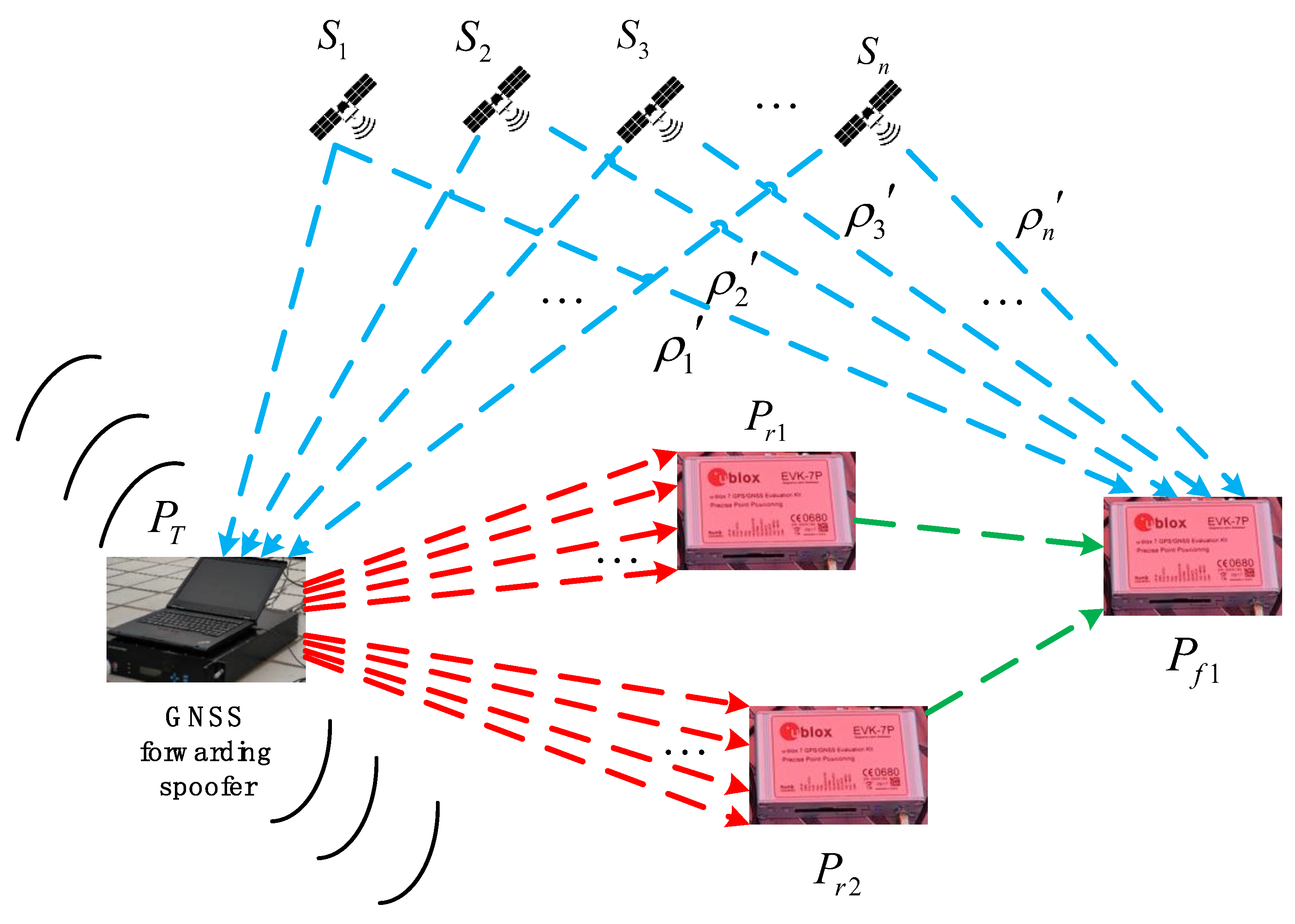
According to the spoofing purpose of a spoofer to the group of multiple receivers, we propose two forwarding spoofer area deployment algorithms for MSMT scenarios. The first is the multi-target same-point spoofing algorithm (MSPSA), and the second is the multi-target different-point spoofing algorithm (MDPSA). The scenarios are all conducted in a two-dimensional plane. In actual spoofing, it is impossible for the spoofer to be infinitely far away from receivers. It is assumed that the possible deployment location of a spoofer is also limited; that is, we demarcate all spoofers and receivers within a given geometric area , which is also a given area of the spoofing scene. At this time, the deployment location of a spoofer can only be selected within a given area.
4.1. MSPSA for Group Multiple Receivers
In this scenario, a spoofer expects to spoof the positioning results of six receivers located at different positions in the group to the same spoofing point
. We define this situation as “same-point spoofing”. To achieve the purpose of spoofing, according to
Section 2.1, at this time, a spoofer can cheat multiple receivers at the same time through a forwarding spoofer. The MSPSA applicable to this scenario will be described in detail below.
Step 1: it is assumed that a spoofer obtains the positions of the six victim receivers in the group by radar observation, which are expressed as , , , and .
Step 2: a unique circle can be determined according to the three noncollinear points on the plane. Among the six victim receivers, any three receivers located in noncollinear positions , , and can be selected. Taking these three receivers as points on the circle, a unique circle can be formed. According to the principle of permutation and combination, if any three receivers in the group are not collinear, there will be combinations.
Take one of the combinations,
, as an example. It is assumed that in combination
, three receivers
,
, and
form a circle, which is defined as the forwarding spoofing circle
. In fact, this is a forwarding spoofing circle formed by a single GNSS forwarding spoofing device deployed in
, as shown in
Figure 5(bottom).
is also the center position of the forwarding spoofing circle
. The victim receivers located on the circle will be subjected to critical spoofing, while receivers located inside the circle will be subjected to higher-power forwarding spoofing. To improve the concealment of spoofing, the spoofer obviously prefers that victim receivers are all located at the critical spoofing position because this requires the minimum power to realize forwarding spoofing; it is considered here that forwarding signals will hardly affect the receiver located outside the circle.
Step 3: calculate the positional relationship between the remaining three receivers located at , , and and the spoofing circle . If one of the remaining three receivers is located on the spoofing circle , it will be subjected to critical spoofing by the spoofing device located at . If there is one located within spoofing circle , it will be spoofed by higher-power forwarding spoofing by a spoofer located at . If there is one outside spoofing circle , it will not be affected by the spoofer at .
Step 4: according to the judgment in step 3, there will be the following four situations.
(1) Case 1: among the remaining three receivers, three are outside spoofing circle
. The unique spoofing circle
is formed by three noncollinear receivers,
,
, and
, other than spoofing circle
, which is formed by a single GNSS forwarding spoofing device deployed in
, as shown in
Figure 6.
Subsequently, it is determined that the three receivers located at
,
, and
, other than the receivers located at
,
, and
, intersect with spoofing circle
and spoofing circle
. The equation is expressed as (10);
and
, respectively, represent the distances from the center
,
of the corresponding spoofing circle to the
th receiver. When the receiver is located on spoofing circle
, the spoofing fails because of signal crosstalk with spoofing circle
. When the receiver is located inside spoofing circle
, spoofing fails in the same way. When the receiver is outside spoofing circle
and on spoofing circle
, the receiver is critically spoofed. When the receiver is outside spoofing circle
and within spoofing circle
, the receiver is spoofed by higher-power forwarding spoofing.
Thus, the deployment positions of the two spoofers are determined, and the spoofing situations of the receivers are obtained.
(2) Case 2: two of the remaining three receivers are outside spoofing circle . ① When the two receivers and form a spoofing circle, spoofing circles and pass through the two receivers respectively.
Spoofing circle
is determined by the optimal programming algorithm. First, the center
of spoofing circle
is on the perpendicular line of line segment
. Furthermore, to pursue the concealment of a spoofer in the geographical position, the shortest sum of the distances between the center
of spoofing circle
and all six receivers is taken as the objective function. At the same time, there are two constraints: the first is that the other six receivers cannot intersect with spoofing circle
, and the second is that spoofing circles
and
cannot intersect, as shown in Equation (11).
According to Equation (11), the spoofing circle can be determined by the optimization programming algorithm.
(3) Case 3: among the remaining three receivers, one receiver located at
is outside spoofing circle
. Spoofing circle
is determined by the optimal programming algorithm. To pursue the concealment of spoofing in the geographical position, the shortest sum of the distances between the center
of spoofing circle
and all six receivers is taken as the objective function; At the same time, there are two constraints: the first is that the other five receivers cannot intersect with spoofing circle
, and the second is that spoofing circles
and
cannot intersect, as shown in Equation (12).
According to Equation (12), spoofing circle can be determined by the optimization programming algorithm.
(4) Case 4: among the remaining three receivers, 0 is outside spoofing circle . In this case, there is only one spoofer, and the relationship between the six victim receivers and spoofing circle is clear.
Step 5: steps 2–4 are all about combination . At this time, all combinations are traversed. After all the above combinations are processed, the following four indexes, SN, , CSR, and SSR, are proposed as the performance criteria for judging a spoofer deployment scheme:
- (1)
SN: number of GNSS forwarding spoofers used;
- (2)
: the sum of the distances from each spoofer to each victim receiver;
- (3)
CSR: critical spoofing rate (CSR), the proportion of critical spoofed receiver to the number of all spoofed receivers;
- (4)
SSR: spoofing success rate (SSR), the proportion of spoofed receivers in the total number of receivers.
In MSPSA, the above four indexes will be calculated.
It is easy to understand that from the perspective of the equipment costs of a spoofer, it is expected that the less the index 1, the better. From the concealment of spoofing in geographical space, index 2 is the sum of all elements of
in (13), where
represents the straight-line distance from the
th spoofing device to the
th victim receiver, and the larger the better. Index 3 is used to evaluate the concealment degree of spoofing performed by spoofer. The higher the CSR is, the more the spoofed receivers are subjected to critical spoofing. Index 4 is used to evaluate the success rate of spoofing task completed by spoofing device. The higher the SSR, the more receivers are successfully spoofed.
However, the importance of the four indexes will not be ranked here, which will be determined by the intention of spoofer. This means that spoofers will decide which deployment scheme to choose according to their specific actual needs, and MSPSA will provide all possible deployment schemes and corresponding indexes for a spoofer to choose.
According to the above detailed description of the algorithm steps, the key flow of MSPSA is given, as shown in
Figure 7.
4.2. MDPSA for Group Multiple Receivers
In this scenario, a spoofer expects to spoof the positioning results of six victim receivers located at different positions
,
,
, and
in the group to different spoofing points
,
,
, and
, while maintaining the relative positional relationship between the real positions of the receivers among these spoofing points. This situation is defined as “different-point spoofing”. To achieve the purpose of spoofing, according to
Section 2.1, at this time, a spoofer needs to deploy six GNSS forwarding spoofing devices to spoof multiple receivers at the same time; that is, a single spoofing device only completes the spoofing of one receiver because this is “different-point spoofing”. The regional deployment algorithm applicable to this scenario will be described in detail below.
Step 1: it is assumed that a spoofer obtains the positions of the six victim receivers in the group by radar observation, which are expressed as , , , and .
Step 2: each spoofer spoofs one receiver, corresponding to the receiver located at
. A single GNSS forwarding spoofer deployed at
forms forwarding spoofing circle
, as shown in
Figure 5(bottom).
is the center position of forwarding spoofing circle
. The receiver located at
will be subjected to critical spoofing. Similarly, the receiver located inside the circle will be subjected to higher-power forwarding spoofing. The receiver outside circle will not be affected by a signal broadcast by a spoofer. Therefore, corresponding to the six victim receivers, the six spoofers will form six forwarding spoofing circles,
,
,
, and
, as shown in
Figure 8.
Step 3: the restriction conditions of six forwarding spoofing circles need to be considered. On the one hand, for any one of the forwarding spoofing circles
, except for the receiver located in
that it is responsible for spoofing, no victim receiver in other areas can intersect with forwarding spoofing circle
; otherwise, it will obviously cause unnecessary signal collision to the spoofing of other receivers and lead to possible spoofing failure. On the other hand, all spoofers are deployed in a given area
, as shown in Equation (14).
Step 4: after the above restrictions are given, we still take the SN, , CSR, and SSR proposed in MSPSA as the performance criteria for evaluating the spoofing deployment scheme. However, it should be noted that SN = 6, CSR = 100%, and SSR = 100% are easy to achieve in different-point spoofing. Therefore, we take index as the objective function and take (15) as the constraint condition to optimize the solution.
According to the above detailed description of the algorithm steps, we give the key processes of MDPSA, as shown in
Table 1.