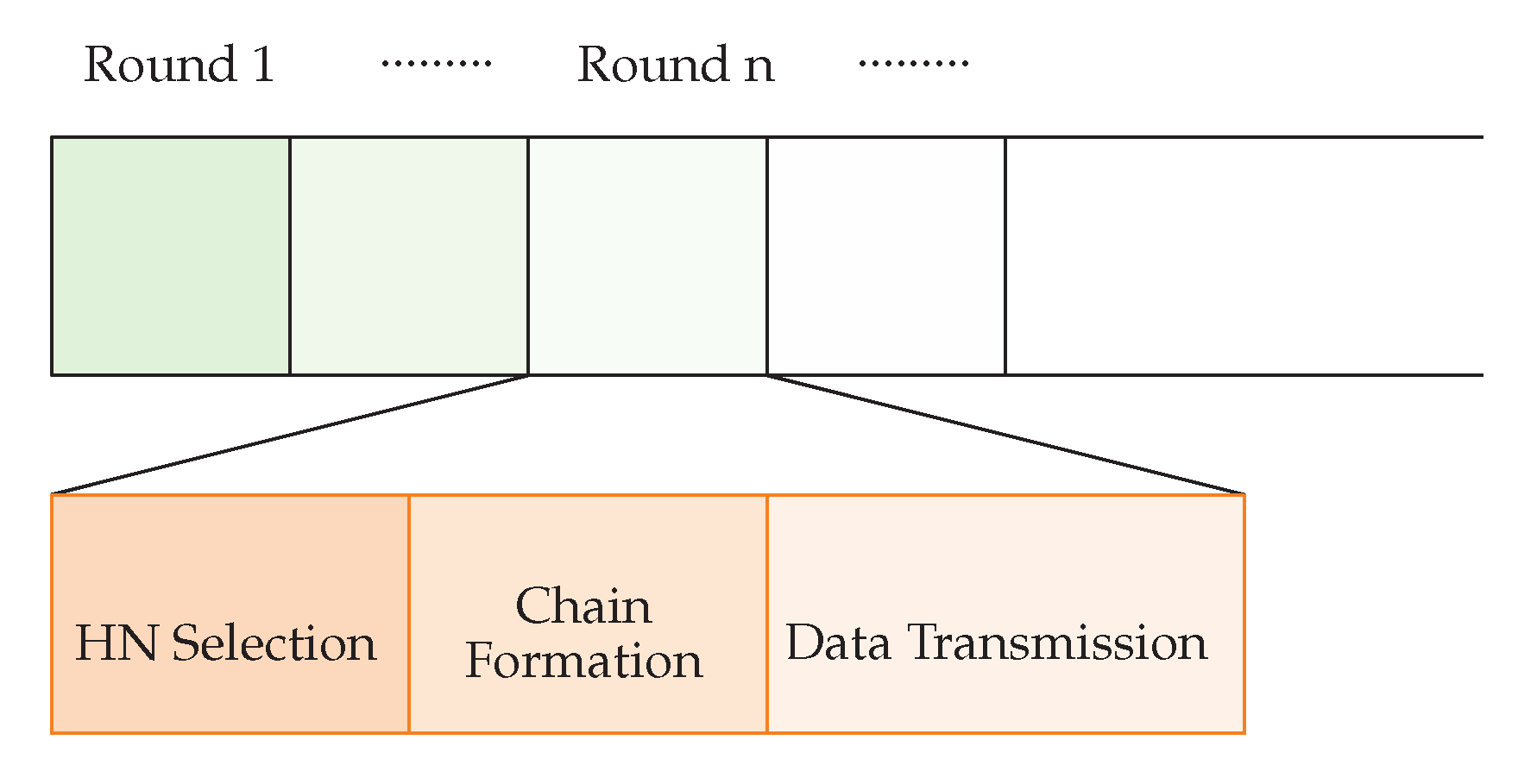
If only some of the nodes in the network participate with all of the processes, while others are inactive or idle, then it produces a greater chances for that node to die early and network partitioning eventually decreases the network lifetime. WEMER works in rounds and according to Figure 5 every round is further divided into three phases.
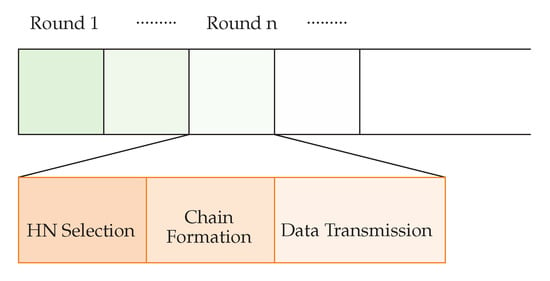
Figure 5.
Data transmission Phase.
In order to send the sensing information to the BS, every wedge constructs a virtual path which will join the outermost sector to the BS. A node then selected as a Head Node from a sector, and that Head Node sends the cumulative traffic of its sectors, and its predecessors to its successors. Only one node from a sector is used to forward the data to the BS, so MAC level contention is greatly reduced.
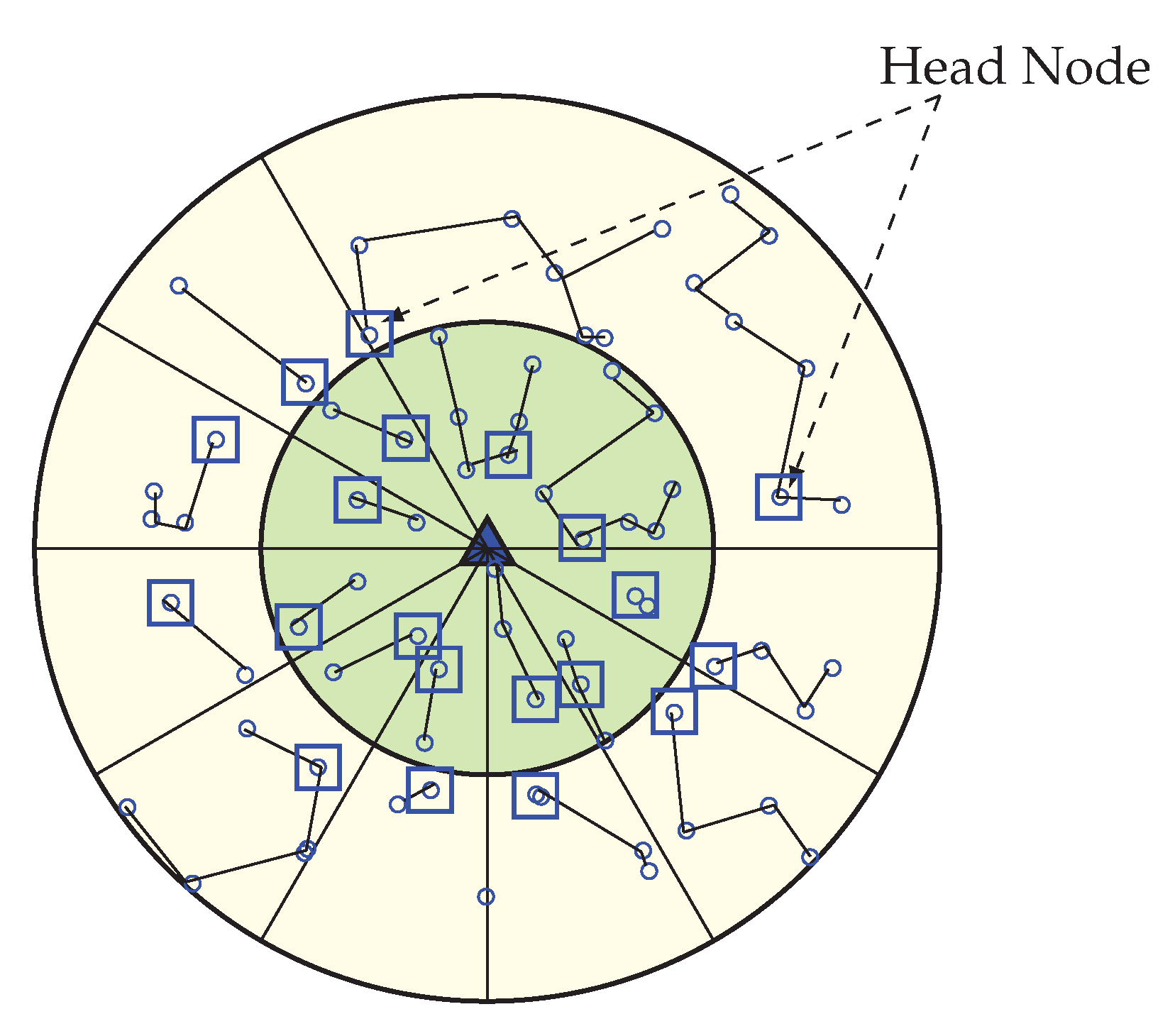
Head Node Selection Phase
In WEMER, the position of the BS is in the center of the network, and the HN selection process starts from the inner most sector of the network. There is only one HN for every sector. A HN can be selected for a sector by both the node’s RE and the distance with its relevant successor HN. A node which has less RE than its sector’s average energy can not participate in the HN selection competition. In the HN selection phase, nodes from a sector sets a timer () according to the following equation, in order to become a HN,
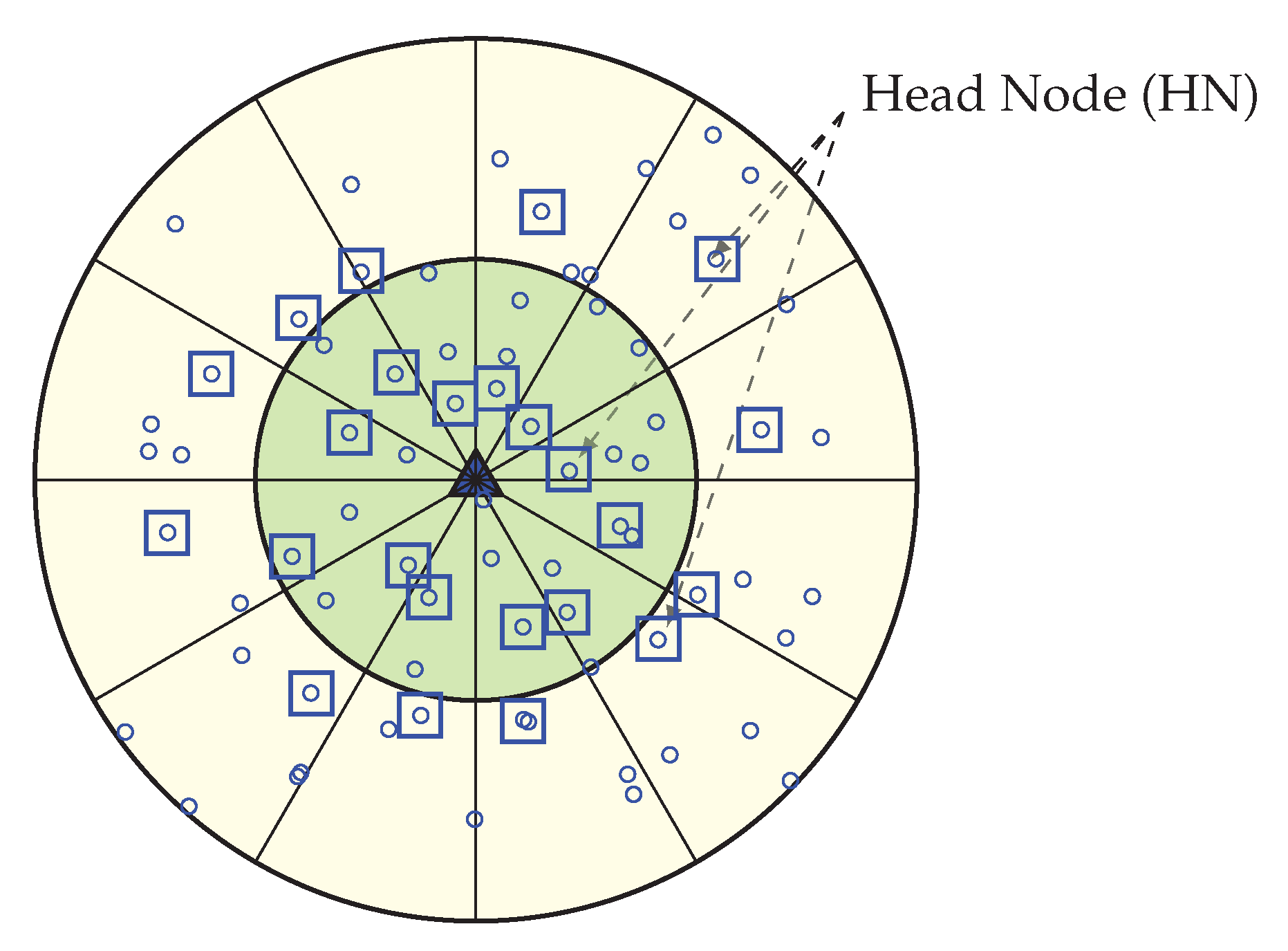
Here is the RE of the node, is the threshold distance obtained from Equation 1, is the distance between the node i and its successor head node (in case of ), is the distance between the node i and the BS (in case of ). The HN selection procedure starts from the corona 1. Here, every node set a timer () where is divided by the summation of RE () and distance factor (/), so that higher residual energy and less distance node can send earlier within the total advertisement time (). After receiving sensor nodes that are in the same sector, the node leaves the competition and nodes that belongs to the successor sector calculate the distance based on the RSSI of the packet. Node belongs to Corona 2 sets their timer according to Equation 3 and in the same procedure node which has high residual energy and less distance between the predecessor HN sends packet. Figure 6 is showing the Head Node for every sector. This HN selection process run at every round in order to select the most capable node as HN, and until any node becomes more capable, the same HN can operate for many continuous rounds. If any node becomes better than the current HN of its sector again, a new HN selection phase is called and the most suitable node become new HN. The pseudo-code of the head node selection procedure is shown in Algorithm 1.
| Algorithm 1: Head node selection procedure for sector |
 |
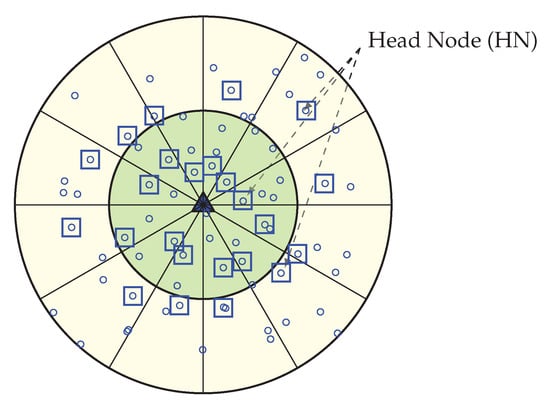
Figure 6.
Selection of a Head Node (HN) for each sector.
Chain Construction Phase
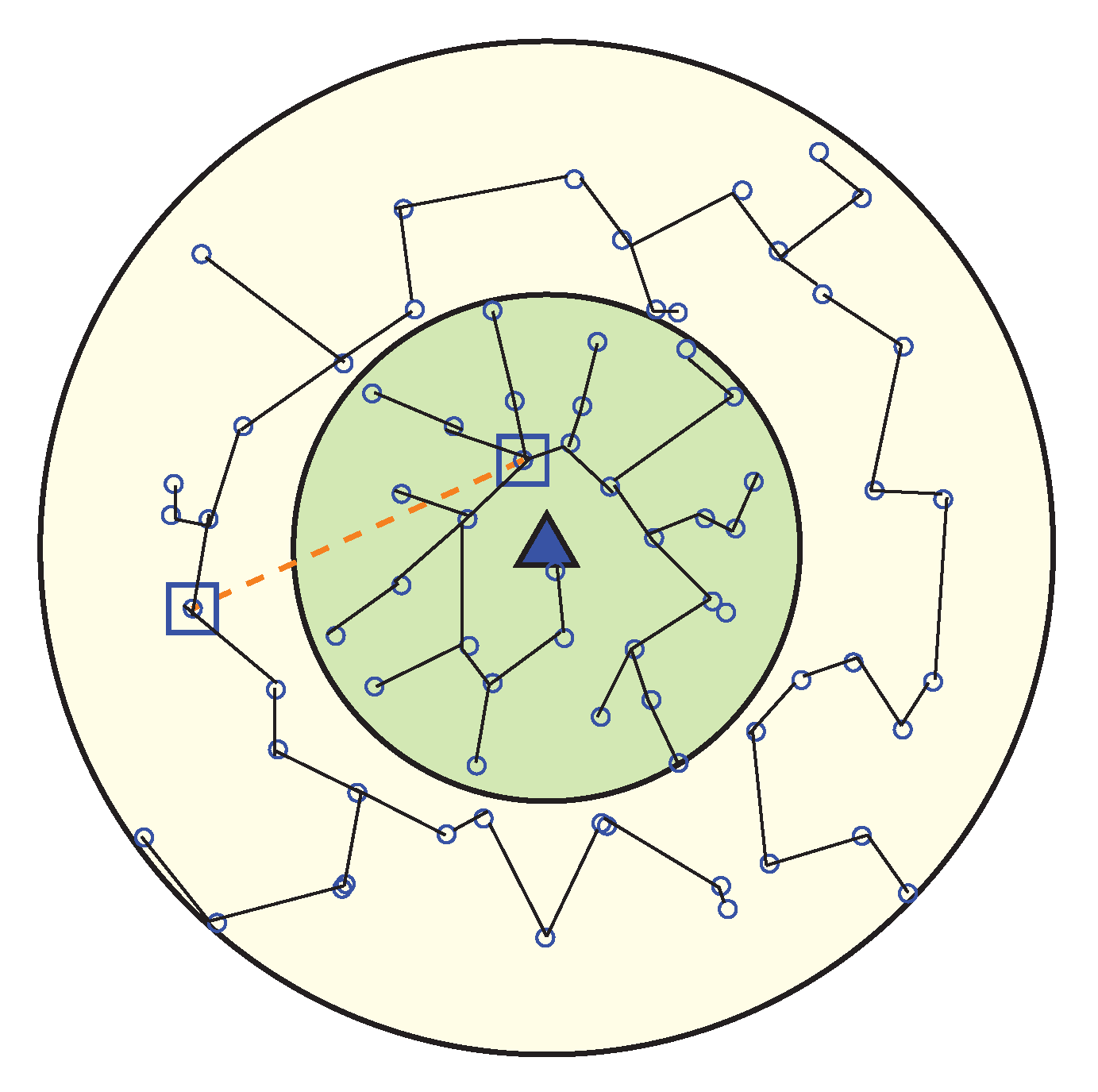
The main concern of the chain construction phase is to find a low cost chain that covers all nodes of the sector. PEGASIS and CCS use greedy algorithms in order to build a chain, starting from the farthest node of the network. A greedy algorithm is always a good choice for chain construction, but for large networks it causes a serious problem that leads to the long link(LL) problem [50,51].
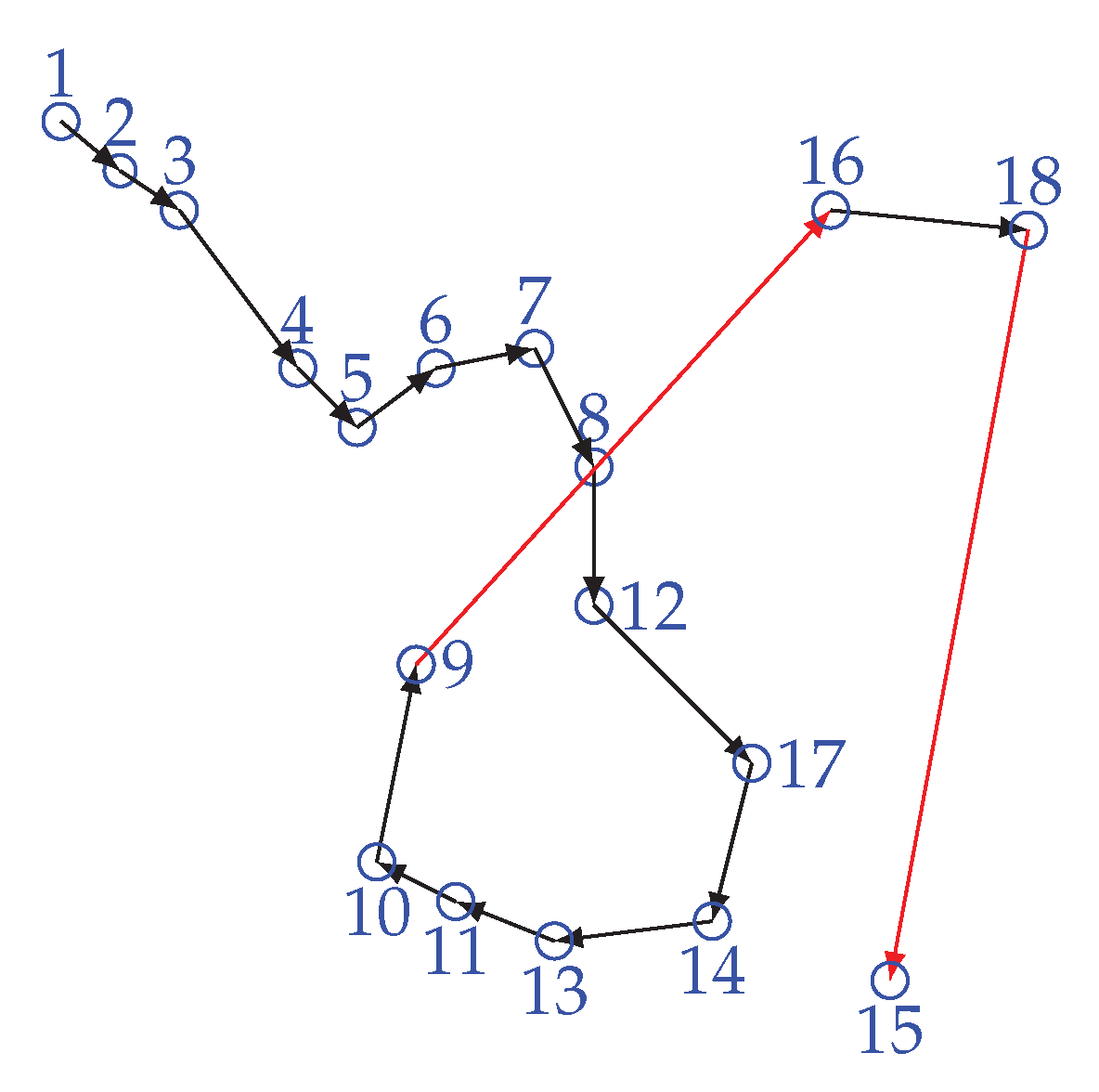
Figure 7 is showing the scenario of the LL problem. In order to solve the LL problem, the proposed scheme makes an enhancement over the greedy method. Instead of connecting with the next minimum distance node that is not in the chain, WEMER connects with a node that is already in the chain, and with whom distance is minimum. In each sector, the chain construction procedure will be started from the farthest node from the head node and it joins the chain first. Then, it finds the distance between itself and other nodes which have not joined the chain yet. It finds the nearest node and sets it as node i waiting to join the chain, i represents the node joined. Node i gets the information of distance between itself and nodes, which are on the chain, it then finds the nearest node j and directly connects with it to join the chain. At this point node i becomes the new end node of the chain. This procedure continues until all sensor nodes have joined the chain, so that a branching chain is finally formed. Figure 8 is showing the chain between node for every sector.
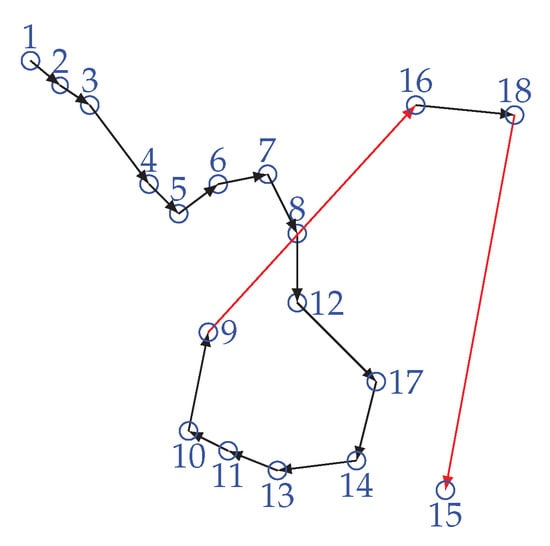
Figure 7.
Long link problem.
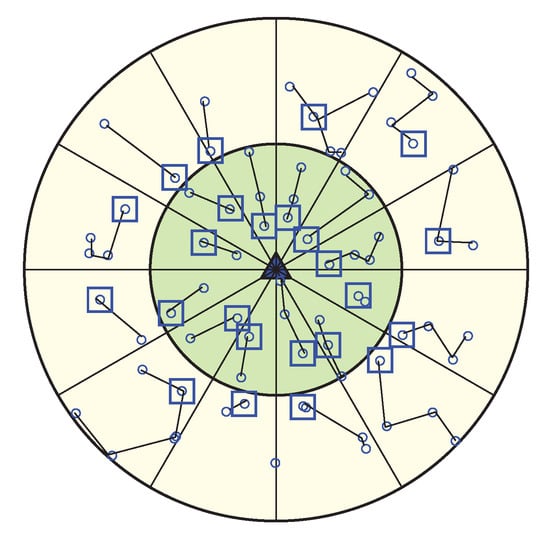
Figure 8.
Chain construction for every sector with head node.
In order to distribute the energy load evenly among all nodes, LL should be avoided. This new chain creation procedure solves the LL(Long Link) problem of greedy algorithms. Thus, a new chain construction method ensure less energy consumption of nodes. The pseudo-code of chain construction procedure is shown in Algorithm 2.
| Algorithm 2: Chain construction procedure for each sector |
 |
Data Communication Phase
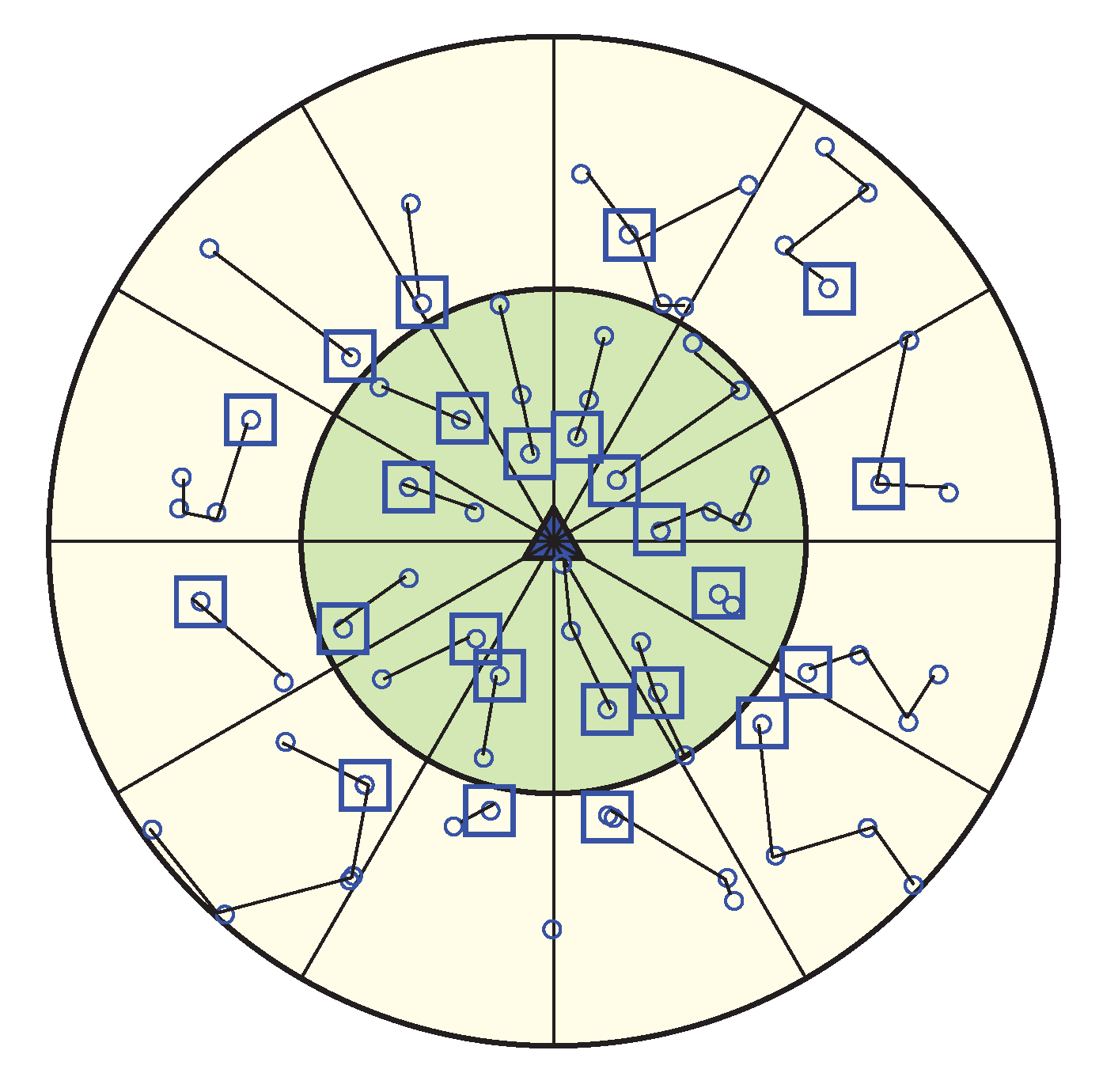
After WEMER performs the first two phases, the HN initiates a token passing approach in order to start the data transmission from the maximum distance node to the HN of the chain. The chain formed in WEMER has more than two end nodes. If, for a node, the connected node count is zero; i.e no node is connected with it, the node is called as the end node/tail node of that chain. As each chain may have more than two end nodes, before data transmission, every end node needs to inform whether it is a head node or not to its connected node. This information helps the flow of data transmission. As a chain has more than two end nodes, it is necessary to know the right path to reach the HN. For this reason in token passing approach every end node informs its connected node if it is HN or not. The pseudo-code of the data communication procedure is shown in Algorithm 3. All nodes in each sector transmit their data along the chain to its selected node, in its slotted time. In order to deliver data, every node send its sense data to its selected neighbor node, in its time slots, assigned by the TDMA mechanism, and after receiving the data, the neighbor node fuses them with its own data and forwards these to its selected neighbor node or HN. After collecting all the data from sector, HN sends this data to its or HN. When the HN within Corona 1 of a sector receives all the data from its predecessor sector, after aggregation, sent all these data to the BS. As the data transmission procedure starts from the outer most coronas, for these reason when Sink receives data from the HN of its corona 1, then one round is complete. In this scheme, the HN in every sector is changed in every round according to distance and energy, thus it reduces the burden of some nodes to elect repeatedly for the HN. Figure 9 is showing connection between nodes along with links between the HN.
| Algorithm 3: Data Communication procedure |
 |
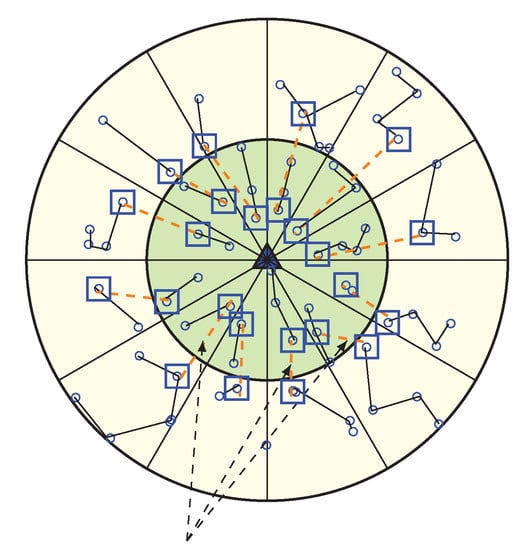
Figure 9.
Data Communication Phase.
3.2.3. Merging Procedure of a Wedge
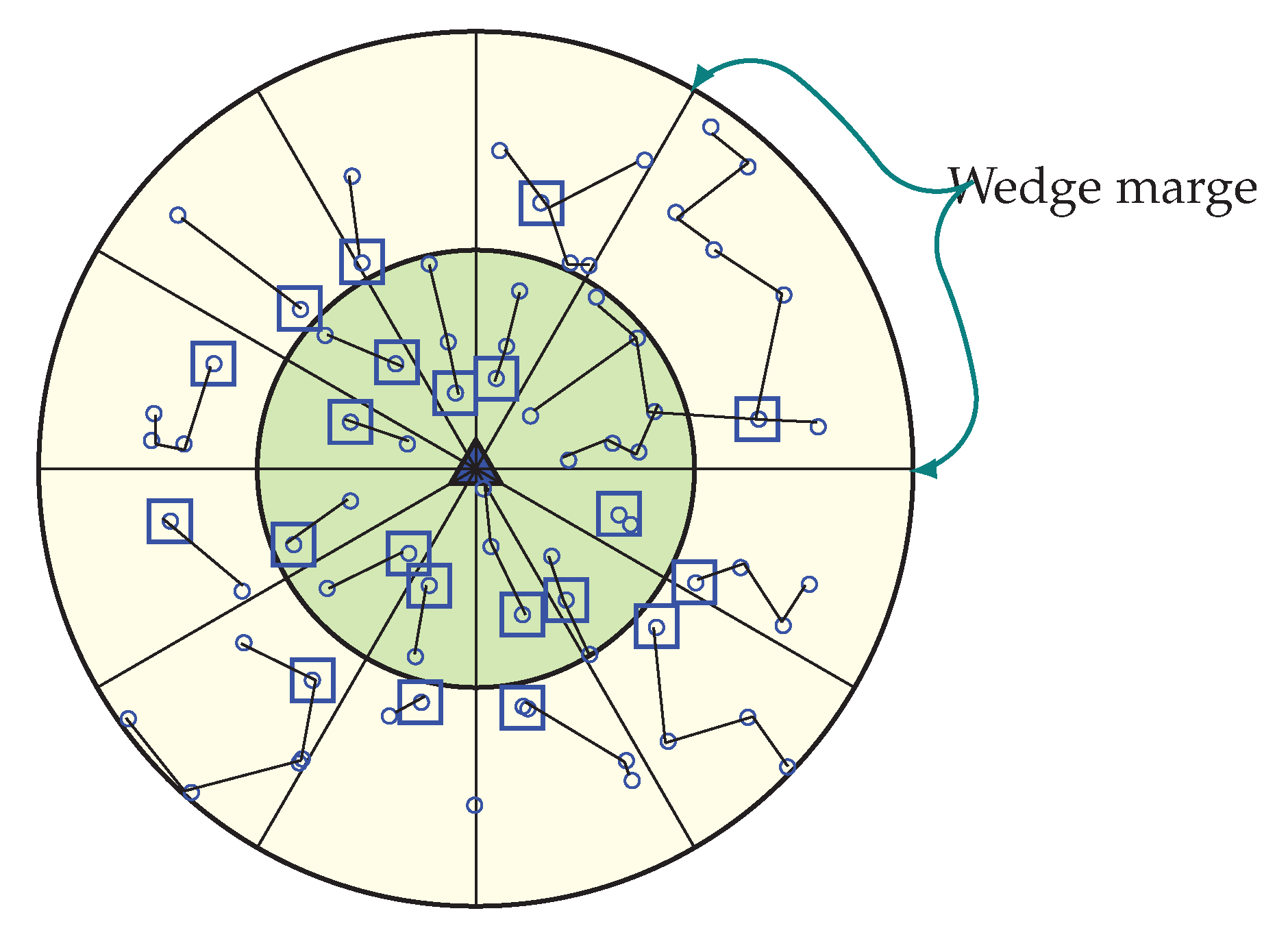
The result of the energy hole is a network partition along with sink isolation and network failure. Moreover it degrades network performance. For this reason the energy hole problem needs to be eliminated in order to maximize the network lifetime. So after the data transmission phase of every round, WEMER checks the average energy of every sector. This is because, if any sectors average energy become low, it creates an energy hole in that portion of the network. For this cause, the wedge which has a sector with low energy then merge with one of the neighboring wedges.
Wedge Merging Step
In our WEMER scheme, wedge merging happen for two reasons. First, in the network initialization phase after the formation of both the corona and wedge, BS check if every sector has more than one node; if not, BS will then merge the wedge of that sector with its neighboring wedge. Second, in the data transmission period, sensor nodes lose their energy to transmit and receive data. So, every head node needs to check for the average energy of its sector after every round. When the RE of a sector becomes less than 40% of its initial energy, the corresponding wedge, belonging to the sector with reduced RE, get merge with one of the neighboring wedges. Figure 10 is the scenario of network after the first wedge merge.
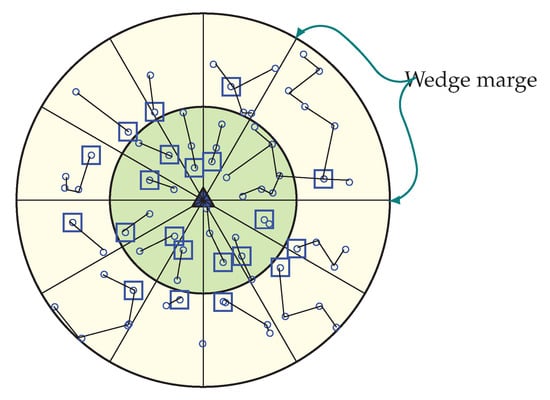
Figure 10.
Occurrence of first wedge merge with a new chain formation and Header Node (HN) selection.
Afterwards, every round, a HN belonging to each sector checks whether the average energy of the sector reaches 40% of its initial energy or not. If it becomes less, the HN starts the wedge merging procedure. In order to start merging wedges, the HN of the lower RE sector sends a beacon named avg_en to its two neighboring wedges, in order to inform them of their average energy. When any HN receives an avg_en beacon from a HN, it responds by sending its sector’s average energy to that HN, as every HN is acquainted with its own sector’s average energy. After the response from the neighboring wedge’s head node, the wedge with the higher energy head node is selected as a wedge to merge. The wedge merging procedure starts from the inner most sector of the corresponding wedge that contains the low energy sector, and ends at the outermost sector of that wedge. Suppose that a sector with the position (2, 2) has a low energy and decides to start merging, it will then send avg_en beacon to the sectors with position (2, 3) and (2, 1) by sending their average energy. After receiving avg_en, the beacon head node responds by sending their average energy, and sector (2, 3) will be selected for merging, as this sector has more average energy than sector (2, 1). At first, sector (1, 3) and (1, 2) get merge and all nodes from sector (1, 2) updates their sectors as (1, 3). After that, sector (2, 2) and (2, 3) are merge, and this procedure continues until the outermost sector merges.
Update of Nodes Position
In the wedge merging procedure, every node in the merge wedge updates their position according to the new wedge; in this way two different wedges become one. Additionally, neighbors of merged wedges update their neighbor’s information. The new wedge selects its head node and then creates new chain for data communication. In Figure 10, the first merged wedge is showing. After completing several round in the network, every sector has enough energy in order to continue its data transmission but, the HN of sector (2, 2) found that its average energy is lower than 40% of its initial energy, so it starts to merge with another sector. From two neighbor sectors (2, 1) and (2, 3), it found that sector (2, 1) has more energy than sector (2, 3). Thus, it merge with sector (2, 1) and a new sector is constructed, shown in Figure 10. As the low energy sector is merged with the sector of high energy, it again gets more high energy nodes to make a chain. Figure 11 is showing when all wedges merge in the network.
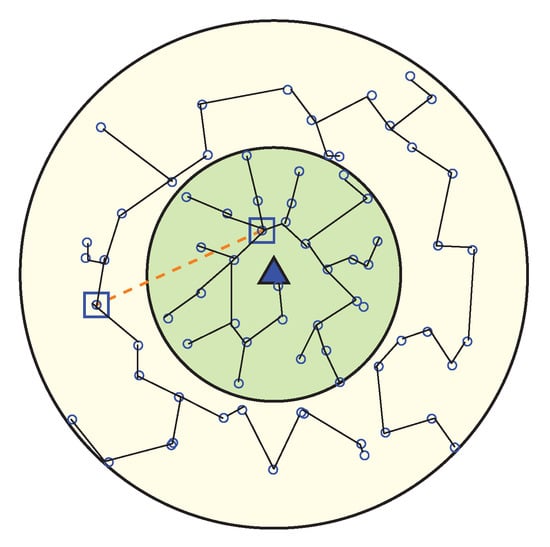
Figure 11.
Network topology after all wedges are merged.
3.2.4. Avoid Long Link Communication
In order to make the WEMER efficient, the distance threshold concept is used. When one or more wedges merge, a node that is farthest from the HN needs to travel a long distance in order to send their data to the HN. This introduces a longer link in data transmission. In order to avoid this long link, a new concept of using the distance threshold () is proposed in order to reduce data from long link traverse of the network. In a sector, when the maximum distance between two nodes become greater than the value, more than one HN can be created for that sector.
After wedge merging, every node calculates their distance with the other nodes of the sector. If the maximum distance between two nodes is greater than , then, according to the distance, more HNs can be selected for that sector. As width of corona one and corona two is not same, two different distance thresholds are used. For corona one, the distance threshold is 30, whereas for corona two, the distance threshold is 45. Figure 12 is showing two HNs in a sector.
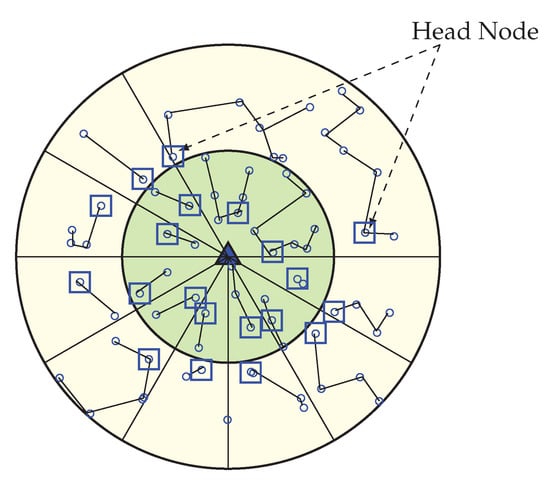
Figure 12.
Avoidance of long distance communication by selecting more than one HN for a sector.
Multiple HN selection procedure is similar as single HN selection type, however, the difference is that, in order to make a certain distance between the HN when the first HN selects, it sends to its sector within transmission range . The nodes who receive this message can not participate for any other HN selection competition during this round, and the node who did not receive any message continues the head node selection procedure in order to be the second HN for a sector. This procedure continues until all nodes receive . Figure 13 is showing the scenario of HN when all wedges merge in the network. After the HN selection procedure, in order to construct a chain, nodes join to the HN which is closest to it. The chain construction and data transmission technique is the same as a single HN procedure type.
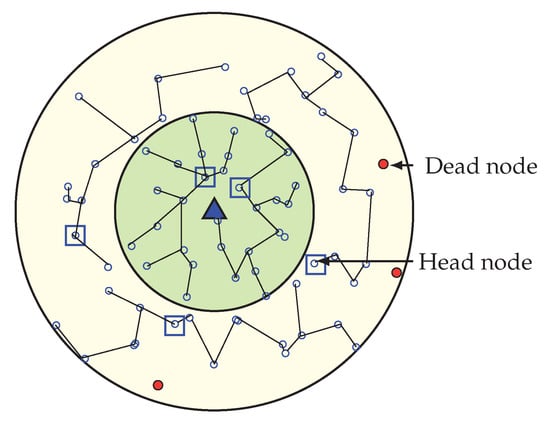
Figure 13.
When all wedges merge.
4. Simulation and Result
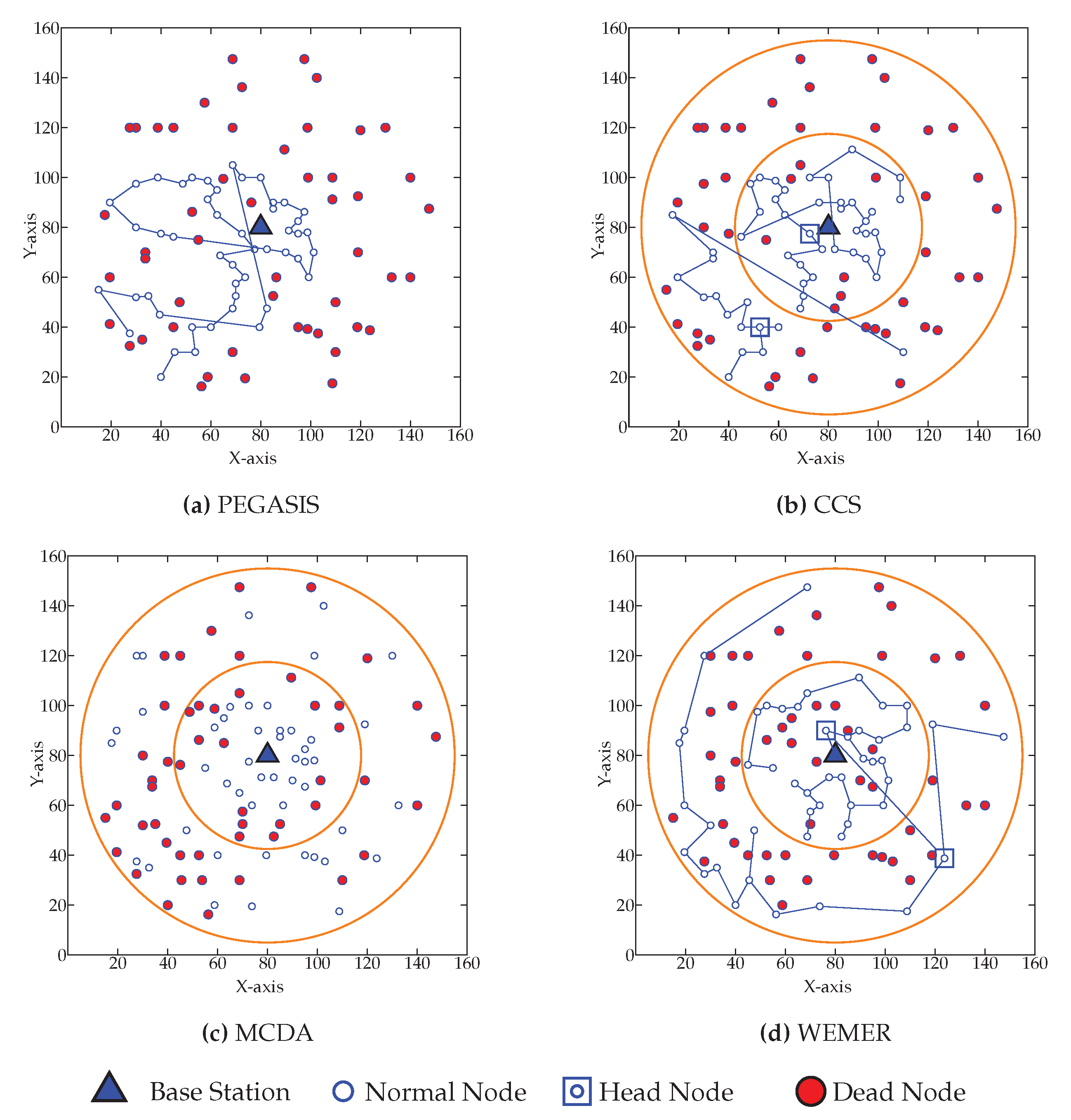
In this section, extensive simulation results are provided, with comparisons of performance between the proposed WEMER technique and three other popular methods: Power Efficient GAthering in Sensor Information Systems (PEGASIS), Concentric Clustering Scheme (CCS), and Multilayer Cluster Designing Algorithm (MCDA). This is done to study the performance of energy consumption, the network lifetime, as well as alive and dead nodes over rounds in this section.
Simulation is done in the MATLAB [52] environment in order to evaluate the performance of the proposed WEMER scheme with the three popular protocols PEGASIS, CCS and MCDA. By using the simulation result with different simulation scenarios, WEMER is compared with the previous protocol.
4.1. Experiment Setup
Table 2 shows the parameters used in the simulation. A homogeneous sensor network is assumed, in which all sensor nodes have equal sensing and processing capabilities initially. Each node has the initial energy of 0.5 Joule, and the length of the data message is 4000 bits. Our selection of these values is highly motivated by [45,53,54,55,56]. Each sensor node has location information, and no mobility is taken in account to mean that nodes are static in nature. In the proposed scheme, the data is passed through a multi-hop approach.

Table 2.
System Parameters
4.2. Results and Discussion
In this section, the performance analysis of the WEMER scheme is carried out through simulation results. Performance improvement in terms of network lifetime, energy cost, and balanced energy consumption is investigated and compared to existing protocols: PEGASIS, CCS and MCDA.
4.2.1. Residual Energy of Network per Round
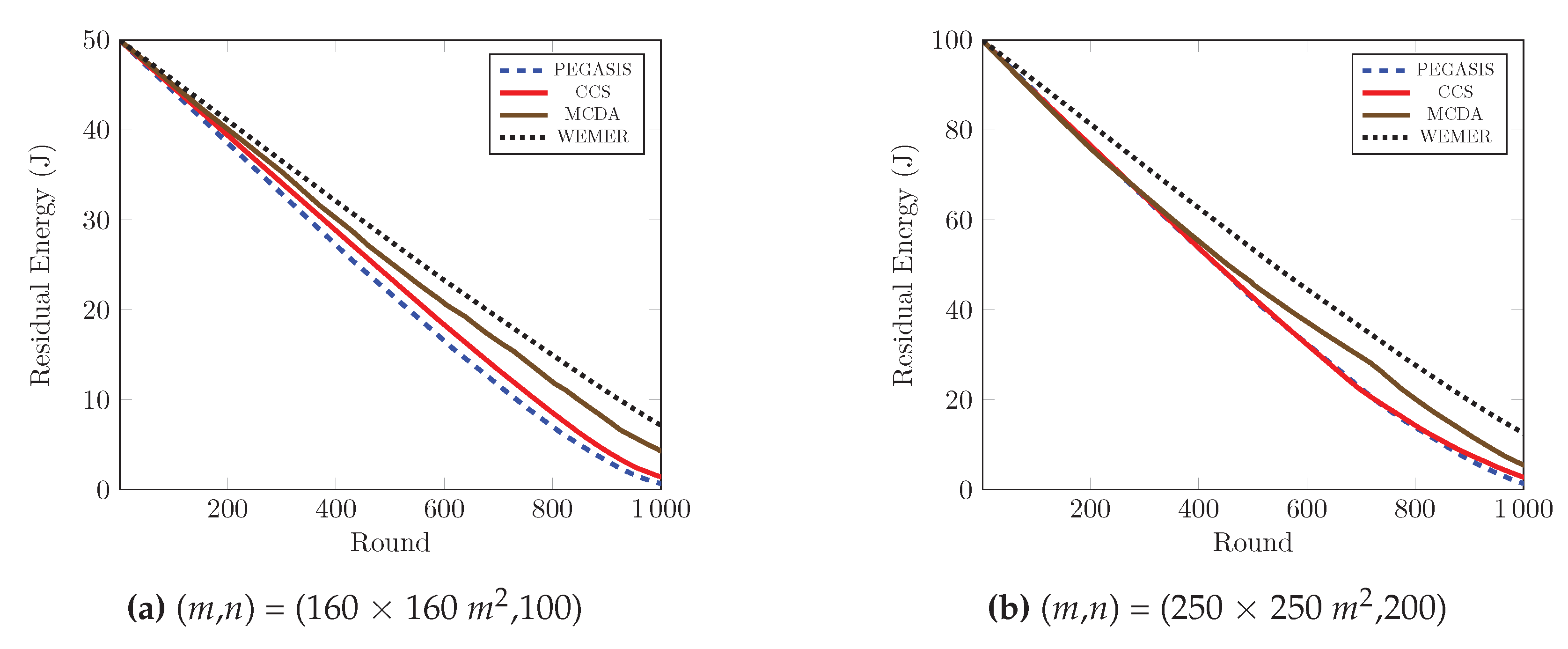
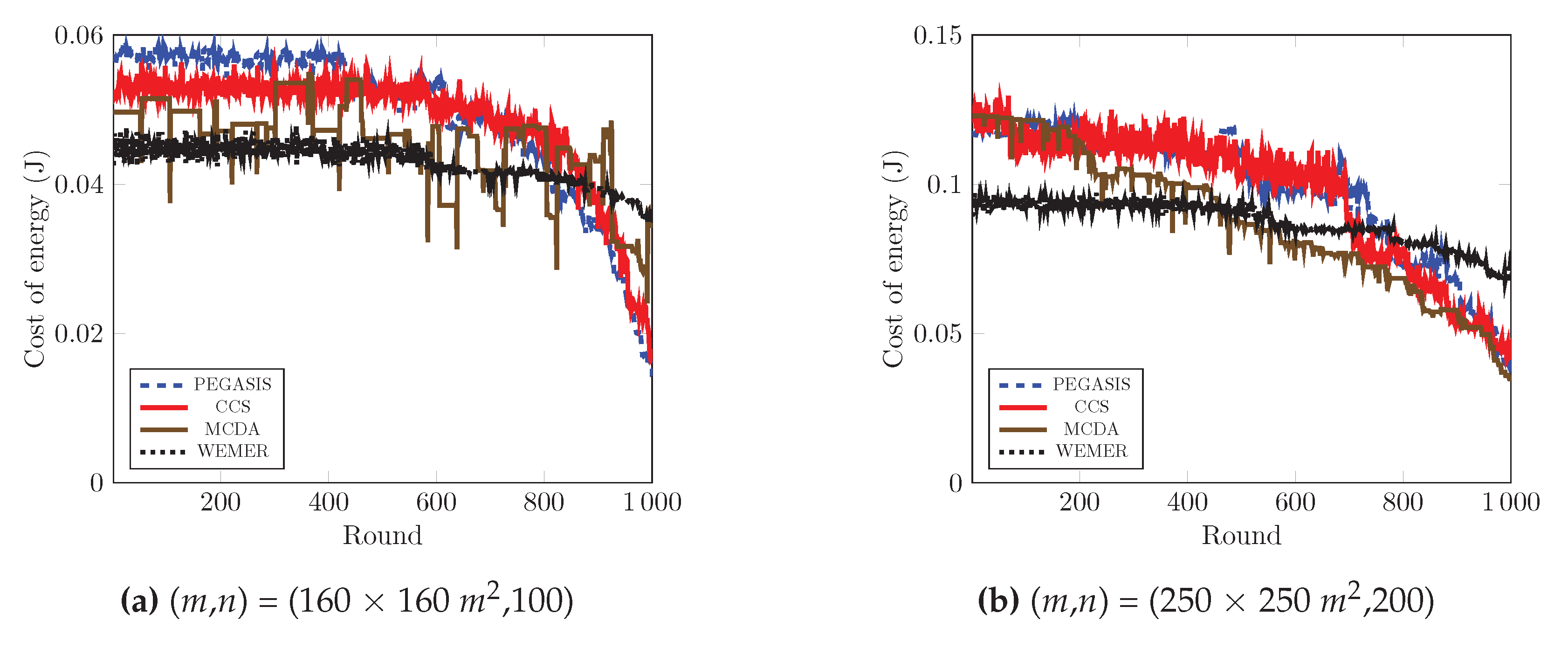
The remaining energy of the sensor nodes after each round, affects the network lifetime directly. If the remaining energy of the nodes is high, then the network lifetime is high; and vice versa. Figure 14 demonstrates the performance comparison in terms of residual energy of the network, with respect to the round. Figure 14a shows that, at round 600, the remaining energy of the network is 33.1%, 36.65% and 41.45% for PEGASIS, CCS and MCDA respectively, while in the proposed protocol, the remaining energy of the network is 46.56% of the initial energy. Furthermore, at round 1000, the remaining energy of the proposed protocol is greater than 6.47 J, 5.7 J, and 2.87 J compared with the PEGASIS, CCS and MCDA protocols respectively. It is clear from the figure that proposed protocol is more energy efficient than PEGASIS, CCS and MCDA, as the selection of the HN for every sector depends on both the distance with the relevant HN and residual energy, the nodes that contain low residual energy and are isolated from other nodes of the sector, can not be selected as Head Node. Figure 14b demonstrates the results of the same metric for 250 × 250 m area with 200 nodes, and it also agrees with the previous characteristics.
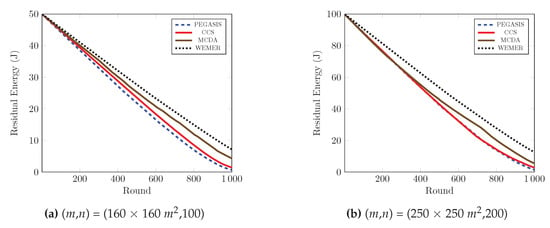
Figure 14.
Residual energy of network with respect to round
4.2.2. Number of Alive Nodes over Round
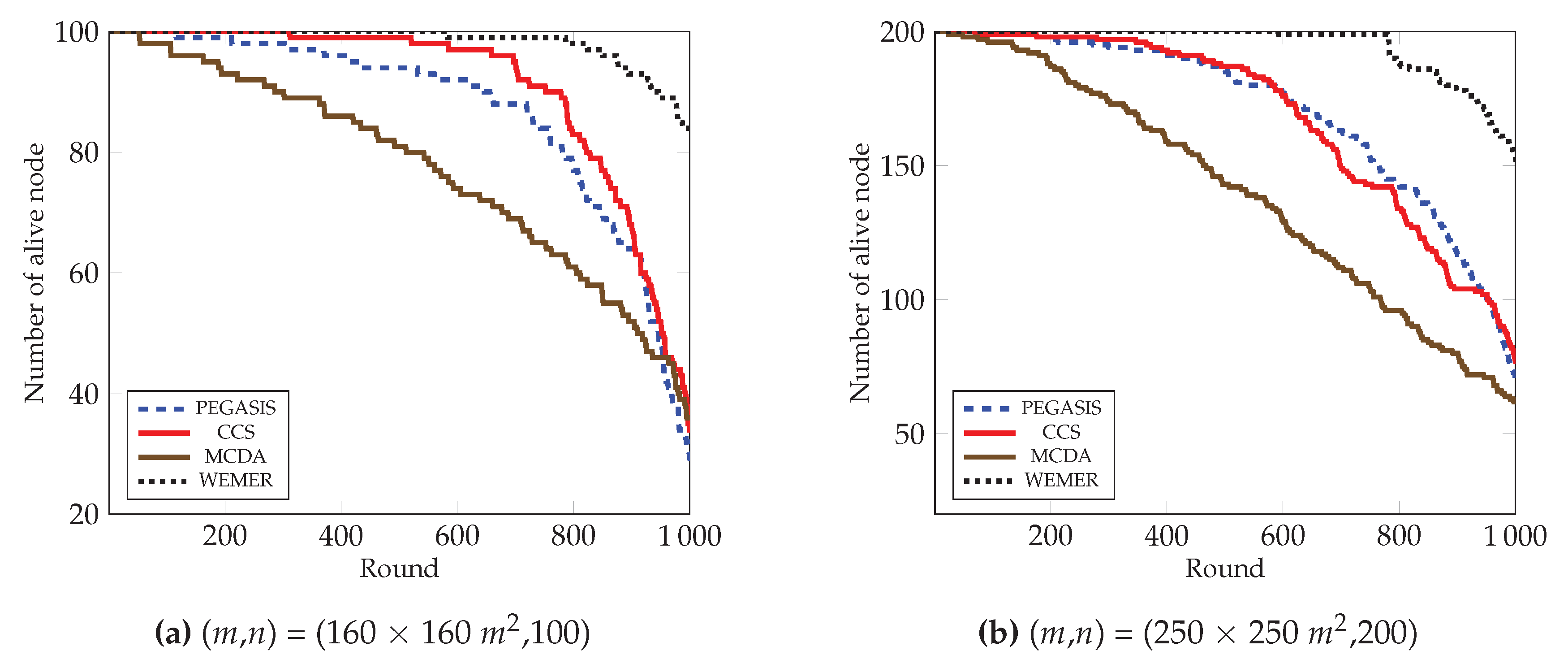
To prolong the network lifetime of network, the number of alive nodes is an important parameter. Figure 15 clearly depicts that the number of alive nodes in the network is higher than the competitive protocols. At round 800 in Figure 15a, 98% of the nodes are still alive in the proposed protocol, whereas 77%, 83%, and 61% of the nodes are alive in the network for the PEGASIS, CCS, and MCDA protocols respectively. Accordingly, at round 1000, 56%, 50% and 48% more nodes are alive in the proposed protocol, as compared to the existing PEGASIS, CCS, and MCDA protocols respectively. This is because the PEGASIS protocol constructs a chain by using a greedy method, thus it creates a Long Link (LL) between nodes during chain construction, so that nodes deplete energy very fast and die early. CCS also uses a greedy method in order to construct a chain and also suffer from LL, whereas MCDA is free from LL, however, because its layer 1 nodes directly communicate with the BS, the nodes in the boundary deplete their energy much faster than any other node. In contrast, the chain construction procedure of proposed WEMER is so efficient that it reduces both the distance and LL between sensor nodes. Additionally, HN selection depends on the distance between the or HN or BS and the energy, so all nodes get the chance to be a HN. All of these considered parameters of WEMER reduce energy consumption of nodes and increase the lifetime of the network. Figure 15b also shows that the proposed protocol significantly outperforms PEGASIS, CCS, and MCDA protocols.
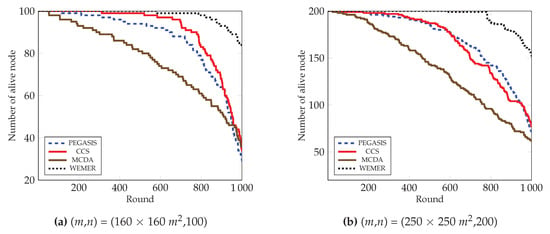
Figure 15.
Number of alive nodes over round.
4.2.3. Number of Dead Nodes over a Round
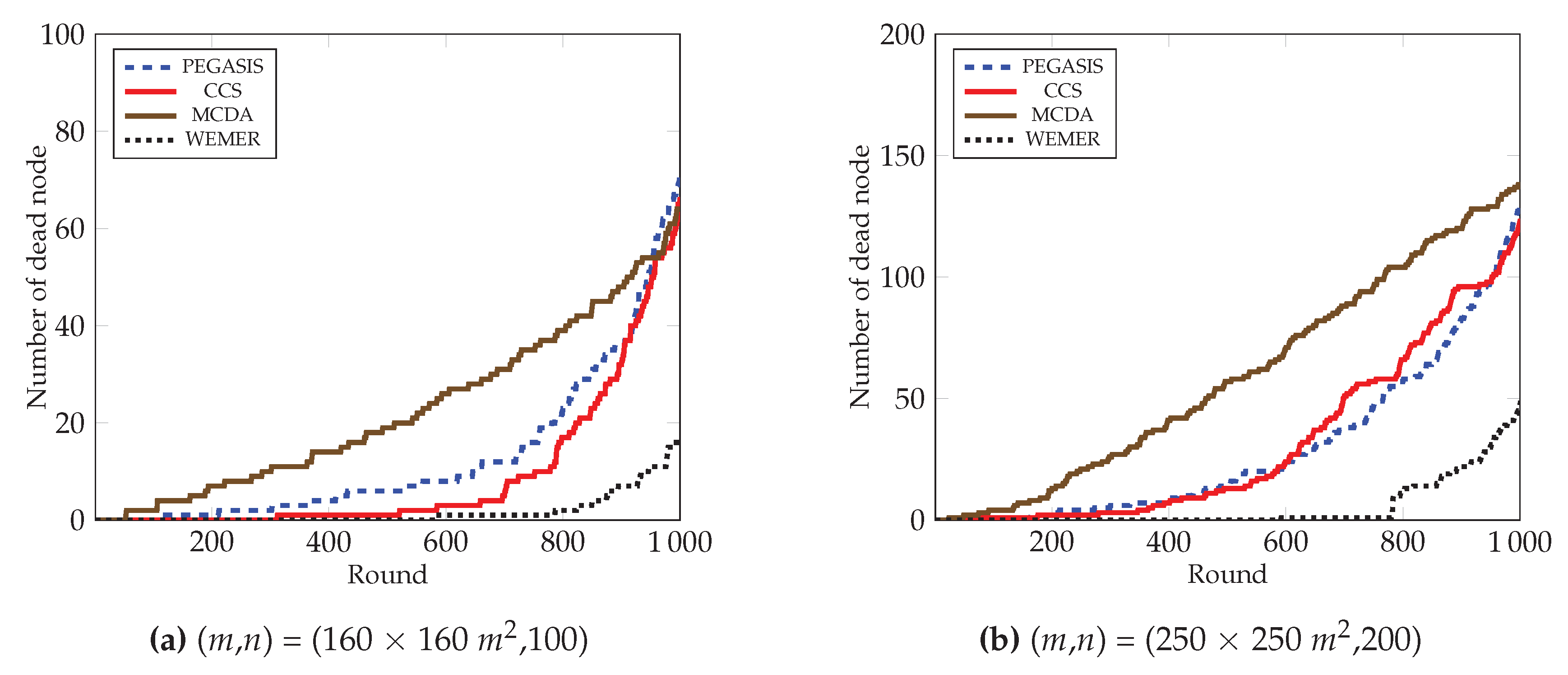
In Figure 16, the number of dead node over the round of all protocols is demonstrated. It is clear from the figure that the number of dead nodes in the network of the proposed protocol is much less than the existing protocols. The proposed protocol deals with the load balance by creating sectors, and then selecting the most fit node as head node. As a result, the proposed protocol prohibits the sudden death of the node. At round 700, only 1% of nodes have died in the proposed protocol. In contrast, 12%, 5%, and 31% nodes die in the PEGASIS, CCS, and MCDA protocols respectively. Both the PEGASIS and the CCS protocols face the long link problem that has already been discussed; in such a situation, nodes need to forward data in a long path. This eventually causes too much energy consumption, as well as the premature death of nodes. From Figure 16b, it is also observed that at round 800, only 6% nodes die in case of the proposed protocol, whereas the number increases to 28.5%, 33%, and 52% for PEGASIS, CCS, and MCDA protocols respectively.
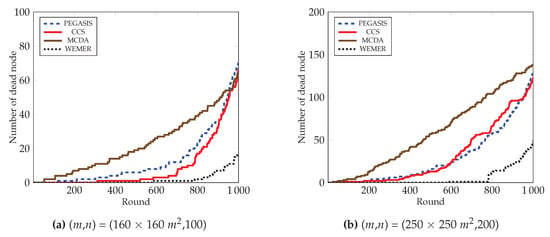
Figure 16.
Number of dead nodes over round.
4.2.4. Percentage of Dead Node
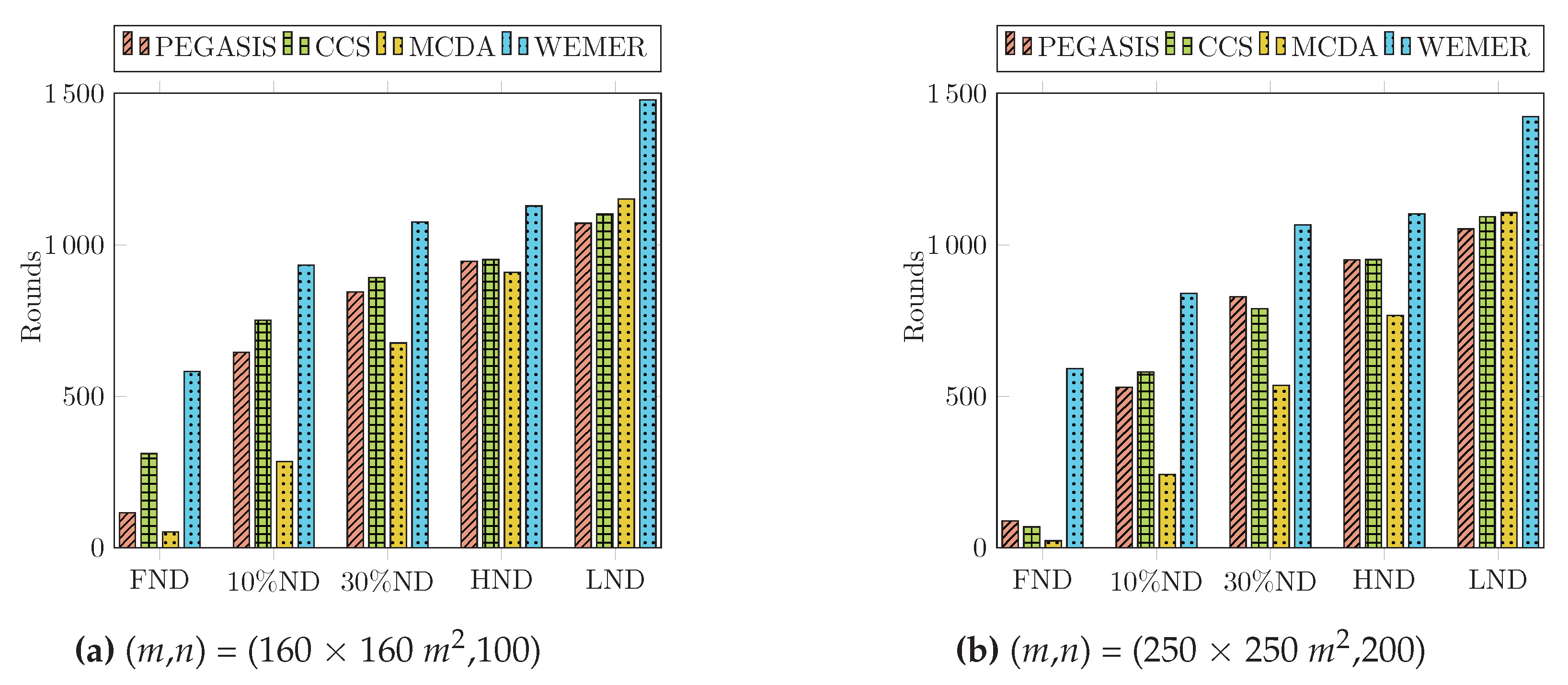
The condition of the network can easily be identified through First Node Die (FND), Half Node Die (HND), and Last Node Die (LND). In this paper we also carried out two more parameters: 10% Node Die (TND) and 30% Node Die (THND), in order to compare the performance. The instability period of the network starts after the FND occurs, as shown in Table 3. The percentage of dead nodes also demonstrates the total lifetime of the network in terms of a round. Figure 17a clearly shows that for PEGASIS, CCS, and MCDA, the first node dies at round 115, 311, 52, however, for WEMER, the first node dies at round 582. Fifty percent and Last Node Die for WEMER at round 1128 and 1478 respectively, whereas for PEGASIS, CCS, MCDA, fifty percent and Last Node Die at round 945, 951, 909 and 1071, 1102, 1154 respectively. In the case of the MCDA protocol, the FND and TND occur early, but the moderate load balancing scheme extend the lifetime of nodes, as compared to PEGASIS and CCS. From Figure 17b and Table 4, it is also obvious that WEMER outperforms PEGASIS, CCS, and MCDA in terms of network stability period considering 200 nodes and 250 × 250 m area.

Table 3.
Comparison of the proposed WEdge MERging (WEMER) with contemporary protocols in terms of longevity and energy consumption when area is 160 × 160 m and N = 100.
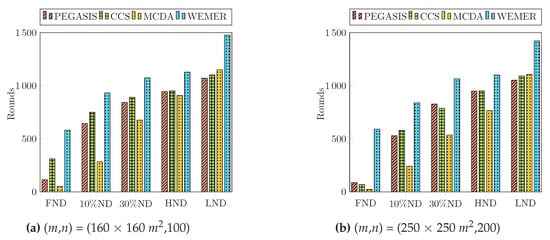
Figure 17.
Percentage of dead node.

Table 4.
Comparison of the proposed WEMER with contemporary protocols in terms of longevity and energy consumption when area is 250 × 250 m and N = 200.
If all node of corona 1 died and node of corona 2 is still active, than corona 2 node directs communicate with base station. The detailed network condition about how the nodes connect after nodes die are given below:
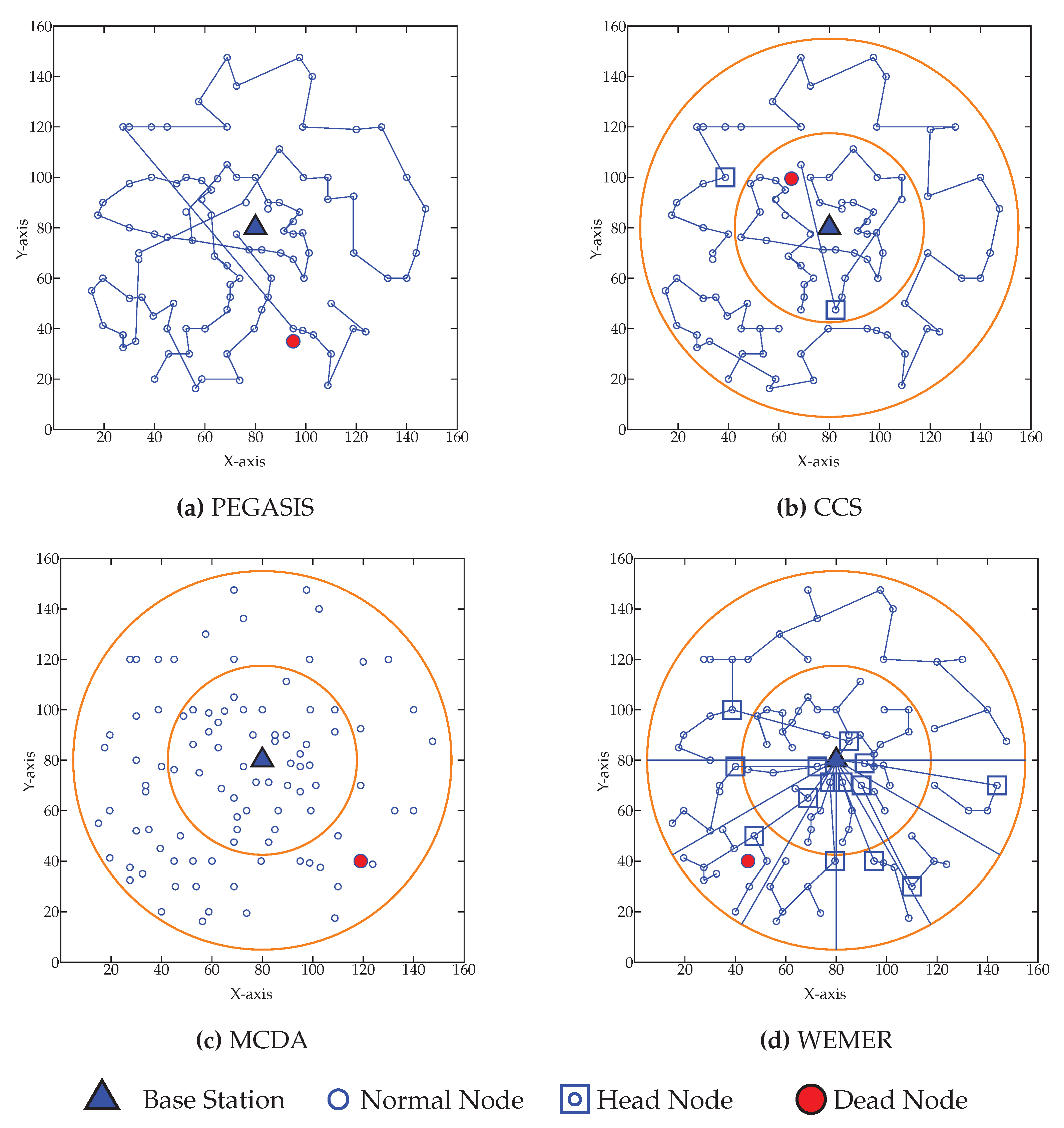
Network After First Node Died
Figure 18 shows the network condition when first node died for WEMER and all three compared protocol. Figure 18a is showing the node’s data transmission condition for PEGASIS. For PEGASIS, at round 115 the first node died and when a node died a new chain is constructed bypassing that dead node. At the same way for CCS, MCDA and WEMER’s first node died at round 311, 388, 582 and are showing in Figure 18b–d. When the node died in the network, that node cannot take part in data transmission, so it is necessary to make energy consumption of every node very low so that it dies after a long time. It is very clear from the figure that WEMER performs better than all three protocols. The more nodes involved in data transmission process, the more it helps BS closer nodes to save their energy or protect high energy consumption. As chain construction procedure and HN selection took place after every round so it make sure that no low residual energy node select as HN and no node select HN repeatedly.
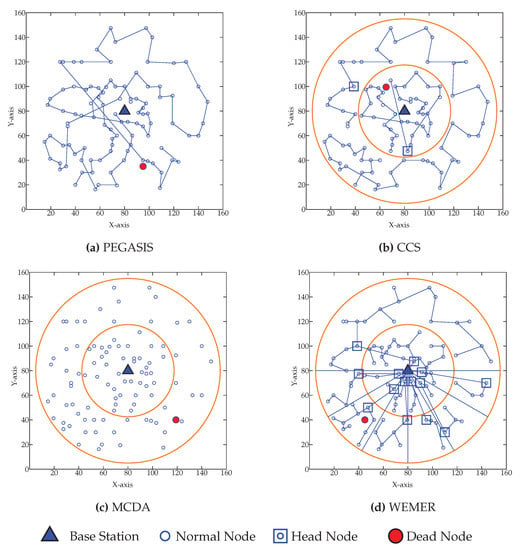
Figure 18.
Network topology after First node die (a) at 115th round for Power Efficient GAthering in Sensor Information Systems (PEGASIS) (b) at 311th round for Concentric Clustering Scheme (CCS) (c) at 52th round for Multilayer Cluster Designing Algorithm (MCDA) (d) at 582th round for WEMER.
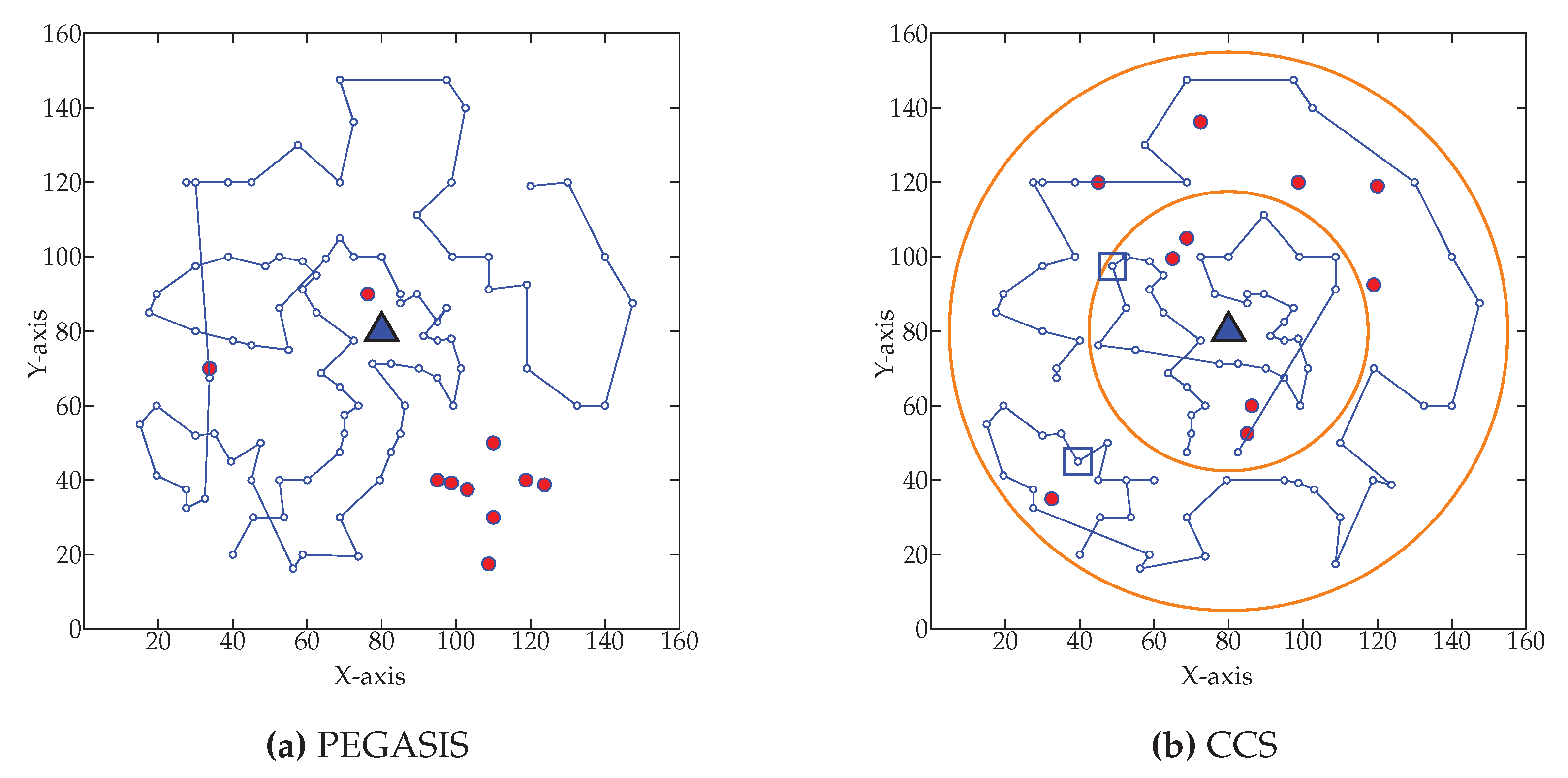
Network After Ten Percent of Node Died
Figure 19 shows the network condition when ten percent node dies for WEMER and three comparative protocols. Figure 19a shows the node’s data transmission condition for PEGASIS. For PEGASIS, ten percent of its node dies at 645th round. Similarly, the same percentage of nodes dies at 751st, 601st, and 933rd round for CCS, MCDA, and WEMER protocols demonstrated in Figure 19b–d respectively.
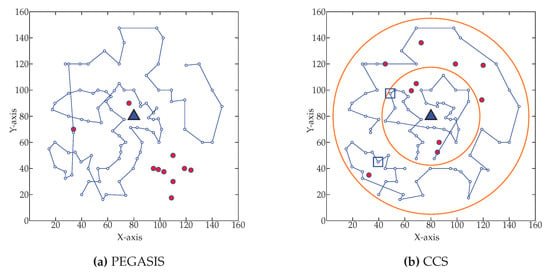
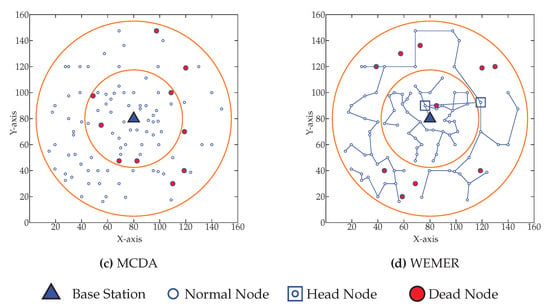
Figure 19.
Network topology after Ten percent node die (a) at 645th round for PEGASIS (b) at 751st round for CCS (c) at 601st round for MCDA (d) at 938th round for WEMER.
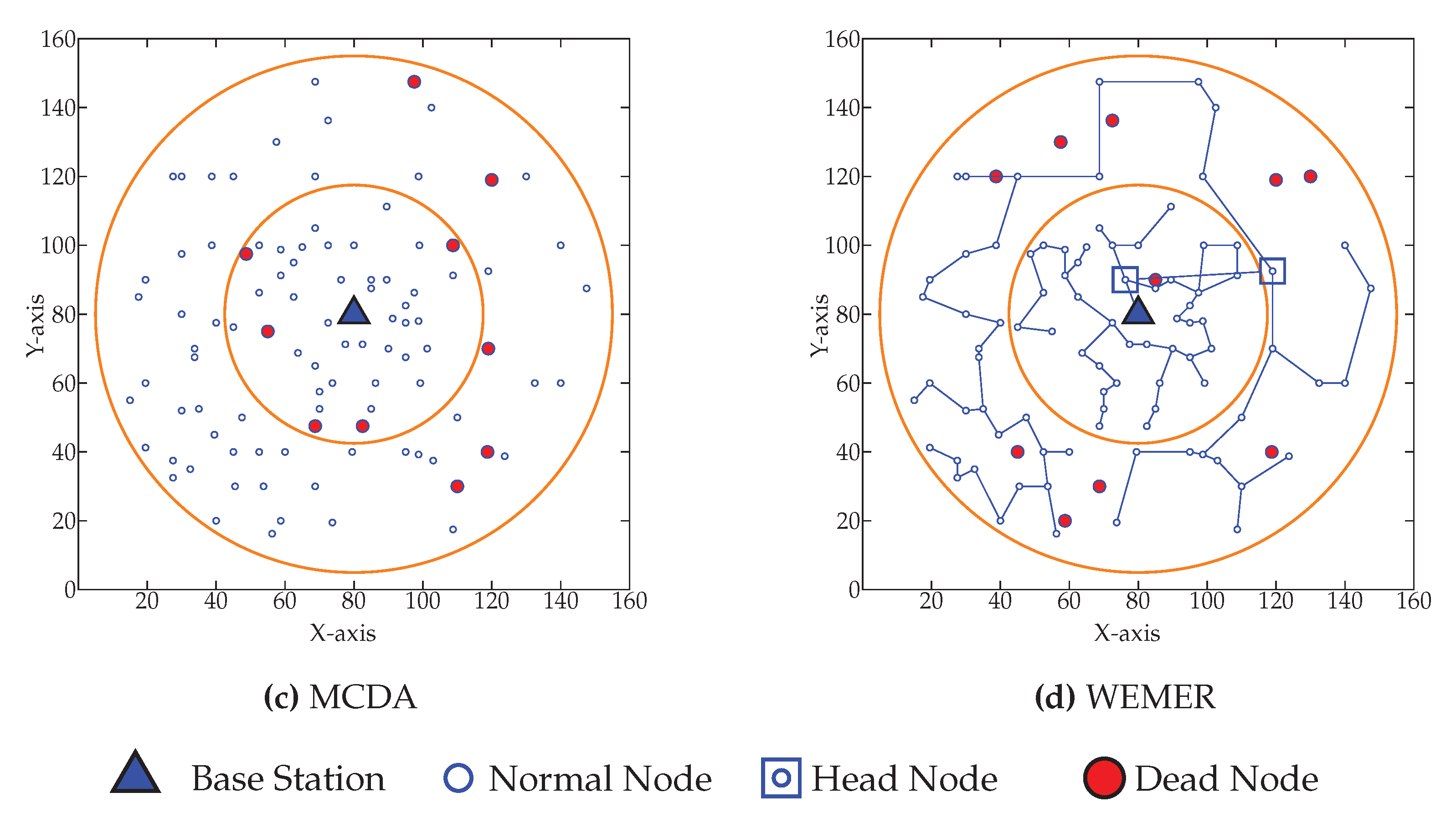
Network After Fifty Percent of Node Died
Figure 20 shows the network topology when fifty percent of nodes die. Figure 20a shows that fifty percent node dies at 945th round in PEGASIS. Figure 20b–d show that the same percentage of nodes die for CCS, MCDA and WEMER at 951st, 987th, 1128th round respectively.
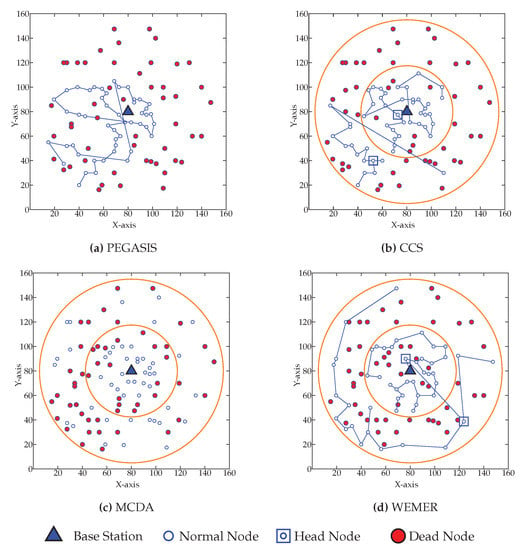
Figure 20.
Network topology after Fifty node die (a) at 945th round for PEGASIS (b) at 951st round for CCS (c) at 987th round for MCDA (d) at 1128th round for WEMER.
4.2.5. Average Energy Cost of a Node for a Round
To maximize the lifetime of the network, the energy cost per round is another essential parameter. Figure 21a clearly shows that at round 800, CCS and PEGASIS consumes 0.05 J per round and then the consumed energy abruptly drops as the energy cost of the network is greatly reduced due to the fact that most of the nodes die beyond 800th round. On the other hand, MCDA’s cost per energy is in a zigzag manner, thus, sometimes the network consumes high energy and sometimes low energy. In contrast, the proposed protocol consumes energy in a stable manner. The proper head node selection and wedge merging scheme allows the network to consumes a stable rate and prohibits the sudden death of the network. As shown in Figure 21a and Table 3, the average energy cost of the network is 0.049297 J, 0.0485402 J, and 0.045712 J for PEGASIS, CCS, and MCDA respectively, whereas it is 0.042847 J for the proposed protocol. Furthermore, the maximum energy consumption in any particular round is 0.044642 J for the proposed protocol, in contrast to 0.058585 J. 0.053361 J, and 0.49652 J for PEGASIS, CCS, and MCDA respectively. Besides, Figure 21b and Table 4 demonstrate that the proposed WEMER reduces the energy cost by 12.70%, 11.14%, and 0.82% as compared to PEGASIS, CCS, and MCDA respectively.
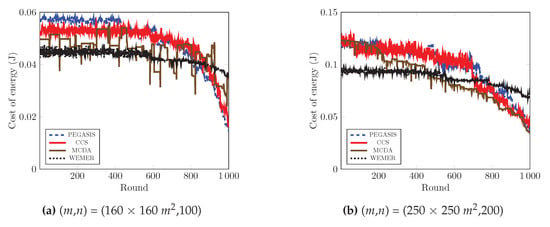
Figure 21.
Average energy cost over round.
5. Conclusions
Extending the network lifetime is one of the most challenging issues in WSNs. Uneven energy consumption among the nodes contributes to the creation of energy holes, which significantly decreases the network lifetime. In this research work, a dynamic WEdge MERging (WEMER) based scheme named WEMER is proposed, that minimizes energy hole creation by dividing the whole network into a number of coronas and wedges, and then merging a wedge with one of the neighboring wedges whenever it is likely to have a hole. In the head node selection phase, WEMER considers both the residual energy of each node, and the distance between node and successor HN as parameters to select the most efficient head node. This makes the energy consumption among nodes more balanced. For routing, WEMER uses an enhanced version of a greedy algorithm in order to construct the chain between nodes, which effectively makes the energy consumption lower. Simulation result shows that the proposed WEMER scheme outperforms the contemporary schemes in terms of network lifetime, energy consumption, and energy cost.
Author Contributions
Conceptualization, M.S.A. and M.S.A.S.; methodology, N.S. and A.K.; software, N.S. and A.K.; validation, M.S.A. and M.S.A.S.; formal analysis, N.S. and A.K.; investigation, N.S. and A.K.; resources, N.S. and A.K.; data curation, N.S. and A.K.; writing—original draft preparation, N.S. and A.K.; writing—review and editing, W.L.L.; visualization, N.S. and A.K.; supervision, M.S.A. and M.S.A.S.; project administration, M.S.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| HN | Head Node |
| WEMER | WEdge MERging |
| PEGASIS | Power Efficient Gathering in Sensor Information Systems |
| CCS | Concentric Clustering Scheme |
| MCDA | Multilayer Cluster Designing Algorithm |
| WSNs | Wireless Sensor Networks |
| BS | Base Station |
| RE | Residual Energy |
| EHP | Energy Hole Problem |
| ADRP | Adaptive Decentralized Re-clustering Protocol |
| CH | Cluster Head |
| MDC | mobile data collector |
| CCO | Cluster Coordinator |
| DCD | Distributed Cluster Designing |
| CCD | Centralized Cluster Designing |
| CCS | Concentric Clustering Scheme |
| CN | Corona Number |
| WN | Wedge Number |
| LL | Long link |
| TDMA | Time Division Multiple Access |
| FND | First Node Die |
| HND | Half Node Die |
| LND | Last Node Die |
| TND | 10% Node Die |
| THND | 30% Node Die |
References
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: A survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Puccinelli, D.; Haenggi, M. Wireless sensor networks: Applications and challenges of ubiquitous sensing. IEEE Circuits Syst. Mag. 2005, 5, 19–31. [Google Scholar] [CrossRef]
- Rabby, M.K.M.; Alam, M.S.; Shawkat, M.S.A. A priority based energy harvesting scheme for charging embedded sensor nodes in wireless body area networks. PLoS ONE 2019, 14, e0214716. [Google Scholar] [CrossRef] [PubMed]
- Rabby, M.K.M.; Alam, M.S.; Shawkat, S.A.; Hoque, M.A. A scheduling scheme for efficient wireless charging of sensor nodes in WBAN. In Proceedings of the Second IEEE/ACM International Conference on Connected Health: Applications, Systems and Engineering Technologies, Philadelphia, PA, USA, 17–19 July 2017; pp. 31–36. [Google Scholar]
- Jan, N.; Javaid, N.; Javaid, Q.; Alrajeh, N.; Alam, M.; Khan, Z.A.; Niaz, I.A. A balanced energy-consuming and hole-alleviating algorithm for wireless sensor networks. IEEE Access 2017, 5, 6134–6150. [Google Scholar] [CrossRef]
- Naureen, A.; Zhang, N.; Furber, S. Identifying Energy Holes in Randomly Deployed Hierarchical Wireless Sensor Networks. IEEE Access 2017, 5, 21395–21418. [Google Scholar] [CrossRef]
- Ren, J.; Zhang, Y.; Zhang, K.; Liu, A.; Chen, J.; Shen, X.S. Lifetime and energy hole evolution analysis in data-gathering wireless sensor networks. IEEE Trans. Ind. Inform. 2016, 12, 788–800. [Google Scholar] [CrossRef]
- Sharmin, N.; Alam, M.S.; Moni, S.S. WEMER: An energy hole mitigation scheme in Wireless Sensor Networks. In Proceedings of the 2016 IEEE International WIE Conference on Electrical and Computer Engineering (WIECON-ECE), Pune, India, 19–21 December 2016; pp. 229–232. [Google Scholar]
- Perillo, M.; Cheng, Z.; Heinzelman, W. An analysis of strategies for mitigating the sensor network hot spot problem. In Proceedings of the Second Annual International Conference on Mobile and Ubiquitous Systems: Networking and Services, San Diego, CA, USA, 17–21 July 2005; pp. 474–478. [Google Scholar]
- Jung, J.W.; Ingram, M.A. Residual-energy-activated cooperative transmission (REACT) to avoid the energy hole. In Proceedings of the 2010 IEEE International Conference on Communications Workshops (ICC), Capetown, South Africa, 23–27 May 2010; pp. 1–5. [Google Scholar]
- Olariu, S.; Stojmenovic, I. Design guidelines for maximizing lifetime and avoiding energy holes in sensor networks with uniform distribution and uniform reporting. In Proceedings of the 25th IEEE International Conference on Computer Communications, Barcelona, Spain, 23–29 April 2006; pp. 1–12. [Google Scholar]
- Sharma, R. Energy holes avoiding techniques in sensor networks: A survey. Int. J. Eng. Trends Technol. 2015, 20, 204–208. [Google Scholar] [CrossRef]
- Ammari, H.M. Investigating the energy sink-hole problem in connected k-covered wireless sensor networks. IEEE Trans. Comput. 2014, 63, 2729–2742. [Google Scholar] [CrossRef]
- Wu, X.; Chen, G.; Das, S.K. Avoiding energy holes in wireless sensor networks with nonuniform node distribution. IEEE Trans. Parallel Distrib. Syst. 2008, 19, 710–720. [Google Scholar]
- Liu, X. A novel transmission range adjustment strategy for energy hole avoiding in wireless sensor networks. J. Netw. Comput. Appl. 2016, 67, 43–52. [Google Scholar] [CrossRef]
- Singh, V.K.; Kumar, M. A Compressed Sensing Approach to Resolve The Energy Hole Problem in Large Scale WSNs. Wirel. Pers. Commun. 2018, 99, 185–201. [Google Scholar] [CrossRef]
- Asharioun, H.; Asadollahi, H.; Wan, T.C.; Gharaei, N. A survey on analytical modeling and mitigation techniques for the energy hole problem in corona-based wireless sensor network. Wirel. Pers. Commun. 2015, 81, 161–187. [Google Scholar] [CrossRef]
- Pantazis, N.A.; Nikolidakis, S.A.; Vergados, D.D. Energy-efficient routing protocols in wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2013, 15, 551–591. [Google Scholar] [CrossRef]
- Lu, H.; Li, J.; Wang, G. A novel energy efficient routing algorithm for hierarchically clustered wireless sensor networks. In Proceedings of the Fourth International Conference on Frontier of Computer Science and Technology, Shanghai, China, 17–19 December 2009; pp. 565–570. [Google Scholar]
- Chen, Y.; Li, Q.; Fei, L.; Gao, Q. Mitigating energy holes in wireless sensor networks using cooperative communication. In Proceedings of the 2012 IEEE 23rd International Symposium on Personal Indoor and Mobile Radio Communications (PIMRC), Sydney, NSW, Australia, 9–12 September 2012; pp. 857–862. [Google Scholar]
- Yu, J.; Qi, Y.; Wang, G.; Gu, X. A cluster-based routing protocol for wireless sensor networks with nonuniform node distribution. AEU-Int. J. Electron. Commun. 2012, 66, 54–61. [Google Scholar] [CrossRef]
- Jain, A.; Reddy, B. Sink as Cluster head: An energy efficient clustering method for wireless sensor networks. In Proceedings of the 2014 International Conference on Data Mining and Intelligent Computing (ICDMIC), New Delhi, India, 5–6 September 2014; pp. 1–6. [Google Scholar]
- Karmaker, A.; Hasan, M.M.; Moni, S.S.; Alam, M.S. An efficient cluster head selection strategy for provisioning fairness in wireless sensor networks. In Proceedings of the 2016 IEEE International WIE Conference on Electrical and Computer Engineering (WIECON-ECE), Pune, India, 19–21 December 2016; pp. 217–220. [Google Scholar]
- Bajaber, F.; Awan, I. Adaptive decentralized re-clustering protocol for wireless sensor networks. J. Comput. Syst. Sci. 2011, 77, 282–292. [Google Scholar] [CrossRef]
- Batra, P.K.; Kant, K. LEACH-MAC: A new cluster head selection algorithm for Wireless Sensor Networks. Wirel. Netw. 2016, 22, 49. [Google Scholar] [CrossRef]
- Gharajeh, M.S. Avoidance of the energy hole in wireless sensor networks using a layered-based routing tree. Int. J. Syst. Control. Commun. 2016, 7, 116–131. [Google Scholar]
- Banerjee, R.; Bhattacharyya, C.K. Energy efficient routing and bypassing energy-hole through mobile sink in WSN. In Proceedings of the 2014 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 3–5 January 2014; pp. 1–6. [Google Scholar]
- Yetgin, H.; Cheung, K.T.K.; El-Hajjar, M.; Hanzo, L.H. A Survey of Network Lifetime Maximization Techniques in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2017, 19, 828–854. [Google Scholar] [CrossRef]
- Wang, N.; Zhou, Y.; Xiang, W. An Energy Efficient Clustering Protocol for Lifetime Maximization in Wireless Sensor Networks. In Proceedings of the Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Zanjireh, M.M.; Larijani, H. A survey on centralised and distributed clustering routing algorithms for WSNs. In Proceedings of the 2015 IEEE Vehicular Technology Conference (VTC Spring), Glasgow, UK, 11–14 May 2015; pp. 1–6. [Google Scholar]
- Karmaker, A.; Alam, M.S.; Hasan, M.M.; Craig, A. An energy-efficient and balanced clustering approach for improving throughput of wireless sensor networks. Int. J. Commun. Syst. 2017. [Google Scholar] [CrossRef]
- Peixoto, J.P.J.; Costa, D.G. Wireless visual sensor networks for smart city applications: A relevance-based approach for multiple sinks mobility. Future Gener. Comput. Syst. 2017, 76, 51–62. [Google Scholar] [CrossRef]
- Yarinezhad, R.; Sarabi, A. Reducing delay and energy consumption in wireless sensor networks by making virtual grid infrastructure and using mobile sink. AEU-Int. J. Electron. Commun. 2018, 84, 144–152. [Google Scholar] [CrossRef]
- Toor, A.S.; Jain, A. Energy Aware Cluster Based Multi-hop Energy Efficient Routing Protocol using Multiple Mobile Nodes (MEACBM) in Wireless Sensor Networks. AEU-Int. J. Electron. Commun. 2019, 102, 41–53. [Google Scholar] [CrossRef]
- Lindsey, S.; Raghavendra, C.S. PEGASIS: Power-efficient gathering in sensor information systems. In Proceedings of the Aerospace Conference Proceedings, Big Sky, MT, USA, 9–16 March 2002; Volume 3, p. 3. [Google Scholar]
- Rani, S.; Malhotra, J.; Talwar, R. Energy efficient chain based cooperative routing protocol for WSN. Appl. Soft Comput. 2015, 35, 386–397. [Google Scholar] [CrossRef]
- Jung, S.M.; Han, Y.J.; Chung, T.M. The concentric clustering scheme for efficient energy consumption in the PEGASIS. In Proceedings of the 9th International Conference on Advanced Communication Technology, Okamoto, Japan, 12–14 February 2007; Volume 1, pp. 260–265. [Google Scholar]
- Jabbar, S.; Minhas, A.A.; Paul, A.; Rho, S. Multilayer cluster designing algorithm for lifetime improvement of wireless sensor networks. J. Supercomput. 2014, 70, 104–132. [Google Scholar] [CrossRef]
- Prabha, K.L.; Selvan, S. Energy Efficient Energy Hole Repelling (EEEHR) Algorithm for Delay Tolerant Wireless Sensor Network. Wirel. Pers. Commun. 2018, 101, 1395–1409. [Google Scholar] [CrossRef]
- Baniata, M.; Heo, M.; Lee, J.; Park, J.W.; Hong, J. Energy-efficient unequal chain length clustering for WSN. In Proceedings of the 33rd Annual ACM Symposium on Applied Computing, Pau, France, 9–13 April 2018; pp. 2125–2131. [Google Scholar]
- Elkamel, R.; Messouadi, A.; Cherif, A. Extending the lifetime of wireless sensor networks through mitigating the hot spot problem. J. Parallel Distrib. Comput. 2019, 133, 159–169. [Google Scholar] [CrossRef]
- Wang, Z.; Qin, X.; Liu, B. An energy-efficient clustering routing algorithm for WSN-assisted IoT. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Zhao, X.; Xiong, X.; Sun, Z.; Zhang, X.; Sun, Z. An immune clone selection based power control strategy for alleviating energy hole problems in wireless sensor networks. J. Ambient. Intell. Humaniz. Comput. 2019, 1–14. [Google Scholar] [CrossRef]
- Mohemed, R.E.; Saleh, A.I.; Abdelrazzak, M.; Samra, A.S. Energy-efficient routing protocols for solving energy hole problem in wireless sensor networks. Comput. Netw. 2017, 114, 51–66. [Google Scholar] [CrossRef]
- Naranjo, P.G.V.; Shojafar, M.; Mostafaei, H.; Pooranian, Z.; Baccarelli, E. P-SEP: A prolong stable election routing algorithm for energy-limited heterogeneous fog-supported wireless sensor networks. J. Supercomput. 2017, 73, 733–755. [Google Scholar] [CrossRef]
- Hasan, M.; Karmaker, A.; Alam, M.S.; Craig, A. Minimizing the Adverse Effects of Asymmetric Links: A Novel Cooperative Asynchronous MAC Protocol for Wireless Sensor Networks. Sensors 2019, 19, 2402. [Google Scholar] [CrossRef]
- Hasan, M.M.; Karmaker, A.; Moni, S.S.; Alam, M.S. COASYM-MAC: A Cooperative Asymmetric MAC Protocol for Wireless Sensor Network. In Proceedings of the 2016 9th International Conference on Electrical and Computer Engineering (ICECE), Dhaka, Bangladesh, 20–22 December 2016; pp. 558–561. [Google Scholar]
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 7 January 2000. [Google Scholar]
- Gupta, G.P.; Misra, M.; Garg, K. Multiple mobile agents based data dissemination protocol for wireless sensor networks. In Proceedings of the International Conference on Computer Science and Information Technology, Hong Kong, China, 29–30 December 2012; pp. 334–345. [Google Scholar]
- Yu, Y.C.; Wei, G. An improved PEGASIS algorithm in wireless sensor network. Acta Electron. Sin. 2008, 36, 1309–1313. [Google Scholar]
- Chen, K.H.; Huang, J.M.; Hsiao, C.C. CHIRON: An energy-efficient chain-based hierarchical routing protocol in wireless sensor networks. In Proceedings of the Wireless Telecommunications Symposium, Prague, Czech Republic, 22–24 April 2009; pp. 1–5. [Google Scholar]
- MathWorks—Makers of MATLAB and Simulink. Available online: https://www.mathworks.com (accessed on 3 October 2019).
- Liu, X.; Wu, J. A Method for Energy Balance and Data Transmission Optimal Routing in Wireless Sensor Networks. Sensors 2019, 19, 3017. [Google Scholar] [CrossRef]
- Behera, T.M.; Mohapatra, S.K.; Samal, U.C.; Khan, M.S.; Daneshmand, M.; Gandomi, A.H. Residual Energy Based Cluster-head Selection in WSNs for IoT Application. IEEE Internet Things J. 2019. [Google Scholar] [CrossRef]
- Anzola, J.; Pascual, J.; Tarazona, G.; González Crespo, R. A Clustering WSN Routing Protocol Based on kd Tree Algorithm. Sensors 2018, 18, 2899. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Y.; Liu, M.; Liu, Q. An energy-balanced clustering protocol based on an improved CFSFDP algorithm for wireless sensor networks. Sensors 2018, 18, 881. [Google Scholar] [CrossRef] [PubMed]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).