Trustability for Resilient Internet of Things Services on 5G Multiple Access Edge Cloud Computing
Abstract
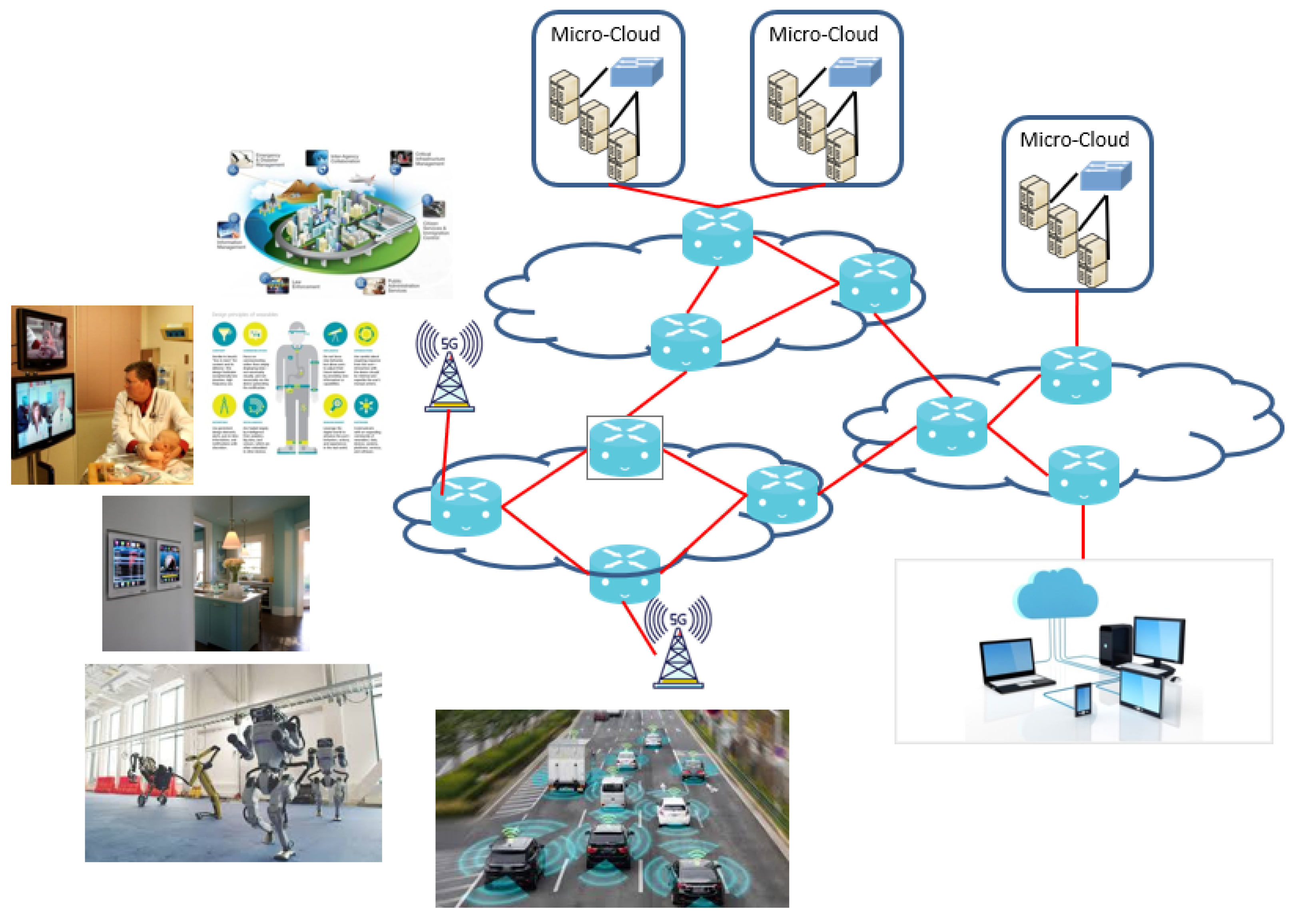
:1. Introduction
- The trustability metric was demonstrated using a sampling subsystem with a sensor activation option, where an external attack occurs on a sensor;
- Different possible outcomes of internal incident scenarios were presented in a sample cloud environment, where the trustability of the service is tracked by the framework for each scenario;
- The trustability metric captured the trustability of the service whenever the cloud architecture allowed for the addition and removal of extra nodes for each task;
- The net utility function captured the need for additional nodes and helped to decide when to remove nodes in order to optimize the utility of the service;
- Overall, this paper proposes the use of a trust management framework with a trustability metric and a net utility function on a variety of external and internal incident scenarios in order to help take timely actions to keep the service alive and optimize the utility.
2. Materials and Methods
2.1. Trust Management Framework
2.2. Trust Management in Systems and Cloud
2.3. Redundancy, Cost, and Utility
| Algorithm 1: Trustability, , is calculated as an exponential function, where is decided by comparing the impression, m, with the threshold, . |
| Input: |
| Output: |
| if then |
| | |
| end |
| else |
| | |
| end |
3. Results and Discussion
3.1. External Attacks
3.2. Internal Incidents
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| 5G | Fifth Generation |
| 6G | Sixth Generation |
| CISA | Cybersecurity and Infrastructure Security Agency |
| IoT | Internet of Things |
| MEC | Multi-access Edge Computing |
| AI | Artificial Intelligence |
| DM | Decision Maker |
| S | Sensor |
| N | Node |
| UAV | Unmanned Aerial Vehicle |
| US | United States |
| USDA | United States Department of Agriculture |
| NIFA | National Institute of Food and Agriculture |
| NSF | National Science Foundation |
References
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.; Konwinski, A.; Lee, G.; Patterson, D.; Rabkin, A.; Stoica, I.; et al. A view of cloud computing. Commun. ACM 2010, 53, 50–58. [Google Scholar] [CrossRef] [Green Version]
- Dinh, H.T.; Lee, C.; Niyato, D.; Wang, P. A survey of mobile cloud computing: Architecture, applications, and approaches. Wirel. Commun. Mob. Comput. 2013, 13, 1587–1611. [Google Scholar] [CrossRef]
- Krutz, R.L.; Vines, R.D. Cloud Security: A Comprehensive Guide to Secure Cloud Computing; Wiley Publishing: Hoboken, NJ, USA, 2010. [Google Scholar]
- Rong, C.; Nguyen, S.T.; Jaatun, M.G. Beyond lightning: A survey on security challenges in cloud computing. Comput. Electr. Eng. 2013, 39, 47–54. [Google Scholar] [CrossRef]
- Pearson, S. Privacy, security and trust in cloud computing. In Privacy and Security for Cloud Computing; Springer: London, UK, 2013; pp. 3–42. [Google Scholar]
- Xia, F.; Yang, L.T.; Wang, L.; Vinel, A. Internet of things. Int. J. Commun. Syst. 2012, 25, 1101. [Google Scholar] [CrossRef]
- Chettri, L.; Bera, R. A comprehensive survey on Internet of Things (IoT) toward 5G wireless systems. IEEE Internet Things J. 2019, 7, 16–32. [Google Scholar] [CrossRef]
- Goyal, M.; Prakash, S.; Xie, W.; Bashir, Y.; Hosseini, H.; Durresi, A. Evaluating the Impact of Signal to Noise Ratio on IEEE 802.15.4 PHY-Level Packet Loss Rate. In Proceedings of the 2010 13th International Conference on Network-Based Information Systems, Takayama, Japan, 14–16 September 2010; pp. 279–284. [Google Scholar] [CrossRef]
- Yang, T.; Ikeda, M.; Mino, G.; Barolli, L.; Durresi, A.; Xhafa, F. Performance Evaluation of Wireless Sensor Networks for Mobile Sink Considering Consumed Energy Metric. In Proceedings of the 2010 IEEE 24th International Conference on Advanced Information Networking and Applications Workshops, Perth, WA, Australia, 20–23 April 2010; pp. 245–250. [Google Scholar] [CrossRef] [Green Version]
- Xie, W.; Goyal, M.; Hosseini, H.; Martocci, J.; Bashir, Y.; Baccelli, E.; Durresi, A. A Performance Analysis of Point-to-Point Routing along a Directed Acyclic Graph in Low Power and Lossy Networks. In Proceedings of the 2010 13th International Conference on Network-Based Information Systems, Takayama, Japan, 14–16 September 2010; pp. 111–116. [Google Scholar] [CrossRef] [Green Version]
- Durresi, A.; Paruchuri, V. Geometric broadcast protocol for sensor and actor networks. In Proceedings of the 19th International Conference on Advanced Information Networking and Applications (AINA’05), Taipei, Taiwan, 28–30 March 2005; Volume 1, pp. 343–348. [Google Scholar] [CrossRef]
- Ullo, S.L.; Sinha, G.R. Advances in smart environment monitoring systems using IoT and sensors. Sensors 2020, 20, 3113. [Google Scholar] [CrossRef]
- Park, S.; Choi, J.Y. Hierarchical anomaly detection model for in-vehicle networks using machine learning algorithms. Sensors 2020, 20, 3934. [Google Scholar] [CrossRef]
- Islam, S.R.; Kwak, D.; Kabir, M.H.; Hossain, M.; Kwak, K.S. The internet of things for health care: A comprehensive survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Hussein, N.H.; Khalid, A. A survey of cloud computing security challenges and solutions. Int. J. Comput. Sci. Inf. Secur. 2016, 14, 52. [Google Scholar]
- Sarwar, A.; Khan, M.N. A review of trust aspects in cloud computing security. Int. J. Cloud Comput. Serv. Sci. 2013, 2, 116. [Google Scholar] [CrossRef]
- Barlet, G. CISA’s StrategicPlan Is Ushering in a New Cybersecurity Era. 2022. Available online: https://www.darkreading.com/vulnerabilities-threats/cisa-s-strategic-plan-is-ushering-in-a-new-cybersecurity-era (accessed on 5 December 2022).
- Easterly, J. CISA Strategic Plan 2023–2025. 2022. Available online: https://www.cisa.gov/sites/default/files/publications/StrategicPlan_20220912-V2_508c.pdf (accessed on 5 December 2022).
- Li, N.; Mitchell, J.C.; Winsborough, W.H. Design of a role-based trust-management framework. In Proceedings of the 2002 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 12–15 May 2002; pp. 114–130. [Google Scholar]
- Zhang, P.; Durresi, A. Trust management framework for social networks. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; pp. 1042–1047. [Google Scholar]
- Ruan, Y.; Alfantoukh, L.; Durresi, A. Exploring stock market using twitter trust network. In Proceedings of the Advanced Information Networking and Applications (AINA), 2015 IEEE 29th International Conference, Gwangiu, Republic of Korea, 24–27 March 2015; pp. 428–433. [Google Scholar]
- Zhang, P.; Durresi, A.; Barolli, L. Survey of trust management on various networks. In Proceedings of the Complex, Intelligent and Software Intensive Systems (CISIS), 2011 International Conference, Seoul, Republic of Korea, 30 June–2 July 2011; pp. 219–226. [Google Scholar]
- Ruan, Y.; Durresi, A. A survey of trust management systems for online social communities—Trust modeling, trust inference and attacks. Knowl.-Based Syst. 2016, 106, 150–163. [Google Scholar] [CrossRef] [Green Version]
- Ruan, Y.; Zhang, P.; Alfantoukh, L.; Durresi, A. Measurement theory-based trust management framework for online social communities. Acm Trans. Internet Technol. 2017, 17, 16. [Google Scholar] [CrossRef]
- Ruan, Y.; Durresi, A.; Alfantoukh, L. Using Twitter trust network for stock market analysis. Knowl.-Based Syst. 2018, 145, 207–218. [Google Scholar] [CrossRef] [Green Version]
- Uslu, S.; Kaur, D.; Rivera, S.J.; Durresi, A.; Babbar-Sebens, M. Trust-Based Game-Theoretical Decision Making for Food-Energy-Water Management. In Proceedings of the International Conference on Broadband and Wireless Computing, Communication and Applications, Antwerp, Belgium, 7–9 November 2019; Springer: Cham, Switzerland, 2019; pp. 125–136. [Google Scholar]
- Uslu, S.; Kaur, D.; Rivera, S.J.; Durresi, A.; Babbar-Sebens, M. Trust-Based Decision Making for Food-Energy-Water Actors. In Proceedings of the International Conference on Advanced Information Networking and Applications, Caserta, Italy, 15–17 April 2020; Springer: Cham, Switzerland, 2020; pp. 591–602. [Google Scholar]
- Uslu, S.; Kaur, D.; Rivera, S.J.; Durresi, A.; Babbar-Sebens, M.; Tilt, J.H. Control Theoretical Modeling of Trust-Based Decision Making in Food-Energy-Water Management. In Proceedings of the International Conference on Broadband and Wireless Computing, Communication and Applications, Yonago, Japan, 28–30 October 2020; Springer: Cham, Switzerland, 2020; pp. 97–107. [Google Scholar]
- Kaur, D.; Uslu, S.; Durresi, A.; Mohler, G.; Carter, J.G. Trust-Based Human-Machine Collaboration Mechanism for Predicting Crimes. In Proceedings of the International Conference on Advanced Information Networking and Applications, Caserta, Italy, 15–17 April 2020; Springer: Cham, Switzerland, 2020; pp. 603–616. [Google Scholar]
- Kaur, D.; Uslu, S.; Durresi, A. Trust-Based Security Mechanism for Detecting Clusters of Fake Users in Social Networks. In Proceedings of the Workshops of the International Conference on Advanced Information Networking and Applications, Matsue, Japan, 27–29 March 2019; Springer: Cham, Switzerland, 2019; pp. 641–650. [Google Scholar]
- Rittichier, K.J.; Kaur, D.; Uslu, S.; Durresi, A. A Trust-Based Tool for Detecting Potentially Damaging Users in Social Networks. In International Conference on Network-Based Information Systems; Springer: Cham, Switzerland, 2021; pp. 94–104. [Google Scholar]
- Li, J.; Li, R.; Kato, J. Future trust management framework for mobile ad hoc networks. IEEE Commun. Mag. 2008, 46, 108–114. [Google Scholar]
- Movahedi, Z.; Hosseini, Z.; Bayan, F.; Pujolle, G. Trust-distortion resistant trust management frameworks on mobile ad hoc networks: A survey. IEEE Commun. Surv. Tutorials 2015, 18, 1287–1309. [Google Scholar] [CrossRef]
- Ruan, Y.; Durresi, A.; Alfantoukh, L. Trust management framework for internet of things. In Proceedings of the Advanced Information Networking and Applications (AINA), 2016 IEEE 30th International Conference, Crans-Montana, Switzerland, 23–25 March 2016; pp. 1013–1019. [Google Scholar]
- Ruan, Y.; Durresi, A.; Uslu, S. Trust Assessment for Internet of Things in Multi-access Edge Computing. In Proceedings of the 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 1155–1161. [Google Scholar]
- Ruan, Y.; Durresi, A. A trust management framework for cloud computing platforms. In Proceedings of the Advanced Information Networking and Applications (AINA), 2017 IEEE 31st International Conference, Taipei, Taiwan, 27–29 March 2017; pp. 1146–1153. [Google Scholar]
- Kaur, D.; Uslu, S.; Durresi, M.; Durresi, A. A geo-location and trust-based framework with community detection algorithms to filter attackers in 5G social networks. Wirel. Netw. 2022, 1–9. [Google Scholar] [CrossRef]
- Pessach, D.; Shmueli, E. A Review on Fairness in Machine Learning. ACM Comput. Surv. 2022, 55, 51. [Google Scholar] [CrossRef]
- Kaur, D.; Uslu, S.; Durresi, A. Requirements for Trustworthy Artificial Intelligence–A Review. In Proceedings of the International Conference on Network-Based Information Systems, Victoria, BC, Canada, 31 August–2 September 2020; Springer: Cham, Switzerland, 2020; pp. 105–115. [Google Scholar]
- Thiebes, S.; Lins, S.; Sunyaev, A. Trustworthy artificial intelligence. Electron. Mark. 2021, 31, 447–464. [Google Scholar] [CrossRef]
- Kaur, D.; Uslu, S.; Rittichier, K.J.; Durresi, A. Trustworthy Artificial Intelligence: A Review. ACM Comput. Surv. 2022, 55, 39. [Google Scholar] [CrossRef]
- Varshney, K.R. Trustworthy machine learning and artificial intelligence. Xrds Crossroads ACM Mag. Stud. 2019, 25, 26–29. [Google Scholar] [CrossRef]
- Kaur, D.; Uslu, S.; Durresi, A. Trustworthy AI Explanations as an Interface in Medical Diagnostic Systems. In Proceedings of the International Conference on Network-Based Information Systems, Sanda-Shi, Japan, 7–9 September 2022; Springer: Cham, Switzerland, 2022; pp. 119–130. [Google Scholar]
- Uslu, S.; Kaur, D.; Rivera, S.J.; Durresi, A.; Babbar-Sebens, M.; Tilt, J.H. A Trustworthy Human–Machine framework for collective decision making in Food–Energy–Water management: The role of trust sensitivity. Knowl.-Based Syst. 2021, 213, 106683. [Google Scholar] [CrossRef]
- European Comission. Ethics Guidelines for Trustworthy AI; Technical Report. 2018. Available online: https://digital-strategy.ec.europa.eu/en/library/ethics-guidelines-trustworthy-ai (accessed on 5 December 2022).
- ISO/IEC TR 24028:2020; Information Technology—Artificial Intelligence—Overview of Trustworthiness in Artificial Intelligence. International Organization for Standardization: Geneva, Switzerland, 2020.
- Cao, H.; Zou, W.; Wang, Y.; Song, T.; Liu, M. Emerging Threats in Deep Learning-Based Autonomous Driving: A Comprehensive Survey. arXiv 2022, arXiv:2210.11237. [Google Scholar]
- Khan, M.A.; Kumar, N.; Mohsan, S.A.H.; Khan, W.U.; Nasralla, M.M.; Alsharif, M.H.; Żywiołek, J.; Ullah, I. Swarm of UAVs for Network Management in 6G: A Technical Review. IEEE Trans. Netw. Serv. Manag. 2022; early access. [Google Scholar] [CrossRef]
- Saraswat, D.; Verma, A.; Bhattacharya, P.; Tanwar, S.; Sharma, G.; Bokoro, P.N.; Sharma, R. Blockchain-Based Federated Learning in UAVs Beyond 5G Networks: A Solution Taxonomy and Future Directions. IEEE Access 2022, 10, 33154–33182. [Google Scholar] [CrossRef]
- Velliangiri, S.; Manoharan, R.; Ramachandran, S.; Rajasekar, V. Blockchain Based Privacy Preserving Framework for Emerging 6G Wireless Communications. IEEE Trans. Ind. Inform. 2022, 18, 4868–4874. [Google Scholar] [CrossRef]
- Uslu, S.; Kaur, D.; Rivera, S.J.; Durresi, A.; Durresi, M.; Babbar-Sebens, M. Trustworthy Acceptance: A New Metric for Trustworthy Artificial Intelligence Used in Decision Making in Food-Energy-Water Sectors. In Proceedings of the International Conference on Advanced Information Networking and Applications, Toronto, ON, Canada, 12–14 May 2021; Springer: Cham, Swizerland, 2021; pp. 208–219. [Google Scholar]
- Uslu, S.; Kaur, D.; Rivera, S.J.; Durresi, A.; Durresi, M.; Babbar-Sebens, M. Trustworthy Fairness Metric Applied to AI-Based Decisions in Food-Energy-Water. In Proceedings of the International Conference on Advanced Information Networking and Applications, Sydney, NSW, Australia, 13–15 April 2022; Springer: Cham, Switzerland, 2022; pp. 433–445. [Google Scholar]
- Kaur, D.; Uslu, S.; Durresi, A.; Badve, S.; Dundar, M. Trustworthy Explainability Acceptance: A New Metric to Measure the Trustworthiness of Interpretable AI Medical Diagnostic Systems. In Proceedings of the Conference on Complex, Intelligent, and Software Intensive Systems, Asan, Republic of Korea, 1–3 July 2021; Springer: Cham, Switzerland, 2021; pp. 35–46. [Google Scholar]
- Ruan, Y.; Durresi, A. A trust management framework for clouds. Comput. Commun. 2019, 144, 124–131. [Google Scholar] [CrossRef]
















Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Uslu, S.; Kaur, D.; Durresi, M.; Durresi, A. Trustability for Resilient Internet of Things Services on 5G Multiple Access Edge Cloud Computing. Sensors 2022, 22, 9905. https://doi.org/10.3390/s22249905
Uslu S, Kaur D, Durresi M, Durresi A. Trustability for Resilient Internet of Things Services on 5G Multiple Access Edge Cloud Computing. Sensors. 2022; 22(24):9905. https://doi.org/10.3390/s22249905
Chicago/Turabian StyleUslu, Suleyman, Davinder Kaur, Mimoza Durresi, and Arjan Durresi. 2022. "Trustability for Resilient Internet of Things Services on 5G Multiple Access Edge Cloud Computing" Sensors 22, no. 24: 9905. https://doi.org/10.3390/s22249905
APA StyleUslu, S., Kaur, D., Durresi, M., & Durresi, A. (2022). Trustability for Resilient Internet of Things Services on 5G Multiple Access Edge Cloud Computing. Sensors, 22(24), 9905. https://doi.org/10.3390/s22249905




