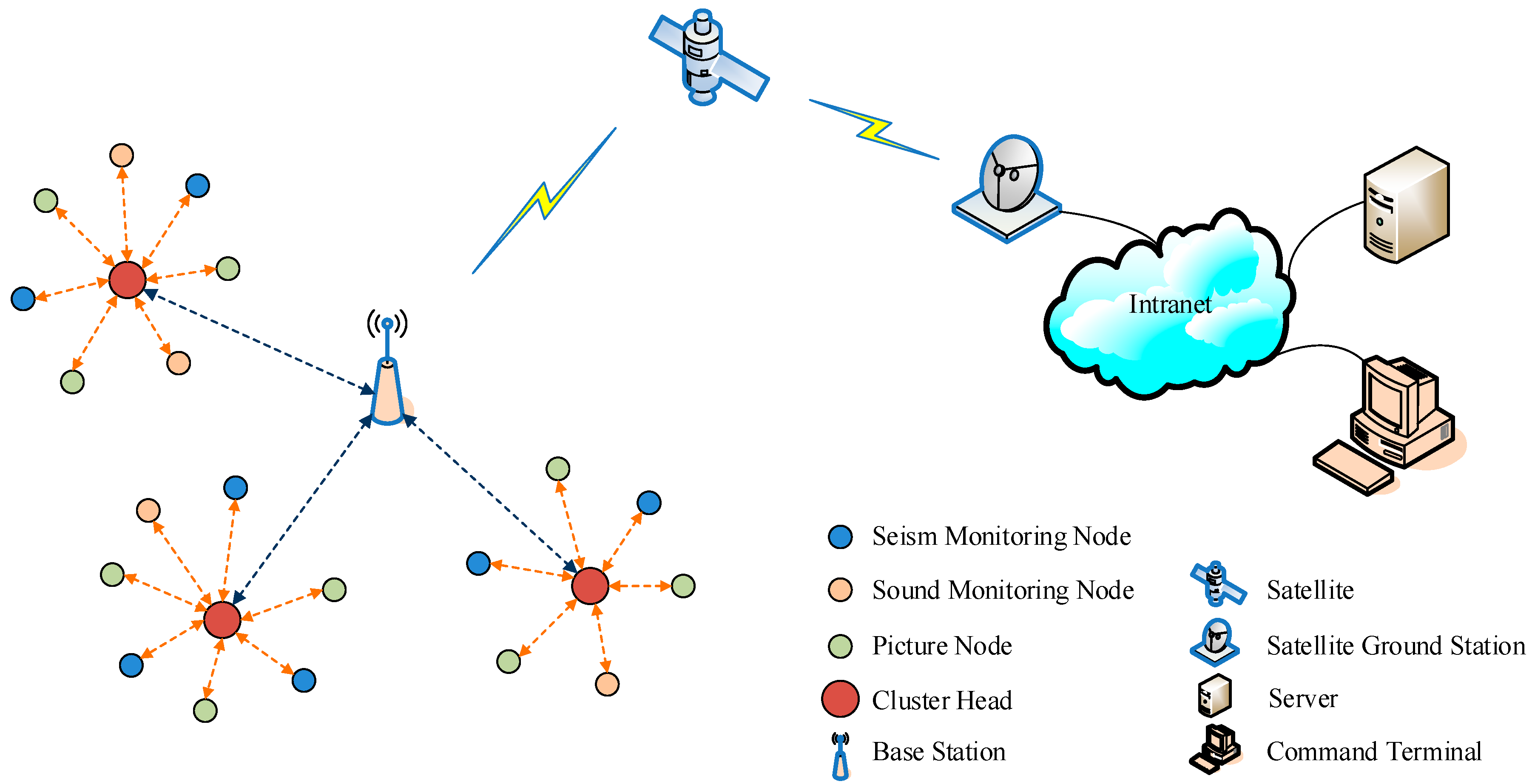
3. Collaborative Disaster-Monitoring System
Based on WSNs, earthquake information can be collected and delivered to seismic areas. With rapid advances in communication, embedded computing, and sensing techniques, various WSNs have been developed. WSNs can perform collaborative real-time monitoring, sensing, and gathering of data in various environments or surveillance objects. These data are processed to obtain accurate information that is finally delivered to the user. WSNs can obtain massive, detailed, and reliable physical world information at any time or place. However, for a disaster-monitoring system, the primary goal is to transmit alerts and superior information as quickly as possible, even when the network is under a heavy load. The limited computing power, communication ability, and battery energy of the heterogeneous nodes for wireless sensor networks must be considered.
A network topology diagram of the collaborative disaster-monitoring system is shown in
Figure 1. The system is a three-layered architecture of the Internet of Things. It consists of three parts: the wireless sensor networks as the perception layer, the satellite communication part as the communication layer, and the service center as the application layer. The wireless sensor network contains three types of sensor node: the seismic, picture, and sound nodes. Each node has two wireless communication interfaces. First, all sensor nodes are divided into clusters, and the node with the highest relative energy in a cluster is selected as the cluster head. Subsequently, in-cluster communication is performed using a hybrid superior node token ring scheme with one communication interface. Sensor nodes transmit data to the cluster head via a one-hop transmission. Communication between the cluster heads and the base station follows the TDMA mode with another communication interface. Seismic monitoring nodes gather seismic information using a seismometer. Picture-monitoring nodes capture pictures of a scene, and sound-monitoring nodes capture sound signals. These nodes then transmit information to the base station. Different types of nodes are equipped with batteries of different capacities. The base station contains a satellite transceiver and a battery rechargeable with solar energy. The satellite communication part is responsible for the long-distance transmission of information. It does not rely on the ground-based infrastructure. The base station delivers the collected information to the service center via satellites, satellite ground stations, and internal networks. The server of the service center can process all kinds of information both in time and effectively. Thus, based on the satellite link, disaster information can be obtained and processed even when the ground-based communication infrastructure in the earthquake zone is destroyed.
Seismic data can be treated as continuous variables in disaster-monitoring applications in WSNs. Continuous values are collected from spot observations; hence, each piece of data collected is important and indispensable. However, this may result in an excessive burden on the small nodes of the WSNs. Benefiting from advances in information technology, the method of compressed sensing for WSNs is effective for reducing this burden. Assuming that the distribution of data is sparse in a certain domain, this type of data collection with sensor nodes can be compressed using the compressed sensing method. In a collaborative disaster-monitoring system based on the compressed sensing method, seismic data can be obtained in an energy-efficient manner.
This system provides real-time and efficient ground vibration data, events, and alerts through satellite links. First, the seismic monitoring nodes perform compressive sampling of seismic variables and then deal with the compressive sampling data, alert them to network packets, and send them to the base station. The base station has a higher computing power and a larger solar energy supply than the sensor nodes. Therefore, at the base station, the system reconstructs seismic data and detects seismic events in accordance with our belief propagation fusion method [
45]. This system transmits earthquake data, events and alerts to the server through a satellite link. The task of the disaster-monitoring system is to maintain the surveillance of earthquake activities, and most importantly, transmit alerts for dangerous vibrations as quickly as possible. After earthquake alerts are received and broadcast by the system server, people around the earthquake epicenter can take prompt action to avoid and mitigate damage.
4. Scheme Description
In disaster-monitoring systems, the MAC protocol plays the most important role in terms of delay, throughput, and reliability. The distributed polling scheme is an important type of the MAC protocol. In WSNs, polling involves sending a wireless query to each node and waiting for a unique response from the addressed node. This method supports real-time and high-throughput applications, and can automatically adapt to changes in traffic. For a distributed polling scheme in WSNs, a particular token frame is assigned to allocate wireless resources, and this token is transmitted along a virtual logical ring. Although the distributed polling scheme requires nodes of a cluster to be within a one-hop range, it provides high real-time and abnormity-handling power. Abnormity handling guarantees that the failure of any node cannot invalidate the entire network using a distributed polling scheme. This can significantly improve the reliability of WSNs in disaster-monitoring systems.
The nodes of WSNs are divided into two types for disaster-monitoring applications. One type includes superior nodes, such as seismic monitoring nodes, which have superior data and alert data for transmission. The other type comprises ordinary nodes, such as picture-monitoring nodes, sound-monitoring nodes. Ordinary nodes have ordinary data to transmit. The operation of HT-MAC is divided into rounds, each of which consists of two stages: a set-up stage and a steady-state stage. To optimize energy consumption and maximize network lifetime, these two stages are performed alternately. At the beginning of one round, at the set-up stage, the nodes in this system are clustered according to their relative energy and location. Clustering can significantly improve the energy efficiency of the entire network. At the steady-state stage, the HT-MAC scheme is based on the distributed polling scheme. The timeline of HT-MAC at the steady-state stage is shown in
Figure 2.
In this study, the protocol stack of ordinary and superior nodes includes physical, data link, network, transport, and application layers. Cooperation between layers is very important. The physical layer is responsible for the digital coding, modulation, filtering, and spreading of the signal. The physical layer of the protocol stack utilizes the direct-sequence spread–spectrum technique. The HT-MAC protocol is power-aware and can adjust the transmission power to save energy. The network layer protocol adopts static routing technology, and the nodes in the cluster send information to the cluster head, and then the cluster head converges and forwards the information to the base station. The transport layer is responsible for maintaining the flow of the superior, alert, and ordinary data. Different types of sensing tasks can be built and used in the application layer.
The operating procedures of the HT-MAC scheme in normal and abnormal situations are as follows.
4.1. Set-Up Stage
Clustering algorithms are very important for the network lifetime and delay performance of WSNs. The pLEACH algorithm is applied to cluster hierarchical sensor networks [
46]. As previously mentioned, a collaborative disaster-monitoring system has a hierarchical architecture. The pLEACH algorithm is an adaptive clustering hierarchy algorithm with a high network lifetime and low communication delay. Based on centralized processing in the base station, the clustering algorithm first partitions the nodes into an optimal number of clusters and then selects the node with the highest energy in the cluster as the cluster head. In this study, we extend the pLEACH algorithm to heterogeneous sensor networks.
In heterogeneous sensor networks, the clustering method also pursues the maximum network lifetime; that is, the death of the first node is averaged in a round. Data aggregation and relays occur in the cluster head (CH); therefore, the cluster head nodes consume more energy than the other nodes. The rotation of the cluster head may balance the energy dissipation of the sensor nodes. The decision metric used to select the cluster heads is important. We define
Trwtch as the residual working time of the CH, as a cluster head, for the basis of cluster head selection:
where
Er is the residual energy of a sensor node,
Psc is the mean power of sensing and calculation for this type of sensor node, and
Par is the mean power of data aggregation and relay as a cluster head for a sensor node.
Trwtch indicates the persistent working time if a node is selected as a cluster head.
In this study, energy models similar to those proposed in [
39] were used. The energy consumption of radio transmission can be calculated as follows:
where
ETx(
l,
d) is the energy of
l-bit message transmission over distance
d,
Eelec is the energy consumption for digital coding, modulation, filtering, and spreading of the signal,
εfs is the energy consumption of short distance transmission, and
εmp is the energy consumption of long distance transmission. In addition,
d0 is the threshold of the distance and can be obtained when
d =
d0, in Equation (2):
For receiving an
l bit message, the radio expends
The proposed clustering algorithm is a centralized cluster head selection scheme. Only the base station is responsible for the cluster division of the entire network. Base stations generally have a continuous power supply, high storage and computing power, and global network information. Therefore, a complex algorithm can be used to obtain optimized clustering results. The proposed clustering algorithm comprises two phases.
In the first phase, each sensor node sends its location and current energy to a base station using the CSMA/CA approach. According to this information, the base station obtains the optimal number of clusters [
39]. Ordinary nodes are divided equally into sectors; thus, there are approximately equal numbers of ordinary nodes in each sector. Subsequently, all sensor nodes in a sector, including ordinary and superior nodes, form a cluster. The cluster head is selected from the ordinary nodes in a cluster. Therefore, the distance from any non-head node to the cluster head is less than the network radius, which reduces the overall communication energy consumption in the network.
In the second phase of the proposed clustering algorithm, the cluster head is selected. When the network is initialized, each sensor node sends a report message to the base station regarding its current energy and location. Based on these messages, the base station first calculates Trwtch, the residual working time, as a cluster head for each ordinary node. Subsequently, an ordinary node with the maximum Trwtch in a cluster is selected as the cluster head. Finally, the base station broadcasts information on the cluster heads and members of a cluster to all the sensor nodes. The information consists of the locations of the sensor nodes in a cluster; thus, the nodes can adjust their transmission power to fit the transmission distance within a cluster.
4.2. Steady-State Stage
In the steady-state stage, HT-MAC operates in the duty cycle mode. Each cluster has
M superior nodes and
N ordinary nodes, and one of the ordinary nodes is selected as the cluster head. The ordinary nodes in a cluster form a virtual ring, and the token runs in the ring. In one period, the ordinary node that owns the token first asks superior nodes if there are any data to transmit. If the superior nodes have data, they transmit the data sequentially from superior node 1 to superior node
M. That is, in one period, the ordinary node with the token polls all the superior nodes individually in the cluster. Then, this ordinary node sends its own data to the destination node, which only transmits data frames that have already arrived when the node starts transmitting. Subsequently, this ordinary node passes the token to the next ordinary node, and the cluster enters the sleeping state. Considering the relatively short active state of the sensor nodes, the sleeping time accounts for a large proportion of the period time. During the sleeping state, the alert data of the superior nodes are transmitted using a low-power listening and shortened preamble approach to satisfy the delay and energy requirements of the alert. The low-power listening and shortened preamble approach was based on the X-MAC protocol [
47]. The preamble sequence consists of many smaller shortened preambles with destination addresses. Using the time interval between the shortened preambles, the receiving node sends early acknowledgments to the source node. The sending node transmits the data packet immediately after receiving early confirmation to avoid excessive preambling of the sending node and overhearing of the receiving node, which reduces delays and energy consumption. A random back-off is performed to mitigate collisions between multiple sending nodes. Therefore, the alerts of superior nodes have a shorter communication delay, meeting the requirements of disaster-monitoring applications.
HT-MAC WSNs are composed of several clusters. To reduce the interference between adjacent clusters, each cluster in the HT-MAC scheme communicates based on a direct-sequence spread spectrum. Therefore, each cluster applies a unique spread code. In each cluster, the nodes deliver polling tokens individually, based on the virtual logical ring. In a virtual ring, a node’s predecessor is its previous node, and its successor is its next node. Consider a special situation in which there is only one node in the virtual ring: one node’s predecessor and successor.
For normal operation of the virtual ring, there are two basic procedures: a node may join or a node may leave a ring. First, a node joins a virtual ring. Each node in the virtual ring periodically transmits an invitation token that makes the node join the virtual ring. The procedure for joining a virtual ring is as follows. Node m in the ring first delivers an invitation token (m, n), where n denotes the successor node of node m. Node m invites a node to join between node m and n, using this invitation token. Upon receiving an invitation token, a node that intends to join the virtual ring checks whether it is within the coverage of the cluster. If confirmed, this node responds to the invitation of node m, and sets node m as the predecessor and node n as the successor. Node m sets this node as the successor, and node n sets this node as the predecessor. Therefore, this node joins the virtual ring. When multiple nodes want to join simultaneously, each node delays its response to the invitation token for a random time to avoid collisions. The node that sends the invitation token then determines which node will join the virtual ring, and delivers an acceptance token to that node for joining.
Second, the node can leave the virtual ring. The polling token should be owned when a node is ready to leave the ring. If the polling token is passed to this node, it sends a message to its predecessor node to indicate that it is leaving. Consequently, the predecessor node allows this node to leave and gives the successor node a special token informing it that the predecessor has changed. This procedure is illustrated in
Figure 3. Node 1 sends a message to Node 4 when Node 1 is about to leave the ring, as shown in
Figure 3a; then, for setting up the predecessor to Node 4, a token for setting up the predecessor is passed from Node 4 to Node 2. Node 2 accepts this token and establishes Node 4 as its predecessor. Subsequently, Node 2 sends a token reply to Node 4, which establishes Node 2 as the successor. The situation after Node 1 leaves is shown in
Figure 3b. In the case that multiple nodes leave the ring at the same time, since only the nodes that obtain the token can leave the ring network, the multiple nodes will leave the ring successively, according to the order in which the token is obtained.
The procedure for initiating a virtual ring is as follows. Each cluster has a cluster head node based on the proposed clustering method. Initially, the virtual ring has only one node, the cluster head node. The cluster head broadcasts an invitation token to join. One of the ordinary nodes in the cluster is verified as joining the virtual ring. This operation continues, and all ordinary nodes in the cluster finally join the virtual ring. The virtual ring initialization is complete.
4.3. Abnormity Handling
For reliable transmission in a disaster-monitoring system, the operating mode under abnormal situations should be considered in HT-MAC. In the following, we analyze abnormal situations and describe the handling methods based on the previous work [
48].
When a node is abnormal and unavailable, the situation is shown in
Figure 4.
Figure 4a shows the normal ring. When a node leaves the neighbor node’s coverage, for example, in the case in which Node 1 leaves the coverage of Node 4, Node 4 is responsible for handling the situation. In the HT-MAC scheme, a node receives an acknowledgment frame to confirm that its successor accepts the polling token. Hence, Node 1 begins transmitting data once its acknowledgment frame is received by Node 4. If the acknowledgment frame is not received, Node 4 continues to deliver a polling token to Node 1. After several attempts, Node 4 drops delivering the polling token. At this point, the virtual ring is opened. In such a situation, Node 4 delivers a token to arrange for Node 2 to be its new successor. When Node 2 accepts the token, it sets Node 4 as its predecessor and delivers a token reply to Node 4. Node 4 accepts the reply and sets Node 2 as its successor. This virtual ring is then closed, as shown in
Figure 4b. The algorithm for handling abnormalities when a node is unavailable is presented in Algorithm 1.
In the case of a node moving out of coverage, the aforementioned operating procedure is also applicable. In fact, because the successor node cannot differentiate between failure, quitting, and interference from link noise, Algorithm 1 can be applied to all these cases.
For the abnormal situation of a no-polling token in a virtual ring, efforts must be made to bring the virtual ring to work. This is illustrated in
Figure 5a. At that moment, Node 1 departs from the coverage of all the other nodes; meanwhile, Node 1 owns the polling token, as shown in
Figure 5b. In such a situation, there are no active polling tokens in the network. In the HT-MAC scheme, if a node has not received a polling token within the maximum period time, it generates a new token to deliver. Consequently, each node ultimately creates a new polling token. Therefore, multiple tokens exist in the ring simultaneously. This case is processed as follows.
| Algorithm 1. Abnormity handling when a node is unavailable. |
Input: current node—current node with the polling token
Output: current node—current node with the new successor node |
| 1 | A node delivers the polling token to its successor node; |
| 2 | if this node does not receive the token acknowledgement frame from the successor node |
| 3 | This node continues to deliver the polling token to the successor node several times; |
| 4 | if these retransmissions all fail |
| 5 | This node delivers the token for setting up a new successor to the next node of the successor node; |
| 6 | In the next node of the successor, the token is received and the predecessor node is set up with the current node; |
| 7 | The new successor node is set up with the next node of the successor; |
| 8 | The ring is reconfigured; |
| 9 | end if |
| 10 | end if |
| 11 | End |
This method can remove multiple polling tokens, as shown in
Figure 6. In HT-MAC, each polling token frame contains two parts: a token identifier and a sequence number. The token maker is a node that generates a polled token. The token identifier is determined by the MAC addresses of the token maker node. The token maker produces an integer as the polling token sequence number and increases it by one each time the token passes through the maker.
Based on the received polling token, the sequence number and token identifier are recorded by each node in the ring. Whenever a new polling token arrives, the node checks whether the sequence number of the new token is less than that of the previous token. If this is the case, the token is deleted by the node. Meanwhile, the node checks the received token for whether the sequence number of this token is the same as the previous one, and whether the token identifier is less than the previous token. If this is the case, the token will also be deleted by the node. As shown in Algorithm 2, this method guarantees that only one token exists in a virtual ring.
| Algorithm 2. Abnormity handling of multiple tokens. |
Input: token maker—token with the ring address and token sequence number
Output: current node—deleted token |
| 1 | Token maker produces the ring address; |
| 2 | Token maker sets the token sequence number by adding one every time when it passes the token maker; |
| 3 | The nodes in the ring record the token identifier and sequence number of the polling token; |
| 4 | A node receives a new polling token; |
| 5 | if the sequence number is less than the previous one |
| 6 | Delete the received polling token; |
| 7 | else |
| 8 | if the token identifier is less than the previous token |
| 9 | Delete the polling token received; |
| 10 | else |
| 11 | This node transmits the data; |
| 12 | In this node, the polling token is transmitted to the successor node; |
| 13 | end if |
| 14 | end if |
| 15 | End |
5. Theoretical Analysis
The details of the HT-MAC scheme in the steady-state stage are shown in
Figure 7. HT-MAC is based on the duty cycle. After clustering, all nodes in one cluster begin to listen. A polling token is created and owned by the cluster head node. Subsequently, the token owner node asks the first superior node whether there are data to transmit. If the superior node has data to transmit, it simultaneously transmits the data directly to the destination node. The token owner node then asks the second superior node to transmit the data. This polling among the superior nodes is performed until the last superior node, superior node
M. Subsequently, an ordinary node with a polling token determines whether there are data to transmit. If there are data, they are transmitted to the destination node directly. The node with the polling token then transfers the polling token to the next ordinary node in the virtual ring, and the algorithm for handling abnormalities when a node is unavailable is performed. The other nodes receive polling tokens and determine whether they are successor nodes. If there is a successor node, it obtains the polling token and checks if the token is corrupted. If the token is corrupted, the successor node will discard this token and deal with the abnormality using Algorithm 1; otherwise, the token reply will be sent. Then, the successor node performs abnormity handling of multiple tokens and enters the sleeping state. After a superior node receives a token reply from an ordinary node and there are alert data in this superior node, the superior node transmits the alert data at once under the low-power listening and shortened preamble approach. Otherwise, the superior node enters a sleeping state. During the sleeping state, if an alert appears in one superior node, the alert awakens the superior node and is transmitted at once, using the low-power listening and shortened preamble approach. The next period starts at the end of the sleeping state. Therefore, the polling token is transferred in a virtual token ring network. In the following sections, to facilitate theoretical analysis, we assume that there are two superior nodes within one cluster.
We assume that the ring network includes
N + 2 nodes, and that there are two superior nodes and
N ordinary nodes. Every node follows the first come, first served queue principle, and assumes that the queue capacity is unlimited. All the nodes provide a gated service; in other words, they send the arrived frames only when it is their turn to transmit. In ordinary node
i (
i = 1, 2, …,
N), queue
i (
i = 1, 2, …,
N) represents the queue of node
i. Node
i has a Poisson process input, with an arrival rate of
λi. The service time for the frames transmitted by an ordinary node is independent. The distribution function of the service time in an ordinary node
i is
Hi(
x).
P1 and
P2 represent the queues of superior Nodes 1 and 2, respectively. The input of the superior nodes is a Poisson process, and in superior Nodes 1 and 2, the arrival rates of the Poisson process are
λP1 and
λP2, respectively. The service time for the frames transmitted by a superior node is independent. The probability distribution of the frame transmission time is a general distribution in superior Nodes 1 and 2, and the distribution functions are
HP1(
x) and
HP2(
x), respectively. In the period from
tn to
tn+1, as shown in
Figure 2, the data frame transmission time of ordinary node
i is
τi, the sleep time is
si, and the polling token walking time is
μi. Within time
t, the number of frames arriving in an ordinary node queue
i is
υi(
t). When the token ring system reaches a stable state, the instant at which ordinary node
i begins to transmit frames, the probability of ordinary node
k with
jk frames waiting is
gi(
j1,
j2, …,
jP1,
jP2). In ordinary nodes, assume that the instant when an ordinary node begins to transmit the data is …,
tn,
tn+1, …, so that … <
tn <
tn+1 < …. According to the random process, random variables may be defined as follows:
εn(
i) is the frame number in ordinary node
I when the very moment is
tn;
εn is the ordinary node identifier when ordinary node
i starts transmitting packets in the period from
tn to
tn+1; in ordinary node
i,
hi is the mean frame transmission time; and
hP1 and
hP2 are the mean frame transmission times of superior nodes
P1 and
P2, respectively. Subsequently, the state of the system at
tn is described by (
εn,
εn(1),
εn(2), …,
εn(
N),
εn(
P1),
εn(
P2)); meanwhile, the state space of the system becomes
I = {(
i,
k1,
k2, …,
kj, …,
kN,
kP1,
kP2):
i = 1, 2, …,
N;
kj = 0, 1, 2, …;
j = 1, 2, …,
N,
P1,
P2}. Hence, the transition probabilities with respect to the state (
εn,
εn(1),
εn(2), …,
εn(
N),
εn(
P1),
εn(
P2)) construct an irreducible, aperiodic Markov chain. The Markov chain is ergodic, and the system can be assumed to be in statistical equilibrium. In this case, the limiting probabilities of the states (
εn,
εn(1),
εn(2), …,
εn(
N),
εn(
P1),
εn(
P2)) are obtained as follows:
Equation (5) indicates that the number of frames in a node remains steady after a long time. For the existence of an equilibrium state, the necessary and sufficient conditions are as follows:
where
ρi is the traffic intensity for ordinary node
i, and
ρP1 and
ρP2 are the traffic intensities for superior nodes
P1 and
P2, respectively. The above equation shows that the system exists in an equilibrium state when the total traffic intensity of the system is less than 1.
FP1(x) and FP2(x) are the frame transmission times for superior nodes P1 and P2 at any instant ti with x frames, respectively. Between tn and tn+1, in superior nodes P1 and P2, the frame transmission times are FP1[εn(P1)] and FP2[εn(P2)], respectively.
Consequently, the superior and ordinary nodes have the following number of frames at instant
tn+1:
From the assumption of Poisson arrivals of node data, the following relation holds if
τi,
μi and
si do not overlap:
Therefore, the generating function of the transition probability Pr(
i + 1,
εn+1(1),
εn+1(2), …,
εn+1(
N),
εn+1(
P1),
εn+1(
P2)) is as follows:
where
A,
B, and
C are given by the following:
Letting
n→∞ on both sides of Equation (9), we obtain the generating function of the transition probability Pr(
i + 1,
εn+1(1),
εn+1(2), …,
εn+1(
N),
εn+1(
P1),
εn+1(
P2)) is
Gi(
x1,
x2 …,
xN,
xP1,
xP2) as follows:
In the above equation, when the polling token moves forward during the period from tn to tn+1, (i = 1,2, …, N) is the Laplace–Stieltjes transform of the walking time probability distribution; is the Laplace–Stieltjes transform of the sleeping time probability distribution when the polling token moves forward from tn to tn+1. In ordinary node i with a Poisson input, Hi(x) represents the busy period probability distribution, and is the Laplace–Stieltjes transform of Hi(x). In superior nodes P1 and P2 with a Poisson input, HP1(x) and HP2(x) represent the busy period probability distributions for P1 and P2, respectively, and and are the Laplace–Stieltjes transforms of HP1(x) and HP2(x), respectively. Using the above recursive formula, Gi(x1, x2 …, xN, xP1, xP2) can be described as a functional equation; however, an explicit representation cannot be derived.
We denote
gi(
j) as the mean node queue length in queue
j (
j = 1, 2, …,
N,
P1,
P2), when ordinary node
i begins to transmit data, where
i = 1, 2, …,
N:
From Equation (11) for
i = 1, 2, …,
N, we set:
In Equation (11), the differential operation of
xj and
xl→1 (
l = 1, 2, …,
N,
P1,
P2) yields
The above equation represents the relationship between the mean queue lengths of the different nodes. We then combine the first and second equations in Equation (14) with
i =
j,
j + 1, …,
i − 1,
i, and the following is obtained:
where, when
j >
i, the following is attained:
When the ordinary nodes in the token ring network are symmetric, that is,
λi =
λ,
μi =
μ,
hi =
h, and
si =
s, and the system is in the equilibrium state, the following can be set:
With Equations (14)–(17), the following is obtained:
Additionally,
g(
P1) is given by the following:
From Equations (14), (18) and (19), we obtain
Equation (20) is the mean queue length of node
k when ordinary node
k (
k = 1, 2, …,
N) begins to transmit data. Substituting Equation (20) into Equation (19) yields
From Equations (18) and (20),
g(
P2) can be expressed as
When an ordinary node
k (
k = 1, 2, …,
N) begins transmitting data, Equations (21) and (22) are the mean queue lengths of superior nodes
P1 and
P2, respectively. Thereafter, we can derive the mean cycle time of the token ring network when the ordinary nodes are symmetric and the system is in an equilibrium state:
Substituting Equations (20)–(22) into the above equation, the following is obtained:
Equation (24) represents the mean cycle time of the HT-MAC scheme, and the mean cycle time indicates the extreme case of frame delay in a virtual ring network. Because the nodes are comparatively close to each other, the radio propagation delay can be ignored. In the worst case, a frame waits for one period to be transmitted to an ordinary node; therefore, the mean upper bound of the frame delay in the ordinary node is as follows:
We can judge the frame delay in the system using the mean upper bound to satisfy the delay requirement. Unlike an ordinary node, a superior node has a higher priority; therefore, it has the chance to transmit frames in each period. Thus, the mean upper bound of the frame delay in superior Node 1 can be derived as follows:
Additionally, the mean upper bound of the frame delay in superior Node 2 can be derived as follows:
The mean queue length, mean cycle time, and mean upper bound of frame delay for the HT-MAC scheme are obtained. Next, we analyzed the performance of the proposed scheme. The theoretical results and investigations of the HT-MAC scheme were verified through simulations.
6. Performance Evaluation
In this section, we evaluate the performance of the HT-MAC scheme and compare it with those of other protocols. With Equations (20)–(22) and (24)–(27), the theoretical mean queue length, mean cycle time, and mean upper bound of the frame delay are obtained for the HT-MAC scheme. A computer simulation model of HT-MAC based on Network Simulator-2 (NS-2) was established to verify the theoretical results and evaluate scheme performance. NS-2 is an object-oriented discrete event simulator that covers a large number of network types, elements, protocols, applications, traffic models, and energy models. HT-MAC performance was evaluated in two parts: clustering performance and data transmission performance.
In the simulations, we deployed N = 100 ordinary nodes and M = 10 superior nodes that were randomly distributed in a 500 m × 500 m field. Ordinary nodes consisted of picture- and sound-monitoring nodes, and these two types of nodes each accounted for 50% of the total number of ordinary nodes. Without loss of generality, we assume that the base station is located at the center of the sensing field. In addition, the link rate was 11 Mb/s, the token frame length was 8 bytes, and for the superior and ordinary nodes, the mean data frame length was 256 bytes.
6.1. Clustering Performance
The proposed clustering method was compared with the pLEACH algorithm using the same radio model and simulation parameters. The message sizes sent by the sound-monitoring, seismic monitoring, and picture-monitoring nodes to the cluster head in each round were 5, 15, and 25 kB. The initial energies of the sound-, seismic, and picture-monitoring nodes were 2 J, 3 J, and 5 J, respectively. The other simulation parameters of the proposed model are listed in
Table 3.
In HT-MAC,
Trwtch, the residual working time as a cluster head, is the variable that determines which node is the cluster head. We assume that a sensor node gains
l bits of sensing data in time
tsc; thus,
Psc the mean power of sensing and calculation for this node is
where
Esc is the energy consumption for sensing and calculating this type of node. If a sensor node aggregates
k bits of data and relays them to a base station at a distance
d in time
tar,
Par is the mean power of the data aggregation and relay as a cluster head:
Through clustering simulations, the number of alive nodes for pLEACH and HT-MAC are is in
Figure 8. At the same number of rounds, HT-MAC had more live nodes than pLEACH. Owing to the uneven energy consumption, pLEACH started to experience node energy exhaustion at over 847 rounds. However, HT-MAC did not experience node energy exhaustion until more than 1227 rounds. After experiencing a rapid decline, the number of live HT-MAC nodes gradually stabilized at approximately 1700 rounds. When the number of members in a cluster decreases, the energy consumption of the cluster head for relaying decreases significantly. A similar phenomenon was observed with pLEACH.
The total amount of data received at the base station during the network lifetime is shown in
Figure 9. This shows that the amount of received data increases smoothly at the beginning for HT-MAC and pLEACH. After 847 rounds, HT-MAC received significantly more data at the base station than the pLEACH algorithm, and the growth of the data received by pLEACH became slower. The data received by HT-MAC also become slower after 1227 rounds, but HT-MAC still receives much more data than the pLEACH algorithm, and it perseveres longer.
6.2. Data Transmission Performance
After clustering, the nodes transmitted sensing data at the steady-state stage in each cluster. The mean queue length, mean cycle time, and mean upper bound of the frame delay were obtained for the HT-MAC scheme. We verified the results of the theoretical analysis and studied the system performance as shown in
Figure 10,
Figure 11,
Figure 12,
Figure 13,
Figure 14,
Figure 15,
Figure 16 and
Figure 17.
The simulations used the same parameters as in the theoretical analysis, and the system was assumed to have 5, 10, and 20 ordinary nodes in a cluster. Each cluster consists of two superior nodes. We compared the simulation and theoretical results with the change in total traffic intensity under different conditions. The total traffic intensity is the ratio of all node loads (both ordinary and superior nodes) to the link rate. The total traffic intensity range is from 0.1 to 0.95 in theoretical calculations and simulations, with a step of 0.05. Ordinary nodes have symmetrical inputs, the traffic intensity proportion of the superior node to the ordinary node is denoted by L, and the values are 1 and 2.
Figure 10 presents the mean queue length of superior Node 1, and shows that the simulation results agree with the theoretical results under different degrees of total traffic intensity. As shown in
Figure 10, when the total traffic intensity increases, the mean queue length of superior node 1 also increases. When the load proportion
L is the same, more nodes in the cluster lead to a smaller mean queue length for the superior node. In fact, more nodes in the cluster cause a lower traffic intensity for superior node 1 under the same total traffic intensity. When the number of nodes is the same (
N = 5) and
L is larger, the mean length of the superior node increases.
Figure 11 presents the mean queue length of superior Node 2 and shows that the simulation results conform to the theoretical results under different degrees of total traffic intensity.
Figure 11 is similar to
Figure 10; however, the mean queue length of superior Node 2 is less than that of superior Node 1 under the same configuration.
Figure 12 shows the mean queue length of ordinary nodes, which agrees with the theoretical results under different degrees of total traffic intensity. This verified the accuracy of the theoretical analysis. In
Figure 12, when the total traffic intensity exceeds 0.8, the mean queue length of ordinary nodes increases substantially.
Figure 13 shows the mean cycle times for the different situations. The simulation and theoretical results were in agreement under various conditions.
Figure 13 shows that the mean cycle time is similar when the number of nodes and total traffic intensity are the same. With
N = 5, the mean cycle time increases when the total traffic intensity exceeds 0.8. When
N = 20 and the total traffic intensity exceeds 0.7, the mean cycle time increases rapidly.
Frame delays are vital in disaster-monitoring applications. As part of the WirelessHART simulation scenario, alert data were added to WirelessHART. Contention-free period slots were used for alert data, whereas contention access period slots were used for ordinary data. In the WirelessHART simulation, superior data were based on a contention-free period. We created a DRX simulation scenario and set the alert and superior data delay thresholds to 0.4 s. The traffic intensity proportion of the superior node to that of the ordinary node is 2. The queue buffers of the superior, ordinary, and alert data were 1 kB each. As shown in
Figure 14,
Figure 15,
Figure 16 and
Figure 17, the performance of HT-MAC is presented and compared with those of the WirelessHART and DRX protocols.
In the HT-MAC scheme, superior data frames are much faster than ordinary data frames. With increasing traffic intensity, superior data frame delays change only slightly, far less than the frame delay of ordinary data.
The mean queue length of the superior data at the superior node is shown in
Figure 15. When
N = 5, the mean queue length of the superior data for DRX starts to rise rapidly at a traffic intensity of 0.5, and reaches the maximum of the queue buffer at a traffic intensity of 0.65. At
N = 20, the DRX protocol is similar to that at
N = 5. When
N = 5, the mean queue length of the superior data for WirelessHART starts to increase rapidly at a traffic intensity of 0.7. However, when
N = 20, the mean queue length of the superior data for WirelessHART continues to increase slowly. When
N = 5 and 20, HT-MAC always has a very short queue length for superior data.
Compared with the DRX scheme, HT-MAC has a smaller data-frame delay when the traffic intensity increases. As the traffic intensity increases above 0.4 (N = 5) and 0.5 (N = 20), DRX’s superior data frame delay increases rapidly. The results for WirelessHART were similar to those for DRX. When the traffic intensity exceeds 0.4 (N = 5), the superior data frame delay of WirelessHART increases rapidly.
HT-MAC’s alert data frame delay is clearly better than that of DRX, particularly when the total traffic intensity exceeds 0.4, and the alert data frame delay remains low and is smaller than that of WirelessHART. For N = 5, the maximum alert data frame delay of HT-MAC is 9 ms and 15 ms for N = 20. The ordinary data frame delay of HT-MAC also remains low when the total traffic intensity increases. However, when the total traffic intensity exceeds 0.4, the ordinary data frame delay of WirelessHART increases. When the total traffic intensity exceeds 0.5, the ordinary data frame delay of DRX increases. The mean upper bound of frame delay is an important performance metric. The simulation results showed that 99.23% of the frame delays satisfied the mean upper bound of the frame delay in an ordinary node, 99.57% satisfied the mean upper bound for superior Node 1, and 99.42% satisfied the mean upper bound for superior Node 2. For HT-MAC, the frame delay performance for the three types of data was better than those of the WirelessHART and DRX schemes.
Throughput is also a key indicator in disaster-monitoring applications. For N = 20, the mean throughput of the ordinary node is 364 kb/s, and that of the superior node is 732 kb/s. When N = 5, the mean throughput of the ordinary node is 973 kb/s, and that of the superior node is 1.9 Mb/s. In the HT-MAC scheme, the delay and throughput specifications for superior, alert, and ordinary data follow the requirements for crucial services such as earthquake surveillance.
7. Conclusions and Future Work
In disaster-monitoring scenarios, real-time accurate information with uninterrupted monitoring is crucial. In this study, we first present a collaborative disaster-monitoring system based on WSNs, and show the entire architecture of the system. Then, we obtain seismic data in a highly energy-efficient manner, based on the compressed sensing method.
In this study, a superior node hybrid scheme, HT-MAC, for disaster monitoring in wireless sensor networks is proposed, and the operating procedures of clustering and data transmission are presented. The proposed clustering algorithm for heterogeneous networks can effectively extend the network’s lifetime. HT-MAC operates in duty cycle mode at the steady-state stage, and ordinary nodes transmit multimedia data based on a virtual token ring. During each period, seismic data are promptly transmitted when each superior node is polled. Owing to the relatively short active state of the sensor nodes, the alert data are transmitted with a low-power listening and shortened preamble approach during the sleep state to satisfy the delay requirement. HT-MAC can simultaneously satisfy the requirements of three types of data for disaster-monitoring applications. These three types of data are ordinary data with high throughput, seismic data with high throughput and low delay, and alert data with high reliability and low delay of tens of milliseconds. HT-MAC must support reliable transmission, even in abnormal situations, and the handling procedures for abnormal situations are described in detail. Based on embedded Markov chains, a model of the HT-MAC scheme was developed, and the mean queue length, mean cycle time, and mean upper bound of the frame delay were obtained.
A simulation model of HT-MAC was built, and the simulation results verified the theoretical analysis. Using the simulation models of HT-MAC and pLEACH, the HT-MAC clustering algorithm significantly outperformed the pLEACH algorithm and increased the lifetime of the network. Based on the simulations of WirelessHART and DRX, the frame delay performance of HT-MAC was better than that of WirelessHART and DRX. We found that the mean delay of the superior and alert data was far less than that of the ordinary data, and a low delay level was maintained, especially when the traffic intensity was heavy. The alert data have a maximum frame delay of 15 ms, and HT-MAC provided a data rate of several hundred kb/s for superior and ordinary data. These results satisfy the requirements of disaster-monitoring applications.
As the next step, we will establish a testbed to analyze and validate the HT-MAC scheme. Technological advances have enabled the development of disaster-monitoring systems [
13]; collaborative disaster-monitoring systems can be widely used in earthquake early warning and rescue, volcanic eruption early warning and monitoring, landslide early warning, and other disaster-monitoring applications. In the future, we will implement collaborative disaster-monitoring systems in order to perform seismic monitoring. Practical application of HT-MAC may significantly improve our ability to cope with disasters.