A Systematic Literature Review and Meta-Analysis on Scalable Blockchain-Based Electronic Voting Systems
Abstract
1. Introduction
- We describe the research methodology and a literature evaluation on scalable Blockchain-based electronic voting;
- We introduce the background knowledge of electronic voting and Blockchain technology from the perspective of scalability, summarized in the previous work. The motivations and benefits for applying Blockchain to electronic voting are discussed in terms of requirements and challenges in electronic voting and the characteristics of Blockchain;
- We summarize an optimized research framework according to the Blockchain architecture, including the scalability aspect of Blockchain and horizontal and vertical scalability trilemma in Blockchain, and analyse and specify significant characteristics of Blockchain scalability;
- As for the Blockchain applications in electronic voting, we reviewed the previous work on electronic voting based on Blockchain and focused on scalability;
- We analysed the previous research by following our methodology to answer the required questions regarding Blockchain function/performance requirements for electronic voting by comparing different Blockchain project implementations to provide a reference for practitioners;
- Finally, some open issues and challenges in the field of the electronic voting system, combined with Blockchain, are highlighted, such as shading, consensus algorithm, block size increase, directed acyclic graph, forking, and an increase in authorized hardware devices to decrease block generation rate;
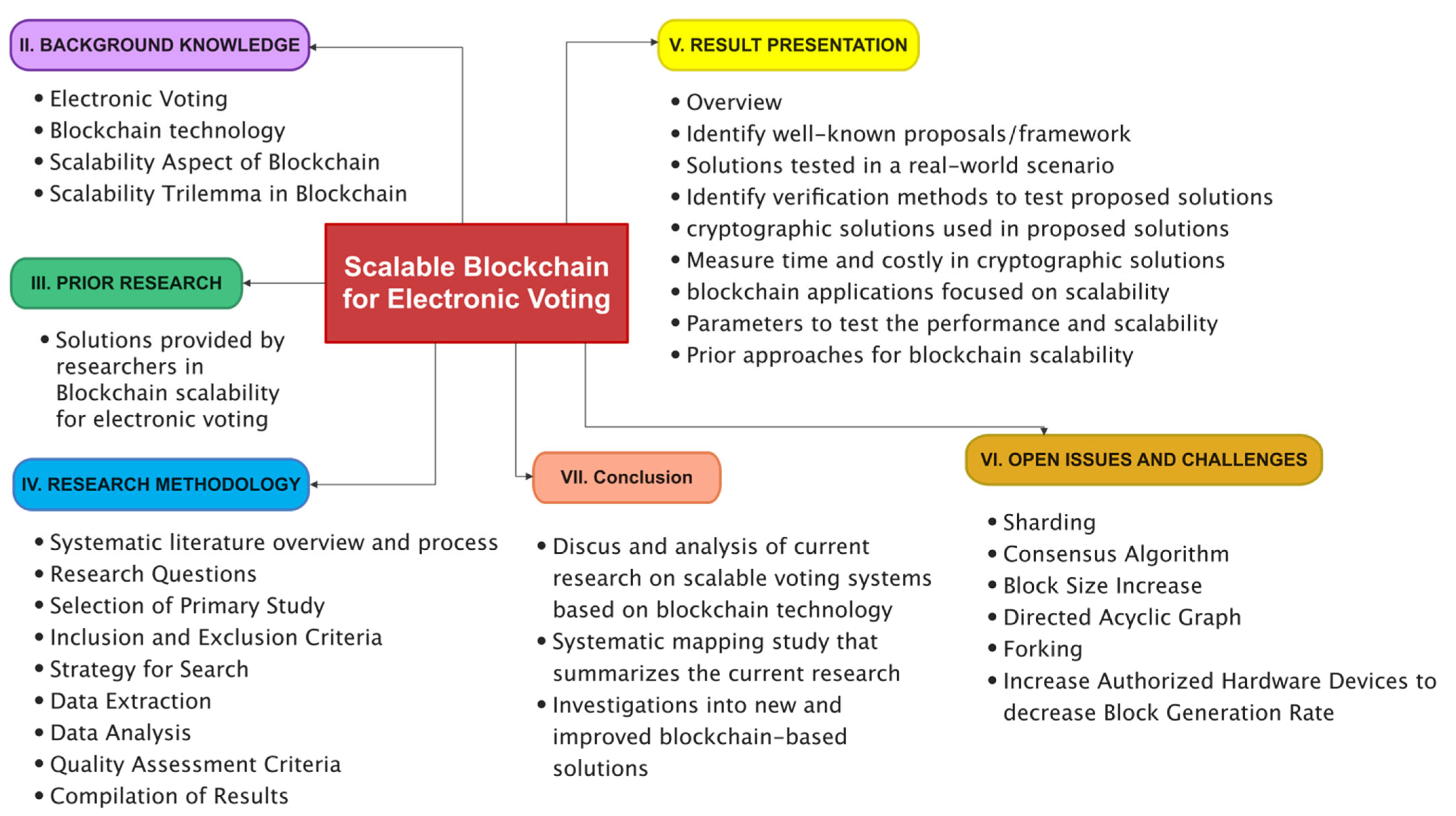
2. Background Knowledge
2.1. Electronic Voting
- Optical scanning;
- Electronically printed ballots;
- Centralized and decentralized software or applications for voting through the Internet;
- Remoteness;
- Supervision.
- Insufficient clarity and comprehension of such systems on the part of non-experts;
- An absence of standards and norms;
- Threats posed by system suppliers, malevolent users, and privileged insiders and the potential for these individuals to attack and manipulate the system;
- Cost increases due to required information and communication technologies (ICT) such as infrastructure, maintenance, and power consumption;
2.2. Blockchain Technology
- The ability to write;
- The ability to read.
2.3. Scalability Aspect of Blockchain
- Horizontal: This is accomplished by adding/increasing the number of computers in an existing pool/network;
- Vertical: This is accomplished by adding more power (such as memory, processing, and storage-efficient approaches) to an existing pool of resources. As a result, these core notions have been employed to describe scalability in Blockchains.
2.4. Scalability Trilemma in Blockchain
- Scalability: A high rate of transactions per second; decentralization: involvement of a vast number of individuals in the construction and certification of blocks;
- Security: Increasing the cost of gaining control over the network.
2.4.1. Decentralization over Scalability
2.4.2. Security over Scalability
2.4.3. Scalability over Security and Decentralization
- A comprehensive assessment of studies on scalable Blockchain-based electronic voting systems;
- Identifying the most critical trends in the subject;
- Identifying the key issues that scalable Blockchain-based electronic voting systems confront.
3. Related Work
4. Research Methodology
4.1. Systematic Literature Overview and Process
- Planning the review;
- Selection process;
- Conducting the review;
- Screening and refinement;
- Reporting the review.
4.2. Research Questions
4.3. Selection of Primary Study
- Scopus;
- ScienceDirect;
- IEEE Xplore Digital Library;
- SpringerLink;
- ACM Digital Library.
4.4. Inclusion and Exclusion Criteria
4.5. Strategy for Search
- Population: Articles describing scalable Blockchain-based electronic voting solutions for big or small-scale elections were reviewed.
- Intervention: Gathering information on electronic voting systems built on Blockchain platforms.
- Comparison: The results of the research will not be compared.
- Outcomes: It is essential to understand the scalability of Blockchain-based electronic voting systems and how they are utilized in real-world situations, advantages and disadvantages, and the cryptographic methods.
- Setting: Electronic voting, scalable Blockchain electronic voting, and Blockchain.
4.6. Data Extraction
- The initial investigation, during which the majority of the relevant texts were gathered.
- Duplication removal, where removes the duplicate papers.
- The final selection was based on the title and abstract, and the inclusion and exclusion criteria were applied to the results.
- After a thorough reading, all chosen papers were subjected to inclusion and exclusion criteria.




4.7. Data Analysis
4.8. Quality Assessment Criteria
4.9. Compilation of Results
5. Result Presentation
5.1. Overview
5.2. RQ1: What Are Some of the Most Well-Known Proposals/Implementations for Scalable Blockchain-Based Electronic Voting?
| # | Blockchain Framework | Articles |
|---|---|---|
| 1 | Bitcoin | [7,24,128,128,149,150,156,164] |
| 2 | Ethereum | [14,26,34,46,53,123,125,130,131,135,139,140,141,141,142,143,144,144,148,152,153,154,165,168,169,170,171,177,181] |
| 3 | Hyperledger Fabric | [29,46,129,136,145,146,158,160,163,185] |
| 4 | Hyperledger Sawtooth | [127,137], |
| 5 | Multichain | [126,149,176] |
| 6 | Helios | [165] |
| 7 | Phantom | [148] |
| 8 | Blockchain Database | [39,132,133,134,155,159,162,178,182] |
| 9 | Conflux | [147] |
| 10 | Waves | [157] |
| 11 | Platform Independent | [138,166,174,175,179] |
5.3. RQ2: Were Those Solutions Tested in a Real-World Scenario?
5.4. RQ3: What Are the Verification Methods Used to Test Those Solutions?
5.5. RQ4: What Are the Different Cryptographic Solutions Employed in Previous Research?
5.6. RQ5: Were the Cryptographic Operations Used in Prior Solutions too Costly and Time-Consuming?
5.7. RQ6: What Are the Latest Blockchain Applications Focused on Scalability?
5.8. RQ7: What Parameters Test the Performance and Scalability of the Electoral Process on a Large Scale?
5.9. RQ8: What Are the Prior Approaches for Blockchain Scalability to Efficiently Enhance the Electoral Process on a Large Scale?
- Payment channel networks: By constructing a micropayment channel, the payment channel allows several parties to conduct various off-chain transactions without publicly committing all transactions. Minimizing the workload on the main chain leads to an increase in throughput. In a typical payment channel network, just two transactions are required to update a record on the main-chain to complete all transactions between parties or satisfy the need for an on-chain transaction. Participants in this network can undertake an unlimited number of transactions. Through intermediaries, even parties not in a direct relationship can enter into transactions [128,160].
- Sharding: A Blockchain’s mining node stores all the states, including account balance and transaction history, which reduces transaction throughput linearly. Sharding divides an extensive database into manageable pieces to boost efficiency [123,127]. In the Blockchain, it is the horizontal separation of the main chain into shards. Each partition/shard stores its state. Sharding is a technique that separates the main chain into multiple independent groups, even though it is considered an off-chain solution. As a result, each transaction broadcast on the network does not have to be mined by a single node. Each shard acts as its Blockchain inside the network through the Merkle tree and may be joined to the main chain using cryptographic means.
| Scalable Classifications or Approaches | Impact on Scalability | Articles | Issues/Challenges | |
|---|---|---|---|---|
| On-chain | Blockchain pipelining | Throughput | [145,187] | It is well-known that some approaches, such as BigchainDB, are vulnerable to a 33 percent attack. |
| Blockchain delivery network | Throughput and storage | [126,164] | Malicious actors may be able to spread blocks via this vulnerability. Reliable network infrastructure is a must here. | |
| Block size adjustment | Throughput and latency | [1,188] | Application-specific, forks, increased block generation rate (BGR) | |
| Off-chain | Payment channel networks | Throughput | [128,160] | Issues with one’s privacy and security. For transactions to be committed, it is necessary for both parties to be online or to lock their tokens. |
| Sharding | Throughput | [123,127] | Security (shard takeover problem) Exchange of information (maintaining atomicity and preventing overloading of shards in cross-shard transactions) | |
| Hardware-assisted approaches Parallel mining Redesigning a new Blockchain | Throughput and latency | [129,146] | Adding nodes degrades performance. TPS/latency centralises. Requires an attractive incentive system | |
| Throughput and BGR | [147,187] | Requires numerous active miners in a single network | ||
| Horizontal/vertical scalability | [152,185] | Fork avoidance, adversaries, avoidance incentive mechanism | ||
6. Analysis and Discussion
6.1. Sharding
6.2. Consensus Algorithm
6.3. Block Size Increase
6.4. Directed Acyclic Graph
6.5. Increase Authorized Hardware Devices to Decrease Block Generation Rate
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Khan, K.M.; Arshad, J.; Khan, M.M. Investigating performance constraints for blockchain based secure e-voting system. Futur. Gener. Comput. Syst. 2019, 105, 13–26. [Google Scholar] [CrossRef]
- Gritzalis, D.A. Secure Electronic Voting; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Taş, R.; Tanrıöver, Ö.Ö. A Systematic Review of Challenges and Opportunities of Blockchain for E-Voting. Symmetry 2020, 12, 1328. [Google Scholar] [CrossRef]
- Noizat, P. Blockchain electronic vote. In Handbook of Digital Currency; Elsevier: Amsterdam, The Netherlands, 2015; pp. 453–461. [Google Scholar]
- Garg, K.; Saraswat, P.; Bisht, S.; Aggarwal, S.K.; Kothuri, S.K.; Gupta, S. A Comparitive Analysis on E-Voting System Using Blockchain. In Proceedings of the 2019 4th International Conference on Internet of Things: Smart Innovation and Usages (IoT-SIU), Ghaziabad, India, 18–19 April 2019; pp. 1–4. [Google Scholar]
- Febriyanto, E.; Rahayu, N.; Pangaribuan, K.; Sunarya, P.A. Using Blockchain Data Security Management for E-Voting Systems. In Proceedings of the 2020 8th International Conference on Cyber and IT Service Management (CITSM), Pangkal Pinang, Indonesia, 23–24 October 2020; pp. 1–4. [Google Scholar]
- Adiputra, C.K.; Hjort, R.; Sato, H. A proposal of blockchain-based electronic voting system. In Proceedings of the 2018 Second World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 30–31 October 2018; pp. 22–27. [Google Scholar]
- Pawlak, M.; Poniszewska-Marańda, A. Trends in blockchain-based electronic voting systems. Inf. Process. Manag. 2021, 58, 102595. [Google Scholar] [CrossRef]
- Roh, C.-H.; Lee, I.-Y. A study on electronic voting system using private blockchain. J. Inf. Process. Syst. 2020, 16, 421–434. [Google Scholar]
- Vivek, S.; Yashank, R.; Prashanth, Y.; Yashas, N.; Namratha, M. E-voting systems using blockchain: An exploratory literature survey. In Proceedings of the 2020 Second International Conference on Inventive Research in Computing Applications (ICIRCA), Coimbatore, India, 15–17 July 2020; pp. 890–895. [Google Scholar]
- Jafar, U.; Ab Aziz, M.J.; Shukur, Z. Blockchain for Electronic Voting System—Review and Open Research Challenges. Sensors 2021, 21, 5874. [Google Scholar] [CrossRef]
- Abuidris, Y.; Hassan, A.; Hadabi, A.; Elfadul, I. Risks and opportunities of blockchain based on e-voting systems. In Proceedings of the 2019 16th International Computer Conference on Wavelet Active Media Technology and Information Processing, Chengdu, China, 16–18 December 2019; pp. 365–368. [Google Scholar]
- Zheng, S.; Huo, R.; Huang, T.; Liu, J.; Wang, S.; Feng, W. Survey of blockchain: Principle, progress and application. J. Commun. 2020, 41, 134. [Google Scholar]
- Pawade, D.; Sakhapara, A.; Badgujar, A.; Adepu, D.; Andrade, M. Secure Online Voting System Using Biometric and Blockchain. In Data Management, Analytics and Innovation; Springer: Berlin/Heidelberg, Germany, 2020; pp. 93–110. [Google Scholar]
- Aysan, A.; Bergigui, F.; Disli, M. Blockchain-Based Solutions in Achieving SDGs after COVID-19. J. Open Innov. Technol. Mark. Complex. 2021, 7, 151. [Google Scholar] [CrossRef]
- Aysan, A.F.; Bergigui, F. Blockchain paths in rebooting the global response to the sustainable development goals after COVID-19. Preprints 2020, 2020100074. [Google Scholar] [CrossRef]
- World Health Organization. A Year without Precedent: WHO’s COVID-19 Response. Available online: https://www.who.int/news-room/spotlight/a-year-without-precedent-who-s-covid-19-response (accessed on 15 November 2021).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System Bitcoin: A Peer-to-Peer Electronic Cash System. Bitcoin. Org. 2009. Available online: https://bitcoin.org/en/bitcoin-paper (accessed on 23 November 2021).
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain technology: Beyond bitcoin. Appl. Innov. 2016, 2, 71. [Google Scholar]
- Deep, G.; Mohana, R.; Nayyar, A.; Sanjeevikumar, P.; Hossain, E. Authentication Protocol for Cloud Databases Using Blockchain Mechanism. Sensors 2019, 19, 4444. [Google Scholar] [CrossRef]
- Çabuk, U.C.; Adiguzel, E.; Karaarslan, E. A survey on feasibility and suitability of blockchain techniques for the e-voting systems. arXiv 2020, arXiv:2002.07175. [Google Scholar] [CrossRef]
- Ravikumar, S.; Antony Kumar, K.; Sathana, V. E-voting system using blockchain with network security. Turk. J. Comput. Math. Educ. (TURCOMAT) 2021, 12, 19–22. [Google Scholar]
- Nicolas, K.; Wang, Y.; Giakos, G.C.; Wei, B.; Shen, H. Blockchain System Defensive Overview for Double-Spend and Selfish Mining Attacks: A Systematic Approach. IEEE Access 2020, 9, 3838–3857. [Google Scholar] [CrossRef]
- Yi, H. Securing e-voting based on blockchain in P2P network. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 137. [Google Scholar] [CrossRef]
- Twesige, R.L. A simple explanation of Bitcoin and Blockchain technology. Comput. Sci. 2015, 1, 1–5. [Google Scholar]
- Zhang, Y.; Li, Y.; Fang, L.; Chen, P.; Dong, X. Privacy-protected Electronic Voting System Based on Blockchin and Trusted Execution Environment. In Proceedings of the 2019 IEEE 5th International Conference on Computer and Communications (ICCC), Chengdu, China, 6–9 December 2019; pp. 1252–1257. [Google Scholar]
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G.; Group, P. Preferred reporting items for systematic reviews and meta-analyses: The PRISMA statement. Ann. Intern. Med. 2009, 151, 264–269. [Google Scholar] [CrossRef]
- Kitchenham, B.; Brereton, O.P.; Budgen, D.; Turner, M.; Bailey, J.; Linkman, S. Systematic literature reviews in software engineering—A systematic literature review. Inf. Softw. Technol. 2009, 51, 7–15. [Google Scholar] [CrossRef]
- Verwer, M.B.; Dionysiou, I.; Gjermundrød, H. TrustedEVoting (TeV) a Secure, Anonymous and Verifiable Blockchain-Based e-Voting Framework. In Proceedings of the International Conference on e-Democracy, Athens, Greece, 12–13 December 2019; pp. 129–143. [Google Scholar]
- Draper, S.W.; Brown, M.I. Increasing interactivity in lectures using an electronic voting system. J. Comput. Assist. Learn. 2004, 20, 81–94. [Google Scholar] [CrossRef]
- ND Institute. Common Electronic Voting and Counting Technologies. Available online: https://www.ndi.org/e-voting-guide/common-electronic-voting-and-counting-technologies (accessed on 12 March 2022).
- Kiayias, A.; Zacharias, T.; Zhang, B. An Efficient E2E Verifiable E-voting System without Setup Assumptions. IEEE Secur. Priv. 2017, 15, 14–23. [Google Scholar] [CrossRef]
- Shahzad, B.; Crowcroft, J. Trustworthy Electronic Voting Using Adjusted Blockchain Technology. IEEE Access 2019, 7, 24477–24488. [Google Scholar] [CrossRef]
- Braghin, C.; Cimato, S.; Cominesi, S.R.; Damiani, E.; Mauri, L. Towards Blockchain-Based E-Voting Systems. In Proceedings of the International Conference on Business Information Systems, Seville, Spain, 26–28 June 2019; pp. 274–286. [Google Scholar]
- Kumar, D.A.; Begum, T.U.S. Electronic voting machine—A review. In Proceedings of the International Conference on Pattern Recognition, Informatics and Medical Engineering (PRIME-2012), Tamilnadu, India, 21–23 March 2012; pp. 41–48. [Google Scholar]
- Alam, A.; Rashid, S.Z.U.; Salam, M.A.; Islam, A. Towards blockchain-based e-voting system. In Proceedings of the 2018 International Conference on Innovations in Science, Engineering and Technology (ICISET), Chittagong, Bangladesh, 27–28 October 2018; pp. 351–354. [Google Scholar]
- Jefferson, D.; Rubin, A.D.; Simons, B.; Wagner, D. Analyzing internet voting security. Commun. ACM 2004, 47, 59–64. [Google Scholar] [CrossRef]
- Kshetri, N.; Voas, J. Blockchain-Enabled E-Voting. IEEE Softw. 2018, 35, 95–99. [Google Scholar] [CrossRef]
- Han, G.; Li, Y.; Yu, Y.; Choo, K.-K.R.; Guizani, N. Blockchain-Based Self-Tallying Voting System with Software Updates in Decentralized IoT. IEEE Netw. 2020, 34, 166–172. [Google Scholar] [CrossRef]
- Springall, D.; Finkenauer, T.; Durumeric, Z.; Kitcat, J.; Hursti, H.; MacAlpine, M.; Halderman, J.A. Security analysis of the Estonian internet voting system. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 703–715. [Google Scholar]
- Serdult, U.; Germann, M.; Mendez, F.; Portenier, A.; Wellig, C. Fifteen years of internet voting in Switzerland [history, governance and use]. In Proceedings of the 2015 Second International Conference on eDemocracy & eGovernment (ICEDEG), Quito, Ecuador, 8–10 April 2015; pp. 126–132. [Google Scholar]
- Iqbal, M.; Matulevičius, R. Blockchain-based application security risks: A systematic literature review. In Proceedings of the International Conference on Advanced Information Systems Engineering, Rome, Italy, 3–7 June 2019; pp. 176–188. [Google Scholar]
- Gjøsteen, K. Analysis of an internet voting protocol. Cryptol. ePrint Arch. 2010, 380. [Google Scholar]
- Rubin, A.D. Security considerations for remote electronic voting. Commun. ACM 2002, 45, 39–44. [Google Scholar] [CrossRef]
- Damgård, I.; Groth, J.; Salomonsen, G. The theory and implementation of an electronic voting system. In Secure Electronic Voting; Springer: Boston, MA, USA, 2003; pp. 77–99. [Google Scholar]
- Soud, M.; Helgason, S.; Hjálmtýsson, G.; Hamdaqa, M. TrustVote: On elections we trust with distributed ledgers and smart contracts. In Proceedings of the 2020 2nd Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), Paris, France, 28–30 September 2020; pp. 176–183. [Google Scholar]
- Leema, A.A.; Gulzar, Z.; Padmavathy, P. Trusted and Secured E-Voting Election System Based on Block Chain Technology. In Proceedings of the International Conference on Computer Networks, Big Data and IoT (ICCBI—2019), Madurai, India, 19–20 December 2019; Springer Science and Business Media LLC: Cham, Switzerland, 2020; pp. 81–88. [Google Scholar]
- Lee, K.; James, J.I.; Ejeta, T.G.; Kim, H.J. Electronic voting service using block-chain. J. Digit. Forensics Secur. Law 2016, 11, 8. [Google Scholar] [CrossRef][Green Version]
- Simons, B.; Jones, D.W. Internet voting in the US. Commun. ACM 2012, 55, 68–77. [Google Scholar] [CrossRef]
- Kremer, S.; Ryan, M.; Smyth, B. Election verifiability in electronic voting protocols. In Proceedings of the European Symposium on Research in Computer Security, Guildford, UK, 14–18 September 2010; pp. 389–404. [Google Scholar]
- Germann, M.; Serdült, U. Internet voting and turnout: Evidence from Switzerland. Elect. Stud. 2017, 47, 1–12. [Google Scholar] [CrossRef]
- Park, S.; Specter, M.; Narula, N.; Rivest, R.L. Going from bad to worse: From Internet voting to blockchain voting. J. Cybersecur. 2021, 7, tyaa025. [Google Scholar] [CrossRef]
- Pawlak, M.; Poniszewska-Marańda, A.; Kryvinska, N. Towards the intelligent agents for blockchain e-voting system. Procedia Comput. Sci. 2018, 141, 239–246. [Google Scholar] [CrossRef]
- Pawlak, M.; Guziur, J.; Poniszewska-Marańda, A. Towards the blockchain technology for ensuring the integrity of data storage and transmission. In Proceedings of the OTM Confederated International Conferences on the Move to Meaningful Internet Systems, Valletta, Malta, 22–26 October 2018; pp. 297–304. [Google Scholar]
- Soni, Y.; Maglaras, L.; Ferrag, M.A. Blockchain based voting systems. In Proceedings of the European Conference on Cyber Warfare and Security, Online, 25–26 June 2020; Academic Conferences International Limited: Oxford, UK; pp. 241–248. [Google Scholar]
- Drechsler, W.; Madise, Ü. Electronic voting in Estonia. In Electronic Voting and Democracy; Palgrave Macmillan: London, UK, 2004; pp. 97–108. [Google Scholar]
- Kohno, T.; Stubblefield, A.; Rubin, A.D.; Wallach, D.S. Analysis of an electronic voting system. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 9–12 May 2004; pp. 27–40. [Google Scholar]
- Ali, M.S.; Vecchio, M.; Pincheira, M.; Dolui, K.; Antonelli, F.; Rehmani, M.H. Applications of Blockchains in the Internet of Things: A Comprehensive Survey. IEEE Commun. Surv. Tutorials 2018, 21, 1676–1717. [Google Scholar] [CrossRef]
- Hewa, T.; Ylianttila, M.; Liyanage, M. Survey on blockchain based smart contracts: Applications, opportunities and challenges. J. Netw. Comput. Appl. 2021, 177, 102857. [Google Scholar] [CrossRef]
- Yli-Huumo, J.; Ko, D.; Choi, S.; Park, S.; Smolander, K. Where Is Current Research on Blockchain Technology?—A Systematic Review. PLoS ONE 2016, 11, e0163477. [Google Scholar] [CrossRef]
- Haber, S.; Stornetta, W.S. How to time-stamp a digital document. In Proceedings of the Conference on the Theory and Application of Cryptography, Trondheim, Norway, 30 May–3 June 1990; pp. 437–455. [Google Scholar]
- Bayer, D.; Haber, S.; Stornetta, W.S. Improving the Efficiency and Reliability of Digital Time-Stamping. In Seq II: Methods in Communication, Security, and Computer Science; Springer: Berlin, Germany, 1992; pp. 329–334. [Google Scholar]
- Giraldo, F.D.; Milton, C.B.; Gamboa, C.E. Electronic Voting Using Blockchain and Smart Contracts: Proof of Concept. IEEE Lat. Am. Trans. 2020, 18, 1743–1751. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Boston, MA, USA, 11–14 December 2017; pp. 557–564. [Google Scholar]
- Katta, P.; Mohammed, O.A.; Prabaakaran, K.; Divya, M.; Jayashree, G.; Keerthika, D. Smart voting using Fingerprint, Face and OTP Technology with Blockchain. J. Phys. Conf. Ser. 2021, 1916, 012139. [Google Scholar] [CrossRef]
- Efanov, D.; Roschin, P. The All-Pervasiveness of the Blockchain Technology. Procedia Comput. Sci. 2018, 123, 116–121. [Google Scholar] [CrossRef]
- Ahram, T.; Sargolzaei, A.; Sargolzaei, S.; Daniels, J.; Amaba, B. Blockchain technology innovations. In Proceedings of the 2017 IEEE Technology & Engineering Management Conference (TEMSCON), Santa Clara, CA, USA, 8–10 June 2017; pp. 137–141. [Google Scholar]
- Jalal, I.; Shukur, Z.; Bakar, K. Validators Performance Efficiency Consensus (VPEC): A Public Blockchain. Test Eng. Manag. 2020, 83, 17530–17539. [Google Scholar]
- Salman, T.; Zolanvari, M.; Erbad, A.; Jain, R.; Samaka, M. Security Services Using Blockchains: A State of the Art Survey. IEEE Commun. Surv. Tutorials 2018, 21, 858–880. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Privacy preservation in blockchain based IoT systems: Integration issues, prospects, challenges, and future research directions. Future Gener. Comput. Syst. 2019, 97, 512–529. [Google Scholar] [CrossRef]
- Lu, Y. The blockchain: State-of-the-art and research challenges. J. Ind. Inf. Integr. 2019, 15, 80–90. [Google Scholar] [CrossRef]
- Pilkington, M. Blockchain Technology: Principles and Applications. In Research Handbook on Digital Transformations; Xavier, F., Zhegu, O.M., Eds.; Edward Elgar Publishing: London, UK, 2015; pp. 225–253. [Google Scholar]
- Batubara, F.R.; Ubacht, J.; Janssen, M. Challenges of blockchain technology adoption for e-government: A systematic literature review. In Proceedings of the 19th Annual International Conference on Digital Government Research: Governance in the Data Age, Delft, The Netherlands, 30 May–1 June 2018; pp. 1–9. [Google Scholar]
- Lucca, A.V.; Sborz, G.M.; Leithardt, V.; Beko, M.; Zeferino, C.A.; Parreira, W. A Review of Techniques for Implementing Elliptic Curve Point Multiplication on Hardware. J. Sens. Actuator Netw. 2020, 10, 3. [Google Scholar] [CrossRef]
- Imran, M.; Rashid, M.; Jafri, A.R.; Najam-ul-Islam, M. ACryp-Proc: Flexible asymmetric crypto processor for point multiplication. IEEE Access 2018, 6, 22778–22793. [Google Scholar] [CrossRef]
- Wu, B.; Duan, T. The advantages of blockchain technology in commercial bank operation and management. In Proceedings of the 2019 4th International Conference on Machine Learning Technologies, Cairo, Egypt, 28–30 March 2019; pp. 83–87. [Google Scholar]
- Niranjanamurthy, M.; Nithya, B.; Jagannatha, S. Analysis of Blockchain technology: Pros, cons and SWOT. Clust. Comput. 2019, 22, 14743–14757. [Google Scholar] [CrossRef]
- Golosova, J.; Romanovs, A. The advantages and disadvantages of the blockchain technology. In Proceedings of the 2018 IEEE 6th workshop on advances in information, electronic and electrical engineering (AIEEE), Vilnius, Lithuania, 8–10 November 2018; pp. 1–6. [Google Scholar]
- Hussain, H.A.; Mansor, Z.; Shukur, Z. Comprehensive Survey and Research Directions On Blockchain Iot Access Control. Int. J. Adv. Comput. Sci. Appl. 2021, 12, 239–244. [Google Scholar] [CrossRef]
- Yadav, S.; Singh, S.P. Blockchain critical success factors for sustainable supply chain. Resour. Conserv. Recycl. 2020, 152, 104505. [Google Scholar] [CrossRef]
- Sheth, H.; Dattani, J. Overview of blockchain technology. Asian J. Converg. Technol. 2019, V. [Google Scholar] [CrossRef]
- Upadhyay, N. Demystifying blockchain: A critical analysis of challenges, applications and opportunities. Int. J. Inf. Manag. 2020, 54, 102120. [Google Scholar] [CrossRef]
- Monrat, A.A.; Schelén, O.; Andersson, K. A survey of blockchain from the perspectives of applications, challenges, and opportunities. IEEE Access 2019, 7, 117134–117151. [Google Scholar] [CrossRef]
- Huang, J.; He, D.; Obaidat, M.S.; Vijayakumar, P.; Luo, M.; Choo, K.-K.R. The application of the blockchain technology in voting systems: A review. ACM Comput. Surv. 2021, 54, 1–28. [Google Scholar] [CrossRef]
- Baudier, P.; Kondrateva, G.; Ammi, C.; Seulliet, E. Peace engineering: The contribution of blockchain systems to the e-voting process. Technol. Forecast. Soc. Chang. 2020, 162, 120397. [Google Scholar] [CrossRef]
- Bellini, E.; Ceravolo, P.; Damiani, E. Blockchain-based e-vote-as-a-service. In Proceedings of the 2019 IEEE 12th International Conference on Cloud Computing (CLOUD), Milan, Italy, 8–13 July 2019; pp. 484–486. [Google Scholar]
- Jafar, U.; Aziz, M.J.A. A State of the Art Survey and Research Directions on Blockchain Based Electronic Voting System. In Proceedings of the International Conference on Advances in Cyber Security, Penang, Malaysia, 8–9 December 2020; Springer: Berlin/Heidelberg, Germany; pp. 248–266. [Google Scholar]
- Adeshina, S.A.; Ojo, A. Maintaining Voting Integrity using Blockchain. In Proceedings of the 2019 15th International Conference on Electronics, Computer and Computation (ICECCO), Abuja, Nigeria, 10–12 December 2019; pp. 1–5. [Google Scholar]
- Rosasooria, Y.; Saon, S.; Isa, M.A.M.; Yamaguchi, S.; Ahmadon, M.A. E-voting on blockchain using solidity language. In Proceedings of the 2020 Third International Conference on Vocational Education and Electrical Engineering (ICVEE), Surabaya, Indonesia, 3–4 October 2020; pp. 1–6. [Google Scholar]
- Neziri, V.; Shabani, I.; Dervishi, R.; Rexha, B. Assuring Anonymity and Privacy in Electronic Voting with Distributed Technologies Based on Blockchain. Appl. Sci. 2022, 12, 5477. [Google Scholar] [CrossRef]
- Ismail, L.; Materwala, H. A review of blockchain architecture and consensus protocols: Use cases, challenges, and solutions. Symmetry 2019, 11, 1198. [Google Scholar] [CrossRef]
- Tso, R.; Liu, Z.-Y.; Hsiao, J.-H. Distributed E-Voting and E-Bidding Systems Based on Smart Contract. Electronics 2019, 8, 422. [Google Scholar] [CrossRef]
- Iftikhar, Z.; Javed, Y.; Zaidi, S.; Shah, M.; Khan, Z.I.; Mussadiq, S.; Abbasi, K. Privacy Preservation in Resource-Constrained IoT Devices Using Blockchain—A Survey. Electronics 2021, 10, 1732. [Google Scholar] [CrossRef]
- Khanna, A.; Sah, A.; Bolshev, V.; Jasinski, M.; Vinogradov, A.; Leonowicz, Z.; Jasiński, M. Blockchain: Future of e-Governance in Smart Cities. Sustainability 2021, 13, 11840. [Google Scholar] [CrossRef]
- Ma, X.; Zhou, J.; Yang, X.; Liu, G. A Blockchain Voting System Based on the Feedback Mechanism and Wilson Score. Information 2020, 11, 552. [Google Scholar] [CrossRef]
- Apeh, A.J.; Ayo, C.K.; Adebiyi, A. A Scalable Blockchain Implementation Model for Nation-Wide Electronic Voting System. In Proceedings of the International Conference on Computational Science and Its Applications, Cagliari, Italy, 13–16 September 2021; pp. 84–100. [Google Scholar]
- Poon, J.; Buterin, V. Plasma: Scalable autonomous smart contracts. White Pap. 2017, 1–47. Available online: https://plasma.io/plasma.pdf (accessed on 6 September 2022).
- M Capital. Blockcrunch: DeFi Is a Ticking Time Bomb with Ben Sparango and Christian Keroles. Available online: https://multicoin.capital/es/2020/02/25/blockcrunch-defi-is-a-ticking-time-bomb-with-ben-sparango-and-christian-keroles/ (accessed on 12 April 2022).
- Kohad, H.; Kumar, S.; Ambhaikar, A. Scalability of Blockchain based E-voting system using Multiobjective Genetic Algorithm with Sharding. In Proceedings of the 2022 IEEE Delhi Section Conference (DELCON), New Delhi, India, 11–13 February 2022; pp. 1–4. [Google Scholar]
- Khan, D.; Jung, L.T.; Hashmani, M.A. A Scalable Blockchain Consensus Model. In Proceedings of the 2021 International Conference on Computer & Information Sciences (ICCOINS), Kuala Lumpur, Malaysia, 13–15 July 2021; pp. 151–156. [Google Scholar]
- Majumder, S.; Ray, S. Usage of Blockchain Technology in e-Voting System Using Private Blockchain. In Intelligent Data Engineering and Analytics; Springer: Singapore, 2022; pp. 51–61. [Google Scholar]
- Jalal, I.; Shukur, Z.; Bakar, K.A.A. A Study on Public Blockchain Consensus Algorithms: A Systematic Literature Review. Algebra Number Theory 2020. [Google Scholar] [CrossRef]
- Dhulavvagol, P.M.; Bhajantri, V.H.; Totad, S.G. Blockchain Ethereum Clients Performance Analysis Considering E-Voting Application. Procedia Comput. Sci. 2020, 167, 2506–2515. [Google Scholar] [CrossRef]
- Fernandes, A.; Garg, K.; Agrawal, A.; Bhatia, A. Decentralized Online Voting using Blockchain and Secret Contracts. In Proceedings of the 2021 International Conference on Information Networking (ICOIN), Jeju Island, Korea, 13–16 January 2021; pp. 582–587. [Google Scholar]
- Akbari, E.; Wu, Q.; Zhao, W.; Arabnia, H.R.; Yang, M.Q. From blockchain to internet-based voting. In Proceedings of the International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 14–16 December 2017; pp. 218–221. [Google Scholar]
- Cucurull, J.; Rodríguez-Pérez, A.; Finogina, T.; Puiggali, J. Blockchain-based internet voting: Systems’ compliance with international standards. In Proceedings of the International Conference on Business Information Systems, Berlin, Germany, 18–20 July 2018; pp. 300–312. [Google Scholar]
- Akbari, E.; Zhao, W.; Yang, S.; Luo, X. The impact of block parameters on the throughput and security of blockchains. In Proceedings of the 2020 the 2nd International Conference on Blockchain Technology, Hilo, HI, USA, 12–14 March 2020; pp. 13–18. [Google Scholar]
- Xie, J.; Yu, F.R.; Huang, T.; Xie, R.; Liu, J.; Liu, Y. A Survey on the Scalability of Blockchain Systems. IEEE Netw. 2019, 33, 166–173. [Google Scholar] [CrossRef]
- El Fezzazi, A.; Adadi, A.; Berrada, M. Towards a Blockchain based Intelligent and Secure Voting. In Proceedings of the 2021 Fifth International Conference on Intelligent Computing in Data Sciences (ICDS), Fez, Morocco, 20–22 October 2021; pp. 1–8. [Google Scholar]
- Febrero, P.; Pereira, J. Cryptocurrency Constellations across the Three-Dimensional Space: Governance Decentralization, Security, and Scalability. IEEE Trans. Eng. Manag. 2020, 1–12. [Google Scholar] [CrossRef]
- Berdik, D.; Otoum, S.; Schmidt, N.; Porter, D.; Jararweh, Y. A Survey on Blockchain for Information Systems Management and Security. Inf. Process. Manag. 2020, 58, 102397. [Google Scholar] [CrossRef]
- Ayed, A.B.; Belhajji, M.A. The blockchain technology: Applications and threats. In Securing the Internet of Things: Concepts, Methodologies, Tools, and Applications; IGI Global: Hershey, PA, USA, 2020; pp. 1770–1781. [Google Scholar]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Futur. Gener. Comput. Syst. 2017, 107, 841–853. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.-N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Xiao, S.; Wang, X.A.; Wang, W.; Wang, H. Survey on blockchain-based electronic voting. In Proceedings of the International Conference on Intelligent Networking and Collaborative Systems, Victoria, BC, Canada, 31 August–2 September 2019; Springer: Berlin/Heidelberg, Germany; pp. 559–567. [Google Scholar]
- Košt’ál, K.; Bencel, R.; Ries, M.; Kotuliak, I. Blockchain e-voting done right: Privacy and transparency with public blockchain. In Proceedings of the 2019 IEEE 10th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 18–20 October 2019; pp. 592–595. [Google Scholar]
- Shanmugasundaram, G.; Kalaimathy, A.; Johnvee, M.; Pavithra, S. Perspective Analysis of Digital Voting Systems. In Proceedings of the 2019 IEEE International Conference on System, Computation, Automation and Networking (ICSCAN), Pondicherry, India, 29–30 March 2019; pp. 1–6. [Google Scholar]
- Willemson, J. Bits or paper: Which should get to carry your vote? J. Inf. Secur. Appl. 2018, 38, 124–131. [Google Scholar] [CrossRef]
- Poddar, V.; Mondal, S.; Dutta, N.; Dey, H. Incorporating Advancements In Voting Strategies: A Survey. In Proceedings of the 2018 9th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 8–10 November 2018; pp. 249–254. [Google Scholar]
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering; Keele University: Keele, UK, 2007. [Google Scholar]
- Wohlin, C. Guidelines for snowballing in systematic literature studies and a replication in software engineering. In Proceedings of the 18th International Conference on Evaluation and Assessment in Software Engineering, London, UK, 13–14 May 2014; pp. 1–10. [Google Scholar]
- Cruz-Benito, J. Systematic Literature Review & Mapping; University of Salamanca: Salamanca, Spain, 2016. [Google Scholar]
- Abuidris, Y.; Kumar, R.; Yang, T.; Onginjo, J. Secure large-scale E-voting system based on blockchain contract using a hybrid consensus model combined with sharding. ETRI J. 2020, 43, 357–370. [Google Scholar] [CrossRef]
- Kamil, M.; Bist, A.S.; Rahardja, U.; Santoso, N.P.L.; Iqbal, M. COVID-19: Implementation e-voting blockchain concept. Int. J. Artif. Intell. Res. 2021, 5, 25–34. [Google Scholar] [CrossRef]
- Rathee, G.; Iqbal, R.; Waqar, O.; Bashir, A.K. On the design and implementation of a blockchain enabled e-voting application within iot-oriented smart cities. IEEE Access 2021, 9, 34165–34176. [Google Scholar] [CrossRef]
- Khan, K.M.; Arshad, J.; Khan, M.M. Empirical analysis of transaction malleability within blockchain-based e-Voting. Comput. Secur. 2020, 100, 102081. [Google Scholar] [CrossRef]
- MohanaPriya, D.; Devadharshini, G.; Divya, S.; Rajalatchumy, J. Towards A Privacy-Preserving Voting System through Blockchain Technologies. In Proceedings of the 2021 International Conference on System Computation Automation and Networking (ICSCAN), Puducherry, India, 30–31 July 2021; pp. 1–6. [Google Scholar]
- Dimitriou, T. Efficient, Coercion-free and Universally Verifiable Blockchain-based Voting. Comput. Netw. 2020, 174, 107234. [Google Scholar] [CrossRef]
- Daramola, O.; Thebus, D. Architecture-centric evaluation of blockchain-based smart contract e-voting for national elections. Informatics 2020, 7, 16. [Google Scholar] [CrossRef]
- Krishnamurthy, R.; Rathee, G.; Jaglan, N. An enhanced security mechanism through blockchain for E-polling/counting process using IoT devices. Wirel. Netw. 2019, 26, 2391–2402. [Google Scholar] [CrossRef]
- Shao, W.; Jia, C.; Xu, Y.; Qiu, K.; Gao, Y.; He, Y. Attrichain: Decentralized traceable anonymous identities in privacy-preserving permissioned blockchain. Comput. Secur. 2020, 99, 102069. [Google Scholar] [CrossRef]
- Yang, X.; Yi, X.; Nepal, S.; Kelarev, A.; Han, F. Blockchain voting: Publicly verifiable online voting protocol without trusted tallying authorities. Futur. Gener. Comput. Syst. 2020, 112, 859–874. [Google Scholar] [CrossRef]
- Li, Y.; Susilo, W.; Yang, G.; Yu, Y.; Liu, D.; Du, X.; Guizani, M. A Blockchain-Based Self-Tallying Voting Protocol in Decentralized IoT. IEEE Trans. Dependable Secur. Comput. 2020, 19, 119–130. [Google Scholar] [CrossRef]
- Zaghloul, E.; Li, T.; Ren, J. Anonymous and coercion-resistant distributed electronic voting. In Proceedings of the 2020 International Conference on Computing, Networking and Communications (ICNC), Big Island, HI, USA, 17–20 February 2020; pp. 389–393. [Google Scholar]
- Priya, K.L.S.; Rupa, C. Block chain technology based electoral franchise. In Proceedings of the 2020 2nd International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bangalore, India, 5–7 March 2020; pp. 1–5. [Google Scholar]
- Mukherjee, P.P.; Boshra, A.A.; Ashraf, M.M.; Biswas, M. A hyper-ledger fabric framework as a service for improved quality e-voting system. In Proceedings of the 2020 IEEE Region 10 Symposium (TENSYMP), Dhaka, Bangladesh, 5–7 June 2020; pp. 394–397. [Google Scholar]
- Vivek, S.; Yashank, R.; Prashanth, Y.; Yashas, N.; Namratha, M. E-Voting System using Hyperledger Sawtooth. In Proceedings of the 2020 International Conference on Advances in Computing, Communication & Materials (ICACCM), Dehradun, India, 21–22 August 2020; pp. 29–35. [Google Scholar]
- Roopak, T.; Sumathi, R. Electronic voting based on virtual id of aadhar using blockchain technology. In Proceedings of the 2020 2nd International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bangalore, India, 5–7 March 2020; pp. 71–75. [Google Scholar]
- Alvi, S.T.; Uddin, M.N.; Islam, L. Digital voting: A blockchain-based e-voting system using biohash and smart contract. In Proceedings of the 2020 Third International Conference on Smart Systems and Inventive Technology (ICSSIT), Tirunelveli, India, 20–22 August 2020; pp. 228–233. [Google Scholar]
- Li, H.; Li, Y.; Yu, Y.; Wang, B.; Chen, K. A blockchain-based traceable self-tallying e-voting protocol in ai era. IEEE Trans. Netw. Sci. Eng. 2020, 8, 1019–1032. [Google Scholar] [CrossRef]
- Al-madani, A.M.; Gaikwad, A.T.; Mahale, V.; Ahmed, Z.A. Decentralized E-voting system based on Smart Contract by using Blockchain Technology. In Proceedings of the 2020 International Conference on Smart Innovations in Design, Environment, Management, Planning and Computing (ICSIDEMPC), Aurangabad, India, 30–31 October 2020; pp. 176–180. [Google Scholar]
- Xu, Z.; Cao, S. Efficient Privacy-Preserving Electronic Voting Scheme Based on Blockchain. In Proceedings of the 2020 IEEE International Conference on Smart Internet of Things (SmartIoT), Beijing, China, 14–16 August 2020; pp. 190–196. [Google Scholar]
- Killer, C.; Rodrigues, B.; Scheid, E.J.; Franco, M.; Eck, M.; Zaugg, N.; Scheitlin, A.; Stiller, B. Provotum: A blockchain-based and end-to-end verifiable remote electronic voting system. In Proceedings of the 2020 IEEE 45th Conference on Local Computer Networks (LCN), Sydney, Australia, 16–19 November 2020; pp. 172–183. [Google Scholar]
- Panja, S.; Bag, S.; Hao, F.; Roy, B. A Smart Contract System for Decentralized Borda Count Voting. IEEE Trans. Eng. Manag. 2020, 67, 1323–1339. [Google Scholar] [CrossRef]
- Zhou, Y.; Liu, Y.; Jiang, C.; Wang, S. An improved FOO voting scheme using blockchain. Int. J. Inf. Secur. 2019, 19, 303–310. [Google Scholar] [CrossRef]
- Chaisawat, S.; Vorakulpipat, C. Fault-tolerant architecture design for blockchain-based electronics voting system. In Proceedings of the 2020 17th International Joint Conference on Computer Science and Software Engineering (JCSSE), Chiangmai, Thailand, 6–8 May 2020; pp. 116–121. [Google Scholar]
- Xiao, S.; Wang, X.A.; Wang, H. Large-scale electronic voting based on conflux consensus mechanism. In Proceedings of the International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Lodz, Poland, 1–3 July 2019; Springer: Berlin/Heidelberg, Germany; pp. 291–299. [Google Scholar]
- Bosri, R.; Uzzal, A.R.; Al Omar, A.; Hasan, A.T.; Bhuiyan, M.Z.A. Towards a Privacy-Preserving Voting System Through Blockchain Technologies. In Proceedings of the 2019 IEEE International Symposium on Dependable, Autonomic and Secure Computing (DASC), Fukuoka, Japan, 5–8 August 2019; pp. 602–608. [Google Scholar]
- Bistarelli, S.; Mercanti, I.; Santancini, P.; Santini, F. End-to-End Voting with Non-Permissioned and Permissioned Ledgers. J. Grid Comput. 2019, 17, 97–118. [Google Scholar] [CrossRef]
- Gao, S.; Zheng, D.; Guo, R.; Jing, C.; Hu, C. An Anti-Quantum E-Voting Protocol in Blockchain With Audit Function. IEEE Access 2019, 7, 115304–115316. [Google Scholar] [CrossRef]
- Zhang, S.; Wang, L.; Xiong, H. Chaintegrity: Blockchain-enabled large-scale e-voting system with robustness and universal verifiability. Int. J. Inf. Secur. 2019, 19, 323–341. [Google Scholar] [CrossRef]
- Almeida, R.L.; Ricci, L.; Camarinha-Matos, L.M. Votechain: Community based scalable internet voting framework. In Proceedings of the Doctoral Conference on Computing, Electrical and Industrial Systems, Costa de Caparica, Portugal, 8–10 May 2019; Springer: Berlin/Heidelberg, Germany; pp. 70–80. [Google Scholar]
- Lyu, J.; Jiang, Z.L.; Wang, X.; Nong, Z.; Au, M.H.; Fang, J. A secure decentralized trustless E-voting system based on smart contract. In Proceedings of the 2019 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Rotorua, New Zealand, 5–8 August 2019; pp. 570–577. [Google Scholar]
- Vo-Cao-Thuy, L.; Cao-Minh, K.; Dang-Le-Bao, C.; Nguyen, T.A. Votereum: An ethereum-based e-voting system. In Proceedings of the 2019 IEEE-RIVF International Conference on Computing and Communication Technologies (RIVF), Danang, Vietnam, 20–22 March 2019; pp. 1–6. [Google Scholar]
- Li, P.; Lai, J. LaT-Voting: Traceable anonymous E-voting on blockchain. In Proceedings of the International Conference on Network and System Security, Sapporo, Japan, 15–18 December 2019; Springer: Berlin/Heidelberg, Germany; pp. 234–254. [Google Scholar]
- Sun, X.; Wang, Q.; Kulicki, P.; Sopek, M. A Simple Voting Protocol on Quantum Blockchain. Int. J. Theor. Phys. 2019, 58, 275–281. [Google Scholar] [CrossRef]
- Faour, N. Transparent E-Voting dApp Based on Waves Blockchain and RIDE Language. In Proceedings of the 2019 XVI International Symposium “Problems of Redundancy in Information and Control Systems” (REDUNDANCY), Moscow, Russia, 21–25 October 2019; pp. 219–223. [Google Scholar]
- Seftyanto, D.; Amiruddin, A.; Hakim, A.R. Design of Blockchain-based electronic election system using Hyperledger: Case of Indonesia. In Proceedings of the 2019 4th International Conference on Information Technology, Information Systems and Electrical Engineering (ICITISEE), Yogyakarta, Indonesia, 20–21 November 2019; pp. 228–233. [Google Scholar]
- Chaieb, M.; Koscina, M.; Yousfi, S.; Lafourcade, P.; Robbana, R. Dabsters: A privacy preserving e-voting protocol for permissioned blockchain. In International Colloquium on Theoretical Aspects of Computing; Springer: Cham, Switzerland, 2019; pp. 292–312. [Google Scholar]
- Kirillov, D.; Korkhov, V.; Petrunin, V.; Makarov, M.; Khamitov, I.M.; Dostov, V. Implementation of an e-voting scheme using hyperledger fabric permissioned blockchain. In Proceedings of the International Conference on Computational Science and Its Applications, Cagliari, Italy, 1–9 July 2019; pp. 509–521. [Google Scholar]
- Bellini, E.; Ceravolo, P.; Bellini, A.; Damiani, E. Designing process-centric blockchain-based architectures: A case study in e-voting as a service. In Data-Driven Process Discovery and Analysis; Springer: Berlin/Heidelberg, Germany, 2018; pp. 1–23. [Google Scholar]
- Chandra Priya, J.; Sathia Bhama, P.R.; Swarnalaxmi, S.; Aisathul Safa, A.; Elakkiya, I. Blockchain centered homomorphic encryption: A secure solution for E-balloting. In Proceedings of the International Conference on Computer Networks, Big data and IoT, Madurai, India, 19–20 December 2018; pp. 811–819. [Google Scholar]
- Zhang, W.; Yuan, Y.; Hu, Y.; Huang, S.; Cao, S.; Chopra, A.; Huang, S. A privacy-preserving voting protocol on blockchain. In Proceedings of the 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 2–7 July 2018; pp. 401–408. [Google Scholar]
- Bartolucci, S.; Bernat, P.; Joseph, D. SHARVOT: Secret SHARe-based VOTing on the blockchain. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May–3 June 2018; pp. 30–34. [Google Scholar]
- Perez, A.J.; Ceesay, E.N. Improving end-to-end verifiable voting systems with blockchain technologies. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1108–1115. [Google Scholar]
- Singh, A.; Chatterjee, K. SecEVS: Secure Electronic Voting System Using Blockchain Technology. In Proceedings of the 2018 International Conference on Computing, Power and Communication Technologies (GUCON), Greater Noida, India, 28–29 September 2018; pp. 863–867. [Google Scholar]
- Srivastava, G.; Dwivedi, A.D.; Singh, R. PHANTOM protocol as the new crypto-democracy. In Proceedings of the IFIP International Conference on Computer Information Systems and Industrial Management, Bialystok, Poland, 16–18 June 2018; pp. 499–509. [Google Scholar]
- Hjálmarsson, F.Þ.; Hreiðarsson, G.K.; Hamdaqa, M.; Hjálmtýsson, G. Blockchain-based e-voting system. In Proceedings of the 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 2–7 July 2018; pp. 983–986. [Google Scholar]
- Hardwick, F.S.; Gioulis, A.; Akram, R.N.; Markantonakis, K. E-Voting with blockchain: An E-Voting protocol with decentralisation and voter privacy. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1561–1567. [Google Scholar]
- Fusco, F.; Lunesu, M.I.; Pani, F.E.; Pinna, A. Crypto-voting, a Blockchain based e-Voting System. In Proceedings of the 10th International Joint Conference on Knowledge Discovery, Knowledge Engineering and Knowledge Management (KMIS), Seville, Spain, 18–20 September 2018; pp. 223–227. [Google Scholar]
- Yavuz, E.; Koç, A.K.; Çabuk, U.C.; Dalkılıç, G. Towards secure e-voting using ethereum blockchain. In Proceedings of the 2018 6th International Symposium on Digital Forensic and Security (ISDFS), Antalya, Turkey, 22–25 March 2018; pp. 1–7. [Google Scholar]
- Curran, K. E-Voting on the Blockchain. J. Br. Blockchain Assoc. 2018, 1, 4451. [Google Scholar] [CrossRef]
- Patil, H.V.; Rathi, K.G.; Tribhuwan, M.V. A study on decentralized e-voting system using blockchain technology. Int. Res. J. Eng. Technol. 2018, 5, 48–53. [Google Scholar]
- Panja, S.; Roy, B.K. A secure end-to-end verifiable e-voting system using zero knowledge based blockchain. Cryptol. Eprint Arch. 2018. Available online: https://eprint.iacr.org/2018/466.pdf (accessed on 18 January 2022).
- Pawlak, M.; Guziur, J.; Poniszewska-Marańda, A. Voting process with blockchain technology: Auditable blockchain voting system. In Proceedings of the International Conference on Intelligent Networking and Collaborative Systems, Victoria, BC, Canada, 31 August–2 September 2018; pp. 233–244. [Google Scholar]
- Khan, K.M.; Arshad, J.; Khan, M.M. Secure digital voting system based on blockchain technology. Int. J. Electron. Gov. Res. 2018, 14, 53–62. [Google Scholar] [CrossRef]
- Khoury, D.; Kfoury, E.F.; Kassem, A.; Harb, H. Decentralized voting platform based on ethereum blockchain. In Proceedings of the 2018 IEEE International Multidisciplinary Conference on Engineering Technology (IMCET), Beirut, Lebanon, 14–15 November 2018; pp. 1–6. [Google Scholar]
- Hanifatunnisa, R.; Rahardjo, B. Blockchain based e-voting recording system design. In Proceedings of the 2017 11th International Conference on Telecommunication Systems Services and Applications (TSSA), Lombok, Indonesia, 26–27 October 2017; pp. 1–6. [Google Scholar]
- Hsiao, J.-H.; Tso, R.; Chen, C.-M.; Wu, M.-E. Decentralized E-voting systems based on the blockchain technology. In Advances in Computer Science and Ubiquitous Computing; Springer: Berlin/Heidelberg, Germany, 2017; pp. 305–309. [Google Scholar]
- Liu, Y.; Wang, Q. An e-voting protocol based on blockchain. Cryptol. Eprint Arch. 2017. Available online: https://eprint.iacr.org/2017/1043.pdf (accessed on 8 February 2022).
- Tarasov, P.; Tewari, H. The Future of E-Voting. IADIS Int. J. Comput. Sci. Inf. Syst. 2017, 12, 148–165. [Google Scholar]
- Ayed, A.B. A conceptual secure blockchain-based electronic voting system. Int. J. Netw. Secur. Its Appl. 2017, 9, 1–9. [Google Scholar]
- McCorry, P.; Shahandashti, S.F.; Hao, F. A smart contract for boardroom voting with maximum voter privacy. In Proceedings of the International Conference on Financial Cryptography and Data Security, Sliema, Malta, 3–7 April 2017; Springer: Berlin/Heidelberg, Germany; pp. 357–375. [Google Scholar]
- Al-Maaitah, S.; Qatawneh, M.; Quzmar, A. E-Voting System Based on Blockchain Technology: A Survey. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Guangzhou, China, 22–25 December 2021; pp. 200–205. [Google Scholar]
- Denis González, C.; Frias Mena, D.; Massó Muñoz, A.; Rojas, O.; Sosa-Gómez, G. Electronic Voting System Using an Enterprise Blockchain. Appl. Sci. 2022, 12, 531. [Google Scholar] [CrossRef]
- Kaur, M.; Khan, M.Z.; Gupta, S.; Noorwali, A.; Chakraborty, C.; Pani, S.K. Mbcp: Performance analysis of large scale mainstream blockchain consensus protocol. IEEE Access 2021, 9, 80931–80944. [Google Scholar] [CrossRef]
- Fan, X.; Chai, Q. Roll-DPoS: A randomized delegated proof of stake scheme for scalable blockchain-based internet of things systems. In Proceedings of the 15th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, New York, NY, USA, 5–7 November 2018; pp. 482–484. [Google Scholar]
- Zhang, K.; Jacobsen, H.-A. Towards Dependable, Scalable, and Pervasive Distributed Ledgers with Blockchains; Technical Report; University of Toronto: Toronto, CA, Canada, 2018. [Google Scholar]
- Boyen, X.; Carr, C.; Haines, T. Graphchain: A blockchain-free scalable decentralised ledger. In Proceedings of the 2nd ACM Workshop on Blockchains, Cryptocurrencies, and Contracts, Incheon, Korea, 4 June 2018; pp. 21–33. [Google Scholar]
- Kokoris-Kogias, E.; Jovanovic, P.; Gasser, L.; Gailly, N.; Syta, E.; Ford, B. Omniledger: A secure, scale-out, decentralized ledger via sharding. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), Francisco, CA, USA, 21–23 May 2018; pp. 583–598. [Google Scholar]
- Ibrahim, M.; Ravindran, K.; Lee, H.; Farooqui, O.; Mahmoud, Q.H. Electionblock: An electronic voting system using blockchain and fingerprint authentication. In Proceedings of the 2021 IEEE 18th International Conference on Software Architecture Companion (ICSA-C), Stuttgart, Germany, 22–26 March 2021; pp. 123–129. [Google Scholar]
- Khlaponin, Y.; Vyshniakov, V.; Ternavska, V.; Selyukov, O.; Komarnytskyi, O. Development of audit and data protection principles in electronic voting systems. Eastern-Eur. J. Enterp. Technol. 2021, 4, 112. [Google Scholar]
- Gao, N.; Huo, R.; Wang, S.; Huang, T.; Liu, Y. Sharding-Hashgraph: A High-Performance Blockchain-Based Framework for Industrial Internet of Things with Hashgraph Mechanism. IEEE Internet Things J. 2021, 9, 17070–17079. [Google Scholar] [CrossRef]
- Wang, G.; Shi, Z.J.; Nixon, M.; Han, S. Sok: Sharding on blockchain. In Proceedings of the 1st ACM Conference on Advances in Financial Technologies, Zurich, Switzerland, 21–23 October 2019; pp. 41–61. [Google Scholar]
- Wu, S.; Galindo, D. Evaluation and Improvement of Two Blockchain Based E-Voting System: Agora and Proof of Vote; Galindo, D., Ed.; University of Birmingham: Birmingham, UK, 2018; Available online: http://www.dgalindo.es/mscprojects/shuang.pdf (accessed on 15 February 2022).
- Agbesi, S.; Asante, G. Electronic voting recording system based on blockchain technology. In Proceedings of the 2019 12th CMI Conference on Cybersecurity and Privacy (CMI), Copenhagen, Denmark, 28–29 November 2019; pp. 1–8. [Google Scholar]
- Utakaeva, I.K. Directions and features of application of the blockchain technology. J. Phys. Conf. Ser. 2019, 1353, 012103. [Google Scholar] [CrossRef]
- Heiberg, S.; Kubjas, I.; Siim, J.; Willemson, J. On trade-offs of applying block chains for electronic voting bulletin boards. Cryptol. Eprint Arch. 2018. Available online: https://eprint.iacr.org/2018/685.pdf (accessed on 13 March 2022).






| Requirements | Description |
|---|---|
| Anonymity | A vote should not be associated with a voter. |
| Auditability and accuracy | Voting processes should be able to be checked, audited, and certifiable by autonomous agents. |
| Democracy/singularity | Every voter should be allowed to vote only once. |
| Vote privacy | There is no way to prove the voter by his/her casted vote. |
| Robustness and integrity | It should be impossible to change or eliminate votes after they have been cast. |
| Voter verifiability | Everyone should be able to independently confirm that all the votes have been tallied accurately. |
| Verifiable participation/authenticity | Only those voters who have the right to cast a vote are verified by the system. |
| Transparency and fairness | Voting systems should be transparent and rely on the accuracy, precision, and protection of voter security. |
| Availability and mobility | Voting systems should be permanently accessible during the election period. Voting systems should not restrict the voting location. |
| Accessibility and reassurance | Voting systems should be available for people with disabilities or special conditions without requiring specific equipment or abilities. |
| Recoverability and identification | Electoral systems can detect flaws, defects, and attacks and restore voting data to their previous state. |
| ID | Question | Description |
|---|---|---|
| RQ1 | What are some of the most well-known proposals for scalable Blockchain-based electronic voting? | This topic highlights the most widely used Blockchain implementations utilized as the foundation for electronic voting systems. It enables the comparison and contrasting of several Blockchain and their attributes. |
| RQ2 | Were those solutions tested in a real-world scenario? | It might be possible to improve upon existing solutions by looking at how they were implemented in the actual world. |
| RQ3 | What are the verification methods used to test those solutions? | This question tries to find out how a solution was tested against the specifications of an electronic voting system. |
| RQ4 | What are the different cryptographic solutions employed in previous research? | Many cryptographic primitives and procedures are used in today’s electronic voting systems. The primary objective of this investigation is to locate them so that information about them may be incorporated into other potential solutions. |
| RQ5 | Were the cryptographic operations used in prior solutions too costly and time-consuming? | In the current scenario, cryptosystems are using too much power to solve the puzzle. Analysis of those solutions that claim to reduce the computational cost. |
| RQ6 | What are the latest Blockchain applications focused on scalability? | Blockchain applications are no longer limited to Bitcoin. Understanding the real influence of Blockchain technology on scalability will need an examination of the most recent practical uses. |
| RQ7 | What parameters test the performance and scalability of the electoral process on a large scale? | This question aims to test the current scalable Blockchain solutions on a large scale to check the performance of these solutions on a national-based electronic voting system. |
| RQ8 | What are the prior approaches for Blockchain scalability to efficiently enhance the electoral process on a large scale? | This question aims to highlight the previous scalable solutions, approaches, and future directions on a national level. |
| Sr. | Query Strings |
|---|---|
| 1. | (“blockchain” OR “block-chain” OR “distributed ledger”) AND “voting” |
| 2. | (“blockchain” OR “block-chain” OR “distributed ledger”) AND (“evoting” OR “electronic voting” OR “Internet voting” OR “Ivoting”) AND “voting system” |
| 3. | (“blockchain” OR “block-chain” OR “distributed ledger”) AND (“evoting” OR “electronic voting” OR “Internet voting” OR “Ivoting”) AND (“scalability” OR “scalable”) AND “large-scale” |
| 4. | (“blockchain” OR “block-chain” OR “distributed ledger”) AND (“evoting” OR “electronic voting” OR “Internet voting” OR “Ivoting”) AND (“scalability” OR “scalable”) AND (“scalable” OR “scalability”) AND “national level” |
| 5. | (Blockchain OR block-chain OR distributed ledger) AND (large-scale OR national level) AND (voting) AND (scalable OR scalability) AND (lightweight) |
| ID | Inclusion Criteria (IC) |
|---|---|
| IC1 | Complete studies of at least five pages are required for this survey. It must be a peer-reviewed work that has been published in conference proceedings or journals. |
| IC2 | Included studies must be published in the last five years (01.01.2017–31.03.2022). |
| IC3 | Studies respond to a research question or propose a suitable solution about scalability in electronic voting. |
| IC4 | Research examining the scalability of electronic voting systems based on Blockchain technology. |
| IC5 | Empirical data relating to the application and Blockchain studies that address scalable Blockchain-based electronic voting must be included in the study. |
| ID | Exclusion Criteria (EC) |
|---|---|
| EC1 | Those studies that are not written in English. |
| EC2 | Studies that were published before (01.01.2017) and after (31.03.2022). |
| EC3 | Studies that are irrelevant to the study since they do not address research questions. |
| EC4 | Grey literature should not be included. |
| EC5 | Duplicated studies. |
| EC6 | Papers more than five years old. |
| Field | Description |
|---|---|
| ID | Individual study identifier. |
| Authors | List of the authors. |
| Year | Year of the journal. |
| Title | Title of the journal. |
| Source | IEEE Digital Library, Springer Link, Scopus, ACM Digital Library, and Science Direct |
| Type | Journal and conference papers only. |
| Research Question 1 | What are some of the most well-known proposals for scalable Blockchain-based electronic voting? |
| Research Question 2 | Were those solutions tested in a real-world scenario? |
| Research Question 3 | What are the verification methods used to test those solutions? |
| Research Question 4 | What are the different cryptographic solutions employed in previous research? |
| Research Question 5 | Were the cryptographic operations used in prior solutions too costly and time-consuming? |
| Research Question 6 | What are the latest Blockchain applications focused on scalability? |
| Research Question 7 | What parameters test the performance and scalability of the electoral process on a large scale? |
| Research Question 8 | What are the prior approaches for Blockchain scalability to efficiently enhance the electoral process on a large scale? |
| ID | Quality Assessment Criteria (QAC) |
|---|---|
| QAC1 | Does the research contribute to the field of Blockchain-based electronic voting that can be scaled up? |
| QAC2 | Are the methods described in these papers being utilized in practice today? |
| QAC3 | Are practitioners going to benefit from this article? |
| QAC4 | Are the limitations of the proposed method presented and examined? |
| QAC5 | Are the findings of the research being addressed in any way? |
| QAC6 | Is there a suitable explanation provided for the background of the study? |
| QAC7 | Is the context of the study sufficiently explained? |
| QAC8 | Does the research include presentations of the related works? |
| QAC9 | Are the study’s objectives and scope adequately stated? |
| ID | Article Title | Research Method | Research Result | Research Gap | Ref. |
|---|---|---|---|---|---|
| 1 | Secure large-scale E-voting system based on Blockchain contract using a hybrid consensus model combined with sharding | Simulation: Proposed PSC-Bchain hybrid consensus | Security, performance, and scalability of Blockchain-based e-voting systems | Coercion resistance and receipt freeness | [123] |
| 2 | COVID-19: Implementation e-voting Blockchain Concept | Quantitative: SUS trial analysis | Tackles election during COVID-19, brings effectiveness and efficiency | Authentication, refining the process of Blockchain for e-voting | [124] |
| 3 | On the Design and Implementation of a Blockchain Enabled E-Voting Application Within IoT-Oriented Smart Cities | Simulation: Designed a new system model for e-voting application | Privacy, trust, and security | Real-time data | [125] |
| 4 | Empirical analysis of transaction malleability within Blockchain-based e-Voting | Experimental: Process model diagram for transaction malleability | Network delay and block generation rate | Needs to develop new mechanisms and methods to mitigate malleability attack | [126] |
| 5 | Towards A Privacy-Preserving Voting System Through Blockchain Technologies | Experimental: Proposed algorithm for privacy-preserving voting | Political race control, control hacking of electronic democratic machine, cost-productive | Adaptability, coercion resistance, and scalability | [127] |
| 6 | Efficient, Coercion-free and Universally Verifiable Blockchain-based Voting | Experimental: Proposed algorithm with zkSNARK | Coercion resistance, receipt freeness, and universal verifiability | Trustworthy election authorities | [128] |
| 7 | Architecture-Centric Evaluation of Blockchain-Based Smart Contract E-Voting for National Elections | Architecture trade-off analysis method (ATAM) | Security attacks, internal vote manipulation, and endorsed transparency | Lack of security and consensus protocol | [129] |
| 8 | An enhanced security mechanism through Blockchain for E-polling/counting process using IoT devices | Simulation: Proposed e-voting layout with IoT devices | Enhanced security via Blockchain in e-voting applications using IoT devices | Insufficient evidence to handle malicious IoT devices | [130] |
| 9 | AttriChain Decentralized traceable anonymous identities in privacy-preserving permissioned Blockchain | Simulation: Proposed AttriChain protocol for security in permissioned Blockchain | Increases user privacy and autonomy in a permissioned network and enables auditing | Inability to deal with financial scenarios, public Blockchains are not supported | [131] |
| 10 | Blockchain voting Publicly verifiable online voting protocol without trusted tallying authorities | Simulation: Proposed a novel encryption scheme | Voters can store, verify, and tally all submitted votes | Double encryption and zero-knowledge/partial-knowledge proofs are weaknesses | [132] |
| 11 | A Blockchain-based self-tallying voting protocol in decentralized IoT | Simulation: Proposed self-tallying voting protocol with IoT | Self-tallying technology encrypts votes for a specified duration to guarantee voting confidentiality | Yes/no voting does not work in boardrooms or classrooms | [133] |
| 12 | Anonymous and Coercion-Resistant Distributed Electronic Voting | Simulation: Proposed scheme resistant to double voting | Enhanced the integrity, efficiency, and voter turnout of the election process | Ignores security and privacy | [134] |
| 13 | Blockchain Technology based Electoral Franchise | Simulation: Proposed architecture BCT-based electronic franchise | Immutable and distributable to minimize voting system assaults | Needs trusted third-parties, data integrity, and verification | [135] |
| 14 | A hyper-ledger fabric framework as a service for improved quality e-voting system | Proposed framework as a service | A highly maintainable, large-scale, cost-effective solution for personalized private Blockchain | Private Blockchain compromised data integrity and privacy | [136] |
| 15 | E-Voting System using Hyperledger Sawtooth | Experimental: Using Sawtooth with Solidity language | Large-scale implementation, reliability, as well as security | Nontransparent; system may be flawed based on consensus | [137] |
| 16 | Electronic voting based on virtual id of aadhar using Blockchain technology | Proposed framework: virtual ID based on UIDAI | Secured e-voting system by using biometric details | Generating and analysing fingerprints is hard | [138] |
| 17 | Blockchain-Based Self-Tallying Voting System with Software Updates in Decentralized IoT | Simulation: It uses IoT. The algorithm’s efficiency and average runtime are examined | A self-tallying voting system with software updates in decentralized IoT | Inability to deal with user privacy and security | [39] |
| 18 | Digital Voting A Blockchain-based E-Voting System using Biohash and Smart Contracts | Simulation: Smart contract and bio hash | Data integrity and anonymity, privacy, security | Fingerprint authentication is expensive and inaccurate | [139] |
| 19 | A Blockchain-based Traceable Self-tallying E-voting Protocol in AI Era | Simulation: AI-based self-tallying e-voting scheme | Satisfies anonymity, time-bounded privacy, linkability, and full traceability | Absence to real-world applications on large scale | [140] |
| 20 | Decentralized E-voting system based on Smart Contract by using Blockchain Technology | Simulation: Ethereum with smart contract on local blockchain | Reliable, safe, flexible, and able to support real-time services | Latency throughput issues arise. Ethereum’s speed limits large-scale deployment. | [141] |
| 21 | Efficient, coercion-free and universally verifiable Blockchain-based voting | Simulation: Ethereum with smart contract with a focus to reduce the gas fee | Scalable and practical for large-scale elections | A trustworthy administrator registers voters and an aggregator compile results | [128] |
| 22 | TrustVote On Elections We Trust with Distributed Ledgers and Smart Contracts | Simulation: Ethereum with Hyperledger | Compares permissioned and public Blockchain for better performance, transaction speed, and privacy | Coercion-resistant, needs trusted authorities | [46] |
| 23 | Efficient Privacy-Preserving Electronic Voting Scheme Based on Blockchain | Simulation: Ethereum with multicandidate electronic voting scheme | Good performance and the feasibility and correctness of the voting scheme | Permissioned Blockchain requires trusted authorities, scalability issues on large scale | [142] |
| 24 | Provotum A Blockchain-based and End-to-end Verifiable Remote Electronic Voting System | Simulation: End-to-end verifiable remote private Blockchain scheme | Practical design and architecture of public bulletin boards, ballot secrecy, and end-to-end verifiability | Does not support multiway elections, lack of secure communication channels | [143] |
| 25 | Investigating performance constraints for Blockchain based secure e-voting system | Simulation: Permissioned and permissionless blockchain to measure performance | Efficiency, performance, and scalability | It does not explicitly state security aspects such as uniqueness and ballot reception | [1] |
| 26 | A Smart Contract System for Decentralized Borda Count Voting | Simulation: A decentralized, multicandidate, public-verifiable voting system. | Self-tallying decentralized and ranked-choice voting system | Large-scale voting is also impossible. No protocol considers voter privacy | [144] |
| 27 | Secure Online Voting System Using Biometric and Blockchain | Experimental: Using Biometric with sidechain | Tamper-proof storage, user authenticity, and data security | It cannot engage stakeholders on Blockchain quality or feasibility | [14] |
| 28 | An improved FOO voting scheme using Blockchain | Experimental: many-functional Blockchain-based FOO protocol | Fairness and correctness | Coercion-resistant | [145] |
| 29 | Fault-Tolerant Architecture Design for Blockchain-Based Electronics Voting System | Simulation: fault-tolerant e-voting systems | Data security, performance, measuring computing resources and agility | Weaknesses in anonymization, Internet security, and managing unforeseen events | [146] |
| 30 | Large-Scale Electronic Voting Based on Conflux Consensus Mechanism | Simulation: comparative Blockchain-based voting systems | Decentralized, self-managed, noninteractive, and free of charge | Inability to deal coercion-resistant privacy and security | [147] |
| 31 | Securing e-voting based on Blockchain in P2P network | Simulation: using Python with ECC public key cryptography | Avoids forgery of votes, authentication, nonrepudiation, and changing of vote before a preset deadline | The system’s PKI database may invalidate its vote block verification process | [24] |
| 32 | Towards A Privacy-Preserving Voting System Through Blockchain Technologies | Proposed: Cost-productive framework | Fairness, independence, and unbiasedness | The proposed system was not tested and implemented | [148] |
| 33 | End-to-End Voting with Non-Permissioned and Permissioned Ledgers | Simulation: E2E verifiable system using Bitcoin and MultiChain | Uncoercibility and receipt freeness and data confidentiality and neutrality | Not formally proven, needs to measure the qualitative properties | [149] |
| 34 | An Anti-Quantum E-Voting Protocol in Blockchain with Audit Function | Simulation: Niederreiter’s code-based cryptosystem | True fairness, audit voters, transparency, and efficiency in small-scale election | Largely appropriate for small-scale elections | [150] |
| 35 | Chaintegrity: Blockchain-enabled large-scale e-voting system with robustness and universal verifiability | Simulation: Impractical properties of Blockchain-based e-voting | Large-scale e-voting system | Uniqueness and ballot reception are not explicitly stated | [151] |
| 36 | voteChain: Community Based Scalable Internet Voting Framework | Proposal presented: Mixed approach to achieve require results | Scalable Internet voting | Multiple vote casting, possibility of attack | [152] |
| 37 | A Secure Decentralized Trustless E-Voting System Based on Smart Contract | Simulation: Privacy-preserving e-voting protocol | Decentralized, trustless electronic voting system based on the smart contract | Cannot scale, needs a lot of processing and communication power | [153] |
| 38 | Towards Blockchain-Based E-Voting Systems | Simulation: Efficiency- and scalability-based system | Cost-effective, lightweight, and efficient | The study did not specify the system’s needs | [34] |
| 39 | Votereum: An Ethereum-Based E-Voting System | Simulation: Robust, private, and verifiable system | Privacy, uniqueness, universal verifiability, and robustness | This mechanism cannot assure free receipt or withstand coercion | [154] |
| 40 | TrustedEVoting (TeV) a Secure, Anonymous and Verifiable Blockchain-Based e-Voting Framework | Conceptual design: Secure and verifiable e-voting system (TeV) | Nontampering, voter anonymity, and vote verifiability | TeV was not implemented or evaluated in a nationwide election | [29] |
| 41 | LaT-Voting: Traceable Anonymous E-Voting on Blockchain | Simulation: Traceability prefixes anonymous protocol | Authentication, privacy, and subtle traceability | No central authority to monitor | [155] |
| 42 | A Simple Voting Protocol on Quantum Blockchain | Simulation: Quantum Blockchain electronic | Anonymous, binding, nonreusable, verifiable, eligible, fair, and self-tallying | It lacks auditability consistency | [156] |
| 43 | Transparent E-Voting dApp Based on Waves Blockchain and RIDE Language | Simulation: Privacy and tally voting system | Substantially enhances performance | Waves votes dApps. Large-block, voter-controlled blockchains | [157] |
| 44 | Design of Blockchain-based electronic election system using Hyperledger: Case of Indonesia | Proposed design: Blockchain necessity, issue solution, and secure election needs | Security and performance | Security and performance were not tested on the design | [158] |
| 45 | DABSTERS: A Privacy Preserving e-Voting Protocol for Permissioned Blockchain | Formal Verification: Election privacy and transparency protocol | Voter privacy, integrity, and verifiability | ProVerif validated. Performance and implementation assessments are lacking | [159] |
| 46 | Privacy-protected Electronic Voting System Based on Blockchin and Trusted Execution Environment | Simulation: Cost-effective and efficient electronic voting | Economical, efficient, and privacy for board-scale elections | Needs more research on large-scale elections and the system | [26] |
| 47 | Implementation of an E-Voting Scheme Using Hyperledger Fabric Permissioned Blockchain | Simulation: Consortium blockchain with smart contracts | Increased transparency and trust | The system was developed for general e-voting, not stakeholder demands | [160] |
| 48 | Designing Process-Centric Blockchain-Based Architectures A Case Study in e-voting as a Service | Architecture Design: Blockchain-based e-voting with cloud | Process-centric, trusted, configurable and multipurpose electronic voting service | Security and privacy were not discussed and it was not implemented | [161] |
| 49 | Blockchain centered homomorphic encryption: A secure solution for E-balloting | Simulation: Blockchain voting through additive homomorphism | Prevention of multiple voting, privacy and end-to-end verifiability | Scalability and multicasting voting issues | [162] |
| 50 | A privacy-preserving voting protocol on Blockchain | Simulation: Homomorphic encryption counts smart-contract votes | End-to-end privacy, detectability, and correctability against cheating | The system is unfair and does not prevent malicious activity | [163] |
| 51 | SHARVOT: Secret SHARe-Based VOTing on the Blockchain | Proposed Solution: Used circle shuffle technique | Privacy, anonymity, ballot irrevocability, and transparency | Needs centralization. Authorities sabotage voting | [164] |
| 52 | Improving end-to-end verifiable voting systems with Blockchain technologies | Experimental: Helios has DDoS and data manipulation difficulties | End-to-end verifiability, data tampering, immutability, and public accessibility | This voting technique involves a “centralized database service” | [165] |
| 53 | SecEVS: Secure Electronic Voting System Using Blockchain Technology | Experimental: Secure electronic voting system using Blockchain technology | Transparency, decentralization, irreversibility, and nonrepudiation | This work is costly and time-consuming | [166] |
| 54 | A proposal of Blockchain-based electronic voting system | Experimental: double-envelope encryption and Blockchain | High availability and universal verifiability | E-voting privacy was not discussed | [7] |
| 55 | PHANTOM protocol as the new crypto-democracy | Mathematical Modelling: PHANTOM protocol with encription method | Vote rigging, hacking, election manipulation, and polling booth capturing | This protocol was not implemented or evaluated | [167] |
| 56 | Blockchain-based e-voting system | Experimental: Scheme uses a smart contract to tally the result | Security and decreased cost of hosting a nationwide election | Compromised security, privacy, and anonymity | [168] |
| 57 | E-Voting with Blockchain: An E-Voting Protocol with Decentralisation and Voter Privacy | Experimental: Proposed a decentralized voting scheme | Open, fair, and independently verifiable | It does not provide auditability, consistency, or privacy | [169] |
| 58 | Blockchain-Enabled E-Voting | Experimental: Smartphone-based electronic platform | Reduced voter fraud and increased voter access | It is more of an example of i-voting rather than e-voting | [38] |
| 59 | Crypto-voting, a Blockchain based e-Voting System | Experimental: Voting uses sidechains, holds voters and vote data | Traceability and auditability | Compromising on fairness | [170] |
| 60 | Towards secure e-voting using ethereum Blockchain | Experimental: Voting through Ethereum with Android application | Safer, cheaper, more secure, more transparent, and easier to use | The drawbacks are that it lacks robustness and receiving freedom | [171] |
| 61 | Towards the intelligent agents for Blockchain e-voting system | Conceptual model: Auditable Blockchain voting system multiagent concept | Transparency and auditability | Data and privacy insecurity via email voting | [53] |
| 62 | A Survey of Blockchain Based on E-voting Systems | Survey: It highlights current security and privacy vulnerabilities | Security and privacy requirements of the existing Blockchain e-voting systems | It lacks scalability, throughput, and latency | [53] |
| 63 | E-Voting on the Blockchain | Analysis: Blockchain voting is discussed | Reduced voter fraud and increased voter access | It is not entirely decentralized; utilizes Blockchain to store votes | [172] |
| 64 | A study on decentralized e-voting system using Blockchain technology | Proposed model: E-voting system with SHA voter data encryption | Vote rigging and hacking of the EVM | One chain per candidate adds storage and processing complexity | [173] |
| 65 | A secure end-to-end verifiable e-voting system using zero knowledge based Blockchain | Proposed scheme: DRE-ip with zero-knowledge-based public Blockchain | Authenticated, end-to-end verifiable, and with secret ballot election | Large computational costs make these technologies costly to use and deploy in DeFi. | [174] |
| 66 | Voting process with Blockchain technology: Auditable Blockchain voting system | Proposed scheme: supervised Internet voting system | Audit and verification capability | Lack of audits and system verification compromises transparency and tamper-proofness | [175] |
| 67 | Secure Digital Voting System Based on Blockchain Technology | Scheme: E-voting using jeopardizing cryptographic hashes | Increased efficiency and reduced errors | It allowed multiple votes to one user | [176] |
| 68 | Decentralized Voting Platform Based on Ethereum Blockchain | Experimental: Voting on multiple votes per mobile (MSISDN) | Ensuring data integrity, transparency, enforcement, and privacy | Absence of clarity and time consumption | [177] |
| 69 | Blockchain based e-voting recording system design | Simulation: Recording of voting result using Blockchain algorithm | Security, transparency, and reduced cheating sources of database manipulation | Lack of personal voter authentication | [178] |
| 70 | Decentralized E-Voting Systems Based on the Blockchain Technology | Scheme: Blockchain-based, secret sharing and homomorphic encryption | Anonymity, privacy, and verifiability | Missed quality targets | [179] |
| 71 | An e-voting protocol based on Blockchain | Scheme: Blockchain and blind signature | Satisfied coercion resistance and access control | The limits are coercion resistance, robustness, and fairness | [180] |
| 72 | The future of e-voting | Academic proposal: Zcash protocol with zero knowledge | Security and anonymity | A server challenge-response handshake to stores email, fake emails are simple | [181] |
| 73 | A conceptual secure Blockchain-based electronic voting system | Academic proposal: voting scheme using hash value | Secure, reliable, anonymous voting might improve local or national elections | Lack of authentication and privacy for users | [182] |
| 74 | A smart contract for boardroom voting with maximum voter privacy | Academic proposal: Comprehensive secure protocol using the Ethereum | An Internet voting system that is both decentralized and self-tallying while also protecting the privacy of voters | Their arithmetic-heavy technique requires a lot of computing power | [183] |
| 75 | E-Voting System Based on Blockchain Technology: A Survey | Analysis: Blockchain voting security and transparency | Less trust, privacy, and security | Absence of dialogue around scalability and anonymity | [184] |
| 76 | Blockchain for Electronic Voting System Review and Open Research Challenges | Analysis: Blockchain voting challenges and future research | Privacy protection, scalability, and transaction speed | Usage authentication not stated | [11] |
| Verification Method | Research Article |
|---|---|
| Examination of evaluation criteria | [175,184] |
| Scalability testing (nodes, transactions per second, response time) | [182,185] |
| Performance tests (blocks per hour, blocks per day, transaction latency, transaction throughput) | [123,176] |
| Security test/analysis (vulnerability towards specific types of attacks) | [125,181] |
| Cost evaluation | [127,171] |
| Cryptography | Cryptography Solution | Research Article |
|---|---|---|
| Symmetric Key | Advanced Encryption Standard (AES) | [127,134] |
| Asymmetric/Public Key | Homomorphic | [128,179] |
| RSA | [137,160] | |
| Elliptic Curve Cryptography (ECC) | [24,162] | |
| Elliptic Curve Digital Signature Algorithm (ECDSA) | [129,181] | |
| ElGamal | [132,162] | |
| DSA | [144] | |
| Hash Functions | SHA’s | [182,185] |
| Cryptography Solution | Articles | Cost | Time (Key Generation Time) |
|---|---|---|---|
| Advanced Encryption Standard (AES) | [127,134] | N/A | 1 KB file size encryption time: 128-bit key generation ~14,594 microsecond, 192-bit key generation ~14,432 microsecond, and 256-bit key generation ~16,222 microsecond. Relatively fast over all ~ 0.0023 s. |
| Homomorphic | [128,179] | N/A | Bits slower ~ 41 milliseconds. |
| RSA | [137,160] | 512-bit RSA keys—2 CPU hours (the cost of USD 0.06) 1024-bit RSA keys—97 CPU days (the cost of USD 40–80) 2048-bit RSA keys—140.8 CPU years, (the cost of USD 20,000–USD 40,000) | 1024-bit key generation ~0.16 s, 2240-bit key generation ~7.47 s, 3072-bit key generation ~9.80 s. Overall key generation time ~15 min, RSA bits slower. |
| Elliptic Curve Cryptography (ECC) | [24,162] | 160 bits ECC keys— (the cost of USD 0.02) 224 bits ECC keys— (the cost of USD 3333.33–6666.67) | 1024-bit key generation ~0.08 s, 2240-bit key generation ~0.18 s, 3072-bit key generation ~0.27 s. |
| Elliptic Curve Digital Signature Algorithm (ECDSA) | [129,181] | N/A | 163-bit key generation ~0.08 s, 233-bit key generation ~0.18 s, 283-bit key generation ~0.27 s, 409-bit key generation ~0.64 s, 571-bit key generation ~1.44 s, |
| ElGamal | [132,162] | N/A | 25 KB file size encryption time: ~1858.6 millisecond, 50 KB file size encryption time: ~2346.2 millisecond. |
| Digital Signature Algorithm (DSA) | [144] | N/A | 512-bit key generation ~19 millisecond, 1024-bit key generation ~82 millisecond. |
| SHA’s (SHA-2 to SHA 256) | [182,185] | N/A | 1.4 MB file size 0.04 s, 2.2 MB ~ 0.07 s, 3.3 MB ~0.13 s, 5.9 MB ~ 0.21 s and 6.9 MB ~ 0.24 s. |
| Scalability Scenario Classification | Research Articles |
|---|---|
| Small Scale or Organization Voting | [183,185] |
| National Voting | [123,167] |
| Generic Voting | [135,161] |
| Performance Parameter | Description | Articles |
|---|---|---|
| Block frequency | Interval time between two succeeding blocks | [140,178] |
| Block size | A block’s capacity to hold the number of transactions | [24,185] |
| Workload type | Smart contract | [141,165] |
| CPU Usage/Node configuration | CPU, network speed, RAM | [14,34,179] |
| Network size | The number of nodes | [181,186] |
| Network structure/Network usage | Network structure of the Blockchain | [125,182] |
| Workload quantity | Total transactions to be carried out | [1,165] |
| Amount of miners/sealers/Memory usage | Actively participating nodes | [14,164] |
| Blockchain client and API | E.g., Geth or Parity, web3.js or web3.py | [136,166] |
| Scalability Metric | Description | Articles |
|---|---|---|
| Throughput | Number of accomplished transactions per second (TPS) | [123,178] |
| Latency | The time difference in seconds between when a transaction is submitted and completed | [126,163] |
| Scalability | When a parameter is altered, there are changes in both throughput and latency (e.g., the network size or the hardware configuration of a node) | [147,177] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jafar, U.; Ab Aziz, M.J.; Shukur, Z.; Hussain, H.A. A Systematic Literature Review and Meta-Analysis on Scalable Blockchain-Based Electronic Voting Systems. Sensors 2022, 22, 7585. https://doi.org/10.3390/s22197585
Jafar U, Ab Aziz MJ, Shukur Z, Hussain HA. A Systematic Literature Review and Meta-Analysis on Scalable Blockchain-Based Electronic Voting Systems. Sensors. 2022; 22(19):7585. https://doi.org/10.3390/s22197585
Chicago/Turabian StyleJafar, Uzma, Mohd Juzaiddin Ab Aziz, Zarina Shukur, and Hafiz Adnan Hussain. 2022. "A Systematic Literature Review and Meta-Analysis on Scalable Blockchain-Based Electronic Voting Systems" Sensors 22, no. 19: 7585. https://doi.org/10.3390/s22197585
APA StyleJafar, U., Ab Aziz, M. J., Shukur, Z., & Hussain, H. A. (2022). A Systematic Literature Review and Meta-Analysis on Scalable Blockchain-Based Electronic Voting Systems. Sensors, 22(19), 7585. https://doi.org/10.3390/s22197585







