VASERP: An Adaptive, Lightweight, Secure, and Efficient RFID-Based Authentication Scheme for IoV
Abstract
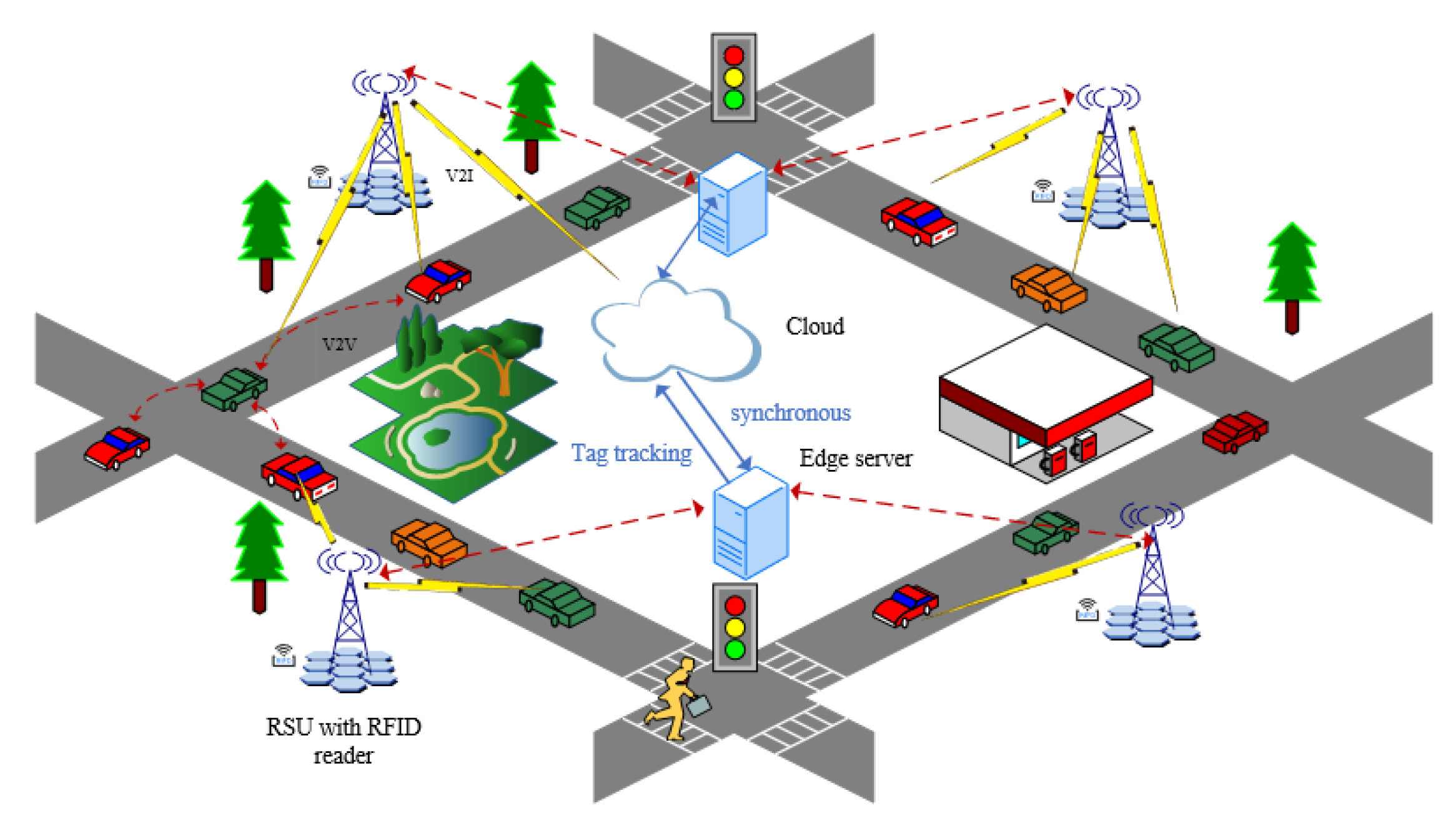
:1. Introduction
- This paper presents an edge server-based RFID authentication protocol for IoV, which reduces the computing and communication costs of the cloud due to the high overhead of cloud computing, communication, and storage;
- The protocol proposed in this research is the first to achieve fast authentication in the IoV traffic congestion scenario, significantly lower computing and communication overhead, and to satisfy security and lightweight authentication requirements.
2. Related Work
- (1)
- Lightweight RFID authentication protocols based on bit operationsTo reduce computational and communication overhead in the RFID authentication process, several scholars have proposed lightweight RFID protocols based on bit operations. Chen et al. [17] introduced a lightweight authentication protocol based on an asymmetric encryption algorithm, where the reader performs most of the complex work, and the tag only needs to execute simple operations such as bitwise XOR, one-bit circular shift, and bit flip. This method reduces computational and communication overhead. Fan et al. [18] proposed a lightweight RFID authentication privacy protection scheme that encrypts authentication data through the operation of a cross and the operation of rotation. Although the computational overhead of this algorithm is relatively small, it is vulnerable to attacks. Aghili et al. [19] introduced a lightweight authentication protocol and designed a more secure function to encrypt private data in the authentication process by improving the function. Fan et al. [20] proposed an efficient protocol that uses rotation and enhanced permutation encryption to reduce RFID overhead. However, the ambiguous timestamp in this protocol is vulnerable to brute-force attacks, leading to secret information leakage. Although these protocols are lightweight, they use simple bit operations such as XOR, bit flip, and rotation to encrypt private data, which can be vulnerable to attacks and may result in key leakage.
- (2)
- RFID authentication protocols based on quadratic residueScholars have implemented RFID mutual authentication using the quadratic residue algorithm to improve security. Fan et al. [21] proposed a lightweight authentication protocol based on the quadratic residue and the operation of rotation. However, the computational speed of the quadratic residue is slow, leading to high computational overhead, which does not meet the lightweight requirements. Doss et al. [22] proposed a grouping-proof authentication protocol based on the quadratic residue zero-knowledge property. However, in this protocol, the reader is not authenticated, which can make it vulnerable to counterfeit readers that illegally read the tag data. Lee et al. [23] proposed a protocol based on homomorphic encryption and quadratic residue to address the issue of ownership transfer in the RFID of the IoV, which can achieve batch ownership transfer of tags. However, Tu et al. [24] conducted a security assessment of the protocol and identified security loopholes that could result in attacks such as replay, tracking, and simulated tag attack. To address these issues, Song et al. [25] proposed a quadratic residue-based zero-knowledge authentication protocol with active tags that have zero-knowledge properties.
- (3)
- RFID authentication protocols based on grouping-proofTo achieve fast authentication in large-scale RFID systems, Rahman et al. [26] proposed a group-based anonymous privacy authentication protocol to achieve batch authentication. This method is better than the original tree-based authentication protocol, and the group-based protocol security level is higher. To address the security challenge of simultaneous authentication of multiple readers and tags in a distributed RFID system, Liu et al. [27] proposed a Grouping-Proofs-Based Authentication Protocol (GUPA) that can withstand classic attacks such as replay, forgery, and tracking. However, Sun et al. [28] pointed out that the GUPA scheme [27] is vulnerable to man-in-the-middle attacks and can result in key leakage, leading to replay, forgery, tracking, and rejection of proofs. Therefore, Sun et al. [28] utilized a hash function to encrypt private data for better authentication security. To solve the problem of high communication overhead when authenticating tags in batches, Yang et al. [29] proposed an efficient authentication grouping-proof protocol based on symmetric keys and bit collisions, which can solve the conflict issue of one-time authentication of multiple tags.
- (4)
- RFID authentication protocol based on ECCWu et al. [30] introduced a UAV-assisted IoV authentication protocol that utilizes ECC and hash functions for encryption. Analysis shows that the protocol can withstand various attacks, but its computational and communication overheads are relatively high. Shabani et al. [31] proposed an ECC-based RFID authentication protocol for IoV, but this protocol may result in tag tracking. Kumar et al. [32] proposed an ECC-based RFID authentication protocol for vehicle cloud computing, RSEAP, which is resistant to man-in-the-middle attacks and replay attacks and has high-performance communication. However, Safkhani et al. [33] pointed out that the protocol proposed by Kumar et al. could not provide the claimed security or improved vulnerability based on RSEAP. They therefore proposed a more secure RSEAP2 protocol with less computing and communication overhead, but with more overhead in authentication. During the process, neither the tag nor the cloud will verify the identity of the reader, which may lead to man-in-the-middle attacks and impersonation of the reader attacks. Meher et al. [34] proposed an ECC-based RFID authentication protocol without public/private key pairs to address the issue of limited resources of RFID tags, greatly reducing the computation and storage costs of the tags.
- (5)
- Other RFID authentication protocolsChander et al. [35] proposed an RFID protocol based on hash functions and bit logic functions, which are easy to implement but vulnerable to attacks. Jangirala et al. [36] proposed a blockchain RFID protocol based on a single hash function, bit-by-bit dissimilarity, and bit-by-bit rotation operations, enhancing security and increasing communication overhead. Salem et al. [37] proposed a privacy-preserving RFID authentication protocol based on ElGamal encryption. The protocol allows for direct authentication between the tag and server without the need for the reader’s involvement. Unlike traditional authentication methods in which both the tag and the server authenticate each other, in this protocol, only the tag authenticates the server. However, it also makes the protocol sensitive to beacon attacks simulated by potential attackers. Shariq et al. [38] proposed a Schnorr-based RFID authentication protocol. However, the protocol provides only one-way verification of the server and does not verify the legitimacy of the tag. Akram et al. [39] proposed an RFID authentication protocol based on cloud computing for IoV. The protocol utilizes a chaotic map to achieve mutual authentication and offers significant advantages in terms of computing, communication, and storage compared to other protocols. However, the mutual authentication process within the protocol is cloud-based, which may overload computing, communication, and cloud storage.
3. Preliminaries
3.1. ECC Algorithm over Finite Fields
- ;
- Let , then , where represents the additive inverse of P;
- Let , then ;
- Let , , then , is determined by:where
3.2. Difficult Problems
3.3. Adversary Model
- (1)
- An adversary can interrupt communication between readers, tags, and edge servers through common channels;
- (2)
- The adversary in this paper can launch active and passive attacks against the protocol;
- (3)
- Adversaries can launch attacks using fake readers or tags.
4. The VASERP Protocol
| Algorithm 1: An adaptive, lightweight, secure, and efficient RFID-based authentication scheme for IoV. |
Register with the cloud; the cloud synchronizes the RID to the edge server after hashing and encryption broadcast to the surrounding area, where ,. receive if compute if Perform rapid mutual authentication phase else Perform the transfer of ownership phase else return 0 (Request Timeout) |
4.1. Initialization Phase
4.2. Registration Phase
4.2.1. Tag Registration
4.2.2. Reader Registration
4.3. Fast Mutual Authentication Phase
4.4. The Ownership Transfer Phase
5. Security Analysis
5.1. Formal Analysis
5.2. Informal Analysis
6. Performance Comparison and Discussion
6.1. Security Comparison
6.2. Computational Overhead Comparison
6.3. Communication Overhead Comparison
6.4. Storage Overhead Comparison
7. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Lai, J.; Luo, C.; Wu, J.; Li, J.; Wang, J.; Chen, J.; Feng, G.; Song, H. TagSort: Accurate relative localization exploring RFID phase spectrum matching for Internet of Things. IEEE Internet Things J. 2019, 7, 389–399. [Google Scholar] [CrossRef]
- Cao, B.; Gu, Y.; Lv, Z.; Yang, S.; Zhao, J.; Li, Y. RFID reader anticollision based on distributed parallel particle swarm optimization. IEEE Internet Things J. 2020, 8, 3099–3107. [Google Scholar] [CrossRef]
- Gupta, B.B.; Gaurav, A.; Marín, E.C.; Alhalabi, W. Novel graph-based machine learning technique to secure smart vehicles in intelligent transportation systems. IEEE Trans. Intell. Transp. Syst. 2022. [Google Scholar] [CrossRef]
- Hammoud, A.; Otrok, H.; Mourad, A.; Dziong, Z. On demand fog federations for horizontal federated learning in IoV. IEEE Trans. Netw. Serv. Manag. 2022, 19, 3062–3075. [Google Scholar] [CrossRef]
- Liang, W.; Xie, S.; Cai, J.; Wang, C.; Hong, Y.; Kui, X. Novel private data access control scheme suitable for mobile edge computing. China Commun. 2021, 18, 92–103. [Google Scholar] [CrossRef]
- Diao, C.; Zhang, D.; Liang, W.; Li, K.C.; Hong, Y.; Gaudiot, J.L. A novel spatial-temporal multi-scale alignment graph neural network security model for vehicles prediction. IEEE Trans. Intell. Transp. Syst. 2022, 24, 904–914. [Google Scholar] [CrossRef]
- Song, X.; Li, X.; Tang, W.; Zhang, W. A fusion strategy for reliable vehicle positioning utilizing RFID and in-vehicle sensors. Inf. Fusion 2016, 31, 76–86. [Google Scholar] [CrossRef]
- Qin, H.; Peng, Y.; Zhang, W. Vehicles on RFID: Error-cognitive vehicle localization in GPS-less environments. IEEE Trans. Veh. Technol. 2017, 66, 9943–9957. [Google Scholar] [CrossRef]
- Chen, R.; Huang, X.; Zhou, Y.; Hui, Y.; Cheng, N. UHF-RFID-based real-time vehicle localization in GPS-less environments. IEEE Trans. Intell. Transp. Syst. 2021, 23, 9286–9293. [Google Scholar] [CrossRef]
- Pedraza, C.; Vega, F.; Manana, G. PCIV, an RFID-based platform for intelligent vehicle monitoring. IEEE Intell. Transp. Syst. Mag. 2018, 10, 28–35. [Google Scholar] [CrossRef]
- Long, J.; Liang, W.; Li, K.C.; Wei, Y.; Marino, M.D. A Regularized Cross-Layer Ladder Network for Intrusion Detection in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2022, 19, 1747–1755. [Google Scholar] [CrossRef]
- Zhang, S.; Hu, B.; Liang, W.; Li, K.C.; Gupta, B.B. A Caching-based Dual K-Anonymous Location Privacy-Preserving Scheme for Edge Computing. IEEE Internet Things J. 2023, 10, 9768–9781. [Google Scholar] [CrossRef]
- Liang, W.; Yang, Y.; Yang, C.; Hu, Y.; Xie, S.; Li, K.C.; Cao, J. PDPChain: A consortium blockchain-based privacy protection scheme for personal data. IEEE Trans. Reliab. 2022. [Google Scholar] [CrossRef]
- Fang, W.; Li, Y.; Zhang, H.; Xiong, N.; Lai, J.; Vasilakos, A.V. On the throughput-energy tradeoff for data transmission between cloud and mobile devices. Inf. Sci. 2014, 283, 79–93. [Google Scholar] [CrossRef]
- Sandor, V.K.A.; Lin, Y.; Li, X.; Lin, F.; Zhang, S. Efficient decentralized multi-authority attribute based encryption for mobile cloud data storage. J. Netw. Comput. Appl. 2019, 129, 25–36. [Google Scholar] [CrossRef]
- Yang, A.; Weng, J.; Yang, K.; Huang, C.; Shen, X. Delegating authentication to edge: A decentralized authentication architecture for vehicular networks. IEEE Trans. Intell. Transp. Syst. 2020, 23, 1284–1298. [Google Scholar] [CrossRef]
- Chen, M.; Chen, S.; Fang, Y. Lightweight anonymous authentication protocols for RFID systems. IEEE/ACM Trans. Netw. 2017, 25, 1475–1488. [Google Scholar] [CrossRef]
- Fan, J.; Elmagarmid, A.K.; Zhu, X.; Aref, W.G.; Wu, L. ClassView: Hierarchical video shot classification, indexing, and accessing. IEEE Trans. Multimed. 2004, 6, 70–86. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H.; Kaliyar, P.; Conti, M. SecLAP: Secure and lightweight RFID authentication protocol for Medical IoT. Future Gener. Comput. Syst. 2019, 101, 621–634. [Google Scholar] [CrossRef]
- Fan, K.; Luo, Q.; Zhang, K.; Yang, Y. Cloud-based lightweight secure RFID mutual authentication protocol in IoT. Inf. Sci. 2020, 527, 329–340. [Google Scholar] [CrossRef]
- Fan, K.; Zhu, S.; Zhang, K.; Li, H.; Yang, Y. A lightweight authentication scheme for cloud-based RFID healthcare systems. IEEE Netw. 2019, 33, 44–49. [Google Scholar] [CrossRef]
- Doss, R.; Trujillo-Rasua, R.; Piramuthu, S. Secure attribute-based search in RFID-based inventory control systems. Decis. Support Syst. 2020, 132, 113270. [Google Scholar] [CrossRef]
- Lee, C.C.; Li, C.T.; Cheng, C.L.; Lai, Y.M.; Vasilakos, A.V. A novel group ownership delegate protocol for RFID systems. Inf. Syst. Front. 2019, 21, 1153–1166. [Google Scholar] [CrossRef]
- Tu, Y.J.; Kapoor, G.; Piramuthu, S. On Group Ownership Delegate Protocol for RFID Systems. Inf. Syst. Front. 2022, 24, 1577–1584. [Google Scholar] [CrossRef]
- Song, J.; Harn, P.W.; Sakai, K.; Sun, M.T.; Ku, W.S. An RFID zero-knowledge authentication protocol based on quadratic residues. IEEE Internet Things J. 2021, 9, 12813–12824. [Google Scholar] [CrossRef]
- Rahman, F.; Hoque, M.E.; Ahamed, S.I. Anonpri: A secure anonymous private authentication protocol for RFID systems. Inf. Sci. 2017, 379, 195–210. [Google Scholar] [CrossRef]
- Liu, H.; Ning, H.; Zhang, Y.; He, D.; Xiong, Q.; Yang, L.T. Grouping-proofs-based authentication protocol for distributed RFID systems. IEEE Trans. Parallel Distrib. Syst. 2012, 24, 1321–1330. [Google Scholar] [CrossRef]
- Sun, D.Z.; Mu, Y. Security of grouping-proof authentication protocol for distributed RFID systems. IEEE Wirel. Commun. Lett. 2017, 7, 254–257. [Google Scholar] [CrossRef]
- Yang, A.; Boshoff, D.; Hu, Q.; Hancke, G.P.; Luo, X.; Weng, J.; Mayes, K.; Markantonakis, K. Privacy-preserving group authentication for rfid tags using bit-collision patterns. IEEE Internet Things J. 2021, 8, 11607–11620. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Luo, X.; Gu, K. A novel authentication scheme for edge computing-enabled Internet of Vehicles providing anonymity and identity tracing with drone-assistance. J. Syst. Archit. 2022, 132, 102737. [Google Scholar] [CrossRef]
- Shabani, F.; Gharaee, H.; Ghaffari, F. An intelligent RFID-enabled authentication protocol in VANET. In Proceedings of the 2018 9th International Symposium on Telecommunications (IST), Tehran, Iran, 17–19 December 2018; pp. 587–591. [Google Scholar]
- Kumar, V.; Ahmad, M.; Mishra, D.; Kumari, S.; Khan, M.K. RSEAP: RFID based secure and efficient authentication protocol for vehicular cloud computing. Veh. Commun. 2020, 22, 100213. [Google Scholar] [CrossRef]
- Safkhani, M.; Camara, C.; Peris-Lopez, P.; Bagheri, N. RSEAP2: An enhanced version of RSEAP, an RFID based authentication protocol for vehicular cloud computing. Veh. Commun. 2021, 28, 100311. [Google Scholar] [CrossRef]
- Meher, B.K.; Amin, R.; Das, A.K.; Khan, M.K. KL-RAP: An Efficient Key-Less RFID Authentication Protocol Based on ECDLP for Consumer Warehouse Management System. IEEE Trans. Netw. Sci. Eng. 2022, 9, 3411–3420. [Google Scholar] [CrossRef]
- Chander, B.; Gopalakrishnan, K. A secured and lightweight RFID-tag based authentication protocol with privacy-preserving in Telecare medicine information system. Comput. Commun. 2022, 191, 425–437. [Google Scholar] [CrossRef]
- Jangirala, S.; Das, A.K.; Vasilakos, A.V. Designing secure lightweight blockchain-enabled RFID-based authentication protocol for supply chains in 5G mobile edge computing environment. IEEE Trans. Ind. Inform. 2019, 16, 7081–7093. [Google Scholar] [CrossRef]
- Salem, F.M.; Amin, R. A privacy-preserving RFID authentication protocol based on El-Gamal cryptosystem for secure TMIS. Inf. Sci. 2020, 527, 382–393. [Google Scholar] [CrossRef]
- Shariq, M.; Singh, K.; Bajuri, M.Y.; Pantelous, A.A.; Ahmadian, A.; Salimi, M. A secure and reliable RFID authentication protocol using digital schnorr cryptosystem for IoT-enabled healthcare in COVID-19 scenario. Sustain. Cities Soc. 2021, 75, 103354. [Google Scholar] [CrossRef]
- Akram, W.; Mahmood, K.; Li, X.; Sadiq, M.; Lv, Z.; Chaudhry, S.A. An energy-efficient and secure identity based RFID authentication scheme for vehicular cloud computing. Comput. Netw. 2022, 217, 109335. [Google Scholar] [CrossRef]
- Chandrakar, P.; Om, H. A secure and robust anonymous three-factor remote user authentication scheme for multi-server environment using ECC. Comput. Commun. 2017, 110, 26–34. [Google Scholar] [CrossRef]
- Lee, Y.K.; Sakiyama, K.; Batina, L.; Verbauwhede, I. Elliptic-curve-based security processor for RFID. IEEE Trans. Comput. 2008, 57, 1514–1527. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.; Khan, M.K.; Kumar, N. A robust and anonymous patient monitoring system using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 80, 483–495. [Google Scholar] [CrossRef]





| Symbols | Description |
|---|---|
| , | the jth reader, the identifier of the jth reader |
| , | the ith tag, the identifier of the ith tag |
| kth edge server | |
| timestamp | |
| the random numbers generated by the tag, reader, and server, respectively | |
| k | the key is shared among the edge server, reader, and tag |
| ⊕ | XOR operation |
| cascade operation | |
| p | the order of a finite field is a large prime number |
| finite field of order p | |
| elliptic curve over a finite field of large prime order p | |
| G | the base point of |
| Q | the public key of the edge server |
| P | public key of reader and tag |
| d | the private key of the edge server, which is a large prime number |
| h | hash function |
| Index | Content |
|---|---|
| … | … |
| Protocol | VASERP | [31] | [32] | [33] | [34] |
|---|---|---|---|---|---|
| Tag anonymity | yes | no | yes | yes | no |
| Resistance against replay attacks | yes | no | no | yes | yes |
| Resistance against man-in-the-middle attacks | yes | no | no | yes | no |
| Mutual authentication | yes | yes | yes | yes | no |
| Forward security | yes | no | yes | yes | yes |
| Resistance against tag tracking | yes | no | yes | yes | yes |
| Resistance against impersonation attacks | yes | yes | no | yes | yes |
| Key agreement protocol | yes | yes | yes | yes | yes |
| Resistance against desynchronization attacks | yes | yes | yes | yes | yes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gong, Y.; Li, K.; Xiao, L.; Cai, J.; Xiao, J.; Liang, W.; Khan, M.K. VASERP: An Adaptive, Lightweight, Secure, and Efficient RFID-Based Authentication Scheme for IoV. Sensors 2023, 23, 5198. https://doi.org/10.3390/s23115198
Gong Y, Li K, Xiao L, Cai J, Xiao J, Liang W, Khan MK. VASERP: An Adaptive, Lightweight, Secure, and Efficient RFID-Based Authentication Scheme for IoV. Sensors. 2023; 23(11):5198. https://doi.org/10.3390/s23115198
Chicago/Turabian StyleGong, Yinyan, Kuanching Li, Lijun Xiao, Jiahong Cai, Jiahong Xiao, Wei Liang, and Muhammad Khurram Khan. 2023. "VASERP: An Adaptive, Lightweight, Secure, and Efficient RFID-Based Authentication Scheme for IoV" Sensors 23, no. 11: 5198. https://doi.org/10.3390/s23115198
APA StyleGong, Y., Li, K., Xiao, L., Cai, J., Xiao, J., Liang, W., & Khan, M. K. (2023). VASERP: An Adaptive, Lightweight, Secure, and Efficient RFID-Based Authentication Scheme for IoV. Sensors, 23(11), 5198. https://doi.org/10.3390/s23115198







