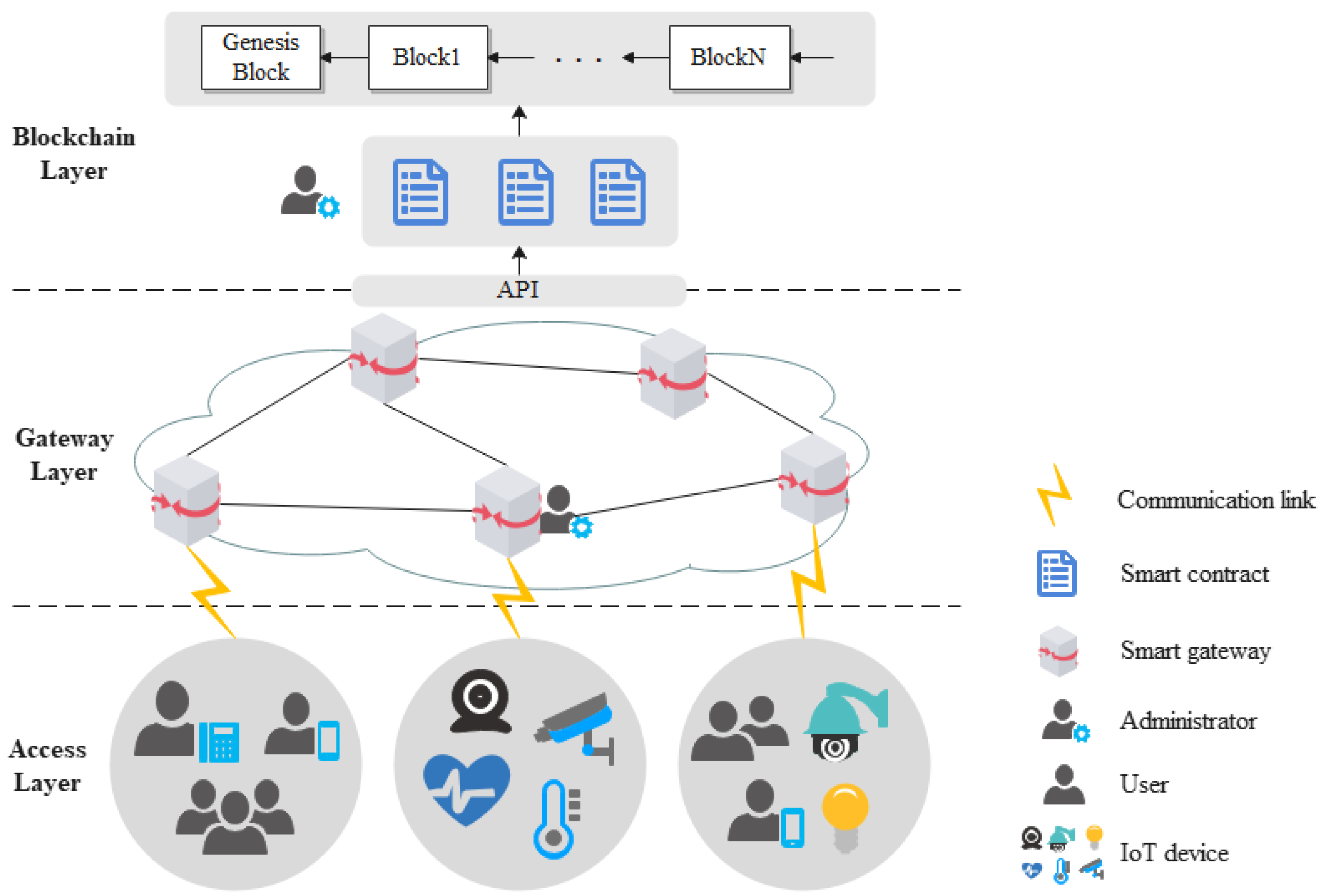
This section provides a detailed description of the three function modules in the framework of a blockchain-based IoT access control and behavior regulation system.
4.1. Access Control Module
The access control module mainly performs authentication and access control decision-making processes, and is the first line of defense for the system.
Due to the limited computing abilities of most IoT devices, the identity authentication link adopted a relatively simple account-password authentication method. That is, the user or resource would generate a self-defined key (K) to be saved in the blockchain at the registration stage. Then, during the authentication phase, the user or resource would need to send another K and the blockchain would compare it with the K of registration. If the two keys were equal, authentication would be successful; otherwise, authentication would fail.
Considering the fine-grained requirements of IoT, the access control link adopted the ABAC model.
To describe the characteristics of users and IoT devices in detail, some parameters are defined in this module, as shown in
Table 1. Based on these parameters, the access control smart contract (AC_SC) was designed to automatically execute the module function on the blockchain to ensure the transparency and trustworthiness of the execution process.
Before introducing the algorithm designed in this paper, several blockchain built-in functions need to be introduced, because it is with the help of the following functions that we can use smart contracts to perform operations on the blockchain’s data.
PutState(a, b) is a built-in function provided by the blockchain that takes two arguments a and b. Argument a should be string type and b can be any data type, such as struct UI or RI in
Table 1.
When we call the function PutState(‘x’, 100) on a smart contract, the blockchain will generate a transaction with the content “set the value of ‘x’ to 100” and write it to the block ledger after consensus. At the same time, the value (or state) of “x” will be updated to 100 in the world state database. The world state database is a non-relational database that stores data through key-value pairs. In fact, most blockchains (including Ethereum and Fabric) maintain two sets of data: one is the block ledger and the other is the world state database, as shown in
Figure 3. The block ledger sequentially records the insert, update, and delete operations for all data on the blockchain, which is used for auditing and traceability; whereas the world state database records the newest state of all data in the blockchain, which is used to improve retrieval efficiency.
GetState(a) is a built-in function provided by the blockchain that takes one argument. When we call the function GetState(“x”) on a smart contract, the blockchain will query the world state database and return the newest value of “x”. It is to be noted that the process of querying data will not be written into the block ledger, as it does not involve modification of data.
DelState(a) is a built-in function provided by the blockchain that takes one argument. When we call the function DelState(“x”) on a smart contract, the blockchain will generate a transaction with the content “delete ‘x’ from ledger” and write it to the block ledger after consensus. At the same time, the key-value pair data ‘x’:100 will be removed from the world state database. Next time we call GetState(“x”), it will return the null.
Based on the parameters and built-in functions above, the algorithms in the AC_SC are described below.
When the smart gateway receives a user UID registration request, it will invoke Algorithm 1 with input parameters: user-defined UID, K, and user UA, signed by the administrator.
| Algorithm 1 UID_Register |
| Input UID registration information: UID, K, UA |
| Output Registration result |
| 1. result = false; |
| 2. UI = getState(UID); |
| 3 check = checkSignature(UA) |
| 3. if (UI == null and check == true){ |
| 4. new(TS); |
| 5. UI = {UID, K, UA, 0, 0, 0, 0, TS} |
| 6. putState(UID, UI);} |
| 7. return true; |
Algorithm 1 first checks if the UID has been registered by another user, and subsequently verifies the administrator’s signature on the UA. If the UID is not yet registered and the signature is correct, Algorithm 1 will declare a new struct UI, put the user’s UID, K, and UA into the struct, and store the UI into the blockchain by calling the function PutState(UID, UI).
Similar to Algorithm 1, the smart gateway receives RID registration request messages from IoT devices and invokes Algorithm 2. Algorithm 2 puts the registration information of IoT devices into a new struct RI and stores it on the blockchain by calling function PutState(RID, RI) to implement the IoT device registration and policy deployment.
| Algorithm 2 RID_Register |
| Input RID registration information: RID, K, PS |
| Output Registration result |
| 1. result = false; |
| 2. RI = getState(RID); |
| 3. if (RI == null){ |
| 4. RI = {RID, K, PS} |
| 5. putState(RID, RI);} |
| 6. return true; |
When a user asks for access authorization, the smart gateway will invoke Algorithm 3 to perform the access control process. Algorithm 3 is the core of the access control module.
| Algorithm 3 Access_Control |
| Input Access control information: UID, RID, K, AA, EA, D |
| Output Access control result |
| 1. result = false; |
| 2. RI = getState(RID); |
| 3. UI = getState(UID); |
| 4. if (UI == null){ |
| 5. return false;} |
| 6. if (UI.K ! = K){ |
| 7. UI.AuthenF++; |
| 8. putState(UID, UI); |
| 9. return false;} |
| 10. UI.AuthenS++; |
| 11. for P in RI.PS{ |
| 12. if (UI.UA, EA, AA ⊂ P){ |
| 13. result = true; |
| 14. break;} |
| 15. } |
| 16. if (result == false){ |
| 17. UI.AbacF++; |
| 18. putState(UID, UI); |
| 19. return false;} |
| 20. UI.AbacS++; |
| 21. Time = time.now( ); |
| 22. T = {Time, D, RID}; |
| 23. UI.TS.append(T); |
| 24. putState(UID, UI); |
| 25. return string(true) + json(T); |
(1) Identity authentication
In the ABAC model, different identity characteristics determine different rights. Therefore, to ensure that all access authorizations are correctly granted, Algorithm 3 first checks the user’s identity and considers the user successfully authenticated when the input K is exactly the same as the user registration K stored on the blockchain. Then 1 is added to the field AuthenS in the user’s UI. If user authentication fails, Algorithm 3 will add 1 to the field AuthenF in the user’s UI and this authorization request will be directly rejected; no further steps are performed.
Notably, after the smart contract algorithm is executed, all updates or deletions to data, such as AuthenS or AuthenF on the chain, will be immediately written into the block ledger and updated to the world state database.
(2) Attribute acquisition and policy query
After a successful authentication, Algorithm 3 will then get the user’s UA from UI by calling function getState(UID) and the query resource PS from RI by calling function getState(RID). This step is to prepare for the access control process
(3) Access decision
Finally, an access decision needs to be made. Algorithm 3 will traverse all policies in the resource PS until any policy can match with user attribute UA, environment attribute EA, and user access action AA.
A successful match means that the user has the right to access the resource. A T will be generated for the user, which shows the resource the authorization token can be used to access and how long it is valid for. The token will be written to the field T of the user’s UI and stored on the chain through the built-in function PutState(UID, UI). Eventually all blockchain nodes (smart gateways) will be able to query the authorization token.
Similar to the authentication process, the access control result of the user will lead to an update of the field AbacS or AbacF.
4.2. Separation Mapping Module
The function of the separation mapping module is to prevent unauthorized user traffic from reaching its destination through the core network, which is the second line of security for the system. For this purpose, two classes of IP addresses were defined and a new inter-domain communication mechanism was designed based on the LISP protocol.
EID refers to the IP address used by users and IoT devices in the access network. EID is only involved in intra-domain routing, not inter-domain routing, and there is no routing information of EID in the core network.
RLOC refers to the IP address used by the core network routing node (smart gateway); the routing table of the core network contains only the routing entries of the RLOC.
(1) EID registration
When a user or IoT device first connects to the network, they need to perform an EID registration process. The smart gateway will generate mapping information (MI) for the user or device, which is used to bind their EID with the RLOC as well as other parameters of the smart gateway, then updates this MI to other blockchain nodes (smart gateways) by calling blockchain function putState(UID/RID, MI). MI is a struct type with four fields: the EID field is used to store registrant’s EID address; the ID field is used to store the identifier of the registrant, i.e., UID or RID; the RLOC field is used to store the RLOC address of smart gateway; the Flag field is used to indicate whether the registrant is a user or an IoT device.
(2) Using EID for communication
When nodes located in different access networks need to communicate, they use their EIDs as the IP address of all the packets they send.
(3) Packet capture
The smart gateway located at the egress of the access network will capture all cross-domain packets. These packets need to finish the separation mapping process to change their IP address from EID type to RLOC type; otherwise, they will not be addressable in the core network and will finally be dropped.
(4) Separation mapping
For the sake of illustration, consider EID1 as the EID address of the IoT device and EID2 as the EID address of the user. For a packet sent by an IoT device, the smart gateway can directly get its mapping information, such as RID and RLOC, by calling function getState(EID1).
For the user, the smart gateway needs to determine whether the user bound to this EID address has the right to access the resource characterized by this RID. For this purpose, the smart gateway queries the user’s MI stored on the blockchain by calling function getState(EID2), then queries the user’s UI by calling function getState(MI.UID), and gets TS in UI. Once the user’s TS is obtained, all T in the TS will be traversed to verify if access authorization exists for the resource characterized by that RID.
If the authorization does not exist or the authorization time has expired, this means the user is illegally accessing the resource and the smart gateway needs to directly discard the packet; otherwise, the packet belongs to legitimate access traffic, and the next process should be performed.
(5) Header encapsulation [
24] and routing forwarding
For every legal packet, the smart gateway encapsulates another layer of IP headers for the packet with the RLOCs of its source and destination EIDs, then routes it to the core network. Other smart gateways in the core network will forward the packet according to its outer header.
(6) Header decapsulation
Eventually, the smart gateway at the other end will receive the packet, remove the outer header, and forward the original packet to the receiving end, and this cross-domain communication process is completed.
With the above mechanism, all illegal packets from unauthorized users can be intercepted at the egress of the access network. Among them, the EID registration process and separation mapping process are implemented by the separation mapping smart contract (SM_SC), to ensure the decentralization of data storage and query. This algorithm is shown in Algorithm 4.
Similar to Algorithm 3, Algorithm 4 first verifies the user’s identity by comparing K. After success of authentication, Algorithm 4 will make a new struct MI, put the EID registration information into it, and then store it on the blockchain by calling function PutState(EID, MI) to realize the function of EID registration.
| Algorithm 4 EID_Register |
| Input EID registration information: Flag, UID/RID, EID, RLOC, K |
| Output Registration result |
| 1. result = false; |
| 2. UI/RI = getState(UID/RID); |
| 3. if (UI/RI == null || UI/RI.K ! = K){ |
| 4. return result;} |
| 5. MI = [UID/RID, EID, RLOC, Flag]; |
| 6. putState(EID, MI); |
| 7. return true; |
Algorithm 5 locates the identities of the communicating parties based on the EIDs of packet, verifies the user authorization token, then returns the corresponding RLOC address to achieve separation mapping.
| Algorithm 5 EID_Mapping |
| Input EID1, EID2 |
| Output Separation map result |
| 1. MI1 = getState(EID1); |
| 2. MI2 = getState(EID2); |
| 3. if (MI1 == null or MI2 == null){ |
| 4. return false;} |
| 5. if (MI1.Flag == ‘UID’){ |
| 6. MI1, MI2 = MI2, MI1;} |
| 7. RLOC1 = MI1.RLOC; |
| 8. RID = MI1.ID; |
| 9. TS = (getState(MI2.ID)).TS; |
| 10. for T in TS{ |
| 11. if (T.Time + T.D > time.now ( ) && T.RID == RID){ |
| 12. RLOC2 = MI2.RLOC; |
| 13. return RLOC1, RLOC2;}} |
| 14. return false; |
4.3. Security Feedback Module
The security feedback module is deployed after the access control module and separation mapping module, to monitor access traffic and block malicious traffic in time; it is the third line of security for the system. The working mechanism of the module is as follows:
(1) Traffic detection
To monitor user access behavior, traffic detection methods need to be deployed at smart gateways. Traffic detection methods are a class of software that analyzes traffic data and identifies abnormal traffic in the network through port-based, signature-based, machine learning-based, and deep packet inspection-based methods [
25]. It should be noted that our system supports the deployment of any traffic detection method as long as the method is able to analyze network traffic in real time and output detection results containing abnormal IP addresses.
For example, in [
26], the author built self-generated dataset by simulating traffic attacks on an experimental platform, used it to train neural networks, combined the trained model and statistics detection model to detect network traffic, and reported detection results in real time. This method is well suited for deployment in our system.
(2) Locating UID based on EID
For the output of abnormal traffic information by traffic detection methods, the system has to figure out that which user is using the EID address for communication. Thus, the identity of the abnormal user (UID) is located by calling function getState(EID) to get the corresponding MI, and the abnormal user’s behavior record and other information are easily acquired by calling function getState(MI.ID).
(3) Credit evaluation
Considering that the traffic detection method has a certain false alarm rate, after locating the identity of the sender of the abnormal traffic, it is necessary to make further judgments in conjunction with their behavior records in the system. The behavior records refer to the parameters, AuthenF, AuthenS, AbacF, AbacS, etc. in
Table 1, which are recorded and updated by the blockchain every time the user requests to perform an authentication and authorization process. The abnormal user credit is evaluated by Equation (1). If the credit is higher than a certain threshold, the abnormal user is considered to have good access behavior and identified as a normal user. Otherwise, when both the traffic detection method and credit evaluation deems the user’s behavior abnormal, the abnormal user is identified as a malicious user.
(4) Information feedback
For malicious users, the inter-module interface is used to feedback their information, and other modules respond in time. Specifically, the access control module will delete the identity information of the malicious user and no longer provide access authorization for him, whereas the separation mapping module will delete the mapping information of the malicious user and no longer forward their traffic to the core network. Finally, the proposed system will successfully stop malicious users from attacking IoT devices.
In the introduction above, steps 2–4 are all implemented on the blockchain through the security feedback smart contract (SF_SC), which guarantees the trustworthiness of the verdict, using Algorithm 6.
Algorithm 6 implements the identity location, credit evaluation, and user classification for abnormal traffic.
| Algorithm 6 User_Judge |
| Input EID of abnormal traffic |
| Output Credit evaluation result |
| 1. result = false; |
| 2. MI = getState(EID); |
| 3. if (MI == null or MI.Flag == ‘RID’){ |
| 4. return result;} |
| 5. UI = getState(MI.ID); |
| 6. credit = credit_evaluate(UI); |
| 7. if (credit < 60){ |
| 8. result = true;} |
| 9. else { |
| 10. return result;} |
Algorithm 7 receives malicious user’s EID as input and removes all information about the malicious user from the blockchain in time, thus completing the security feedback and response process.
| Algorithm 7 Delete |
| Input EID of malicious traffic |
| Output None |
| 1. MI = getState(EID); |
| 2. UID = MI.ID; |
| 3. deleteState(EID); |
| 4. deleteState(UID); |
| 5. return; |