Continuous and Secure Integration Framework for Smart Contracts
Abstract
1. Introduction
1.1. Contributions
- First, this paper presents a systematic analysis of applying a DevOps routine to smart contract development. In particular, we analyze how this practice may be adopted to continuously and securely integrate smart contract development into existing software. For this analysis, we go over the state-of-art of DevOps routine, its phases, and how to adapt them to use them in blockchain-based developments. We then survey software tools used in each DevOps Cycle’s phase, technologies for deploying blockchains and developing smart contracts, and known security vulnerabilities on smart contracts.
- As a result of the previous analysis, this paper presents a framework to implement DevOps to smart contracts and the interaction of its phases. To highlight its practicability, we analyze a set of tools for each stage. In concrete, we include a brief description of these tools and their potential use in implementing the proposed framework. Additionally, we present a case use to which the framework may be applied.
1.2. Paper Structure
2. Background
2.1. DevOps
2.2. DevOps Tools
2.3. DevOps Cloud-Based Tools
- Microsoft Azure Pipelines: Pipelines simplify hardware and VM management using Microsoft’s agents and allow users to automate code builds and deployments with Pipelines. Azure offers support for every major platform and tool through container jobs. Important to note is that Azure allows the user to do a deployment to multiple cloud providers and on-premise machines [32].
- Google Cloud Build: It is a fully managed platform to build, test, and deploy code from multiple source code repositories. Cloud Build permits the user to deploy the build to the platform of choice. Important to note is that Google offers “Binary Authorization” to perform deep security scans, enforce standardized container release practices and verify images to ensure no tampering is done on deployment [33].
- Alibaba Cloud DevOps Pipeline (Flow): An automated delivery pipeline service that offers tools to go from continuous integration to continuous deployment. Flow benefits include integrating multiple cloud repositories, code and security scanning, and deployment to public clouds or self-hosted environments [34].
- IBM Cloud Continuous Delivery (CCD): IBM CCD platform allows user to handle their pipeline entirely through tools integration. It offers issue tracking, source code repository, and web IDE in addition to the tools required to build, test and deploy. IBM CCD offers deployment exclusively to the IBM Cloud [35].
- Amazon AWS CodePipeline: It is a platform to build, test, and deploy code based on a defined release process model. It is based on three services: AWS CodeBuild (code building and testing), AWS CodeDeploy (deployment to AWS servers or on-premise servers), and AWS CodeStar (user interface for configuration) [36].
- Redhat OpenShift Pipelines: OpenShift Pipelines is a Kubernetes-native CI/CD solution based on Tekton. Therefore, this allows each pipeline step to run on its container. Openshift Pipelines can build, test, and deploy applications to public cloud platforms and on-premise [37].
3. Blockchains and Smart Contracts
- Ethereum: One of the most popular open-source public blockchain platforms with a cryptocurrency called ETH or Ether. Ethereum is the oldest smart contract platform, allowing developers to build decentralized apps through its Ether. Ethereum Virtual Machine (EVM) software stores and executes all smart contracts, with Solidity as the relevant programming language. However, this blockchain suffers from concurrency issues which developers are working to reduce [46].
- Hyperledger Fabric: A private blockchain platform with smart contract features that first became available as an enterprise blockchain platform. It is an open-source Linux project which supports the collaborative development of blockchain-based distributed ledgers. This blockchain architecture bases itself on a microservice architecture for an appropriate deployment. Hyperledger developers have access to tools that allow them to develop smart contracts more efficiently and quickly [47].
- New Economy Movement (NEM): A platform for private blockchains focused on building solutions for requirements using a cryptocurrency called XEM, which can be traded but not used as payment. Created initially in 2015 based on another blockchain called NXT [48,49]. Unlike other blockchains, NEM uses a proof-of-importance (POI) mechanism instead of a proof-of-work (POW) mechanism. NEM offers several advantages to the users, such as ease of deployment, deep customization, performance, and complete security.
- Stellar: It is a blockchain-based platform that facilitates economic transactions over boundaries. For the Stellar blockchain, smart contracts manifest as Stellar Smart Contracts (SSC) [50]. The crypto coin used in Stellar is Lumen [51]. A Stellar Smart Contract (SSC) is a composition of connected and executed transactions using various constraints with a processing time between three and five seconds. Stellar allows users to create, trade, and send digital representations of all forms of money (i.e., bitcoin, dollars, and pesos) while securing this with the Stellar Consensus Protocol (SCP).
- EOS: It is a blockchain-based platform designed to develop scalable and secure applications with smart contract capability [52]. EOS provides decentralized storage of enterprise solutions to solve the scalability issues faced by Bitcoin and Ethereum. A difference between the EOS platform and others is that it eliminates all users’ fees and uses a Proof-of-Stake (PoS) algorithm.
- Corda: An open-source blockchain project, designed for business from the start, allows users to transact directly with smart contracts [53]. This practice streamlines business processes to reduce transaction costs and record-keeping. The R3 Corda platform represents the smart contract corresponding to real-world contracts. It is an agile and flexible platform that can scale to meet business requirements. Applications built on Corda, CorDapps are designed and developed to transform businesses across various sectors, including insurance, healthcare, finance, and energy.
4. Smart Contracts Security
4.1. Smart Contract Vulnerabilities
- Reentrancy: This vulnerability is considered one of the most severe. The reentrancy vulnerability relies on the interaction between two smart contracts. If, through smart contract dependencies, a contract hands over the control to another contract, it allows this second contract to call back into the first contract before the first initiated interaction between them is completed. Therefore, the second contract could have an action to refund gas and do this operation multiple times to empty the balance of the smart contract of the target. The correct order of operations during a balance transfer is essential to prevent this attack.
- tx.origin: tx.origin is a global variable used in Solidity smart contracts containing the account’s address that sends the transaction. The vulnerability, named after this variable, aims to identify the user who initiated the chain of interactions between contracts. This action is done during the authorization method to spoof unauthorized users as authorized and obtain leveraged privileges in the contract.
- Callstack depth exception: Contracts have a call stack limit of 1024. Therefore it is possible to make a smart contract execution fail by making external calls and exceeding this maximum stack call size. An attacker can use this call as an advantage to produce an output that suits them the best during a contract execution if the call stack exception is not handled correctly by the contract.
- Timestamp dependence: A contract that depends on the timestamp can be vulnerable if used in a vital contract call. An attacker can manipulate the timestamp to produce an output that suits them best.
- Transaction-ordering dependence: This vulnerability is a prevalent security bug in the smart contract that consists of relying on the order of transaction execution. This vulnerability can have the attacker be the smart contract owner or the miner. It consists of making the gas price of the transaction change during the execution of the smart contract because the attacker sends a transaction that modifies the price before the transaction being executed finishes.
- Gasless send: This situation happens when, under certain conditions, the gas sent to execute a contract call is not enough to cover the call. This situation generates a “gas exhaustion” exception and, therefore, a transaction failure. The exception happens if the recipient’s contract has a fallback function with a large code base. It is crucial to throw an exception if a failure based on gas consumption happens and to ensure that the gas requirements for contracts’ calls are not too high.
- Call to the unknown: It happens when a Call, Send or DelegateCall primitive of the Solidity language is called inside a contract. However, this one internally uses a function defined inside all contracts (as part of the Solidity language) but is not found in the miner’s environment during execution.
- Overflow and underflow: This vulnerability can occur when transactions do not check the input data to verify it is an authorized input. Smart contract overflow occurs when the value provided exceeds the maximum value defined for its data type. In the case of Solidity, it is a 256-bit number. In the case of underflow, it is trying to achieve the same by using numbers under the limit permitted by Solidity.
- Short address attack: This vulnerability occurs in Ethereum Virtual Machine (EVM). It permits padded arguments that allow an attacker to send a crafted address that leads to a contract exploit. The EVM will add zeros to the end of the encoded arguments to make up for an expected length of 20 bytes (applied only when the argument is less than 20 bytes). This attack is not explicitly made on the Solidity contracts themselves but on the third-party applications that interact with them. It is usually an issue when third-party applications interacting with smart contracts do not validate the inputs.
4.2. Analysis Methods
4.2.1. Static Vulnerability Detection
- Control analysis: Focuses on the flow of the different calls in a structure. The analysis revises the calls done in a process, function, method, or subroutine.
- Data analysis: Concerns using defined data to ensure data objects are correctly operating.
- Fault/failure analysis: Analyzes faults and failures in the data components used inside the code.
- Interface analysis: Verifies the interfaces between solutions and applications to determine that the components interact appropriately.
- Pattern recognition analysis: Searches for portions of code known to contain potentially vulnerable code.
4.2.2. Dynamic Vulnerability Detection
- Fault localization: Searches for faults in the code by giving multiple random values to tests to see if the tests fail with a specific value.
- Memory errors and concurrency errors analysis: Searches for resource and memory leaks during race conditions on multi-threaded programs.
- Performance analysis: Traces software applications at run-time and captures data to identify the causes of poor performance.
4.3. Blockchain Development Tools
| Blockchain | Tool Name | Classification | Description | Last Updated |
|---|---|---|---|---|
| Ethereum | Oyente [83] | Static Analysis | An Analysis Tool for Smart Contracts | Nov 2020 |
| Ethereum | Solgraph [84] | Static Analysis | Visualize Solidity control flow for smart contract security analysis | Jan 2019 |
| Ethereum | MadMax [85] | Dynamic Analysis | Ethereum Static Vulnerability Detector for Gas-Focussed Vulnerabilities | Jun 2021 |
| Ethereum | Manticore [86] | Dynamic Analysis | Manticore is a symbolic execution tool for analysis of smart contracts and binaries. | Mar 2022 |
| Ethereum | Mythril [87] | Dynamic Analysis | Security analysis tool for EVM bytecode. | Apr 2022 |
| Ethereum | ContractLarva [88] | Dynamic Analysis | Runtime verification tool for Solidity smart contracts. | Mar 2022 |
| Ethereum | SolMet [89] | Static Analysis | A static analysis tool for calculating OO-style source code metrics for Solidity smart contracts. | Nov 2020 |
| Ethereum | Vandal [90] | Static Analysis | Static program analysis framework for Ethereum smart contract bytecode. | Jul 2020 |
| Ethereum | Securify [91] | Static Analysis | A security scanner for Ethereum smart contracts. | Sep 2021 |
| Ethereum | Slither [92] | Static Analysis | Static Analyzer for Solidity | Apr 2022 |
| Ethereum | Ethlint [93] | Static Analysis | Code quality & Security Linter for Solidity | Sep 2019 |
| Hyperledger Fabric | Revive-CC [94] | Static Analysis | Static analysis tool for Hyperledger Fabric smart contracts written in Go. | Jul 2020 |
| Hyperledger Fabric | Blockchain Analyzer [95] | Data Analysis | Analyze ledger data stored within a Hyperledger Fabric peer. | Feb 2020 |
| Hyperledger Fabric | Chaincode Analyzer [96] | Static Analysis | CLI tool to detect the codes which can be risks potentially such as nondeterminism in smart contract in Hyperledger Fabric. | Feb 2020 |
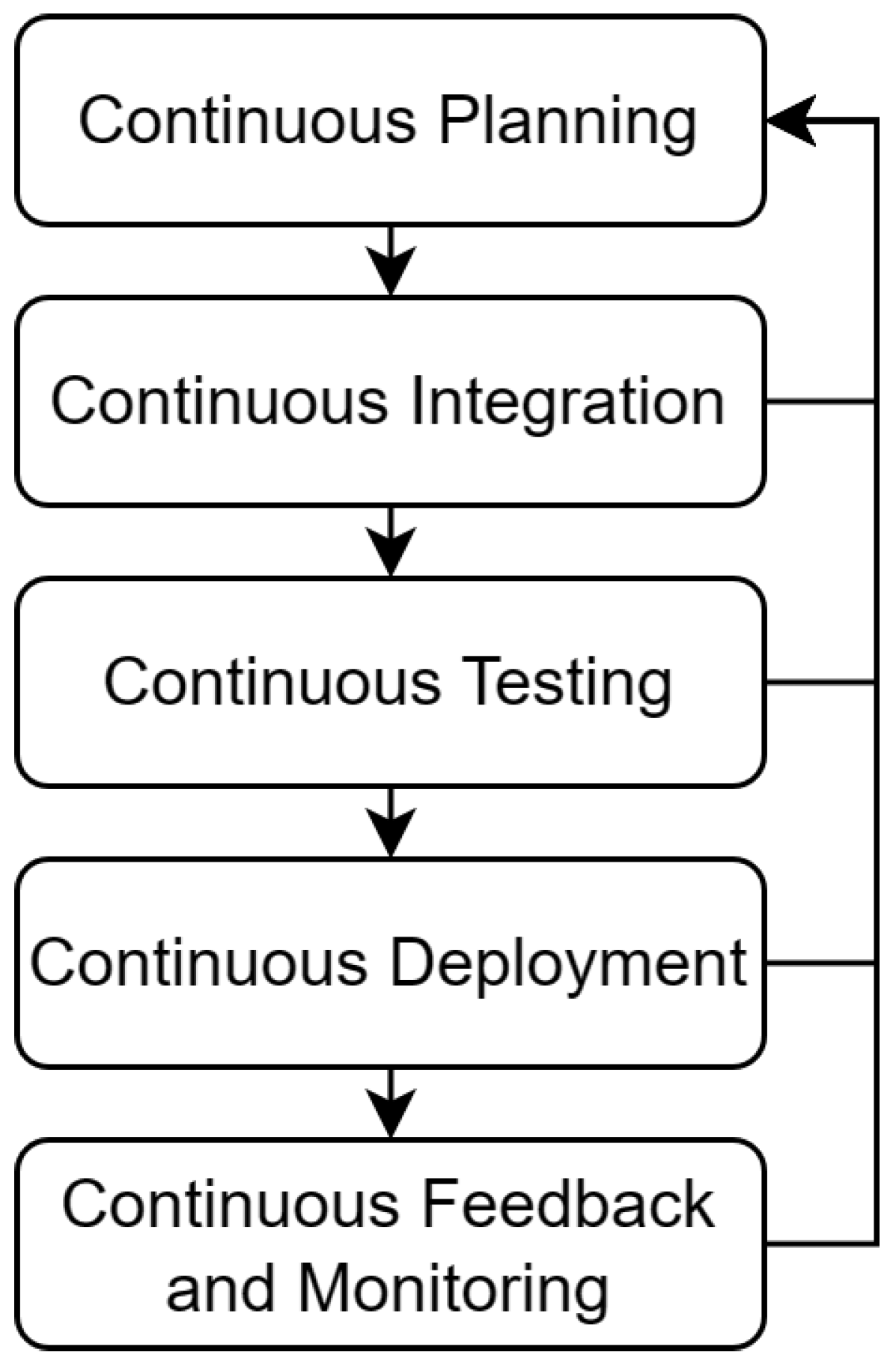
5. DevOps Framework for Smart Contracts Integration
5.1. Preparation
5.1.1. Analysis of Current Systems
5.1.2. Defining the Quality Strategy
5.1.3. Securing the Development Process with the Respective Tooling
5.1.4. Validation of Existing Code Base and Dependencies
5.1.5. Setup of Tools Environment
5.2. Continuous Planning
5.2.1. Task Discovery
5.2.2. Task Planification
5.2.3. Task Assignment
5.2.4. Indicators
- Resources Available: The total amount of resources assigned to a project. This doesn’t necessarily mean only human resources but other types of resources too (computational, tools, third-party supports).
- Assignment Time: The time taken between task creation and task assignment.
- Lead Time: Time taken between task assignment and task completion. This can only be calculated once the full development cycle is completed.
- Feature Prioritization: Reinforces the value of DevOps, where constant iterations are being done to meet user demands. This will determine if the tasks being assigned meet the needs of those features being utilized the most.
5.3. Continuous Integration
5.3.1. Code
5.3.2. Unit Test Creation
5.3.3. Commit
5.3.4. Build
5.3.5. Indicators
- Unplanned Work: Represents on-demand changes done while work is in progress due to unidentified situations during task discovery. This could also be due to unexpected situations occurring due to ongoing changes. No matter the reason, however, this is a metric that should be accounted for. Aimed at being a low value, as it represents proper discovery work being done and no changes being accepted once work has started.
- Change Volume: Determines the extent to which code was changed when fulfilling a given task. Ideally, the change volume should remain low implying only the task objectives are being changed.
- Test Coverage: Constitutes the percent of functionality in a smart contract that is covered by unit tests. A low value implies the unit test creation step is being skipped, which then will lead to unexpected bugs.
5.4. Continuous Testing
5.4.1. Static Analysis
5.4.2. Dynamic Analysis
5.4.3. Private Blockchain Deployment
5.4.4. Unit Testing
5.4.5. Integration Testing
5.4.6. Indicators
- Test Pass Rate: If code releases consistently fail unit tests, this suggests that teams are ignoring safe practices, and work must be done to correct those issues. This value should always remain high, implying functionality works as expected according to the tests created.
- Error Detection Rate: Represents the errors and warnings detected by the static and dynamic analyses. The detection rate value aim is to be as low as possible, implying that the common errors found in code are accounted for.
- Escape Rate: Represents the value of changes creating changes in functionality that were not caught in testing. A high value implies that the testing must be reviewed to determine where the issue lies.
5.5. Continuous Deployment
5.5.1. Release
5.5.2. Deploy
5.5.3. Indicators
- Deployment Time: The time between release and deployment. Deployments can occur with high frequency if tasks are simplified enough, but these times should remain relatively constant. Any dramatic increases in deployment time will warrant further investigation,
- Recovery Time: The time indicating the team’s ability to respond appropriately to issues during deployment. It would mean little if issues are found promptly but not followed by an equally rapid recovery time.
- Failed Deployment Rate: This value represents the ratio of deployment failures and is related to the previous indicator. The value should be kept as low as possible to indicate that a low amount of issues are being generated.
5.6. Continuous Feedback and Monitoring
5.6.1. Monitoring Smart Contract
5.6.2. Monitoring Permissions
5.6.3. Monitoring Client
5.6.4. Feedback
5.6.5. Indicators
- Compliance: This highlights the difference between the deployed work and the planned work. A high compliance value ensures that expectations are being met.
- Ticket Volume: This concept reflects alerts (a monitoring user generates) to indicate bugs or unexpected functionality. An increased ticket volume suggests issues in the deployed code and not caught in testing.
- Performance: A key indicator for any application. Code deployed should not affect the performance of previous functionality and should not generate unaccounted slow performance times.
6. General Use Case
- The next is the continuous planning phase, which consists of two tasks: planning and assignment. Issue tracker software covers these functionalities. Examples of software dedicated to issuing tracking are Atlassian Jira, HubSpot, ClickUp, and Backlog. However, other applications like Gitlab or Microsoft Teams have issue-tracking capabilities.
- The next phase is the continuous integration phase, which consists of coding tasks. For the smart contract coding, it is necessary to create unit tests for the smart contract and commit to the repository hosting the smart contract or groups of smart contracts. Once completed, a build process using an automation server should verify that the recent commit will allow the code to build successfully. The repository, with technologies mentioned in Section 4.3, can be hosted by software such as Github, Gitlab, VisualSVN Server, or Apache Subversion, among others. Meanwhile, the automation server, as mentioned in Section 4.3, can be done by software such as Jenkins, Tekton, Travis-CI, Circle-CI, and AppVeyor.
- The next phase is continuous testing, which tests the code directly using static analysis tools. Dynamic analysis tools are also run on the compiled code. Some tools are referenced in Table 4. The automation server should do these tests once the build successfully generates a report on possible bugs. Finally, manual and automatic integration tests are available using blockchain simulators such as Ganache or Geth once all tool testing finishes.
- The release of the smart contract is generated, which involves the creation of the needed files to publish the smart contract on a blockchain. After this, the files are deployed onto the blockchain. Everything in the continuous deployment phase should be left to the automation server, or at least as much as possible.
- The continuous monitoring of the released smart contract starts operating. The proposal is to do this by monitoring statistics related to the smart contract and the data generated by it and its users. Also, monitoring related permissions to the smart contract must be constant, so there is a verification regarding undesired permission changes. A feedback report is filed from the operations team to send back to the development team.
7. Implementation Issues
7.1. Secure Deployment and Integration
- Define, design, and implement a mechanism to allow existing software to request/execute a smart contract method. Given that a complete overhaul of the software architecture is expensive and not accounting for the cases where specific technologies do not allow this to be done, the goal would be to reutilize as much as possible from the current software. However, a mechanism that would connect current software with a smart contract with minimal change is out of the scope of the proposed framework.
- Define, design, and implement a mechanism to authenticate and authorize requests to access resources in the smart contract from existing software. Such a mechanism should correspond to identities created in the existing software to accounts from the blockchain. This part would help extend the authorization model to control what identities may or may not access resources deployed in implementing or updating smart contracts. Authentications or authorizations should not be lost under any circumstance for a system. For all migration cases, the framework’s deployment step should consider any migration on the authentication and authorization model to guarantee that data is kept.
- Define, design, and implement a mechanism to properly handle/integrate the different versions of a smart contract deployed into the blockchain. Since a contract version is unavailable for modification after deployment, such a mechanism should help direct existing software requests to the smart contract’s correct version. This mechanism would act as a proxy, which mediates requests from existing software to the smart contract. During the deployment of the updated smart contract, the deployment of this proxy should also be updated. Whether this mechanism is another smart contract or another tool is left to the implementer. However, it is recommended to find an automated way according to the implementation.
7.2. Secure Monitoring
- Define, design, and implement metrics to measure events related to the operation of a smart contract. An event is a convenient tool given by smart contracts to record executions in the contract. Events that were emitted stay in the blockchain along with the other contract data and are available for future audits. A mechanism should be available to constantly seek this data to transform it into a visual form. This mechanism would work as feedback for the different teams working on implementation.
- Define, design, and implement a mechanism to utilize the data from the smart-contract operation. Such a mechanism should access the data extracted mentioned in the previous point. This data can then be given as machine models, fed and deployed to measure the previously defined metrics. The objective of this mechanism is to make this data available in visual form for the different teams involved in the implementation.
8. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Rizky, M.; Sulistiyo, D. Implementation of Continuous Integration and Continuous Delivery (CI/CD) on Automatic Performance Testing. In Proceedings of the 9th International Conference on Information and Communication Technology, Yogyakarta, Indonesia, 3–5 August 2021. [Google Scholar] [CrossRef]
- de Aguiar Monteiro, L. A Proposal to Systematize Introducing DevOps into the Software Development Process. In Proceedings of the 2021 IEEE/ACM 43rd International Conference on Software Engineering: Companion Proceedings (ICSE-Companion), Madrid, Spain, 25–28 May 2021; pp. 269–271. [Google Scholar] [CrossRef]
- De Kort, W. DevOps on the Microsoft Stack, 1st ed.; Apress Berkley: Berkeley, CA, USA, 2016; Volume 1. [Google Scholar]
- Liao, Q. Modelling CI/CD Pipeline Through Agent-Based Simulation. In Proceedings of the IEEE International Symposium on Software Reliability Engineering Workshops, Coimbra, Portugal, 27–30 October 2020. [Google Scholar] [CrossRef]
- Chen, N.; Hoi, S.C.H.; Xiao, X. Software process evaluation: A machine learning framework with application to defect management process. Empir. Softw. Eng. 2014, 19, 1531–1564. [Google Scholar] [CrossRef]
- Nogueira, A.; Ribeiro, J.; Zenha-Rela, M.; Craske, A. Improving La Redoute’s CI/CD pipeline and DevOps processes by applying Machine Learning techniques. In Proceedings of the International Conference on the Quality of Information and Communications Technology, Talavera de la Reina, Spain, 2–14 September 2018. [Google Scholar] [CrossRef]
- Aldeen, M.; Elyass, R.; Hmad, A.; Ahmed, M. Adopting Continuous Integeration and Continuous Delivery for Small Teams. In Proceedings of the International Conference on Computer, Control, Electrical, and Electronics Engineering, Dubai, United Arab Emirates, 9–10 May 2019. [Google Scholar]
- Tegeler, T.; Gossen, F.; Steffen, B. A Model-driven Approach to Continuous Practices for Modern Cloud-based Web Applications. In Proceedings of the 9th International Conference on Cloud Computing, Data Science and Engineering (Confluence), Noida, India, 10–11 January 2019; pp. 1–6. [Google Scholar]
- Virmani, M. Understanding DevOps & bridging the gap from continuous integration to continuous delivery. In Proceedings of the Fifth International Conference on the Innovative Computing Technology (INTECH 2015), Galicia, Spain, 20–22 May 2015; pp. 78–82. [Google Scholar] [CrossRef]
- Erich, F. DevOps is Simply Interaction Between Development and Operations. In Proceedings of the Software Engineering Aspects of Continuous Development and New Paradigms of Software Production and Deployment, Château de Villebrumier, France, 6–8 May 2019; Bruel, J.M., Mazzara, M., Meyer, B., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 89–99. [Google Scholar]
- Throner, S.; Hutter, H.; Sanger, N.; Schneider, M.; Hanselmann, S.; Petrovic, P.; Abeck, S. An Advanced DevOps Environment for Microservice-based Applications. In Proceedings of the IEEE International Conference on Service-Oriented System Engineering, Oxford, UK, 23–26 August 2021. [Google Scholar] [CrossRef]
- Wang, S.; Ouyang, L.; Yuan, Y.; Ni, X.; Han, X.; Wang, F.Y. Blockchain-Enabled Smart Contracts: Architecture, Applications, and Future Trends. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 2266–2277. [Google Scholar] [CrossRef]
- Szabo, N. Nick Szabo—Smart Contracts: Building Blocks for Digital Markets. Extropy J. Transhuman Thought 1996, 16, 2–20. [Google Scholar]
- Zampetti, F.; Geremia, S.; Bavota, G.; Di Penta, M. CI/CD Pipelines Evolution and Restructuring: A Qualitative and Quantitative Study. In Proceedings of the IEEE International Conference on Software Maintenance and Evolution, Luxembourg, 27 September–1 October 2021. [Google Scholar] [CrossRef]
- Kim, K.B.; Lee, J. Automated Generation of Test Cases for Smart Contract Security Analyzers. IEEE Access 2020, 8, 209377–209392. [Google Scholar] [CrossRef]
- Wöhrer, M.; Zdun, U. DevOps for Ethereum Blockchain Smart Contracts. In Proceedings of the 2021 IEEE International Conference on Blockchain (Blockchain), Melbourne, Australia, 3–8 December 2021; pp. 244–251. [Google Scholar] [CrossRef]
- Lenarduzzi, V.; Lunesu, M.I.; Marchesi, M.; Tonelli, R. Blockchain Applications for Agile Methodologies. In Proceedings of the 19th International Conference on Agile Software Development, Companion, Association for Computing Machinery, Porto, Portugal, 21–25 May 2018. [Google Scholar] [CrossRef]
- Marchesi, L.; Marchesi, M.; Tonelli, R. ABCDE—Agile block chain DApp engineering. Blockchain Res. Appl. 2020, 1, 100002. [Google Scholar] [CrossRef]
- Al-Mazrouai, G.; Sudevan, S. Managing Blockchain Projects with Agile Methodology. In Proceedings of the 6th International Conference on Big Data and Cloud Computing Challenges, Kansas City, MO, USA, 9–10 September 2019; Vijayakumar, V., Neelanarayanan, V., Rao, P., Light, J., Eds.; Springer: Singapore, 2019; pp. 179–187. [Google Scholar] [CrossRef]
- Shah, J.; Dubaria, D.; Widhalm, J. A Survey of DevOps tools for Networking. In Proceedings of the 2018 9th IEEE Annual Ubiquitous Computing, Electronics Mobile Communication Conference (UEMCON), New York, NY, USA, 8–10 November 2018; pp. 185–188. [Google Scholar] [CrossRef]
- Agrawal, P.; Rawat, N. Devops, A New Approach To Cloud Development & Testing. In Proceedings of the 2019 International Conference on Issues and Challenges in Intelligent Computing Techniques (ICICT), Ghaziabad, India, 27–28 September 2019; Volume 1, pp. 1–4. [Google Scholar] [CrossRef]
- Pang, C.; Hindle, A.; Barbosa, D. Understanding DevOps Education with Grounded Theory. In Proceedings of the 2020 IEEE/ACM 42nd International Conference on Software Engineering: Companion Proceedings (ICSE-Companion), Seoul, Republic of Korea, 5–11 October 2020; pp. 260–261. [Google Scholar]
- Wahaballa, A.; Wahballa, O.; Abdellatief, M.; Xiong, H.; Qin, Z. Toward unified DevOps model. In Proceedings of the 2015 6th IEEE International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 23–25 September 2015; pp. 211–214. [Google Scholar] [CrossRef]
- Mahboob, J.; Coffman, J. Continuous Integration, Delivery and Deployment: A Systematic Review on Approaches, Tools, Challenges and Practices. In Proceedings of the IEEE 11th Annual Computing and Communication Workshop and Conference, Virtual, 27–30 January 2021. [Google Scholar] [CrossRef]
- Railić, N.; Savić, M. Architecting Continuous Integration and Continuous Deployment for Microservice Architecture. In Proceedings of the 20th International Symposium INFOTEH-JAHORINA, Jahorina, Bosnia and Herzegovina, 17–19 March 2021. [Google Scholar] [CrossRef]
- Shah, J.; Dubaria, D.; Widhalm, J. Distributing Parallel Virtual Image Application using Continuous Integrity/Continuous Delivery Based on Cloud Infrastructure. In Proceedings of the 8th International Conference on Cyber and IT Service Management, Santa Barbara, CA, USA, 23–24 October 2020. [Google Scholar]
- Agarwal, A.; Gupta, S.; Choudhury, T. Continuous and Integrated Software Development using DevOps. In Proceedings of the International Conference on Advances in Computing and Communication Engineering, Paris, France, 22–23 June 2018. [Google Scholar]
- Fayollas, C.; Bonnin, H.; Flebus, O. SafeOps: A concept of continuous safety. In Proceedings of the 16th European Dependable Computing Conference, Munich, Germany, 7–10 September 2020. [Google Scholar] [CrossRef]
- Düllmann, T.; Paule, C.; van Hoorn, A. Exploiting DevOps Practices for Dependable and Secure Continuous Delivery Pipelines. In Proceedings of the ACM/IEEE 4th International Workshop on Rapid Continuous Software Engineering, Gothenburg, Sweden, 29 May 2018. [Google Scholar] [CrossRef]
- Khleel, N.A.A.; Károly, N. Comparison of version control system tools. Multidiszcip. TudomáNyok 2020, 10, 61–69. [Google Scholar] [CrossRef]
- Singh, C.; Seth, N.; Kaur, M.; Kaur, B. Comparison of Different CI/CD Tools Integrated with Cloud Platform. In Proceedings of the 9th International Conference on Cloud Computing, Data Science and Engineering, Naples, Italy, 17–20 September 2019. [Google Scholar]
- Azure Pipelines. 2022. Available online: https://azure.microsoft.com/en-us/services/devops/pipelines/ (accessed on 4 April 2022).
- DevOps and CI/CD on Google Cloud Explained. 2021. Available online: https://cloud.google.com/blog/topics/developers-practitioners/devops-and-cicd-google-cloud-explained (accessed on 4 April 2022).
- Alibaba Cloud DevOps Pipeline (Flow). 2022. Available online: https://www.alibabacloud.com/product/apsara-deveops/flow (accessed on 4 April 2022).
- IBM Cloud Continuous Delivery. 2022. Available online: https://www.ibm.com/cloud/continuous-delivery (accessed on 4 April 2022).
- DevOps and AWS. 2022. Available online: https://aws.amazon.com/devops/ (accessed on 4 April 2022).
- Cloud-native CI/CD on Red Hat OpenShift. 2022. Available online: https://cloud.redhat.com/learn/topics/ci-cd (accessed on 5 April 2022).
- Chen, G.; He, M.; Gao, J.; Liu, C.; Yin, Y.; Li, Q. Blockchain-Based Cyber Security and Advanced Distribution in Smart Grid. In Proceedings of the IEEE 4th International Conference on Electronics Technology, Chengdu, China, 7–10 May 2021. [Google Scholar] [CrossRef]
- Brandstatter, T.; Schulte, S.; Cito, J.; Borkowski, M. Characterizing Efficiency Optimizations in Solidity Smart Contracts. In Proceedings of the IEEE International Conference on Blockchain, Toronto, ON, Canada, 3–6 May 2020. [Google Scholar] [CrossRef]
- Murugan, S.; Kris, S. A Survey on Smart Contract Platforms and Features. In Proceedings of the 7th International Conference on Advanced Computing and Communication Systems, Coimbatore, India, 19–20 May 2021. [Google Scholar] [CrossRef]
- Li, Y. Finding Concurrency Exploits on Smart Contracts. In Proceedings of the IEEE/ACM 41st International Conference on Software Engineering: Companion Proceedings, Montreal, QC, Canada, 25–31 May 2019. [Google Scholar] [CrossRef]
- Chen, J. Finding Ethereum Smart Contracts Security Issues by Comparing History Versions. In Proceedings of the 35th IEEE/ACM International Conference on Automated Software Engineering, Melbourne, Australia, 21–25 September 2020. [Google Scholar] [CrossRef]
- Dika, A.; Nowostawski, M. Security Vulnerabilities in Ethereum Smart Contracts. In Proceedings of the IEEE Confs on Internet of Things, Green Computing and Communications, Cyber, Physical and Social Computing, Smart Data, Blockchain, Computer and Information Technology, Congress on Cybermatics, Halifax, NS, Canada, 30 July–3 August 2018. [Google Scholar] [CrossRef]
- Sayeed, S.; Marco-Gisbert, H.; Caira, T. Smart Contract: Attacks and Protections. IEEE Access 2020, 8, 24416–24427. [Google Scholar] [CrossRef]
- Destefanis, G.; Marchesi, M.; Ortu, M.; Tonelli, R.; Bracciali, A.; Hierons, R. Smart Contracts Vulnerabilities: A Call for Blockchain Software Engineering? In Proceedings of the 1st International Workshop on Blockchain Oriented Software Engineering, Campobasso, Italy, 20 March 2018. [Google Scholar]
- Richards, S. SCALING. 2022. Available online: https://ethereum.org/en/developers/docs/scaling/ (accessed on 22 March 2022).
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; Association for Computing Machinery: New York, NY, USA. [Google Scholar] [CrossRef]
- Pervez, H.; Muneeb, M.; Irfan, M.U.; Haq, I.U. A Comparative Analysis of DAG-Based Blockchain Architectures. In Proceedings of the 2018 12th International Conference on Open Source Systems and Technologies (ICOSST), Lahore, Pakistan, 19–21 December 2018; pp. 27–34. [Google Scholar] [CrossRef]
- Kraus, N.; Kraus, K.; Manzhura, O. Newest Digital Technology in Management of National Economic System; Atlantis Press: Amsterdam, The Netherlands, 2019; pp. 1–5. ISSN 2352-5428. [Google Scholar] [CrossRef][Green Version]
- Lokhava, M.; Losa, G.; Mazières, D.; Hoare, G.; Barry, N.; Gafni, E.; Jove, J.; Malinowsky, R.; McCaleb, J. Fast and Secure Global Payments with Stellar. In Proceedings of the 27th ACM Symposium on Operating Systems Principles, SOSP ’19, Huntsville, ON, Canada, 27–30 October 2019; Association for Computing Machinery: New York, NY, USA; pp. 80–96. [Google Scholar] [CrossRef]
- Katsiampa, P. An empirical investigation of volatility dynamics in the cryptocurrency market. Res. Int. Bus. Financ. 2019, 50, 322–335. [Google Scholar] [CrossRef]
- Song, W.; Zhang, W.; Zhai, L.; Liu, L.; Wang, J.; Huang, S.; Li, B. EOS.IO blockchain data analysis. J. Supercomput. 2022, 78, 5974–6005. [Google Scholar] [CrossRef]
- Benji, M.; Sindhu, M. A Study on the Corda and Ripple Blockchain Platforms. In Advances in Big Data and Cloud Computing; Peter, J.D., Alavi, A.H., Javadi, B., Eds.; Springer: Singapore, 2019; pp. 179–187. [Google Scholar]
- Aponte-Novoa, F.A.; Orozco, A.L.S.; Villanueva-Polanco, R.; Wightman, P. The 51% Attack on Blockchains: A Mining Behavior Study. IEEE Access 2021, 9, 140549–140564. [Google Scholar] [CrossRef]
- Aponte, F.; Gutierrez, L.; Pineda, M.; Meriño, I.; Salazar, A.; Wightman, P. Cluster-Based Classification of Blockchain Consensus Algorithms. IEEE Lat. Am. Trans. 2021, 19, 688–696. [Google Scholar] [CrossRef]
- Aponte-Novoa, F.A.; Villanueva-Polanco, R. On Proof-of-Accuracy Consensus Protocols. Mathematics 2022, 10, 2504. [Google Scholar] [CrossRef]
- Aponte-Novoa, F.A.; Povedano Álvarez, D.; Villanueva-Polanco, R.; Sandoval Orozco, A.L.; García Villalba, L.J. On Detecting Cryptojacking on Websites: Revisiting the Use of Classifiers. Sensors 2022, 22, 9219. [Google Scholar] [CrossRef] [PubMed]
- Liao, J.W.; Tsai, T.T.; He, C.K.; Tien, C.W. SoliAudit: Smart Contract Vulnerability Assessment Based on Machine Learning and Fuzz Testing. In Proceedings of the Sixth International Conference on Internet of Things: Systems, Management and Security, Granada, Spain, 22–25 October 2019. [Google Scholar]
- López, A.; Turégano, A.; Sandoval, A.; García, L. An Analysis of Smart Contracts Security Threats Alongside Existing Solutions. Entropy 2020, 22, 203. [Google Scholar] [CrossRef] [PubMed]
- Akca, S.; Rajan, A.; Peng, C. SolAnalyser: A Framework for Analysing and Testing Smart Contracts. In Proceedings of the 26th Asia-Pacific Software Engineering Conference, Putrajaya, Malaysia, 2–5 December 2019. [Google Scholar]
- Ashfaq, Q.; Khan, R.; Farooq, S. A Comparative Analysis of Static Code Analysis Tools that check Java Code Adherence to Java Coding Standards. In Proceedings of the 2019 2nd International Conference on Communication, Computing and Digital systems (C-CODE), Islamabad, Pakistan, 6–7 March 2019; pp. 98–103. [Google Scholar] [CrossRef]
- Paul, A. More Software Safety A Static Analysis Tools Perspective. Atzelectronics Worldw. 2017, 12, 16–21. [Google Scholar]
- Hermeling, M. Static Code Analysis in Continuous Integration—Agile and Rule-compliant Development. Atzelectronics Worldw. 2019, 14, 26–29. [Google Scholar] [CrossRef]
- Kumar, R.; Indraveni, K.; Goel, A.K. Automation of detection of security vulnerabilities in web services using dynamic analysis. In Proceedings of the 9th International Conference for Internet Technology and Secured Transactions (ICITST-2014), London, UK, 8–10 December 2014; pp. 334–336. [Google Scholar] [CrossRef]
- Zaazaa, O.; El Bakkali, H. Dynamic vulnerability detection approaches and tools: State of the Art. In Proceedings of the 2020 Fourth International Conference on Intelligent Computing in Data Sciences (ICDS), Fez, Morocco, 21–23 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Theunissen, T.; Hoppenbrouwers, S.; Overbeek, S. In Continuous Software Development, Tools Are the Message for Documentation. In Proceedings of the 23rd International Conference on Enterprise Information Systems—ICEIS, Online Streaming, 26—28 April 2021; Volume 2, pp. 153–164. [Google Scholar] [CrossRef]
- Remix. 2022. Available online: https://github.com/ethereum/remix-project (accessed on 26 March 2022).
- Eth Fiddle. 2022. Available online: https://ethfiddle.com/ (accessed on 26 March 2022).
- Loom Network. 2022. Available online: https://github.com/loomnetwork (accessed on 26 March 2022).
- ChainIDE. 2022. Available online: https://chainide.gitbook.io/chainide-english-1/ (accessed on 17 April 2022).
- Replit. 2022. Available online: https://github.com/replit (accessed on 26 March 2022).
- Visual Studio Code. 2022. Available online: https://github.com/microsoft/vscode (accessed on 17 April 2022).
- What’s New in IntelliJ IDEA 2022.1. 2022. Available online: https://www.jetbrains.com/idea/whatsnew/ (accessed on 17 April 2022).
- Remix Desktop. 2022. Available online: https://github.com/ethereum/remix-desktop (accessed on 17 April 2022).
- Truffle. 2022. Available online: https://github.com/trufflesuite/truffle (accessed on 17 April 2022).
- Hyperledger Composer. 2019. Available online: https://github.com/hyperledger-archives/composer (accessed on 17 April 2022).
- Software and SDKs. 2022. Available online: https://developers.stellar.org/docs/software-and-sdks/ (accessed on 17 April 2022).
- EOS Studio Releases. 2020. Available online: https://github.com/ObsidianLabs/EOS-Studio-Releases (accessed on 17 April 2022).
- EOS Studio Desktop. 2019. Available online: https://github.com/ObsidianLabs/EOS-Studio-Desktop (accessed on 17 April 2022).
- EOSIO Web IDE. 2020. Available online: https://github.com/EOSIO/eosio-web-ide (accessed on 17 April 2022).
- Zeus IDE. 2020. Available online: https://github.com/liquidapps-io/zeus-ide (accessed on 17 April 2022).
- Ertl, D.; Krapfenbauer, H. A Case Study of Developing an IDE for Embedded Software Using Open Source. In Proceedings of the 4th International Conference on Software Engineering Advances (ICSEA), Porto, Portugal, 20–25 September 2009; pp. 191–196. [Google Scholar] [CrossRef]
- Oyente. 2020. Available online: https://github.com/enzymefinance/oyente (accessed on 17 April 2022).
- Solgraph. 2019. Available online: https://github.com/raineorshine/solgraph (accessed on 17 April 2022).
- MadMax. 2021. Available online: https://github.com/nevillegrech/MadMax (accessed on 17 April 2022).
- Manticore. 2022. Available online: https://github.com/trailofbits/manticore (accessed on 17 April 2022).
- Mythril. 2022. Available online: https://github.com/ConsenSys/mythril (accessed on 17 April 2022).
- ContractLarva. 2022. Available online: https://github.com/gordonpace/contractLarva (accessed on 17 April 2022).
- SolMet Solidity parser. 2020. Available online: https://github.com/chicxurug/SolMet-Solidity-parser (accessed on 17 April 2022).
- Vandal. 2020. Available online: https://github.com/usyd-blockchain/vandal (accessed on 17 April 2022).
- Securify v2.0. 2021. Available online: https://github.com/eth-sri/securify2 (accessed on 17 April 2022).
- Slither. 2021. Available online: https://github.com/crytic/slither (accessed on 17 April 2022).
- Ethlint. 2021. Available online: https://github.com/duaraghav8/Ethlint (accessed on 17 April 2022).
- Revive-CC. 2020. Available online: https://github.com/sivachokkapu/revive-cc (accessed on 17 April 2022).
- Blockchain Analyzer. 2020. Available online: https://github.com/hyperledger-labs/blockchain-analyzer (accessed on 17 April 2022).
- Chaincode Analyzer. 2020. Available online: https://github.com/FujitsuLaboratories/ChaincodeAnalyzer (accessed on 17 April 2022).
- Porru, S.; Pinna, A.; Marchesi, M.; Tonelli, R. Blockchain-Oriented Software Engineering: Challenges and New Directions. In Proceedings of the 39th International Conference on Software Engineering Companion, IEEE Press, ICSE-C ’17, Buenos Aires, Argentina, 20–28 May 2017; pp. 169–171. [Google Scholar] [CrossRef]
- Chakraborty, P.; Shahriyar, R.; Iqbal, A.; Bosu, A. Understanding the Software Development Practices of Blockchain Projects: A Survey. In Proceedings of the 12th ACM/IEEE International Symposium on Empirical Software Engineering and Measurement, Association for Computing Machinery, ESEM ’18, New York, NY, USA, 3–6 May 2018. [Google Scholar] [CrossRef]
- Brar, H.K.; Kaur, P.J. Differentiating Integration Testing and unit testing. In Proceedings of the 2015 2nd International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 11–13 March 2015; pp. 796–798. [Google Scholar]
- Górski, T. Continuous Delivery of Blockchain Distributed Applications. Sensors 2022, 22, 128. [Google Scholar] [CrossRef] [PubMed]
- Khan, S.N.; Loukil, F.; Ghedira-Guegan, C.; Benkhelifa, E.; Bani-Hani, A. Blockchain smart contracts: Applications, challenges, and future trends. Peer Netw. Appl. 2021, 14, 2901–2925. [Google Scholar] [CrossRef] [PubMed]
- Azzopardi, S.; Ellul, J.; Pace, G.J. Monitoring Smart Contracts: ContractLarva and Open Challenges Beyond. In Proceedings of the Runtime Verification, Limassol, Cyprus, 10–13 November 2018; pp. 113–137. [Google Scholar]

| Cloud Provider | On-Premise Deployment | Multi-Cloud Deployment | Additionals |
|---|---|---|---|
| Microsoft | Yes | Yes | Extension marketplace |
| No | Yes | Binary Authorization | |
| Alibaba | Yes | Yes | |
| IBM | No | No | Issue tracking, Web IDE |
| Amazon | Yes | No | |
| Redhat | Yes | Yes |
| Blockchain | Open Source | Supports Cryptocurrency | Miner Participation | Smart Contract Language | Consensus Mechanism | Scalable |
|---|---|---|---|---|---|---|
| Ethereum | Yes | Yes | Public | Solidity | Proof of Work | No |
| Hyperledger Fabric | Yes | No | Public, Private | Java, Solidity, Golang | Proof of Work | Yes |
| NEM | No | Yes | Private | Java | Proof of Importance | Yes |
| Stellar | Yes | Yes | Public | Solidity, Javascript, Java, Go | Stellar Consensus Protocol | Yes |
| EOS | Yes | Yes | Public | C++ | Proof of Stake | Yes |
| Corda | Yes | No | Private | DAML, Kotlin, Java | Validity and Uniqueness | Yes |
| Description | Tool Name | Classification | Blockchain | Last Updated |
|---|---|---|---|---|
| Web-based IDE with built-in static analysis, and a test blockchain virtual machine | Remix [67] | Web-IDE | Ethereum | Apr 2022 |
| Web-based IDE that lets you write, compile, and debug your smart contract, powered by Loom Network | EthFiddle [68,69] | Web-IDE | Ethereum | Jun 2021 |
| A Cloud-Based Multi-Chain IDE that provides debugging, testing and deployment one-stop services, developers don’t need to install extra tools while working on smart contracts | ChainIDE [70] | Web-IDE | Ethereum | Mar 2022 |
| A customizable development environment for Ethereum with hot reloading, error checking, and first-class testnet support | Replit [71] | Web-IDE | Ethereum | Apr 2022 |
| Visual Studio Code is a lightweight but powerful source code editor which runs on your desktop and is available for Windows, macOS and Linux. | Visual Studio Code [72] | Local-IDE | Ethereum, Hyperledger Fabric, Corda | Apr 2022 |
| IntelliJ IDEA is an integrated development environment written in Java for developing computer software. | JetBrains IDEs [73] | Local-IDE | Ethereum, Corda | Apr 2022 |
| Remix Desktop is an Electron version of Remix IDE. It works on Linux, Windows, & Macs. | Remix Desktop [74] | Local-IDE | Ethereum | Dec 2021 |
| Truffle is a development environment, testing framework and asset pipeline for multiple blockchains. | Truffle [75] | Local-IDE | Ethereum, Corda | Apr 2022 |
| An application development framework which simplifies and expedites the creation of Hyperledger fabric blockchain applications. | Hyperledger Composer [76] | Local-IDE | Hyperledger Fabric | Aug 2019 |
| Stellar uses no specific IDE to work with. You install the stellar-sdk for the language you want to program with which means you can interact with the network through the API | Stellar-SDK [77] | Local-IDE | Stellar | Apr 2022 |
| A web IDE integrated with various tools required for EOSIO in a unified graphical application. | EOS Studio [78] | Web-IDE | EOS | Feb 2020 |
| Desktop version for EOS studio for Windows, Linux and Mac. | EOS Studio Desktop [79] | Local-IDE | EOS | Sep 2019 |
| IDE providing developers with a personal single-node EOSIO blockchain for development and testing. | EOSIO Quickstart Web IDE [80] | Web-IDE | EOS | Jun 2020 |
| A source code editor for Windows, Linux and macOS. | Zeus IDE [81] | Local-IDE | EOS | May 2021 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Reyes, A.; Jimeno, M.; Villanueva-Polanco, R. Continuous and Secure Integration Framework for Smart Contracts. Sensors 2023, 23, 541. https://doi.org/10.3390/s23010541
Reyes A, Jimeno M, Villanueva-Polanco R. Continuous and Secure Integration Framework for Smart Contracts. Sensors. 2023; 23(1):541. https://doi.org/10.3390/s23010541
Chicago/Turabian StyleReyes, Alvaro, Miguel Jimeno, and Ricardo Villanueva-Polanco. 2023. "Continuous and Secure Integration Framework for Smart Contracts" Sensors 23, no. 1: 541. https://doi.org/10.3390/s23010541
APA StyleReyes, A., Jimeno, M., & Villanueva-Polanco, R. (2023). Continuous and Secure Integration Framework for Smart Contracts. Sensors, 23(1), 541. https://doi.org/10.3390/s23010541







