A Consortium Blockchain-Based Secure and Trusted Electronic Portfolio Management Scheme
Abstract
:1. Introduction
1.1. Issues and Challenges
- How can secure, reliable, privacy-preserving e-portfolio credential issuance and verification be enabled?
- How can e-portfolio data authenticity and integrity be guaranteed?
- How can the blockchain enable learners to own, publish, and manage their e-portfolios while providing recruiters or potential employers the ability to verify the e-portfolio credentials and artifacts in a decentralized fashion?
1.2. Contributions
- We propose a consortium blockchain-based decentralized, secure, and trusted e-portfolio management scheme that is integrated with recruitment platforms. This system provides users with effective methods for sharing their e-portfolios when applying to job opportunities, searching candidate profiles, matching, and recommending services for personalized user experiences.
- The e-portfolio data is stored in a cryptographically secure and machine-verifiable manner in which the elliptic curve digital signature algorithm (ECDSA) is adopted to guarantee data authenticity and integrity. The blockchain is used to record all the transactions and logs for tamper-proof, trusted e-portfolio data provenance, accountability, and traceability.
- We have designed and developed smart contracts that empower learners to completely own, publish, and manage their e-portfolios while enabling recruiters or potential employers to verify e-portfolio credentials and artifacts without relying on TTPs.
- Decentralized identifiers (DIDs) and verifiable credentials (VCs) are designed and implemented for the proposed scheme following the World Wide Web Consortium (W3C) standard specifications [16,17,18]. DIDs are used for user profile identification, authentication, and authorization, whereas VCs are used for e-portfolio credential proof authentication and verification.
- A prototype of the proposed scheme is built using the Quorum blockchain for secure, confidential, quick, and privacy-protected transactions, as well as scalable performance in the consortium network. In addition, we analyzed the privacy and security of the system and provided an evaluation of its performance. The performance is evaluated in terms of computational complexity, transaction latency and throughput, block propagation latency, e-certificate signing, and generation and verification time.
2. Background and Related Work
2.1. Electronic Portfolio Concepts
2.2. Verifiable Claims
2.3. Decentralized Identifiers (DIDs)
| Listing 1. Example of a DID document schema in JSON-LD 1 format. |
| 1: {“@context”:”https://www.w3.org/ns/did/v1”, |
| 2: “id”:”did:example:2d3fAe6954e1Dg3f3a0c9f4a04AF796a”, |
| 3: “type”: [“UserProfileIdentifier”], |
| 4: “issuer”:”did:example:6384c92b19ed2Ab67f9c1V423F9e3421”, |
| 5: “issuanceDate”:”2022-01-03T14:15:26Z”, |
| 6: “publicKey”: [{ |
| 7: “id”:”did:example:2d3fAe6954e1Dg3f3a0c9f4a04AF796a/#keys-1”, |
| 8: “type”:”Ed25519VerificationKey2020”, |
| 9: “publicKeyMultibase”:”5hcZuqdn7qbXgfpEmq…wcJgR19YA3VWgB”}], |
| 10: “claim”: { |
| 11: “id”:”did:example:2d3fAe6954e1Dg3f3a0c9f4a04AF796a”, |
| 12: “fullName”: “Mpyana Merlec”, |
| 13: “email”:”abc@example.com”, |
| 14: “profileURL”: [“https://myprofile.org”, “https://linkedin.com/myprofile”], |
| 15: “affiliation”: { |
| 16: “position”: “Graduate student”, |
| 17: “institution”: { |
| 18: “name”:”Korea University”, |
| 19: “department”: “Computer Science and Engineering” } |
| 20: } |
| 21: }, |
| 22: “authentication”:[{ |
| 23: “type”:”Ed25519VerificationKey2020”, |
| 24: “publicKey”:”5hcZuqdn7qbXgfpExP…aTPYTwcJgR19YA3VWgB”, |
| 25: “signatureValue”:”4xRJc5oMwKiVXZAeUTk…JFuC9hy5cDpJeujmbaZpYDF” }], |
| 26: “proof”:{ |
| 27: “type”:”Ed25519Signature2020”, |
| 28: “created”:”2022-01-03T15:12:19Z”, |
| 29: “creator”:”did:example:2d3fAe6954e1Dg3f3a0c9f4a04AF796a”, |
| 30: “verificationMethod”:”did:example:2d3fAe6954e1…a04AF796a/issuer#01”, |
| 31: “signatureValue”:”2G3YnyHsvgKBtm8Q2m…i3j1tER4R4aC67PckWpWx5N”} |
| 32: } |
| 1 JavaScript object notation for linked data—https://json-ld.org/ (accessed on 31 January 2022). |
2.4. Verifiable Credentials and Presentations
| Listing 2. Example of a verifiable credential schema in JSON-LD format. |
| 1: {“@context”:” https://www.w3id.org/credentials/v1”, |
| 2: “id”:”did:example:16ac244ea930bc2cbf225c3d15b44674”, |
| 3: “type”: [“ePortfolioVerifiableCredential”], |
| 4: “issuer”:”did:example:8d6fbg6410e1071f2a0c9f4a04eE726a”, |
| 5: “issuanceDate”:”2022-01-04T16:15:24Z”, |
| 6: “expiringDate”:”2023-01-03T16:15:24Z”, |
| 7: “claim”: { |
| 8: “id”:”did:example: d6259eEA53eRi1ac8b16807fade3c70660b”, |
| 9: “type”:”ePortfolioVerifiableCredential”, |
| 10: “title”:”Blockchain-based e-Portfolio Management System”, |
| 11: “portfolioURL”:”http://github.com/myportfio/ePortfolio”, |
| 12: “created”:”2022-01-03T14:10:12Z”, |
| 13: “creator”: [{“id”:”did:example:2d3fAe6954e1Dg3f3a0c9f4a04AF796a’”}], |
| 14: “reviewer”: [{“id”:”did:example:1531b2D926ac6379aG4fw6520bd7a30b”}], |
| 15: “evaluator”: [{“id”:”did:example:6384c92b19ed2Ab67f9c1V423F9e3421”}], |
| 16: “score”:”95”}, |
| 17: “proof”: { |
| 18: “type”:”Ed25519Signature2020”, |
| 19: “created”:”2022-01-05T14:12:19Z”, |
| 20: “creator”:”did:example:6384c92b19ed2Ab67f9c1V423F9e3421”, |
| 21: “proofPurpose”:”ePortfolioCredentialVerification”, |
| 22: “verificationMethod”:”ttps://example.edu/issuers/keys/#1”, |
| 23: “signitureValue”:”sITJX1CxPCT8yAVPAYuN...zVBAh4vGHSrQyHUdBBPM” } |
| 24: } |
2.5. Cryptography Primitives
| Algorithm 1. Ed25519 key setup and signature generation [20] |
| Curve parameter: G(x, y), a, d, p, order n |
| Input: secret key Sk, message M |
| Output: signature S |
| 1: Hash k: h = SHA512(Sk) |
| 2: a = h[0 : 32] |
| 3: a = h[32 : 64] |
| 4: c = SHA512(b M) |
| 5: Interpret a and c as integers in little-endian notation. |
| 6: Compute public key: Pk = SkG |
| 7: Generate the first part of signature: R = cG |
| 8: h′ = SHA512(R Pk M) |
| 9: Interpret h′ as an integer in little-endian notation. |
| 10: Generate the second part of signature: s = (c + ah′) mod n |
| 11: Combine signature pair: S = encode(R) + encode(s) |
| 12: return signature S. |
| Algorithm 2. Ed25519 signature verification [20] |
| Curve parameter: G(x, y), a, d, p, order n |
| Input: message M, public key Pk, signature S |
| Output: True/False |
| 1: Separate signature pair: R, s = S[0 : 32], decode(S[32 : 64]) |
| 2: h = SHA512(R Pk M) |
| 3: Interpret h as an integer in little-endian notation. |
| 4: return |
2.6. Consortium Blockchain
- Access control permission: Permissions at the network and system level are required for nodes and users to join and operate in the consortium blockchain network. A set of roles and various permissions are assigned to each user account and node.
- Consensus-driven decentralized governance: The blockchain is governed by the consensus of a set of authorized participating nodes in a decentralized manner. It is easy to manage and enforce the infrastructure’s rules and policies.
- Low energy and computing resource consumption: The consortium blockchain does not use PoW-like consensus protocols, which consume considerable energy and computing resources when solving complex mathematical puzzles.
- Confidentiality and privacy: Consortium blockchains provide support for transaction confidentiality and privacy. They are essential for enterprise blockchain decentralized applications (DApps).
- High transaction throughput: Consortium blockchain networks providing high transaction throughput as a consensus on the state of the ledger can be rapidly reached via a set of authorized validator nodes.
- Security and scalability: The consortium blockchain provides fault tolerance capability and better protection against disturbances even when nodes behave arbitrarily or maliciously.
2.7. Related Work
| Paper | User-Centric | E-Portfolio | RPI 1 | DIDs/VCs & VPs 2 | Verifiable Repository | Smart Contract | Blockchain Network/ Platform | Privacy/Security | Implementation | Performance Evaluation |
|---|---|---|---|---|---|---|---|---|---|---|
| [5,6,7,8] | √ | √ | X | X/X | X | X | X/X | X/X | X | X |
| [14] | √ | X | X | √/√ | X | X | Public/- | √/√ | √ | X |
| [29] | √ | √ | √ | X/X | X | X | - | X/X | X | X |
| [30] | √ | X | X | X/X | X | X | Private/- | X/X | √ | X |
| [31] | √ | √ | X | X/X | X | √ | Consortium/- | - | X | X |
| [33] | √ | √ | X | X/X | X | √ | Consortium/Hyperledger Fabric | √/√ | Prototype | √ |
| [34] | √ | √ | X | X/X | X | √ | Consortium/Hyperledger Fabric | √/√ | Prototype | X |
| [35] | √ | X | X | X/X | X | √ | Private/Ethereum | √/√ | Prototype | √ |
| [36] | √ | √ | X | X/X | X | √ | Public/Ethereum | X/√ | Prototype | X |
| [37] | √ | √ | X | X/X | X | √ | Consortium/Hyperledger Fabric | √/√ | Prototype | √ |
| [38] | √ | X | X | X/X | X | √ | Public/Ethereum | X/√ | Prototype | X |
| [39] | √ | X | X | √/√ | X | √ | Public/Ethereum | X/√ | √ | X |
| [40] | √ | X | X | X/X | X | - | Semiprivate/- | √/√ | √ | X |
| [41] | √ | X | X | X/X | X | √ | Private/Ethereum | √/√ | Prototype | X |
| [42] | √ | X | X | X/X | X | √ | Consortium/Hyperledger Fabric | √/√ | Prototype | √ |
| [45] | √ | X | X | X/X | X | √ | Public/Ethereum | X/√ | Prototype | √ |
| This work | √ | √ | √ | √/√ | √ | √ | Consortium/Quorum | √/√ | Prototype | √ |
3. Proposed Scheme
3.1. Key Stakeholder and Role Identification
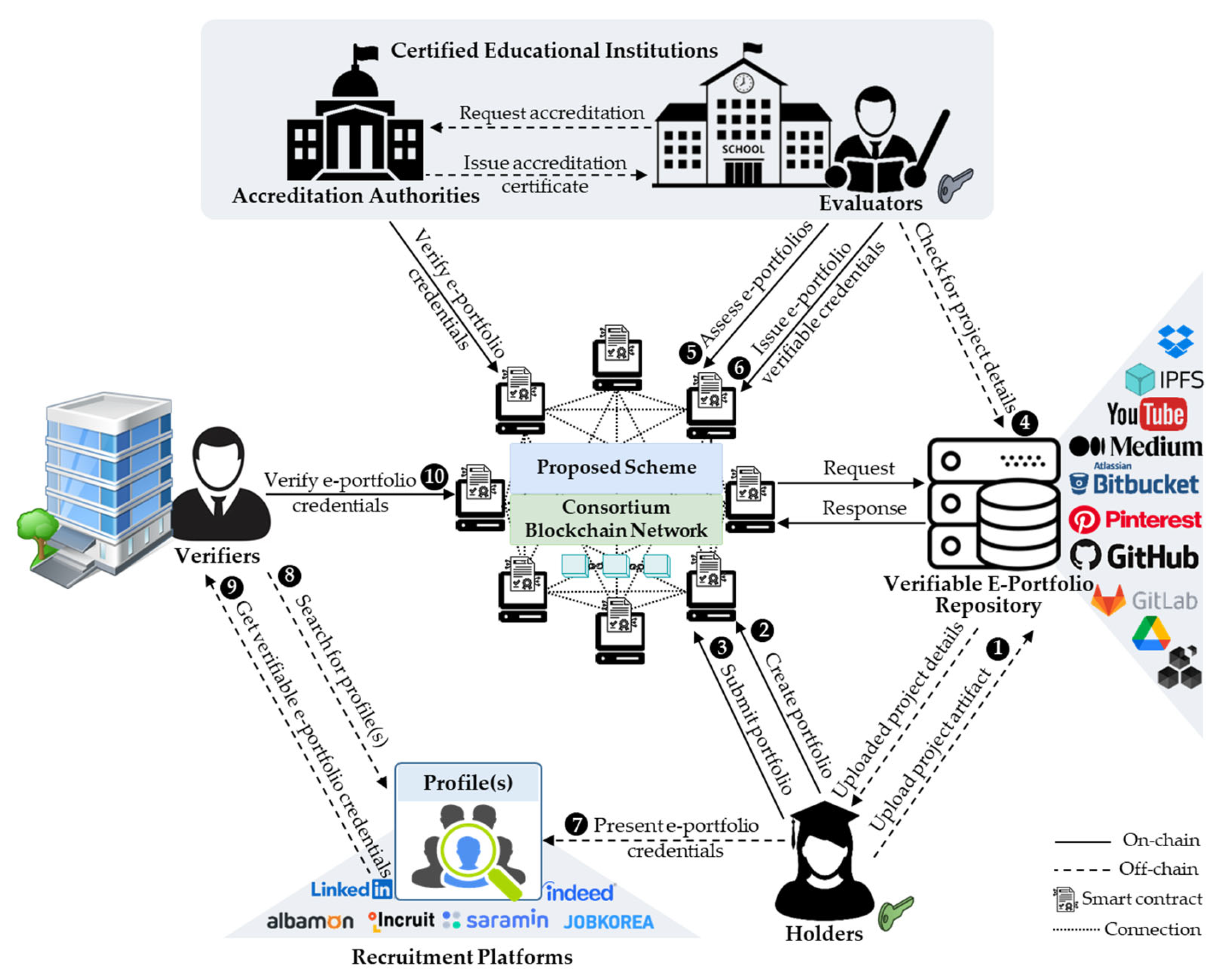
- Accreditation authorities certify educational institutions and evaluators by issuing verifiable credentials to them. Accreditation authorities include governments, higher education ministries, and national or international education accreditation agencies.
- Certified educational institutions (i.e., colleges, universities, or training centers) provide learning programs, assess learners, and certify learning results and artifacts by issuing cryptographically secure and machine-verifiable e-certificate credentials.
- Holders (i.e., students or lifelong learners) completely own, publish, and manage e-portfolios. Portfolio holders possess verifiable credentials, from which verifiable presentations are generated and shared with verifiers to prove ownership.
- Evaluators (i.e., accredited professors, instructors, or teachers) assess submitted e-portfolio claims and issue and transmit verifiable certificate credentials to the e-portfolio holders. Submitted portfolios can also be peer-reviewed by experts who are seen as certified reviewers.
- Verifiers, by receiving verifiable credentials using smart contracts, verify the e-portfolio certificate credential’s authenticity and integrity. Examples of verifiers include company recruiters, employers, and higher education supervisors.
- Recruitment platforms (i.e., LinkedIn, Indeed, and SaramIn) provide job or internship opportunity postings, candidate profiles searching, matching, and recommendation services.
- A verifiable e-portfolio repository is a system that allows users to store, share, and access e-portfolio resources. Verifiable e-portfolio repositories contain publicly, selectively, or privately published verifiable e-portfolio artifacts such as research papers, interview audio or videos, and application source codes. These repositories may require the use of DIDs and verifiable credentials. Examples of verifiable e-portfolio repositories include decentralized databases or distributed ledger-based registries.
- (1)
- The portfolio holders upload their e-portfolio project artifacts to the e-portfolio repositories, which are protected by private keys for ownership and access control.
- (2)
- Subsequently, the portfolio holders create and edit e-portfolio proposals, which can be temporarily saved until their completion.
- (3)
- After completing, holders can submit their e-portfolio proposals to be assessed by evaluators, who are accredited instructors or professors.
- (4)
- The evaluators first check that the artifacts in the submitted e-portfolios are published in a verifiable repository.
- (5)
- Thereafter, evaluators can assess the submitted e-portfolios by evaluating the individual student or learner’s performance and achievement(s). If there are no complaints from learners, evaluators can sign and confirm the evaluation results, which are recorded in the blockchain.
- (6)
- E-certificates can be issued for all assessed and confirmed e-portfolios that satisfy the requirements. These certificates are signed and sent to the corresponding holders. Every e-certificate is digitally signed using the private and public key pair of the evaluator who assessed the corresponding e-portfolio. The public key is encoded in a QR code, which is embedded in the e-certificate and is used for verifying the authenticity and integrity of the e-portfolio credentials.
- (7)
- Thereafter, the e-portfolio holders can add or publish the e-portfolio certificates on their recruitment platform profiles, which can be used as evidence of learning achievements and presented to recruiters or potential employers.
- (8)
- Verifiers (i.e., recruiters) can search for candidate profiles that match their job requirements.
- (9)
- Verifiers can request e-portfolio credentials from the candidate holders for authenticity and integrity verification.
- (10)
- Using smart contracts, verifiers confirm the authenticity and integrity of the e-portfolio credentials stored in the blockchain.
3.2. System Architecture
- The secure and trusted e-portfolio management layer provides secure and reliable e-portfolio management features, and it consists of the following modules:
- (a)
- The user profile manager is responsible for managing membership enrollments, user profiles, roles, DIDs, and credentials. It is composed of four sub-modules. (a) The enrollment manager provides features that support the user enrollment process; (b) the membership manager is used to assign and revoke membership credentials; (c) the profile manager manages the user profiles’ personal information, and (d) the user role manager is used for assigning and managing user profile roles.
- (b)
- The e-portfolio manager manages learners’ e-portfolios, which are assessed and certified by educators. It comprises the following sub-components: (a) Portfolio editor and viewer modules are used by learners to create and edit e-portfolios. They display the list of e-portfolios, which are filtered by category and status. (b) The assessment manager is used by learners and evaluators to submit e-portfolio assessment requests and to assess submitted e-portfolios, respectively. (c) The review manager enables reviewers to assess e-portfolios, and (d) the recommendation manager recommends user profiles based on their e-portfolio characteristics to provide personalized user experiences.
- (c)
- The verifiable credentials manager is responsible for generating, verifying, validating, and publishing e-portfolio certificates, and it comprises the following: (a) the e-certificate generator issues on-demand digital certificates for assessed e-portfolios; (b) verifier and validator submodules verify and validate the results of verified e-portfolio certificates; (c) the e-certificate publisher records e-portfolio certificates details on the blockchain; (d) the e-certificate viewer displays the recorded e-portfolio certificates.
- (d)
- The security and privacy manager provides custom user security and privacy management functionalities. It comprises the following modules: (a) The security manager provides user credentials and e-portfolio data security-related features such as authentication, authorization, confidentiality, and accountability. (b) The access control manager authorizes or denies access to e-portfolio data depending on the access control policies and rules embedded in the consent agreement contracts [47]. (c) The privacy manager helps users define and manage their privacy preferences, and (d) the audit manager enables users to audit their e-portfolio history in terms of when it was requested and accessed and by whom for verification. The user profile manager and security and privacy manager components extend the generic permissioned features provided by the lower layer.
- The blockchain technology and decentralized storage layer provides a consortium blockchain-based immutable transaction distributed ledger and state database, which are maintained via a consensus of authorized peer nodes in the network. This layer provides an operating environment for running smart contracts.
- (a)
- Quorum blockchain [27] has two core components: (a) the Quorum node, which is a forked version of the Go-Ethereum client and is modified to support contract and transaction privacy, and (b) the private transaction manager (PTM), which comprises the transaction manager (TM) and enclave sub-modules. The TM manages private transactions by allowing the access and exchange of encrypted transaction data only between authorized participant nodes. The enclave is a distributed ledger component that independently provides the cryptographic methods used for symmetric key generation, data encryption, and decryption.
- (b)
- The decentralized storage system orchestrates the verifiable e-portfolio repository data storage and access in a distributed or decentralized fashion. It comprises three core components: (a) The API gateway provides application programming interfaces (APIs) to access and interact with the e-portfolio repository; (b) the e-portfolio repository manager manages the e-portfolio repository contents, and (c) the e-portfolio management transactional database (PMS_TDB) is a distributed database used to store the transaction records before being committed and pushed to the blockchain ledger.
- The secure communication infrastructure layer provides a secure and reliable communication service based on dedicated legacy Internet secure channels or a novel secure Internet architecture, known as SCION (scalability, control, and isolation on next-generation networks) [48], that enables private paths.
3.3. Working Operations
3.3.1. E-Portfolio Creation and Submission
| Algorithm 3. E-portfolio registration |
| Smart contract parameter: |
| Input: |
| Output: Transaction execution state |
| 1: Collect the completed portfolios from the transactional database: P=SELECT*FROM PMS_TDB where pf_status=“COMPLETED” |
| 2: while (Pid, PN, τ, ω, ρ, Pk, s, δ, ν) do |
| 3: Check whether Pid exists in the blockchain: |
| 4: E ←sc.getPortfolioInfo(Pid) |
| 5: if E ! = NULL then |
| 6: Execute the transaction T to store Pid instance in blockchain: |
| 7: T ← sc.newPortfolio(Pid, PN, τ, ω, ρ, Pk, s, δ, ν) |
| 8: if err ! = NULL then |
| 9: return errorMessage(err.Text) |
| 10: else |
| 11: Emit sc.newPortfolioCreated(Pid, ω, ρ) |
| 12: Store Th in the PMS_TDB transactional database |
| 13: end if |
| 14: else |
| 15: return “Pid already exists” |
| 16: break exit() |
| 17: end if |
| 18: end while |
3.3.2. E-Portfolio Assessment and Certificate Issuance
| Algorithm 4. E-certificate issuance |
| Smart contract parameter: |
| Input: |
| Output: Transaction execution state |
| 1: P← sc.getCertificateInfo(Cid) |
| 2: if P == NULL then |
| 3: P ← sc.getPortfolioInfo(Pid) |
| 4: if P == NULL then |
| 5: return “No portfolio issued for Pid.” |
| 6: else |
| 7: sc.issuePortfolioCertificate(P) |
| 8: end if |
| 9: else |
| 10: return “Certificate already issued for Cid.” |
| 11: end if |
3.3.3. E-Certificate Generation and Verification
| Algorithm 5. E-certificate generation |
| Smart contract parameter: |
| Input: |
| Output: E-certificate |
| 1: P ← sc.getCertificateInfo(Cid) |
| 2: if E ! = NULL then |
| 3: Generate signature: S = Ed25519.sign(Sk, P) |
| 4: Generate QR code: QR = |
| 5: Embed P and QR on Ct. |
| 6: else |
| 7: return “No certificate issued for Cid.” |
| 8: end if |
| Algorithm 6. E-certificate verification |
| Input: Certificate, evaluator’s DID |
| Output: Verification result |
| 1: Read the QR code on the certificate. |
| 2: Extract information from the QR code. |
| 3: if P matches the certificate details then |
| 4: if Pk evaluator’s DID then |
| 5: Verify the signature: v = Ed25519.verify(P, Pk, S) |
| 6: if v == T rue then |
| 7: return “Certificate is genuine.” |
| 8: else |
| 9: return “Invalid signature” |
| 10: end if |
| 11: else |
| 12: return “Pk is not genuine.” |
| 13: end if |
| 14: else |
| 15: return “Portfolio does not match.” |
| 16: end if |
4. Implementation and Evaluation
4.1. Implementation Details
4.2. Privacy and Security Analysis
- Privacy preservation: To preserve user privacy, the identity and personal information of e-portfolio holders (learners) or evaluators from their learning institutions are not shared across different organizations. Instead, we used DIDs and VCs for user profile identification, authentication, and authorization. Verifiable claims are used for e-portfolio credential proof authentication and verification. Furthermore, the proposed solution enables users to define personalized privacy and security settings, which are supported by the underlying permissioned blockchain.
- Authentication/authorization and accountability: To access and operate the system, each user must register for a membership user profile with an authorized user role(s) assigned. As all transaction histories are logged in the blockchain-based distributed ledger to ensure traceability, all of the participants are accountable for their activities. GoQuorum [49] provides enhanced network permission models for node and user authentication and authorization.
- Data authenticity and integrity: The e-portfolio information recorded on the blockchain cannot be arbitrarily modified because the blockchain is a tamper-proof distributed ledger. To guarantee user credentials and e-portfolio data authenticity and integrity, all the transaction history and logs are saved in the blockchain for its tamper-resistance, trusted data provenance insurance, and accountability features.
- Availability and reliability: Conventional certification systems are not publicly verifiable without TTPs, whereas the proposed scheme provides a privacy-preserving self-sovereign e-certificate issuance and verification model that is decentralized, reliable, and secure. Using smart contracts, the verifiers or recruiters can easily validate a certificate by verifying the embedded QR code without interacting with the evaluator or issuing institution.
- MITM attack resilience: Making a false claim using a duplicate e-certificate is possible; however, it will not be successful. It is possible to modify the embedded e-portfolio data on the certificate or change the signature. In the case of a duplicate or tampered certificate, the signature cannot be verified by the evaluator’s public key because the portfolio information is not signed with the correct evaluator’s secret key. The only way to generate an illegitimate e-certificate is to steal the secret key of the corresponding evaluator. Therefore, evaluators are advised to store their secret keys in safe devices. Storing secret keys in insecure devices or sharing the keys with others may create opportunities for unauthorized holders to claim illegitimate e-certificates.
- Smart contract security: The security analysis of our solidity smart contracts, which are deployed on the quorum blockchain, was performed using the latest SmartCheck [55] and VeriSmart [56] tools. Smart contracts are secure against well-known vulnerabilities such as integer overflow, integer underflow, access control, unchecked low-level calls, reentrancy attacks, and timestamp manipulation. Furthermore, as quorum eliminated the transaction fees existing in the Ethereum public blockchain, users will never run out of gas [27].
4.3. Performance Evaluation
4.3.1. Computational Complexity Analysis
4.3.2. E-Portfolio Transaction Latency and Throughput
4.3.3. Block Propagation Latency
4.3.4. Certificate Signing, Generation, and Verification Time
5. Limitations and Open Challenges
5.1. Process Level
- (a)
- Smart contract vulnerabilities: As smart contracts are leveraged to automate processes, they must be correctly coded and systematically verified to ensure that they can run accurately without bugs and security vulnerabilities before deployment. In addition, smart contracts are immutably stored on the blockchain after deployment and cannot be updated or upgraded to patch bugs or security vulnerabilities. Smart contract security [55,56,57,58] is a serious issue that must be considered in terms of the entire system lifecycle from requirement analysis to coding, deployment, and maintenance.
- (b)
- Privacy and security policies: Users must define adequate privacy and security policies to protect their resources. This process might be challenging if the system does not provide sufficient support.
- (c)
- Operation standards and regulations: Operational and regulatory standards are required for a massive adoption of blockchain technology in education for lifelong records keeping and self-sovereign credentials issuance and verification.
5.2. Data Level
- (a)
- Access control and key management: Efficient access control mechanisms are required for authentication and authorization. User-friendly cryptographic key management schemes are needed to confidentially encrypt and decrypt user data.
- (b)
- Blockchain oracle: The data exchange between the off-chain and on-chain environment is enabled by smart contracts, which must be properly integrated within DApps to avoid the blockchain oracle issue [59].
- (c)
- Consensus algorithms: Robust and fault-tolerant consensus mechanisms are critical for data synchronization among participating nodes and to maintain the consistency of the ledger.
5.3. Infrastructure Level
- (a)
- Standardization: Standards are essential for enabling the resolution, authentication, and interoperability of DIDs and VCs across various domains over the Internet. Cryptographic keys are essential for creating the digital signatures used to verify user identity and prevent data tampering.
- (b)
- Organization, node, and account permissions: The consortium blockchain should support enhanced permission features at the network, organization, node, account, and resource levels depending on business needs. Organizations should be able to create sub-organizations and assign roles to their nodes and accounts. Private contracts and transactions should be visible and accessible only to authorized users.
- (c)
- Blockchain network and communication infrastructure security: Although the proposed scheme has leveraged smart contracts and a distributed ledger to enable decentralization, in some cases, integrated recruitment platforms and/or verifiable repository services (e.g., GitHub or Google Drive) may still be centralized; these services may be targeted by distributed denial-of-service (DDoS) attacks to render e-portfolio resources unavailable. However, this vulnerability can be mitigated using a secure and highly available Internet architecture like SCION [48], which provides secure multi-communication paths that cannot be hijacked and guarantees communication despite DDoS attacks. The blockchain security issues [60] also require further research.
5.4. Physical Level
6. Conclusions and Future Research
- We plan to investigate recommended algorithms for providing efficient matches between learners and educators through online education platforms and between job seekers and employers through trusted skill marketplaces.
- Automated tools for auditing and fixing smart contract vulnerabilities are essential for ensuring system security at the process level.
- The design of user-friendly and efficient key management approaches would enable users to take advantage of our proposed solution.
7. Patent
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Lorenzo, G.; Ittelson, J. An overview of e-portfolios. Educ. Learn. Initiat. 2005, 1, 1–27. [Google Scholar]
- Garis, J.W. e-Portfolios: Concepts, designs, and integration within student affairs. New Dir. Stud. Serv. 2007, 2007, 3–16. [Google Scholar] [CrossRef] [Green Version]
- Jenson, J.D.; Treuer, P. Defining the E-Portfolio: What It Is and Why It Matters. Chang. Mag. High. Learn. 2014, 46, 50–57. [Google Scholar] [CrossRef]
- Bhattacharya, M.; Hartnett, M. E-portfolio assessment in higher education. In Proceedings of the 2007 37th Annual Frontiers in Education Conference—Global Engineering: Knowledge without Borders, Opportunities without Passports, Milwaukee, WI, USA, 10–13 October 2007; pp. T1G-19–T1G-24. [Google Scholar]
- Mapundu, M.; Musara, M.E. Portfolios as a tool to enhance student learning experience and entrepreneurial skills. S. Afr. J. High. Educ. 2019, 33, 191–214. [Google Scholar] [CrossRef] [Green Version]
- Kim, Y.; Jin, G.S. Korean e-Portfolio standardization. In Proceedings of the 2010 9th International Conference on Information Technology Based Higher Education and Training (ITHET), Cappadocia, Turkey, 29 April–1 May 2010; pp. 163–167. [Google Scholar]
- Meeus, W.; Questier, F.; Derks, T. Open source eportfolio: Development and implementation of an institution-wide electronic portfolio platform for students. Educ. Media Int. 2006, 43, 133–145. [Google Scholar] [CrossRef]
- Macias, J.A. Enhancing Project-Based Learning in Software Engineering Lab Teaching Through an E-Portfolio Approach. IEEE Trans. Educ. 2012, 55, 502–507. [Google Scholar] [CrossRef] [Green Version]
- Hewa, T.; Ylianttila, M.; Liyanage, M. Survey on blockchain based smart contracts: Applications opportunities and challenges. J. Netw. Comput. Appl. 2021, 117, 102857. [Google Scholar] [CrossRef]
- Merlec, M.M.; Lee, Y.K.; In, H.P. SmartBuilder: A Block-based visual programming framework for smart contract development. In Proceedings of the 2021 IEEE International Conference on Blockchain (Blockchain), Melbourne, Australia, 6–8 December 2021; pp. 90–94. [Google Scholar]
- Del-Valle-Soto, C.; Rossa-Sierra, A. Cryptocurrencies: A futuristic perspective or a technological strategy. In Proceedings of the International Conference on Applied Human Factors and Ergonomics; Springer: Cham, Switzerland, 2020; pp. 504–509. [Google Scholar]
- Tapscott, D.; Kaplan, A. Blockchain Revolution in Education and Lifelong Learning: Preparing for Disruption, Leading the Transformation. IBM Blockchain Research Institute-IBM Institute For Business Value. April 2019. Available online: https://bit.ly/3Gvsudk (accessed on 31 January 2022).
- Grech, A.; Sood, I.; Ariño, L. Blockchain, Self-Sovereign Identity and Digital Credentials: Promise Versus Praxis in Education. Front. Blockchain 2021, 4, 7. [Google Scholar] [CrossRef]
- Hyperledger Indy Project. Available online: https://www.hyperledger.org/use/hyperledger-indy/ (accessed on 31 January 2022).
- Ngwira, L.; Merlec, M.M.; Lee, Y.K.; In, H.P. Towards context-aware smart contracts for Blockchain IoT systems. In Proceedings of the 2021 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 20–22 October 2021; pp. 82–87. [Google Scholar]
- Otto, N.; Lee, S.; Sletten, B.; Burnett, D.; Sporny, M.; Ebert, K. Verifiable Credentials Use Cases; W3C Working Group Note. 24 September 2019. Available online: https://www.w3.org/TR/vc-use-cases/ (accessed on 31 January 2022).
- Sporny, M.; Noble, G.; Longley, D.; Burnett, D.C.; Zundel, B. Verifiable Credentials Data Model 1.0: Expressing Verifiable Information on the Web. 2019. Available online: https://www.w3.org/TR/verifiable-claims-data-model/ (accessed on 31 January 2022).
- Reed, D.; Sporny, M.; Longley, D.; Allen, C.; Grant, R.; Sabadello, M. Decentralized Identifiers (Dids) V1.0: Core Architecture Data Model and Representations. 2020. Available online: https://w3c-ccg.github.io/did-spec/ (accessed on 31 January 2022).
- Bernstein, D.J.; Duif, N.; Lange, T.; Schwabe, P.; Yang, B.Y. High speed high-security signatures. J. Cryptogr. Eng. 2012, 2, 77–89. [Google Scholar] [CrossRef] [Green Version]
- Liusvaara, I.; Josefsson, S. Edwards Curve Digital Signature Algorithm (EdDSA). Internet Research Task Force. January 2017. Available online: https://tools.ietf.org/html/rfc8032 (accessed on 31 January 2022).
- Islam, M.M.; Hossain, M.S.; Hasan, M.K.; Shahjalal, M.; Jang, Y.M. FPGA implementation of high-speed area-efficient processor for elliptic curve point multiplication over prime field. IEEE Access 2019, 7, 178811–178826. [Google Scholar] [CrossRef]
- Bernstein, D.J. Curve25519: New Diffie-Hellman speed records. In International Workshop on Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2006; Volume 3958, pp. 207–228. [Google Scholar]
- Islam, M.M.; Hossain, M.S.; Hasan, M.K.; Shahjalal, M.; Jang, Y.M. Design and implementation of high-performance ECC processor with unified point addition on twisted Edwards curve. Sensors 2020, 20, 5148. [Google Scholar] [CrossRef] [PubMed]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. Proc. Thirteen EuroSys Conf. 2018, 30, 1–15. [Google Scholar]
- Brown, R.G.; Carlyle, J.; Grigg, I.; Hearn, M. Corda: An introduction. R3 CEV 2016, 1, 14. [Google Scholar]
- Baliga, A. Performance evaluation of the quorum blockchain platform. arXiv 2018, arXiv:1810.13177. [Google Scholar]
- Dib, O.; Brousmiche, K.L.; Durand, A.; Thea, E.; Ben Hamida, E. Consortium blockchains: Overview applications and challenges. Int. J. Adv. Telecommun. 2018, 11, 51–64. [Google Scholar]
- Wanotayapitak, S.; Saraubon, K.; Nilsook, P. Process design of cooperative education management system by cloud-based blockchain EPortfolio. Int. J. Online Biomed. Eng. 2019, 15, 4–17. [Google Scholar] [CrossRef]
- Arenas, R.; Fernandez, P. CredenceLedger: A permissioned blockchain for verifiable academic credentials. In Proceedings of the 2018 IEEE International Conference on Engineering, Technology and Innovation (ICE/ITMC), Stuttgart, Germany, 17–20 June 2018; pp. 1–6. [Google Scholar]
- Chen, Z.; Zhu, Y. Personal archive service system using blockchain technology: Case study, promising and challenging. In Proceedings of the 2017 IEEE International Conference on AI & Mobile Services (AIMS), Honolulu, HI, USA, 25–30 June 2017; pp. 93–99. [Google Scholar]
- Jirgensons, M.; Kapenieks, J. Blockchain and the Future of Digital Learning Credential Assessment and Management. J. Teach. Educ. Sustain. 2018, 20, 145–156. [Google Scholar] [CrossRef] [Green Version]
- Zheng, Y. Design of a Blockchain-Based e-Portfolio Evaluation System to Assess the Education and Teaching Process. Int. J. Emerg. Technol. Learn. (iJET) 2021, 16, 261–280. [Google Scholar] [CrossRef]
- Zhao, G.; Hui, H.; Bingbing, D.; Qing, X.; Zhen, F. A Blockchain-based system for student e-portfolio assessment using smart contract. In Proceedings of the 2020 4th International Conference on Computer Science and Artificial Intelligence, Zhuhai, China, 11–13 December 2020; pp. 34–40. [Google Scholar]
- Ocheja, P.; Flanagan, B.; Ueda, H.; Ogata, H. Managing lifelong learning records through blockchain. Res. Pract. Technol. Enhanc. Learn. 2019, 14, 1–19. [Google Scholar] [CrossRef] [Green Version]
- Gräther, W.; Kolvenbach, S.; Ruland, R. Blockchain for education: Lifelong learning passport. In Proceedings of the 1st ERCIM Blockchain Workshop 2018, European Society for Socially Embedded Technologies (EUSSET), Amsterdam, The Netherlands, 8–9 May 2018; Volume 10, pp. 1–8. [Google Scholar]
- Jeong, J.; Kim, D.; Ihm, S.Y.; Lee, Y.; Son, Y. Multilateral Personal Portfolio Authentication System Based on Hyperledger Fabric. ACM Trans. Internet Technol. (TOIT) 2021, 21, 1–17. [Google Scholar] [CrossRef]
- Mikroyannidis, A.; Domingue, J.; Bachler, M.; Quick, K. Smart Blockchain badges for data science education. In Proceedings of the 2018 IEEE Frontiers in Education Conference (FIE), San Jose, CA, USA, 3–6 October 2018; pp. 1–5. [Google Scholar]
- Santos, J.; Duffy, K.H. A Decentralized Approach to Blockcerts Credential Revocation. A White Paper from Rebooting the Web of Trust V. 2018. Available online: https://github.com/WebOfTrustInfo/rwot5-boston/tree/master/final-documents (accessed on 31 December 2021).
- Rasool, S.; Saleem, A.; Iqbal, M.; Dagiuklas, T.; Mumtaz, S.; Qayyum, Z.U. Docschain: Blockchain-Based IoT Solution for Verification of Degree Documents. IEEE Trans. Comput. Soc. Syst. 2020, 7, 827–837. [Google Scholar] [CrossRef]
- Tariq, A.; Haq, H.B.; Ali, S.T. Cerberus: A blockchain-based accreditation and degree verification system. arXiv 2019, arXiv:1912.06812. [Google Scholar]
- Nguyen, M.; Dao, T.; Do, B. Towards a blockchain-based certificate authentication system in Vietnam. PeerJ Comput. Sci. 2020, 6, e266. [Google Scholar] [CrossRef] [Green Version]
- Vidal, F.R.; Gouveia, F.; Soares, C. Revocation mechanisms for academic certificates stored on a blockchain. In Proceedings of the 2020 15th Iberian Conference on Information Systems and Technologies (CISTI), Seville, Spain, 24–27 June 2020; pp. 1–6. [Google Scholar]
- San, A.M.; Nopporn, C.; Chanboon, S. Blockchain-based learning credential revision and revocation method. In Proceedings of the 21st Annual Conference on Information Technology Education, New York, NY, USA, 7–9 October 2020; pp. 42–45. [Google Scholar]
- Lone, A.H.; Naaz, R. Forgery Protection of Academic Certificates through Integrity Preservation at Scale using Ethereum Smart Contract. Scalable Comput. Pract. Exp. 2020, 21, 673–688. [Google Scholar] [CrossRef]
- Mukta, R.; Martens, J.; Paik, H.; Lu, Q.; Kanhere, S.S. Blockchain-based verifiable credential sharing with selective disclosure. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Zuangzhou, China, 29 December–1 January 2020; pp. 959–966. [Google Scholar]
- Merlec, M.M.; Lee, Y.K.; Hong, S.-P.; In, H.P. A Smart Contract-Based Dynamic Consent Management System for Personal Data Usage under GDPR. Sensors 2021, 21, 7994. [Google Scholar] [CrossRef]
- Zhang, X.; Hsiao, H.; Hasker, G.; Chan, H.; Perrig, A.; Andersen, D. Scion: Scalability, control, and isolation on next-generation networks. In Proceedings of the 2011 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 22–25 May 2011; pp. 212–227. [Google Scholar]
- GoQuorum. Available online: https://github.com/ConsenSys/quorum (accessed on 31 January 2022).
- Moniz, H. The Istanbul BFT Consensus Algorithm. arXiv 2020, arXiv:2002.03613. [Google Scholar]
- Ongaro, D.; John, O. In search of an understandable consensus algorithm. In Proceedings of the 2014 {USENIX} Annual Technical Conference ({USENIX}{ATC} 14, Philadelphia, PA, USA, 19–20 June 2014; pp. 305–319. [Google Scholar]
- Tessera. Available online: https://github.com/consensys/tessera (accessed on 31 January 2022).
- Constellation: A Self-Managing Peer-to-Peer System. Available online: https://github.com/consensys/constellation (accessed on 31 January 2022).
- Cakeshop. Available online: https://github.com/ConsenSys/cakeshop (accessed on 31 January 2022).
- Tikhomirov, S.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. SmartCheck: Static analysis of ethereum smart contracts. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May–3 June 2018; pp. 9–16. [Google Scholar]
- So, S.; Lee, M.; Park, J.; Lee, H.; Oh, H. VeriSmart: A highly precise safety verifier for Ethereum smart contracts. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020; pp. 1678–1694. [Google Scholar]
- Leng, J.; Zhou, M.; Zhao, J.L.; Huang, Y.; Bian, Y. Blockchain security: A survey of techniques and research directions. IEEE Trans. Serv. Comput. 2020, 7, 50759–50779. [Google Scholar] [CrossRef]
- Rouhani, S.; Ralph, D. Security, performance, and applications of smart contracts: A systematic survey. IEEE Access 2019, 7, 50759–50779. [Google Scholar] [CrossRef]
- Caldarelli, G. Understanding the Blockchain Oracle Problem: A Call for Action. Information 2020, 11, 509. [Google Scholar] [CrossRef]
- Leng, J.; Jiang, P.; Xu, K.; Liu, Q.; Zhao, J.L.; Bian, Y.; Shi, R. Makerchain: A blockchain with chemical signature for self-organizing process in social manufacturing. J. Clean. Prod. 2019, 234, 767–778. [Google Scholar] [CrossRef]








| Features | Ethereum | Hyperledger Fabric | Hyperledger Indy | Corda | Quorum |
|---|---|---|---|---|---|
| Industry | Cross-industry | Cross-industry | Digital identities (DIDs) | Financial | Cross-industry |
| Mode of operation (ledger) | Permissionless (public) | Permissioned (private) | Permissioned (Public) | Permissioned (private) | Permissioned (public/private) |
| Consortium network support | X | N/A | √ | √ | |
| Decentralization | Decentralized | Partially | Decentralized | Partially | Decentralized |
| Consensus protocols | PoW 1 | Pluggable | PBFT 4 | Notary-based | Pluggable |
| Transaction throughput (TPS) | ~20 tps | >2000 tps | - | ~170 tps | ~1000 tps |
| Smart contract support | √ | √ | X | √ | √ |
| Transaction/smart contract privacy | X/X | √/√ | √/X | √/√ | √/√ |
| Native cryptocurrency | ETH 2 | N/A 3 | N/A | N/A | ETH |
| Symbol | Description |
|---|---|
| Ca, Aa, SC | Smart contract address, account address, smart contract |
| Pid,PN, δ | E-portfolio identifier, e-portfolio title name, e-portfolio status |
| Cid,Ct | E-certificate identifier, e-certificate template |
| τ | Registration timestamp (date and time) |
| ω | E-portfolio creator user profile identifier |
| ρ | Evaluator’s (i.e., professor or instructor) name |
| Pk,Sk, S | Public key, secret or private key, digital signature |
| s, ν | Evaluation score, e-portfolio access URL (uniform resource locator) |
| Th,QR | Transaction hash, quick response code |
| PMS_T DB | E-portfolio management system transactional database |
| Hardware | Description |
|---|---|
| CPU/ GPU | AMD® Ryzen 7 1700-8 Core/NV132 |
| RAM/SSD | 64 GB/2 TB |
| Network interface | I211 Gigabit Network |
| Software | Description |
| OS | Ubuntu 20.04.3 LTS, 64bit |
| Number of nodes | 6 |
| Network generation/Docker engine | Docker-compose v1.25.4/v20.10.8 |
| GoQuorum/Tessera version | v20.10.0/v21.1.1 |
| Client version | linux-amd64/go1.15.5 |
| Nodejs/Npm/Python/Flask | v10.19.0/v6.14.4/v3.9.5/v2.0.1 |
| Consensus protocol | IBFT, RAFT |
| Cakeshop | v0.11.0 |
| MongoDB server | Community edition v5.0.2 |
| Type | Docker Container | Number |
|---|---|---|
| Quorum blockchain network core nodes | quorum node | 6 |
| txmanager | 6 | |
| ethlogger | 6 | |
| Management, monitoring, and reporting tools | cakeshop | 1 |
| quorum reporting | 1 | |
| splunk app for quorum | 1 | |
| elasticsearch engine | 1 | |
| cadvisor | 1 |
| Transaction Type | RO | WO |
|---|---|---|
| E-portfolio registration | O(1) | O(1) |
| E-certificate issuance | O(2) | O(2) |
| E-certificate verification | O(1) | O(1) |
| Parameter | Value |
|---|---|
| E-portfolio registration transaction latency (ms) | 164.677 |
| Transaction size (KB) | 2.380 |
| Block size (KB) | 4.251 |
| Number of transactions per block | 1 |
| Block propagation latency (ms) | 1.081 |
| Parameter | Value |
|---|---|
| Ed25519 signing time per certificate (ms) | 2.470 |
| Certificate issuance transaction latency (ms) | 446.744 |
| Certificate generation time (sec) | 287.931 |
| Ed25519 verification time per certificate (ms) | 139.071 |
| Certificate file size (KB) | 720 |
| Transaction size (KB) | 2.896 |
| Block size (KB) | 4.768 |
| Number of transactions per block | 1 |
| Block propagation latency (ms) | 1.705 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Merlec, M.M.; Islam, M.M.; Lee, Y.K.; In, H.P. A Consortium Blockchain-Based Secure and Trusted Electronic Portfolio Management Scheme. Sensors 2022, 22, 1271. https://doi.org/10.3390/s22031271
Merlec MM, Islam MM, Lee YK, In HP. A Consortium Blockchain-Based Secure and Trusted Electronic Portfolio Management Scheme. Sensors. 2022; 22(3):1271. https://doi.org/10.3390/s22031271
Chicago/Turabian StyleMerlec, Mpyana Mwamba, Md. Mainul Islam, Youn Kyu Lee, and Hoh Peter In. 2022. "A Consortium Blockchain-Based Secure and Trusted Electronic Portfolio Management Scheme" Sensors 22, no. 3: 1271. https://doi.org/10.3390/s22031271
APA StyleMerlec, M. M., Islam, M. M., Lee, Y. K., & In, H. P. (2022). A Consortium Blockchain-Based Secure and Trusted Electronic Portfolio Management Scheme. Sensors, 22(3), 1271. https://doi.org/10.3390/s22031271









