An Efficient, Anonymous and Robust Authentication Scheme for Smart Home Environments
Abstract
1. Introduction
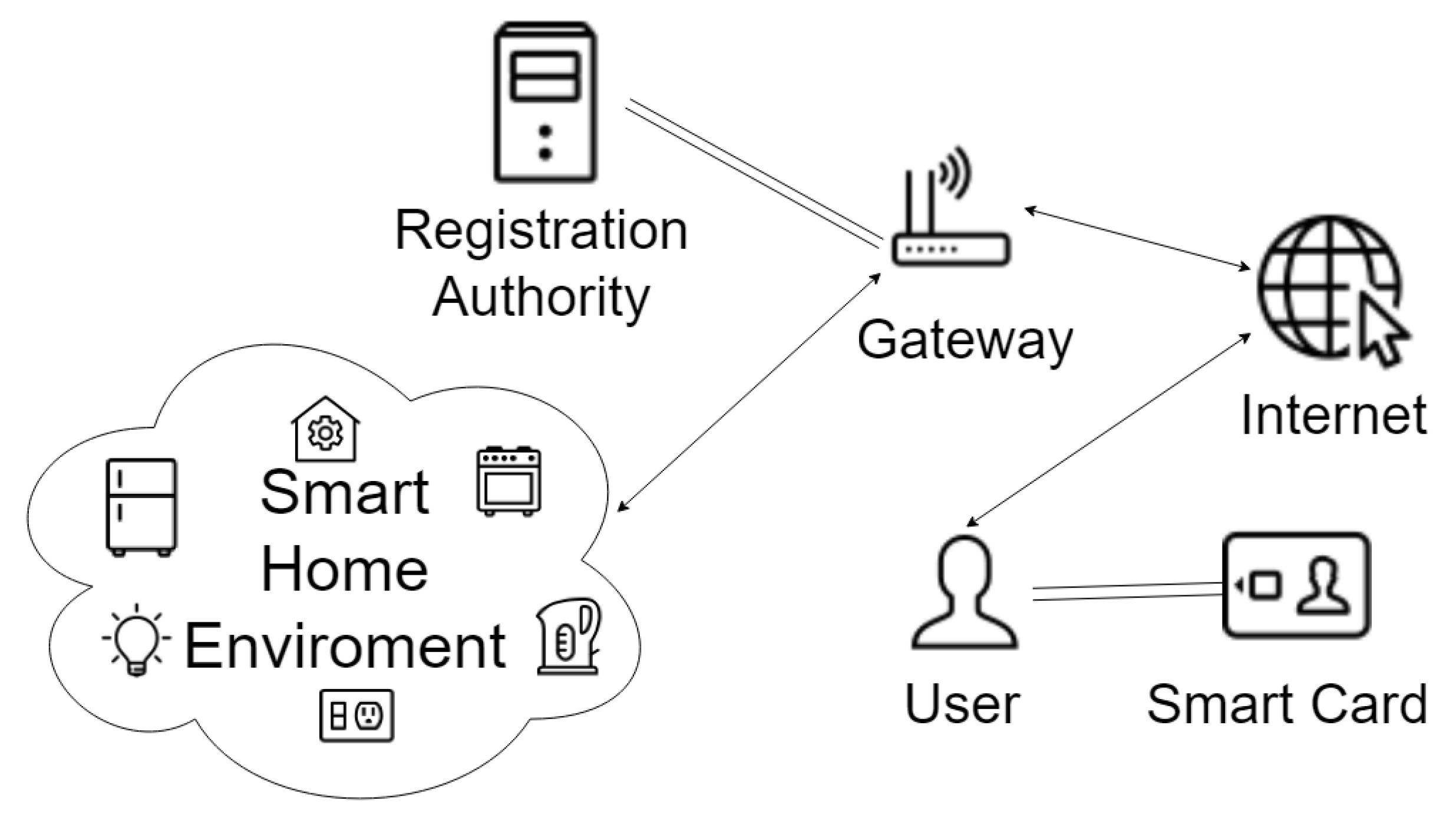
1.1. Network and Threat Models
1.2. Research Contributions
- We first analyze the recently proposed anonymous authentication scheme by Shuai et al. [7] for the smart home environment and then highlight that their scheme fails to resist known attacks, such as privileged-insider attack, through offline password guessing and lost/stolen smart card attacks, user impersonation attacks, parallel session attacks, and password change attacks.
- We present a more secure user authentication scheme that avoids the security pitfalls demonstrated in Shuai et al.’s scheme.
- Through formal as well as informal security analysis, we show the resistance of the proposed scheme against various potential attacks needed in a smart home environment.
- We then present a comparative study to demonstrate the superior security and functionality features of the proposed scheme relative to the existing relevant authentication schemes.
- Finally, we provide a practical perspective on the applicability of the proposed scheme through a network simulator (NS3) simulation study.
1.3. Related Work
2. Review of Shuai et al.’s Scheme
2.1. Initialization Phase
2.2. Registration Phase
2.2.1. User Registration
- Step 1.U first picks his/her identity , password and generates a random secret a. U then calculates pseudo-password and securely dispatches the credentials to .
- Step 2. If is already registered, rejects the request. Otherwise, computes , . generates a random value in order to record the number of user login failures, and sets . Next, writes to a smart card and securely issues to the user U.
- Step 3. On receiving the smart card , U calculates and , and appends and to the smart card . The smart card finally contains the credentials .
2.2.2. Device Enrollment
- Step 1. first securely transmits its identity to .
- Step 2. If is already enrolled, the request is rejected by the . Otherwise, computes and securely sends the secret key to .
- Step 3. On receiving the reply, saves the secret key in its memory.
2.3. Login and Authentication Phase
- Step 1. User U first enters his/her identity and password , and calculates , and . Only if the check holds, the login is successful. In case of a failed login attempt, the smart card of the user U updates . This value records the login attempts and if it exceeds a pre-defied threshold, the user U is considered as compromised and is suspended till he/she re-registers.After a successful login, the smart card generates two random numbers and , and computes , , , , and , and sends the login request message 〉 to via open channel.
- Step 2. On receiving the login request 〉, computes , , , , . Only if the condition holds, believes the legitimacy of the login request. then generates a random number and computes , , . Finally, sends the authentication request message , to via public channel.
- Step 3. On receiving the message , , calculates , and checks if . If true, generates a random number and computes , , and finally transmits the authentication reply message to .
- Step 4. On receiving the message from , computes , , , and if , computes and , and sends the acknowledgement message to U via public channel.
- Step 5. On receiving the message from , U computes , and , and if , is authenticated by the , and also the session key is established between U and .
3. Security Vulnerabilities in Shuai et al.’s Scheme
3.1. Privileged-insider Attack through Offline Password Guessing and Lost/Stolen Smart Card Attacks
3.2. User Impersonation and Parallel Session Attacks
3.3. Password Change Attack
4. The Proposed Scheme
4.1. Initialization Phase
4.2. Registration Phase
4.2.1. Dynamic Device Enrollment
- Step 1. first securely transmits its identity to .
- Step 2. If is already enrolled, the request is rejected by the . Otherwise, computes the secret key , and securely sends to and makes public.
- Step 3. On receiving the reply from the , saves the secret key in its memory.
4.2.2. Mobile User Registration
- Gen: It is a “probabilistic generation function” that computes a pair from the user biometrics information. The resultant is the “biometric secret key” and is the “public reproduction parameter” necessary for reconstruction of from , a noisy biometric reading from the same user. Formally, .
- Rep: It is a “deterministic reproduction method” which constructs the original biometric secret key using a noisy biometrics reading, and the public reproduction parameter provided the Hamming distance between and is less than or equal to a pre-defined error tolerance threshold value, say . Formally, , with the restriction that .
- Step 1.U selects his/her identity and securely sends to .
- Step 2. If is already registered, rejects the request. Otherwise, generates and computes , and also sets . After that commits the tuple to the table in the gateway node . also writes the credentials to a smart card , and securely issues to the user U.
- Step 3. After getting , U provides a password and imprints biometric template at the sensor of a specific terminal. U uses the probabilistic fuzzy generator function to calculate the biometric secret ket and a public reproduction parameter as . After that, U computes , and , and replaces and in the smart card with . The smart card finally contains the credentials .
4.3. Login and Authentication Phase
- Step 1.U first inputs his/her identity and password , and imprints his/her biometric at the sensor of a particular terminal. The smart card of U then uses public to compute from as , and proceeds to calculate and . If the condition holds, the login is treated as successful one. In case of a failed login attempt, the smart card increments and aborts the phase. On the other side, if it exceeds a pre-defined threshold, the user U is considered as compromised, and is suspended till he/she re-registers.After a successful login, generates two random numbers and , and calculates , and , and dispatched the login request message to the via public channel.
- Step 2. After receiving the login request , the looks up using from its table, and computes , . If is fresh, the calculates . Now, if , the request is considered as invalid, and the process is aborted instantly. Otherwise, the generates a new random number and calculates , , , and . Finally, dispatches the authentication request message , to the accessed smart device via open channel.
- Step 3. On receiving the message , , calculates . If is fresh, calculates . If , the request is considered as failed, and it is then aborted. On the other side, picks a random number , computes the session key shared with U, and . Next, transmits the authentication reply message to via public channel.
- Step 4. On receiving the message from , computes . If is also fresh, the continues to calculate . If , the request is considered as invalid and the process is aborted immediately. Otherwise, the generates another random number and computes , and . then updates the tuple in its table, and sends the ackowledgement message to the U via open channel.
- Step 5. On receiving the message from , the user U recovers , and then computes and . If , the login is considered as failed one and it is aborted immediately. Otherwise, the user U computes the session key and the updated values for , , . Finally, U resets to 0 as , and updates the smart card with the values by replacing the old values .
4.4. Password and Biometric Update Phase
4.5. Smart Card Revocation Phase
5. Security Analysis
5.1. Formal Security Analysis through Real-Or-Random Model
- Participants: Let the oracles , and denote the uth, dth and gth instances of a user U, a smart device and the gateway node , respectively.
- Partnering: Two oracles and are said to be partnered provided they share the same communication session-id , and the partial transcript of the exchanged messages is unique.
- Freshness: and are considered fresh as long as the session key between U and remains unexposed to an adversary .
- Adversary: The ROR model defines the DY adversary . Formally, the adversary can execute the queries described below.
- –
- : This query is modeled as an eavesdropping attack. Therefore, this query allows to intercept the messages exchanged among U, , and .
- –
- : This query is modeled an active attack. It allows to transmit a message, say to an oracle , and receive the response message in reply.
- –
- : Through this query, can learn the confidential values , , from a user U’s smart card .
- –
- : Through this query, can learn the secret key stored in the captured smart device . The queries and are assumed to be under a weak corruption model [29] and they can not corrupt the ephemeral keys and states of the participating oracle.
- –
- : As per the “indistinguishability in the ROR model” [27], the semantic security of the session key between U and can be determined by this query. To initiate, tosses an “unbiased coin” whose outcome, say c, determines the output of the query. If is fresh, the oracle or produces , if . Otherwise, if , the oracle produces a random number. In all other cases, the returned value will be null.
- Semantic security of the session key: As per the ROR model, to compromise the semantic security of the session key, must be able to differentiate an instance’s actual session key from a random key. can perform a limited number of and queries, but can execute as many queries as desired.If represents the advantage of in compromising the semantic security of the proposed scheme , we have, , where is an event of ’s success.
- Random oracle: All participating entities including can invoke the “cryptographic one-way hash function”, , which is further modeled as a random oracle, say .
- Game: This game models a real attack on the semantic security of the proposed scheme by . As initially the bit c is guessed,
- Game: This game models as an eavesdropping attack by on . Through the query, can intercept the messages , , , and . can query the oracle and attempt to determine if the received result is the actual session key. As the session key is , and to compute the same must learn short term secret keys ( and ) as well as long term secrets ( and K). Therefore, gains no additional advantage for wining this game. Consequently, it follows that
- Game: This game models as an active attack through use of the and hash queries. attempts to beguile a legitimate entity into accepting a modified message. As discussed previously, can repeat the queries to the oracles in order to induce hash collisions. However, since all the messages contain random nonces, hash coalitions cannot be induced on by . It is worth noticing that both the games and are identical except for the and hash queries in the game . Thus, through the use of birthday paradox, we have,
- Game: An extension to , the game is the final game and it simulates the and queries. Querying these oracles, can learn , , , and , respectively. The probability of to correctly guess the biometric secret key of bit-length and the user identity of bit-length are and , respectively [33].As the user chosen passwords tend to follow the Zipf’s law, by utilizing trawling guessing attacks, ’s advantage will be over when or [30]. If can utilize a user’s personal information for the targeted guessing attacks, he/she will have an advantage over when [30]. In practical implementation, only a finite number of erroneous password attempts are permitted to the adversary . Therefore, the games and are identical except for the guessing attacks. Thus, we can formulate the following relation as in [32]:However, must guess a bit after executing the query to win the game . Therefore, it follows that
5.2. Formal Security Verification through AVISPA Simulation
- SUMMARY: It states if the tested protocol is “safe”, “unsafe”, or if the analysis was “inconclusive”.
- DETAILS: It reports the explanation relevant to the SUMMARY section.
- PROTOCOL: It provides the protocol to be verified.
- GOAL: It states the goal as specified in the HLPSL.
- BACKEND: It mentions the backend that has been utilized.
- STATISTICS: It provides the trace for the vulnerabilities to the target protocol, if they are present, with additional useful statistics.
5.3. Informal Security Analysis
5.3.1. Replay Attack
5.3.2. Forgery Attack
5.3.3. Impersonation Attack
5.3.4. Man-in-the-Middle Attack
5.3.5. Loss of Smart Card and Offline Guessing Attack
5.3.6. Privileged-Insider Attack
5.3.7. Ephemeral Secret Leakage (ESL) Attack
5.3.8. Parallel Session Attack
5.3.9. Stolen Verifier Attack
5.3.10. Smart Card Impersonation Attack
5.3.11. Anonymity and Untracability
6. Comparative Study
6.1. Communication Costs Comparison
6.2. Computation Costs Comparison
6.3. Security and Functionality Features Comparison
7. Practical Impact Study through NS3 Simulation
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A Survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Gomez, C.; Paradells, J. Wireless home automation networks: A survey of architectures and technologies. IEEE Commun. Mag. 2010, 48, 92–101. [Google Scholar] [CrossRef]
- Kim, J.E.; Boulos, G.; Yackovich, J.; Barth, T.; Beckel, C.; Mosse, D. Seamless integration of heterogeneous devices and access control in smart homes. In Proceedings of the Eighth International Conference on Intelligent Environments (IE’12), Guanajato, Mexico, 26–29 June 2012; pp. 206–213. [Google Scholar]
- Kumar, P.; Gurtov, A.; Iinatti, J.; Ylianttila, M.; Sain, M. Lightweight and secure session-key establishment scheme in smart home environments. IEEE Sen. J. 2015, 16, 254–264. [Google Scholar] [CrossRef]
- Suryadevara, N.K.; Mukhopadhyay, S.C.; Wang, R.; Rayudu, R. Forecasting the behavior of an elderly using wireless sensors data in a smart home. Eng. Appl. Artif. Intell. 2013, 26, 2641–2652. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally Composable Notions of Key Exchange and Secure Channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques–Advances in Cryptology (EUROCRYPT’02), Amsterdam, The Netherlands, 28 April–2 May 2002; pp. 337–351. [Google Scholar]
- Banerjee, S.; Odelu, V.; Das, A.K.; Jangirala, S.; Kumar, N.; Chattopadhyay, S.; Choo, K.K.R. A Provably-Secure and Lightweight Anonymous User Authenticated Session Key Exchange Scheme for Internet of Things Deployment. IEEE Internet Things J. 2019, 6, 8739–8752. [Google Scholar] [CrossRef]
- Jeong, J.; Chung, M.Y.; Choo, H. Integrated OTP-based user authentication scheme using smart cards in home networks. In Proceedings of the 41st Annual Hawaii International Conference on System Sciences (HICSS’08), Waikoloa, HI, USA, 7–10 January 2008; p. 294. [Google Scholar]
- Vaidya, B.; Park, J.H.; Yeo, S.S.; Rodrigues, J.J. Robust one-time password authentication scheme using smart card for home network environment. Comput. Commun. 2011, 34, 326–336. [Google Scholar] [CrossRef]
- Kim, H.J.; Kim, H.S. AUTH HOTP-HOTP based authentication scheme over home network environment. In Proceedings of the International Conference on Computational Science and Its Applications (ICCSA’11), Santander, Spain, 20–23 June 2011; pp. 622–637. [Google Scholar]
- Vaidya, B.; Makrakis, D.; Mouftah, H.T. Device authentication mechanism for smart energy home area networks. In Proceedings of the IEEE International Conference on Consumer Electronics (ICCE’11), Berlin, Germany, 9–12 January 2011; pp. 787–788. [Google Scholar]
- Hanumanthappa, P.; Singh, S. Privacy preserving and ownership authentication in ubiquitous computing devices using secure three way authentication. In Proceedings of the International Conference on Innovations in Information Technology (IIT’12), Abu Dhabi, UAE, 18–20 March 2012; pp. 107–112. [Google Scholar]
- Li, Y. Design of a key establishment protocol for smart home energy management system. In Proceedings of the Fifth International Conference on Computational Intelligence, Communication Systems and Networks (CICSYN’13), Madrid, Spain, 5–7 June 2013; pp. 88–93. [Google Scholar]
- Han, K.; Kim, J.; Shon, T.; Ko, D. A novel secure key paring protocol for RF4CE ubiquitous smart home systems. Pers. Ubiquitous Comput. 2013, 17, 945–949. [Google Scholar] [CrossRef]
- Santoso, F.K.; Vun, N.C. Securing IoT for smart home system. In Proceedings of the International Symposium on Consumer Electronics (ISCE’15), Madrid, Spain, 9–11 April 2015; pp. 1–2. [Google Scholar]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure remote user authenticated key establishment protocol for smart home environment. IEEE Trans. Depend. Secur. Comput. 2017. [Google Scholar] [CrossRef]
- Yu, B.; Li, H. Anonymous authentication key agreement scheme with pairing-based cryptography for home-based multi-sensor Internet of Things. Int. J. Distrib. Sens. Netw. 2019, 15, 1–11. [Google Scholar] [CrossRef]
- Naoui, S.; Elhdhili, M.H.; Saidane, L.A. Novel Smart Home Authentication Protocol LRP-SHAP. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC’19), Marrakech, Morocco, 15–18 April 2019; pp. 1–6. [Google Scholar]
- Fakroon, M.; Alshahrani, M.; Gebali, F.; Traore, I. Secure remote anonymous user authentication scheme for smart home environment. Internet Things 2020, 9, 1–20. [Google Scholar] [CrossRef]
- Dey, S.; Hossain, A. Session-key establishment and authentication in a smart home network using public key cryptography. IEEE Sen. Lett. 2019, 3, 1–4. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the Annual International Cryptology Conference (CRYPTO’99), Santa Barbara, CA, USA, 15–19 August 1999; pp. 388–397. [Google Scholar]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: how to generate strong keys from biometrics and other noisy data. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques–Advances in Cryptology (EUROCRYPT’04), Lecture Notes in Computer Science (LNCS), Interlaken, Switzerland, 2–6 May 2004; Volume 3027, pp. 523–540. [Google Scholar]
- Abdalla, M.; Fouque, P.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography (PKC’05), Lecture Notes in Computer Science (LNCS), Les Diablerets, Switzerland, 23–26 January 2005; Volume 3386, pp. 65–84. [Google Scholar]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispa-project.org/ (accessed on 23 March 2019).
- Chang, C.C.; Le, H.D. A provably secure, efficient, and flexible authentication scheme for ad hoc wireless sensor networks. IEEE Trans. Wirel. Commun. 2016, 15, 357–366. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s Law in Passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Gope, P.; Das, A.K.; Kumar, N.; Cheng, Y. Lightweight and Physically Secure Anonymous Mutual Authentication Protocol for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inf. 2019, 15, 4957–4968. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Rodrigues, J.J.; Park, Y. Physically Secure Lightweight Anonymous User Authentication Protocol for Internet of Things Using Physically Unclonable Functions. IEEE Access 2019, 7, 85627–85644. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Goswami, A. A Secure Biometrics-Based Multi-Server Authentication Protocol Using Smart Cards. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1953–1966. [Google Scholar] [CrossRef]
- von Oheimb, D. The high-level protocol specification language hlpsl developed in the eu project avispa. In Proceedings of the 3rd APPSEM II (Applied Semantics II) Workshop (APPSEM’05), Frauenchiemsee, Germany, 12–15 September 2005; pp. 1–17. [Google Scholar]
- AVISPA. SPAN, the Security Protocol ANimator for AVISPA. 2019. Available online: http://www.avispa-project.org/ (accessed on 23 March 2019).
- Wu, L.; Wang, J.; Choo, K.R.; He, D. Secure Key Agreement and Key Protection for Mobile Device User Authentication. IEEE Trans. Inf. Forensics Secur. 2019, 14, 319–330. [Google Scholar] [CrossRef]




| Scheme | No. of Bytes | No. of Messages |
|---|---|---|
| Shuai et al. [7] | (108 + 84 + 36 + 68) = 296 | 4 |
| Yu and Li [21] | (84 + 124 + 164 + 164) × 2 = 1072 | 8 |
| Naoui et al. [22] | (104 + 52 + 56 ) = 212 | 3 |
| Fakroon et al. [23] | (100 + 52 + 52 +84) = 288 | 4 |
| Dey and Hossain [24] | (132 + 132 + 52 + 52 + 52) = 420 | 5 |
| Proposed scheme | (68 + 40 +56 +72) = 236 | 4 |
| Scheme | U | Total Cost | ||
|---|---|---|---|---|
| Shuai et al. [7] | ||||
| ≈ 13.741 ms | ≈ 13.797 ms | ≈ 0.168 ms | ≈ 27.604 ms | |
| Yu and Li [21] | ||||
| ≈ 188.062 ms | ≈ 386.219 ms | ≈ 188.062 ms | ≈762.343 ms | |
| Naoui et al. [22] | ||||
| ≈ 32.453 ms | ≈ 34.166 ms | ≈ 1.713 ms | ≈68.332 ms | |
| Fakroon et al. [23] | ||||
| ≈ 0.224 ms | ≈ 0.28 ms | ≈ 1.344 ms | ≈1.848 ms | |
| Dey and Hossain [24] | - | |||
| ≈ 32.005 ms | ≈ 0.0 ms | ≈ 31.949 ms | ≈63.954 ms | |
| Proposed | ||||
| ≈ 13.965 ms | ≈ 0.56 ms | ≈ 0.224 ms | ≈14.749 ms |
| Feature | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Shuai et al. [7] | ☑ | ☑ | ☑ | ☑ | ☑ | ☒ | ☒ | ☒ | ☒ | ☒ | ☒ |
| Yu and Li [21] | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ |
| Naoui et al. [22] | ☑ | ☑ | ☑ | ☑ | ☑ | ☒ | ☒ | ☒ | ☒ | ☒ | ☒ |
| Fakroon et al. [23] | ☑ | ☑ | ☑ | ☑ | ☑ | ☒ | ☒ | ☒ | ☑ | ☑ | ☒ |
| Dey and Hossain [24] | ☒ | ☒ | ☒ | ☑ | ☒ | ☒ | NA | NA | ☒ | NA | ☒ |
| Proposed | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ |
| Parameter | Description | |
|---|---|---|
| Platform | NS3(3.28)/Ubuntu 16.04 LTS | |
| Network scenarios | No. of users | No. of smart devices |
| 1 | 3 | 5 |
| 2 | 3 | 10 |
| 3 | 3 | 15 |
| 4 | 5 | 15 |
| 5 | 5 | 20 |
| 6 | 8 | 20 |
| Mobility | Random (0–3 m/s) | |
| Simulation time | 1200 s | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Park, Y. An Efficient, Anonymous and Robust Authentication Scheme for Smart Home Environments. Sensors 2020, 20, 1215. https://doi.org/10.3390/s20041215
Banerjee S, Odelu V, Das AK, Chattopadhyay S, Park Y. An Efficient, Anonymous and Robust Authentication Scheme for Smart Home Environments. Sensors. 2020; 20(4):1215. https://doi.org/10.3390/s20041215
Chicago/Turabian StyleBanerjee, Soumya, Vanga Odelu, Ashok Kumar Das, Samiran Chattopadhyay, and Youngho Park. 2020. "An Efficient, Anonymous and Robust Authentication Scheme for Smart Home Environments" Sensors 20, no. 4: 1215. https://doi.org/10.3390/s20041215
APA StyleBanerjee, S., Odelu, V., Das, A. K., Chattopadhyay, S., & Park, Y. (2020). An Efficient, Anonymous and Robust Authentication Scheme for Smart Home Environments. Sensors, 20(4), 1215. https://doi.org/10.3390/s20041215





