Enhanced Multicast Repair Fast Reroute Mechanism for Smart Sensors IoT and Network Infrastructure
Abstract
1. Introduction
2. The Fast ReRoute
2.1. The Principle of Fast ReRoute
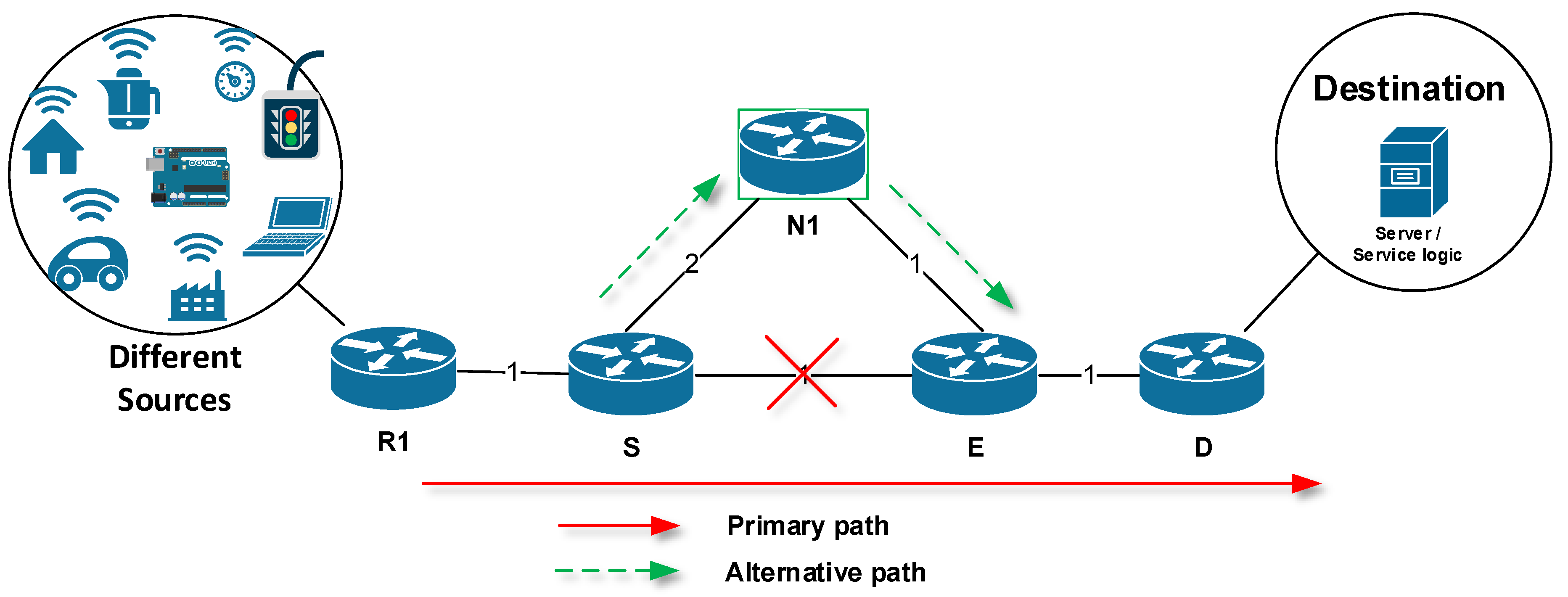
- Phase One: Detection of a link failure by the specialized FRR technology. This phase activates the FRR mechanism. In the Figure 1, the Fast ReRoute process starts after a failure of the link between routers S and E has been detected. Here, following the terminology, the router S detects a link failure.
- Phase Two: Temporary modification of affected routing records by the FRR mechanism. During this phase, precalculated alternative routes are being installed (the FRR mechanism is active).
- Phase Three: Performing background routing protocol update. Routes installed using the FRR mechanism are used to route packets until the network convergence is completed (the FRR mechanism is active).
- Phase Four: The routing protocol completes the necessary routing information update. As the next step, the FRR mechanism is deactivated and the routing process is taken over by the routing protocol.
2.2. Precomputation Approach of Fast ReRoute
3. Related Works
3.1. Problem Formulation
3.1.1. Cost-Based Calculation of Alternative Route
3.1.2. Single Failure Recovery
3.1.3. Dependency on Link-State Routing Protocols
3.1.4. Packet Modification
- Modifying special bits in the IPv4 header (MRC [11]);
3.1.5. Preparatory Calculations
4. M-REP FRR Mechanism
4.1. Description of the Original M-REP Mechanism
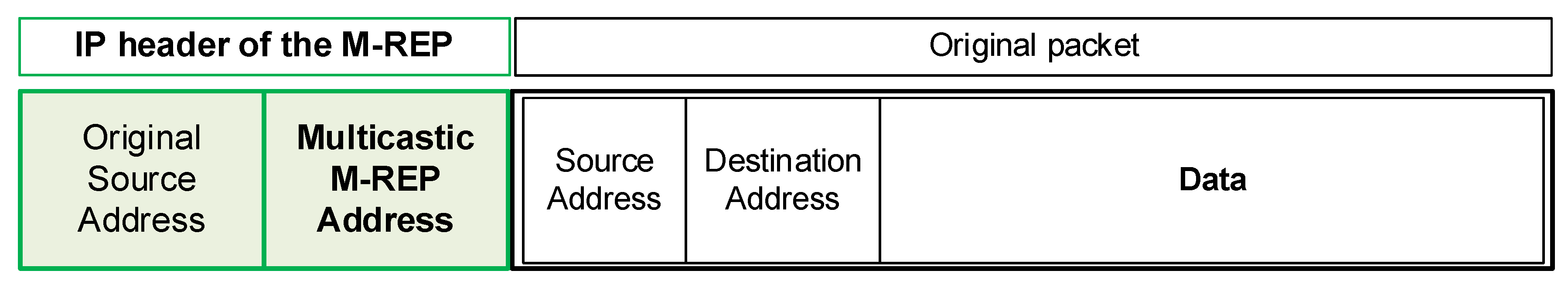
- S router (source router) is a router that has detected a connection failure with its primary next-hop for a specific destination host. Router S begins to encapsulate the original unicast protected flow (or the protected flow, see Table 2) into packets of a specific multicast (S, G) flow. Here, the S address is the original address of the host, that sends packets. G is a specific, pre-configured multicast group address, that is used by the M-REP IPFRR to encapsulate packets of the protected flow. Router S becomes the root of the tree created by the M-REP mechanism.
- D router is a router that performs M-REP IPFRR multicast flow recovery back to the original unicast packets of the protected flow. Router D will further route and forward packets to the destination host as unicast. The destination host, i.e., the target for the original protected flow, must be directly connected or reachable through the D router.
- R router is a router with implemented IPFRR M-REP mechanism.
4.2. M-REP State Machine
5. Enhancements for M-REP
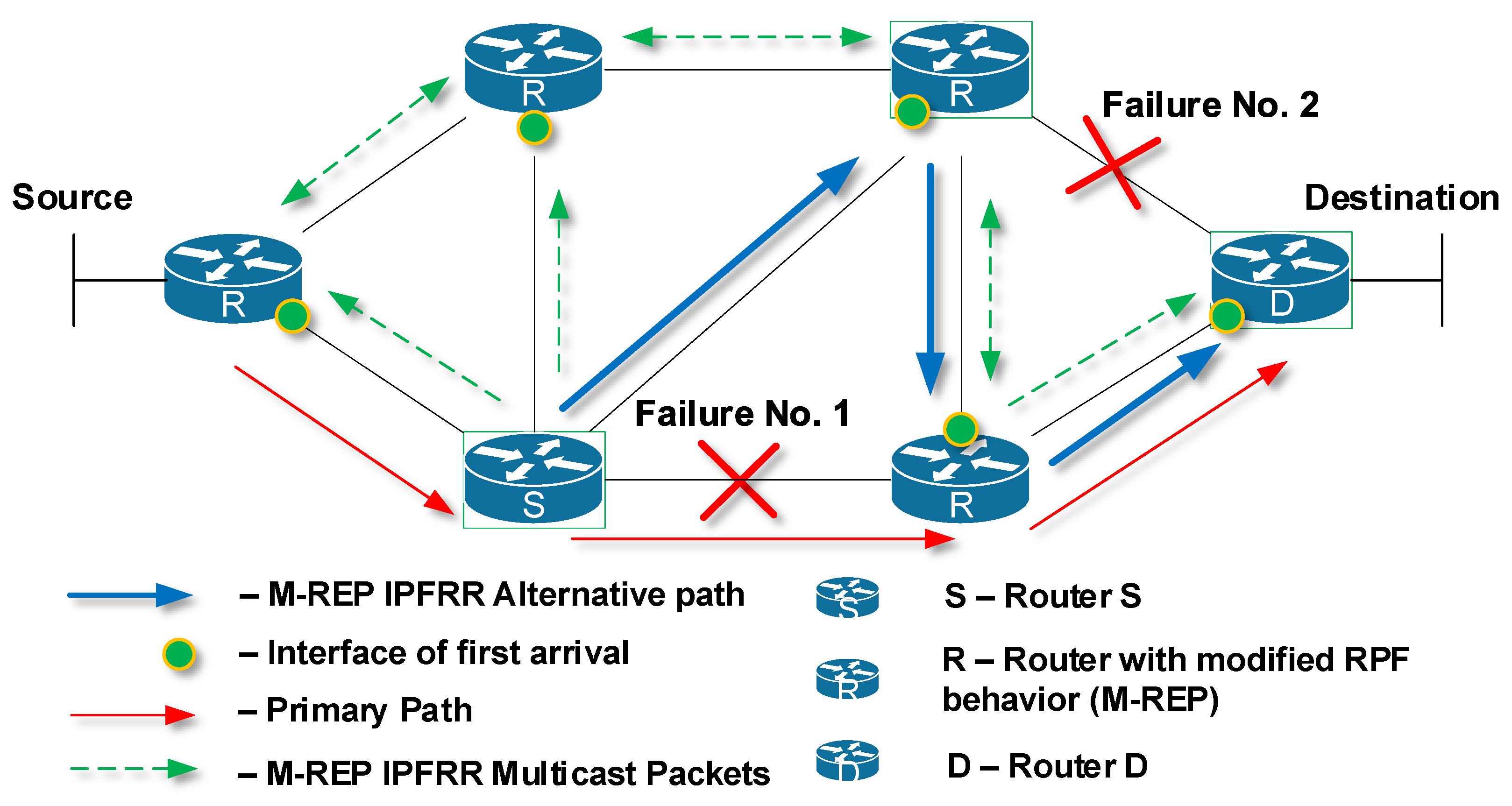
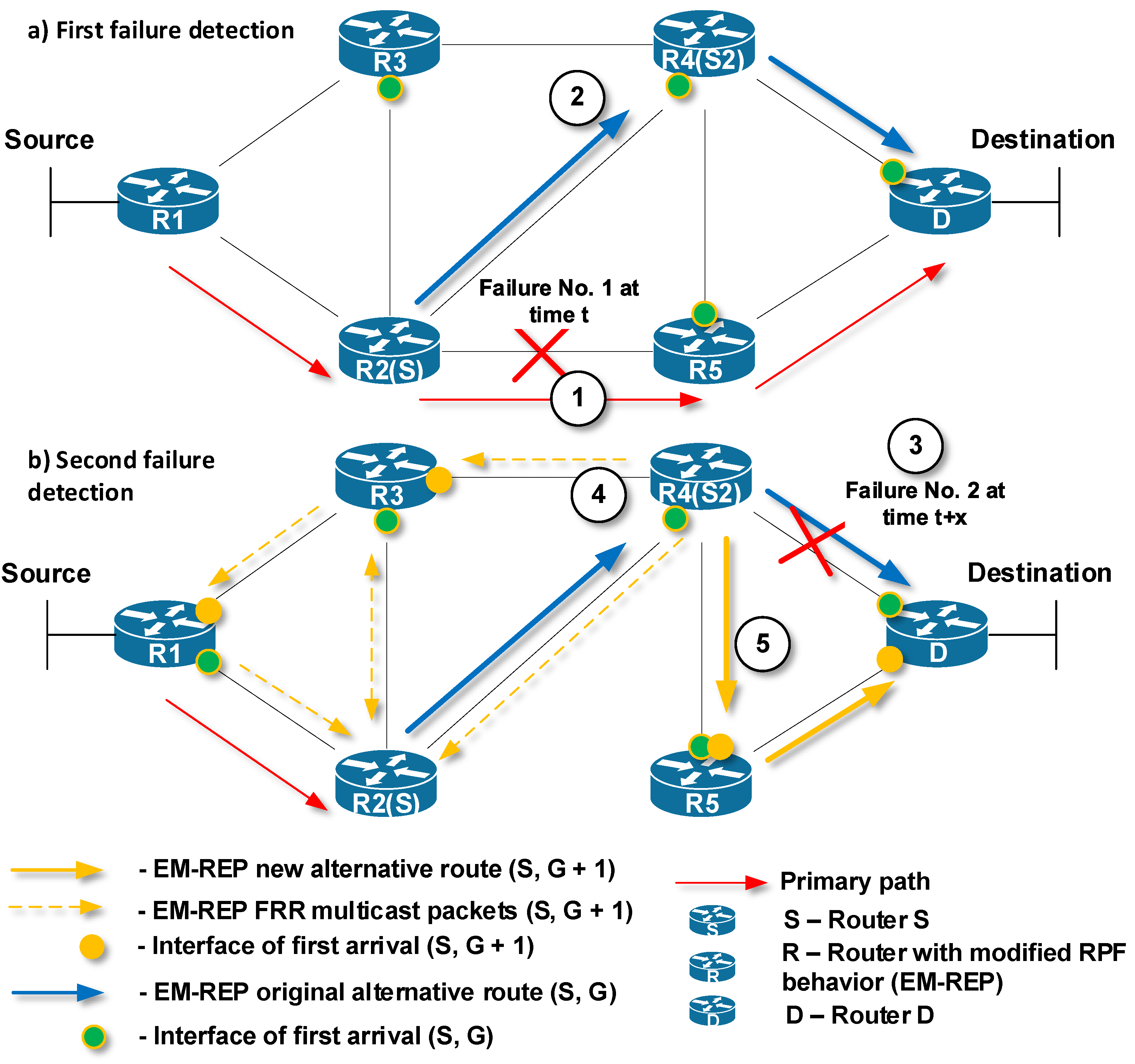
5.1. Multiple Failures
- Push is defined as the encapsulation of an M-REP packet;
- Swap is defined as the replacement of a multicast M-REP address by another one;
- Pop is defined as the decapsulation of M-REP packets, i.e., the decapsulation of original unicast flow from the multicast M-REP packets.
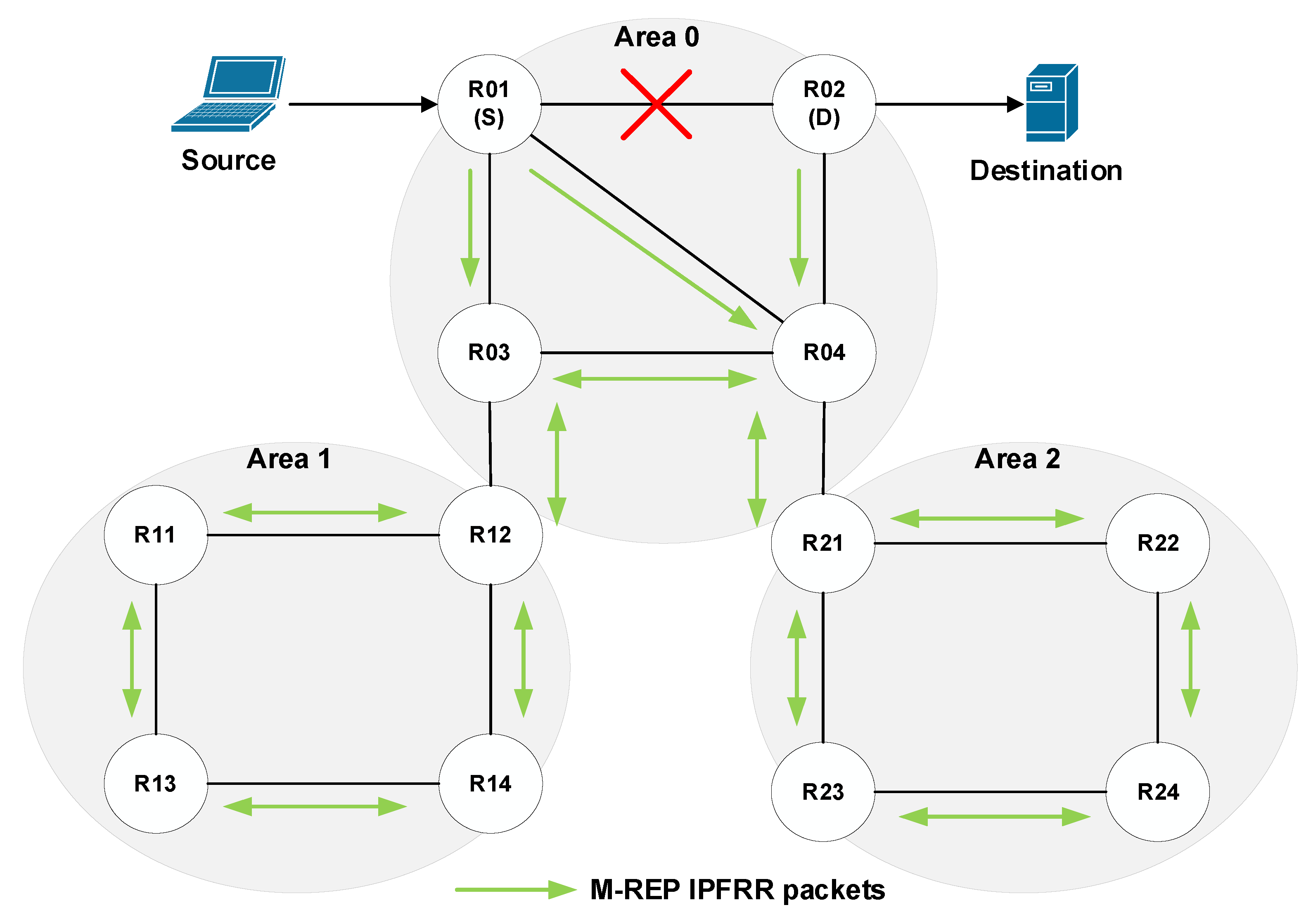
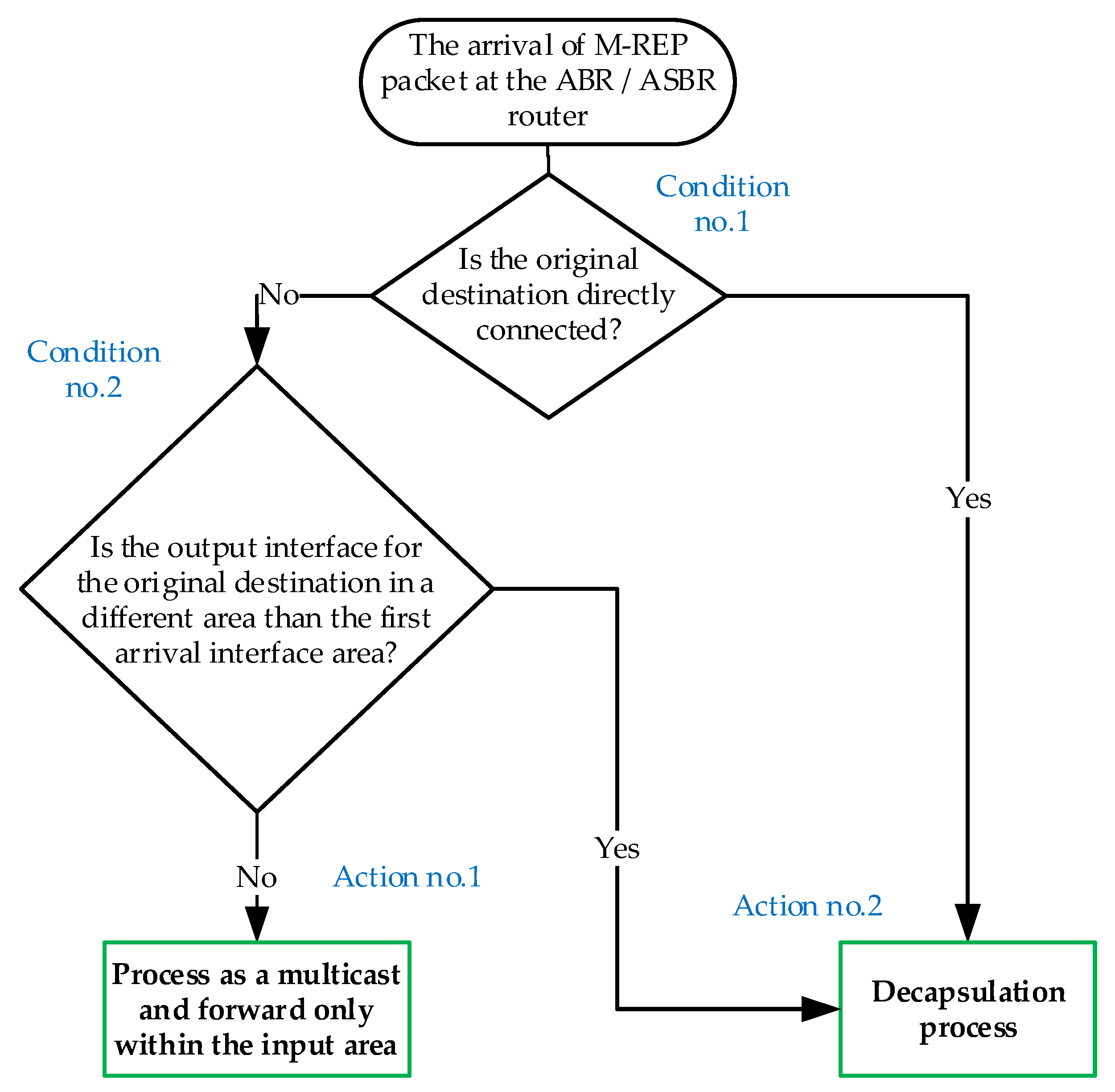
5.2. ABR Extension
5.3. Manual Configuration of Router D
6. Evaluation of the EM-REP Proposal
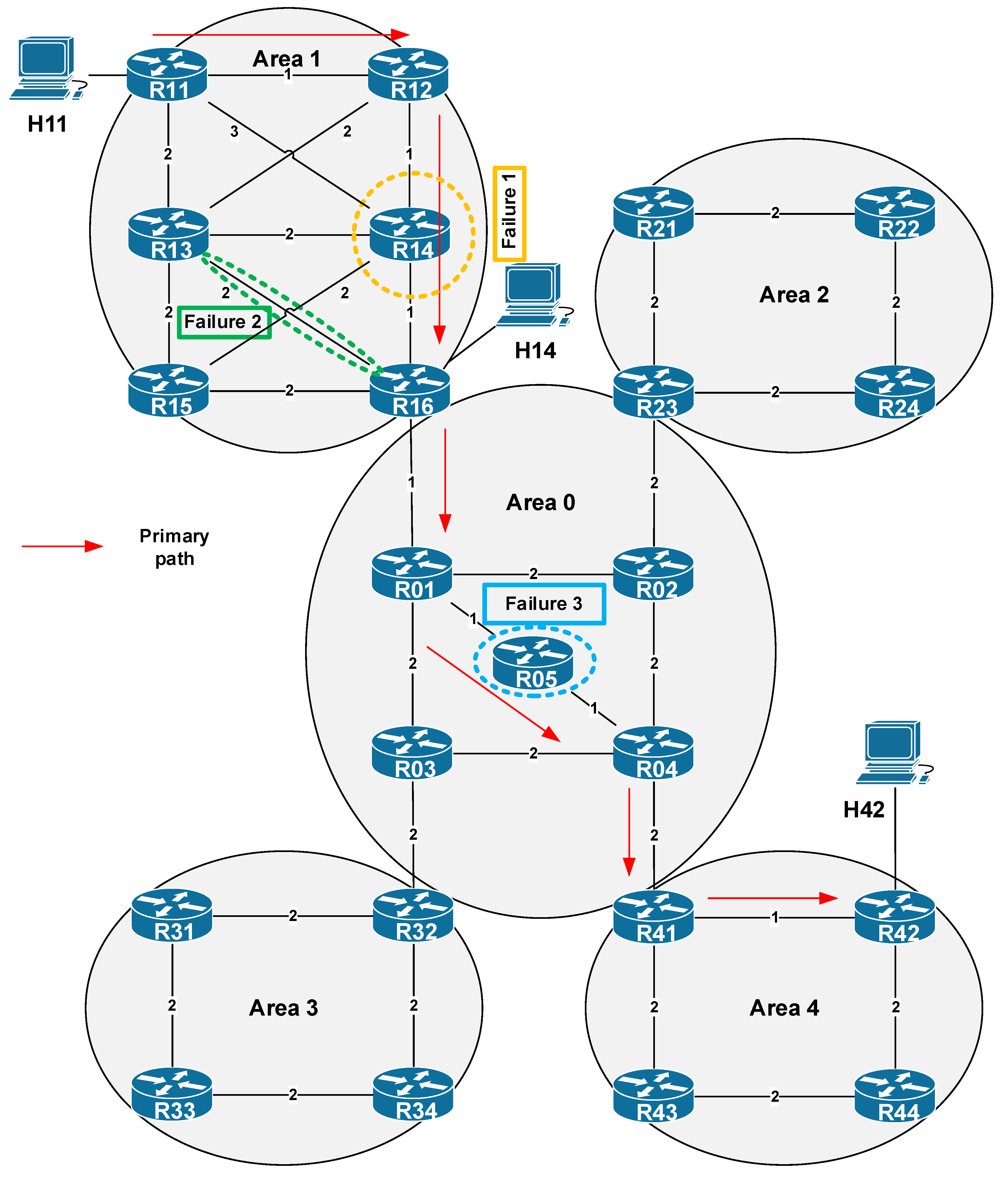
6.1. Simulation Process: Algorithm Behavior
6.2. Evaluation of the EM-REP Mechanism
6.3. Time of Repair: Algorithm Speed
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kvist, F.; Urke, A.R.; Øvsthus, K. Energy efficient determinism in WSN through reverse packet elimination. Sensors 2020, 20, 2890. [Google Scholar] [CrossRef] [PubMed]
- Moreno, J.; Matamoros, O.M.; Reyes, I.L.; Tejeida-Padilla, R.; Hernández, L.C.; Durán, J.P.F.P. Energy-efficient industrial internet of things software-defined network by means of the peano fractal. Sensors 2020, 20, 2855. [Google Scholar] [CrossRef] [PubMed]
- Guerrero-Sanchez, A.E.; Rivas-Araiza, E.A.; Gonzalez-Cordoba, J.L.; Toledano-Ayala, M.; Takacs, A. Blockchain mechanism and symmetric encryption in a wireless sensor network. Sensors 2020, 20, 2798. [Google Scholar] [CrossRef] [PubMed]
- Fathallah, K.; Abid, M.A.; Ben Hadj-Alouane, N. Enhancing energy saving in smart farming through aggregation and partition aware IOT routing protocol. Sensors 2020, 20, 2760. [Google Scholar] [CrossRef]
- Haseeb, K.; Almogren, A.; Din, I.U.; Islam, N.; Altameem, A. SASC: Secure and authentication-based sensor cloud architecture for intelligent internet of things. Sensors 2020, 20, 2468. [Google Scholar] [CrossRef]
- Lihakanga, R.; Ding, Y.; Medero, G.M.; Chapman, S.; Goussetis, G. A high-resolution open source platform for building envelope thermal performance assessment using a wireless sensor network. Sensors 2020, 20, 1755. [Google Scholar] [CrossRef]
- Petija, R.; Michalko, M.; Jakab, F.; Feciľak, P. Convergence of routing protocols in real and simulated environments. In Proceedings of the 2018 16th International Conference on Emerging eLearning Technologies and Applications (ICETA), Stary Smokovec, Slovakia, 15–16 November 2018; pp. 425–430. [Google Scholar]
- Harada, Y.; Hui, W.; Fukushima, Y.; Yokohira, T. A reroute method to recover fast from network failure. In Proceedings of the 2014 International Conference on Information and Communication Technology Convergence (ICTC), Busan, Korea, 22–24 October 2014; pp. 903–908. [Google Scholar]
- Cheng, Z.; Zhang, X.; Li, Y.; Yu, S.; Lin, R.; He, L. Congestion-aware local reroute for fast failure recovery in software-defined networks. J. Opt. Commun. Netw. 2017, 9, 934. [Google Scholar] [CrossRef]
- Antonakopoulos, S.; Bejerano, Y.; Koppol, P. A simple IP fast reroute scheme for full coverage. In Proceedings of the 2012 IEEE 13th International Conference on High Performance Switching and Routing, Belgrade, Serbia, 24 June 2012; pp. 15–22. [Google Scholar]
- Csikor, L.; Rétvari, G. IP fast reroute with remote Loop-Free Alternates: The unit link cost case. In Proceedings of the 2012 IV International Congress on Ultra Modern Telecommunications and Control Systems, St. Petersburg, Russia, 3–5 October 2012; pp. 663–669. [Google Scholar] [CrossRef]
- Yeremenko, O.; Yeremenko, O.; Hailan, A. Two-level method of fast ReRouting in software-defined networks. In Proceedings of the 2017 4th International Scientific-Practical Conference Problems of Infocommunications, Kharkiv, Ukraine, 10–13 October 2017; pp. 376–379. [Google Scholar]
- Robertson, G.; Roy, N.; Penumarthi, P.K.; Nelakuditi, S.; O’Kane, J.M. Loop-free convergence with unordered updates. IEEE Trans. Netw. Serv. Manag. 2017, 14, 373–385. [Google Scholar] [CrossRef]
- Malik, S.U.R.; Srinivasan, S.; Khan, S. Convergence time analysis of open shortest path first routing protocol in internet scale networks. Electron. Lett. 2012, 48, 1188. [Google Scholar] [CrossRef]
- Pal, V.K.; Ramteke, S.M. A framework for fast IP rerouting. In Proceedings of the International Conference on Information Communication and Embedded Systems (ICICES2014), Chennai, India, 27–28 February 2014; pp. 1–6. [Google Scholar]
- Muthumanikandan, V.; Valliyammai, C.; Harish, S. Link failure detection and alternate path tracing in openflow based Ethernet networks. In Proceedings of the 2017 Ninth International Conference on Advanced Computing (ICoAC), Chennai, India, 14–16 December 2017; pp. 352–356. [Google Scholar]
- Gjoka, M.; Ram, V.; Yang, X. Evaluation of IP fast reroute proposals. In Proceedings of the 2007 2nd International Conference on Communication Systems Software and Middleware, Bangalore, India, 7–12 January 2007; pp. 1–8. [Google Scholar]
- Krishnan, Y.N.; Shobha, G. Performance analysis of OSPF and EIGRP routing protocols for greener internetworking. In Proceedings of the 2013 International Conference on Green High Performance Computing (ICGHPC), Nagercoil, India, 14 March 2013; pp. 1–4. [Google Scholar]
- Thorenoor, S.G. Dynamic routing protocol implementation decision between EIGRP, OSPF and RIP based on technical background using OPNET modeler. In Proceedings of the 2010 Second International Conference on Computer and Network Technology, ICCNT 2010, Bangkok, Thailand, 23–25 April 2010; pp. 191–195. [Google Scholar]
- Masruroh, S.U.; Fiade, A.; Iman, M.F. Performance evaluation of routing protocol RIPv2, OSPF, EIGRP with BGP. In Proceedings of the 2017 International Conference on Innovative and Creative Information Technology: Computational Intelligence and IoT, ICITech, Salatiga, Indonesia, 2–4 November 2017; pp. 1–7. [Google Scholar]
- Papán, J.; Segec, P.; Moravcik, M.; Kontsek, M.; Mikuš, L.; Uramova, J.; Konstek, M. Overview of IP fast reroute solutions. In Proceedings of the 2018 16th International Conference on Emerging eLearning Technologies and Applications (ICETA), Stary Smokovec, Slovakia, 15–16 November 2018; pp. 417–424. [Google Scholar]
- Elhourani, T.; Gopalan, A.; Ramasubramanian, S. IP fast rerouting for multi-link failures. IEEE/ACM Trans. Netw. 2016, 24, 3014–3025. [Google Scholar] [CrossRef]
- Gopalan, A.; Ramasubramanian, S. IP fast rerouting and disjoint multipath routing with three edge-independent spanning trees. IEEE/ACM Trans. Netw. 2016, 24, 1336–1349. [Google Scholar] [CrossRef]
- Braun, W.; Menth, M. Loop-free alternates with loop detection for fast reroute in software-defined carrier and data center networks. J. Netw. Syst. Manag. 2016, 24, 470–490. [Google Scholar] [CrossRef]
- Elhourani, T.; Gopalan, A.; Ramasubramanian, S. IP fast rerouting for multi-link failures. In Proceedings of the IEEE INFOCOM 2014—IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 2148–2156. [Google Scholar]
- Shand, M.; Bryant, S. IP Fast Reroute Framework; Internet Engineering Task Force (IETF): Wilmington, DE, USA, 2010; ISSN 2070-1721, RFC5714. [Google Scholar]
- Tavernier, W.; Papadimitriou, D.; Colle, D.; Pickavet, M.; Demeester, P. Packet loss reduction during rerouting using network traffic analysis. Telecommun. Syst. 2011, 52, 861–879. [Google Scholar] [CrossRef]
- Fundo, A.; Bashllari, A.; Nace, D.; Shinko, I. A hybrid rerouting scheme. Telecommun. Syst. 2013, 56, 69–78. [Google Scholar] [CrossRef]
- Rak, J.; Pickavet, M.; Trivedi, K.S.; Lopez, J.A.; Koster, A.M.; Sterbenz, J.P.; Cetinkaya, E.; Gomes, T.; Gunkel, M.; Walkowiak, K.; et al. Future research directions in design of reliable communication systems. Telecommun. Syst. 2015, 60, 423–450. [Google Scholar] [CrossRef]
- Csikor, L.; Rétvári, G. On providing fast protection with remote loop-free alternates. Telecommun. Syst. 2015, 60, 485–502. [Google Scholar] [CrossRef]
- Tavernier, W.; Papadimitriou, D.; Colle, D.; Pickavet, M.; Demeester, P. Self-configuring loop-free alternates with high link failure coverage. Telecommun. Syst. 2013, 56, 85–101. [Google Scholar] [CrossRef]
- Tipper, D. Resilient network design: Challenges and future directions. Telecommun. Syst. 2013, 56, 5–16. [Google Scholar] [CrossRef]
- Su, H.-K. A local fast-reroute mechanism for single node or link protection in hop-by-hop routed networks. Comput. Commun. 2012, 35, 970–979. [Google Scholar] [CrossRef]
- Jarry, A. Fast reroute paths algorithms. Telecommun. Syst. 2011, 52, 881–888. [Google Scholar] [CrossRef]
- Nagy, M.; Tapolcai, J.; Rétvári, G. Optimization methods for improving IP-level fast protection for local shared risk groups with loop-free alternates. Telecommun. Syst. 2013, 56, 103–119. [Google Scholar] [CrossRef]
- Kim, M.; Chae, K. DMP: Detouring using multiple paths against jamming attack for ubiquitous networking system. Sensors 2010, 10, 3626–3640. [Google Scholar] [CrossRef] [PubMed]
- Landaluce, H.; Arjona, L.; Perallos, A.; Falcone, F.; Angulo, I.; Muralter, F. A review of IoT sensing applications and challenges using RFID and wireless sensor networks. Sensors 2020, 20, 2495. [Google Scholar] [CrossRef] [PubMed]
- Csikor, L.; Tapolcai, J.; Rétvári, G. Optimizing IGP link costs for improving IP-level resilience with Loop-Free Alternates. Comput. Commun. 2013, 36, 645–655. [Google Scholar] [CrossRef]
- Hegde, S.; Bowers, C.; Gredler, H.; Litkowski, S. Remote-LFA node protection and manageability. RFC Editor 2017. [Google Scholar] [CrossRef]
- Cevher, S.; Ulutas, M.; Hökelek, I. Topology-aware multiple routing configurations for fault tolerant networking. J. Netw. Syst. Manag. 2015, 24, 944–973. [Google Scholar] [CrossRef]
- Cevher, S.; Ulutaş, M.; Altun, S.; Hökelek, I. Multiple routing configurations for fast re-route in software defined networks. In Proceedings of the 2016 24th Signal Processing and Communication Application Conference (SIU), Zonguldak, Turkey, 16–19 May 2016; pp. 993–996. [Google Scholar]
- Cevher, S.; Ulutaş, M.; Hökelek, I. Performance evaluation of multiple routing configurations. In Proceedings of the 2013 21st Signal Processing and Communications Applications Conference (SIU), Haspolat, Turkey, 24–26 April 2013; pp. 1–4. [Google Scholar]
- El-Serafy, M.A.; Elsayed, A.M.; Aly, M.H.; El-Badawy, E.-S.A.; Ghaleb, I.A.; El-Badawy, E.-S. Multiple routing configurations for datacenter disaster recovery applicability and challenges. In Proceedings of the 2014 International Conference on Computer and Communication Engineering, Dwarahat, India, 22–23 February 2014; pp. 146–149. [Google Scholar]
- Limin, Z.; Zheqing, L.; Hui, W.; Peiyu, L.; Xi, C. A new backup topology design method for IP fast recovery. In Proceedings of the 2016 2nd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 14–17 October 2016; pp. 1992–1997. [Google Scholar]
- Menth, M.; Hartmann, M.; Martin, R.; Čičić, T.; Kvalbein, A. Loop-free alternates and not-via addresses: A proper combination for IP fast reroute? Comput. Netw. 2010, 54, 1300–1315. [Google Scholar] [CrossRef]
- Kuang, K.; Wang, S.; Wang, X. Discussion on the combination of loop-free alternates and maximally redundant trees for IP networks fast reroute. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 1131–1136. [Google Scholar]
- Atlas, A.; Bowers, C.; Enyedi, G. An Architecture for IP/LDP Fast Reroute Using Maximally Redundant Trees (MRT-FRR); Internet Engineering Task Force (IETF): Wilmington, DE, USA, 2016; ISSN 2070-1721, RFC7812. [Google Scholar]
- Lemeshko, O.; Kinan, A.; Wahhab, M.A.J.A.; Yeremenko, O. Multicast fast re-route schemes for multiflow case. Exp. Des. Appl. CAD Syst. Microelectron. 2015, 422–424. [Google Scholar] [CrossRef]
- Aman, A.H.M.; Hashim, A.H.A.; Ramli, H.A.M. Mathematical evaluation of context transfer and multicast fast reroute in multicast enabled network mobility management. Int. J. Control Autom. 2017, 10, 207–216. [Google Scholar] [CrossRef]
- Xu, M.; Li, Q.; Pan, L.; Li, Q.; Wang, D. Minimum protection cost tree: A tunnel-based IP fast reroute scheme. Comput. Commun. 2012, 35, 2082–2092. [Google Scholar] [CrossRef]
- Braun, W.; Albert, M.; Eckert, T.; Menth, M. Performance comparison of resilience mechanisms for stateless multicast using BIER. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 230–238. [Google Scholar] [CrossRef]
- Sundarrajan, A.; Ramasubramanian, S. Fast rerouting for IP multicast under single node failures. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013; pp. 2076–2081. [Google Scholar]
- Chaitou, M. A new fast backup method for bidirectional multicast traffic in MPLS networks: Control plane procedures and evaluation by simulations. J. Netw. Syst. Manag. 2016, 25, 210–228. [Google Scholar] [CrossRef]
- Karan, A.; Filsfils, C.; Decraene, B. Multicast-Only Fast Reroute; ISSN 2070-1721, RFC7431. Internet Engineering Task Force (IETF): Wilmington, DE, USA, 2015. [Google Scholar] [CrossRef]
- Eckert, T.; Cauchie, G.; Menth, M. Traffic Engineering for Bit Index Explicit Replication (BIER-TE); Internet-Draft; Internet Engineering Task Force (IETF): Wilmington, DE, USA, 2019. [Google Scholar]
- Papán, J.; Segec, P.; Paluch, P.; Uramova, J.; Moravcik, M. The new Multicast Repair (M-REP) IP fast reroute mechanism. Concurr. Comput. Pr. Exp. 2018. [Google Scholar] [CrossRef]
- Papán, J.; Segec, P.; Drozdova, M.; Mikus, L.; Moravcik, M.; Hrabovsky, J. The IPFRR mechanism inspired by BIER algorithm. In Proceedings of the 2016 International Conference on Emerging eLearning Technologies and Applications (ICETA), High Tatras, Slovakia, 24–25 November 2016; pp. 257–262. [Google Scholar]
- Papán, J.; Segec, P.; Moravcik, M.; Hrabovsky, J.; Mikus, L.; Uramova, J. Existing mechanisms of IP fast reroute. In Proceedings of the 2017 15th International Conference on Emerging eLearning Technologies and Applications (ICETA) 2017, High Tatras, Slovakia, 26–27 October 2017; pp. 1–7. [Google Scholar]
- Papán, J.; Segec, P.; Palúch, P.; Mikuš, Ľ.; Moravcik, M. The Survey of Current IPFRR Mechanisms; Springer: Berlin/Heidelberg, Germany, 2016; Volume 511, pp. 229–240. [Google Scholar]
- Papán, J.; Segec, P.; Palúch, P. Tunnels in IP fast reroute. In Proceedings of the 10th International Conference on Digital Technologies 2014, Zilina, Slovakia, 9–11 July 2014; pp. 270–274. [Google Scholar]
- Papán, J.; Segec, P.; Palúch, P.; Jozef, P. Analysis of existing IP Fast Reroute mechanisms. In Proceedings of the 2015 International Conference on Information and Digital Technologies, Zilina, Slovakia, 7–9 July 2015; pp. 291–297. [Google Scholar]
- Filsfils, C.; Francois, P.; Shand, M.; Decraene, B.; Uttaro, J.; Leymann, N.; Horneffer, M. Loop-Free Alternate (LFA) Applicability in Service Provider (SP) Networks; Internet Engineering Task Force (IETF): Wilmington, DE, USA, 2015; ISSN 2070-1721, RFC6571. [Google Scholar]
- Litkowski, S.; Bashandy, A.; Filsfils, C.; Decraene, B.; Francois, P. Topology Independent Fast Reroute using Segment Routing; Internet-Draft; Internet Engineering Task Force (IETF): Wilmington, DE, USA, 2019. [Google Scholar]
- Rožić, Ć.; Sasaki, G. Cost of loop-free alternates in IP-Over-WDM networks. J. Opt. Commun. Netw. 2015, 7, 368. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, J.; Hao, G. An autonomous connectivity restoration algorithm based on finite state machine for wireless sensor-actor networks. Sensors 2018, 18, 153. [Google Scholar] [CrossRef]
- Wang, L.; Li, Y.; Pan, B.; Wu, Q.; Yin, J.; Xu, L. Network coding for efficient video multicast in device-to-device communications. Sensors 2020, 20, 2254. [Google Scholar] [CrossRef]
- Lin, Z.; Tao, D.; Wang, Z. Dynamic construction scheme for virtualization security service in software-defined networks. Sensors 2017, 17, 920. [Google Scholar] [CrossRef]
- Minoli, D. Multicast routing-dense-mode protocols: PIM DM. In IP Multicast with Applications to IPTV and Mobile DVB-H; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2007; pp. 152–184. [Google Scholar]
- ANSA by Brno University of Technology. Available online: https://ansa.omnetpp.org/ (accessed on 25 October 2019).
- INET Framework—INET Framework. Available online: https://inet.omnetpp.org/ (accessed on 25 October 2019).







| FRR Mechanism | 100% Repair Coverage | Precomputing | Packet Modification | Dependency on Link-State Routing Protocols |
|---|---|---|---|---|
| ECMP FRR | No | Yes | No | No |
| BIER-TE (M) | Yes | Yes | Yes | No |
| Directed LFA | Yes | Yes | Yes | Yes |
| LFA | No | Yes | No | No |
| MoFRR | No | Yes | No | No |
| MPLS-TE FRR | No | Yes | Yes | No |
| MRC | Yes | Yes | Yes | Yes |
| MRT | Yes | Yes | Yes | Yes |
| Not-Via Addresses | Yes | Yes | Yes | Yes |
| Remote LFA | No | Yes | Yes | Yes |
| TI-LFA | Yes | Yes | Yes | Yes |
| Protected Flow | Unicast flow of packets with specified source and destination IP addresses (source, destination). The M-REP protects packets of a secured flow from losses during network failures. The unicast source address specifies a sending host, the unicast destination address specifies the receiving host. |
| M-REP Address | Special reserved multicast address used exclusively by the M-REP mechanism. The address represents a multicast G address of PIM-DM (S, G) pair, that is reserved and preconfigured for each protected flow. Each protected flow has unique G multicast address. |
| M-REP Flow | A multicast (S, G) flow that encapsulates packets of a protected flow in the event of a failure. The S address is the original source IP address of the protected flow. The G address is the multicast M-REP address. Together, they define a multicast distribution (Source, M-REP address) pair. |
| Received Packet | A packet of a protected flow received by a router. The router identifies the packet based on configured IP addresses of a protected flow. |
| Received Multicast Packet | A packet of the M-REP flow received by a router. The packet is identified by its M-REP address destination address. |
| Protected Interface | Router output interface selected according to the unicast routing table used. The interface is used for the routing of a protected flow (destination). |
| Failure of Protected Interface | Loss of connectivity on the protected interface. |
| Reverse-path forwarding (RPF) Interface | A router interface that first receives a multicast packet with the specified destination M-REP address (M-REP address). This interface has a similar role to the RPF interface in the “original” PIM-DM specification. Each router may have at most one RPF interface per M-REP address. |
| Connected Destination | The network that contains the host with a protected flow destination address. The D router is directly connected to this network by one of its interfaces. |
| M-REP Requirements | Point-to-point routers. The original destination of the original unicast communication must be directly connected to router D. |
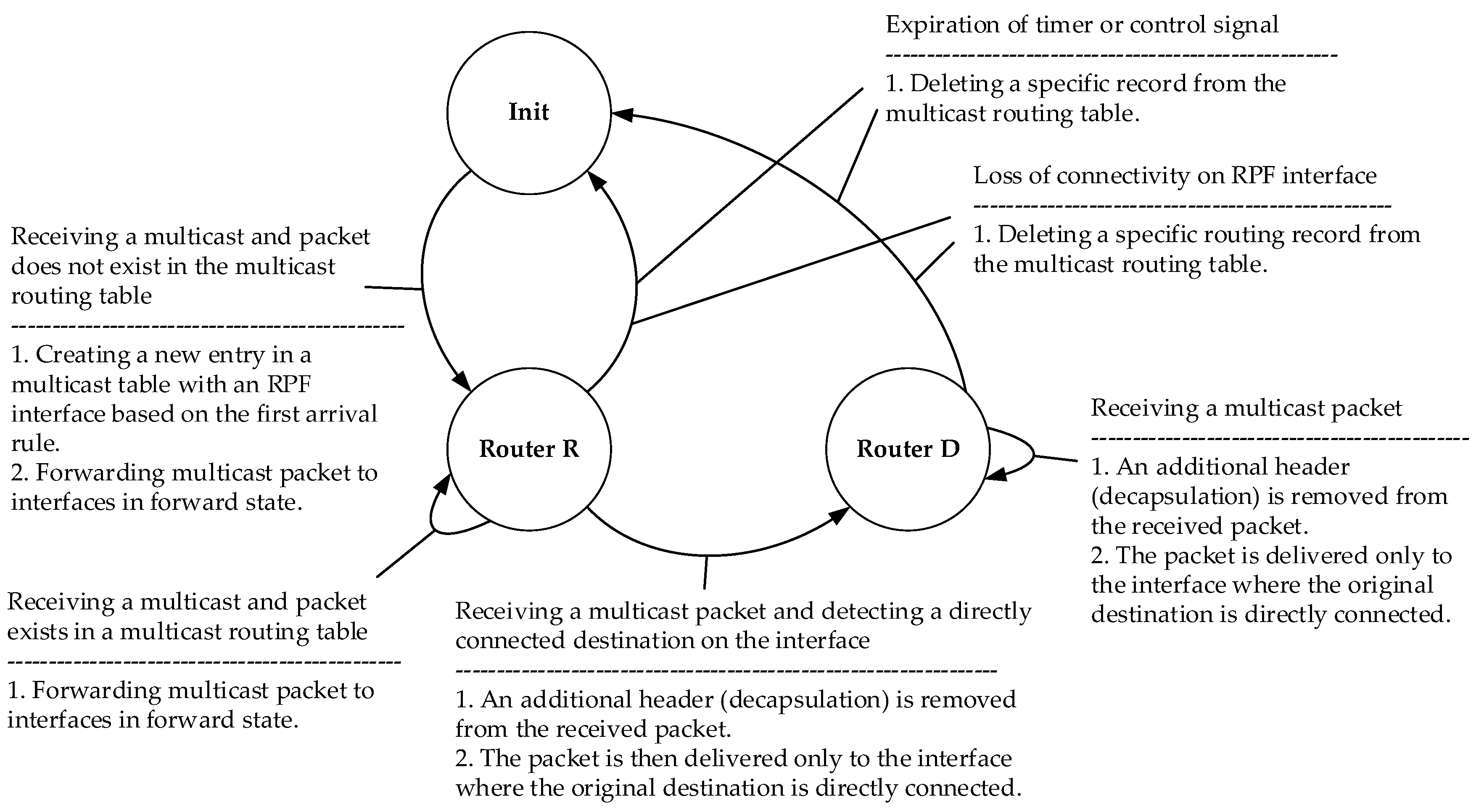
| State: | Any Condition |
| Event: | - |
| New state: | Init |
| Action: | Initializing the M-REP mechanism on the router. The mechanism is initialized only for the first time. After this action, it is in the monitoring mode. |
| State: | Init |
| Event: | Failure of a protected interface |
| New state: | Router S |
| Action: | If the router detects a connectivity failure on the output interface during the processing of protected packet flow (defined by source, destination addresses), it becomes router S. After the failure is detected, all packets within a protected flow are encapsulated with an additional packet header (source, M-REP add). Router S does not have an input RPF interface for the multicast flow, which means that it discards the packet (s) with the destination multicast address (M-REP add). Note: Deactivation of the M-REP mechanism can also be performed using a timer set to a time, which will ensure that the convergence process in the network has completed. In this case, the timer starts when the encapsulation starts. |
| State: | Router S |
| Event: | Recovery of connection on protected interface or control signal or timer. |
| New state: | Init |
| Action: | The router stops encapsulating the protected flow and enters the Init state. |
| State: | Init |
| Event: | Receiving a multicast packet and no entry in the multicast routing table. |
| New state: | Router R |
| Action: | The router has received a packet with the multicast address (M-REP add) and does not have a directly connected destination. If the router does not have an entry in its multicast routing table for (source, M-REP add) pair, it creates a new entry with the RPF interface that has first received the multicast packet. The RPF interface is just one. Interfaces other than RPF and with active PIM-DM, become output interfaces. Received multicast packet is then forwarded to all output interfaces. If the router has a multicast routing table entry for (source, M-REP add) pair and has received a multicast packet on the RPF interface, the packet is forwarded to all PIM-DM output interfaces. If the router has a multicast routing table entry for (source, M-REP add) pair and has received a multicast packet on the NON-RPF interface, the multicast packet is dropped. |
| State: | Router R |
| Event: | Receiving multicast packet and destination is directly connected on an interface. |
| New state: | Router D |
| Action: | The router has received a multicast packet (the multicast address M-REP add is used) and has directly connected destination. Router D is a router that has the original destination directly connected to one of its interfaces. Multicast header is then removed from the received multicast packet, which means that packet is decapsulated and returned to its original state. After decapsulation, the packet is sent out through the interface where the directly connected destination is located. Interfaces other than the RPF interface will send a Prune message. |
| State: | Router R, Router D |
| Event: | Timer expires or control signal |
| New state: | Init |
| Action: | Deletes the entry in the multicast routing table. After this action, mechanism moves to the Init state. |
| State: | Router R, Router D |
| Event: | Loss of connectivity on an RPF interface. |
| New state: | Init |
| Action: | Deletes the entry in the multicast routing table and move to the Init state. |
| Time | Description of Action |
|---|---|
| <200 | Time necessary for the OSPF convergence and stabilization of network processes. |
| 200 | H11 starts the flow |
| 210 | Router R14 failure |
| 212 | Drop of link R13 / R16 |
| 215 | Router R05 failure |
| Time | Source/Destination | Name | Destination Address |
|---|---|---|---|
| 215.00007242 | →R01 | UDPBasicAppData-185 | 192.168.66.2 |
| 215.00008484 | R01 → R02 | UDPBasicAppData-185 | 226.1.1.1 |
| 215.00008484 | R01 → R03 | UDPBasicAppData-185 | 226.1.1.1 |
| 215.00009726 | R02 → R04 | UDPBasicAppData-185 | 226.1.1.1 |
| 215.00009726 | R02 → R23 | UDPBasicAppData-185 | 226.1.1.1 |
| 215.00009726 | R03 → R32 | UDPBasicAppData-185 | 226.1.1.1 |
| 215.00010968 | R04 → R41 | UDPBasicAppData-185 | 226.1.1.1 |
| 215.0001221 | R41 → R42 | UDPBasicAppData-185 | 192.168.66.2 |
| 215.00013452 | R42 → H42 | UDPBasicAppData-185 | 192.168.66.2 |
| Advantages | Disadvantages |
|---|---|
| No pre-computation Suitable for networks of any size Independence of unicast routing protocols in general, but with optimized feature set when using OSPF 100% repair coverage Support of multiple failure repairs at the same time Fix multiple failures at different times (solution presented in Section 5.1) Relatively easy implementation through PIM-DM modification | Does not support multiaccess network segments, i.e., only point-to-point links are supported Random alternative route (hard to predetermine) Packet modification (tunneling) Flooding/pruning process of PIM-DM distribution path |
| Title | 100% Repair Coverage | Precalculations (Precomputing) | Packet Modification | Dependency on Link-State Routing Protocols |
|---|---|---|---|---|
| EM-REP | Yes | No | Yes | No |
| ECMP FRR | No | Yes | No | No |
| BIER-TE (M) | Yes | Yes | Yes | No |
| Directed LFA | Yes | Yes | Yes | Yes |
| LFA | No | Yes | No | No |
| MoFRR | No | Yes | No | No |
| MPLS-TE FRR | No | Yes | Yes | No |
| MRC | Yes | Yes | Yes | Yes |
| MRT | Yes | Yes | Yes | Yes |
| Not-Via Addresses | Yes | Yes | Yes | Yes |
| Remote LFA | No | Yes | Yes | Yes |
| TI-LFA | Yes | Yes | Yes | Yes |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Papan, J.; Segec, P.; Yeremenko, O.; Bridova, I.; Hodon, M. Enhanced Multicast Repair Fast Reroute Mechanism for Smart Sensors IoT and Network Infrastructure. Sensors 2020, 20, 3428. https://doi.org/10.3390/s20123428
Papan J, Segec P, Yeremenko O, Bridova I, Hodon M. Enhanced Multicast Repair Fast Reroute Mechanism for Smart Sensors IoT and Network Infrastructure. Sensors. 2020; 20(12):3428. https://doi.org/10.3390/s20123428
Chicago/Turabian StylePapan, Jozef, Pavel Segec, Oleksandra Yeremenko, Ivana Bridova, and Michal Hodon. 2020. "Enhanced Multicast Repair Fast Reroute Mechanism for Smart Sensors IoT and Network Infrastructure" Sensors 20, no. 12: 3428. https://doi.org/10.3390/s20123428
APA StylePapan, J., Segec, P., Yeremenko, O., Bridova, I., & Hodon, M. (2020). Enhanced Multicast Repair Fast Reroute Mechanism for Smart Sensors IoT and Network Infrastructure. Sensors, 20(12), 3428. https://doi.org/10.3390/s20123428








