A Hierarchical Blockchain-Assisted Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks
Abstract
:1. Introduction
1.1. Contribution
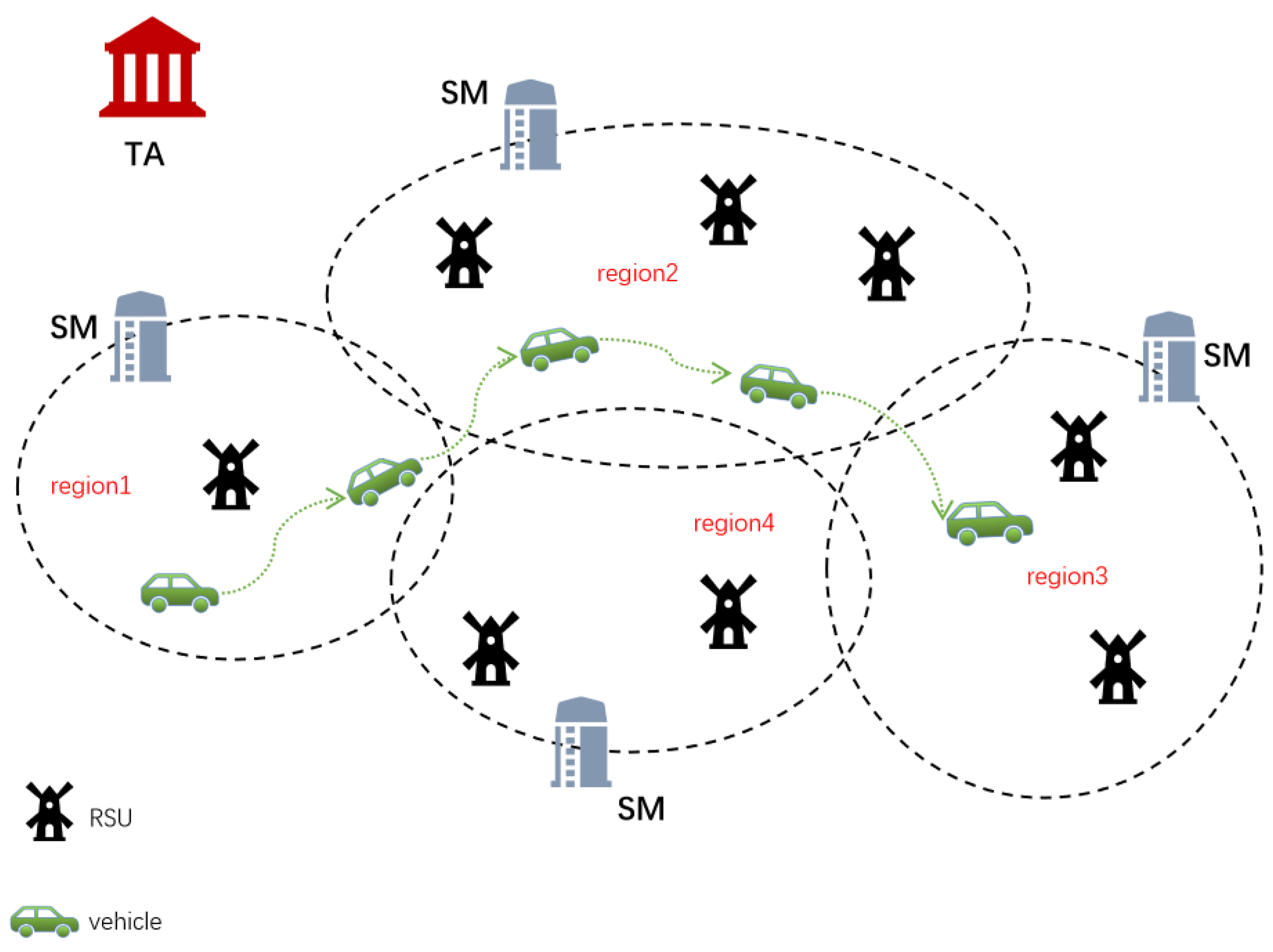
- First, to reduce the deployment costs and the associated processing time, the proposed scheme adopted distributed VFC, which uses multiple regional managers instead of a single TA.
- Second, to achieve unlinkability, the proposed scheme employs a dynamic key derivation algorithm to generate dynamic public-private key pairs for each communication of vehicles.
- Third, through Java and NS-3 simulation experiments, we show that our scheme is suitable for VANETs in terms of communication and computing overhead.
1.2. Organization
2. Related Work
3. Preliminaries
3.1. Broadcast Encryption
- (1)
- Setup: In our proposal, the maximum number of SMs is set to be n. Let L stand for a set where . This step is mainly TA distributes a key for each , for . Then TA publish a public parameter .
- (2)
- Enc(): A vehicle want to jion the internet of vehicles, it uses to calculate the encryption key K and the header . The vehicle then encrypts a message M using K as a symmetric encryption key. Let be the encryption of M. Finally, it broadcast .
- (3)
- Dec(): Let be an example to decrypt . If , by inputting , the set L, the key and , can easily compute a message encryption key . It’s remarkable that , this indicates that can decrypt and retrieve M by using .
3.2. Mathematical Complexity Assumptions
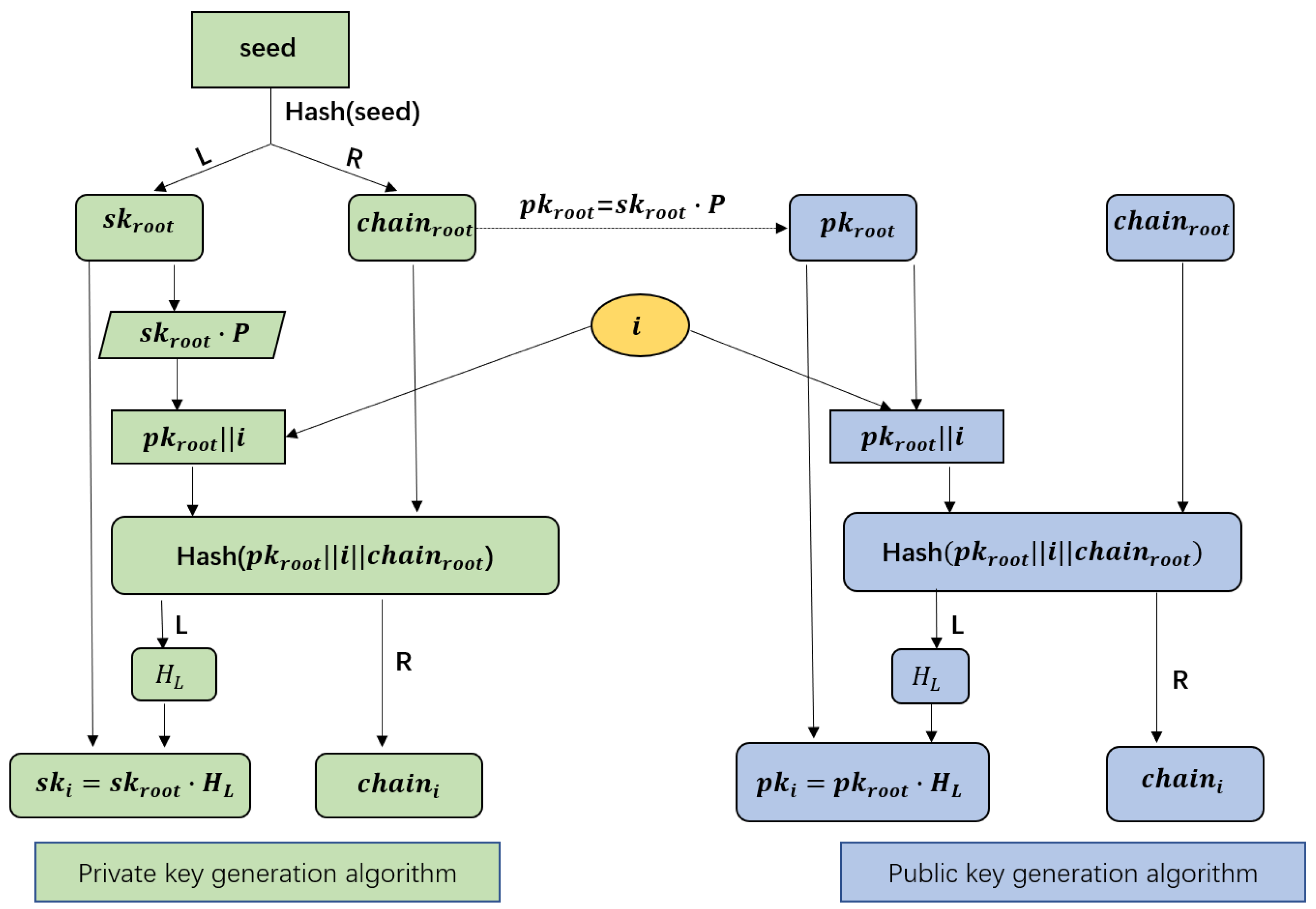
3.3. Key Derivation
- Private key generation algorithm: The goal of this algorithm is for vehicles to generate a private key for subsequent communication. A vehicle randomly selects a seed to create the root private key () and root chain code (). Then calculates the appropriate root public key () and sends <> to public key generator (i.e., SM). Based on , and serial number of the current communication (i), the vehicle can derive a different private key.
- Public key generation algorithm: The purpose of this algorithm is for SMs to generate corresponding public keys for subsequent communication of vehicles. According to Figure 2, for the same serial number i, . It ensures that the public key retrieved by the verifier corresponds to the private key of the vehicle.
4. Scheme Description
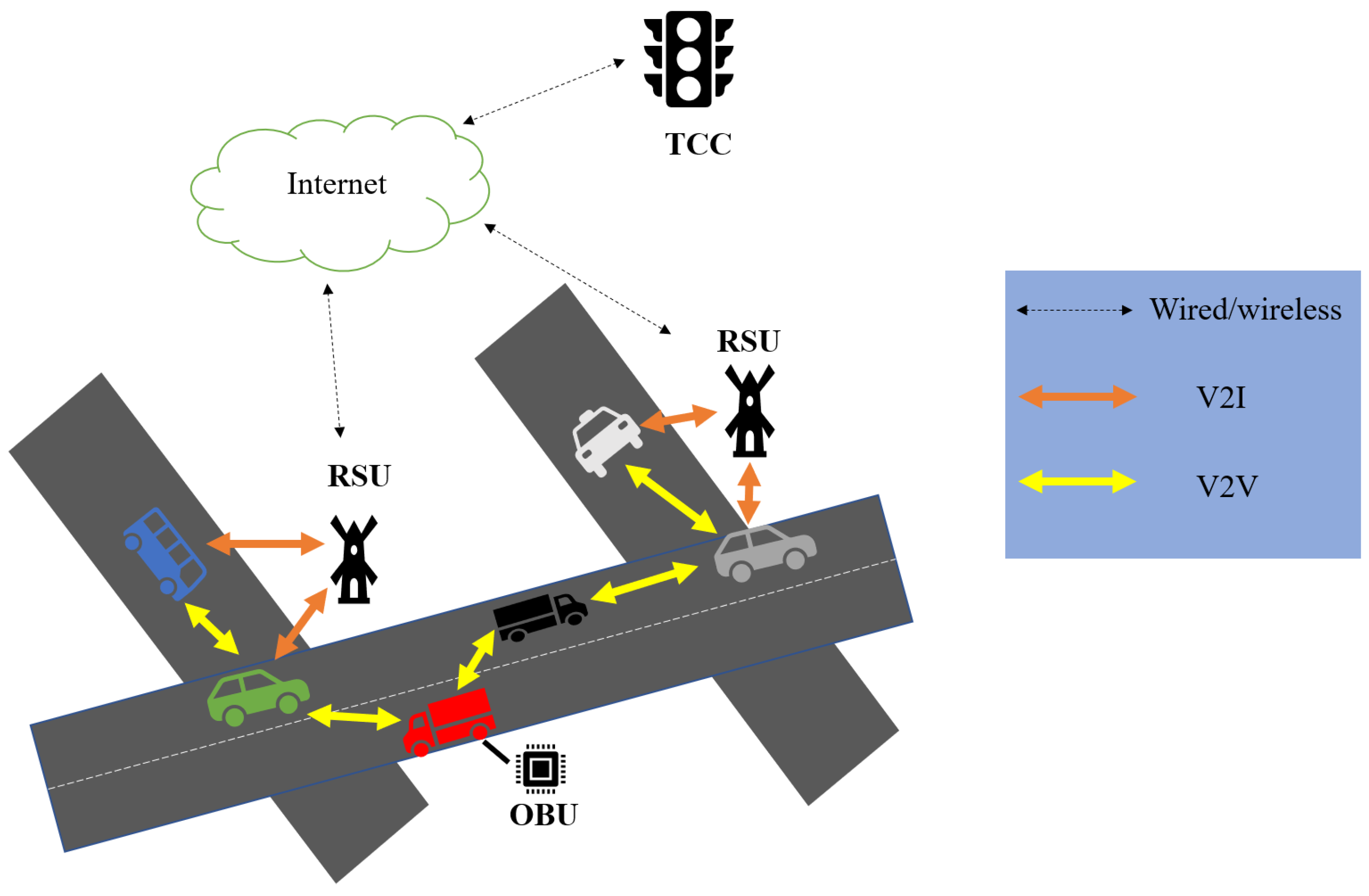
4.1. System Model
- Trusted Authority (TA): TA is a completely trusted department that generally has strong computing and communication capabilities. In our system, TA is required to complete registration SMs and vehicles. If necessary, TA can find out the real identity of a malicious vehicle through a relevant message.
- Service Manager (SM): an SM is mainly responsible for the identification of new vehicles joining VANETs in its region. Furthermore, SM is also responsible for the calculation of public keys and pseudonyms for subsequent communication of its certified vehicles.
- Road Side Unit (RSU): RSU is a semi-trusted roadside infrastructure that can communicate wirelessly with vehicles according to the Dedicated Short Range Communication (DSRC) protocol [24]. Furthermore, RSUs are also responsible for forwarding messages between vehicles and SMs and providing VFS to vehicles.
- Vehicle: as moving nodes, vehicles are outfitted with On-Board Units (OBUs), which are wireless communication devices. OBU is a tamper-proof device that also has certain computation and communication capabilities. By using OBUs, vehicles may exchange their current road traffic circumstances and driving status with the adjacent vehicles and RSUs in real-time via DSRC protocol. What’more, OBU’s information will never be revealed.
4.2. Security and Privacy Requirements
- Identity authentication: SM can effectively verify the legitimacy of new vehicles joining VANETs.
- Message authentication: for any received message, the verifier can verify that the message is valid.
- Identity privacy preservation: except for TA, no one can deduce the true identity of vehicles from the intercepted messages.
- Unlinkability: it will be impossible for a adversary to link two messages transmitted by the same vehicle.
- Traceability: if required, TA can determine the message sender’s true identity. This guarantees that messages are held accountable.
- Resist various attacks: our scheme also assures that oth-er assaults in VANETs, such as the replay attack, the impersonation attack and the modification attack, can be easily identified.
4.3. Initialization Phase
- Picks two random large prime integers and choose an additive group G generated by a point P with order q on a non-singular elliptic curve mod p where .
- Picks two large prime numbers at random and chooses two multiplicative groups , generated by a point g with order .
- Selects a number at random as its private key, then computes as its public key.
- Chooses a random number , calculates for .
- Picks a random number , and then computes . Next, TA set .
- Choose a secure hash function H, where .
- Finally, the TA sends the public parameters to all SMs and vehicles.
4.4. Registration Phase
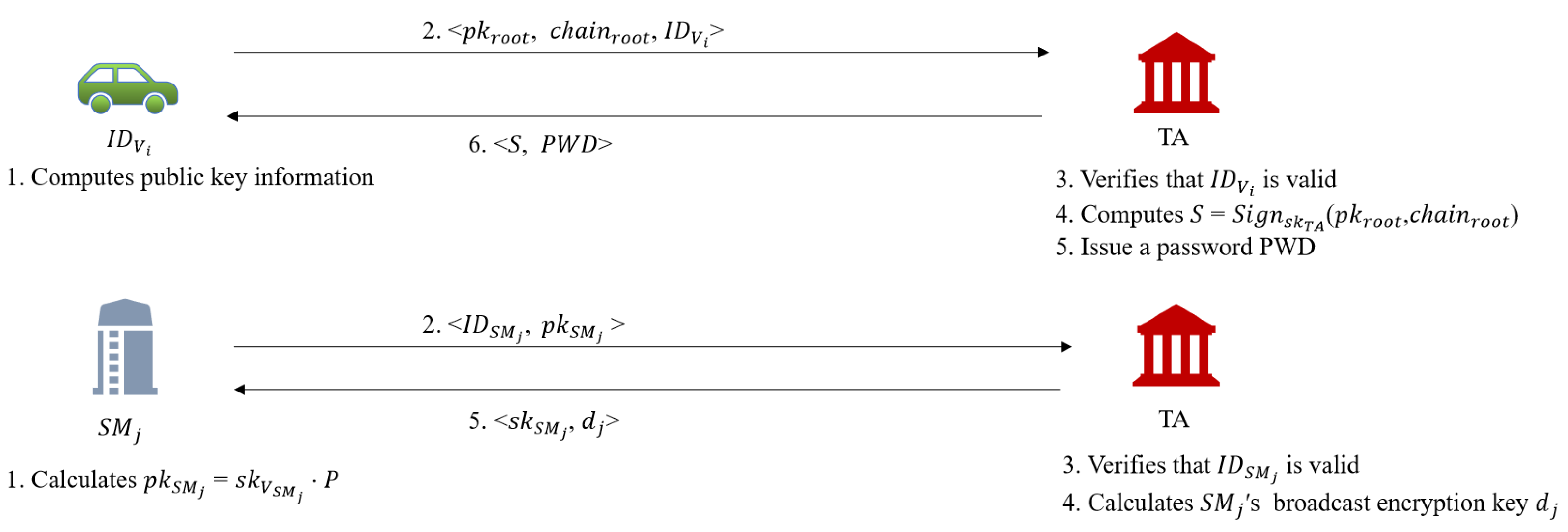
- Assume that jth SM’s real identity is . It choos-es a random integer as its private key and calculates as public key. Then sends <, > to TA through a secure channel.
- TA first checks the availability of in its databa-se after getting this registration request. If a match is found, TA will rejects this registration request. Otherwise, TA computes for to decrypt broadcast messages. Then TA stores and into its database and returns to through a secure channel.
- stores into its database.
- Assume that ith vehicle’s real identity is , first randomly chooses a private seed to generate the private information . Then computes . Finally, sends to TA via a secure channel.
- When the TA receives this registration request, it first checks whether is vaild. If not, the TA will rejects this request. Otherwise, the TA issue a password and a certificate S for and , where . Finally, the TA stores into its repository and returns to via a secure channel.
- save into its repository.
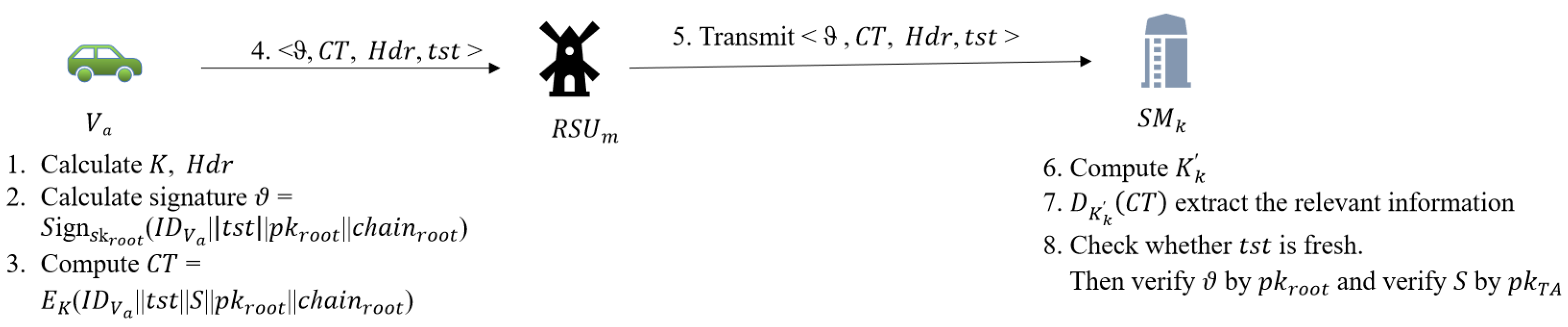
4.5. Identity Authentication Phase
- Picks a random integer and then computes symmetric encryption (e.g., AES) key . Then sets the header , where and .
- Calculate the signature . where is current timestamp and is real identity of .
- Compute the ciphertext . Then sends to the nearest RSU, let us assume it is and its region manager is .
- will transmits to .
- Check whether is fresh. will reject this message if is not fresh.
- Compute . Then executes to extract , S, , and .
- Verify by using and verify S by using TA’s public key. will reject this message As long as there is a validation failure. Then calculates corresponding pseudonyms and public keys pairs (, ) for future communications by excuting public key generation algorithm described in IV-D. Here =, where z is the number of elements in each set. For any , where and .
- Send to blockchain.
4.6. Consensus Phase
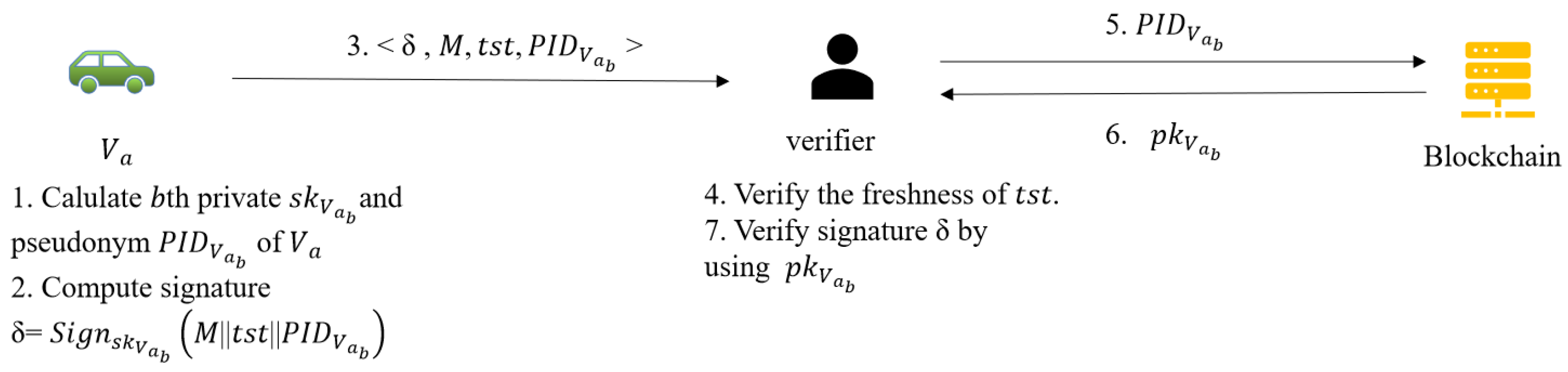
4.7. Message Authentication Phase
- Assume the current serial number of is b, first initiates a request to the OBU by entering and . OBU will reject the request if it does not match its own stored information, otherwise it goes to the next step.
- OBU calculates the current private key private key and based on private key generation algorithm. Then, calculates the current pseudonym where and .
- Finally, returns to .
- Upon receiving the above information, calculates signatureand then broadcasts the message .
- When a receiver wants to verify the message, it first checks whether the timestamp is valid. If valid, search for the corresponding public key on blockchain according to the pseudonym. The receiver will rejects the message if the query fails. Finally, the receiver validates the signature by using . If the authentication succeeds, the message is trusted.
5. Security Analysis
5.1. Correctness
5.2. Security Model
5.3. Formal Analysis
5.4. Nonformal Analysis
- Identity authentication: Because of the security of ECDSA, without TA’s private key, no one can impersonate TA and fabricate a certificate. Therefore, SMs can determine whether the vehicle is a legitimate vehicle as long as it verify the certificate sent by the vehicle with TA’s public key.
- Message authentication: According to the security of ECDSA, without signature key, no one can fake a legitimate message. It simply implies that a verifier only needs to compare the received signature message to the appropriate key to verify whether the message is legitimate.
- Identity privacy preservation: In Identity Authentication phase, Only legal SMs are able to decode the communication and determine a vehicle’s true identification. In Message Authentication phase, this real identity will be hidden under a pseudonym, which means no one(besides TA, who has its private key ) could deduce a vehicle’s true identification from the delivered communications. Therefore, our scheme can satisfiy the identity privacy preservation.
- Unlinkability: The vehicle produces a new private key and pseudonym each time it transmits a message M, then signs M. Because the pseudonym is linked to the chain code of vehicles, to link two message delivered by the same vehicle, adversary should own the chain code and of this vehicle. However, this two information only known by TA and the regional managers. Hence, our proposal can meet the security property requirement of Unlinkability.
- Traceability: Note that only TA owns its private key . Since , when necessary(e.g., a vehicle sends a error messages that causes a traffic accident), TA can retrieve the vehicle’s genuine identifying information. through .
- Resist various attacks: Other assaults that our plan can withstand are outlined below.
- -
- Replay attack: Either in the identity authentication phase or in the message authentication phase, the timestamp is included in the messages sent by the vehicle. The repeat of the message could be discovered by SMs and other verifiers by checking the freshness of . Therefore, our proposal can resist replay attack effectively.
- -
- impersonation attack: An attacker must create a valid signature for a message in order to spoof a legitimate vehicle. Based on the above discussion, this is impossible for an attacker and the verifier can easily detect such a malicious attack by validating this signature.
- -
- modification attack: To alter a message M to , an attacker need to generate a valid signature for message . It impossible for the attacker without sender’s private key, and this modified message will be discard by verifiers. As a result, our approach is resistant to modification.
- -
- Stolen Verifier Table Attack: The proposed sc-heme does not require the verifier to maintain a verification table to complete the authentication. It means that the attacker will not be able to steal any verifier tables for nefarious purposes.
5.5. Security Comparisons
6. Performance Analysis
6.1. Computing Overhead
- : the time required for a bilinear pairing.
- : the time required for a signature based on ECC.
- : the time required for a validation based on ECC.
- : the time required for a scale multiplication operation based on ECC.
- : the time required for a encryption related to AES.
- : the time required for a decryption related to AES.
- : the time required for a point multiplication operation (i.e., ), where and ∈ and the inverse of is .
- : the time required for a an exponentiation operation where and .
- : the time required for a general hash function operation. in G.
6.2. Communication Overhead
6.3. Message Authentication Delay and Packet Loss Rate
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Zeadally, S.; Hunt, R.; Chen, Y.S.; Irwin, A.; Hassan, A. Vehicular ad hoc networks (vanets): Status, results, and challenges. Telecommun. Syst. 2012, 50, 217–241. [Google Scholar]
- Toor, Y.; Muhlethaler, P.; Laouiti, A.; La, A. Vehicle ad hoc networks: Applications and related technical issues. IEEE Commun. Surv. Tutor. 2008, 10, 74–88. [Google Scholar] [CrossRef]
- Mejri, M.N.; Ben-Othma, J.; Hamdi, M. Survey on vanet security challenges and possible cryptographic solutions. Veh. Commun. 2014, 1, 53–66. [Google Scholar]
- Raya, M.; Papadimitratos, P.; Hubaux, J.P. Securing vehicular communications. IEEE Wirel. Commun. 2006, 13, 8–15. [Google Scholar] [CrossRef] [Green Version]
- Isaac, J.T.; Zeadally, S.; Camara, J.S. Security attacks and solutions for vehicular ad hoc networks. IET Commun. 2010, 4, 894–903. [Google Scholar] [CrossRef]
- Hubaux, J.P.; Capkun, S.; Luo, J. The security and privacy of smart vehicles. IEEE Secur. Priv. 2004, 2, 49–55. [Google Scholar] [CrossRef] [Green Version]
- Lu, Z.; Qu, G.; Liu, Z. A survey on recent advances in vehicular network security, trust, and privacy. IEEE Trans. Intell. Transp. 2018, 20, 760–776. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Zhang, C.; Lin, X.; Lu, R.; Ho, P.H. RAISE: An efficient rsu-aided message authentication scheme in vehicular communication networks. In Proceedings of the IEEE International Conference on Communications, Beijing, China, 19–23 May 2008. [Google Scholar]
- Zhang, J.; Xu, M.; Liu, L. On the security of a secure batch verification with group testing for vanet. Int. J. Netw. Secur. 2014, 16, 355–362. [Google Scholar]
- Lin, C.; He, D.; Huang, X.; Kumar, N.; Choo, K.-K.R. BCPPA: A blockchain-based conditional privacy-preserving authentication protocol for vehicular ad hoc networks. IEEE Trans. Intell. Transp. 2020, 22, 7408–7420. [Google Scholar] [CrossRef]
- Shojafar, M.; Cordeschi, N.; Baccarelli, E. Energy-efficient adaptive resource management for real-time vehicular cloud services. IEEE Trans. Cloud Comput. 2019, 7, 196–209. [Google Scholar] [CrossRef]
- Hou, X.; Li, Y.; Chen, C.; Wu, D.; Jin, D.; Chen, S. Vehicular fog computing: A viewpoint of vehicles as the infrastructures. IEEE Trans. Veh. Technol. 2016, 65, 3860–3873. [Google Scholar] [CrossRef]
- Yao, Y.; Chang, X.; Misc, J.; Misc, V.B.; Li, L. BLA: Blockchain-assisted lightweight anonymous authentication for distributed vehicular fog services. IEEE Internet Things J. 2019, 6, 3775–3784. [Google Scholar] [CrossRef]
- Kaur, K.; Garg, S.; Kaddoum, G.; Gagnon, F.; Ahmed, S.H. Blockchain-based lightweight authentication mechanism for vehicular fog infrastructure. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 22–24 May 2019. [Google Scholar]
- Picconi, F.; Ravi, N.; Gruteser, M.; Iftode, L. Probabilistic validation of aggregated data in vehicular ad hoc networks. In Proceedings of the Third International Workshop on Vehicular Ad Hoc Networks, VANET 2006, Los Angeles, CA, USA, 29 September 2007. [Google Scholar]
- Zhang, Y.; Wen, J. The iot electric business model: Using blockchain technology for the internet of things. Peer-to-Peer Netw. Appl. 2017, 10, 983–994. [Google Scholar] [CrossRef]
- Zhong, H.; Wen, J.; Cui, J.; Zhang, S. Efficient Conditional Privacy-Preserving and Authentication Scheme for Secure Service Provision in Vanet. Tsinghua Sci. Technol. 2016, 21, 620–629. [Google Scholar] [CrossRef]
- Wang, P.; Liu, Y. SEMA: Secure and Efficient Message Authentication Protocol for VANETs. IEEE Syst. J. 2021, 15, 846–855. [Google Scholar] [CrossRef]
- Ali, I.; Lawrence, T.; Omala, A.A.; Li, F. An efficient hybrid signcryption scheme with conditional privacy-preservation for heterogeneous vehicular communication in vanets. IEEE Trans. Veh. Technol. 2020, 11266–11280. [Google Scholar] [CrossRef]
- Wang, C.; Shen, J.; Lai, J.; Liu, J. B-TSCA: Blockchain Assisted Trustworthiness Scalable Computation for V2I Authentication in VANETs. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1386–1396. [Google Scholar] [CrossRef]
- Lu, Z.; Wang, Q.; Qu, G.; Zhang, H.; Liu, Z. A blockchain-based privacy-preserving authentication scheme for vanets. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2019, 27, 2792–2801. [Google Scholar] [CrossRef]
- Boneh, D.; Gentry, C.; Waters, B. Collusion resistant broadcast encryption with short ciphertexts and private keys. In Proceedings of the Advances in Cryptology—CRYPTO 2005: 25th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005. [Google Scholar]
- Boukerche, A.; Oliveira, H.A.B.F.; Nakamura, E.F.; Loureiro, A.A.F. Vehicular ad hoc networks: A new challenge for localization-based systems. Comput. Commun. 2008, 31, 2838–2849. [Google Scholar] [CrossRef]

| Scheme | Key Technology | Pros | Cons |
|---|---|---|---|
| Picconi [16] | Challenge the aggregator to provide a proof |
| Certificate management is difficult |
| Zhang [17] | k-anonymity |
| Certificate management is difficult |
| He [8] | Elliptic Curve Cryptography |
| The implementation of cross-region authentication is complex |
| Zhong [18] | Pseudonym-based signatures |
| The implementation of cross-region authentication is complex |
| Wang [19] | Pseudonyms-based and group-based signatures |
| Require frequent authentication |
| Ali [20] | Hybrid signature |
| No consideration for unlinkability |
| Yao [14] |
|
| No consideration for unlinkability |
| Kaur [15] |
|
| No consideration for unlinkability |
| Wang [21] |
|
| Require frequent interaction |
| Lu [22] |
|
| Require frequent interaction |
| Lin [11] |
|
| High message processing and queuing latency |
| Notations | Definition |
|---|---|
| L | |
| two large prime integers | |
| G | an additive cyclic group of prime order q |
| P | a generator of G |
| n | the number of SMs |
| two multiplicative cyclic groups of prime order | |
| g | a generator of |
| e | a bilinear map where |
| current timestamp | |
| real identity | |
| pseudonym | |
| symmetric encryption utilizing K | |
| symmetric decryption utilizing K | |
| H | hash function |
| ⊕ | exclusive-OR operation |
| ‖ | concatenation operation |
| Yao [14] | Lin [11] | Ali [20] | Ours | |
|---|---|---|---|---|
| Identity authentication | ✓ | ✓ | ✓ | ✓ |
| Message authentication | ✓ | ✓ | ✓ | ✓ |
| Identity privacy preservation | ✓ | ✓ | ✓ | ✓ |
| Unlinkability | × | ✓ | × | ✓ |
| Traceability | ✓ | ✓ | ✓ | ✓ |
| Resist various attacks | ✓ | ✓ | ✓ | ✓ |
| Algorithm | Average Time (ms) |
|---|---|
| 4.6003 | |
| 1.5271 | |
| 6.5458 | |
| 0.7088 | |
| 0.0434 | |
| 0.0198 | |
| 0.0118 | |
| 0.6871 | |
| 0.0047 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, X.; Niu, X.; Wang, Y.; Xiong, L.; Jiang, Z.; Gong, C. A Hierarchical Blockchain-Assisted Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. Sensors 2022, 22, 2299. https://doi.org/10.3390/s22062299
He X, Niu X, Wang Y, Xiong L, Jiang Z, Gong C. A Hierarchical Blockchain-Assisted Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. Sensors. 2022; 22(6):2299. https://doi.org/10.3390/s22062299
Chicago/Turabian StyleHe, Xingyu, Xianhua Niu, Yangpeng Wang, Ling Xiong, Zhizhong Jiang, and Cheng Gong. 2022. "A Hierarchical Blockchain-Assisted Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks" Sensors 22, no. 6: 2299. https://doi.org/10.3390/s22062299
APA StyleHe, X., Niu, X., Wang, Y., Xiong, L., Jiang, Z., & Gong, C. (2022). A Hierarchical Blockchain-Assisted Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. Sensors, 22(6), 2299. https://doi.org/10.3390/s22062299





