A Secure and Lightweight Authentication Protocol for IoT-Based Smart Homes
Abstract
1. Introduction
1.1. Contributions
- We analyze the security vulnerabilities of Xiang and Zheng’s protocol [6]. To resolve the security drawbacks of their protocol, we propose a secure and lightweight authentication protocol for IoT-based smart homes.
- We demonstrate that our protocol is secure against various kinds of known attacks by reporting on an informal security analysis.
- We conducted formal analysis using the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool [7,8,9], Burrows–Abadi–Needham (BAN) logic [10], and the real or random (ROR) model [11]. With the formal analysis, we proved secure mutual authentication, the session key security, and the resistance against MITM and replay attacks of our protocol.
- We provide a comparison of performance and security properties between our protocol and related protocols. The results show that our protocol provides better security and computational costs compared to related protocols.
1.2. Adversary Model
- can eavesdrop, intercept, inject, replay, and modify transmitted messages via a public channel and then can perform MITM, replay, impersonation attacks, etc. [17].
- can access short-term keys, long-term keys, and session states of each party.
1.3. Organization
2. Related Works
3. System Model
4. Review of Xiang and Zheng’s Protocol
4.1. Smart Device Registration Phase
4.2. Authentication and Key Agreement Phase
4.2.1. Low Security Risk
- Step 1:
- computes and extracts current timestamp . Then calculates and . Finally, sends to , where is the header of the message through an insecure channel.
- Step 2:
- Upon receiving the message at timestamp , knows the current security risk level is low from the message header. also computes and checks if and . If it is not equal, the authentication process will be aborted. Then, computes and extracts the current timestamp . also computes and . Finally, sends to , where is the header of the message . computes the session key for the future data communication.
- Step 3:
- After receiving at timestamp , computes , , and . Then, checks if and . If it is correct, computes the session key and adds to the trusted device list.
4.2.2. High Security Risk
- Step 1:
- computes , and generates a random number . After that, extracts a current timestamp , and computes and . Then, sends the message to , where is the message header of through a public channel.
- Step 2:
- After getting at timestamp , knows the security risk level is high from the header of . then computes and . After that, checks whether and . If the check is failed, the authentication process will be terminated. Otherwise, computes and generates a random number . Then, extracts the current timestamp , and computes and . Finally, sends the message to , where is the message header of , and computes the session key .
- Step 3:
- Upon receiving at timestamp , computes , , and . Then, checks whether and . If it is correct, computes the session key and adds to the trusted device list.
5. Cryptanalysis of Xiang and Zheng’s Protocol
5.1. Stolen Smart Device Attack
5.2. Impersonation Attack
5.2.1. Low Security Risk
- Step 1:
- With the obtained secret credentials from and from the previous session, can send the message .
- Step 2:
- Upon getting , computes and extracts the current timestamp . After that, computes and , and sends the message .
- Step 3:
- After receiving , computes and . Then, verifies the validity of and . If it is equal, computes and generates the current timestamp . After that, computes and . Finally, sends the message to and computes the session key .
- Step 4:
- Upon getting , computes , , and . After that, checks the validity of and . If it is equal, computes .
5.2.2. High Security Risk
- Step 1:
- can send to using obtained secret credentials and .
- Step 2:
- Upon getting , calculates and generates a random number . After that, extracts the current timestamp , and computes and . Then, sends .
- Step 3:
- After receiving , computes and . Then, verifies the validity of and . If all checks pass, computes , generates a random number , and extracts the current timestamp . After that, computes , , and . Finally, sends to .
- Step 4:
- Upon getting , computes , , and . Then, checks the validity of and . If it is equal, computes .
5.3. Session Key Disclosure Attack
5.4. Mutual Authentication
6. Proposed Protocol
6.1. Initialization Phase
6.2. Registration Phase
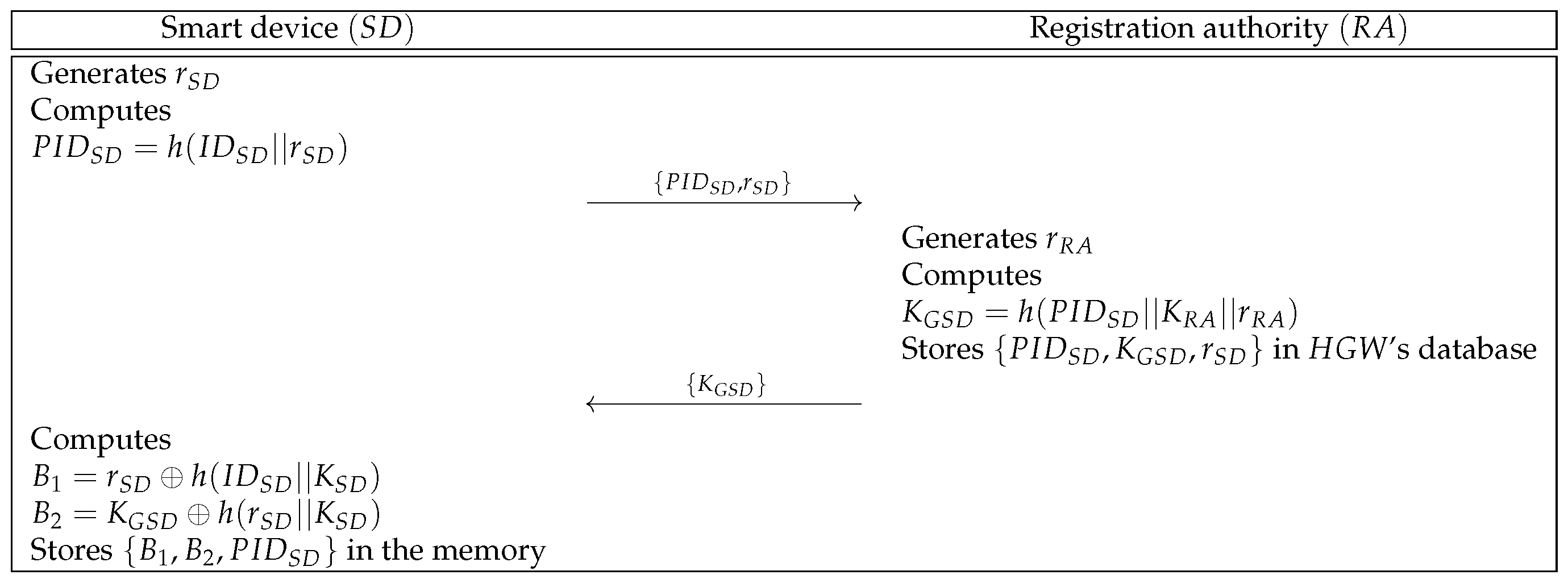
6.2.1. Smart Device Registration Phase
- Step 1:
- generates a random number and computes . Then, sends to through a secure channel.
- Step 2:
- Upon getting the message, generates and computes . Then, stores in ’s database and sends to over a secure channel. After that, makes public.
- Step 3:
- After receiving the message, computes and . Then, stores in the memory.
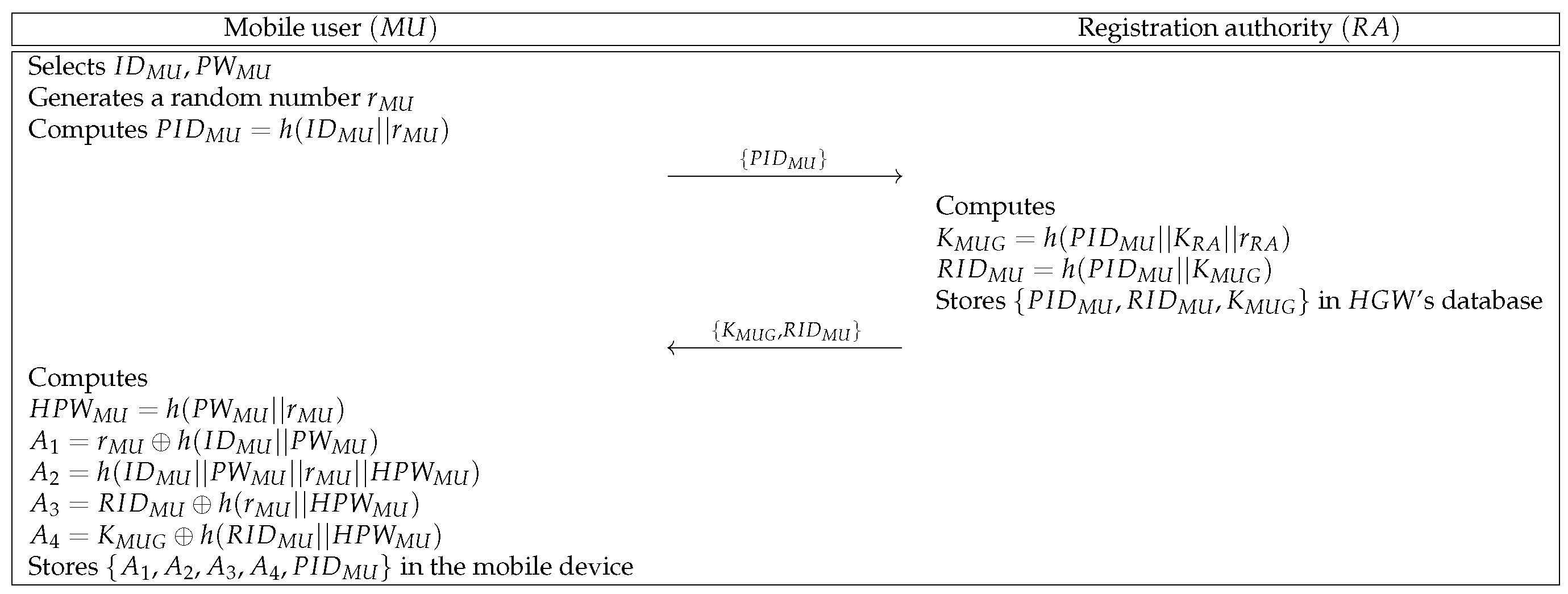
6.2.2. Mobile User Registration Phase
- Step 1:
- selects identity and password and generates a random number . Then, computes and sends to through a secure channel.
- Step 2:
- Upon receiving the message, computes and . Then, stores in ’s database and sends to via a secure channel.
- Step 3:
- After receiving the message, computes , , , , and . Then, stores in the mobile device.
6.3. Authentication and Key Agreement Phase
- Step 1:
- inputs identity and password and computes , , and . Then, checks if . If this condition is satisfied, generates a random nonce and computes , , , , and . After that, sends to through a public channel.
- Step 2:
- Upon getting the message, retrieves and corresponding to , and computes and . checks if . If it is equal, retrieves and corresponding to . Then, generates a random nonce and computes , , , , and . Finally, sends to .
- Step 3:
- After receiving the message, computes , , , and . checks if . If this condition is valid, generates a random nonce . Then, computes , , , and . Finally, sends to .
- Step 4:
- Upon receiving the message, computes and . checks if . Then, computes , , and , and computes and .stores with in ’s database. Finally, sends to .
- Step 5:
- After receiving the message, computes , and . checks if . After that, computes . Then, updates , , and . Then, replaces to in the mobile device. computes and sends to .
- Step 6:
- After receiving the message from , computes and checks if . If it is correct, deletes {} in the database.
6.4. Password Update Phase
- Step 1:
- inputs identity and old password to the mobile device over a secure channel.
- Step 2:
- Mobile device computes , , and . Then, the mobile device checks whether . If this condition is met, the mobile device sends the authentication message to .
- Step 3:
- Upon receiving the authentication message, inputs the new password to the mobile device.
- Step 4:
- After getting the new password, the mobile device computes , , , , , , and . Finally, the mobile device replaces with .
7. Security Analysis
7.1. Informal Security Analysis
7.1.1. Mobile User Impersonation Attack
7.1.2. Home Gateway Impersonation Attack
7.1.3. Smart Device Impersonation Attack
7.1.4. Session Key Disclosure Attack
7.1.5. Replay and MITM Attack
7.1.6. Offline Guessing Attack
7.1.7. Stolen Smart Device Attack
7.1.8. Privileged-Insider Attack
7.1.9. Known Session-Secret Temporary Information Attack
7.1.10. Desynchronization Attack
7.1.11. Perfect Forward Secrecy
7.1.12. Mutual Authentication
7.1.13. Anonymity and Untraceability
7.2. BAN Logic
7.2.1. Rules
- Message meaning rule ():
- Nonce verification rule ():
- Jurisdiction rule ():
- Freshness rule ():
- Belief rule ():
7.2.2. Goals
- Goal 1:
- .
- Goal 2:
- .
- Goal 3:
- .
- Goal 4:
- .
7.2.3. Assumptions
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
7.2.4. Idealized Forms
- :
- :
- :
- :
7.2.5. Proof
- Step 1:
- From , we can obtain .
- Step 2:
- Using and with , we can get .
- Step 3:
- can obtained using and with .
- Step 4:
- Using and with , we can get .
- Step 5:
- We can obtain from .
- Step 6:
- can obtained using and with .
- Step 7:
- Utilizing and with , we can get .
- Step 8:
- For obtaining , we can use and with .
- Step 9:
- From , we can obtain .
- Step 10:
- For getting , we can utilize and with .
- Step 11:
- For obtaining , we can use and with .
- Step 12:
- Using and with , we can get .
- Step 13:
- We can get from .
- Step 14:
- can obtained using and with .
- Step 15:
- can obtained using and with .
- Step 16:
- Using and with , we can get .
- Step 17:
- Since the session key is , we can obtain from , , and .
- Step 18:
- From , , and , we can get .
- Step 19:
- can obtained from and .
- Step 20:
- can obtained using and .
7.3. ROR Model
- : performs this query to obtain transmitted messages over a public channel between , , and .
- : This query represents that can extract sensitive information stored in the mobile device of .
- : This query is that reveals the current session key between and . If an adversary cannot reveal the session key between and using the query, then is secure.
- : With this query, can send the message M to and receive a response message.
- : Before the start of the game, a fair coin is tossed and the result becomes only known to . uses this result to make a decision of the query. If runs the query and the session key is fresh, returns for = 1 or a random number for = 0. Otherwise, it returns a null (⊥).
7.3.1. Security Proof
- : This game allows to execute the real attack against the proposed protocol. chooses a random bit at the beginning of . Then, we obtain the following in accordance with this game.
- : In this game, runs the query and eavesdrops transmitted messages , , , and . Then, executes and queries to validate whether the derived session key is real or not. In our protocol, the session key is constructed as . To derive the session key, needs to know the identities and random nonces of , , and . Consequently, there are no instances in which increases ’s winning probability. Therefore, and turn out to be indistinguishable, and we can obtain the following.
- : To obtain the session key, performs and queries in this game. can perform an active attack by modifying exchanged messages. However, all exchanged messages are constructed with secret credentials and random nonces, and protected using one-way hash function . In addition, is difficult to derive secret credentials and random nonces because it is a computationally infeasible problem according to the property of . Hence, we can get the following result through the use of birthday paradox [44].
- : In the final game , can try to get the session key with the query. By the query, can extract sensitive values stored in the mobile device of . Sensitive values are expressed as , , , and . Since has no knowledge of and , cannot derive secret values and from the extracted values. Besides, it is a computationally infeasible task for to guess and simultaneously. In conclusion, and are indistinguishable. By utilizing Zipf’s law, the following result can be obtained.As all games have been run, must guess the bit for winning the game. Therefore, we can obtain the following result.From Equations (1) and (2), we obtain the result as follows.With Equations (5) and (6), we derive the below equation.By using the triangular inequality, we can have the following result with Equations (4), (5), and (7).Finally, by multiplying both sides of Equation (8) by two, we can obtain the required result.
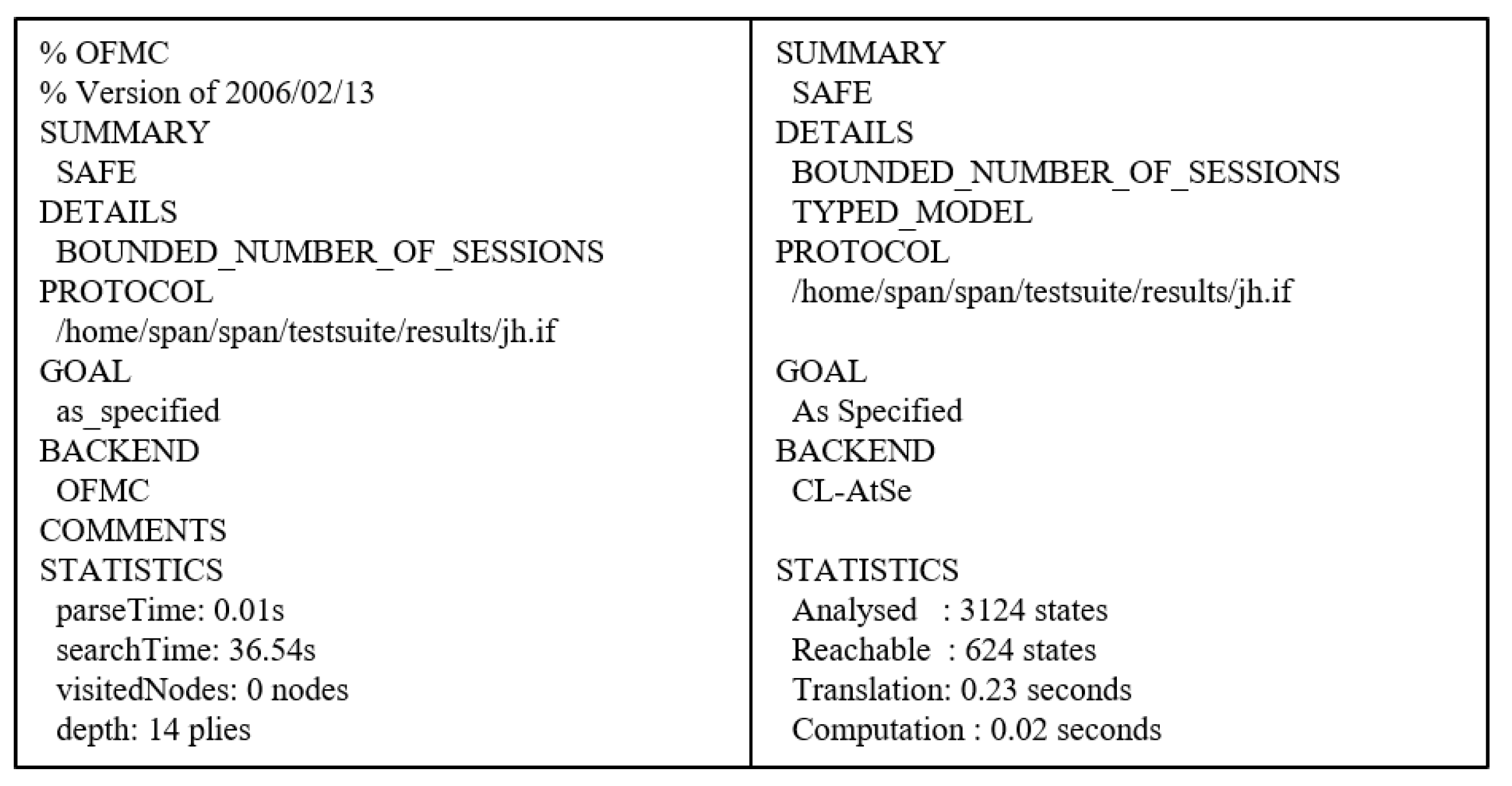
7.4. AVISPA Tool
7.4.1. Specifications of the Proposed Protocol
7.4.2. Result of AVISPA
8. Performance and Security Analyses
8.1. Computational Costs
8.2. Communication Costs
8.3. Security Properties
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Shin, S.; Kwon, T. A lightweight three-factor authentication and key agreement scheme in wireless sensor networks for smart homes. Sensors 2019, 19, 2012. [Google Scholar] [CrossRef] [PubMed]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Lightweight and secure password based smart home authentication protocol: LSP-SHAP. J. Netw. Syst. Manag. 2019, 27, 1020–1042. [Google Scholar] [CrossRef]
- Baruah, B.; Dhal, S. A two-factor authentication scheme against FDM attack in IFTTT based smart home system. Comput. Secur. 2018, 77, 21–35. [Google Scholar] [CrossRef]
- Kumar, P.; Gurtov, A.; Iinatti, J.; Ylianttila, M.; Sain, M. Lightweight and secure session-key establishment scheme in smart home environments. IEEE Sens. J. 2015, 16, 254–264. [Google Scholar] [CrossRef]
- Kumar, P.; Braeken, A.; Gurtov, A.; Iinatti, J.; Ha, P.H. Anonymous secure framework in connected smart home environments. IEEE Trans. Inf. Forensics Secur. 2017, 12, 968–979. [Google Scholar] [CrossRef]
- Xiang, A.; Zheng, J. A situation-aware scheme for efficient device authentication in smart grid-enabled home area networks. Electronics 2020, 9, 989. [Google Scholar] [CrossRef]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispa-project.org/ (accessed on 10 November 2020).
- SPAN: A Security Protocol Animator for AVISPA. Available online: http://www.avispa-project.org/ (accessed on 10 November 2020).
- Mandal, S.; Bera, B.; Sutrala, A.K.; Das, A.K.; Choo, K.R.; Park, Y. Certificateless-signcryption-based three-factor user access control scheme for IoT environment. IEEE Internet Things J. 2020, 7, 3184–3197. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password based authenticated key exchange in the three-party setting. In Public Key Cryptgraphy; Springer: Les Diablerets, Switzerland, 2005; pp. 65–84. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Lee, J.; Yu, S.; Kim, M.; Park, Y.; Das, A.K. On the design of secure and efficient three-factor authentication protocol using honey list for wireless sensor networks. IEEE Access 2020, 8, 107046–107062. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Lee, K.; Park, K.; Park, Y. Secure authentication protocol for wireless sensor networks in vehicular communications. Sensors 2018, 18, 3191. [Google Scholar] [CrossRef] [PubMed]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In International Conference on the Theory and Applications of Cryptographic Thechniques (EUROCRYPT’02); Springer: Amsterdam, The Netherlands, 2002; pp. 337–351. [Google Scholar]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.P.C.; Park, Y. AKM-IoV: Authenticated key management protocol in fog computing-based internet of vehicles deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Park, Y.; Park, Y.; Lee, S.; Chung, B. A secure and efficient three-factor authentication protocol in global mobility networks. Appl. Sci. 2020, 10, 3565. [Google Scholar] [CrossRef]
- Roy, S.; Chatterjee, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Vasilakos, A.V. On the design of provably secure lightweight remote user authentication scheme for mobile cloud computing services. IEEE Access 2017, 5, 25808–25825. [Google Scholar] [CrossRef]
- Park, K.; Park, Y.; Park, Y.; Das, A.K. 2PAKEP: Provably secure and efficient two-party authenticated key exchange protocol for mobile environment. IEEE Access 2018, 6, 30225–30241. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Alhakami, H.; Baz, A.; Al-Turjman, F. Securing demand response management: A certificate-based access control in smart grid edge computing infrastructure. IEEE Access 2020, 8, 101235–101243. [Google Scholar] [CrossRef]
- Park, K.; Noh, S.; Lee, H.; Das, A.K.; Kim, M.; Park, Y.; Wazid, M. LAKS-NVT: Provably secure and lightweight authentication and key agreement scheme without verification table in medical internet of things. IEEE Access 2020, 8, 119387–119404. [Google Scholar] [CrossRef]
- Ul Haq, I.; Wang, J.; Zhu, Y. Secure two-factor lightweight authentication protocol using self-certified public key cryptography for multi-server 5G networks. J. Netw. Comput. Appl. 2020, 161, 102660. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.P.; Khan, M.K.; Kumar, N. A robust and anonymous patient monitoring system using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 80, 483–495. [Google Scholar] [CrossRef]
- Chandrakar, P.; Om, H. A secure and robust anonymous three-factor remote user authentication scheme for multi-server environment using ECC. Comput. Commun. 2017, 110, 26–34. [Google Scholar] [CrossRef]
- Santoso, F.K.; Vun, N.C.H. Securing IoT for smart home system. In Proceedings of the 2015 International Symposium on Consumer Electronics (ISCE), Madrid, Spain, 24–26 June 2015; pp. 1–2. [Google Scholar]
- Fakroon, M.; Alshahrani, M.; Gebali, F.; Traore, I. Secure remote anonymous user authentication scheme for smart home environment. Internet Things 2020, 9, 100158. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Rodrigues, J.J.P.C.; Park, Y. Physically secure lightweight anonymous user authentication protocol for internet of things using physically unclonable functions. IEEE Access 2019, 7, 85627–85644. [Google Scholar] [CrossRef]
- Dey, S.; Hossian, A. Session-key establishment and authentication in a smart home network using public key cryptography. IEEE Sens. Lett. 2019, 3, 7500204. [Google Scholar] [CrossRef]
- Gaba, G.S.; Kumar, G.; Monga, H.; Kim, T.; Kumar, P. Robust and lightweight mutual authentication scheme in distributed smart environments. IEEE Access 2020, 8, 69722–69733. [Google Scholar] [CrossRef]
- Kumar, P.; Chouhan, L. A privacy and session key based authentication scheme for medical IoT networks. Comput. Commun. 2021, 166, 154–164. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Vaidya, B.; Park, J.H.; Yeo, S.S.; Rodrigues, J.J. Robust one-time password authentication scheme using smart card for home network environment. Comput. Commun. 2011, 34, 326–336. [Google Scholar] [CrossRef]
- Kim, H.J.; Kim, H.S. AUTH HOTP-HOTP based authentication scheme over home network environment. In International Conference on Computational Science and Its Applications; Springer: Berlin/Heidelberg, Germany, 2011; pp. 622–637. [Google Scholar]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure remote user authenticated key establishment protocol for smart home environment. IEEE Trans. Dependable Secur. Comput. 2017, 17, 391–406. [Google Scholar] [CrossRef]
- Lyu, Q.; Zheng, N.; Liu, H.; Gao, C.; Chen, S.; Liu, J. Remotely access “my” smart home in private: An anti-tracking authentication and key agreement scheme. IEEE Access 2019, 7, 41835–41851. [Google Scholar] [CrossRef]
- Poh, G.S.; Gope, P.; Ning, J. Privhome: Privacy-preserving authenticated communication in smart home environment. IEEE Trans. Dependable Secur. Comput. 2019. [Google Scholar] [CrossRef]
- Irshad, A.; Usman, M.; Chaudry, S.A.; Bashir, A.K.; Jolfaei, A.; Srivastava, G. Fuzzy-in-the-loop-driven low-cost and secure biometric user access to server. IEEE Trans. Reliab. 2020. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Park, Y. An efficient, anonymous and robust authentication scheme for smart home environments. Sensors 2020, 20, 1215. [Google Scholar] [CrossRef]
- AL-Turjman, F.; Deebak, D.B. Seamless authentication: For IoT-big data technologies in smart industrial application systems. IEEE Trans. Ind. Inf. 2020. [Google Scholar] [CrossRef]
- Lee, J.; Yu, S.; Park, K.; Park, Y.; Park, Y. Secure three-factor authentication protocol for multi-gateway IoT environments. Sensors 2019, 19, 2358. [Google Scholar] [CrossRef] [PubMed]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Park, K.; Park, Y.; Das, A.K.; Yu, S.; Lee, J.; Park, Y. A dynamic privacy-preserving key management protocol for V2G in social internet of things. IEEE Access 2019, 7, 76812–76832. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Park, K.; Das, A.K.; Park, Y. IoV-SMAP: Secure and efficient message authentication protocol for IoV in smart city environment. IEEE Access 2020, 8, 167875–167886. [Google Scholar] [CrossRef]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-authenticated key exchange using Diffie-Hellman. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; pp. 156–171. [Google Scholar]
- Vigano, L. Automated security protocol analysis with the AVISPA tool. Electron. Notes Theor. Comput. Sci. 2006, 155, 61–86. [Google Scholar] [CrossRef]
- Mo, J.; Chen, H. A lightweight secure user authentication and key agreement protocol for wireless sensor networks. Secur. Commun. Netw. 2019, 2019, 2136506. [Google Scholar] [CrossRef]





| Notation | Description |
| Mobile user | |
| Home gateway | |
| Smart device | |
| Registration authority | |
| Identity of | |
| Identity of | |
| Identity of | |
| Pseudo identity of | |
| Pseudo identity of | |
| Password of | |
| Master key of | |
| Secret key of | |
| Shared secret key between and | |
| Shared secret key between and | |
| , , , , , | Random number |
| Session key between and | |
| One-way hash function | |
| Symmetric encryption/decryption using key K | |
| ⊕ | XOR operation |
| Concatenation operation | |
| T | Timestamp |
| Maximum transmission delay | |
| Message header at the low/low security risk |
| Notation | Description |
| Secret key | |
| Wbelieves statement S | |
| Statement S is fresh | |
| Wreceives statement S | |
| W once said S | |
| Wcontrols statement S | |
| Statement S is combined with secret statement T | |
| Statement S is masked by | |
| W and N share to communicate with each other | |
| is known only to W, N, and trusted principals of W and N |
| Protocol | Total | Computational Costs |
| Shuai et al. [31] | 22.0651 ms | |
| Wazid et al. [34] | 7.8841 ms | |
| Banerjee et al. [38] | 7.3633 ms | |
| Xiang and Zheng [6] | Low-security risk: | 0.0044 ms |
| High-security risk: | 0.5256 ms | |
| Ours | 0.0168 ms |
| Protocol | Communication Costs | Number of Messages |
| Shuai et al. [31] | (960 + 320 + 320 + 320) = 1920 bits | 4 |
| Wazid et al. [34] | (480 + 960 + 512 + 1408) = 3360 bits | 4 |
| Banerjee et al. [38] | (448 + 320 + 320 + 320) = 1408 bits | 4 |
| Xiang and Zheng [6] | Low-security risk: (132 + 324 + 324) = 780 bits | 3 |
| High-security risk: (132 + 676 + 676) = 1484 bits | 3 | |
| Ours | (640 + 640 + 320 + 320 + 160) = 2080 bits | 5 |
| Security Properties | [31] | [34] | [38] | [6] | Ours |
|---|---|---|---|---|---|
| Impersonation attack | ∘ | ∘ | ∘ | × | ∘ |
| Session key disclosure attack | ∘ | ∘ | ∘ | × | ∘ |
| Replay attack | ∘ | ∘ | ∘ | ∘ | ∘ |
| MITM attack | ∘ | ∘ | ∘ | ∘ | ∘ |
| Off-line guessing attack | × | ∘ | ∘ | ∘ | ∘ |
| Stolen smart device attack | - | - | - | × | ∘ |
| Privileged-insider attack | ∘ | ∘ | ∘ | × | ∘ |
| Known session-secret temporary information attack | - | - | ∘ | × | ∘ |
| Desynchronization attack | ∘ | × | - | × | ∘ |
| Perfect forward secrecy | × | × | - | × | ∘ |
| Mutual authentication | ∘ | ∘ | ∘ | × | ∘ |
| Anonymity | ∘ | × | × | × | ∘ |
| Untraceability | ∘ | ∘ | × | × | ∘ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oh, J.; Yu, S.; Lee, J.; Son, S.; Kim, M.; Park, Y. A Secure and Lightweight Authentication Protocol for IoT-Based Smart Homes. Sensors 2021, 21, 1488. https://doi.org/10.3390/s21041488
Oh J, Yu S, Lee J, Son S, Kim M, Park Y. A Secure and Lightweight Authentication Protocol for IoT-Based Smart Homes. Sensors. 2021; 21(4):1488. https://doi.org/10.3390/s21041488
Chicago/Turabian StyleOh, JiHyeon, SungJin Yu, JoonYoung Lee, SeungHwan Son, MyeongHyun Kim, and YoungHo Park. 2021. "A Secure and Lightweight Authentication Protocol for IoT-Based Smart Homes" Sensors 21, no. 4: 1488. https://doi.org/10.3390/s21041488
APA StyleOh, J., Yu, S., Lee, J., Son, S., Kim, M., & Park, Y. (2021). A Secure and Lightweight Authentication Protocol for IoT-Based Smart Homes. Sensors, 21(4), 1488. https://doi.org/10.3390/s21041488






