4.2. Numerical Results and Analysis
In this section, the detailed experimental results are reported. To investigate the performance of each algorithm in different situations, the number of users is set to 30, 45, and 60, respectively.
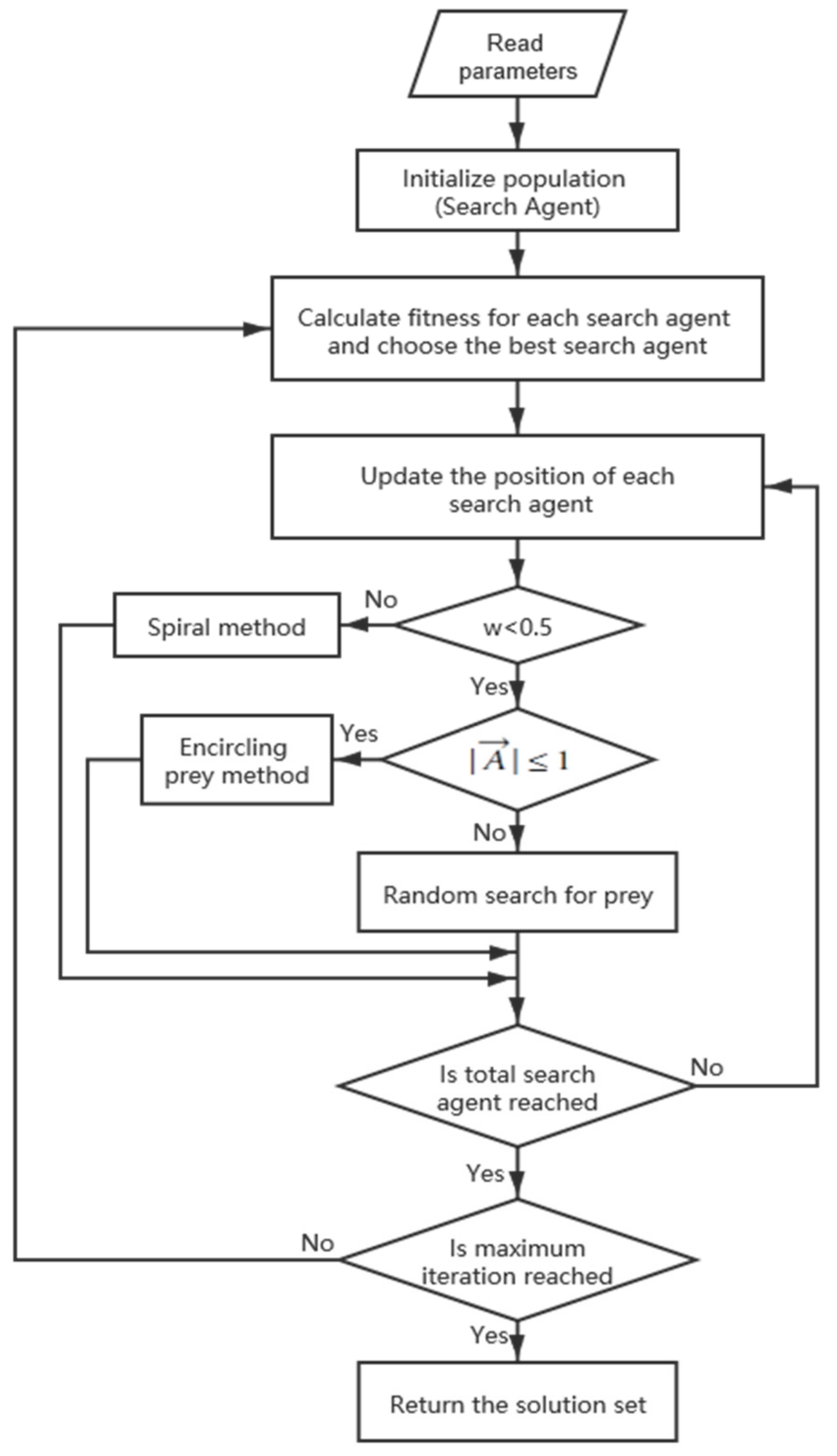
To better examine the MOWOA proposed, the result of our method is compared with that of GrEA, MOEA/D-DE, MOEA/D-DRA, NSGA-III, e-MOEA, and CGbAIS. The iteration times of all algorithms is set to 30. The quantity of search agents of MOWOA and MOWOA2 is 100. The capacity of external archives of MOWOA and MOWOA2 is 30. Correspondingly, the amount of search agents of GrEA, NSGA-III, and e-MOEA is 30, and all these three algorithms are employed with real number coding. For MOEA/D-DE and MOEA/D-DRA, the probability that parent solutions are selected from the neighborhood is 0.9. Additionally, the maximal number of solutions replaced by a child solution is two. Both MOEA/D-DE and MOEA/D-DRA are employed with the penalty-based boundary intersection (PBI) [
53] to disintegrate. As for CGbAIS, population size is set as 100; memory capacity is set as 30; crossover probability is set as 0.4; the diversity evaluation parameter is set as 0.95; the number of iterations is set as 30.
The different performances of these algorithms when the user number is 30, 45, and 60, respectively, are shown in
Table 3,
Table 4 and
Table 5. To be specific, it includes min/mean time and energy required to obtain the result and the Spacing and HV of the solution set. It should note that when the user number is 30, 45, and 60, respectively, the reference point of computing HV is (1.28, 450), (1.84, 900), and (2.38, 800), respectively. The mean values of time and energy consumption are obtained by performing 100 experiments.
From
Table 3, MOWOA2 has a better result than the other algorithms from analysis of the time and energy consumption, which is 1.1918 for the shortest time and 4.6888 × 10
−18 for the lowest energy. This value has a huge difference in magnitudes from the results of other algorithms.
Table 3 and
Table 4 represent that the lowest energy consumption and average energy consumption of MOWOA are better than the other algorithms except for MOWOA2, while MOWOA2 has the best time and energy consumption.
Additionally, an interesting phenomenon is found by comparing
Table 3,
Table 4 and
Table 5. As the user number increases, the time consumption has the tendency to increase; however, the energy consumption seems not to obey the rule. In particular, the minimum and mean energy consumption are 13.9848 and 161.6287, respectively, when the user number is 60. While the values are 32.3088 and 261.5592, respectively, when the user number is 45 can be seen. It can be supposed that the energy consumption is not a linear relation with the increase in user number.
It can be shown from
Table 3,
Table 4 and
Table 5 that when user number is 30, 45, and 60, the HV value of the MOWOA is 28.6767, 104.9165, and 132.8395, higher than other algorithms except MOWOA2. It means the MOWOA has better convergence and multiformity than other algorithms. Moreover,
Table 3,
Table 4 and
Table 5 represent the HV value of MOWOA2 as 35.3101, 122.7615, and 132.9202, respectively, in the corresponding situation. That means that the improved whale optimization algorithm, MOWOA2, will further exploit its advantages, and its overall performance is much better than the other algorithms. Additionally, it can be seen that the HV index of the MOEA/D-DE, MOEA/D-DRA and e-MOEA algorithms is very poor, all of which rank at the bottom in all three cases. The reason is that these three algorithms based on decomposition strategy can achieve good results by decomposing the optimization of many objectives, which shows that the convergence and diversity of the solution sets obtained by them are not good. It suggests that the decomposition strategy is not appropriate for this problem.
Then, it can be seen from
Table 3,
Table 4 and
Table 5 that, when the number of users is 30 and 45, the Spacing value of the solution set of e-MOEA is the best, with values of 0.0375 and 0.0129, respectively. When the number of users is 60, the Spacing index for the MOEA/D-DE solution set is the best, at 0.0352. This shows that the two algorithms perform well in the aspect of uniformity. In these three cases, the Spacing indexes of the CGbAIS solution set are 4.7710, 2.9393 and 0.8152, respectively, which are almost all the worst. This indicates that the uniformity of CGbAIS is not good. Considering the structure of the CGbAIS algorithm, this algorithm adopts the maximum and minimum distance method, which can group the solutions based on distance. Then, some solutions with near distance are deleted from grouped solutions and only one solution is reserved, to simplify the solution set. However, this also leads to a decrease in uniformity. When the number of users is 30, MOWOA2 and MOWOA are not too bad for uniformity, with Spacing of 0.1658 and 0.2797, respectively, ranking third and fourth among the eight algorithms. However, as the user size increases, they tend to show worse uniformity. With the increase in the number of users, the space of the feasible domain increases, resulting in a larger distance between the solutions obtained by the MOWOA2 and MOWOA. Therefore, the Spacing indexes obtained by the two algorithms are higher than those of other algorithms.
In order to make the conclusion more intuitive and convincing, statistical methods were introduced. Single-sample
t-tests were used to examine significant differences be-tween the Spacing and HV of MOWOA2 and other algorithm metrics. As performing single-sample
t-test needs to meet normality distribution, the normality test of the sample was per-formed on all the other algorithms indexes except MOWOA2, which was used as a reference value. When the number of samples is small, the results of normality test should be measured by using the Kolmogorov–Smirnov (K-S) index. The results of normality tests are shown in
Table 6.
As shown in
Table 6, Sig values are 0.2 and 0.174, both of which are larger than 0.05. Therefore, they obey normal distribution, which meets the condition of a single sample
t-test. Furthermore, the Sig value of Spacing is 0.001 < 0.05 when the number of users is 30, which does not conform to the normal distribution, so the single sample
t-test cannot be used.
The single-sample
t-test was then used to examine the significant differences, with 95% confidence intervals selected by default. As can be seen from
Table 7, all Sig.(two-tailed) values of all test results for these indicators are less than 0.05, so it is considered that the test value is significantly different from the sample mean. The Spacing and HV indexes of MOWOA2 are significantly different from those of other algorithms.
Time and energy consumption obtained by the different algorithms when the user number is 30, 45 and 60 are shown in
Figure 3,
Figure 4 and
Figure 5, respectively. They indicate the differences in convergence and diversity among different algorithms. Compared with the solution sets of the other algorithms, the solution sets of both MOWOA and MOWOA2 are distributed on the lower left in the three Figures, which show that MOWOA and MOWOA2 are closer to the Pareto optimal front. Therefore, the two algorithms proposed in this paper have the advantages in convergence and diversity. In addition, in terms of convergence, the two algorithms perform equally and, in terms of diversity, the position of a redpoint is near to the abscissa axis in
Figure 3,
Figure 4 and
Figure 5, which indicates MOWOA2 improved by using the gravity reference point method can enhance the ability of exploration. Therefore, MOWOA2 is better than MOWOA.
From
Figure 3, it can be seen that the shape of the solution sets obtained by these algorithms in the target function space are different. The shape of the solution sets of MOEA/D-DRA resembles a cloud, which means the convergence of the algorithm is the worst of all algorithms. The lines of the solution sets of MOWOA and MOWOA2 are apparently much closer to the Pareto Front. In addition, although the graphs obtained by other algorithms appear linear, they are far away from the Pareto Front, indicating that their solution set is not optimal.
From
Figure 4, the shape of the solution sets of both GrEA and MOEA/D-DRA are divergent, which shows the convergence of the algorithms is worse than that of other algorithms. The lines of the solution sets of MOWOA and MOWOA2 are apparently much closer to the Pareto Front. Although the shape of the solution set obtained by NSGA-III is also linear, it is inferior to our proposed algorithms. Moreover, the graphs obtained by CGbAIS, e-MOEA and MOEA/D-DE appear relatively concentrated, which indicates that the diversity is poor, and it is far away from Pareto Front, which also indicates that the convergence is poor.
From
Figure 5, the shape of the solution sets of MOEA/D-DRA and e-MOEA are slightly divergent and far away from Pareto Front when the user number is 60, which shows that the convergence of the algorithms is worse than that of other algorithms. The lines of the solution sets of MOWOA and MOWOA2 are apparently much closer to the Pareto Front. Although the shape of the solution set obtained by NSGA-III is also linear, it is inferior to our proposed algorithms. Furthermore, the graphs obtained by CGbAIS, e-MOEA and MOEA/D-DE appear relatively concentrated, which indicates that the diversity is poor, and it is, which also indicates that the convergence is poor.
From
Figure 6,
Figure 7,
Figure 8,
Figure 9,
Figure 10 and
Figure 11, the box figures of the solution sets of energy and time consumption are shown when the user number is 30, 45, and 60, respectively. The red line is the average energy consumption of different solution sets by different algorithms. The diversity of solution sets can be objectively judged according to the length of the blue rectangles. The box figures of energy consumption obtained by different algorithms for different numbers of users can be seen from
Figure 6,
Figure 7 and
Figure 8, The box figures of time consumption obtained by different algorithms for different numbers of users can be seen from
Figure 9,
Figure 10 and
Figure 11.
The average energy consumptions of the solution sets obtained by MOWOA and MOWOA2 are obviously lower than that obtained by other algorithms. The average time consumption of the solution sets obtained by MOWOA2 is obviously lower than that obtained by other algorithms.
The length of the rectangles obtained by MOWOA2 is obviously longer than that obtained by other algorithms, which indicates the diversity of the solution sets of MOWOA2 is excellent. In particular, the length of the rectangles obtained by MOWOA2 is longer than that of MOWOA, which means the diversity of MOWOA2 is better than MOWOA when applying the gravity reference point method.
In
Figure 6, it can be seen that the average energy consumption of the solution sets of MOWOA is the lowest, and that of MOWOA2 is the second-lowest when the user number is 30. However, it does not show that the average energy consumption of the solution sets obtained by MOWOA2 is worse than that of MOWOA. In fact, it can be seen from
Figure 9 that the average time consumption of the solution sets of MOWOA2 is the lower than that of MOWOA when the user number is 30. As mentioned in the previous part of the article, time and energy consumption are mutually exclusive targets. The solution set of MOWOA2 trades higher energy consumption for lower time consumption.
In
Figure 6 and
Figure 9, although the time consumption of GrEA is slightly lower than that of MOWOA2 when the number of users is 30, the energy consumption of GrEA is much higher than that of MOWOA2.
In
Figure 8 and
Figure 11, When the user number is 60, it shows that the average time and energy consumption of the solution sets of MOWOA and MOWOA2 are almost the same, both of which are better than other algorithms.
It can be observed from these figures that time consumption and energy consumption of the solution sets obtained by MOEA/D-DE, MOEA/D-DRA, GrEA, e-MOEA, NSGA-III, and CGbAIS are worse than that obtained by MOWOA and MOWOA2 under the three different settings.
To sum up, we can conclude that MOWOA2 applied to computation offloading mechanism optimization has excellent performance on convergence and diversity.