Bluetooth Low Energy Mesh Networks: Survey of Communication and Security Protocols
Abstract
:1. Introduction
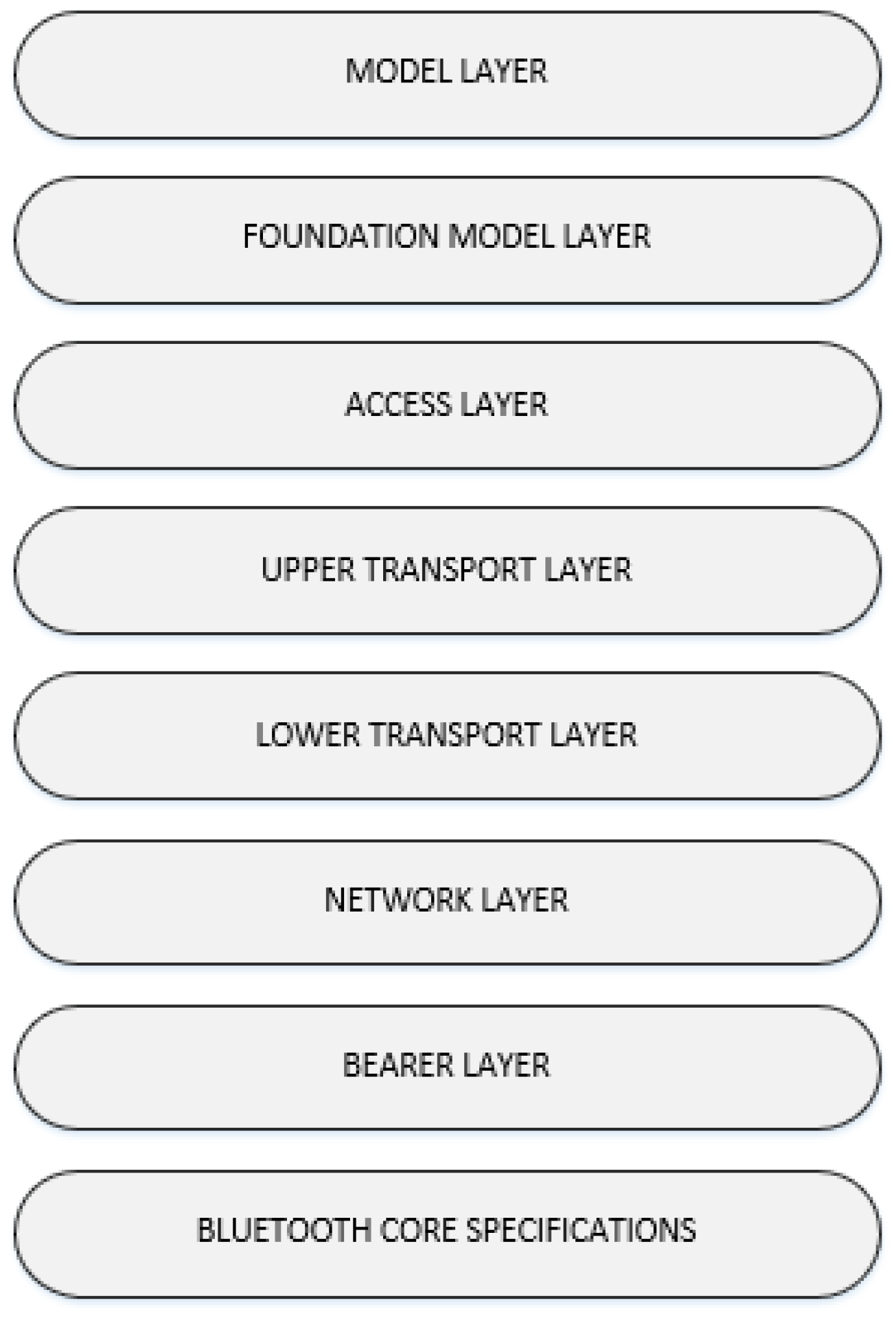
2. BLE Mesh System Architecture
2.1. BLE Network Stack
2.2. BLE Communication Profiles
2.3. BLE Mesh Layers
3. BLE Mesh Communication Protocols
3.1. Message Forwarding Paradigms
3.1.1. Reactive (On-Demand) Protocols
3.1.2. Proactive (Table Driven) Protocols
3.1.3. Cluster-Based Protocols
3.2. BLE Hybrid Mesh Protocols
3.2.1. Connection-Oriented Protocols
3.2.2. Connectionless Protocols
3.2.3. Real-Time Protocols
3.2.4. IPv6 Support
3.3. Heterogeneous BLE Mesh Networks
3.4. Research Direction for BLE Mesh Protocols
4. BLE Mesh Security Issues
4.1. Common WPAN Network Attacks.
4.1.1. Breach of Confidentiality
- Password CrackingThis type of attack can be performed using brute force. It can be performed online as well as offline, but offline attacks are more dangerous, since attackers can conduct password cracking until they succeeded [63].
- Encryption AttacksThese attacks can target different network layers, i.e., physical, network, application layer, etc. In this kind of attack, the malicious node tries to decrypt encrypted data to obtain important information [63].
- Social Engineering AttacksThese attacks take advantage of interpersonal communications, where the attacker obtains important information, such as passwords via the gullibility of the target [63]. This can occur via the impersonation of a legitimate user to force a password reset for the target account. Similarly, passwords written and kept in exposed locations can also invite this kind of attacks.
- Packet SniffingPacket sniffing refers to capturing of network data packets during transit [64]. A packet sniffer is used to execute this attack.
4.1.2. Breach of Integrity/Authentication
- Eavesdropping AttacksEavesdropping attacks can be passive or active. An attacker quietly monitors message transmission and gathers useful information for the desired purpose in passive attacks [62]. In contrast, active attacks occur when fraudulent nodes participate in communications, posing as legitimate nodes to obtain important information for misuse.
- Man in the Middle (MITM) AttacksIn this type of attack, a malicious node inserts itself into the communications channel between two legitimate nodes, while maintaining the facade that they are communicating with each other directly [63]. In the case of BLE, both legitimate GAP central and peripheral nodes will be associated with the impostor node to monitor the messages between the two legitimate nodes.
- Impersonation AttacksThese assaults can be as simple as fake emails authorizing a malicious person as an authorized user to obtain credentials for system access [62].
- Mac Spoofing Attacks
- Replay AttacksA unique, genuine message is retransmitted, or it is delivered late to the destination, influencing the efficiency and operation of the system [62].
- Relay AttacksRelay attack is similar to MITM Attacks. A malevolent node inserts itself into the communications channel between two nodes and forwards copied information to another node for illegitimate use, without the original nodes being aware of the information leak [67].
4.1.3. Breach of Availability
- Physical AttacksPhysical attack refers to breaching of physical security protections, such as theft. It also includes the disruption of wireless communication channels, such as the use of radio frequency jamming attacks. In addition, device cloning, board pin-jacking, and device tampering attacks come under the umbrella of physical attacks [69].
- Battery Exhaustion AttacksWPAN devices are usually battery operated devices that enter sleep mode when inactive. Battery Exhaustion Attacks force continuous fraudulent connection requests to drain the battery and cause the device to become unavailable.
- Denial of Service (DoS) AttacksDoS Attacks occur when an attacker floods the device with continuous connection requests that consume an enormous amount of network bandwidth [70]. DoS occurs when legitimate requests are not serviced due to overload on the device.
- BotnetsBotnets are a collection of malware-compromised Internet-connected devices which enable hackers to take control of the devices [63]. An intruder usually takes advantage of a botnet to instigate the botnet attacks that result in credential and information leaks, unauthorized access, DoS attacks, etc.
4.2. BLE Specific Network Attacks
- Key Negotiation of Bluetooth (KNOB) AttackIn this kind of attack, an attacker without any prior knowledge of any encryption key or link can make two or more victims agree on an encryption key. Hence, an attacker might brute force the encryption key, decrypt ciphertext for eavesdropping, which then enables an attacker to send a message as a legitimate user. Additionally, all Bluetooth versions are susceptible to this attack [76].
- BLE Injection Free AttackThis attack uses MITM attacks as a vector to cause DoS in a BLE network [75].
- Bluejacking AttacksIn this attack, a foe starts an assault by sending unsolicited data to the target user. Successful attacks insert fraudulent contacts into the victim’s address book, similar to how portable phishing and spam attacks function [63].
- BluebuggingBluebugging attack allows for an attacker to access the victim’s cell phone commands and takes over the phone and short message service subsystems [63]. In this attack, the intruder can modify a list of contacts and record phone calls by eavesdropping on the call.
- BluesnarfingIn this assault, an attacker obtains unauthorized access to a Bluetooth enabled device and steals information. This attack not only breaches authentication, confidentiality, availability, but also does not leave any fingerprints for auditing and forensic purposes [67].
- BluebumpThis attack takes advantage of the weak Bluetooth link key-handling protocol, thus allowing an unauthorized device to access services as a legitimate user. Bump attacks can cause data theft and the manipulation of mobile internet connectivity services [67].
- BluedumpBlueDump is an attack where the attacker cause a Bluetooth device to abandon its link key and pair with the attacker’s Bluetooth device instead [67].
- BluemackIt works like the Bluetooth Denial Of Service (DoS) assault, where a Bluetooth-equipped device is compromised via malformed requests from an attacker. The device becomes unresponsive and eventually stops working due to battery exhaustion [67].
- BluechopThe attacker uses an unassociated device to cause an existing slave node to disassociate from the master node to disrupt the operation of the piconet [67].
4.3. Current BLE Vulnerabilities
4.4. Bluetooth Security Enhancements
4.5. Relevance to BLE Mesh Networks
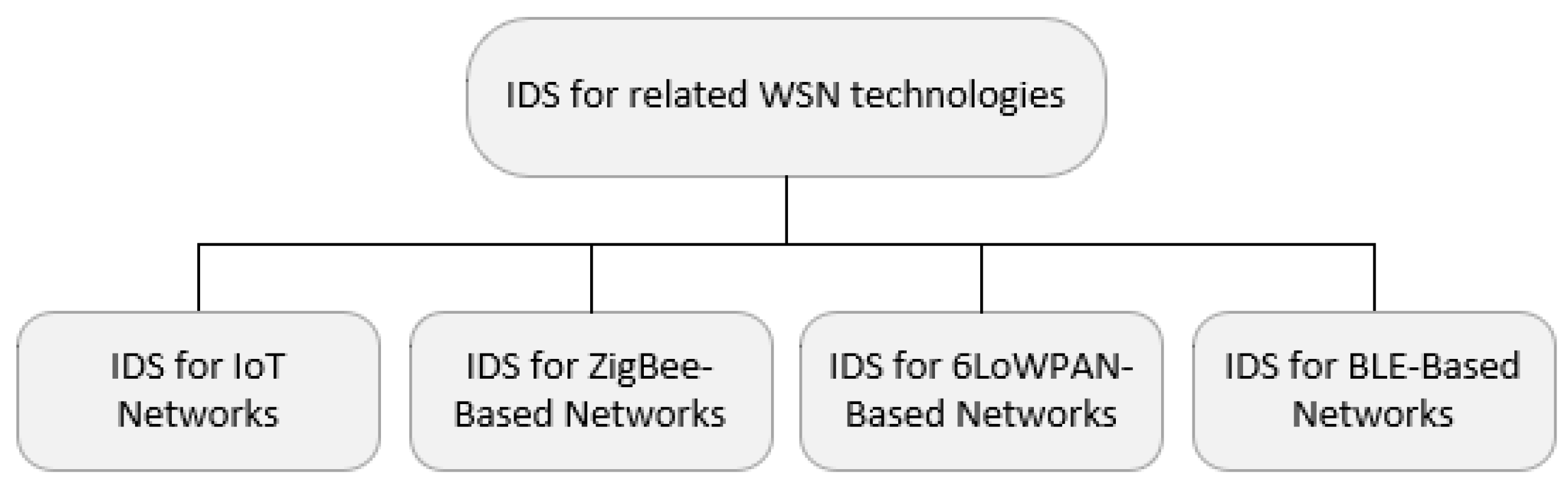
5. IDS for Related WSN Technologies
5.1. IDS for IoT Networks
5.2. IDS for ZigBee-Based Networks
5.3. IDS for 6LoWPAN-Based Networks
5.4. IDS for BLE Networks
5.5. Relevant Approaches for BLE Mesh IDS
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| ABC | Artificial Bee Colony |
| AC | Advertising Channel |
| AFH | Adaptive Frequency Hopping |
| AODV | Ad-hoc On-Demand Distance Vector |
| ARM | Authenticated Rank and routing Metric |
| ATT | Attribute Protocol |
| BATMAN | Better Approach To Mobile Adhoc Networking |
| BES | Best-Effort Scheduling |
| BLE | Bluetooth Low Energy |
| BRIoT | Behavior Rule-based intrusion detection methodology for Internet of Thing |
| BTCP | Bluetooth Topology Construction Protocol |
| CbODRP | Cluster-based On Demand Routing Protocol |
| CBA | Cluster-Based Algorithm |
| CHA-IDS | Compression Header Analyzer Intrusion Detection System |
| CSRK | Connection Signature Resolving Key |
| D-AOMDV | Directional Ad-Hoc On-demand Multipath Distance Vector |
| DC | Data Channel |
| DC-BMN | Data-Channel-based BLE Mesh Networks |
| DL | Damage Level |
| DLM | Deep-Learning Method |
| DoS | Denial of Service |
| DREAM | Distance Routing Effect Algorithm for Mobility |
| DSDV | Destination Sequenced Distance Vector |
| DSR | Dynamic Source Control Routing |
| DT | Device Tree |
| ECDH | Elliptic-curve Diffie–Hellman |
| EE-IDSEP | Energy-Efficient IDS with Energy Prediction |
| E2SR2 | Energy Efficient Secured Ring Routing |
| EE-TS | Energy Efficient Trust System |
| 5FCV | Five-fold Cross Validation |
| FM | FruityMesh |
| FPR | False Positive Rate |
| GAP | Generic Access Profile |
| GATT | Generic Attribute Profile |
| GLRT | Generalized Likelihood Ratio Test |
| HAN | Home Area Networks |
| HCI | Host Control Interface |
| HHT | Hilbert-Huang Transforms |
| HIRO-NET | Heterogeneous Intelligent Robotic Network |
| HMAC | Hash-based Message Authentication Code |
| IDS | Intrusion Detection Systems |
| IETF | Internet Engineering Task Force |
| IIoT | Industrial Internet of Things |
| InBGG | Infinite Bounded Generalized Gaussian |
| InDRES | Intrusion Detection and Response System |
| IoT | Internet of Things |
| 6LoBLE | IPv6 over BLE |
| 6TiSCH | IPv6 over Time-Slotted Channel Hopping |
| IRK | Identity Resolving Key |
| ISFC-BLS | Intelligent and Secured Fuzzy Clustering Algorithm Using Balanced Load Sub-Cluster Formation |
| JW | Just Work |
| KMA | Key-Match Algorithm |
| KNOB | Key Negotiation of Bluetooth |
| k-NN | k-Nearest Neighbor |
| LDoS | Low-rate DoS |
| LESC | Low Energy Secure Connection |
| LL | Link Layer |
| LLP | Low Energy Legacy Pairing |
| L2CAP | Logical Link Control and Adaptation Protocol |
| LTK | Long Term Key |
| MAC | Media Access Control |
| MHTS | Multi-Hop Transfer Service |
| MITM | Man In The Middle |
| ML | Machine Learning |
| MOFCA | Multi-Objective Fuzzy Clustering Algorithm |
| MRT | Multi-Hop Real Time |
| MSV | Message Security Value |
| NC | Numeric Comparison |
| NDN | Named Data Networking |
| NFC | Near Field Communications |
| NFV | Network Function Virtualization |
| NIC | Network Interface Card |
| NOC | Network Operation Centre |
| NN | Neural Network |
| NSQ | Node Security Quantification |
| OLSR | Optimized Link State Routing |
| OOB | Out of Band |
| OS-ELM | Online Sequential-Extreme Learning Machine |
| OSTR | Opportunistic Shortcut Tree Routing |
| PAN | Personal Area Network |
| PCA | Principal Component Analysis |
| PDR | Packet Delivery Ratio |
| PKE | Pass Key Entry |
| PLC | Power Line Communications |
| PUF | Physical Unclonable Function |
| RBF | RSSI-based bounded flooding |
| RFID | Radio-Frequency Identification |
| RPL | Routing Protocol for Low-power and lossy networks |
| SCADA | Supervisory Control And Data Acquisition |
| SDN | Software Defined Network |
| SEECH | Scalable Energy Efficient Clustering Hierarchy |
| SIG | Special Interest Group |
| SLA | Shallow-Learning Approach |
| SM | Security Manager |
| SSP | Secure and Simple Pairing |
| STK | Short Term Key |
| STR | Shortcut Tree Routing |
| SVM | Support Vector Machine |
| TDMA | Time-Division Multiple Access |
| TE | Trust Evaluation |
| TK | Temporary Key |
| TP | Transport Protocol |
| TR | Trickle |
| TTDD | Two-Tier Data Dissemination |
| UUID | Universal Unique Identifier |
| VHF | Very High Frequency |
| WAHN | Wireless Ad-Hoc Network |
| WPAN | Wireless Personal Area Network |
Appendix A. BLE Mesh Networking Concepts
Appendix A.1. Provisioning and Configuration
Appendix A.2. Nodes and Elements
Appendix A.3. BLE Mesh Models
Appendix B. BLE Security Features
Appendix B.1. Low Energy Pairing
Appendix B.1.1. Low Energy Legacy Pairing (LLP)
Appendix B.1.2. Low Energy Secure Connection (LESC)
Appendix B.2. Low Energy Pairing Association Models (LEPAM)
Appendix B.2.1. Out of Band (OOB)
Appendix B.2.2. Pass Key Entry (PKE)
Appendix B.2.3. Just Work (JW)
Appendix B.2.4. Numeric Comparison (NC)
References
- Ghori, M.R.; Wan, T.C.; Sodhy, G.C. Bluetooth Low Energy 5 Mesh Based Hospital Communication Network (B5MBHCN). In Advances in Cyber Security; Springer: Singapore, 2020; Volume 1132, pp. 247–261. [Google Scholar]
- Darroudi, S.M.; Gomez, C. Bluetooth Low Energy Mesh Networks: A Survey. Sensors 2017, 17, 1467. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Gohel, S. Bluetooth Attendance System with Android Application for ERP. In Proceedings of the International Conference on Computing, Power and Communication Technologies (GUCON), Greater Noida, India, 28–29 Septtember 2018; pp. 481–484. [Google Scholar]
- Sthapit, P.; Gang, H.; Pyun, J. Bluetooth Based Indoor Positioning Using Machine Learning Algorithms. In Proceedings of the IEEE International Conference on Consumer Electronics-Asia (ICCE-Asia), Jeju, Korea, 24–26 June 2018; pp. 206–212. [Google Scholar]
- Yumantoro, G.; Kristalina, P.; Sudarsono, A. Performance Evaluation of Indoor Characteristic based on Bluetooth Low Energy Communication System through Statistical Approach. In Proceedings of the International Electronics Symposium on Engineering Technology and Applications (IES-ETA), Bali, Indonesia, 29–30 October 2018; pp. 189–195. [Google Scholar]
- Handojo, A.; Lim, R.; Octavia, T.; Anggita, K. Museum Interactive Information Broadcasting Using Indoor Positioning System and Bluetooth Low Energy: A Pilot Project on Trowulan Museum Indonesia. In Proceedings of the 3rd Technology Innovation Management and Engineering Science International Conference (TIMES-iCON), Bangkok, Thailand, 12–14 December 2018; pp. 1–5. [Google Scholar]
- Sunardy, A.; Surantha, N. Performance Evaluation of Indoor Positioning Algorithm using Bluetooth Low Energy. In Proceedings of the International Conference on Information Technology Systems and Innovation (ICITSI), Bandung, Indonesia, 22–26 October 2018; pp. 503–507. [Google Scholar]
- Mohsin, N.; Payandeh, S.; Ho, D.; Gelinas, J.P. Bluetooth Low Energy Based Activity Tracking of Patient. In Proceedings of the 15th International Conference on Control, Automation, Robotics and Vision (ICARCV), Singapore, 18–21 November 2018; pp. 1991–1996. [Google Scholar]
- Giovanelli, D.; Farella, E.; Fontanelli, D.; Macii, D. Bluetooth-Based Indoor Positioning Through ToF and RSSI Data Fusion. In Proceedings of the International Conference on Indoor Positioning and Indoor Navigation (IPIN), Nantes, France, 24–27 September 2018; pp. 1–8. [Google Scholar]
- Jung, C.; Kim, K.; Seo, J.; Silva, B.; Han, K. Topology Configuration and Multihop Routing Protocol for Bluetooth Low Energy Networks. IEEE Access 2017, 5, 9587–9598. [Google Scholar] [CrossRef]
- Leonardi, L.; Patti, G.; Lo Bello, L. Multi-Hop Real-Time Communications Over Bluetooth Low Energy Industrial Wireless Mesh Networks. IEEE Access 2018, 6, 26505–26519. [Google Scholar] [CrossRef]
- Bluetooth Vulnerabilities. Available online: https://thehackernews.com/2020/02/hacking-bluetooth-vulnerabilities.html (accessed on 20 February 2020).
- Zephyr Projects. Available online: https://docs.zephyrproject.org (accessed on 19 February 2020).
- Townsend, K.; Cufi, C.; Akiba; Davidson, R. Protocol Basics in Getting Started with Bluetooth Low Energy; O’Reilly Media: Sebastopol, CA, USA, 2014; pp. 15–33. Available online: https://www.oreilly.com/library/view/getting-started-with/9781491900550/ (accessed on 18 February 2020).
- Yin, J.; Yang, Z.; Cao, H.; Liu, T.; Zhou, Z.; Wu, C. A Survey on Bluetooth 5.0 and Mesh: New Milestones of IoT. ACM Trans. Sens. Netw. 2019, 15, 1–29. [Google Scholar] [CrossRef]
- Tosi, J.; Taffoni, F.; Santacatterina, M.; Sannino, R.; Formica, D. Performance Evaluation of Bluetooth Low Energy: A Systematic Review. Sensors 2017, 17, 2898. [Google Scholar] [CrossRef] [Green Version]
- Bluetooth. Available online: https://www.bluetooth.com (accessed on 19 February 2020).
- Gomez, C.; Oller, J.; Paradells, J. Overview and Evaluation of Bluetooth Low Energy: An Emerging Low-Power Wireless Technology. Sensors 2012, 12, 11734–11753. [Google Scholar] [CrossRef]
- Zhang, J.; Sun, Z. Assessing multi-hop performance of reactive routing protocols in wireless sensor networks. In Proceedings of the 8th IEEE International Conference on Communication Software and Networks (ICCSN), Beijing, China, 4–6 June 2016; pp. 444–449. [Google Scholar]
- Bhushan, B.; Gupta, S.; Nagpal, C. Comparison of on Demand Routing Protocols. Int. J. Inf. Technol. Comput. Sci. 2013, 5, 61–68. [Google Scholar] [CrossRef]
- Kaur, R.; Kumar, M. A Novel Review on Routing Protocols in MANETs. Undergrad. Acad. Res. J. (UARJ) 2012, 1, 103–108. [Google Scholar]
- Perkins, C.; Das, S. Ad hoc On-Demand Distance Vector (AODV) Routing; Tech., Memo.; University of California: Santa Barbara, CA, USA; University of Cincinnati: Cincinnati, OH, USA, 2003; Available online: https://tools.ietf.org/html/rfc3561 (accessed on 15 March 2020).
- Johnson, D.; Hu, Y. The Dynamic Source Routing Protocol (DSR) for Mobile Ad Hoc Networks for IPv4; Rice University: Houston, TX, USA, 2007; Available online: https://tools.ietf.org/html/rfc4728 (accessed on 15 March 2020).
- Chroboczek, J. The Babel Routing Protocol; University of Paris: Paris, France, 2011; Available online: https://tools.ietf.org/html/rfc6126 (accessed on 15 March 2020).
- Clausen, T.; Jacquet, P. Optimized Link State Routing Protocol (OLSR); Project Hipercom; INRIA: Paris, France, 2003; Available online: https://tools.ietf.org/html/rfc3626 (accessed on 15 March 2020).
- Perkins, C.; Bhagwat, P. Highly Dynamic Destination-Sequenced Distance-Vector Routing (DSDV) for Mobile Computers. ACM SIGCOMM Comput. Commun. Rev. 1999, 24, 234–244. [Google Scholar] [CrossRef]
- Basagni, S. A distance routing effect algorithm for mobility (DREAM). In Proceedings of the 4th Annual ACM/IEEE International Conference on Mobile Computing and Networking, Dallas, TX, USA, October 1998; pp. 76–84. Available online: https://ece.northeastern.edu/fac-ece/basagni/papers/BasagniCSW98.pdf (accessed on 15 March 2020).
- Neumann, A.; Aichele, C.; Lindner, M.; Wunderlich, S. Better Approach To Mobile Ad-hoc Networking; Technische Universität Dresden: Dresden, Germany, 2008. [Google Scholar]
- Jiang, M.; Li, J.; Hu, Y. Cluster Based Routing Protocol (CBRP) Functional Specification; National University of Singapore (NUS): Singapore, 1999. [Google Scholar]
- Luo, H.; Ye, F.; Cheng, J.; Lu, S.; Zhang, L. TTDD: Two-Tier Data Dissemination in Large-Scale Wireless Sensor Networks. Wirel. Netw. 2005, 11, 161–175. [Google Scholar] [CrossRef]
- Tunca, C.; Isik, S.; Donmez, M.Y.; Ersoy, C. Ring Routing: An Energy-Efficient Routing Protocol for Wireless Sensor Networks with a Mobile Sink. IEEE Trans. Mob. Comput. 2015, 14, 1947–1960. [Google Scholar] [CrossRef]
- Bhushan, B.; Sahoo, G. E2SR2: An acknowledgement-based mobile sink routing protocol with rechargeable sensors for wireless sensor networks. Wirel. Netw. 2019, 25, 2697–2721. [Google Scholar] [CrossRef]
- Bhushan, B.; Sahoo, G. ISFC-BLS (Intelligent and Secured Fuzzy Clustering Algorithm Using Balanced Load Sub-Cluster Formation) in WSN Environment. Wirel. Pers. Commun. 2020, 111, 1667–1694. [Google Scholar] [CrossRef]
- Tarhani, M.; Kavian, Y.S.; Siavoshi, S. SEECH: Scalable Energy Efficient Clustering Hierarchy Protocol in Wireless Sensor Networks. IEEE Sens. J. 2014, 14, 3944–3954. [Google Scholar] [CrossRef]
- Sert, S.A.; Bagci, H.; Yazici, A. MOFCA: Multi-objective fuzzy clustering algorithm for wireless sensor networks. Appl. Soft Comput. 2015, 30, 151–165. [Google Scholar] [CrossRef]
- Leon, J.; Duenas, A.; Lano, Y.; Makluf, C.A.; Kemper, G. A Bluetooth Low Energy mesh network auto-configuring Proactive Source Routing protocol. In Proceedings of the IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 8–10 January 2017; pp. 348–349. [Google Scholar]
- Sikora, A.; Krzyszton, M.; Marks, M. Application of Bluetooth low energy protocol for communication in mobile networks. In Proceedings of the International Conference on Military Communications and Information Systems (ICMCIS), Warsaw, Poland, 22–23 May 2018; pp. 1–6. [Google Scholar]
- Garcete, D.A.; Vazquez, L.; Villalba, C. Centralized indoor positioning system using bluetooth low energy. In Proceedings of the XLIV Latin American Computer Conference (CLEI), Sao Paulo, Brazil, 1–5 October 2018; pp. 1–10. [Google Scholar]
- Balogh, A.; Imre, S.; Lendvai, K.; Szabo, S. Service Mediation in multihop Bluetooth Low Energy networks based on NDN approach. In Proceedings of the 23rd International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 16–18 September 2015; pp. 285–289. [Google Scholar]
- Mikhaylov, K.; Tervonen, J. Multihop data transfer service for Bluetooth Low Energy. In Proceedings of the 13th international Conference on ITS Telecommunications (ITST), Tampere, Finland, 5–7 November 2013; pp. 319–324. [Google Scholar]
- Wang, S.; Chiang, K. BLE Tree Networks for Sensor Devices in Internet of Thing. In Proceedings of the DASC, PiCom, DataCom, CyberSciTech, Orlando, FL, USA, 6–10 November 2017; pp. 1304–1309. [Google Scholar]
- Martinez, C.; Eras, L.; Dominguez, F. The Smart Doorbell: A proof-of-concept Implementation of a Bluetooth Mesh Network. In Proceedings of the IEEE Third Ecuador Technical Chapters Meeting (ETCM), Cuenca, Ecuador, 15–19 October 2018; pp. 1–5. [Google Scholar]
- Sirur, S.; Juturu, P.; Gupta, H.P.; Serikar, P.R.; Reddy, Y.K.; Barak, S.; Kim, B. A mesh network for mobile devices using Bluetooth low energy. In Proceedings of the IEEE Sensors, Busan, Korea, 1–4 November 2015. [Google Scholar]
- Guo, Z.; Harris, I.G.; Tsaur, L.; Chen, X. An on-demand scatternet formation and multi-hop routing protocol for BLE-based wireless sensor networks. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; pp. 1590–1595. [Google Scholar]
- Bardoutsos, A.; Filios, G.; Katsidimas, I.; Nikoletseas, S. Energy Efficient Algorithm for Multihop BLE Networks on Resource-Constrained Devices. In Proceedings of the 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini Island, Greece, 29–31 May 2019; pp. 400–407. [Google Scholar]
- Dvinge, R.T.E.; Stalmach, A.; Nalpantidis, L. Connection-Based Bluetooth Mesh Network as a Low Energy Solution for Off-Grid Data Networks. In Proceedings of the 8th International Conference on Modern Circuits and Systems Technologies (MOCAST), Thessaloniki, Greece, 13–15 May 2019; pp. 1–6. [Google Scholar]
- Murillo, Y.; Chiumento, A.; Reynders, B.; Pollin, S. SDN on BLE: Controlling Resource Constrained Mesh Networks. In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar]
- Ng, P.C.; She, J. A Novel Overlay Mesh with Bluetooth Low Energy Network. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; pp. 1–6. [Google Scholar]
- Darroudi, S.M.; Gomez, C. Modeling the Connectivity of Data-Channel-Based Bluetooth Low Energy Mesh Networks. IEEE Commun. Lett. 2018, 22, 2124–2127. [Google Scholar] [CrossRef]
- Murillo, Y.; Reynders, B.; Chiumento, A.; Malik, S.; Crombez, P.; Pollin, S. Bluetooth now or low energy: Should BLE mesh become a flooding or connection oriented network. In Proceedings of the IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–6. [Google Scholar]
- Murillo, Y.; Reynders, B.; Chiumento, A.; Pollin, S. A Multiprotocol Low-Cost Automated Testbed for BLE Mesh. IEEE Commun. Mag. 2019, 57, 76–83. [Google Scholar] [CrossRef]
- Chiumento, A.; Reynders, B.; Murillo, Y.; Pollin, S. Building a connected BLE mesh: A network inference study. In Proceedings of the IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Barcelona, Spain, 15–18 April 2018. [Google Scholar]
- Hansen, E.A.; Nielsen, M.H.; Serup, D.E.; Williams, R.J.; Madsen, T.K.; Abildgren, R. On Relay Selection Approaches in Bluetooth Mesh Networks. In Proceedings of the 10th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Moscow, Russia, 5–9 November 2018; pp. 1–5. [Google Scholar]
- Li, R.; Li, X. Directional Multi-path Routing Algorithm Based on BLE Mesh. In Proceedings of the Cross Strait Quad-Regional Radio Science and Wireless Technology Conference (CSQRWC), Taiyuan, China, 18–21 July 2019; pp. 1–3. [Google Scholar]
- Patti, G.; Leonardi, L.; Lo Bello, L. A Bluetooth Low Energy real-time protocol for Industrial Wireless mesh Networks. In Proceedings of the IECON 2016-42nd Annual Conference of the IEEE Industrial Electronics Society, Florence, Italy, 23–26 October 2016; pp. 4627–4632. [Google Scholar]
- Luo, B.; Sun, Z.; Pang, Y.; Ahmad, A.; Lin, J.; Wu, J.; Zhang, H. Neighbor Discovery for IPv6 over BLEMesh Networks. Appl. Sci. 2020, 10, 1844. [Google Scholar] [CrossRef] [Green Version]
- Darroudi, S.M.; Gomez, C.; Crowcroft, J. Bluetooth Low Energy Mesh Networks: A Standards Perspective. IEEE Commun. Mag. 2020, 30, 1–8. [Google Scholar] [CrossRef]
- Ferranti, L.; D’Oro, S.; Bonati, L.; Demirors, E.; Cuomo, F.; Melodia, T. HIRO-NET: Self-Organized Robotic Mesh Networking for Internet Sharing in Disaster Scenarios. In Proceedings of the 20th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Washington, DC, USA, 10–12 June 2019; pp. 1–9. [Google Scholar]
- Vijay, R.; Prabhakar, T.V.; Hegde, V.; Rao, V.S.; Prasad, R.V. A Heterogeneous PLC with BLE Mesh network for Reliable and Real-time Smart Cargo Monitoring. In Proceedings of the IEEE International Symposium on Power Line Communications and its Applications (ISPLC), Praha, Czech Republic, 3–5 April 2019; pp. 1–6. [Google Scholar]
- Vijay, R.; Singh, H.; Prabhakar, T.V.; Hegde, V.; Shigehalli, P. Air cargo monitoring: A robust tamper detection and reliable communication system. In Proceedings of the SIES, Graz, Austria, 6–8 June 2018. [Google Scholar]
- Garrido-Hidalgo, C.; Hortelano, D.; Roda-Sanchez, L.; Olivares, T.; Ruiz, M.C.; Lopez, V. IoT Heterogeneous Mesh Network Deployment for Human-in-the-Loop Challenges towards a Social and Sustainable Industry 4.0. IEEE Access 2018, 6, 28417–28437. [Google Scholar] [CrossRef]
- Sgora, A.; Vergados, D.D.; Chatzimisios, P. A survey on security and privacy issues in Wireless Mesh Networks. Secur. Commun. Netw. 2013, 9, 1877–1889. [Google Scholar]
- Pammi, A.A. Threats, Countermeasures, and Research Trends for BLE-Based IoT Devices. Master’s Thesis, Arizona State University, Tempe, AZ, USA, 2017. [Google Scholar]
- CIA. Available online: https://devqa.io (accessed on 20 February 2020).
- Mishra, R.; Singh, A.; Kumar, R. VANET Security: Issues, Challenges and Solutions. In Proceedings of the International Conference on Electrical, Electronics, and Optimization Techniques (ICEEOT), Chennai, India, 3–5 March 2016; pp. 1050–1055. [Google Scholar]
- Adomnicai, A.; Fournier, J.A.A.; Masson, A. Hardware Security Threats Against Bluetooth Mesh Networks. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018; pp. 1–9. [Google Scholar]
- Lonzetta, A.M.; Cope, P.; Campbell, J.; Mohd, B.J. Security Vulnerabilities in Bluetooth Technology as Used in IoT. J. Sens. Actuator Netw. 2018, 7, 28. [Google Scholar] [CrossRef] [Green Version]
- Types of Network Attacks. Available online: https://www.omnisecu.com (accessed on 20 February 2020).
- Ghori, M.R.; Wan, T.C.; Anbar, M.; Sodhy, G.C.; Rizwan, A. Review on Security in Bluetooth Low Energy Mesh Network in Correlation with Wireless Mesh Network Security. In Proceedings of the IEEE Student Conference on Research and Development (SCOReD), Bandar Seri Iskandar, Malaysia, 15–17 October 2019; pp. 219–224. [Google Scholar]
- Karimireddy, T.; Bakshi, A. A Hybrid Security Framework for the Vehicular Communications in VANET. In Proceedings of the International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 23–25 March 2016; pp. 1929–1934. [Google Scholar]
- Lai, C.; Li, H.; Liang, X.; Lu, R.; Zhang, K.; Shen, X. CPAL: A Conditional Privacy-Preserving Authentication with Access Linkability for Roaming Service. IEEE IoT J. 2014, 1, 46–57. [Google Scholar] [CrossRef]
- Lai, C.; Lu, R.; Zheng, D.; Li, H.; Shen, X.S. GLARM: Group-Based Lightweight Authentication Scheme for Resource Constrained Machine to Machine Communications. Comput. Netw. 2016, 9, 66–81. [Google Scholar] [CrossRef]
- Chen, D.; Zhang, N.; Qin, Z.; Mao, X.; Qin, Z.; Shen, X.; Li, X.Y. S2M: A Lightweight Acoustic Fingerprints Based Wireless Device Authentication Protocol. IEEE IoT J. 2017, 4, 88–100. [Google Scholar] [CrossRef]
- Chuang, Y.H.; Lo, N.W.; Yang, C.Y.; Tang, S.W. A Lightweight Continuous Authentication Protocol for the Internet of Things. Sensors 2018, 18, 1104. [Google Scholar] [CrossRef] [Green Version]
- Santos, A.C.; Soares Filho, J.L.; Silva, Á.Í.; Nigam, V.; Fonseca, I.E. BLE injection-free attack: A novel attack on bluetooth low energy devices. J. Ambient Intell. Humaniz. Comput. 2019, 20, 1. [Google Scholar] [CrossRef]
- KNOB Attack. Available online: https://knobattack.com/ (accessed on 15 April 2020).
- Yu, X.; Wang, Y. Secure Constructing Bluetooth Scatter net Based on BTCP. In Proceedings of the Fifth International Conference on Information Assurance and Security (IAS), Xi’an, China, 18–20 August 2009; pp. 200–203. [Google Scholar]
- Sadghzadh, S.H.; Shirazani, S.J.R.; Mosleh, M. A new secure scheme purposed for recognition and authentication protocol in Bluetooth environment. In Proceedings of the 12th International Conference on Advanced Communication Technology (ICACT), Phoenix Park, Korea, 7–10 February 2010; pp. 1326–1331. [Google Scholar]
- Xu, G.; Yu, B. Security Enhanced Design of the Bluetooth Simple Pairing Protocol. In Proceedings of the International Conference on Computer Science and Network Technology (ICCSNT), Harbin, China, 24–26 December 2011; pp. 292–296. [Google Scholar]
- Diallo, A.S.; Wajdi, A. A Secure Authentication Scheme for Bluetooth Connection. In Proceedings of the IEEE International Conference on Computer and Communication Engineering (CCET), Kuala Lumpur, Malaysia, 23–25 September 2014; pp. 60–63. [Google Scholar]
- Fan, C.; Shieh, S.; Li, B. On the security of password-based pairing protocol in Bluetooth. In Proceedings of the Asia-Pacific Bluetooth Operations and Management Symposium, Taipei, Taiwan, 21–23 September 2011; pp. 1–4. [Google Scholar]
- Priyanka, S.S.; Nagajayanthi, B. Enhancing Security in Bluetooth Networks. In Proceedings of the ICSEMR, Chennai, India, 27–29 November 2014; pp. 1–3. [Google Scholar]
- Nai, L.W.; Yohan, A. BLE-Based Authentication Protocol for Micropayment Using Wearable Device. Wirel. Pers. Commun. 2020, 112, 2351–2372. [Google Scholar]
- Cha, S.C.; Chen, J.F.; Su, C.; Yeh, K.H. A Blockchain Connected Gateway for BLE-based Devices in the Internet of Things. IEEE Access 2018, 6, 24639–24649. [Google Scholar] [CrossRef]
- Prabavathy, S.; Sundarakantham, K.; Shalinie, S.M. Design of cognitive fog computing for intrusion detection in Internet of Things. J. Commun. Netw. 2018, 20, 291–298. [Google Scholar] [CrossRef]
- Choudhary, S.; Kesswani, N. Detection and Prevention of Routing Attacks in Internet of Things. In Proceedings of the TrustCom/BigDataSE, Newyork, NY, USA, 1–3 August 2018; pp. 1537–1540. [Google Scholar]
- Tian, Q.; Li, J.; Liu, H. A Method for Guaranteeing Wireless Communication Based on a Combination of Deep and Shallow Learning. IEEE Access 2019, 7, 38688–38695. [Google Scholar] [CrossRef]
- Jan, S.U.; Ahmed, S.; Shakhov, V.; Koo, I. Toward a Lightweight Intrusion Detection System for the Internet of Things. IEEE Access 2019, 7, 42450–42471. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Słowińska, M.; Theodorakopoulos, G.; Burnap, P. A Supervised Intrusion Detection System for Smart Home IoT Devices. IEEE Internet Things J. 2019, 6, 9042–9053. [Google Scholar] [CrossRef]
- Zolanvari, M.; Teixeira, M.A.; Gupta, L.; Khan, K.M.; Jain, R. Machine Learning-Based Network Vulnerability Analysis of Industrial Internet of Things. IEEE Internet Things J. 2019, 6, 6822–6834. [Google Scholar] [CrossRef] [Green Version]
- Liang, F.; Hatcher, W.G.; Liao, W.; Gao, W.; Yu, W. Machine Learning for Security and the Internet of Things: The Good, the Bad, and the Ugly. IEEE Access 2019, 7, 158126–158147. [Google Scholar] [CrossRef]
- You, I.; Yim, K.; Sharma, V.; Choudhary, G.; Chen, I.; Cho, J. On IoT Misbehavior Detection in Cyber Physical Systems. In Proceedings of the PRDC, Taipei, Taiwan, 4–7 December 2018; pp. 189–190. [Google Scholar]
- Sharma, V.; You, I.; Yim, K.; Chen, I.; Cho, J. BRIoT: Behavior Rule Specification-Based Misbehavior Detection for IoT-Embedded Cyber-Physical Systems. IEEE Access 2019, 7, 118556–118580. [Google Scholar] [CrossRef]
- Alhakami, W.; ALharbi, A.; Bourouis, S.; Alroobaea, R.; Bouguila, N. Network Anomaly Intrusion Detection Using a Nonparametric Bayesian Approach and Feature Selection. IEEE Access 2019, 7, 52181–52190. [Google Scholar] [CrossRef]
- Arshad, J.; Azad, M.A.; Abdellatif, M.M.; Rehman, M.H.; Salah, K. COLIDE: A Collaborative Intrusion Detection Framework for Internet of Things. IET Netw. 2019, 8, 3–14. [Google Scholar] [CrossRef] [Green Version]
- Abhishek, N.V.; Tandon, A.; Lim, T.J.; Sikdar, B. A GLRT-Based Mechanism for Detecting Relay Misbehavior in Clustered IoT Networks. IEEE Trans. Inf. Forensics Secur. 2020, 15, 435–446. [Google Scholar] [CrossRef]
- Choi, C.; Choi, J. Ontology-Based Security Context Reasoning for Power IoT-Cloud Security Service. IEEE Access 2019, 7, 110510–110517. [Google Scholar] [CrossRef]
- Nguyen, T.G.; Phan, T.V.; Nguyen, B.T.; So-In, C.; Baig, Z.A.; Sanguanpong, S. SeArch: A Collaborative and Intelligent NIDS Architecture for SDN-Based Cloud IoT Networks. IEEE Access 2019, 7, 107678–107694. [Google Scholar] [CrossRef]
- Jokar, P.; Nicanfar, H.; Leung, V.C.M. Specification-based Intrusion Detection for home area networks in smart grids. In Proceedings of the IEEE International Conference on Smart Grid Communications (SmartGridComm), Brussels, Belgium, 17–20 October 2011; pp. 208–213. [Google Scholar]
- Stelte, B.; Rodosek, G.D. Thwarting attacks on ZigBee-Removal of the KillerBee stinger. In Proceedings of the CNSM, Zurich, Switzerland, 14–18 October 2013; pp. 219–226. [Google Scholar]
- Al Baalbaki, B.; Pacheco, J.; Tunc, C.; Hariri, S.; Al-Nashif, Y. Anomaly Behavior Analysis System for ZigBee in smart buildings. In Proceedings of the AICCSA, Marrakech, Morocco, 17–20 November 2015; pp. 1–4. [Google Scholar]
- Maphatsoe, T.; Masinde, M. Asymptotic Analysis of A Fuzzy Based Intrusion Detection System For Zigbee. In Proceedings of the ICONIC, Paline Magnien, Mauritius, 6–7 December 2018; pp. 1–8. [Google Scholar]
- Jokar, P.; Leung, V.C.M. Intrusion Detection and Prevention for ZigBee-Based Home Area Networks in Smart Grids. IEEE Trans. Smart Grid 2018, 9, 1800–1811. [Google Scholar] [CrossRef]
- Jegan, G.; Samundiswary, P. Wormhole Attack Detection in Zigbee Wireless Sensor Networks using Intrusion Detection System. Indian J. Sci. Technol. 2016, 9, 1–10. [Google Scholar] [CrossRef]
- Govindasamy, J.; Punniakodi, S. Energy Efficient Intrusion Detection System for ZigBee based Wireless Sensor Networks. Int. J. Intell. Eng. Syst. 2017, 10, 155–165. [Google Scholar] [CrossRef]
- Chen, T.H.; Meng, C.; Shan, Z.; Fu, Z.; Bhargava, B.K. A Novel Low-Rate Denial of Service Attack Detection Approach in ZigBee Wireless Sensor Network by Combining Hilbert-Huang Transformation and Trust Evaluation. IEEE Access 2019, 7, 32853–32866. [Google Scholar] [CrossRef]
- Kasinathan, P.; Pastrone, C.; Spirito, M.A.; Vinkovits, M. Denial-of-Service detection in 6LoWPAN based Internet of Things. In Proceedings of the WiMob, Lyon, France, 7–9 October 2013; pp. 600–607. [Google Scholar]
- Cervantes, C.; Poplade, D.; Nogueira, M.; Santos, A. Detection of sinkhole attacks for supporting secure routing on 6LoWPAN for Internet of Things. In Proceedings of the IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015. [Google Scholar]
- Surendar, M.; Umamakeswari, A. InDReS: An Intrusion Detection and response system for Internet of Things with 6LoWPAN. In Proceedings of the International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 23–25 March 2016; pp. 1903–1908. [Google Scholar]
- Napiah, M.N.; Idris, M.Y.; Ramli, R.; Ahmedy, I. Compression Header Analyzer Intrusion Detection System (CHA-IDS) for 6LoWPAN Communication Protocol. IEEE Access 2018, 6, 16623–16638. [Google Scholar] [CrossRef]
- Althubaity, A.; Ji, H.; Gong, T.; Nixon, M.; Ammar, R.; Han, S. ARM: A hybrid specification-based intrusion detection system for rank attacks in 6TiSCH networks. In Proceedings of the 22nd IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Limassol, Cyprus, 12–15 September 2017. [Google Scholar]
- Farzaneh, B.; Montazeri, M.A.; Jamali, S. An Anomaly-Based IDS for Detecting Attacks in RPL-Based Internet of Things. In Proceedings of the ICWR, Tehran, Iran, 24–25 April 2019; pp. 61–66. [Google Scholar]
- Ramos, A.; Milfont, R.T.P.; Filho, R.H.; Rodrigues, J.J.P.C. Enabling Online Quantitative Security Analysis in 6LoWPAN Networks. IEEE IoT J. 2019, 6, 5631–5638. [Google Scholar] [CrossRef]
- OConnor, T.; Reeves, D. Bluetooth Network-Based Misuse Detection. In Proceedings of the Annual Computer Security Applications, Anaheim, CA, USA, 8–12 December 2008; pp. 377–391. [Google Scholar]
- Guo, Z.; Harris, I.G.; Jiang, Y.; Tsaur, L. An efficient approach to prevent Battery Exhaustion Attack on BLE-based mesh networks. In Proceedings of the International Conference on Computing, Networking and Communications (ICNC), Santa Clara, CA, USA, 26–29 January 2017; pp. 1–5. [Google Scholar]
- Mateusz, K.; Michal, M. Simulation of watchdog placement for cooperative anomaly detection in Bluetooth Mesh Intrusion Detection System. Simul. Model. Pract. Theory 2019, 101, 102041. [Google Scholar]
- Bluetooth Mesh Security Overview. Available online: https://www.bluetooth.com/blog/bluetooth-mesh-security-overview/ (accessed on 16 April 2020).
- Padgetter, J.; Scarfone, K.; Chen, l. Guide to Bluetooth Security. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-121r2.pdf (accessed on 20 February 2020).






| Ref. | –Protocol –Homogeneous BLE or Heterogeneous | -Connection-Oriented (C) /Routing (R) -Flooding (F)/(R) | Test Bed (T)/ Simulation (S) | PDR | End to End Delay | Power Consumption | Nodes Other Measurements (OM) Throughput | Pros and Cons |
|---|---|---|---|---|---|---|---|---|
| [10] | –CbODRP –Homogeneous BLE | C/R-Reactive | S | × | -Route discovery delay 40–100 ms with 50–90 nodes | Approx 250–500 mA with 50–90 nodes | 50 to 90 Nodes OM-Route Req Messages 0–20 with number of nodes 50–90 -Control Paket Overhead 12–88 with Route Discovery interval 1–10 s | Pros-Good contribution towards hybrid mesh protocols Cons-No new pure mesh protocol proposed -Lack of Hardware Implementation |
| [11] | –MRT-BLE –Homogeneous BLE Network (Static Nodes) (Bounded Packet Delays in Mesh Network) | C (Static Routing Configure Offline to get bounded delays) | T-(BLE) X-NUCLEO-IDB05A1 | -Single Hop (100%) -Two Hops (Approx 100%) -Three Hops (96%) -Four Hops (97%) | -Single Hop (120 ms) -Two Hops (390 ms) -Three Hops (810 ms) -Four Hops (1050 ms) -Five Hops (1400 ms) | × | 8 Nodes | Pros-Positive contribution (hybrid mesh protocols) Cons-Require Dynamıc Configuration Mechanism for free movement of nodes -Missing Dynamic topology management mechanism -Need Realtime routing for efficiency |
| [41] | –BLE-Tree Network –Homogeneous BLE | C and R (Reactive) | T Raspberry Pi 3 Model B (BLE 4.1) S | 100% (for 2 p/s) 97.5% (for 5 p/s) 82% (for 10 p/s) | Round-Trip Time: For 1 Hop = 100 ms 2 Hops = 200 ms 3 Hops = 250 ms 4 Hops = 340 ms 5 Hops=360 ms 6 Hops=530 ms | × | 40 Nodes | Pros-Efficient Breadth First Search algorithm Cons-No detailed analysis (other tree-based protocols)-Security (Authentication methods not discussed) |
| [46] | –FruityMesh –Homogeneous BLE | C (FruityMesh (FM)) /R-Reactive | T-Nordic Thingy: 52 IOT sensor kit -nRF52DK -nRF6707 | × | × | Note: Connection Interval (CI) (7.5–400 ms) (a) 0.65–0.1 mA (Adv Interval 100 ms with CI) (b) 0.6–0.03 mA (Adv Interval 600 ms with CI) (c) Network Life 10–250 days with CI | 1 to 3 Nodes OM with CI from 7.5–400 ms and advertising interval (100 and 600) the current drain is 0–0.65 mA Throughput Approx from 8–0.5 kB/s for CI 5–400 ms and max 3 packets/interval -with CI > 400 ms is 150 b/s | Pros-Good contribution related to power consumption and current drainage Cons-Need to work on more number of nodes and further analysis of performance measurements |
| [49] | –DC-BMN –Homogeneous BLE | C | S-Matlab | × | × | × | 100 Nodes OM For N Slot 10 | Pros-Analystic Model for node isolation probability Cons-No Performance Measurement-No Testbed |
| [50] | –FruityMesh and Trickle –Homogeneous BLE | C (FM) /R-Reactive F-(Trickle (TR)) | T-nRF52 (BLE 5) | FM: 40% (10 p/s) TR: 38%(10 p/s) | FM: Approx 3.8 s TR: 0.35 s | FM: 9.4 mW TR: 28.5 mW | 7 Nodes | Pros-Author performed good comparison between C and F networks Cons-No new algorithm or method proposed |
| [51] | –FruityMesh and Trickle –Homogeneous BLE | C (FM)/ R-Reactive F-TR | T-nRF52 (BLE 5) -Five Hardkernel Odroid-C2 -Netgear GS108T 8-port switch | -FM: 100%, 90%, 40% with 1, 5, 10 p/s resp -TR: 100%, 80%, 38% with 1, 5, 10 p/s resp | -FM: 0.3, 3.7, 3.9 s with 1, 5, 10 p/s resp -TR: 0.4, 0.3, 0.3 s with 1, 5, 10 p/s | FM: 9 mW TR: 28 mW | 37 Nodes | Pros-Good implementation of available hybrid mesh protocols |
| [52] | –BLE Mesh –Homogeneous BLE | C/R-Reactive | T- nRF52 (BLE 5) | High | Low | × | 12 Nodes | Pros-Used network inference for determination of node settings and design choices Cons-Require more experimentation |
| [53] | –K2 Pruning Greedy Connect and Dominator –Homogeneous BLE | F-(Greedy Connect (GC) K2 Pruning (KP) Dominator(D)) | S-Matlab | -Area (330 × 330 msq) K2: Approx 80%–8% with packets 5–200 p/s GC:65%–8% with packets 5–200 p/s | × | × | 1000 Nodes | Pros-Comparative study of various flooding techniques Cons-No proposed protocol |
| [54] | –D-AOMDV –Homogeneous BLE | F | S-Matlab | Approx 75%–88% with number of nodes 10–40 | × | × | 40 Nodes | Pros-Good Simulation Results with 40 Nodes Cons-Require Analysis of more performance parameters |
| [55] | –RT-BLE –Homogeneous BLE (Static Nodes) (Bounded Packet Delays in Mesh Network) | C (Static Routing Configure Offline to get bounded delays) | T-(BLE) X-NUCLEO-IDB05A1 | × | 20 ms | × | 4 Nodes | Pros-Positive contribution (hybrid mesh protocols) Cons-Require Dynamıc Configuration Mechanism for free movement of nodes -Require Dynamic topology management mechanism -Need Realtime routing for efficiency |
| [59] | –BLE-PLC –Heterogenous | C/R-Reactive | T-nRF52832 (BLE 5) -PLC Modem IEEE 1901 -Wiznet 5550 | -BLE Node Distance 0.6 m, transmit power −4 to 4 dBm a. 93%–97.5% (without wifi interference) b. 91%–96.5% (with wifi) | -BLE Node Distance 0.6 m, transmit power (−4 to 4 dBm) a. 8.2–6.3 ms (without wifi) b. 8.4–6.4 ms (with wifi) | × | 12 Nodes | Pros-Good efficient smart cargo Cons-Tested only for PDR and Delay |
| [61] | –OperaBLE –Heterogenous (BLE, LoRaWAN, BAN) (Mobile Nodes) | C/R-Reactive F | T-Arduino UNO -BLE112 and CSRmesh -Light Blue Bean -Raspberry Pi 2 B -LoRaWAN etc | BLE Mesh -Supervisor Request/Response 100% and 92% -Supervisor Taps (96%) -Movements Tx: (Approx 96%) OperaBLE -Supervisor Taps (92%) -OperaBLE movement (Approx 90%) | BLE Mesh -Requests (Average Delay 0.347 s) -Taps (1.407 s) -Movement (Average time per packet 0.290s) | OperaBLE -Program Running 14 mA -Sleep Mode 2 mA | Nodes Not Mentioned OM Security at work -Heart rate measure (Error rate while fatigued 6.5% relaxed 1.05% working, 2.9%) | Pros-Good Heterogenous network for the industry Cons-Require development of coginitive systems for intelligent support enhancement -ML techniques can be applied for movements -Security can be improved |
| Ref. | Protocol | Attack Manipulation |
|---|---|---|
| [77] | BTCP | -Protocol to Secure Scatternet Formation -Efficient Against MITM Attack |
| [78] | RAP-BE | -Combined encrypted key exchange protocols -Efficient Against DoS and Relay Attacks |
| [79] | SEBSPP | -Utilized strong public key exchange mechanism to Mitigate MITM |
| [80] | SSBC | -Implements double layered encryption to secure data communications -Efficient Against MITM and Passive Eavesdropping Attacks |
| [81] | PBBPP | -Analysis of the shortcomings of Pin-Based Authentication Model -Handles Password Guessing Attack |
| [82] | ESBN | -Developed Link Layer Security Mechanism -Battle against MITM and Message Alterations |
| [83] | PUF-AP | -Physical Unclonable Function (PUF)-based authentication protocol -Joint authentication and maintenance of secrecy for the session key -MITM, Replay, Passive Eavesdropping, and Impersonation Attacks |
| [84] | BC-GW | -Blockchain-enabled IoT gateway for BLE-based devices -Preserve user privacy and enforce user preferences when accessing IoT devices |
| Ref. | Protocol | IDS Method | Methodology | Attacks Mitigated | Results and Potential Improvements |
|---|---|---|---|---|---|
| [85] | FogComp-IDS | OS-ELM | Used Fog Computing | Cyber | -False Positive Result (FPR) very low, 25% Faster detection rate -Next step prediction is required to react proactively to the attacks |
| [86] | KMA and CBA | KMA with Hash values CBA with path matrix | Technology utilized 6LoWPAN | Routing (Sinkhole and Selective forwarding) | KMA 50% to 80% True Positive Result (TPR) CBA 76% to 96% TPR -In depth comparative analysis -Only covering few attacks |
| [87] | DLM-SLA-IDS | Anomaly-Based | Dataset UNSW-NB 15 Detection Model -Merged DLM and SLA Algorithm -DLM is Deep auto-encoders -SLA is SVM | General coverage for all attacks | -Proposed method better than other PCA-based and ML methods -Require more accuracy and low FPR rate |
| [88] | LWIDS | Supervised Machine learning-based approach | -Lightweight detection -Used Machine learning based SVM | DoS | Proven that: Good packet arrival rate and SVM based classifier is good for detection Lacks security parameters policy |
| [89] | Three-LIDS | Three layered IDS | -Reporting Normal behavior of nodes -Detect malicious packet -Attack detection | DoS, MITM, reconnaissance and replay | Accuracy -Reporting: 96.2% -Malicious Packet: 90% -Attack Detection: 98% Lacks real time implementation |
| [90] | ML-IDS | Machine Learning Based method | Common Protocols Analysis used for SCADA IIOT devices | Backdoor, Command and SQL injection | Capable of handling new attacks like Backdoor, Command, SQL injection Require hybrid model for better performance |
| [92] | MD-CPS | Behavior Rule Specification-based | Unmanned Aerial Vehicle | Zero-day attacks | High detection and prediction Lacks comparative analysis of other methods and datasets |
| [93] | BRIoT | -Behavior Rule Specification-based -For Mission Critical Cyber Physical System -Exploited UAV | -Unmanned Aerial Vehicle -For Mission Critical Cyber Physical Systems | Zero-day attacks | BRIoT outperformed its predecessor BRUIDS Require more analysis for FPR, FNR viz-a-viz memory, overheads etc |
| [94] | InBGG | -InBGG Bayesian-based approach -Gaussian-based | -Feature selection mechanism -Utilized datasets KDDCup’99, KYOTO 2006+, ISCX | Cyber attacks | InBGG Accuracy KDDCup’99: 84.06% Kyoto 2006+: 88.13% ISCX: 91.82 InBGG FPR KDDCup’99: 16.02% Kyoto 2006+: 13.39% ISCX: 8.37% Require experimentation with more datasets |
| [96] | GLRT | Generalized likelihood ratio test | Three points disturbances detection i.e., unicast packet uplink, downlink and broadcast | Battery Exhaustion and Relay attacks | -Negligible false alarm -Slight missed detection probability Not good where subgroup of IoT devices are under attack |
| [97] | OBSCR | Access Control technique using ontology reasoning | -Analytical vulnerability analysis -Utilized smart meter -Context Inference Rules | Generally, covers all major attacks and Memory dump, Port access Data sniffing, Software Protocol, ZigBee | Proposed system results a. 87.5% b. 91.1% c. 92.5% d. 86.1% e. 78.4% f. 91.5% More detailed analysis of power system and their vulnerabilities |
| [98] | SeArch | Network-based ID (NID) | NID system for SDN-based Cloud IoT | Cyber attacks | Detections: 95.5% Overheads: 8.5% to 15% Requirement to improve overheads to make IDS power efficient |
| Ref. | Protocol | Simulation or Testbed | IDS Method | Methodology | Attacks | Results and Potential Improvements |
|---|---|---|---|---|---|---|
| [99] | SID-HAN | Simulation (NS2) | Layered Specification-based | IEEE 802.15.4 Standard Normal behaviors | ZigBee Mac and Physical Layer | System capable to detect several known and unknown attacks efficiently Require: -IDS for upper layers of ZigBee -Testbed experiments |
| [100] | TA-ZB | Simulation (Avrora) | Anomaly-based | -Analysis of KillerBee framework -Implemented IDS in ZigBee radio | KillerBee-Association flooding and packet replay attacks | -Efficient attack detection -Broad spectrum attack analysis is required |
| [101] | ABAS | Testbed | Anomaly-based | Comparison Analysis with Signature and Specification | DoS, Flooding and Pulse DoS | 0% FPR for known attacks 95% FPR for unknown attacks |
| [102] | FL-IDS | Simulation | Fuzzy Logic | Asymptotic Analysis | Flood | -Require more mathematical and comparison analysis -Require analysis of more attacks |
| [103] | HAN-IDS-IPS | Simulation | Model-based IDS ML based IPS | Design for PHY and MAC Layers of ZigBee HAN | Cyber Attacks | Efficient in detecting Cyber based attacks Require Testbed Analysis |
| [104] | EE-IDS | Simulation | Optimized watchdog mechanism (OWM) | OWM (trust-based method) | Worm Hole | Good energy consumption, PDR, end-end delay Proposed system evaluation against mobility models |
| [105] | EE-IDSEP | Simulation (NS2) | Energy Efficient Trust | -Developed two modules EE-IDS and EE-IDSEP -Comparison Analysis | Worm Hole and DDOS | Proposed protocol efficiency increased by 23% (AODV), 28% (STR), 33% (OSTR) Proposed system evaluation against mobility models |
| [106] | HHT-TE-IDS | Simulation and Test Bed | HHT and EMD | Scalable HHT-based | LDoS | Capable of detecting Low Rate DoS attack |
| Ref. | Protocol | Simulation or Testbed | IDS Method | Methodology | Attacks | Results and Potential Improvements |
|---|---|---|---|---|---|---|
| [107] | DSD6Lo | Testbed | Signature-based | Improved Open source Suricata IDS | DoS | -Improvement in Suricata IDS in terms of attack detection -IDS run on host computer to make system more resourceful Require: -Real attack implementation -Distributed approach and security event databases |
| [108] | INTI | Simulation | Watchdog, Reputation and Trust | Combine WR and TB methods | Sinkhole | 90% Detection Rate (DR) with Fixed Devices, 70% DR with Mobile Devices |
| [109] | InDReS | Simulation (NS-2) | Constraint-based specification | Performance Analysis of InDReS with existing system (INTI) | Sinkhole | Packet Drop Ratio Lower than INTI Throughput Higher than INTI Packet Delivery Ratio Higher than INTI Overhead Lesser than INTI -Behavior rule-based analysis -Analysis of other attacks |
| [110] | CHA-IDS | Simulation (Contiki Cooja) and Testbed | Hybrid (Anomaly +Signature) | -Multi agent system -Feature selection (correlation) -Compared SVELTE, Pongles | Hello Flood Sinkhole Wormhole | 99% True Positive Result (TPR) |
| [111] | ARM | Simulation (Contiki Cooja) | Hybrid Specification -based IDS | Emphasis on RPL | Rank attacks | Stable Phase 100% TPR Instable Phase 10% FPR 60% Accuracy Rate (AR) -Require analysis to overcome more attacks |
| [112] | ABIDS | Simulation (Contiki Cooja) | Anomaly-based | -Threshold value-based RPL attack detection | DIS and Neighbor | High TPR Low False Positive Result (FPR) Require more analysis of the RPL attacks and other available solutions |
| [113] | NSQ | Simulation (Contiki Cooja) | Probabilistic method | Quantitative security assessment of constrained nodes | -Eavesdropping -Data Modification -Blackhole -Selective Forwarding | -High Accuracy -Low power consumption and overheads -Overall efficient system -Require transmission analysis agent enhancement -Real network implementation |
| Ref. | Protocol | Protocol Specifications | Simulation or Testbed | Methodology | Attacks | Results |
|---|---|---|---|---|---|---|
| [114] | BN-MD | Signature-based IDS | Testbed Attack Node -Laptop equipped with BackTrack2 Target Node -Nokia 6310 Phone (BlueBug Attack) -Sony Ericsson T68i Phone (BlueSnarf Attack) -Plantronics M2500 Headset (CarWhisperer Attack) -Motorola v600 Phone (HeloMoto Attack) Defense Node -Hardware Protocol Analyzer -Software IDS Application Intrusion Response Node -Three CambridgeSilicon Radio (CSR) chip-based USB Bluetooth dongles. | -IDS using misuse detection -Sytem for detection of Bluetooth Attacks | Reconnaissance RFCOMM Scan PSM Scan DoS HeaderOverFlow Nasty vCard Information Theft BlueSnarf BlueBugger CarWhisperer HeloMoto | Detection Time (sec) Reconnaissance 110.86 4.74 DoS 0.0006 1.10 Information Theft 1.46 3.25 0.22 3.22 |
| [115] | BBEADP | IDS and IPS for BLE-based Networks | Test Bed -Broadcom chipset 2070X | Developed an IDS and IPS to increase the overall network life and the throughput | Battery Exhaustion | Approximately 29 h more network life AND 46% more throughput |
| [116] | BM-IDS | Anomaly-based IDS | Testbed (DK nRF52832, DK nRF52840) -Simulation: BMWatchSim | Method for Optimal Placement of Watchdog for detection | Unknown attacks like Gray hole, Injection or Flooding | Accuracy S(best): 100% S(75): 97% S(25): 94% |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ghori, M.R.; Wan, T.-C.; Sodhy, G.C. Bluetooth Low Energy Mesh Networks: Survey of Communication and Security Protocols. Sensors 2020, 20, 3590. https://doi.org/10.3390/s20123590
Ghori MR, Wan T-C, Sodhy GC. Bluetooth Low Energy Mesh Networks: Survey of Communication and Security Protocols. Sensors. 2020; 20(12):3590. https://doi.org/10.3390/s20123590
Chicago/Turabian StyleGhori, Muhammad Rizwan, Tat-Chee Wan, and Gian Chand Sodhy. 2020. "Bluetooth Low Energy Mesh Networks: Survey of Communication and Security Protocols" Sensors 20, no. 12: 3590. https://doi.org/10.3390/s20123590
APA StyleGhori, M. R., Wan, T.-C., & Sodhy, G. C. (2020). Bluetooth Low Energy Mesh Networks: Survey of Communication and Security Protocols. Sensors, 20(12), 3590. https://doi.org/10.3390/s20123590







