Multi-Blockchain-Based IoT Data Processing Techniques to Ensure the Integrity of IoT Data in AIoT Edge Computing Environments
Abstract
:1. Introduction
2. Preliminaries
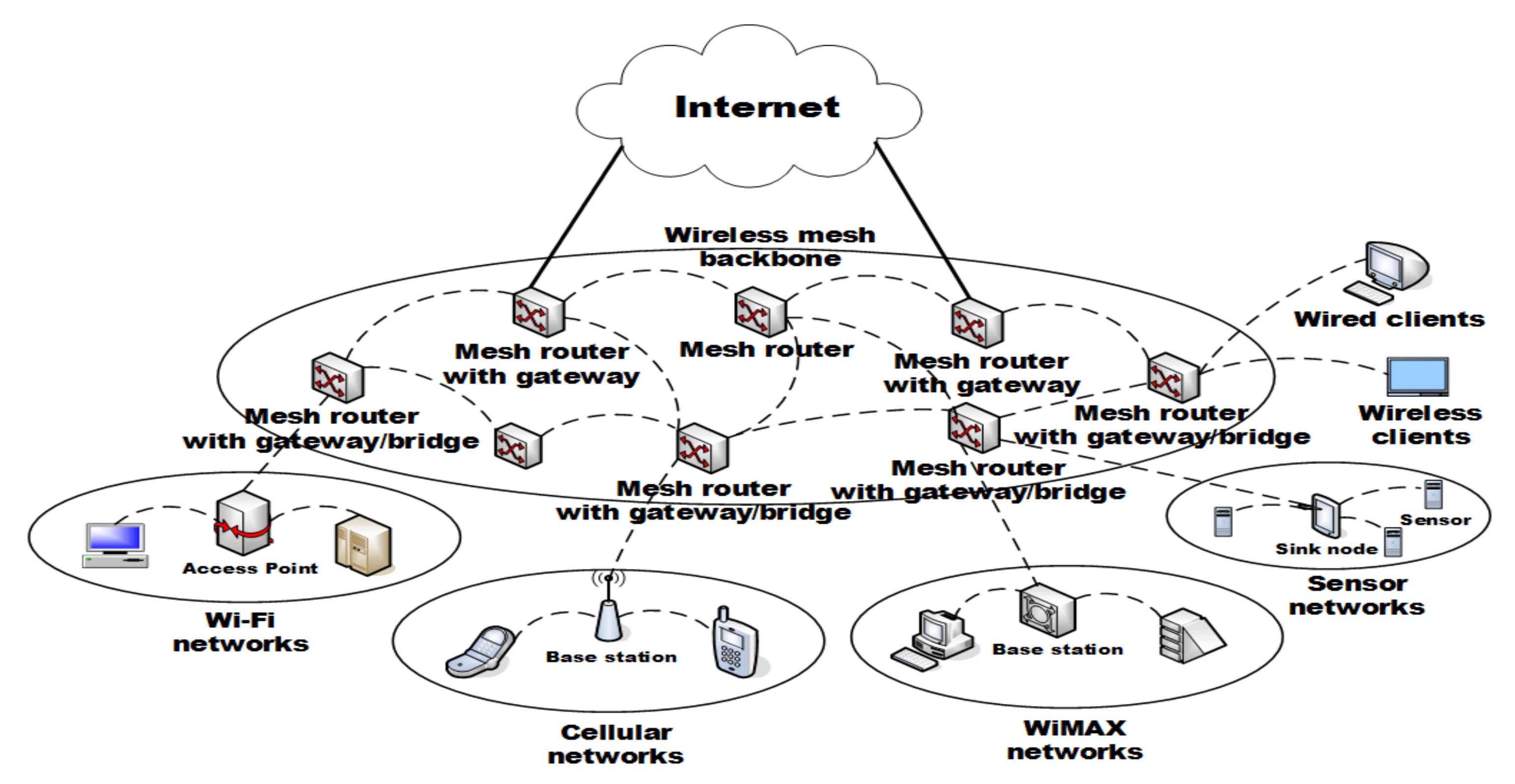
2.1. AIoT Edge Computing
2.2. Blockchain
2.3. Related Works
3. IoT Data Integrity-Verification Techniques Optimized for Distributed Cloud Environments
3.1. Overview
3.2. System Architecture
3.3. Measuring IoT Data Synchronization Using IoT Location Information
3.4. Generating Multiple Blockchains Based IoT Information
| Algorithm 1. IoT information generation algorithm based on blockchain. |
| 1: Initialize information on IoT distributed across AIoT edge computing. |
| 2: for all IoT information do |
| 3: if Receive IoT Information from IoT Devices then |
| 4: Compare IoT Information received from other IoT Devices |
| 5: Store the IoT Information block |
| 6: if the IoT Information block can be identified then |
| 7: Generate random blocks in n-bit form using from all IoT Information. |
| 8: Convert each block to replication |
| 9: if Generate hash values for odd/even |
| 10: Add to first and last of multiple hash chains |
| 11: Verification of the integrity of IoT Information |
| 12: else |
| 13: Regenerate hash values for odd/even |
| 14: end if |
| 15: else |
| 16: Reconfirm the IoT Information |
| 17: end if |
| 18: else |
| 19: Request IoT Information received from other IoT Devices |
| 20: end if |
| 21: end for |
| 22: return creating replication information for Add/Even |
3.5. Blockchain-Based IoT Hash Information Connection
| Algorithm 2. IoT Information Block Hash Connection. |
| 1: initialize IoT information block |
| 2: while IoT information block > 0 do |
| 3: Generate random blocks in n-bit form using |
| 4: Server checks its blocks |
| 5: if Replication block data present in blocks then |
| 6 Makes merkle tree in republication block |
| 7: Calculates block hash from merkle tree |
| 8: Inform other IoT devices |
| 9: else |
| 10: Request replication block data |
| 11: end if |
| 12: end while |
| 13: return IoT devices generates the new block |
3.6. Connection Renewal of IoT Information
4. Evaluation
4.1. Environment Setting
4.2. Performance Metrics
4.3. Performance Analysis
4.3.1. Evaluation of IoT Integrity Verification Time by Blockchain Generation Probability Value
4.3.2. Evaluating the Efficiency of IoT Information Processing in Subnet Gateway Servers
4.3.3. Delay Time for Verification of the Integrity of Blockchain Information
4.3.4. Overhead of IoT Integrity Validation by a Number of Subnet Gateway Servers
4.3.5. Evaluating IoT Connectivity to Validate IoT Integrity Based on Subnet Number
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zhao, Z.; Barijough, K.M.; Gerstlauer, Z. DeepThings: Distributed Adaptive Deep Learning Inference on Resource-Constrained IoT Edge Clusters. IEEE Trans. Comput. Aided Des. Integr. Cricuits Syst. 2018, 37, 2348–2359. [Google Scholar] [CrossRef]
- Chen, Y.; He, J.; Zhang, X.; Hao, C.; Chen, D. Cloud-DNN: An Open Framework for Mapping DNN Models to Cloud FPGAs. In Proceedings of the International Symposium on Field-Programmable Gate Arrays(FPGA), Seaside, CA, USA, 28 February–2 March 2021; pp. 73–82. [Google Scholar]
- Ouaddah, A.; Elkalam, A.A.; Ouahman, A.A. Towards a Novel Privacy-Preserving Access Control Model Based on Blockchain Technology in IoT. In Europe and MENA Cooperation Advances in Information and Communication Technologies; Springer: Cham, Switzerland, 2017; Volume 520, pp. 523–533. [Google Scholar]
- Xu, L.D.; He, W.; Li, S. Internet of Things in industries: A survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2243. [Google Scholar] [CrossRef]
- Miller, D. Blockchain and the Internet of Things in the industrial sector. IT Prof. 2018, 20, 15–18. [Google Scholar] [CrossRef]
- Li, Z.; Wang, D. Achieving One-Round Password-based Authenticated Key Exchange over Lattices. IEEE Trans. Serv. Comput. 2019, 8, 1–14. [Google Scholar] [CrossRef]
- Xu, H.; Yu, W.; Liu, X.; Griffith, D.; Golmie, N. On Data Integrity Attacks against Industrial Internet of Things. In Proceedings of the 2020 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Calgary, AB, Canada, 17 August–22 August 2020; pp. 21–28. [Google Scholar]
- Xiong, Z.; Cai, Z.; Takabi, D.; Li, W. Privacy Threat and Defense for Federated Learning with Non-i.i.d. Data in AIoT. IEEE Trans. Ind. Inform. 2021. [Google Scholar] [CrossRef]
- Yu, F.R.; Liu, J.M.; He, Y.; Si, P.B.; Zhang, Y.H. Virtualization for distributed ledger technology (VDLT). IEEE Access 2018, 6, 25019–25028. [Google Scholar] [CrossRef]
- Eyal, I.; Gencer, A.E.; Sirer, E.G.; Renesse, R.V. Bitcoin-NG: A scalable blockchain protocol. In Proceedings of the 13th USENIX Symposium Network System, Santa Clara, CA, USA, 16–18 March 2016; pp. 45–59. [Google Scholar]
- Aitzhan, N.Z.; Svetinovic, D. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streamsm. IEEE Trans. Dependable Secur. Comput. 2018, 15, 840–852. [Google Scholar] [CrossRef]
- Rafael, P.; Elaine, S. FruitChains: A Fair Blockchain. In Proceedings of the ACM Symposium on Principles of Distributed Computing, Washington, DC, USA, 25–27 July 2017; pp. 315–324. [Google Scholar]
- Xu, X.; Weber, I.; Staples, M.; Zhu, L.; Bosch, J.; Bass, L.; Pautasso, C.; Rimba, A. A Taxonomy of Blockchain-based Systems for Architecture Design. In Proceedings of the IEEE International Conference on Software Architecture (ICSA17), Goghenburg, Sweden, 3–7 April 2017; pp. 243–252. [Google Scholar]
- Khaqqi, K.N.; Sikorski, J.J.; Hadinoto, K.; Kraft, M. Incorporating seller/buyer reputation-based system in blockchain-enabled emission trading application. Appl. Energy 2018, 209, 8–19. [Google Scholar] [CrossRef]
- Yang, Z.; Zheng, K.; Yang, K.; Leung, V.C. A blockchain-based reputation system for data credibility assessment in vehicular networks. In Proceedings of the 2017 IEEE 28th PIMRC Symposium, Montreal, QC, Canada, 8–13 October 2017; pp. 1–5. [Google Scholar]
- Schaub, A.; Bazin, R.; Hasan, O.; Brunie, L. A trustless privacy preserving reputation system. In Proceedings of the IFIP International Information Security and Privacy Conference, Ghent, Belgium, 30 May–1 June 2016; pp. 398–411. [Google Scholar]
- Moinet, A.; Darties, B.; Baril, J.-L. Blockchain based trust & authentication for decentralized sensor networks. arXiv 2017, arXiv:1706.01730. [Google Scholar]
- Karati, A.; Islam, S.H.; Biswas, G.P.; Bhuiyan, M.Z.A.; Vijayakumar, P.; Karuppiah, M. Provably secure identity-based signcryption scheme for crowdsourced industrial Internet of things environments. IEEE Internet Things J. 2018, 5, 2904–2914. [Google Scholar] [CrossRef]
- Esposito, C.; Castiglione, A.; Palmieri, F.; Santis, A.D. Integrity for an event notification within the industrial Internet of things by using group signatures. IEEE Trans. Ind. Inform. 2018, 14, 3669–3678. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Choo, K.R.; Wu, W. Efficient hierarchical identity-based signature with batch verification for automatic dependent surveillance-broadcast system. IEEE Trans. Inf. Forensics Secur. 2017, 12, 454–464. [Google Scholar] [CrossRef]
- Bouachir, Q.; Aloquaily, M.; Tesng, L.; Boukerche, A. Blockchain and Fog Computing for Cyberphysical Systems: The Case of Smart Industry. Computer 2020, 53, 36–45. [Google Scholar] [CrossRef]
- Dong, G.; Wang, X. A Secure IoT Data Integrity Auditing Scheme Based on Consortium Blockchain. In Proceedings of the 2020 5th IEEE International Conference on Big Data Analytics(ICBDA), Xianmen, China, 8–11 May 2020; pp. 246–250.
- Urien, P. Proving IoT Devices Firmware Integrity with Bijective MAC Time Stamped. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things(WF-IoT), New Orleans, LA, USA, 2–16 June 2020; pp. 1–2. [Google Scholar]
- Chen, Y.J.; Wang, L.C.; Wang, S. Stochastic Blockchain for IoT Data Integrity. IEEE Trans. Netw. Sci. Eng. 2020, 7, 373–384. [Google Scholar] [CrossRef]
- Cherupally, S.R.; Boga, S.; Podili, P.; Kataoka, K. Lightweight and Scalable DAG based distributed ledger for verifying IoT data integrity. In Proceedings of the 2021 International Conference on Information Networking (ICOIN), Jeju Island, Korea, 13–16 January 2021; pp. 267–272. [Google Scholar]
- Kuo, S.S.; Su, W.T. A Blockchain-Indexted Storage supporting Scalable Data Integrity in Supply Chain Traceability. In Proceedings of the 2020 IEEE International Conference on Smart Internet of Things(SmartIoT), Beijing, China, 14–16 August 2020; pp. 348–349. [Google Scholar]
- Morton, A. Performance Metrics for All. IEEE Internet Comput. 2009, 13, 82–86. [Google Scholar] [CrossRef]









| Classification | Explanation | Example | |
|---|---|---|---|
| Cloud intelligence utilize | Intelligent Cloud Platform Utilization | - Utilization of cognitive services such as vision, language, and machine learning services provided by cloud platforms of global IT companies such as Google, Amazon, IBM, MS, etc. | - Amazon Alexa - Self-driving cars up - Robot Pepper |
| Intelligent IoT Services Cloud Platform Utilization | - Provide intelligent IoT services by adding recognition and analysis capabilities to the service cloud platform built by hardware object manufacturers to provide applied services | - Artificial Intelligence Home Appliances (LG, Samsung) - Interactive Secretary (Bixby, Siri, etc.) | |
| Intelligence of things | Intelligent Engine Mounting Things on board | - Intelligent engine based on learning algorithms (machine learning, deep learning, etc.) is equipped with its own cognitive and thinking capabilities | - Nest Thermostat - MIT Boxster Robot |
| Intelligent Object Platform and Cognitive Tools Utilization | - Utilization of object platforms to be mounted on objects requiring specialized intelligence, such as data analysis and self-driving cars | - IBM Quark - Qualcomm Drive - Data Platform | |
| Parameter | Value |
|---|---|
| The number of server | 1 |
| The number of AIoT | 20 |
| The number of IoT | 300 |
| The transmit/receive power of the | 0.15 W/0.1 W |
| The network coverage radius | 500 m |
| The static circuit power | 0.03W |
| The path loss exponent | 3 |
| The subnet tree depth | 5 |
| The available bandwidth for / | 10 MHz/5 MHz |
| The power of noise | −174 dBm/Hz |
| Subnet storage capacity | 1 TB |
| Input data size | 3 kbits/s |
| Delay threshold | 10 s |
| Link capacity | 10 Gbps |
| Poisson lambda | |
| Data generation span | 10 min |
| Max access count | 100 |
| The unit price of energy | 0.15 Token/J |
| Value | Z. Yang et al. | C. Esposito et al. | D. He et al. | Proposed Scheme |
|---|---|---|---|---|
| 1 | 17.525 | 15.572 | 14.505 | 12.942 |
| 2 | 16.805 | 16.141 | 14.779 | 13.153 |
| 3 | 18.167 | 15.723 | 14.807 | 12.769 |
| 4 | 17.428 | 16.534 | 15.376 | 13.195 |
| 5 | 16.943 | 15.756 | 14.374 | 12.935 |
| 6 | 18.732 | 16.142 | 15.625 | 13.548 |
| 7 | 18.285 | 16.655 | 15.386 | 12.474 |
| 8 | 17.229 | 15.481 | 14.508 | 12.921 |
| 9 | 18.295 | 16.038 | 15.478 | 13.295 |
| Value | Z. Yang et al. | C. Esposito et al. | D. He et al. | Proposed Scheme |
|---|---|---|---|---|
| 1 | 58.32 | 62.39 | 68.58 | 73.25 |
| 2 | 67.59 | 73.01 | 77.19 | 82.07 |
| 5 | 72.48 | 77.36 | 81.27 | 86.49 |
| 10 | 75.06 | 79.18 | 83.92 | 87.43 |
| 15 | 77.36 | 81.65 | 84.72 | 88.25 |
| 20 | 79.15 | 83.09 | 85.14 | 89.08 |
| Value | Z. Yang et al. | C. Esposito et al. | D. He et al. | Proposed Scheme |
|---|---|---|---|---|
| 1 | 43.907 | 37.102 | 28.762 | 22.337 |
| 2 | 46.275 | 40.538 | 30.189 | 23.874 |
| 5 | 50.649 | 45.647 | 37.546 | 28.478 |
| 10 | 54.735 | 50.493 | 39.098 | 35.744 |
| 15 | 62.404 | 53.285 | 44.277 | 38.285 |
| 20 | 66.581 | 55.188 | 47.645 | 42.968 |
| Value | Z. Yang et al. | C. Esposito et al. | D. He et al. | Proposed Scheme |
|---|---|---|---|---|
| 1 | 9.581 | 7.889 | 5.658 | 4.478 |
| 2 | 12.474 | 9.084 | 7.379 | 5.387 |
| 5 | 13.189 | 11.745 | 8.391 | 6.278 |
| 10 | 14.453 | 13.676 | 11.254 | 9.668 |
| 15 | 16.876 | 15.285 | 13.387 | 10.493 |
| 20 | 18.297 | 16.719 | 15.297 | 12.341 |
| Subnet Number | IoT Data Connectivity | |||
|---|---|---|---|---|
| FP | RP | FRP | Proposed Scheme | |
| 2 | 81.636 | 85.195 | 89.949 | 92.321 |
| 4 | 73.693 | 80.699 | 84.686 | 88.789 |
| 6 | 65.452 | 71.593 | 75.768 | 80.476 |
| 8 | 58.345 | 63.874 | 70.837 | 73.468 |
| 10 | 49.067 | 54.938 | 56.105 | 61.302 |
| 12 | 41.524 | 47.834 | 51.852 | 59.407 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sim, S.-H.; Jeong, Y.-S. Multi-Blockchain-Based IoT Data Processing Techniques to Ensure the Integrity of IoT Data in AIoT Edge Computing Environments. Sensors 2021, 21, 3515. https://doi.org/10.3390/s21103515
Sim S-H, Jeong Y-S. Multi-Blockchain-Based IoT Data Processing Techniques to Ensure the Integrity of IoT Data in AIoT Edge Computing Environments. Sensors. 2021; 21(10):3515. https://doi.org/10.3390/s21103515
Chicago/Turabian StyleSim, Sung-Ho, and Yoon-Su Jeong. 2021. "Multi-Blockchain-Based IoT Data Processing Techniques to Ensure the Integrity of IoT Data in AIoT Edge Computing Environments" Sensors 21, no. 10: 3515. https://doi.org/10.3390/s21103515
APA StyleSim, S.-H., & Jeong, Y.-S. (2021). Multi-Blockchain-Based IoT Data Processing Techniques to Ensure the Integrity of IoT Data in AIoT Edge Computing Environments. Sensors, 21(10), 3515. https://doi.org/10.3390/s21103515






