Acceleration of Inner-Pairing Product Operation for Secure Biometric Verification †
Abstract
1. Introduction
1.1. Related Works
1.2. Contributions
- We propose a new algorithm that accelerates inner-pairing product computation when one of the two input vectors are fixed. For each element in this fixed vector, we apply the precomputation method that was originally proposed for a single pairing in [34]. In addition, we reduce the overall computational complexity by sharing overlapping operations for multiple pairings, as in [31].
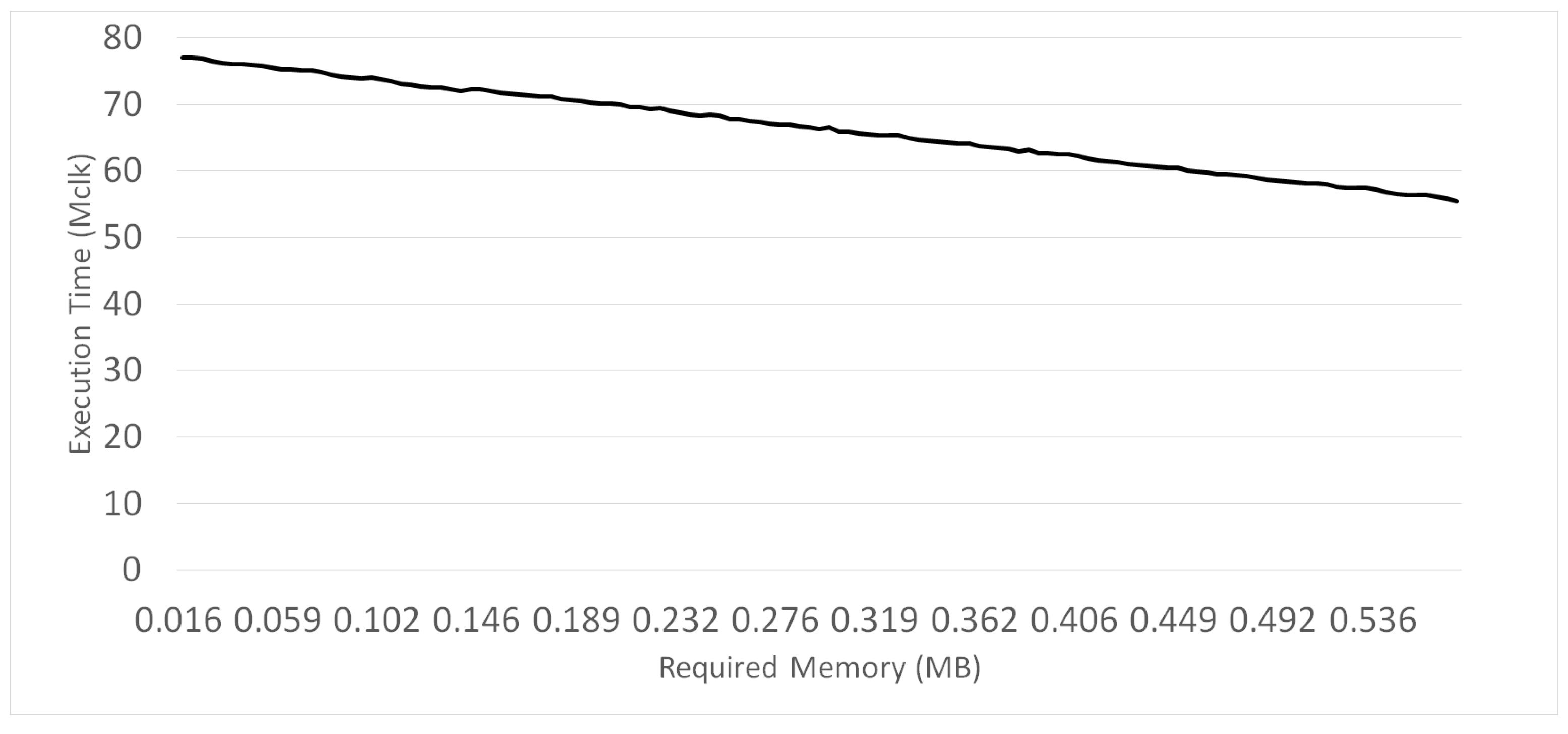
- To handle the situation where the memory is not sufficient to store all the precomputed data for all vector elements, we also propose an adaptive method that can adjust the number of precomputed elements. Therefore, the performance of the proposed method can be fine-tuned adaptively by selectively storing the precomputed elements according to the storage capacity.
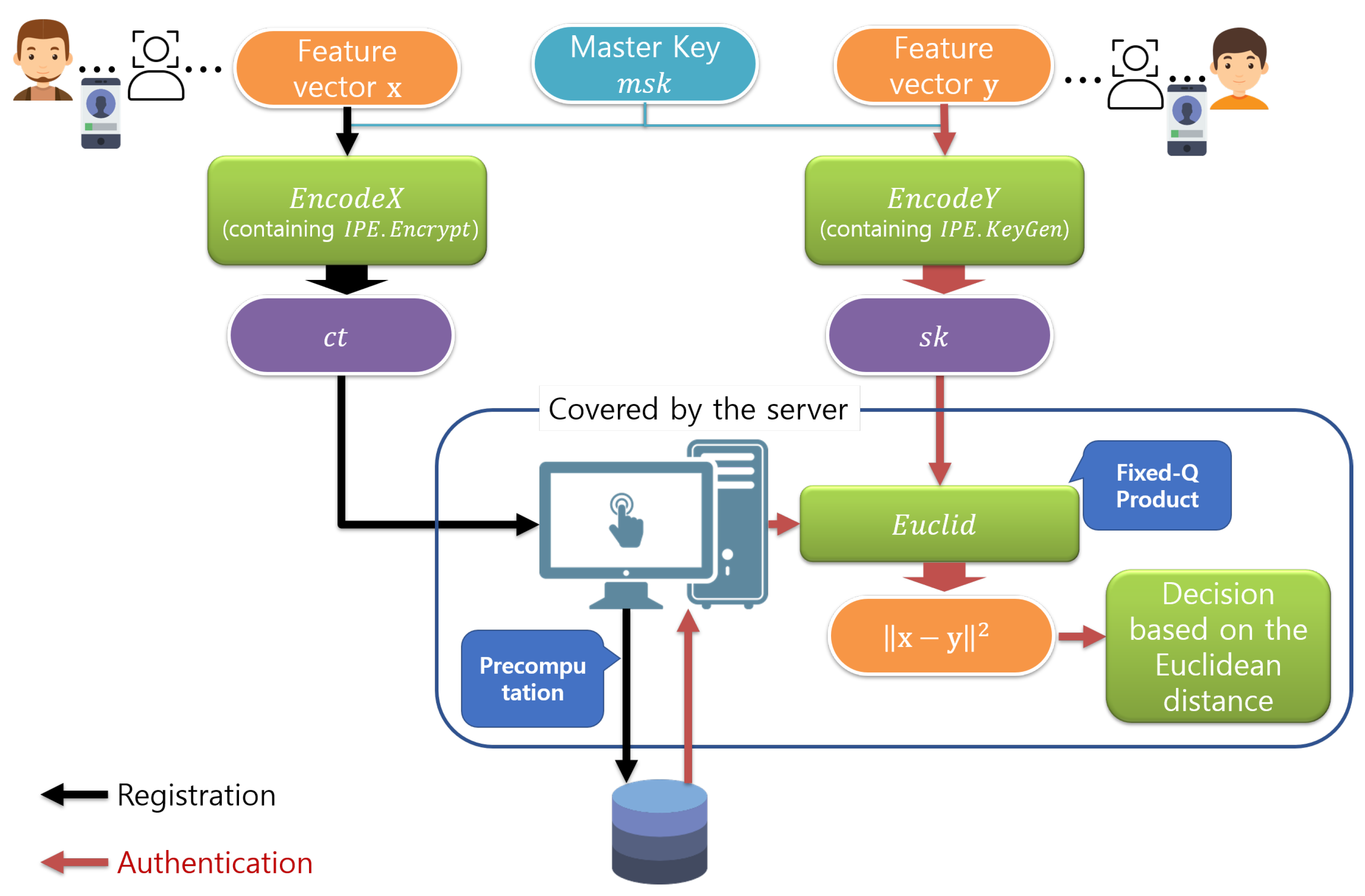
- We demonstrate that the proposed method can significantly accelerate the FE-based biometric verification process. In particular, we exploit the fact that the values related to a biometric template can be precomputed when registered as the template is stored once and repeatedly used without any change.
2. Preliminaries
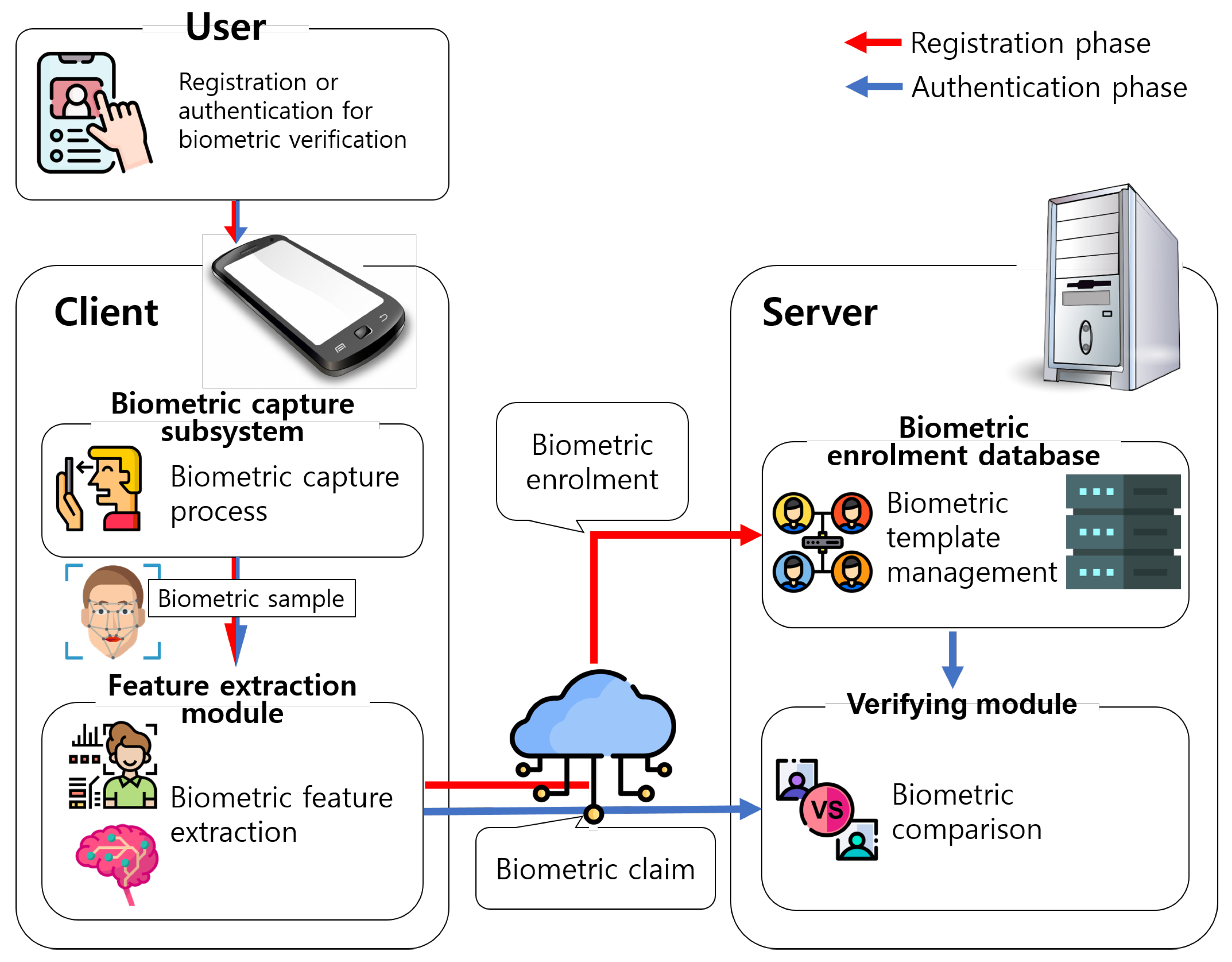
2.1. Remote Biometric Verification System
- A user presents a biometric characteristic to a biosensor in a biometric capture subsystem, and the subsystem runs its biometric capture process to acquire a biometric sample. For facial verification, the user’s smartphone camera takes a picture of the user’s face. In addition to the biometric capture process, a biometric acquisition process is performed when required. The biometric acquisition process includes segmentation, quality control, and other preprocessing steps. For facial verification, various image processing techniques, such as face detection, alignment and frontalization, can be applied.
- The client performs biometric enrolment. To be precise, the client sends the extracted biometric feature to the server, and the server stores the biometric feature as a biometric reference to a biometric enrolment database. In the database, biometric references are managed using a data structure referred to as a biometric template.
2.2. Barreto—Naehrig Curve (BN Curve)
2.3. Pairing
2.3.1. Cryptographic Pairing
- Bilinearity For all , , and ,
- Non-degeneracy For ,
- Computability The map e can be efficiently computed.
2.3.2. Miller’s Algorithm and Final Exponentiation
2.3.3. Optimal Ate Pairing on the BN Curve
| Algorithm 1 Optimal Ate pairing on the BN curve. |
| Input: , the bit length of s, , Output:
|
2.4. Function-Hiding Inner Product Encryption
- Select a bilinear environment according to the security parameter .
- Choose a matrix , where refers to a group of square matrix, where each element belongs to the finite field and an inverse matrix exists.
- Compute .
- Output the public parameter and the master secret key .
- Choose a uniformly random element .
- Using the master key and the vector , output the secret key , s.t. .
- Choose a uniformly random element
- Using the master key and the vector , output the ciphertext , s.t. .
- Using the public parameter , the secret , and the ciphertext , compute and .
- Find a solution z for If this z exists, it satisfies . Output z if it exists; otherwise, output ⊥, indicating that a solution does not exist.
3. Existing Optimization Techniques for Computing Pairing
3.1. Optimal Ate Pairing Product on the BN Curve
- In the case of a modular multiplicative inverse operation, a simultaneous inversion operation [70] can be applied.
- During the computation of Miller’s algorithm, the squaring operation on (e.g., in line 4 of Algorithm 1) can be shared.
- The final exponentiation operation can be shared.
3.2. Fixed Argument Pairings
| Algorithm 2 Products of optimal Ate pairings on the BN curve (Product method). |
| Input: , the bit length of s, , , where j is Output:
|
| Algorithm 3 Fixed-Q precomputation. |
| Input: , the bit length of s, Output:
|
| Algorithm 4 Fixed-Q pairing. |
| Input: , the bit length of , (the precomputation tuple for Q, where ) Output:
|
4. Proposed Method
| Algorithm 5 Fixed-Q Product method. |
| Input: , the bit length of s, , is the precomputation tuple for Output:
|
| Algorithm 6 Adaptive method. |
| Input: , the bit length of s, , is the precomputation tuple for Output:
|
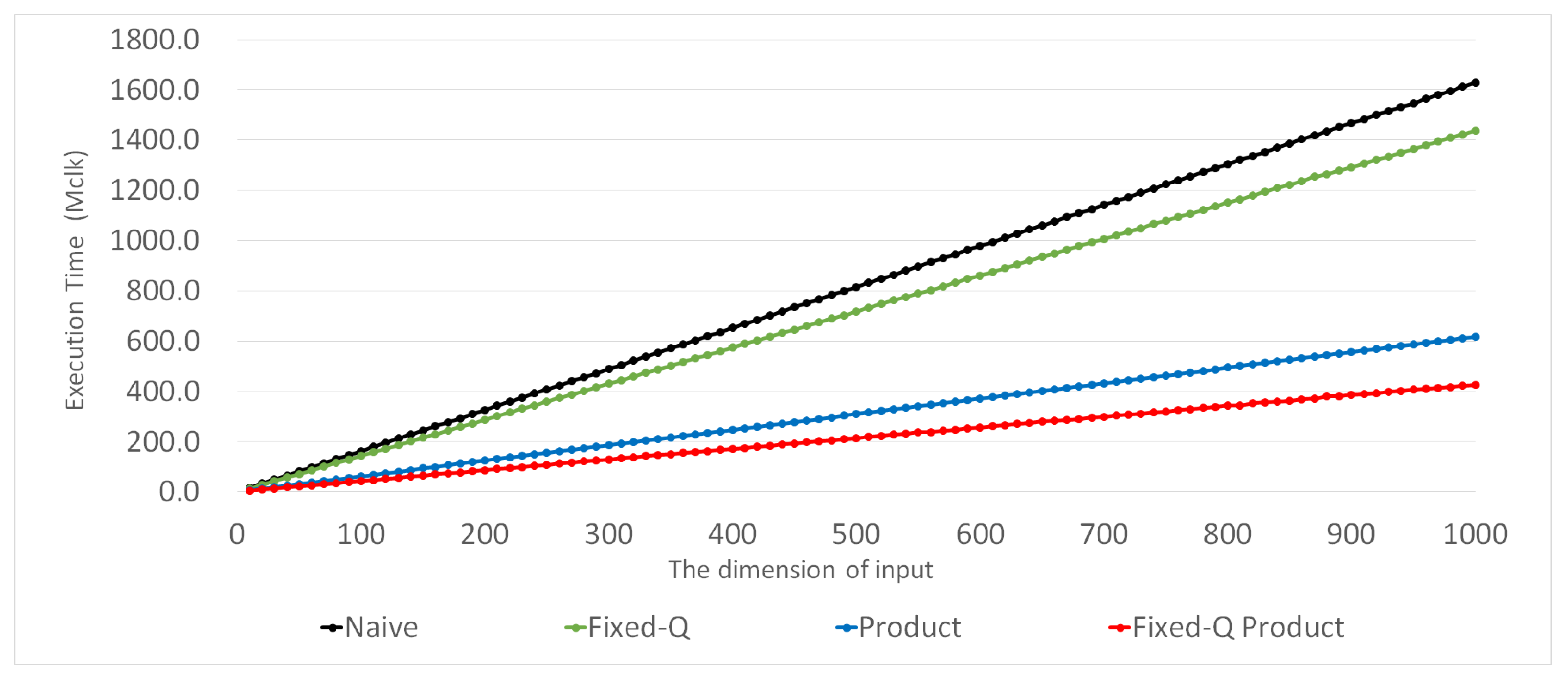
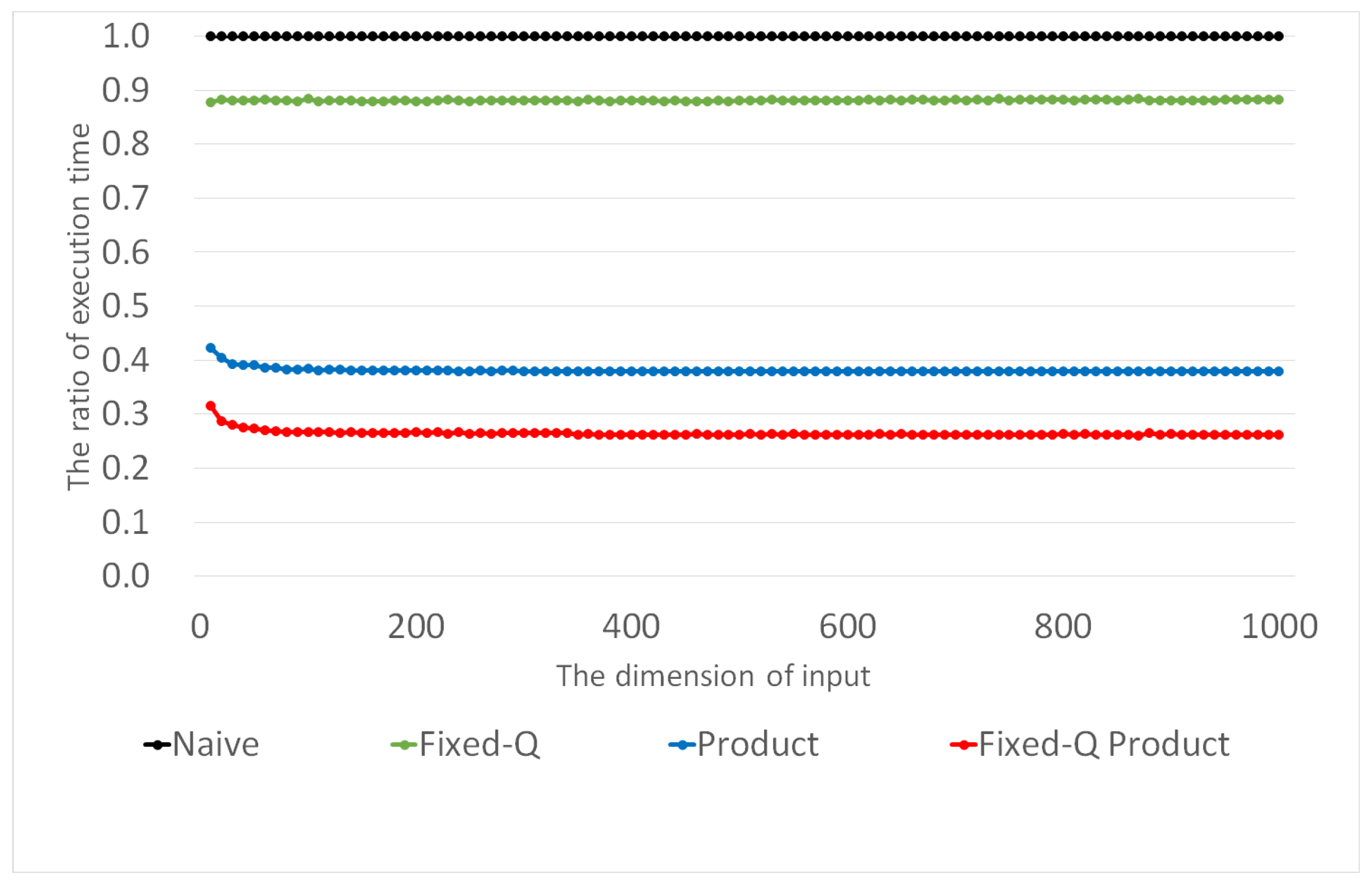
5. Performance Analysis
5.1. Theoretical Analysis
- Naive method
- Product method
- Fixed-Q method
- Fixed-Q Product method (proposed)
5.2. Experimental Results
- Naive method:
- Product method:
- Fixed-Q method:
- Fixed-Q Product method (proposed):
6. Application
- Construct a -dimensional vector from .
- Output .
- Construct a -dimensional vector from .
- Output .
- Calculate .
- Output z. (z satisfies
Security Analysis
- Irreversibility: the irreversibility of our system depends on the security of . Please note that the template is not stored in the client device. Therefore, the only concern is the possibility of template recovery on the server side. However, the guarantees that the server cannot learn any information about the stored ciphertext, except its inner product with another ciphertext. Therefore, the encrypted biometric information is protected by .
- Unlinkability: Our procedure for template encryption, i.e., , involves a uniformly random component . Consequently, it may produce completely different ciphertexts even when the same biometric information is encrypted. Therefore, it is not possible to link two or more biometric templates encrypted using .
- Renewability: Every call to the template encryption procedure generates a completely different ciphertext even for the same user using a random parameter . Therefore, it can create multiple, independently transformed biometric templates.
- Performance: According to the ISO/IEC 19795-1 standard [77], we consider the biometric accuracy as a criterion of performance. It is straightforward that the accuracy of the proposed system is exactly the same as that of the underlying biometric verification system, because the proposed system does not revise the feature extraction process. It only encrypts the extracted features. Therefore, the biometric similarity score computed from and is exactly the same as that computed from the original and .
7. Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
Abbreviations
| FE | Functional encryption |
| PIN | Personal identification number |
| EEG | Electroencephalography |
| HE | Homomorphic encryption |
| ZKPK | Zero-knowledge proof of knowledge |
| TEE | Trusted execution environment |
| BN curve | Barreto-Naehrig curve |
| IPE | Inner product encryption |
References
- Information Technology—Vocabulary—Part 37: Biometrics; Standard, International Organization for Standardization (ISO): Geneva, Switzerland, 2017.
- Im, J.H.; Jeon, S.Y.; Lee, M.K. Practical Privacy-Preserving Face Authentication for Smartphones Secure Against Malicious Clients. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2386–2401. [Google Scholar] [CrossRef]
- Jo, Y.H.; Jeon, S.Y.; Im, J.H.; Lee, M.K. Security analysis and improvement of fingerprint authentication for smartphones. Mob. Inf. Syst. 2016, 2016, 8973828. [Google Scholar] [CrossRef]
- McGoldrick, L.K.; Halámek, J. Recent Advances in Noninvasive Biosensors for Forensics, Biometrics, and Cybersecurity. Sensors 2020, 20, 5974. [Google Scholar] [CrossRef] [PubMed]
- Bollella, P.; Katz, E. Biosensors—Recent Advances and Future Challenges. Sensors 2020, 20, 6645. [Google Scholar] [CrossRef]
- TrustZone—Arm Developer. Available online: https://developer.arm.com/ip-products/security-ip/trustzone (accessed on 31 January 2021).
- Storing Keys in the Secure Enclave. Available online: https://developer.apple.com/documentation/security/certificate_key_and_trust_services/keys/storing_keys_in_the_secure_enclave (accessed on 31 January 2021).
- Ratha, N.K.; Connell, J.H.; Bolle, R.M. Enhancing security and privacy in biometrics-based authentication systems. IBM Syst. J. 2001, 40, 614–634. [Google Scholar] [CrossRef]
- Ratha, N.K.; Chikkerur, S.; Connell, J.H.; Bolle, R.M. Generating cancelable fingerprint templates. IEEE Trans. Pattern Anal. Mach. Intell. 2007, 29, 561–572. [Google Scholar] [CrossRef] [PubMed]
- Juels, A.; Wattenberg, M. A fuzzy commitment scheme. In Proceedings of the 6th ACM Conference on Computer and Communications Security (CCS ’99), Singapore, 1–4 November 1999; pp. 28–36. [Google Scholar]
- Quan, F.; Fei, S.; Anni, C.; Feifei, Z. Cracking cancelable fingerprint template of Ratha. In Proceedings of the 2008 International Symposium on Computer Science and Computational Technology (ISCSCT 2008), Shanghai, China, 20–22 December 2008; Volume 2, pp. 572–575. [Google Scholar]
- Shin, S.W.; Lee, M.K.; Moon, D.; Moon, K. Dictionary attack on functional transform-based cancelable fingerprint templates. ETRI J. 2009, 31, 628–630. [Google Scholar] [CrossRef]
- Nagar, A.; Nandakumar, K.; Jain, A.K. Biometric template transformation: A security analysis. In Proceedings of the Media Forensics and Security II. International Society for Optics and Photonics, San Jose, CA, USA, 27 January 2010; Volume 7541, p. 75410O. [Google Scholar]
- Karimian, N.; Guo, Z.; Tehranipoor, M.; Forte, D. Highly reliable key generation from electrocardiogram (ECG). IEEE Trans. Biomed. Eng. 2016, 64, 1400–1411. [Google Scholar] [CrossRef] [PubMed]
- Nguyen, D.; Tran, D.; Sharma, D.; Ma, W. On the study of EEG-based cryptographic key generation. Procedia Comput. Sci. 2017, 112, 936–945. [Google Scholar] [CrossRef]
- Wang, P.; You, L.; Hu, G.; Hu, L.; Jian, Z.; Xing, C. Biometric key generation based on generated intervals and two-layer error correcting technique. Pattern Recognit. 2021, 111, 107733. [Google Scholar] [CrossRef]
- Jalaly Bidgoly, A.; Jalaly Bidgoly, H.; Arezoumand, Z. A survey on methods and challenges in EEG based authentication. Comput. Secur. 2020, 93, 101788. [Google Scholar] [CrossRef]
- Boyen, X.; Dodis, Y.; Katz, J.; Ostrovsky, R.; Smith, A. Secure remote authentication using biometric data. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques (Eurocrypt 2005), Aarhus, Denmark, 22 May 2005; pp. 147–163. [Google Scholar]
- Bhattasali, T.; Saeed, K.; Chaki, N.; Chaki, R. A survey of security and privacy issues for biometrics based remote authentication in cloud. In Proceedings of the International Conference on Computer Information Systems and Industrial Management (CISIM 2015), Warsaw, Poland, 24 September 2015; pp. 112–121. [Google Scholar]
- Bringer, J.; Chabanne, H.; Patey, A. Privacy-preserving biometric identification using secure multiparty computation: An overview and recent trends. IEEE Signal Process. Mag. 2013, 30, 42–52. [Google Scholar] [CrossRef]
- Rui, Z.; Yan, Z. A survey on biometric authentication: Toward secure and privacy-preserving identification. IEEE Access 2018, 7, 5994–6009. [Google Scholar] [CrossRef]
- Kim, S.; Lewi, K.; Mandal, A.; Montgomery, H.; Roy, A.; Wu, D.J. Function-Hiding Inner Product Encryption is Practical. In Proceedings of the International Conference on Security and Cryptography for Networks (SCN 2018), Amalfi, Italy, 5 September 2018; pp. 544–562. [Google Scholar]
- Zhou, K.; Ren, J. PassBio: Privacy-preserving user-centric biometric authentication. IEEE Trans. Inf. Forensics Secur. 2018, 13, 3050–3063. [Google Scholar] [CrossRef]
- Lee, J.; Kim, D.; Kim, D.; Song, Y.; Shin, J.; Cheon, J.H. Instant Privacy-Preserving Biometric Authentication for Hamming Distance; Cryptology ePrint Archive, Report 2018/1214; IACR, 2018; Available online: https://eprint.iacr.org/2018/1214 (accessed on 1 April 2021).
- Barbosa, M.; Catalano, D.; Soleimanian, A.; Warinschi, B. Efficient Function-Hiding Functional Encryption: From Inner-Products to Orthogonality; Cryptographers’ Track at the RSA Conference (CT-RSA 2019); Springer: Berlin, Germany, 2019; pp. 127–148. [Google Scholar]
- Zhao, Q.; Zeng, Q.; Liu, X. Improved Construction for Inner Product Functional Encryption. Secur. Commun. Netw. 2018, 2018, 6561418. [Google Scholar] [CrossRef]
- Abdalla, M.; Bourse, F.; De Caro, A.; Pointcheval, D. Simple functional encryption schemes for inner products. In Proceedings of the IACR International Workshop on Public Key Cryptography (PKC 2015), Gaithersburg, MD, USA, 30 March–1 April 2015; pp. 733–751. [Google Scholar]
- Datta, P.; Dutta, R.; Mukhopadhyay, S. Functional encryption for inner product with full function privacy. In Proceedings of the IACR International Workshop on Public Key Cryptography (PKC 2016), Taipei, Taiwan, 6–9 March 2016; pp. 164–195. [Google Scholar]
- Kim, S.; Kim, J.; Seo, J.H. A new approach to practical function-private inner product encryption. Theor. Comput. Sci. 2019, 783, 22–40. [Google Scholar] [CrossRef]
- Bünz, B.; Maller, M.; Mishra, P.; Tyagi, N.; Vesely, P. Proofs for Inner Pairing Products and Applications; Cryptology ePrint Archive, Report 2019/1177; IACR, 2019; Available online: https://eprint.iacr.org/2019/1177 (accessed on 1 April 2021).
- Scott, M. Computing the Tate pairing. In Proceedings of the Cryptographers’ Track at the RSA Conference (CT-RSA 2005), San Francisco, CA, USA, 14–18 February 2005; pp. 293–304. [Google Scholar]
- Granger, R.; Smart, N.P. On Computing Products of Pairings. IACR Cryptol. EPrint Arch. 2006, 2006, 172. [Google Scholar]
- Zavattoni, E.; Perez, L.J.D.; Mitsunari, S.; Sánchez-Ramırez, A.H.; Teruya, T.; Rodríguez-Henríquez, F. Software implementation of an attribute-based encryption scheme. IEEE Trans. Comput. 2014, 64, 1429–1441. [Google Scholar] [CrossRef]
- Costello, C.; Stebila, D. Fixed argument pairings. In Proceedings of the International Conference on Cryptology and Information Security in Latin America (Latincrypt 2010), Puebla, Mexico, 8–11 August 2010; pp. 92–108. [Google Scholar]
- Im, J.H.; Kwon, H.Y.; Jeon, S.Y.; Lee, M.K. Privacy-Preserving Electricity Billing System Using Functional Encryption. Energies 2019, 12, 1237. [Google Scholar] [CrossRef]
- Son, Y.B.; Im, J.H.; Kwon, H.Y.; Jeon, S.Y.; Lee, M.K. Privacy-Preserving Peer-to-Peer Energy Trading in Blockchain-Enabled Smart Grids Using Functional Encryption. Energies 2020, 13, 1321. [Google Scholar] [CrossRef]
- Anada, H. Decentralized Multi-authority Anonymous Authentication for Global Identities with Non-interactive Proofs. J. Internet Serv. Inf. Secur. 2020, 10, 23–37. [Google Scholar]
- Pop, C.D.; Antal, M.; Cioara, T.; Anghel, I.; Salomie, I. Blockchain and Demand Response: Zero-Knowledge Proofs for Energy Transactions Privacy. Sensors 2020, 20, 5678. [Google Scholar] [CrossRef]
- Chun, H.; Elmehdwi, Y.; Li, F.; Bhattacharya, P.; Jiang, W. Outsourceable two-party privacy-preserving biometric authentication. In Proceedings of the 9th ACM Symposium on Information, Computer and Communications Security, Kyoto, Japan, 4–6 June 2014; pp. 401–412. [Google Scholar]
- Cheon, J.H.; Chung, H.; Kim, M.; Lee, K.W. Ghostshell: Secure Biometric Authentication Using Integrity-Based Homomorphic Evaluations; Cryptology ePrint Archive, Report 2016/484; IACR, 2016; Available online: https://eprint.iacr.org/2016/484 (accessed on 1 April 2021).
- Im, J.; Choi, J.; Nyang, D.; Lee, M. Privacy-Preserving Palm Print Authentication Using Homomorphic Encryption. In Proceedings of the 2nd Int. Conf. Big Data Intell. Comput., Thessaloniki, Greece, 23–25 October 2016; pp. 878–881. [Google Scholar]
- Lin, D.; Hilbert, N.; Storer, C.; Jiang, W.; Fan, J. UFace: Your universal password that no one can see. Comput. Secur. 2018, 77, 627–641. [Google Scholar] [CrossRef]
- Shahandashti, S.F.; Safavi-Naini, R.; Safa, N.A. Reconciling user privacy and implicit authentication for mobile devices. Comput. Secur. 2015, 53, 215–233. [Google Scholar] [CrossRef]
- Šeděnka, J.; Govindarajan, S.; Gasti, P.; Balagani, K.S. Secure outsourced biometric authentication with performance evaluation on smartphones. IEEE Trans. Inf. Forensics Secur. 2015, 10, 384–396. [Google Scholar] [CrossRef]
- Gasti, P.; Šeděnka, J.; Yang, Q.; Zhou, G.; Balagani, K.S. Secure, fast, and energy-efficient outsourced authentication for smartphones. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2556–2571. [Google Scholar] [CrossRef]
- Abidin, A. On Privacy-Preserving Biometric Authentication. In Proceedings of the Information Security and Cryptology, Beijing, China, 29 November 2017; pp. 169–186. [Google Scholar]
- Gunasinghe, H.; Bertino, E. PrivBioMTAuth: Privacy Preserving Biometrics-Based and User Centric Protocol for User Authentication From Mobile Phones. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1042–1057. [Google Scholar] [CrossRef]
- Droandi, G.; Barni, M.; Lazzeretti, R.; Pignata, T. SEMBA:SEcure multi-biometric authentication. arXiv 2018, arXiv:abs/1803.10758. [Google Scholar]
- Catalano, D.; Fiore, D. Using linearly-homomorphic encryption to evaluate degree-2 functions on encrypted data. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 1518–1529. [Google Scholar]
- Damgård, I.; Pastro, V.; Smart, N.; Zakarias, S. Multiparty Computation from Somewhat Homomorphic Encryption. In Proceedings of the CRYPTO 2012, Barbara, CA, USA, 19–23 August 2012; pp. 643–662. [Google Scholar]
- Sengupta, S.; Cheng, J.; Castillo, C.; Patel, V.; Chellappa, R.; Jacobs, D. Frontal to Profile Face Verification in the Wild. In Proceedings of the 2016 IEEE Winter Conference on Applications of Computer Vision (WACV), Lake Placid, NY, USA, 7–10 March 2016. [Google Scholar]
- The Database of Faces (Formerly ‘The ORL Database of Faces’). Available online: http://cam-orl.co.uk/facedatabase.html (accessed on 1 April 2021).
- Taigman, Y.; Yang, M.; Ranzato, M.; Wolf, L. Deepface: Closing the gap to human-level performance in face verification. In Proceedings of the 2014 IEEE Conference on Computer Vision and Pattern Recognition, Columbus, OH, USA, 23–28 June 2014; pp. 1701–1708. [Google Scholar]
- He, K.; Zhang, X.; Ren, S.; Sun, J. Deep residual learning for image recognition. In Proceedings of the 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Las Vegas, NV, USA, 27–30 June 2016; pp. 770–778. [Google Scholar]
- Barreto, P.S.; Naehrig, M. Pairing-friendly elliptic curves of prime order. In Proceedings of the International Workshop on Selected Areas in Cryptography (SAC 2005), Kingston, ON, Canada, 11–12 August 2005; pp. 319–331. [Google Scholar]
- Aranha, D.F.; Barreto, P.S.; Longa, P.; Ricardini, J.E. The realm of the pairings. In Proceedings of the International Conference on Selected Areas in Cryptography (SAC 2013), Burnaby, BC, Canada, 14–16 August 2013; pp. 3–25. [Google Scholar]
- El Mrabet, N.; Joye, M. Guide to Pairing-Based Cryptography; CRC Press: Boca Raton, FL, USA, 2017. [Google Scholar]
- Silverman, J.H. The Arithmetic of Elliptic Curves; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2009; Volume 106. [Google Scholar]
- Miller, V.S. The Weil pairing, and its efficient calculation. J. Cryptol. 2004, 17, 235–261. [Google Scholar] [CrossRef]
- Scott, M.; Benger, N.; Charlemagne, M.; Perez, L.J.D.; Kachisa, E.J. On the final exponentiation for calculating pairings on ordinary elliptic curves. In Proceedings of the International Conference on Pairing-Based Cryptography (Pairing 2009), Palo Alto, CA, USA, 12–14 August 2009; pp. 78–88. [Google Scholar]
- Cohen, H.; Frey, G.; Avanzi, R.; Doche, C.; Lange, T.; Nguyen, K.; Vercauteren, F. Handbook of Elliptic and Hyperelliptic Curve Cryptography; CRC Press: Boca Raton, FL, USA, 2005. [Google Scholar]
- Granger, R.; Hess, F.; Oyono, R.; Thériault, N.; Vercauteren, F. Ate pairing on hyperelliptic curves. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques (Eurocrypt 2007), Barcelona, Spain, 20–24 May 2007; pp. 430–447. [Google Scholar]
- Hess, F.; Smart, N.P.; Vercauteren, F. The eta pairing revisited. IEEE Trans. Inf. Theory 2006, 52, 4595–4602. [Google Scholar] [CrossRef]
- Matsuda, S.; Kanayama, N.; Hess, F.; Okamoto, E. Optimised versions of the ate and twisted ate pairings. In Proceedings of the International Conference on Cryptography and Coding (IMACC 2007), Cirencester, UK, 18–20 December 2007; pp. 302–312. [Google Scholar]
- Zhao, C.A.; Zhang, F.; Huang, J. A note on the Ate pairing. Int. J. Inf. Secur. 2008, 7, 379–382. [Google Scholar] [CrossRef]
- Lee, E.; Lee, H.S.; Park, C.M. Efficient and generalized pairing computation on abelian varieties. IEEE Trans. Inf. Theory 2009, 55, 1793–1803. [Google Scholar] [CrossRef][Green Version]
- Vercauteren, F. Optimal pairings. IEEE Trans. Inf. Theory 2009, 56, 455–461. [Google Scholar] [CrossRef]
- Beuchat, J.L.; González-Díaz, J.E.; Mitsunari, S.; Okamoto, E.; Rodríguez-Henríquez, F.; Teruya, T. High-speed software implementation of the optimal ate pairing over Barreto–Naehrig curves. In Proceedings of the International Conference on Pairing-Based Cryptography (Pairing 2010), Yamanaka Hot Spring, Japan, 13–15 December 2010; pp. 21–39. [Google Scholar]
- Bishop, A.; Jain, A.; Kowalczyk, L. Function-hiding inner product encryption. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security (ASIACRYPT 2015), Auckland, New Zealand, 29 November–3 December 2015; pp. 470–491. [Google Scholar]
- Hankerson, D.; Menezes, A.J.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Jeon, S.Y.; Lee, M.K. Poster: Acceleration of Pairing Product Operation Using Precomputation. In Proceedings of the 21st World Conference on Information Security Applications 2020 (WISA 2020), Jeju Island, Korea, 26–28 August 2020; p. 5. [Google Scholar]
- Jeon, S.Y. Acceleration of Pairing Operation for Performance Improvement of Functional Encryption. Master’s Thesis, Inha University, Incheon, Korea, 2020. [Google Scholar]
- GNU Multiple Precision Arithmetic Library (GMP). Available online: https://gmplib.org/ (accessed on 31 January 2021).
- GitHub—Herumi/Mcl: A Portable and Fast Pairing-Based Cryptography Library. Available online: https://github.com/herumi/mcl (accessed on 31 January 2021).
- A Library for Doing Number Theory (NTL). Available online: https://www.shoup.net/ntl/ (accessed on 31 January 2021).
- Information Technology—Security Techniques—Biometric Information Protection; Standard, International Organization for Standardization (ISO): Geneva, Switzerland, 2011.
- Information Technology—Biometric Performance Testing and Reporting—Part 1: Principles and Framework; Standard; International Organization for Standardization (ISO): Geneva, Switzerland, 2006.
- Lafkih, M.; Mikram, M.; Ghouzali, S.; El Haziti, M. Evaluation of the Impact of Noise on Biometric Authentication Systems. In Proceedings of the 2019 3rd International Conference on Advances in Artificial Intelligence, Istanbul, Turkey, 26–28 October 2019; pp. 188–192. [Google Scholar]
| Operation Name | Execution Time (Mclk) |
|---|---|
| Squaring on | 0.008 |
| Final exponentiation | 0.629 |
| Basic optimal Ate pairing (Algorithm 1) | 1.595 |
| Fixed-Q pairing (Algorithm 4) | 1.411 |
| Methods | Expected Cost | Measured Cost |
|---|---|---|
| Naive | ||
| Product | ||
| Fixed-Q | ||
| Proposed |
| Biometric Dataset | Face Image Processing [2] | EncodeY | Euclid | Total (Naive) | Total (Proposed) | Ratio | ||
|---|---|---|---|---|---|---|---|---|
| Pairing (Naive) | Pairing (Proposed) | DLP | ||||||
| Auto | 193.27 | 106.47 | 58.86 | 15.66 | 120.30 | 478.90 | 435.70 | 9.0 % |
| Guide | 157.47 | 443.10 | 399.90 | 9.7% | ||||
| CFP | 150.15 | 435.78 | 392.58 | 9.9% | ||||
| ORL | 147.33 | 432.96 | 389.76 | 10.0% | ||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jeon, S.-Y.; Lee, M.-K. Acceleration of Inner-Pairing Product Operation for Secure Biometric Verification. Sensors 2021, 21, 2859. https://doi.org/10.3390/s21082859
Jeon S-Y, Lee M-K. Acceleration of Inner-Pairing Product Operation for Secure Biometric Verification. Sensors. 2021; 21(8):2859. https://doi.org/10.3390/s21082859
Chicago/Turabian StyleJeon, Seong-Yun, and Mun-Kyu Lee. 2021. "Acceleration of Inner-Pairing Product Operation for Secure Biometric Verification" Sensors 21, no. 8: 2859. https://doi.org/10.3390/s21082859
APA StyleJeon, S.-Y., & Lee, M.-K. (2021). Acceleration of Inner-Pairing Product Operation for Secure Biometric Verification. Sensors, 21(8), 2859. https://doi.org/10.3390/s21082859






